Authentication and Single Sign-On
Java ES authentication and authorization services are provided by Access Manager. Access Manager uses information in Directory Server to broker the interaction of users with Java ES web services or other web-based services in an enterprise.
Access Manager makes use of an external component known as a policy agent. The policy agent plugs into the web server hosting a service or resource being secured by Access Manager. The policy agent intercedes on behalf of Access Manager in requests made by users to the secured resources. For some Java ES components, such as Portal Server and Communications Express, the functionality of the policy agent is provided by an Access Manager subcomponent (see Sun Java System Access Manager 7 2005Q4).
Authentication
Access Manager includes an authentication service for verifying the identities of users who request access (by way of HTTP or HTTPS) to web services within an enterprise. For example, a company employee who needs to look up a colleague’s phone number uses a browser to go to the company’s online phone book. To log in to the phone book service, the user has to provide a user ID and password.
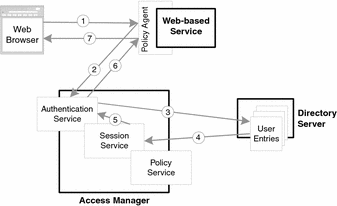
The authentication sequence is shown in Figure 3–2. A policy agent intercedes in the request to log on to the phone book (1), and sends the request to the authentication service (2). The authentication service checks the user ID and password against information stored in Directory Server (3). If the log-in request is valid, the user is authenticated (4), (5), and (6), and the company phone book is displayed to the employee (7). If the log-in request is not valid, an error is generated, and authentication fails.
The authentication service also supports certificate-based authentication over HTTPS.
Figure 3–2 Authentication Sequence
Single Sign-On
The authentication scenario discussed in the previous paragraphs, glosses over an important step. When a user’s authentication request is verified, the Access Manager’s session service is engaged (4), as shown in Figure 3–2. The session service generates a session token, which holds the user’s identity information and a token ID (5). The session token is sent back to the policy agent (6) which forwards the token (as a cookie) to the browser (7) from which the authentication request was made.
When the authenticated user attempts to access another secured service, the browser passes the session token to the corresponding policy agent. The policy agent verifies with the session service that the user’s previous authentication remains valid, and the user is granted access to the second service without being asked to re-enter a user ID and password.
Accordingly, a user needs to sign on only once to be authenticated to multiple web-based services provided by Java Enterprise System. The single sign-on authentication remains in effect until the user explicitly signs off or the session expires.
- © 2010, Oracle Corporation and/or its affiliates
