Analyzing the Deployments
The Identity Web Services Framework can be used in either browser-based mode or desktop mode. The browser-based client uses SAMLv2 or ID-FF protocols to find the Liberty Discovery Service Resource Offering of an authenticated user, or bootstrap, into the ID-WSF framework. The desktop clients can leverage the Liberty Authentication Service to bootstrap into the ID-WSF. OpenSSO Enterprise supports ID-WSF boot strapping through the SAMLv2, ID-FF, or ID-WSF -based authentication service, depending upon the client needs. This chapter describes deployments for both browser-based clients and desktop clients
Browser-based ID-WSF Deployment
The following diagram represents the deployment architecture for ID-WSF using OpenSSO Enterprise for browsed-based clients.
Figure 10–3 Deployment Architecture for Browser-based Identity Web Services
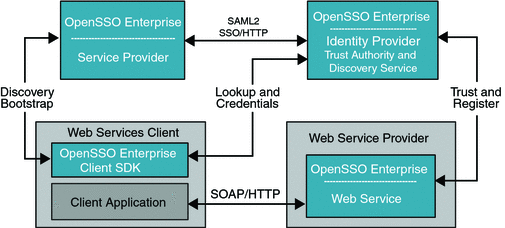
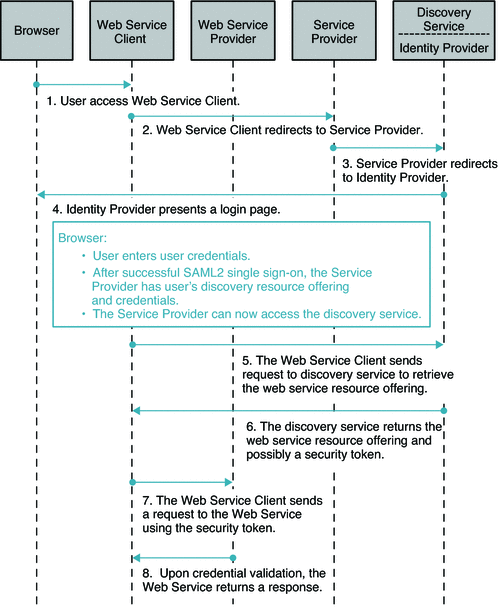
Both Service Provider and Identity Provider are used for authenticating the user's identity using SAMLv2 protocols. OpenSSO Enterprise can be an Identity Provider or a Service Provider or a hosting web service in this deployment. The Service Provider and Web Services Client are in the same domain in this deployment. The Web Service Provider registers its service resource offering with the Discovery Service before it offers services to various clients. The registration can be done through either the Discovery Service protocol or out of band. The OpenSSO Enterprise can be deployed in various roles for this deployment as illustrated in the deployment architecture diagram. The following figures shows the process flow among various entities in the browser-based identity web services deployment.
Figure 10–4 Process Flow for Browser-based Identity Web Services
Desktop ID-WSF Deployment
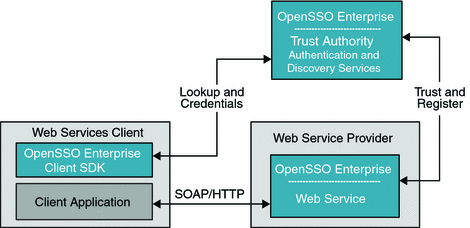
The desktop mode ID-WSF deployment supports desktop mode clients, so they do not require an application container. Desktop ID-WSF is useful for standalone Web Service Clients. The custom Web Service Clients can leverage the OpenSSO Enterprise Client SDK to enable a secure connection for a given payload. The Web Services Client bundles the OpenSSO Enterprise Client SDK that accesses the local OpenSSO Enterprise instance to secure web service requests.
Figure 10–5 Desktop ID-WSF Deployment
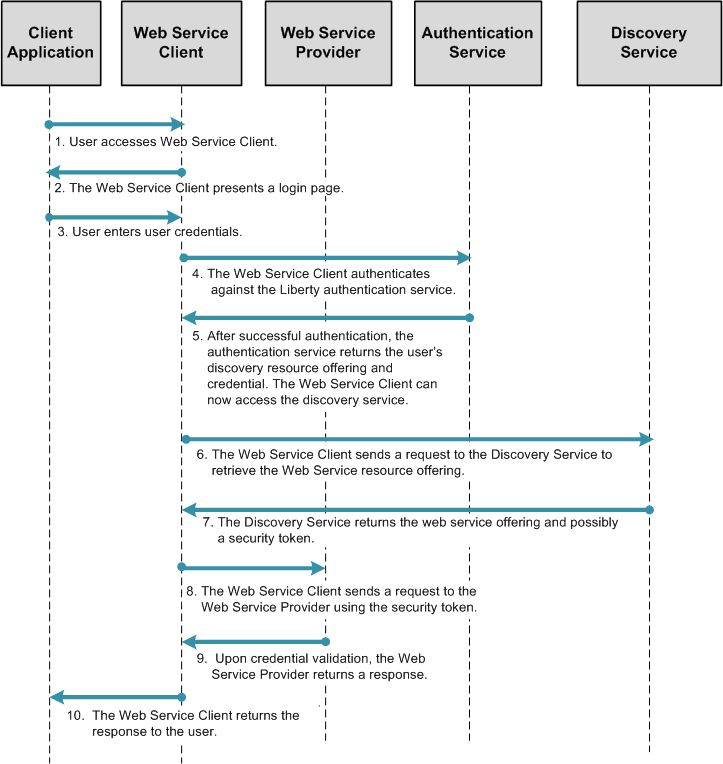
The Web Services package is contained in the OpenSSO Enterprise WAR file and must be deployed along with the OpenSSO Enterprise server to leverage the ID-WSF security framework. The configuration and user data is not required to be same data store as that of OpenSSO Enterprise. The trust authority for ID-WSF is the Discovery Service. The Discovery Service end point is exposed the same way as any data web service, and can fully leverage OpenSSO Enterprise infrastructure components such as authentication, policies, and so forth to serve web service clients and as well as web services. OpenSSO Enterprise is independent in all these roles and can be deployed appropriately based on the customer or application requirements. The following figure illustrates the process flow for desktop ID-WSF.
Figure 10–6 Process Flow for Desktop Identity Web Services
- © 2010, Oracle Corporation and/or its affiliates
