Web Browser Artifact Profile
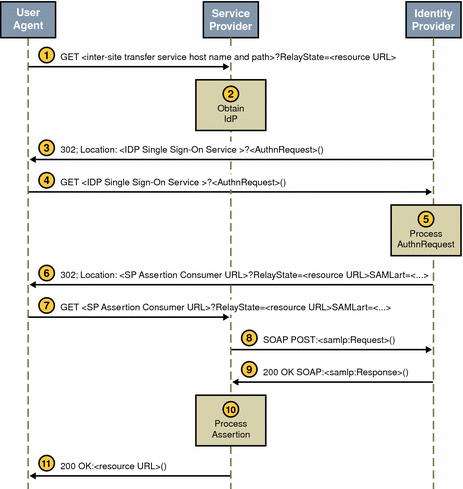
The Web Browser Artifact Profile defines interaction between three parties: a user equipped with a web browser, an authority site, and a trusted partner site. The SOAP communication should be either Basic Authentication or Client Certificate Authentication over SSL. Note that XML signing is a stronger alternative.
-
When an authenticated user attempts to access a trusted partner (generally by clicking a link), the user is directed to a transfer service at the authority site.
In Access Manager, the transfer service is
SAMLAwareServlet. The base of the transfer service URL is http(s)://access-manager-host.domain:port/deploy-uri/SAMLAwareServlet. The URL is appended with the location to which the user is requesting access (?TARGET=URL-of-destination). -
SAMLAwareServletreceives the information and compares the SAML module’s list of Trusted Partners against the user’s TARGET location.Only targets that are configured in the Trusted Partners attribute of the SAML module are accessible. For more information about this attribute, see Trusted Partners.
-
Assuming the TARGET location was found in the list of Trusted Partners,
SAMLAwareServletlooks for and validates the session token from the inbound request.Without a valid session token, Access Manager will not create an assertion.
-
Assuming a valid session token,
SAMLAwareServletcreates an artifact and a corresponding assertion.An artifact is carried as part of the URL and points to an assertion and its source. An artifact is not (and does not contain) security information. The assertion contains the security information. For more information, see SiteAttributeMapper and PartnerSiteAttributeMapper Interfaces.
Note –The need to send an artifact rather than the assertion itself is dictated by the restrictions on URL size that are imposed by many web browsers.
-
SAMLAwareServletredirects the user’s browser to theArtifact Receiver URLwith a query string that contains the artifact and the original TARGET location.
Note –In Access Manager, the
Artifact Receiver URLandSAMLAwareServletare the same. Other SAML implementations might not integrate the two functions.
-
At the
Artifact Receiver URL, the artifact is extracted from the query string to locate theSOAP Receiver URLat the trusted partner site.The SAML API extracts the source ID from the artifact and uses it to locate the
SOAP Receiver URLat the trusted partner site. For more information about the use of SOAP, see SAML SOAP Receiver. -
A SOAP query that contains the artifact is sent to the
SOAP Receiver URLat the trusted partner site that is requesting the assertion to which the artifact points. -
The
SOAP Receiver URLaccepts the returned artifact query from the trusted partner site and responds by sending the correct assertion in a SOAP response. -
The assertion is processed, mapping the user account information from the trusted partner site to the target site’s user account.
The user is either granted or denied access to the trusted partner site. If access is granted, a SSOToken is generated, a cookie is set to the browser, and the user is redirected to the TARGET location.
Figure 9–2 Web Browser Artifact Profile Interactions
A sample has been provided to test the Web Browser Artifact Profile function. See SAML Samples for more information.
- © 2010, Oracle Corporation and/or its affiliates
