Configuration Walkthrough
This section provides the high-level steps used to configure Identity Synchronization for Windows in an high-availability environment.
Note –
Only important steps are provided and any configuration instructions already discussed in the Example Bank case study have been omitted.
For detailed configuration instructions, see the Sun Java System Directory Server Enterprise Edition 6.35 Installation Guide .
Primary Installation
After the Core is installed on config-us.gt.com, the Identity Synchronization for Windows console is started. You configure the Directory Server source first.
Figure 3–6 Configuring the Directory Server Source
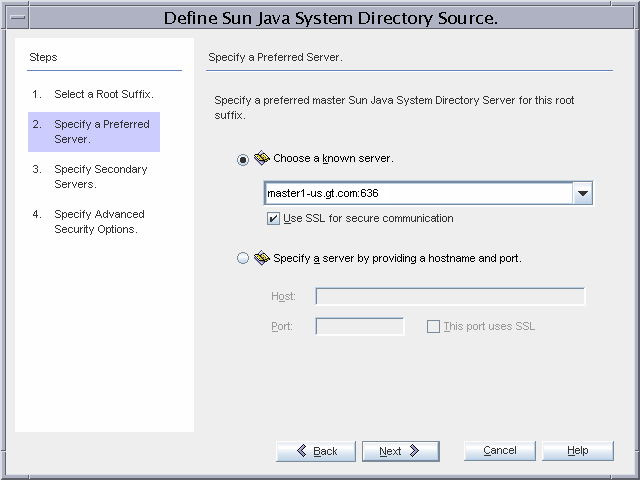
master1-us.gt.com is chosen as the preferred master. The connector communicates with the Directory Server source over SSL.
Figure 3–7 Configuring the Directory Server Source Over SSL
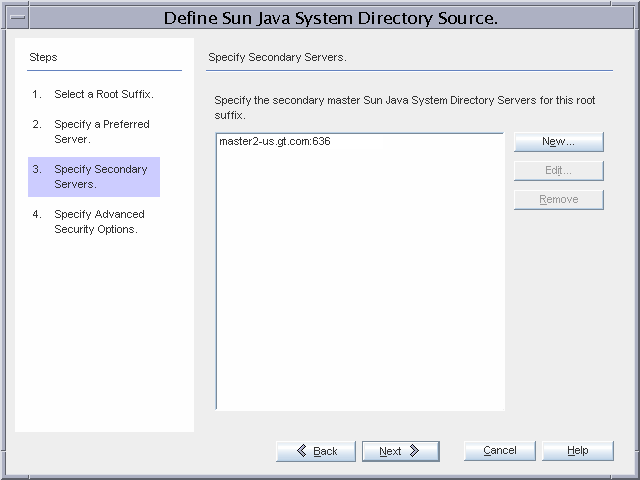
master2-us.gt.com is chosen as the secondary master. The connector communicates with Directory Server over SSL.
Figure 3–8 Configuring Advanced Security Options for the Directory Server Source
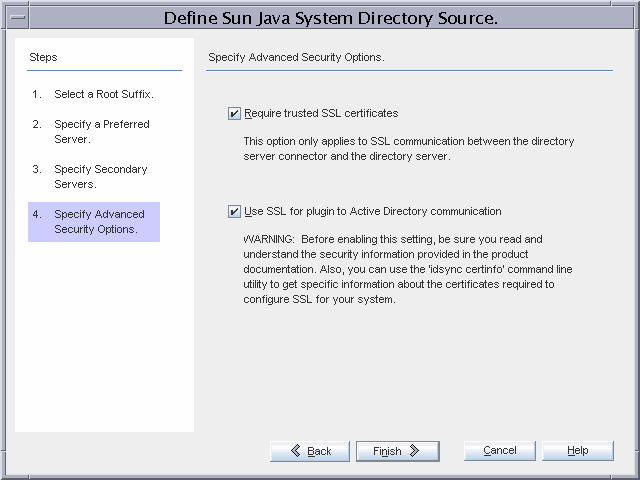
Global Telco requires the strictest security possible, so the Directory Server Connector will require a trusted SSL certificate from the directory server, and the Identity Synchronization for Windows Directory Server Plugins will communicate over SSL to Active Directory. (The Identity Synchronization for Windows Plugins inherit the SSL configuration of the directory server. Therefore, if the Directory Server requires trusted certificates, the plugin can only communicate with Active Directory if it provides a trusted certificate). Enabling these enhanced security options implies additional installation step, outlined below.
Figure 3–9 Configuring the Active Directory Domain
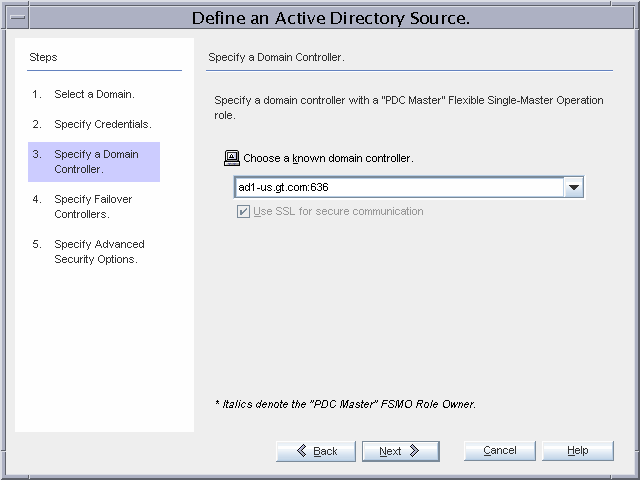
ad1-us.gt.com is the PDC FSMO Role Owner, and is selected as the domain with which the controller for the Active Directory Connector will communicate. The connector communicates over SSL.
Figure 3–10 Configuring Failover Active Directory Domain Controllers to Work over SSL
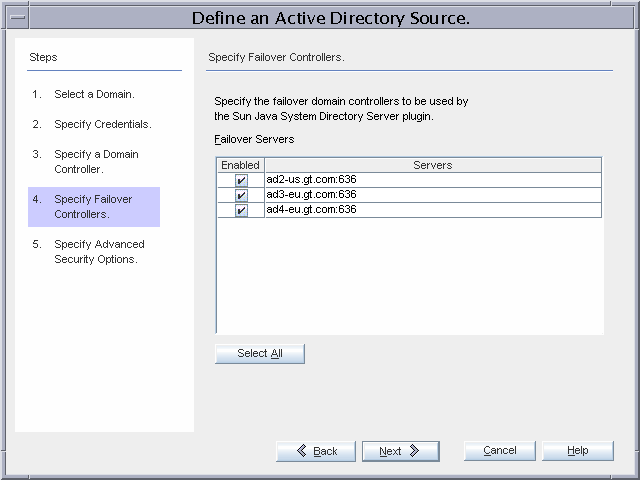
All three remaining domain controllers will be used for failover during on-demand password synchronization.
Figure 3–11 Security Option to Enable for the Active Directory Connector
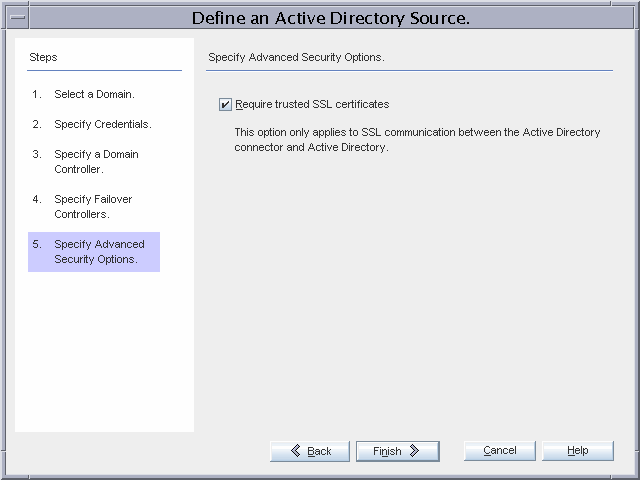
Global Telco requires the strictest security possible, so the Active Directory Connector will require a trusted SSL certificate from ad1-us.gt.com. Enabling this advanced security option implies additional installation steps as outlined below.
Figure 3–12 Attribute Modification Flow Setting
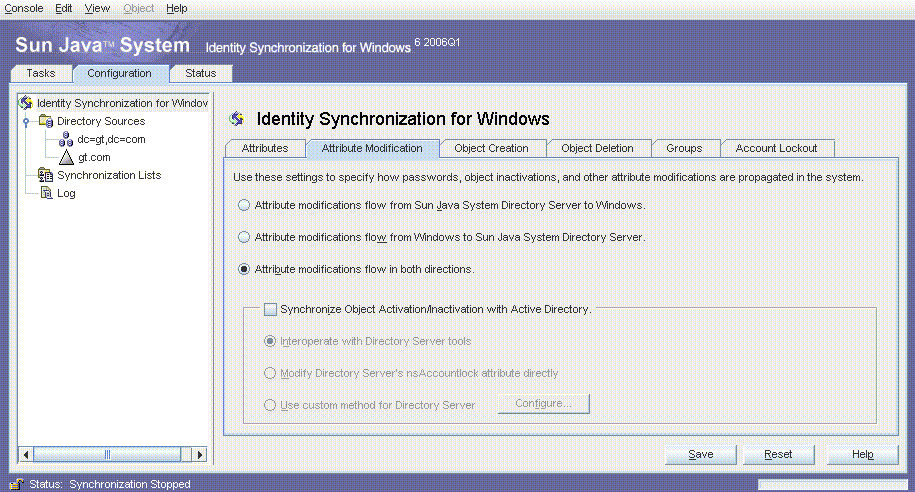
The only default global setting that is changed is the synchronization of attribute modifications from Active Directory to Directory Server, and from Directory Server to Active Directory.
Figure 3–13 Attribute Setting for Synchronization
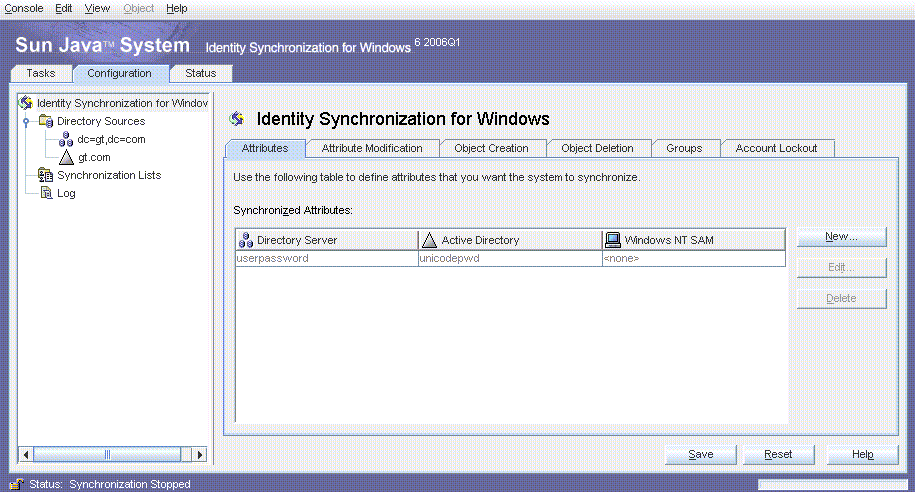
Only passwords are synchronized. No additional attributes are synchronized.
A single SUL, GT_USERS, is created as shown in Primary Installation.
Figure 3–14 Synchronization User List Creation
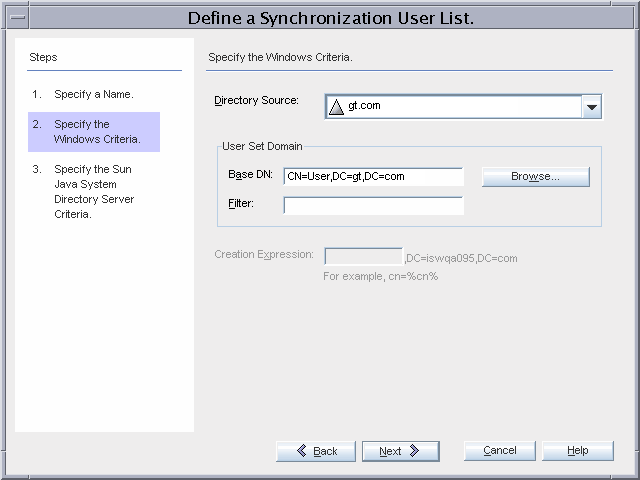
Active Directory users are stored under the default cn=users,dc=gt,dc=com container. The existing users (Administrator, Guest, TsInternetUser, and iswUser) are excluded from synchronization.
Figure 3–15 Excluding User from the Synchronization Process
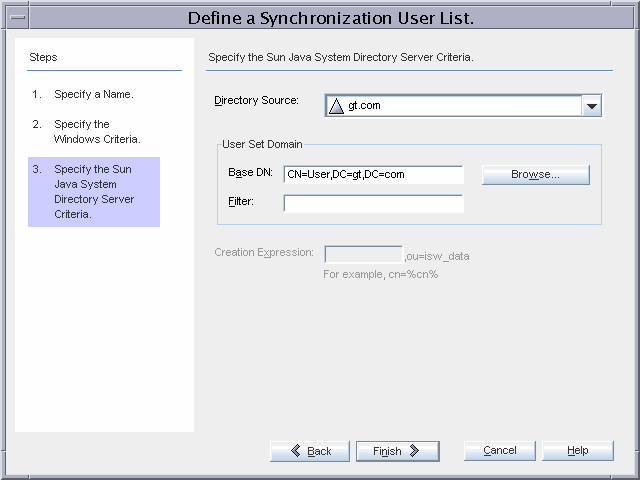
The Directory Server users are stored in the default ou=people,dc=gt,dc=com container.
After the configuration is saved, each connector is installed on connectors-us.gt.com, and the Identity Synchronization for Windows Plugin is installed.
bash-2.05# ./idsync printstat -w <password omitted\> -q <password omitted\> Exploring status of connectors, please wait... Connector ID: CNN100 Type: Sun Java(TM) System Directory Manages: dc=gt,dc=com (ldaps://master1-us.gt.com:636) (ldaps://master2-us.gt.com:636) State: READY Installed on: connectors-us.gt.com Plugin SUBC100 is installed on ldaps://master1-us.gt.com:636 Plugin SUBC101 is installed on ldaps://master2-us.gt.com:636 Plugin SUBC102 is installed on ldaps://master3-eu.gt.com:636 Plugin SUBC103 is installed on ldaps://master4-eu.gt.com:636 Plugin SUBC104 is installed on ldaps://replica1-us.gt.com:636 Plugin SUBC105 is installed on ldaps://replica2-us.gt.com:636 Plugin SUBC106 is installed on ldaps://replica3-eu.gt.com:636 Plugin SUBC107 is installed on ldaps://replica4-eu.gt.com:636 Connector ID: CNN101 Type: Active Directory Manages: gt.com (ldaps://ad2-us.gt.com:636) (ldaps://ad3-eu.gt.com:636) (ldaps://ad4-eu.gt.com:636) (ldaps://ad1-us.gt.com:636) State: READY Installed on: connectors-us.gt.com Sun Java(TM) System Message Queue Status: Started Checking the System Manager status over the Sun Java(TM) System Message Queue. System Manager Status: Started Remaining Installation and Configuration Steps: 1. Install the Sun Directory Server Plugin on every other master and read-only replica that manage users under dc=gt,dc=com. 2. Run 'idsync resync' to establish links between existing Directory Server and Windows users. 3. Start synchronization using the console or the 'idsync startsync' command. SUCCESS
Failover Installation
Once the primary installation is complete, the Identity Synchronization for Windows Core is installed on config-eu.gt.com, and the console is used to configure it.
Figure 3–16 Configuring the Preferred Directory Server
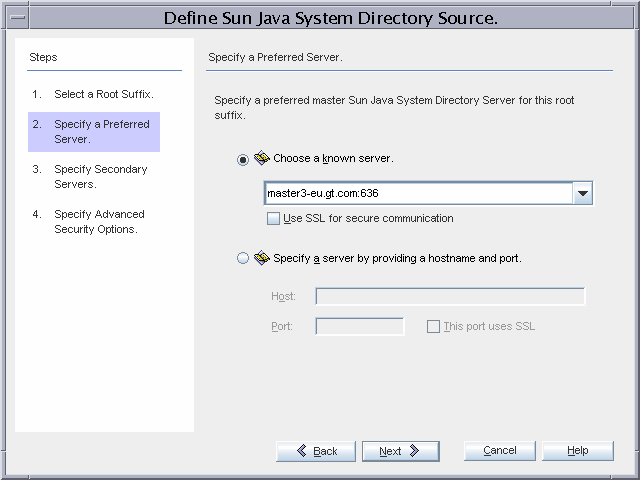
master3-eu.gt.com is the preferred Directory Server master in the failover installation.
Figure 3–17 Configuring the Secondary Directory Server Master
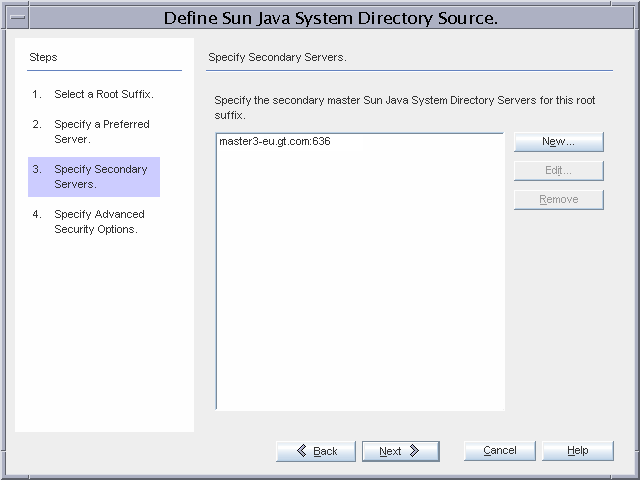
master4-eu.gt.com is the secondary directory server master in the failover installation.
Figure 3–18 Configuring the Active Directory Domain Controller
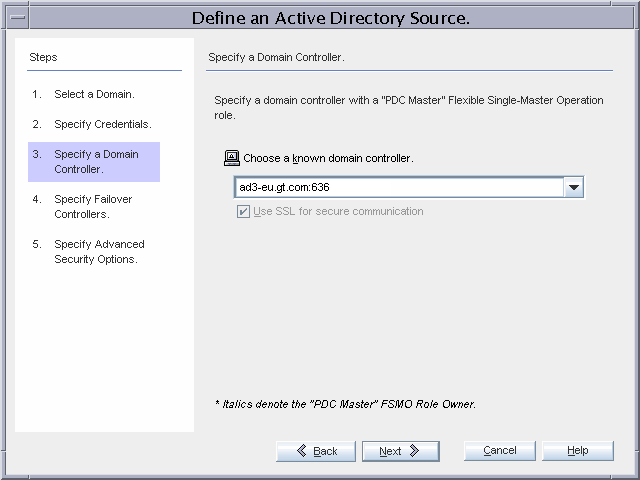
ad3-eu.gt.com is chosen as the domain controller with which the Active Directory Connector will communicate.
A warning is displayed stating that the password updates might get slow because ad3-eu.gt.com is not the PDC FSMO role owner. This warning can be ignored because changing the PDC FSMO role to this domain controller is part of the failover procedure. A similar warning is also displayed when the configuration is saved.
Figure 3–19 Configuring Domain Controllers for Failover during On-Demand Synchronization
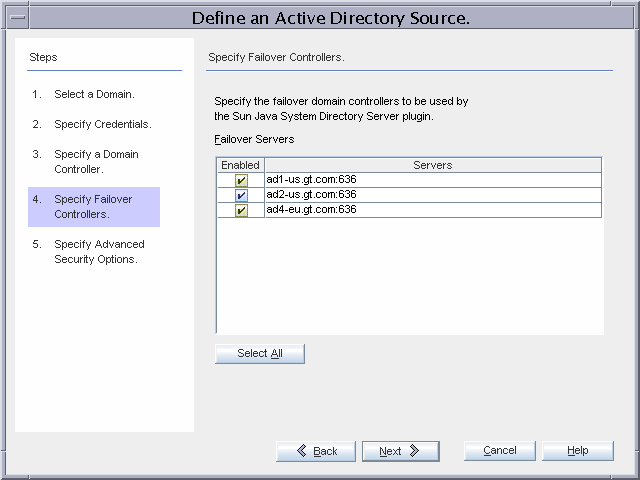
The remaining domain controllers are selected for failover during on-demand password synchronization.
bash-2.05# /opt/SUNWisw/bin/idsync printstat -q < omitted password\> -w <omitted password\> Exploring status of connectors, please wait... Connector ID: CNN100 Type: Sun Java(TM) System Directory Manages: dc=gt,dc=com (ldaps://master3-eu.gt.com:636) (ldaps://master4-eu.gt.com:636) State: READY Installed on: connectors-eu.gt.com
Connector ID: CNN101 Type: Active Directory Manages: gt.com (ldaps://ad1-us.gt.com:636) (ldaps://ad2-us.gt.com:636) (ldaps://ad4-eu.gt.com:636) (ldaps://ad3-eu.gt.com:636) State: READY Installed on: connectors-eu.gt.com Sun Java(TM) System Message Queue Status: Started Checking the System Manager status over the Sun Java(TM) System Message Queue. System Manager Status: Started Remaining Installation and Configuration Steps: 1. Install the Sun Directory Server Plugin at master ldaps://master3-eu.gt.com:636 by re-running the installer. 2. Install the Sun Directory Server Plugin at master ldaps://master4-eu.gt.com:636 by re-running the installer. 3. Install the Sun Directory Server Plugin on every other master and read-only replica that manage users under dc=gt,dc=com. 4. Run 'idsync resync' to establish links between existing Directory Server and Windows users. 5. Start synchronization using the console or the 'idsync startsync' command. SUCCESS
- © 2010, Oracle Corporation and/or its affiliates
