Chapter 4 Logical Design with Access Manager
During the logical design phase of the solution life cycle, you design a logical architecture showing the interrelationships of the logical components of the solution. The logical architecture and the usage analysis from the technical requirements phase form a deployment scenario, which is the input to the deployment design phase. This chapter contains the following sections about logical design for Sun JavaTM System Access Manager:
About Logical Architectures
A logical architecture identifies the software components needed to implement a solution, showing the interrelationships among the components. The logical architecture and the quality of service requirements determined during the technical requirements phase form a deployment scenario. The deployment scenario is the basis for designing the deployment architecture, which occurs in the next phase, deployment design.
Designing a Logical Architecture
When you design a logical architecture, use the use cases identified during the technical requirements phase to determine the Java Enterprise System (Java ES) components that provide the services necessary for the solution. You must also identify any components providing services to the components you initially identify.
You place the Java ES components within the context of a multi-tiered architecture according to the type of services that they provide. Understanding the components as part of a multi-tiered architecture helps you later determine how to distribute the services provided by the components and also helps determine a strategy for implementing quality of service (such as scalability, availability, and others.)
For more detailed information about logical architectures and the solution life cycle, see the Sun Java Enterprise System 2005Q4 Deployment Planning Guide.
Access Manager Components
An Access Manager deployment includes the following products and components:
Web Container
Access Manager must run in one of the following web containers:
-
Sun Java System Web Server
-
Sun Java System Application Server
-
BEA WebLogic Server
-
IBM WebSphere Application Server
For the specific versions of each web container that are supported, see the Sun Java System Access Manager 7 2005Q4 Release Notes.
Directory Server
Access Manager requires an LDAP directory server for these entities:
Access Manager Information Tree
Access Manager 7 2005Q4 requires Sun Java System Directory Server to store the Access Manager information tree. Access Manager creates and maintains the Access Manager information tree, which includes the following information pertinent to system access:
-
How users authenticate
-
Which resources users can access
-
What information is available to applications after users are given access to resources
Identity Repository
Access Manager requires an identity repository to store user data such as users and groups. Previous versions of Access Manager required Sun Java System Directory Server as the identity repository. However, in addition to Sun Java System Directory Server, Access Manager 7 2005Q4 also supports an LDAP version 3 (LDAP v3) compliant directory server.
Message Queue and Berkeley DB for Session Failover
If you are planning to implement session failover, Access Manager requires these additional components:
-
Sun Java System Message Queue. The Message Queue broker cluster manages the session messages between Access Manager instances and the session store database.
-
Berkeley DB by Sleepycat Software, Inc. (http://www.sleepycat.com/) is the default session store database.
Java ES Components That Use Access Manager
Access Manager is usually deployed with other Java ES component products, including:
-
Sun Java System Portal Server, Sun Java System Messaging Server, Sun Java System Calendar Server, Sun Java System Instant Messaging, and Sun Java System Communications Express: To provide single sign-on (SSO)
-
Sun Java System Web Server: To provide optional access control.
Example Access Manager Logical Architectures
This section provides the following scenarios as examples of logical architectures for Access Manager solutions, including:
Access Manager Web Deployment
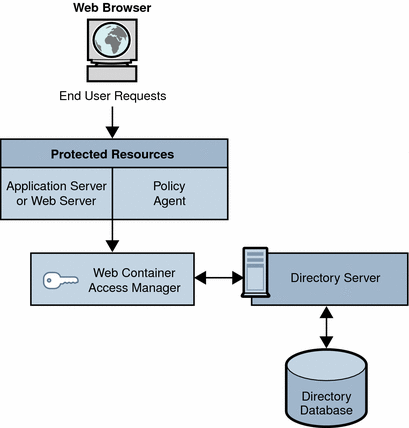
A common Access Manager deployment has a web browser accessing an application or resource deployed on a web server. The application or resource is protected by Access Manager and communicates with it using a policy agent also installed on the web server. The web server might also have the Access Manager SDK deployed. This scenario does not restrict the number of web servers on a machine or the instances of Access Manager deployed on multiple machines. For example, a machine might have multiple web servers, each deploying an instance of Access Manager. Similarly, multiple web servers might also be running on different machines, each deploying an instance of Access Manager.
The following figure shows an Access Manager web deployment scenario.
Figure 4–1 Access Manager Web Deployment
Access Manager Multiple Server Deployment
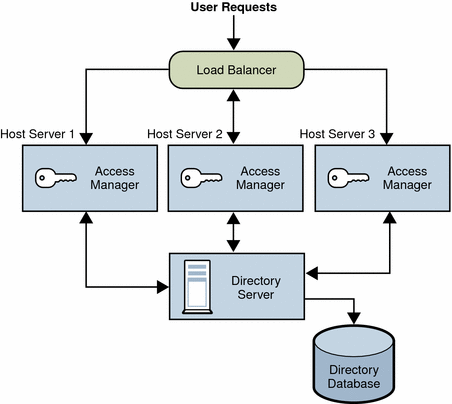
An Access Manager multiple server deployment has two or more host servers, with one or more instances of Access manager installed on each host server. Each Access Manager instance accesses the same Directory Server. You can configure the Directory Server instances in a multiple master replication (MMR) configuration, if required for your deployment.
The Access Manager instance installed on the first host server points to an instance of Directory Server. During installation using the Java ES installer, you can choose an existing Directory Server with or without an existing directory information tree (DIT), depending on your deployment.
You install subsequent instances of Access Manager on other host servers by running the Java ES installer, with the Access Manager instance pointing to a Directory Server with an existing DIT. Access Manager then does not write any information to Directory Server because it recognizes the Directory Server as already existing.
The following figure shows multiple Access Manager instances on different host servers with one Directory Server.
Figure 4–2 Multiple Access Manager Instances With One Directory Server
For more information, see Installing Access Manager on Multiple Host Servers.
Java Application Deployment
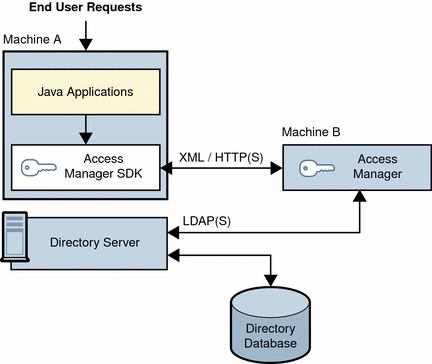
Another common scenario for Access Manager allows Java applications to access an Access Manager SDK installed directly on the server where they are deployed. This scenario requires an additional server with an instance of a web container (such as Sun Java System Web Server or Sun Java System Application Server) running at least one instance of Access Manager. This server also maintains the information to provide single sign-on (SSO). The following figure shows a Java application deployment scenario.
Figure 4–3 Java Application Deployment
Access Manager Session Failover Deployment
Access Manager provides a web container independent session failover implementation using Sun Java System Message Queue (Message Queue) as the communications broker and the Berkeley DB by Sleepycat Software, Inc. as the session store database. Access Manager session failover retains a user’s authenticated session state in the event of a single hardware or software failure, which allows the user’s session to fail over to a secondary Access Manager instance without losing any session information or requiring the user to login again.
Overview of Access Manager Session Failover
Access Manager 7 2005Q4 session failover includes these components:
-
Two or more instances of Access Manager 7 2005Q4, with each instance running on a supported web container on two or more host servers.
-
Message Queue broker cluster, which manages the session messages between the Access Manager instances and the session store database.
-
Berkeley DB by Sleepycat Software, Inc. (http://www.sleepycat.com/), as the session store database. The Berkeley DB client daemon is amsessiondb.
Access Manager session failover follows the Message Queue publish/subscribe (topic destinations) delivery model:
-
When a user initiates, updates, or ends a session, Access Manager publishes a session creation, update, or deletion message to the Message Queue broker cluster.
-
The Berkeley DB client (amsessiondb) subscribes to the Message Queue broker cluster, reads the session messages, and stores the session operations in the database.
If an Access Manager instance fails due to a single hardware or software problem, a user’s session associated with that instance fails over to a secondary Access Manager instance, as follows:
-
The secondary Access Manager instance publishes a query request to the Message Queue broker cluster for the user’s session information.
-
The Berkeley DB clients (amsessiondb) subscribing to the same session request topic on the Message Queue broker cluster receive the query request retrieve the corresponding entry from the session database, and then publish the user’s session information to the Message Queue broker cluster with the session response topic.
-
The secondary Access Manager instance subscribing to the session response topic receives the response with the user’s session and continues without losing any session information or the user having to login again.
If a Message Queue broker fails, Access Manager continues to operate in non-session failover mode. When the Message Queue broker is later restarted, Access Manager returns to session failover mode.
For more information about the Message Queue components and the publish/subscribe delivery model, see the Sun Java System Message Queue Technical Overview.
Session Failover Deployment Scenario
The following figure shows a basic scenario with two host servers, each running an Access Manager instance on a web container, the Message Queue broker cluster, and the Berkeley DB client (amsessiondb). The load balancer distributes client requests to the Access Manager instances. Both Access Manager instances access the same Directory Server (not shown in the figure).
Figure 4–4 Access Manager Session Failover Basic Deployment Scenario
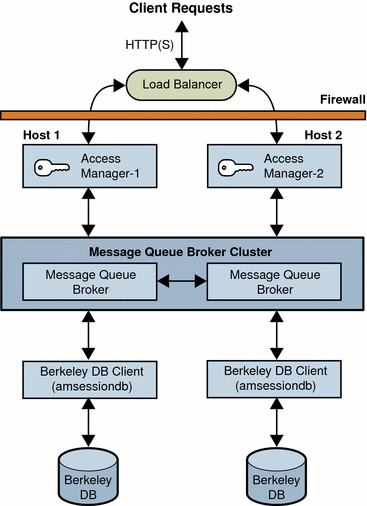
You can add additional sites similar to the one shown in the figure, with each site accessing the same Directory Server. Session failover, however, occurs only for the Access Manager instances within a site; cross-site session failover is not supported in the current release.
For more information, see Implementing Access Manager Session Failover.
Access Manager and Portal Server Deployment
For the Java Enterprise System 2005Q4 release, you can deploy Access Manager with Portal Server either on the same physical server or on multiple servers.
Installation on a Single Server
In this scenario, Access Manager and Portal Server are installed on the same physical server. You must also install or have access to an installed version of Directory Server, which can be either on the same server or a remote server.
To install these components, run the Java Enterprise System installer in a single session and make these selections:
-
On the Component Selection panel, select these products and subcomponents:
-
Under Communication & Collaboration Services, select Portal Server.
-
Under Directory & Identity Services, select Access Manager 7 2005Q4 and its subcomponents:
-
Identity Management and Policy Services Core
-
Access Manager Administration Console
-
Common Domain Services for Federation Management
-
Access Manager SDK
By default, when you select Portal Server, the installer installs only the Access Manager SDK, so you must specifically check the other subcomponents.
Install and configure one of the following web containers:
-
-
Sun Java System Application Server
-
Sun Java System Web Server
-
Installation on Multiple Servers
In this scenario, Portal Server will access Access Manager on a local server from a remote server. You must also install or have access to an installed version of Directory Server, which can be either on a local or remote server:
-
On the local server, install Access Manager and a web container. You must install and configure the components on this server before you install and configure the components on the remote server.
-
On the remote server, install Portal Server and the Access Manager SDK. You do not need to select the other Access Manager subcomponents on the remote server.
For more information about deploying Access Manager and Portal Server, see the Sun Java System Portal Server Deployment Planning Guide.
Federation Management
In 2001, Sun Microsystems joined with other companies to form the Liberty Alliance Project. This project defined standards for developing identity-based infrastructures, software, and web services.
Initially, Access Manager implemented the Identity Federation Framework (Liberty ID-FF) specification, including account federation, authentication domains, and single sign-on (SSO). Subsequent releases of Access Manager added new features, as defined in version 1.2 of the Liberty ID-FF specifications and the version 1.0 specifications of the Liberty Identity Web Services Framework (Liberty ID-WSF). Web services include a framework for retrieving and updating identity data that consists of attributes stored in identity-based service providers across the Internet. A client application programming interface (API) for communication between identity providers and service providers is also provided.
Access Manager 7 2005Q4 provides additional functionality. For example, Access Manager provides the ability to bulk-federate user accounts to applications that are out-sourced to business partners and to map configured roles between the identity provider and the service provider.
For more information, see the Sun Java System Access Manager 7 2005Q4 Federation and SAML Administration Guide. This guide includes an introduction to the open-standard specifications used to develop these features and information about how Access Manager has implemented them. It also includes information about integrated web services and summaries of the application programming interface (API).
- © 2010, Oracle Corporation and/or its affiliates
