Chapter 3 Java Enterprise System Integration Features
This chapter provides conceptual and technical background for understanding features that play key roles in integrating Java ES components into a single software system.
These features help you understand some of the benefits of using Java Enterprise System, as compared to manually integrating disparate infrastructure products.
The chapter covers the following features:
The Java Enterprise System Integrated Installer
All Java ES components are installed using a single installer. This installer provides consistent installation and uninstallation procedures and behavior across all components.
The Java ES installer is an integrated framework that transfers Java ES software to a host system. The installer lets you select and install any number of Java ES components on any computer in your computing environment. The installer also provides for some installation-time configuration, depending on the particular Java ES components being installed.
The Java ES installer does not, in itself, perform distributed installations. To deploy a distributed Java ES software solution, you use the Java ES installer to install the appropriate components on each computer in your environment, one computer at a time. You must use a reasonable sequence of installation sessions and configuration procedures, based on your deployment architecture and component dependencies.
The installer runs interactively in both a graphical mode and a text-based mode, and also provides a parameter-driven silent installation mode. In addition to English, the installer supports seven languages: French, German, Spanish, Korean, Simplified Chinese, Traditional Chinese, and Japanese.
This section discusses the following aspects of the integrated Java ES installer (for more detailed information see the Sun Java Enterprise System 2005Q4 Installation Guide for UNIX):
Preexisting Software Checking
The installer examines the computer on which you are installing and identifies the Java ES components that are already installed. The installer then checks at several levels to make sure that all existing components are at the appropriate release level to interoperate successfully. The installer informs you about those software components that are incompatible and must be upgraded or removed.
Similarly, the installer checks for Java ES shared components (see Shared Components), such as J2SE or NSS, that are already installed. If the installer finds versions of shared components that are incompatible, it lists them. If you proceed with installation, the installer automatically upgrades the shared components to newer versions.
Dependency Checking
The installer does extensive checking of components to verify that the installation components you select function properly together.
Many components have dependencies on other components. The installer provides logic to ensure that those dependencies are met. For this reason, When you select a component to install, the installer automatically includes the components and subcomponents upon which the selected component has dependencies.
You cannot deselect a component if another selected component depends upon that component locally. However, if the dependency is not local, you receive a warning but are able to proceed under the assumption that the dependency is satisfied by a component on a different host computer.
Initial Configuration
Many Java ES components require initial configuration before they can be started. For some components, the Java ES installer can perform this initial configuration.
You can choose to have the installer perform this initial configuration (Configure Now option) or to install the software without performing initial configuration (Configure Later option), in which case you have to explicitly configure each installed component after installation is complete.
If you choose to have the installer do the initial configuration, you supply the required configuration information during installation. In particular, you can specify a set of parameter values that are common across all component products, such as an administrator ID and password.
Uninstallation
Java Enterprise System also provides an uninstallation program. You can use this program to remove components that were installed on the local computer by the Java ES installer. The uninstaller checks for local dependencies, and issues warnings when it discovers such a dependency. The uninstaller does not remove Java ES shared components.
The uninstaller, like the installer, can be run in graphical mode, text-based mode, or silent mode.
Integrated Identity and Security Services
An important feature of Java Enterprise System is its integrated management of user identities and its integrated authentication and authorization framework.
The following sections provide technical background for understanding the integrated identity and security services provided by Java Enterprise System:
Single Identity
Within a Java ES environment, an end user has a single integrated identity. Based on this single identity, a user can be allowed access to various resources, such as a portal, web pages, and services such as messaging, calendar, and instant messaging.
This integrated identity and security capability is based on close collaboration between Directory Server, Access Manager, and other Java ES components.
User access to a Java ES service or resource is achieved by storing user-specific information in a single user entry in a user repository or directory. That information normally includes information such as a unique name and password, an email address, a role in an organization, web page preferences, and so forth. The information in the user entry can be used to authenticate the user, authorize access to specific resources, or provide various services to that user.
In the case of Java Enterprise System, user entries are stored in a directory provided by Directory Server. When a user wants to request a service provided by a Java ES component, that service uses Access Manager to authenticate the user and authorize access to specific resources. The requested service checks user-specific configuration information in the user’s directory entry. The service uses that information to perform the work requested by the user.
The following figure illustrates access to user entries for performing user authentication and authorization and for providing services to a user.
Figure 3–1 Single User Entry Supports Many Services
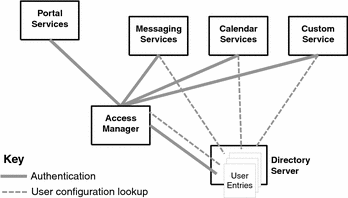
One of the features derived from this system is the ability of a web-based user to sign on to any Java ES service, and in so doing be automatically authenticated to other system services. This capability, known as single sign-on, is a powerful feature provided by Java Enterprise System.
Authentication and Single Sign-On
Java ES authentication and authorization services are provided by Access Manager. Access Manager uses information in Directory Server to broker the interaction of users with Java ES web services or other web-based services in an enterprise.
Access Manager makes use of an external component known as a policy agent. The policy agent plugs into the web server hosting a service or resource being secured by Access Manager. The policy agent intercedes on behalf of Access Manager in requests made by users to the secured resources. For some Java ES components, such as Portal Server and Communications Express, the functionality of the policy agent is provided by an Access Manager subcomponent (see Sun Java System Access Manager 7 2005Q4).
Authentication
Access Manager includes an authentication service for verifying the identities of users who request access (by way of HTTP or HTTPS) to web services within an enterprise. For example, a company employee who needs to look up a colleague’s phone number uses a browser to go to the company’s online phone book. To log in to the phone book service, the user has to provide a user ID and password.
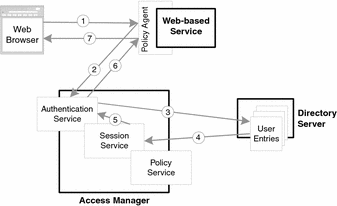
The authentication sequence is shown in Figure 3–2. A policy agent intercedes in the request to log on to the phone book (1), and sends the request to the authentication service (2). The authentication service checks the user ID and password against information stored in Directory Server (3). If the log-in request is valid, the user is authenticated (4), (5), and (6), and the company phone book is displayed to the employee (7). If the log-in request is not valid, an error is generated, and authentication fails.
The authentication service also supports certificate-based authentication over HTTPS.
Figure 3–2 Authentication Sequence
Single Sign-On
The authentication scenario discussed in the previous paragraphs, glosses over an important step. When a user’s authentication request is verified, the Access Manager’s session service is engaged (4), as shown in Figure 3–2. The session service generates a session token, which holds the user’s identity information and a token ID (5). The session token is sent back to the policy agent (6) which forwards the token (as a cookie) to the browser (7) from which the authentication request was made.
When the authenticated user attempts to access another secured service, the browser passes the session token to the corresponding policy agent. The policy agent verifies with the session service that the user’s previous authentication remains valid, and the user is granted access to the second service without being asked to re-enter a user ID and password.
Accordingly, a user needs to sign on only once to be authenticated to multiple web-based services provided by Java Enterprise System. The single sign-on authentication remains in effect until the user explicitly signs off or the session expires.
Authorization
Access Manager also includes a policy service that provides access control to web-based resources in a Java ES environment. A policy is a rule that describes who is authorized to access a specific resource under specific conditions. The authorization sequence is shown in the following figure.
Figure 3–3 Authorization Sequence
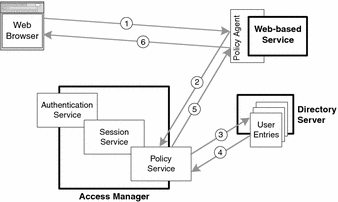
When an authenticated user makes a request for any resource secured with Access Manager (1), the policy agent notifies the policy service (2), which uses information in Directory Server (3) to evaluate the access policy governing the resource to see if the user has permission to access the resource (4). If the user has access privileges (5), then the resource request is fulfilled (6).
Access Manager provides the means for defining, modifying, granting, revoking, and deleting policies within an enterprise. The policies are stored in Directory Server and configured through policy-related attributes in organization entries. Roles can also be defined for users and incorporated in policy definitions.
Access Manager policy agents are the policy enforcers. When the policy service rejects an access request, the policy agent prevents the requesting user access to the secured resources.
Key Terms in This Chapter
This section explains key technical terms used in this chapter, with an emphasis on clarifying the relationships between these terms how they are used in the Java Enterprise System context.
- directory
-
A special kind of database optimized for reading data rather than writing data. Most directories are based on LDAP (Lightweight Directory Access Protocol), an industry-standard protocol.
- policy
-
A rule that describes who is authorized to access a specific resource under specific conditions. The rule can be based on groups of users or roles in an organization.
- single identity
-
An identity that a user has by virtue of a single user entry in a Java Enterprise System directory. Based on this single user entry a user can be allowed access to various Java Enterprise System resources, such as a portal, web pages, and services such as messaging, calendar, and instant messaging.
- single sign-on
-
A feature that allows a user’s authentication to one service in a distributed system to be automatically applied to other services in the system.
- © 2010, Oracle Corporation and/or its affiliates
