Configuring MMP with SSL
To configure the MMP to use SSL, do the following:
Note –
It is assumed that the MMP is installed on a machine that does not have a Message Store or MTA.
 To Configure MMP with SSL
To Configure MMP with SSL
Steps
-
If you have installed the Admin Server, use the Admin Console to install an SSL server certificate. Otherwise use the NSS tools to do this. See Network Security Services Tools
-
If you have installed the Admin Server, from the command line, make the following symbolic links to simplify things:
cd msg_svr_base/config ln -s /var/mps/serverroot/alias/admin-serv-instance-cert7.db cert7.db ln -s /var/mps/serverroot/alias/admin-serv-instance-key3.db key3.db
Also, make sure that those files are owned by the system ID under which the MMP will run. current version of Messaging Server supports the new certificate database format (cert8.db).
-
Since the sslpassword.conf file is set during the initial Messaging Server runtime configuration, you do not need to set one up. See Creating the Initial Messaging Server Runtime Configuration
Note –An alternative approach to steps 1-8 is to copy the following files: cert7.db, key3.db, secmod.db, and sslpassword.conf from an existing Messaging or Directory Server. These servers must have a server certificate and a key appropriate for the same domain already installed.
-
Edit the ImapProxyAService.cfg file and uncomment the relevant SSL settings.
-
If you want SSL and POP, edit the PopProxyAService.cfg file and uncomment the relevant SSL settings.
Additionally, you must edit the AService.cfg file and add |995 after the 110 in the ServiceList setting.
-
Make sure that the BindDN and BindPass options are set in the ImapProxyAService.cfg and PopProxyAService.cfg files.
You should also set the DefaultDomain option to your default domain (the domain to use for unqualified user names).
If you just want server-side SSL support, you are finished. Start the MMP with the following command in the msg_svr_base/sbin directory:
start-msg mmp
 To Configure MMP with Client Certificate-based Login
To Configure MMP with Client Certificate-based Login
If you want client certificate based login, do the following:
Steps
-
Get a copy of a client certificate and the CA certificate which signed it.
-
Start the Sun ONE Console as before (on the same machine as the MMP), but this time import the CA certificate as a Trusted Certificate Authority.
-
Use the Store Administrator you created during your Messaging Server installation.
For more information, see the Specifying Administrator Access to the Store
-
Create a certmap.conf file for the MMP. For example:
certmap default default default:DNComps default:FilterComps e=mail
This means to search for a match with the e field in the certificate DN by looking at the mail attribute in the LDAP server.
-
Edit your ImapProxyAService.cfg file and:
-
Set CertMapFile to certmap.conf
-
Set StoreAdmin and StorePass to values from Step 3.
-
Set UserGroupDN to the root of your Users and Groups tree.
-
-
If you want client certificates with POP3, repeat Step 5 for the PopProxyAService.cfg file.
-
If the MMP is not already running, start it with the following command in the msg_svr_base/sbin directory:
start-msg mmp
-
Import the client certificate into your client. In NetscapeTM Communicator, click on the padlock (Security) icon, then select Yours under Certificates, then select Import a Certificate... and follow the instructions.
Note –All your users will have to perform this step if you want to use client certificates everywhere.
A Sample Topology
The fictional Siroe Corporation has two Messaging Multiplexors on separate machines, each supporting several Messaging Servers. POP and IMAP user mailboxes are split across the Messaging Server machines, with each server dedicated exclusively to POP or exclusively to IMAP (You can restrict client access to POP services alone by removing the ImapProxyAService entry from the ServiceList setting; likewise, you can restrict client access to IMAP services alone by removing the PopProxyAService entry from the ServiceList setting.). Each Messaging Multiplexor also supports only POP or only IMAP. The LDAP directory service is on a separate, dedicated machine.
This topology is illustrated below in Figure 7–2.
Figure 7–2 Multiple MMPs Supporting Multiple Messaging Servers
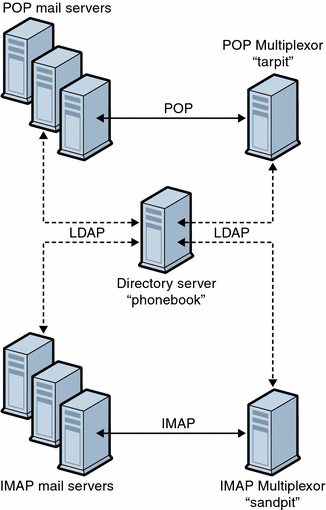
IMAP Configuration Example
The IMAP Messaging Multiplexor in Figure 7–2 is installed on sandpit, a machine with two processors. This Messaging Multiplexor is listening to the standard port for IMAP connections (143). Messaging Multiplexor communicates with the LDAP server on the host phonebook for user mailbox information, and it routes the connection to the appropriate IMAP server. It overrides the IMAP capability string, provides a virtual domain file, and supports SSL communications.
This is its ImapProxyAService.cfg configuration file:
default:LdapUrl ldap://phonebook.siroe.com/o=internet default:LogDir /opt/SUNWmsgsr/config/log default:LogLevel 5 default:BindDN "cn=Directory Manager" default:BindPass secret default:BacksidePort 143 default:Timeout 1800 default:Capability "IMAP4 IMAP4rev1 ACL QUOTA LITERAL+ NAMESPACE UIDPLUS CHILDREN BINARY LANGUAGE XSENDER X-NETSCAPE XSERVERINFO" default:SearchFormat (uid=%s) default:SSLEnable yes default:SSLPorts 993 default:SSLSecmodFile /opt/SUNWmsgsr/config/secmod.db default:SSLCertFile /opt/SUNWmsgsr/config/cert7.db default:SSLKeyFile /opt/SUNWmsgsr/config/key3.db default:SSLKeyPasswdFile "" default:SSLCipherSpecs all default:SSLCertNicknames Siroe.com Server-Cert default:SSLCacheDir /opt/SUNWmsgsr/config default:SSLBacksidePort 993 default:VirtualDomainFile /opt/SUNWmsgsr/config/vdmap.cfg default:VirtualDomainDelim @ default:ServerDownAlert "your IMAP server appears to be temporarily out of service" default:MailHostAttrs mailHost default:PreAuth no default:CRAMs no default:AuthCacheSize 10000 default:AuthCacheTTL 900 default:AuthService no default:AuthServiceTTL 0 default:BGMax 10000 default:BGPenalty 2 default:BGMaxBadness 60 default:BGDecay 900 default:BGLinear no default:BGExcluded /opt/SUNWmsgsr/config/bgexcl.cfg default:ConnLimits 0.0.0.0|0.0.0.0:20 default:LdapCacheSize 10000 default:LdapCacheTTL 900 default:HostedDomains yes default:DefaultDomain Siroe.com |
POP Configuration Example
The POP Messaging Multiplexor example in A Sample Topology is installed on tarpit, a machine with four processors. This Messaging Multiplexor is listening to the standard port for POP connections (110). Messaging Multiplexor communicates with the LDAP server on the host phonebook for user mailbox information, and it routes the connection to the appropriate POP server. It also provides a spoof message file.
This is its PopProxyAService.cfg configuration file:
default:LdapUrl ldap://phonebook.siroe.com/o=internet default:LogDir /opt/SUNWmsgsr/config/log default:LogLevel 5 default:BindDN "cn=Directory Manager" default:BindPass password default:BacksidePort 110 default:Timeout 1800 default:SearchFormat (uid=%s) default:SSLEnable no default:VirtualDomainFile /opt/SUNWmsgsr/config/vdmap.cfg default:VirtualDomainDelim @ default:MailHostAttrs mailHost default:PreAuth no default:CRAMs no default:AuthCacheSize 10000 default:AuthCacheTTL 900 default:AuthService no default:AuthServiceTTL 0 default:BGMax 10000 default:BGPenalty 2 default:BGMaxBadness 60 default:BGDecay 900 default:BGLinear no default:BGExcluded /opt/SUNWmsgsr/config/bgexcl.cfg default:ConnLimits 0.0.0.0|0.0.0.0:20 default:LdapCacheSize 10000 default:LdapCacheTTL 900 default:HostedDomains yes default:DefaultDomain Siroe.com |
- © 2010, Oracle Corporation and/or its affiliates
