Understanding Typical Business Use Cases
The following use cases focus on single sign-on enablement and do not describe authorization options:
Simple Single Sign-On
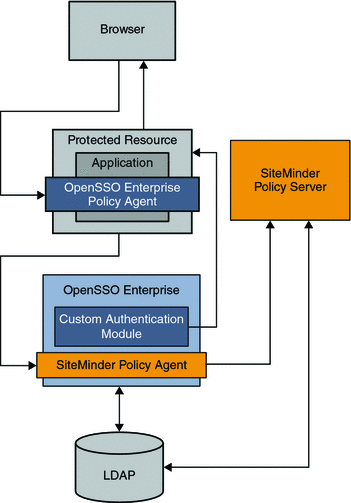
In a simple single sign-on example, the SiteMinder instance is already deployed and configured to protect some of the enterprise applications in a company intranet. In the architecture figure below, the legacy application is contained in the Protected Resource . The company wants to continue leveraging the legacy SiteMinder deployment as the authentication authority. The company also wants to add OpenSSO Enterprise to the environment to leverage its advanced features such as identity federation, XACML policies, web services, and so on. An OpenSSO Enterprise policy agent protects the Protected Resource, while OpenSSO Enterprise itself is protected by a SiteMinder policy agent. The following figure illustrates the deployment architecture for single sign-on using both SiteMinder and OpenSSO Enterprise.
Figure 13–1 Deployment Architecture for Simple Single Sign-On with SiteMinder
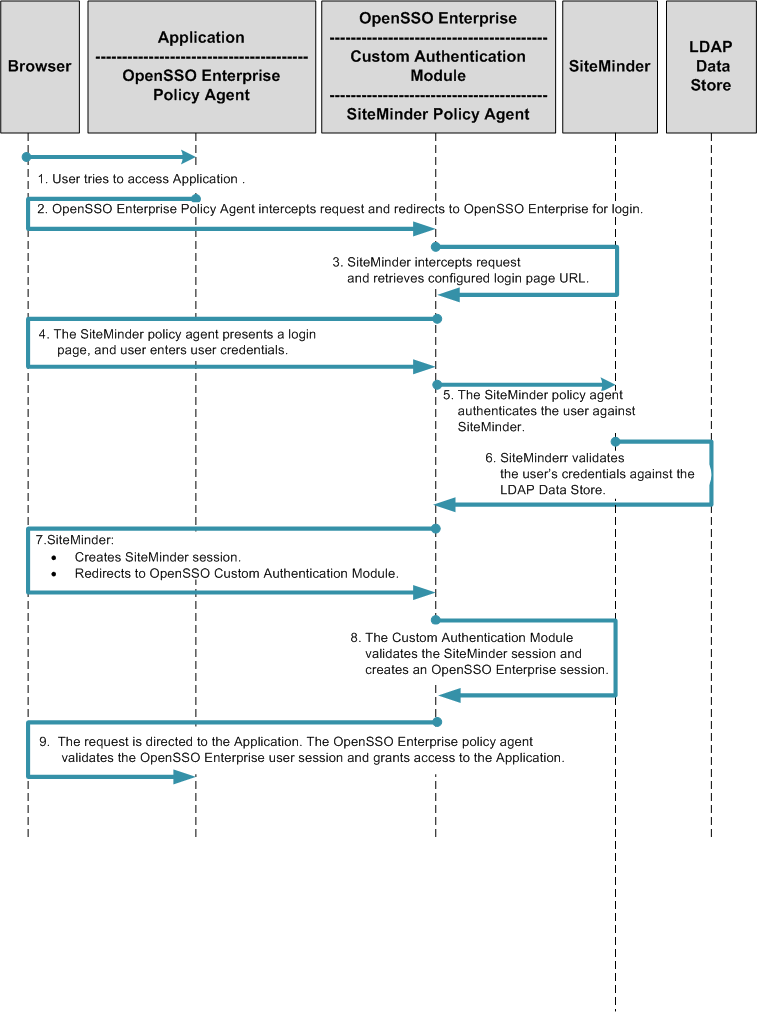
The following figure illustrates the process flow in this deployment.
Figure 13–2 Process Flow for Simple Single Sign-On with SiteMinder
Federated Single Sign-On
The SAML, ID-FF, and WS-Federation protocols provide cross-domain single sign-on among multiple trusted business entities. These protocols are also used in Identity Federation. Identity Federation involves an Identity Provider, also known as an authentication provider, and a Service Provider where the user authentication session at the Identity provider is consumed. The following are common use cases in which SiteMinder is enabled for federation protocols:
-
Enabling SiteMinder for federation protocols in a Service Provider environment
-
Enabling SiteMinder for federation protocols in an Identity Provider environment
Federated Single Sign-On in an Identity Provider Environment
This is the most common of the deployments. This is a good approach when you want to use OpenSSO Enterprise for establishing partner relations and still leverage the SiteMinder authentication framework.
For example, as a company partners with external companies, the company deploys OpenSSO in the Service Provider environment to leverage the SAMLv2 Federation protocols. The following figure illustrates how SiteMinder can be enabled in an Identity Provider environment using OpenSSO Enterprise for federation protocols.
Figure 13–3 Deployment Architecture for Federated Single Sign-On in an Identity Provider Environment
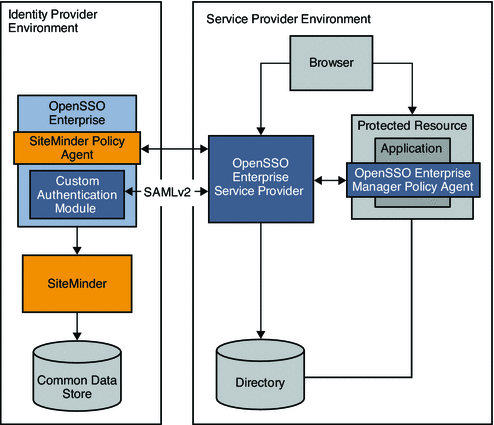
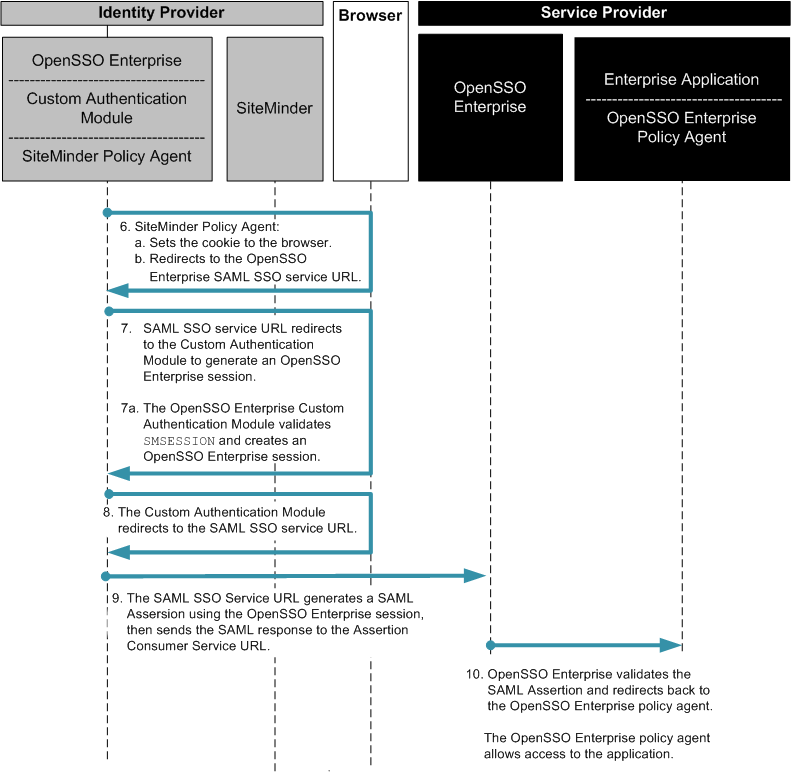
In this example, OpenSSO Enterprise provides federated single sign-on among enterprise applications in partner environments, while SiteMinder continues to provide authentication. The following two figures illustrates a typical transaction flow.
Figure 13–4 Process Flow for Federated Single Sign-On in an Identity Provider Environment
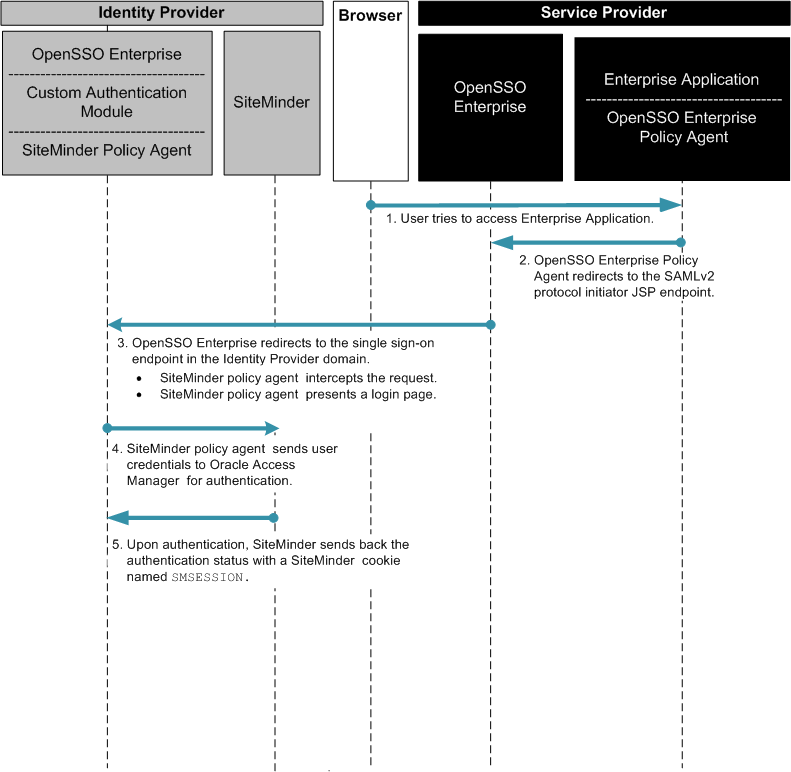
Figure 13–5 Process Flow for Federated Single Sign-On in an Identity Provider Environment (Continued)
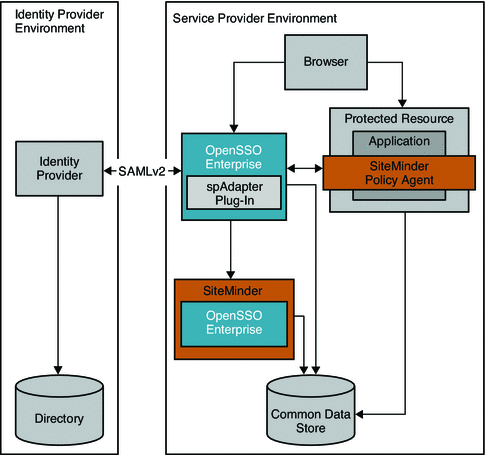
Federated Single Sign-On Use Case in the Service Provider Environment
In this example, the company uses SiteMinder in the Service Provider environment to protect legacy applications. OpenSSO Enterprise is installed solely to invoke Federation protocols. This deployment quickly enables partners (Service Providers) to establish federation environments with their trusted Identity Providers where the authenticates must be delegated.
Figure 13–6 Deployment Architecture for Federated Single Sign-On In the Service Provider Environment
The following two figures illustrate the steps in the single sign-on flow:
Figure 13–7 Process Flow for SiteMinder Federation in the Service Provider Environment
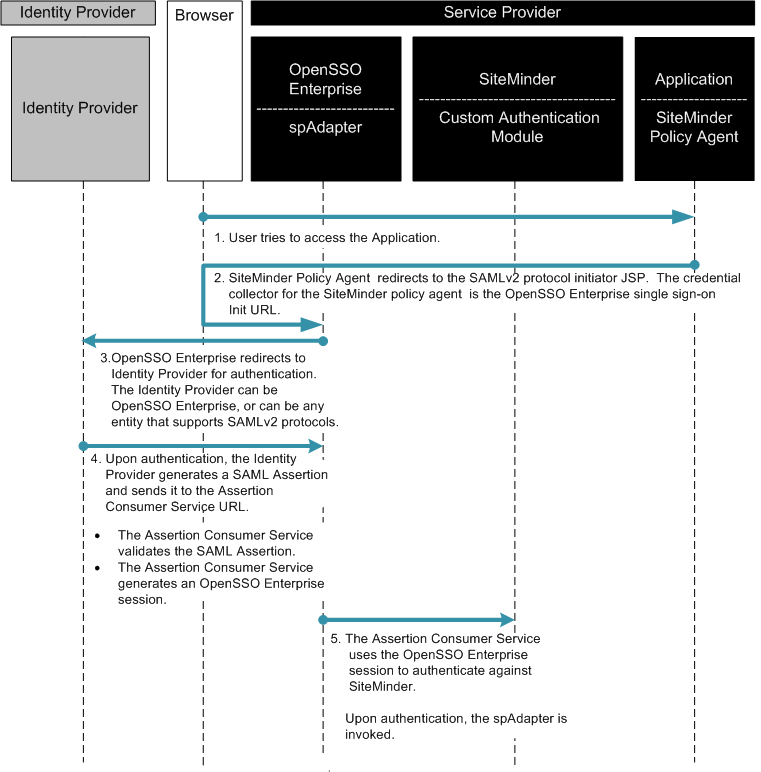
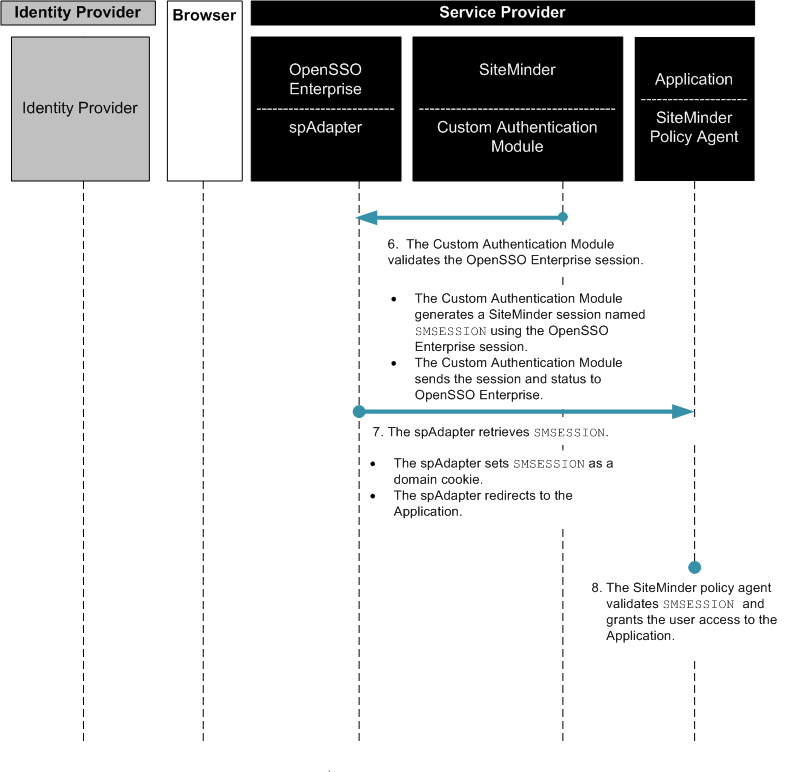
Figure 13–8 Process Flow for SiteMinder Federation in the Service Provider Environment (continued)
- © 2010, Oracle Corporation and/or its affiliates
