9.1 Configuring the Web Policy Agents Load Balancer
Load Balancer 5 can be located in a less-secured zone, and handles traffic for the Web Policy Agents.
Load Balancer 5 is configured for simple persistence so that browser requests from the same IP address will always be directed to the same Web Policy Agent instance . This guarantees that the requests from the same user session will always be sent to the same Web Policy Agent instance. This is important from the performance perspective. Each Web Policy Agent must validate the user session and evaluate applicable policies. The results are subsequently cached on the individual Web Policy Agent to improve the performance. If no load balancer persistence is set, and the same user's requests are spread across two agents, then each agent must build up its own cache. To do so, both agents must validate the session and evaluate policies. This effectively doubles the workload on the Access Manager servers, and cuts the overall system capacity by half. The problem becomes even more acute as the number of Web Policy Agents increases further.
As a general rule, in situations where each Web Policy Agent instance is protecting identical resources, some form of load balancer persistence is highly recommended for the performance reasons. The actual type of persistence may vary when a different load balancer is used, as long as it achieves the goal of sending the requests from the same user session to the same Web Policy Agent instance.
Use the following as your checklist for configuring the Web Policy Agents load balancer:
Figure 9–1 Policy Agents and Load Balancers
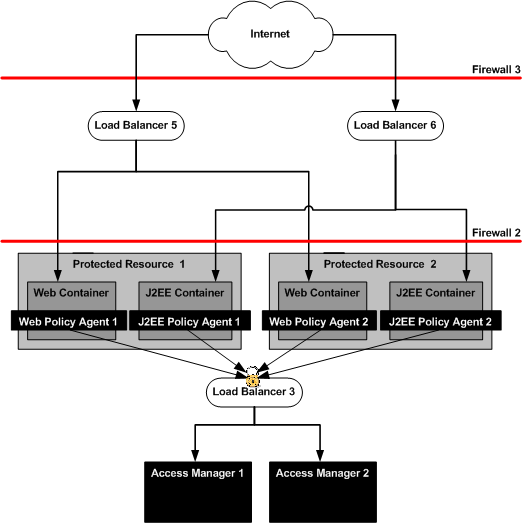
 To Configure the Web Policy Agents Load Balancer
To Configure the Web Policy Agents Load Balancer
-
Go to URL for the Big IP load balancer. login page and log in.
https://ls-f5.example.com
-
Log in using the following information:
- User name:
-
username
- Password:
-
password
-
Create a Pool.
A pool contains all the backend server instances.
-
Open the Configuration Utility.
Click “Configure your BIG-IP (R) using the Configuration Utility.”
-
In the left pane, click Pools.
-
On the Pools tab, click the Add button.
-
In the Add Pool dialog, provide the following information:
- Pool Name
-
Example: WebAgent-Pool
- Load Balancing Method
-
Round Robin
- Resources
-
Add all the Web Policy Agent IP addresses. In this example, add the IP address and port number for ProtectedResource-1:1080 and for ProtectedResource-2:1080.
-
Click the Done button.
-
-
Configure the load balancer for simple persistence.
-
Add a Virtual Server.
If you encounter Javascript errors or otherwise cannot proceed to create a virtual server, try using Microsoft Internet Explorer for this step.
-
In the left frame, Click Virtual Servers.
-
On the Virtual Servers tab, click the Add button.
-
In the Add a Virtual Server dialog box, provide the following information:
- Address
-
xxx.xx.69.14 (for LoadBalancer-5.example.com )
- Service
-
90
- Pool
-
WebAgent-Pool
-
Continue to click Next until you reach the Pool Selection dialog box.
-
In the Pool Selection dialog box, assign the Pool (WebAgent-Pool) that you have just created.
-
Click the Done button.
-
-
Add Monitors.
-
Click the Monitors tab, and then click the Add button.
In the Add Monitor dialog provide the following information:
- Name:
-
WebAgent-http
- Inherits From:
-
Choose http.
-
Click Next.
In the Configure Basic Properties page, click Next.
-
In the Configure ECV HTTP Monitor, in the Send String field, enter the following:
GET / launch.html
Click Next.
-
In the Destination Address and Service (Alias) page, click Done.
On the Monitors tab, the monitor you just added is now contained in the list of monitors.
-
Click the Basic Associations tab.
Look for the IP addresses for ProtectedResource-1:1080 and ProtectedResourece-2:1080.
-
Mark the Add checkbox for ProtectedResource-1 and ProtectedResource-2.
-
At the top of the Node column, choose the monitor that you just added, WebAgent-http.
-
Click Apply.
-
 To Configure the Web Policy Agent
To Configure the Web Policy Agent
In this procedure you modify the AMAgent.properties file. Map Protected Resource 1 and Protected Resource 2 to Load Balancer 5.
-
Log in as a root user to Protected Resource 1.
# cd /etc/opt/SUNWam/agents/es6/ config/_opt_SUNWwbsvr_https-ProtectedResource-1.example.com
-
Use a text editor to modify the AMAgent.properties file.
Make a backup of AMAgent.properties, and then add the following entry:
com.sun.am.policy.agents.config.fqdn.map = LoadBalancer-5.example.com|LoadBalancer-5.example.com
For this property:
com.sun.am.policy.agents.config.notenforced_list
append the following to the end of the value string :
http://ProtectedResource-1.example.com:1080/launch.html http://LoadBalancer-5.example.com:90/launch.html
-
Save the file.
-
Log in as a root user to Protected Resource 2.
# cd /etc/opt/SUNWam/agents/es6/ config/_opt_SUNWwbsvr_https-ProtectedResource-2.example.com
-
Use a text editor to modify the AMAgent.properties file.
Make a backup of AMAgent.properties, and then add the following entry:
com.sun.am.policy.agents.config.fqdn.map = LoadBalancer-5.example.com|LoadBalancer-5.example.com
For this property:
com.sun.am.policy.agents.config.notenforced_list
append the following to the end of the value string :
http://ProtectedResource-2.example.com:1080/launch.html http://LoadBalancer-5.example.com:90/launch.html
-
Save the file.
 To Create Policies for the Agent Resources
To Create Policies for the Agent Resources
The policies you create here are used in a the subsequent verification procedure.
-
Create a referral policy for Load Balancer 5.
-
Go to the Access Manager URL:
https://loadbalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
On the Access Control tab, click the realm name example.com.
-
Click the Policies tab.
-
Click the “Referral URL Policy for users realm” link.
-
In the Edit Policy page, under Rules, click New.
-
In the page “Step 1 of 2: Select Service Type for the Rule,” select “URL Policy Agent (with resource name), and then click Next.
-
In the page “Step 2 of 2: New Rule,” provide the following information:
- Name:
-
URL Rule for LoadBalancer-5
- Resource Name:
-
http://LoadBalancer-5.example.com:90/*
-
Click Finish, and then click Save.
The new rules you added are now contained in the Rules list.
-
-
Create a policy in the users realm.
-
In the Edit Policy page, click the Realms link.
-
On the Access Control tab, click the users link.
-
Click the Policies tab, and then click New Policy.
In the Name field, enter URL Policy for LoadBalancer-5.
-
Under Rules, click NEW.
-
In the page “Step 1 of 2: Select Service Type for the Rule,” click Next.
-
In the page “Step 2 of 2: New Rule,” provide the following information:
- Name:
-
Enter LoadBalancer-5.
- Parent Resource Name:
-
Click http://LoadBalancer-5.example.com:90/* to select it.
The Parent Resource Name you selected is now contained in the Resource Name field.
- GET
-
Mark the checkbox, and verify that the Allow option is selected.
- POST
-
Mark the checkbox, and verify that the Allow option is selected.
-
Click Finish.
-
In the New Policy page, in the Subjects section, click New.
-
In the “Step 1 of 2: Select Subject Type” page, be sure that Access Manager Identity Subject is selected, and then click Next.
-
In the “Step 2 of 2: New Subject — Access Manager Identity Subject” page, provide the following information:
- Name:
-
LoadBalancer-5_Roles
- Filter:
-
In the drop-down list, select Role. Then click Search. The search returns a list of available roles.
-
In the Available: list, select manager and employee, and then click Add.
The roles manager and employee are now contained in the Selected List.
-
Click Finish.
-
On the Policy page, click Create.
The policy you just created is now included in the list of Policies.
-
-
Log out of the Access Manager console and close the browser.
 To Verify that the Web Policy Agents Load
Balancer is Working Properly
To Verify that the Web Policy Agents Load
Balancer is Working Properly
-
Restart Web Server 1 on Protected Resource 1.
#cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com # ./stop; ./start
-
Restart Web Server 2 on Protected Resource 2.
#cd /opt/SUNWwbsvr/https-ProtectedResource-2.example.com # ./stop; ./start
-
In a browser, go to the following URL:
http://loadbalancer-5.example.com:90/index.html
The load balancer redirects the request to the Access Manager login page.
-
Log in to the Access Manager console using the following information:
- Username
-
testuser1
- Password
-
password
If the default Web Server index.html page is displayed, then the load balancer is configured properly.
-
Verify that Load Balancer 5 monitors are monitoring the Web Servers properly.
-
Log in as a root user to Protected Resource 1.
-
Run the tail command.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com/logs # tail -f access
If you see frequent entries similar to this one:
xxx.xx.69.18 - - [06/Oct/2006:13:53:07 -0700] "GET /launch.html" 200 8526
then the custom monitor is configured properly. If you do not see "GET /launch.html", then you must troubleshoot the load balancer configuration.
-
Log in as root to Protected Resource 2.
-
Run the tail command.
# cd /opt/SUNWwbsvr/https-ProtectedResource-1.example.com/logs # tail -f access
If you see frequent entries similar to this one:
xxx.xx.69.18 - - [06/Oct/2006:13:53:07 -0700] "GET /launch.html" 200 8526
then the custom monitor is configured properly. If you do not see "GET /launch.html", then you must troubleshoot the load balancer configuration.
-
- © 2010, Oracle Corporation and/or its affiliates
