XACML Service
eXtensible Access Control Markup Language (XACML) is a markup language that provides an XML syntax for defining policies (who can do what, where can it be done, and when), for querying whether access to a protected resource can be allowed (requests), and for receiving responses to those queries (decisions). XACML is built around the standard access control separation of the Policy Enforcement Point (PEP) and the Policy Decision Point (PDP) as discussed in Authorization and Policy Service Overview except you use XACML formatted queries and responses. The XACML PEP is responsible for intercepting all access requests, collecting the appropriate information (such as who is making the request, which resource is being accessed, and what action is to be taken), and sending a request for a decision to the XACML PDP. The XACML PDP (OpenSSO Enterprise) evaluates configured policies against the information in the decision request. It uses a Context Handler to request the appropriate policies and attributes in order to render one of the following decisions.
-
Permit
-
Deny
-
Not Applicable (no policy created by this PDP applies to the access request)
-
Indeterminate (an error occurred that prevents the PDP from knowing the correct response)
The following sections contain more information.
XACML in OpenSSO Enterprise
OpenSSO Enterprise implements the SAML v2 Profile of XACML version 2.0 thus supporting XACMLAuthzDecisionQuery and XACMLAuthzDecisionStatement. In a OpenSSO Enterprise XACML interaction, after receiving a request for access, the XACML PEP makes a XACMLAuthzDecisionQuery request and receives a XACMLAuthzDecisionStatement response that contains the decision. (The policies themselves are not returned.) The XACML components on the client side include Client SDK interfaces for passing XACML requests and receiving XACML responses as well as an interface to construct the communications.
Note –
The framework relies internally on the Client SDK SAML v2 interfaces for communication between the PEP and PDP, and includes an implementation of the SAML v2 request handler called the XACML2AuthzDecisionQueryHandler that plugs into the SAML v2 Service framework.
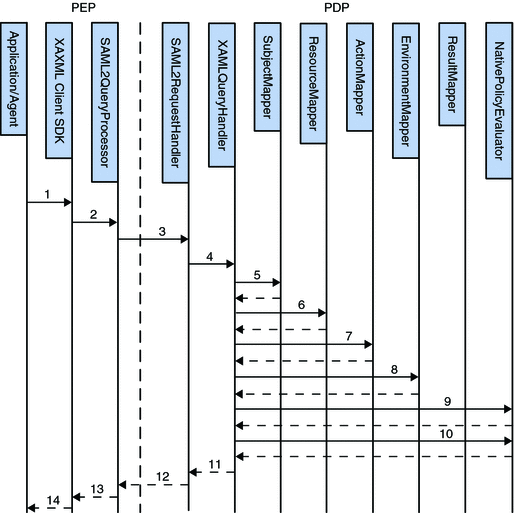
The XACML components on the OpenSSO Enterprise side include out-of-the-box implementations of XACML mappers for subjects, resources, actions and environment. These implementations use the Policy Service to compute authorization decisions. Figure 8–1illustrates how XACML and OpenSSO Enterprise interact with each other. The communications are explained in the procedure following the image.
Figure 8–1 XACML Process Flow
-
The policy agent protecting a resource constructs a XACML access request using the Client SDK.
-
The Client SDK wraps the request in a XACMLAuthzDecisionQuery element and sends it to the SAML v2 query processor on the local machine (also part of the Client SDK).
-
The SAML v2 query processor consults the metadata for the PEP and the PDP, sets additional elements or attributes in the query, signs it (if necessary) and sends a SOAP request containing the query to the PDP.
-
The SAML v2 request handler on the PDP side receives the request, consults the metadata for the PEP and the PDP, verifies the trust relationships, enforces any signing or encryption requirements, verifies the signature and forwards the query to the XACMLAuthzDecisionQueryHandler.
-
The XACMLAuthzDecisionQueryHandler consults the appropriate metadata using the entityID values of the PEP and PDP (included in the request) to find the correct mapper implementations to use.
-
XACMLAuthzDecisionQueryHandler uses the Resource mapper to map the given Resource to a resource and service configured with OpenSSO Enterprise.
-
XACMLAuthzDecisionQueryHandler uses the Action mapper to map the given Action to an action name configured with OpenSSO Enterprise.
-
XACMLAuthzDecisionQueryHandler uses the Environment mapper to map the given Environment to conditions configured with OpenSSO Enterprise.
-
XACMLAuthzDecisionQueryHandler uses the OpenSSO Enterprise policy evaluator to get the policy decision.
-
XACMLAuthzDecisionQueryHandler uses the Result mapper to map the decision to an XACML Result element.
Note –OpenSSO Enterprise is not an XACML policy engine. It has no support for XACML policies themselves and thus no support for retrieving the policies, only the decision.
-
XACMLAuthzDecisionQueryHandler wraps the XACML Result in an XACML Response, the XACML Response in an XACMLAuthzDecisionStatement, the XACMLAuthzDecisionStatement in a SAML Assertion, the Assertion in a SAML Response, and hands over the SAML Response to the SAML v2 request handler.
-
The SAML v2 request handler sets additional attributes and elements (based on the SAML v2 protocol), signs it as required and returns it in a SOAP message to the PEP side.
-
The SAML v2 query processor verifies the trust relationships, the signing requirements, and the signature as necessary. It then extracts the SAML Response from the SOAP message and returns it to the XACML portion of the Client SDK.
-
The Client SDK extracts the XACML Response from the SAML v2 Response and returns it (and the decision) to the client application.
XACML Programming Interfaces
OpenSSO Enterprise provides Java API for using, and interacting with, the XACML Service. For information, see Chapter 14, Using the Client SDK, in Sun OpenSSO Enterprise 8.0 Developer’s Guide, Chapter 2, Using the Policy Service API, in Sun OpenSSO Enterprise 8.0 Developer’s Guide, and the Sun OpenSSO Enterprise 8.0 Java API Reference.
- © 2010, Oracle Corporation and/or its affiliates
