Chapter 1 Overview
Sun JavaTM System Calendar Server 62005Q4 (Calendar Server) is a scalable, Web-based solution for centralized calendaring and scheduling for enterprises and service providers. Calendar Server supports personal and group calendars for both events and tasks as well as calendars for resources such as conference rooms and equipment.
For information about basic configuration scenarios, see the Sun Java System Communications Services 6 2005Q4 Deployment Planning Guide.
This chapter includes the following information:
Note –
In this and subsequent chapters, when fully qualified directory paths are specified, they are for the Solaris platform. The default paths for Solaris are:
/opt/SUNWics5/cal
/var/opt/SUNWics5
/etc/opt/SUNWics5
The default paths for Linux® are:
/opt/sun/calendar
/var/opt/sun/
/etc/opt/sun
Linux users should substitute their default path in any command showing the Solaris default.
Calendar Server Installation
The installation and configuration of Calendar Server has significantly changed from earlier Calendar Server releases (pre-2003Q4 versions). There is no longer a standalone installer for Calendar Server.
If you do not already have at minimum Calendar Server 2003Q4 (6.0) installed, you must use the Sun Java Enterprise System installer to get the 2005Q4 version. With this installer, you can also install other Sun component products and packages. For information about the Java Enterprise System installer, refer to theSun Java Enterprise System 2005Q4 Installation Guide for UNIX.
If you want to upgrade from an earlier version of Sun Java Enterprise System, the upgrade process is described in the Sun Java System 2005Q4 Upgrade and Migration Guide.
For information about migrating from older versions of Calendar Server, refer to the information found in Chapter 4, Database Migration Utilities.
Post Installation Configuration
After you install Calendar Server, you must configure it. The installer does not perform configuration as part of the installation process.
 High Level Task List
High Level Task List
-
Run the Directory Server Setup script, comm_dssetup.pl, to configure Sun Java System Directory Server 5 (if the script has not already been run).
This script is located in the following directory: /opt/SUNWcomds/sbin.
For information about running it, see Chapter 2, Directory Preparation Script (comm_dssetup.pl).
-
Run the Calendar Server configuration program (csconfigurator.sh) to configure your site’s specific requirements and to create a new ics.conf configuration file.
For a description of the parameters in the ics.conf file, see Appendix E, Calendar Server Configuration Parameters.
The program is located in the following directory: /opt/SUNWics5/sbin
For information about running csconfigurator.sh, see Chapter 3, Calendar Server Configuration Program (csconfigurator.sh).
Calendar Server Special Accounts
Calendar Server special accounts include the following:
Calendar Server Administrator (calmaster)
The Calendar Server administrator is a specific user name with its associated password that can manage Calendar Server. For example, a Calendar Server administrator can start and stop Calendar Server services, add and delete users, create and delete calendars, and so on. This user has administrator privileges for Calendar Server but not necessarily for the directory server.
The default user ID for the Calendar Server administrator is calmaster, but you can specify a different user during Calendar Server configuration, if you prefer. After installation you can also specify a different user in the service.admin.calmaster.userid parameter in the ics.conf file.
The user ID you specify for the Calendar Server administrator must be a valid user account in your directory server. If the Calendar Server administrator user account does not exist in the directory server during configuration, the configuration program can create it for you.
The following table describes the Calendar Server administrator configuration parameters in the ics.conf file.
Table 1–1 Calendar Server Administrator (calmaster) Configuration Parameters
Calendar Server User and Group
These special accounts are the user ID and group ID under which Calendar Server runs. Unless there are overriding reasons not to, use the default values, icsuser and icsgroup, which are automatically created by the configuration program, if they do not exist.
If you prefer, however, you can specify values other than icsuser and icsgroup when you run the Calendar Server configuration program. These values are stored in the local.serveruid and local.servergid parameters, respectively, in the ics.conf file.
Superuser (root)
You must log in as or become superuser (root) to install Calendar Server. You can also run as superuser to manage Calendar Server using the command-line utilities. For some tasks, however, you should run as icsuser and icsgroup (or the values you have selected) rather than superuser to avoid access problems for Calendar Server files.
Proxy Administrator Logins
To allow administrators to administer user calendars, you need to set a parameter in the configuration file, ics.conf. The default is "no", which means this kind of proxy authentication is not allowed.
If you are using Communications Express, this parameter must be set to "yes".
For instructions on how to set this parameter and verify that proxy logins are working, see Configuring Logins and Authentication.
Calendar Server End User Administration
End users connect to Calendar Server from client machines using a Web graphical user interface (GUI), Sun Java System Communications Express. Users must have a unique entry in the LDAP directory. Each user can have one or more calendars and can belong to one or more groups.
Administrators, with the proper permissions, can add, delete or modify user LDAP entries, or resource LDAP entries, using the Delegated Administrator Utility (command-line) or Console (GUI).
For documentation on the Delegated Administrator Utility (commadmin), see Sun Java System Communications Services 6 2005Q4 Delegated Administrator Guide.
For documentation on the Delegated Administrator Console, see the Console's online help.
In addition, when necessary, you can use ldapmodify to modify LDAP entries directly. For information about ldapmodify, refer to the Sun ONE Directory Server Resource Kit 5.2 Tools Reference.
Utility programs used in pre-Java Enterprise System deployments, such as csuser, are still bundled with Calendar Server. If you are using Access Manager in your deployment, do not use these utilities for managing or creating user, domain or resource LDAP entries. There are some exceptions. Where these apply, this guide will direct you to the proper utility.
This section describes the following aspects of user and user calendar administration:
Creation of Calendar Server Users
Calendar Server users are created either manually or automatically:
-
Manually — If the Directory Server is configured for Schema 2, an administrator can add users to the directory server using Delegated Administrator and then create the users’ default calendars using the Calendar Server cscal utility.
If the Directory Server is configured for Schema 1, create both the user and the calendar at the same time using the Calendar Server csuser utility.
-
Automatically (autoprovisioning) — If autoprovisioning is configured and if the user already exists in the LDAP directory, then the first time that user logs in. Calendar Server automatically creates a default calendar.
In non-hosted domain mode, Calendar Server creates the calendar ID (calid) of the default calendar from the user ID. For example, if John Doe has a user ID of jdoe, his default calendar calid would be jdoe.
In hosted domain mode, the calid is a combination of the user ID and the user’s domain. For example, if John Doe is in domain example.com, and his user ID is jdoe, then his calid in a hosted domain environment is jdoe@example.com.
For autoprovisioning to occur, the following criteria must be met:
-
The local.autoprovision parameter must be set to “yes” (which is the default) in the ics.conf file.
-
In hosted (virtual) domain mode, the domain must be calendar enabled. A domain is calendar enabled if its LDAP entry contains the icsCalendarDomain object class.
For example, suppose tchang exists in the directory server but is not yet enabled for calendaring (that is, does not have a default calendar). When tchang logs into Calendar Server for the first time, Calendar Server automatically enables tchang for calendaring and creates a default calendar with the calid tchang.
-
Authentication of Calendar Server Users
Calendar Server requires a directory server such Sun Java System Directory Server to authenticate users (and to store user preferences). However, to allow access for users defined in a non-LDAP directory server, Calendar Server includes the Calendar Server API (CSAPI), which you can use to write a plug-in to access a non-LDAP directory. For information about CSAPI, refer to the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Calendar Server User Preferences
Calendar Server allows users to customize their views of calendar data by setting user preferences attributes, which are stored in the directory server. User preferences (as opposed to Calendar Server configuration parameters) refer to the user interface representation of calendar data and include items such as user name, email address, and preferred colors to use when rendering calendar views.
For a list of preferences, refer to the get_userprefs and set_userprefs WCAP commands in the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Calendar Groups
A calendar group is a named list of individual subscribed calendars. Group calendars allow multiple calendars to be combined into a single calendar for viewing. A user creates the groups using the Communications Express graphical user interface.
For example, a user can have a calendar group consisting of a private calendar, department calendar, and company holidays calendar. Users can also use a calendar group to select a list of calendars and view them side-by-side or invite the calendar owners to an event.
These groups are not to be confused with LDAP groups. Groups created in the user interface are stored in the user’s LDAP entry in icsSet attributes. Therefore, other users can’t see them when searching for attendees in LDAP.
For more information about Calendar Server users, see Chapter 14, Administering Users and Resources.
Calendar Resources
A resource is anything that can be scheduled using a calendar, such as a conference room, or a projector. There is a separate resource LDAP entry for each such item. Create the LDAP entry and its associated calendar using the appropriate tools:
-
For Schema 2 - Use Delegated Administrator to create the resource LDAP entry, and the Calendar Server utility resource to create the calendar.
-
For Schema 1 - Use the csresource create command which creates both the resource LDAP entry and the calendar.
Calendar Server Data
This section describes the following information about Calendar Server data:
Calendar Server Data Format
Calendar Server data format is modeled after RFC 2445, Internet Calendaring and Scheduling Core Object Specification (iCalendar). Calendar Server supports the following formats:
-
XML (.xml) — The interface to Communications Express.
-
iCalendar (.ical) — The default format.
You can use CSAPI to develop a translator DLL or shared library for the WCAP protocol. For information about WCAP and CSAPI, see the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Import and Export of Calendar Data
Calendar data can be imported and exported in either iCalendar (.ical) or XML (.xml) format. Calendar Server administrators can import and export calendar data using the Calendar Server csimport and csexport utilities. End users can import and export calendar data using the Communications Express user interface.
Calendar Links for Data Exchange
Calendars can be referenced as links embedded in email messages and on Web pages. Users can then click a link to view a calendar without having to log into Calendar Server, as long as the calendar allows read access. For example, the following link specifies a resource room named Auditorium:
http://calendar.sesta.com:8080/?calid=Auditorium
Calendar Server Alarms
Calendar Server supports server-side email alarms, which can be sent to a list of recipients. The format of the email message is configurable and is maintained as a server attribute, rather than as a user or calendar attribute. Calendar Server has limited support for the ITIP/IMIP standards (RFC 2446 and RFC 2447), including ITIP methods PUBLISH, REQUEST, REPLY, and CANCEL for events.
LDAP Data Cache Option
The LDAP data cache option ensures that LDAP data is available immediately after it has been committed, even if the LDAP directory server is configured to include a delay in the availability of committed data.
For example, if your site has deployed a master/slave LDAP configuration where Calendar Server accesses the master LDAP directory through a slave LDAP directory server, which in turn introduces a delay in the availability of committed LDAP data, the LDAP data cache can ensure that your Calendar Server clients have accurate LDAP data.
This section covers the following topics:
Considerations for Using the LDAP Data Cache
Use these guidelines to determine if your site should configure the LDAP data cache:
-
If Calendar Server at your site accesses your master (or root) LDAP directory server directly with no delays in the availability of committed LDAP data, you don t need to configure the LDAP data cache. Make sure that the local.ldap.cache.enable parameter is set to "no" (which is the default).
-
If you have deployed a Master/Slave LDAP Configuration, where Calendar Server accesses the master LDAP directory through a slave LDAP directory server, there will be a delay in the availability of committed LDAP data. Configure the LDAP data cache to ensure that your end users have the most recent data.
Master/Slave LDAP Configuration
A master/slave LDAP configuration includes a master (root) directory server and one or more slave (consumer or replica) directory servers. Calendar Server can access the master LDAP directory server either directly or through a slave directory server:
-
If Calendar Server accesses the master LDAP directory server directly, the LDAP should be accurate, and you don t need to configure the LDAP data cache.
-
If Calendar Server accesses the master LDAP directory server through a slave directory server, LDAP data changes are usually written transparently using an LDAP referral to the master directory server. The LDAP referral then replicates the data back to each slave directory server.
In this second type of configuration, problems with inaccurate LDAP data can occur because of the delay in the availability of committed LDAP data to the slave directory servers.
For example, Calendar Server commits an LDAP data change, but the new data is not available for a specific amount of time because of the delay in the master directory server updating each slave directory server. A subsequent Calendar Server client operation uses the old LDAP data and presents an out-of-date view.
If the delay in updating the slave directory servers is short (only a few seconds), clients might not experience a problem. However, if the delay is longer (minutes or hours), clients will display inaccurate LDAP data for the length of the delay.
The following table lists operations and the LDAP attributes affected by such a delay:
Operation
LDAP Attributes
Auto provisioning
icsCalendar, icsSubscribed, icsCalendarOwned, icsDWPHost
Calendar groups
icsSet
Calendar creation
icsCalendarOwned, icsSubscribed
Calendar subscription
icsSubscribed
User options
icsExtendedUserPrefs, icsFirstDay, icsTimeZone, icsFreeBusy
Calendar searches
icsCalendarOwned
LDAP Data Cache
The LDAP data cache resolves the master/slave LDAP configuration problem by providing Calendar Server clients with the most recent LDAP data, even when the master directory server has not updated each slave directory server.
If the LDAP data cache is enabled, Calendar Server writes committed LDAP data to the cache database (ldapcache.db file). By default, the LDAP cache database is located in the ldap_cache database directory, but you can configure a different location if you prefer.
When a client makes a change to the LDAP data for a single user, Calendar Server writes the revised data to the LDAP cache database (as well as to the slave directory server). A subsequent client operation retrieves the LDAP data from the cache database. This data retrieval applies to the following operations for a single user:
-
User's attributes at login
-
User's options (such as color scheme or time zone)
-
User's calendar groups
-
User's subscribed list of calendars
Thus, the LDAP data cache database provides for:
-
Data consistency across processes on a single system The database is available to all Calendar Server processes on a multiprocessor system.
-
Data persistence across user sessions The database is permanent and does not require refreshing.
Limitations
The LDAP data cache does not provide for:
-
Reading the cache for searches where a list of entries is expected. For example, searching for attendees for a meeting. This type of search is subject to any LDAP delay. For instance, a newly created calendar will not appear in a calendar search if the LDAP search option is active and the search is performed within the delay period following the creation of a new calendar.
-
Reading and writing of the cache across multiple front-end servers. Each front-end server has its own cache, which is not aware of data in other caches.
-
The capability to handle a user who doesn't always log into the same server. Such a user will generate different LDAP data in the cache on each server.
Calendar Access Control
Calendar Server uses Access Control Lists (ACLs) to determine the access control for calendars, calendar properties, and calendar components such as events and todos (tasks).
This section covers these topics:
Secure Calendar Server Logins
When users log in to Calendar Server through Communications Express, by default the authentication process does not encrypt the login information, including user names and passwords. If you want secure logins as your site, configure Calendar Server to use the Secure Sockets Layer (SSL) protocol to encrypt the login data. For more information, see Chapter 8, Configuring SSL, Configuring SSL.
Access Control by Users
Calendar Server considers the following users when determining access to calendars, calendar properties, and calendar components:
-
Primary calendar owners have full access to their own calendars. Calendar Server does not perform any access control checks for primary owners accessing their own calendars.
-
An administrator such as calmaster, or a superuser such as root, is not subject to access control restrictions and can perform any operation on a calendar or calendar component. For more information, see Calendar Server Special Accounts.
-
Primary calendar owners can designate other owners for their calendars. The other owner can then act on behalf of the primary owner to schedule, delete, modify, accept, or decline events or todos (tasks) for a calendar.
-
The special calendar ID (calid) anonymous can access Calendar Server using any password, if service.http.allowanonymouslogin in the ics.conf file is set to “yes” (which is the default). The anonymous user is not associated with any particular domain. You can change the calid for the anonymous user by editing the calstore.anonymous.calid parameter.
You can also view a calendar anonymously if the calendar’s permissions allow read access for everybody. For example, the following link allows users to anonymously view the calendar with the calid tchang:meetings (if the calendar’s permissions allow read access for everybody):
http://calendar.sesta.com:8080/?calid=tchang:meetings
An anonymous user can view, print and search for public events and tasks on the calendar but cannot perform any other operations.
For information about viewing a resource calendar anonymously, see Linking to a Calendar.
Access Control Lists (ACLs)
Calendar Server uses access control lists (ACLs) to determine access control for calendars, calendar properties, and calendar components such as events and todos (tasks). An ACL consists of one or more access control entries (ACE's), which are strings that collectively apply to the same calendar or component Each ACE in an ACL must be separated by a semicolon.
Note –
ACE strings are case insensitive.
For example:
-
jsmith^c^wd^g consists of a single ACE.
-
@@o^a^r^g;@@o^c^wdeic^g;@^a^sf^g consists of three ACE's.
An ACE consists of the following elements, with each element separated by a caret (^):
-
Who - The individual, user, domain, or type of user who the ACE applies to.
-
What - The target being accessed, such as a calendar or a calendar component such as an event, todo (task), or calendar property.
-
How - The type of access control rights permitted, such as read, write, or delete.
-
Grant - A specific access control right that is either granted or denied.
For example, in the ACE jsmith^c^wd^g:
-
jsmith is the Who element, indicating who the ACE applies to.
-
c is the What element, indicating what is being accessed (only the calendar components).
-
wd is the How element, indicating which access rights are to be granted or denied (write and delete).
-
g is the Grant element, indicating that the specified access rights, write and delete, for the calendar components are granted to jsmith.
Who
The Who element is the principal value for an ACE and indicates who the ACE applies to, such an individual user, domain, or specific type of user.
Who is also called the Universal Principal Name (UPN). The UPN for a user is the user’s login name combined with the user’s domain. For example, user bill in domain sesta.com has the UPN bill@sesta.com.
Table 1–2 “Who” Formats for Access Control Entry (ACE) Strings
What
The What element specifies the target being accessed, such as a calendar, calendar component (event or task), or calendar property.
Table 1–3 “What” Values for Access Control Entry (ACE) Strings|
Value |
Description |
|
|---|---|---|
|
Specifies calendar components such as events and tasks |
|
|
Specifies calendar properties such as name, description, owners, and so forth |
|
|
Specifies an entire calendar (all), including both components and properties |
How
The How element specifies the type of access control rights permitted, such as read, write, or delete.
Table 1–4 “How” Types for Access Control Entry (ACE) Strings|
Type |
Description |
|---|---|
|
r |
Read access. |
|
w |
Write access, including adding new items and modifying existing items. |
|
d |
Delete access. |
|
s |
Schedule (invite) access. Requests can be made, replies will be accepted, and other ITIP scheduling interactions will be honored. |
|
f |
Free/busy (availability) access only. Free/busy access means that a user can see scheduled time on a calendar, but is not allowed to see the event details. Instead, only the words “Not Available” appear by a scheduled time block. Blocks of time without any scheduled events are listed with the word “Available” next to them. |
|
l |
Lookup access for a domain. |
|
e |
Act on behalf of for reply access. This type grants a user the right to accept or decline invitations on behalf of the calendar’s primary owner. This type of access does not need to be granted explicitly because it is implied when a user is designated as an owner (an owner other than the primary owner) of a calendar. |
|
i |
Act on behalf of for invite access. This type grants a user the right to create and modify components in which other attendees have been invited on behalf of the calendar's primary owner. This type of access does not need to be granted explicitly because it is implied when a user is designated as an owner (an owner other than the primary owner) of a calendar. |
|
c |
Act on behalf of for cancel access. This type grants a user the right to cancel components to which attendees have been invited on behalf of the calendar's primary owner. This type of access does not need to be granted explicitly because it is implied when a user is designated as an owner (an owner other than the primary owner) of a calendar. |
|
z |
Self-administrating access - the authenticated user is granted the ability to add or remove an Access Control Entry. Users with this privilege can add and remove privileges for themselves. For example, UserA may not have write access to UserB’s calendar, but UserA has been granted self-administrating access to UserB’s calendar. Therefore, UserA can add an Access Control Entry that grants himself write access to UserB’s calendar. Note: This privilege does not allow UserA to grant other users access to UserB’s calendar. For example, the self-administrating privilege does not allow UserA to grant UserC access to UserB’s calendar. |
Grant
The Grant element specifies whether to grant or deny access for a specified access type, such as d (delete) or r (read).
Table 1–5 Grant Values for Access Control Entry (ACE) Strings|
Value |
Description |
|---|---|
|
g |
Grant the specific access control right. |
|
d |
Deny the specific access control right. |
Examples of ACE's
The following examples show the use of ACE's:
-
Grant the user ID jsmith read access to the entire calendar, including both components and properties:
jsmith^a^r^g
-
Grant jsmith write and delete access to components only:
jsmith^c^wd^g
-
Grant all users in the sesta.com domain privileges to schedule, availability, and read access to components only:
@sesta.com^c^sfr^g
-
Grant all owners write and delete access to components only:
@@o^c^wd^g
-
Deny jsmith all access to calendar data:
jsmith^a^sfdwr^d
-
Grant all owners read, schedule, and availability access to the entire calendar, including both components and properties:
@@o^a^rsf^g
-
Grant read access to all users:
@^a^r^g
Placing ACE's in an ACL
When the Calendar Server reads an ACL, it uses the first ACE it encounters that either grants or denies access to the target. Thus, the ordering of an ACL is significant, and ACE strings should be ordered such that the more specific ones appear before the more general ones.
For example, suppose the first ACE in an ACL for the calendar jsmith:sports grants read access to all users. Then, Calendar Server encounters a second ACE that denies bjones read access to this calendar. In this case, Calendar Server grants bjones read access to this calendar and ignores the second ACE because it is a conflict. Therefore, to ensure that an access right for a specific user such as bjones is honored, the ACE for bjones should be positioned in the ACL before more global entries such as an ACE that applies to all users of a calendar.
Calendar Server Internal Subsystems
Sun Java System Calendar Server includes the following internal subsystems:
The following graphic shows the logical flow through these subsystems.
Figure 1–1 Calendar Server Internal Subsystems Logical Flow
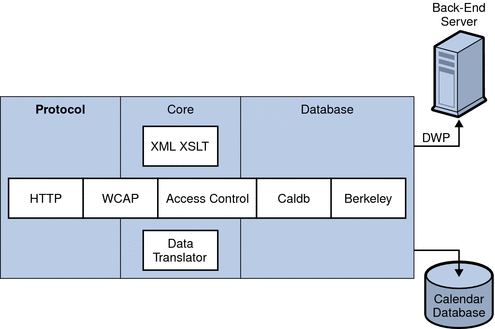
Protocol Subsystem
Clients retrieve calendar data by submitting requests using the HTTP protocol layer. This is a minimal HTTP server implementation, streamlined to support calendar requests. This is done by appending Web Calendar Access Protocol (WCAP) commands to the URL.
WCAP is an open protocol that allows you to write your own interface to Calendar Server. Using WCAP commands (.wcap extension), you can perform most server commands, except for certain administrative commands. You can use WCAP commands to request output as XML or iCalendar wrapped in HTML.
For information about WCAP commands, see the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Core Subsystem
The Core subsystem includes anaccess control component, WCAP using data translators to format data coming from the calendar database component, and any CSAPI plug-ins. The Core subsystem processes calendar requests and generates WCAP output. The Core subsystem also handles user authentication, including Calendar Server API (CSAPI).
Database Subsystem
The Database subsystem uses the Berkeley DB from Sleepycat Software (the database API is not public). The Database subsystem stores and retrieves calendar data to and from the database, including events, todos (tasks), and alarms. Calendar data is based on iCalendar format, and the schema used for Calendar Server data is a super set of the iCalendar standard.
The Database subsystem returns data in a low-level format, and the Core UI generator then translates the low-level data and sends it through WCAP.
For a distributed calendar database, Calendar Server uses the Distributed Wire Protocol (DWP) to provide a networking capability. For more information, see Distributed Database Service: csdwpd.
For information about the calendar database, refer to Chapter 16, Administering Calendar Server Databases with csdb.
Calendar Server Services
Calendar Server services run as daemons (or processes). These services include:
Administration Service: csadmind
The csadmind service provides a single point of authentication for administering Calendar Server. The csadmind service also manages alarm notifications, group scheduling requests.
HTTP Service: cshttpd
Since Calendar Server uses HTTP as its primary transport, the cshttpd service listens for HTTP commands from Calendar Server end users, receives the user commands, and returns calendar data, depending on the format specified in the incoming WCAP command. Data can be formatted in standard RFC 2445 iCalendar format (text/calendar) or XML format (text/xml
Automatic Backup Service: csstored
When properly configured, the csstored service creates automatic backups of the calendar database. However, the service is installed in an unconfigured state. You can configure Calendar Server for automatic backups when the csconfigurator.sh configuration program runs, or you can do it at a later time, as described in this guide.
If the service is started in the unconfigured and disabled state, it will send a message to the administrator every 24 hours stating that automatic backups are not enabled.
For instructions on how to configure this service to perform backups, see Chapter 10, Configuring Automatic Backups (csstored).
When configured properly, the service has the following functionality:
-
Upon system start up and at 24 hour (default interval) intervals thereafter, takes a snapshot of the live Calendar Server calendar database. The interval is configurable. (If the service has been stopped and restarted, it does not take another snapshot unless the configured interval has elapsed since the last snapshot.)
-
Verifies the database by running csdb verify against the backup copy.
If the verify step fails (the database is corrupted), the service notifies the administrator. The administrator can put the live database in read-only mode, allowing you to troubleshoot the problem without having to shut down the databases. While in read-only mode, no modify or delete transactions are accepted (no logging). For more information about read-only mode, see Preventing Service Interruptions When Your Database is Corrupted (Read-only Mode).
Administrator intervention is required when a corruption is sensed. A notification is sent to the administrator.
If the verify succeeds, csstored performs the following additional tasks:
-
Creates an archival backup consisting of the database snapshot and all the transaction log files that were applied to it since the previous snapshot.
-
Creates a hot backup consisting of the database snapshot with the transaction log files applied to it.
Should the live database become corrupted, a hot backup provides an immediate up to date backup of the database with a minimum of data loss and downtime.
For information on how to restore an automatic backup copy, see Restoring an Automatic Backup Copy.
Event Notification Service (ENS): csnotifyd and enpd
The ENS service consists of these individual services:
-
csnotifyd–The csnotifyd service sends notifications of events and todos (tasks). The csnotifyd service also subscribes to alarm events. When an alarm event occurs, csnotifyd sends an SMTP message reminder to each recipient.
-
enpd–The enpd service acts as the broker for event alarms. The enpd service receives notifications of alarms from the csadmind service, checks for subscriptions to this event, and then notifies the event’s subscribers by passing the subscribed-to alarm notifications to csnotifyd. The enpd service also receives and stores subscriptions and cancellations of subscriptions (unsubscribe) from csnotifyd.
Note –
The enpd and csnotifyd services are not required to run on the same server as the cshttpd, csdwpd, or csadmind processes.
Distributed Database Service: csdwpd
The csdwpd service is required to distribute calendar databases across multiple back-end servers. The csdwpd service allows you to spread the calendar database across multiple back-end servers within the same Calendar Server configuration to form a distributed calendar store.
The csdwpd service runs in the background on a back-end server and accepts requests that follow the Database Wire Protocol (DWP) for accessing the calendar database. DWP is an internal protocol used to provide networking capability for the Calendar Server database.
Calendar Server API's and SDK's
Calendar Server includes the following API's and SDK's:
Web Calendar Access Protocol (WCAP)
Calendar Server supports WCAP 3.0, a high-level, command-based protocol that allows communication with clients. WCAP commands, which use the .wcap extension, allow clients to get, modify, and delete calendar components, user preferences, calendar properties, and other calendar information such as time zones. WCAP elements such as times, strings, and parameters generally follow RFC 2445, RFC 2446, and RFC 2447 specifications.
WCAP returns output calendar data in an HTTP message in the following formats:
-
Standard RFC 2445 iCalendar format (text/calendar)
-
XML format (text/xml)
Using WCAP commands, a Calendar Server administrator who logs in using the login.wcap has the following capabilities:
-
To override the access control of WCAP commands
The administrator can use WCAP commands to read (fetch), alter (store), or delete other user’s calendars. For an administrator to have this privilege, the following parameter in the ics.conf file must be set to "yes":
service.admin.calmaster.overrides.accesscontrol="yes"
-
To retrieve and modify user preferences for any user
The administrator can use get_userprefs.wcap and set_userprefs.wcap to retrieve and modify any user’s preferences. For an administrator to have this privilege, the following parameter in the ics.conf file must be set to "yes":
service.admin.calmaster.wcap.allowmodifyuserprefs="yes"
For more information, see the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Calendar Server API (CSAPI)
The Calendar Server API (CSAPI) allows you to customize functional areas of Calendar Server such as user login authentication, access control, and calendar lookup. For example, by default Calendar Server uses entries in an LDAP directory server to authenticate users and to store user preferences. The CSAPI allows you to override the default Calendar Server authentication by implementing another authentication mechanism that is not based on an LDAP directory server.
For information about CSAPI, see the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
Event Notification Service (ENS) API
The Event Notification Service (ENS) is an alarm dispatcher that detects events on an alarm queue and sends notifications of these events to its subscribers. The ENS API allows programmers to modify publish-and-subscribe functions used by Calendar Server to perform functions such as subscribe to events, unsubscribe to events, and notify a subscriber of events. The ENS API's consists of these specific API's: Published API, Subscriber API, and Publish and Subscribe Dispatcher API.
For information about the ENS API, see the Sun Java System Communications Services 6 2005Q4 Event Notification Service Guide.
Proxy Authentication SDK (authSDK)
Calendar Server provides the authSDK for user authentication. With authSDK, you can integrate an existing portal service with Calendar Server, thus allowing users to access various applications without requiring re-authentication. The authSDK consists of the functions packaged in a DLL/shared-object library and a header file.
A connection established between Calendar Server and the authSDK forms a trusted relationship. If a user logs in and successfully authenticates to the authSDK, Calendar Server accepts the certificate generated by the proxy for its functions.
For information about authSDK, see the Sun Java System Calendar Server 6 2005Q4 Developer’s Guide.
- © 2010, Oracle Corporation and/or its affiliates
