Chapter 6 Installing and Configuring a Gateway With Portal Server
Configuring a gateway to access Portal Server allows you to access Portals using a secure protocol, https. If you have Portal Server installed in an Intranet, you can access Portals from another network through Gateway using Internet. Gateway handles the user requests through the secure protocol.
This chapter includes the following sections:
-
Configuring Personal Digital Certificate (PDC) Authentication
-
Installing Load Balancer Plugin and Gateway for Portal Server
-
Installing and Creating Instances of Netlet and Rewriter Proxies
Configuring Gateway During Installation
This section contains the following procedures:
Figure 6–1 Portal Server with Gateway
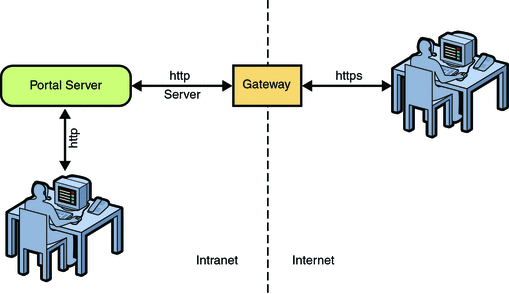
Configuring a Portal Server and a Gateway on a Single Node
This section describes how to configure a Portal Server and a Gateway on a single node in the Configure Now and Configure Later modes.
Using the Configure Now mode, you can configure a Gateway while installing Portal Server, where the Gateway is configured with other components. You can also configure the Gateway using the Configure Later mode, where you need to manually configure Gateway using the psconfig command after installing Portal Server.
 To Configure Portal Server on a Single Node using
the Configure Now Mode
To Configure Portal Server on a Single Node using
the Configure Now Mode
-
Select the Gateway option displayed with Sun Java System Portal Server Secure Remote Access 7.1 when you install Sun Java System Portal Server 7.1.
-
Enter Directory Server, Access Manager, and web container information in the Java ES installer screens.
-
Start Directory Server and web container instance after a successful installation of Portal Server.
-
Start the gateway.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin-user-name -f password-file on
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin-user-name -f password-file --gateway-profile gateway_profile --enable
PortalServer_base/SUNWportal/bin/psadmin start-sra-instance -u admin-user-name -f password-file -N default -t gateway
 To Configure Portal Server on a Single Node using
the Configure Later Mode
To Configure Portal Server on a Single Node using
the Configure Later Mode
-
Select Sun Java System Portal Server 7.1, Directory Server, and web container in the Java ES installer.
-
Select the Gateway option displayed with Sun Java System Portal Server Secure Remote Access 7.1.
-
Install the components using the Java ES installer in the Configure Later mode.
-
Ensure that Directory Server, web container instance, and web container administrator server are running.
-
Modify the example7.xml file.
The example7.xml file is located in the PortalServer_base/SUNWportal/samples/psconfig directory.
-
Configure common agent container.
PortalServer_base/SUNWportal/bin/psconfig --config example7.xml
-
Start the Gateway.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin-user-name -f password-file on
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin-user-name -f password-file --gateway-profile gateway_profile --enable
PortalServer_base/SUNWportal/bin/psadmin start-sra-instance -u admin-user-name -f password-file -N default -t gateway
Configuring Portal Server and Gateway on Separate Nodes
This section describes how to configure Portal Server and Gateway on separate nodes in the Configure Now and Configure Later modes.
Using the Configure Now mode, you can configure a Gateway while installing the Portal Server, where the Gateway is configured with other components. You can also configure the Gateway using the Configure Later mode, where you need to manually configure Gateway using the psconfig command after installing Portal Server.
Ensure that the following ports are opened whenever you configure a Gateway or perform any administrator console or command line operations that involve Gateway.
-
11162 : JMX Port (TCP)
-
11161 : SNMP Adapter Port (UDP)
-
11163 : Commandstream Adapter Port (TCP)
-
11164: RMI Connector Port (TCP)
 To Configure Portal Server and Gateway on Separate
Nodes in the Configure Now Mode
To Configure Portal Server and Gateway on Separate
Nodes in the Configure Now Mode
This procedure requires two nodes: Node 1 and Node 2.
-
Install Portal Server and Directory Server in the Configure Now mode on Node 1.
Note –Select Enable SRA for Portal while installing the Portal Server.
-
(Optional) Set SRA status to Enabled on Node 1, if the Enable SRA for Portal is not selected while installing.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin_user -f password_file on
-
Start the Java ES installer and install Access Manager SDK and Gateway on Node 2 in the Configure Now mode.
Note –Use the same password encryption key on both the nodes.
-
Enable Gateway profile on Node 1.
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin_user -f password_file --gateway-profile gateway_profile --enable
-
Start the SRA instance on Node 2.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin-user-name -f password-file on
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin-user-name -f password-file --gateway-profile gateway_profile --enable
PortalServer_base/SUNWportal/bin/psadmin start-sra-instance -u admin-user-name -f password-file -N default -t gateway
 To Configure Portal Server and Gateway on Separate
Nodes in the Configure Later Mode
To Configure Portal Server and Gateway on Separate
Nodes in the Configure Later Mode
-
Install Portal Server and Directory Server on Node 1 in the Configure Now mode.
-
Install AMSDK on Node 2 in the Configure Now mode using the Java ES installer.
Note –Use the same password encryption key on both the nodes.
-
Install Gateway on Node 2 in the Configure Later mode using the Java ES installer.
-
Enable Gateway profile on Node 1.
PortalServer_base/SUNWportal/bin provision-sra -u admin_user -f password_file --gateway-profile gateway_profile --enable
-
Modify the example10.xml file.
The example10.xml file is located in the PortalServer_base/SUNWportal/samples/psconfig directory.
-
Configure common agent container.
PortalServer_base/SUNWportal/bin/psconfig --config example10.xml
-
Start the Gateway.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin-user-name -f password-file on
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin-user-name -f password-file --gateway-profile gateway_profile --enable
PortalServer_base/SUNWportal/bin/psadmin start-sra-instance -u admin-user-name -f password-file -N default -t gateway
 To Install Gateway on a Non-Default Instance of Application
Server
To Install Gateway on a Non-Default Instance of Application
Server
-
Install Directory Server and Application Server.
-
Start Directory Server and Application Server.
-
Create a node agent.
asadmin create-node-agent --user admin --password password --savemasterpassword=true node1
-
Start the node agent.
./asadmin start-node-agent --user admin --password password node1
-
Create non default server instance.
./asadmin create-instance --user admin --password password --nodeagent node1 server1
-
Start the instance.
./asadmin start-instance --user admin --password password server1
-
Install Access Manager in the Configure Later mode.
-
Edit the amsamplesilent file.
-
Restart Directory Server, Application Server, and Access Manager.
-
Check if Access manager is up and running.
-
Invoke installer and install Portal Server in the Configure Later mode.
-
Edit the example14.xml file and configure common agent container.
./psconfig --config example14.xml
Installing the Gateway with Portal Server in the SSL Mode
Installing the Gateway with Portal Server in SSL mode allows the user, in the same Intranet where Portal Server is installed, to access Portals through a secure protocol.
Figure 6–2 Portal Server in the SSL mode
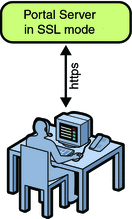
 To Install Gateway with Portal Server in SSL
To Install Gateway with Portal Server in SSL
-
Import the root Certificate Authority (CA) to the certificate database.
cd /usr/jdk/entsys-j2se/jre/lib/security /usr/jdk/entsys-j2se/jre/bin/keytool -keystore cacerts -keyalg RSA -import -trustcacerts -alias alias-name -storepass store-password -file file-name-path
-
Start the Java ES installer and install the Gateway and Access Manager SDK.
-
Create a certificate signing request.
-
Get this certificate signed by the Certificate Authority.
The Certificate Authority will be the Portal Server Administrator.
-
Create a file on the Gateway node, and paste the certificate response.
-
Add the signed certificate to the certificate database of Gateway.
-
Add the Root Certificate Authority to the certificate database.
-
Restart the Gateway.
PortalServer_base/SUNWportal/bin/psadmin switch-sra-status -u admin-user-name -f password-file on
PortalServer_base/SUNWportal/bin/psadmin provision-sra -u admin-user-name -f password-file --gateway-profile gateway_profile --enable
PortalServer_base/SUNWportal/bin/psadmin start-sra-instance -u admin-user-name -f password-file -N default -t gateway
Creating a Gateway Instance
You can also create an instance of Gateway. This allows the user to contact any one of the Gateway instances and access Portals.
 To Create a Gateway Instance
To Create a Gateway Instance
-
Log in to Portal Server administrator console.
-
Click the Secure Remote Access tab.
-
Click New Profile.
-
Type the new profile name and select the Copy Profile Data From option. Click OK.
The following message is displayed: “New profile is successfully created. Please change the relevant ports in the new profile so that they do not clash with those in the existing profiles.”
-
Click OK.
The Profile screen is displayed.
-
Click the new profile created and change the port of the instance so that it does not clash with any ports that are in use.
You need to change both the http and https port numbers.
-
Click OK.
Configuring Personal Digital Certificate (PDC) Authentication
This section describes how to configure a digital certificate for a Gateway.
 To Configure Personal Digital Certificate Authentication
To Configure Personal Digital Certificate Authentication
Before You Begin
-
Ensure that the Gateway and Portal Server are up and running.
-
Edit the AMConfig.properties file on the Portal Server node.
The AMConfig.properties file is located in the AccessManager_base/SUNWam/config directory.
-
Import the certificates to the certificate database of the Gateway.
-
Import the Root Certificate Authority on the Gateway machine.
-
Add the Root Certificate Authority to the Gateway profile.
-
Run the following command:
PortalServer_base/SUNWportal/bin/certadmin -n gateway-profile-name
-
Select Option 3 in the command-line interface.
You are prompted to provide the certificate path. When you provide a valid path, the certificate is added. You will get a message that the certificate is added successfully.
-
-
Generate a Certificate Signing Request for submitting to the Certificate Authority.
-
Submit the Certificate Signing Request to a Certificate Authority and get it approved.
-
Save the certificate response on a file after Certificate Authority has signed it.
-
Import the certificate response file.
-
Import the Root CA certificate on the Portal Server machine.
./certutil -A -n rootca -t "TCu,TCu,TCuw" -d /var/opt/SUNWappserver/domains/domain1/config -a -i rootca-path
-
Register Certificate as an Authentication module.
-
Log in to amconsole as the administrator.
-
Click the Identity Management tab.
-
Select the Organization.
-
Select Services in the View drop-down list.
-
Verify whether the Certificate is displayed in the left pane under the Authentication Modules option.
-
Click Add if the Certificate Service is not displayed in the left pane.
-
Select Certificate in the right pane.
Certificate is displayed under the Authentication Modules option.
-
Click OK.
Certificate is displayed under the Authentication Modules option in the left pane.
-
-
Allow Certificate Authentication to trust any remote host.
-
Log in to amconsole as the administrator.
-
Click the Identity Management tab.
-
Select the Organization.
-
Select Services in the View drop-down list.
-
Click the Arrow button displayed with the Certificate option.
-
Select the None option displayed in the Trusted Remote Hosts list box.
-
Click Remove.
-
Type Any in the text box displayed with the Trusted Remote Hosts list box.
-
Click Add, and click Save in the right panel.
-
-
Add Certificate as a required enforcement criterion.
-
Log in to amconsole as the administrator.
-
Click the Identity Management tab.
-
Select the Organization.
-
Select Services in the View drop-down list.
-
Click the Arrow button that is displayed with the Authentication Configuration option.
The Service Instance screen appears.
-
Click New in the Service Instance screen.
The New Service Instance List screen appears.
-
Enter the service instance name as gatewaypdc.
-
Click Submit.
The Service Instance List screen appears.
-
Click gatewaypdc option.
The gatewaypdc Show Properties screen appears.
-
Click the Edit link.
-
Click Add.
The Add Authentication Modules pop-up window appears.
-
Select Cert as the Module Name.
-
Select Required for Enforcement Criteria.
-
Click OK.
The Authentication Modules pop-up window appears.
-
Click OK and close the pop-up window.
-
-
Add a dynamic user.
-
Add Gateway host in the Portal Server administration console.
-
Restart the server.
Note –This is mandatory because the Amconfig.Properties is updated.
-
Restart the Gateway profile.
-
Install the client certificate issued by the Certificate Authority into the browser.
Access the PDC enabled Gateway.
-
Install the client certificate to the JVM keystore.
-
Add portal services to the dynamic user created.
-
Add a dynamic user to the Distinguished Name (DN).
Installing Load Balancer Plugin and Gateway for Portal Server
This section explains how to install Load Balancer Plugin and Gateway for Portal Server. A Load Balancer handles multiple Portal Server instances. If any one of the Portal Server instances goes down, the Load Balancer automatically redirects the user to the other available Portal Server instance.
A Load Balancer can be installed behind the Gateway or in front of the Gateway. If the Load Balancer is installed behind the Gateway, the user accesses the Portal Server instances through the Gateway. The end user contacts the Gateway. If the Load Balancer is installed in front of the Gateway, the user accesses the Portal Server instances through the Load Balancer.
Figure 6–3 Portal Server with Load Balancer
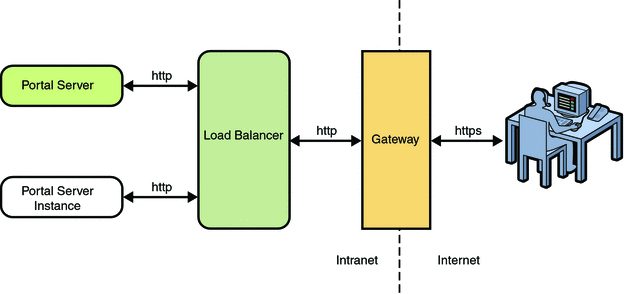
This section explains the following:
 To Install Load Balancer Plugin for Portal Server
To Install Load Balancer Plugin for Portal Server
This task requires the following:
-
Two nodes: Node 1 and Node 2.
-
Two Portal Server instances on Node 1 and Node 2.
-
Install the Load Balancer plugin that is available with the Application Server using the Java ES installer.
Note –Select Web Server as a component to install with the Load balancer plugin.
-
Edit the Loadbalancer.xml file.
The Loadbalancer.xml file is located in the WebServer_base/SUNWwbsvr/https-node3/config/Loadbalancer.xml directory.
A sample Loadbalancer.xml file is displayed as follows:
<!DOCTYPE Load Balancer PUBLIC "-//Sun Microsystems Inc. //DTDSun ONE Application Server 7.1//EN" "sun-Load Balancer_1_1.dtd"> <Load Balancer> <cluster name="cluster1"> <!-- Configure the listeners as space seperated URLs like listeners="http://host:port https://host:port" For example: <instance name="instance1" enabled="true" disable-timeout-in-minutes="60" listeners="http://node1.domain-name:80"/> <instance name="instance1" enabled="true" disable-timeout-in-minutes="60" listeners="http://node2.domain-name:80"/> --> <instance name="instance1" enabled="true" disable-timeout-in-minutes="60" listeners=""/> <web-module context-root="/portal" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/psconsole" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <health-checker url="/" interval-in-seconds="10" timeout-in-seconds="30" /> </cluster> <property name="reload-poll-interval-in-seconds" value="60"/> <property name="response-timeout-in-seconds" value="30"/> <property name="https-routing" value="true"/> <property name="require-monitor-data" value="false"/> <property name="active-healthcheck-enabled" value="false"/> <property name="number-healthcheck-retries" value="3"/> <property name="rewrite-location" value="true"/> </Load Balancer>
-
Restart the Web Server and access Portal through the Load Balancer.
 To Install Gateway in Front of the Load Balancer
To Install Gateway in Front of the Load Balancer
This procedure requires three nodes: Node 1, Node 2, and Node 3.
In this procedure, you do the following:
-
Installs Portal Server, Secure Remote Access, Directory Server, Access Manager, and Application Server on Node 1.
-
Installs Load Balancer on Node 2.
-
Installs Gateway on Node 3.
-
Install Portal Server with Secure Remote Access, Directory Server, Access Manager, and Application Server on Node 1.
-
Install Load Balancer on Node 2.
Load Balancer plugin is available with Application Server 8.2.
Note –Select Web Server as a component to install with Load Balancer.
-
Log in to Access Manager administration console on Node 1.
http://node1:8080/amconsole
-
Select Services in the in the View drop-down list.
-
Click Administration.
-
Add Load Balancer Fully Qualified Domain Name in the organization aliases.
http://node2.domain-name:8080
-
Add the Load Balancer URL in the platform service.
http://node1.domain-name:8080|01
-
Click Core.
-
Change Default Success Login URL to http://node1.domain-name:8080/portal/dt from http://node2.domain-name:8080/portal/dt.
-
-
Edit the AMConfig.properties file.
The AMConfig.properties file is located in the AccessManager_base/SUNWam/Config directory.
-
Restart Portal Server and Application Server on Node 1.
-
Log in to Access Manager administrator console and Portal through the Load Balancer.
http:node2.dommain-name:8080/amconsole
http:node2.dommain-name:8080/portal/dt
-
Install Gateway on Node 3.
-
Provide appropriate Portal Server, Access Manager, and Directory Server values in the Installation panels.
Note –Do not provide any values of the Load Balancer.
The Gateway is installed successfully.
Gateway can be installed in the Configure Later mode also. Change the example10.xml file. Set the PortalAccessURL as the Load Balancer URL. Set the PrimaryPortalHost as the portal where the first portal is installed. This is used to set up trust between two common agent containers. After modifying the example10.xml file, run the psconfig command to configure Portal Server.
-
Configure the Gateway to direct to the Load Balancer instead of Portal Server on Node 3.
-
Set ignoreServerList=true in the platform.conf.default file.
The platform.conf.default file is located in the PortalServer_base/SUNWportal directory.
-
Replace Portal host and port information with Load Balancer host and port in the platform.conf.default file.
The platform.conf.default file is located in the PortalServer_base/SUNWportal directory.
-
Replace Portal host and port information with Load Balancer host and port in the AMConfig-default.properties file on Node 3.
The AMConfig-default.properties file is located in the AccessManager_base/SUNWam directory.
-
Log in to Portal Server administrator console.
http://node1.domain-name:8080/psconsole
-
Click Secure Remote Access > gw448.
-
Enter the Load Balancer URL in the Portal Server(s) list displayed in the right panel.
http://node2.domain-name:8080
-
Add the Load Balancer URL in the URLs to which User Session Cookie is Forwarded list.
-
Click the Security tab.
-
Add the Load Balancer URL for Access Manager console and Access Manger server in the Non-authenticated URLs list.
http://node2.domain-name:8080/amconsole
http://node2.domain-name:8080/amserver
-
Configure the enableSRAforPortal.xml file.
PortalServer_base/SUNWportal/bin/psadmin provision-sra enableSRAforPortal.xml
-
-
Restart Gateway.
Installing and Creating Instances of Netlet and Rewriter Proxies
This section explains how to install Netlet Proxy and Rewriter Proxy. This section also explains how to create a second instance of Netlet and Rewriter proxies using the psadmin command.
This section includes the following:
-
To Create a Second Instance of Netlet Proxy Using the psadmin Command
-
To Create a Second Instance of Rewriter Proxy Using the psadmin Command
 To Install Netlet Proxy in the Configure Now Mode
To Install Netlet Proxy in the Configure Now Mode
-
Invoke the Java ES installer.
-
Select Netlet Proxy in the Components Selection screen and proceed with the installation.
-
Specify the Host IP Address, Access Port (default: 10555), and the Profile Name to which the Netlet Proxy instance needs to be associated in the Portal Server: Secure Remote Access: Configure Netlet Proxy panel.
-
Verify whether the Netlet Proxy instance is running.
netstat -an | grep PORT
 To Install Netlet Proxy in the Configure Later Mode
To Install Netlet Proxy in the Configure Later Mode
-
Install Netlet Proxy in the Configure Later mode using the Java ES installer.
-
Modify the example11.xml with the appropriate values.
The attributes within <NetletPoxy profile=profilename>...</NetletProxy> tags need to be changed.
-
Configure example11.xml.
PortalServer_base/SUNWportal/bin/psconfig --config example11.xml
-
Start Netlet Proxy.
 To Create a Second Instance of Netlet Proxy Using
the psadmin Command
To Create a Second Instance of Netlet Proxy Using
the psadmin Command
-
Install Netlet Proxy in the Configure Later mode using the Java ES installer.
-
Configure common agent container by modifying the example2.xml file.
-
Configure the common agent container.
PortalServer_base/SUNWportal/bin/psconfig --config example2.xml
-
Copy the NLPConfig.properties.template file to a temporary location.
cp PortalServer_base/SUNWportal/template/sra/NLPConfig.properties.template /tmp
-
Modify the values for an existing profile.
-
Create a Netlet Proxy instance.
psadmin create-sra-instance -u admin-user-name -f PASSWORDFILE -S /tmp/NLPConfig.properties.template -t nlproxy
-
Start Netlet Proxy.
 To Install Rewriter Proxy in the Configure Now mode
To Install Rewriter Proxy in the Configure Now mode
-
Invoke the Java ES installer.
-
Select Rewriter Proxy in the Components Selection screen, and proceed with the installation.
-
Specify the Host IP Address, Access Port (default: 10443), and the Profile Name to which this Rewriter Proxy instance needs to be associated in the Portal Server: Secure Remote Access: Configure Rewriter Proxy screen.
-
Check whether the Rewriter Proxy instance is running:
netstat -an | grep PORT
 To Install Rewriter Proxy in the Configure Later Mode
To Install Rewriter Proxy in the Configure Later Mode
-
Install Rewriter Proxy in the Configure Later mode using the Java ES installer.
-
Modify the example11.xml file with the appropriate values.
The attributes within the <RewriterPoxy profile=profilename>...</RewriterProxy> tags need to be changed for Rewriter proxy.
-
Configure the common agent container.
PortalServer_base/SUNWportal/bin/psconfig --config example11.xml
-
Start Rewriter Proxy.
 To Create a Second Instance of Rewriter Proxy Using
the psadmin Command
To Create a Second Instance of Rewriter Proxy Using
the psadmin Command
-
Install Rewriter Proxy in Configure Later mode using the Java ES installer.
-
Configure common agent container by modifying the example2.xml file.
PortalServer_base/SUNWportal/bin/psconfig --config example2.xml
-
Copy the RWPConfig.properties.template file to a temporary location.
cp PortalServer_base/SUNWportal/template/sra/RWPConfig.properties.template /tmp
-
Modify the values for an SRA profile.
-
Create a Rewriter Proxy.
PortalServer_base/SUNWportal/bin/psadmin create-sra-instance -u admin-user-name -f PASSWORDFILE -S /tmp/RWPConfig.properties.template -t rwproxy
-
Start Rewriter Proxy.
- © 2010, Oracle Corporation and/or its affiliates
