Directory Proxy Server Configured for BIND Replay
Directory Proxy Server forwards a BIND request from a client and the credentials of the client to an LDAP server. If the BIND is successful, all subsequent requests from the client to that LDAP server are processed with the authorization of the client.
In BIND replay, if the client makes a subsequent request that is forwarded to another LDAP server, the Directory Proxy Server uses the credentials already provided by the client to BIND to the other LDAP server before forwarding the request.
If a client request contains a proxy authorization control, Directory Proxy Server forwards the control to the backend server.
The following figure shows client identity and credentials being used for authorization by BIND replay.
Figure 19–1 Authentication in BIND Replay
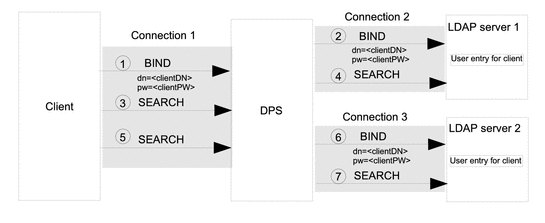
When Directory Proxy Server is initiated, it opens a connection to each LDAP server. When a client connects to Directory Proxy Server it makes requests in the following stages:
-
The client requests a BIND, and provides a DN and a password.
-
Directory Proxy Server authenticates the client to LDAP server 1 by using the client's credentials. An entry for the client exists in LDAP server 1 and the BIND request is granted.
-
The client issues a SEARCH request that is targeted at LDAP server 1.
-
Directory Proxy Server forwards the SEARCH request to LDAP server 1, reusing connection 2.
The SEARCH request is performed with the authorization of the client. If the client request contains a proxy authorization control, the request is processed with authorization of the user specified in the proxy authorization control.
If the client sends more SEARCH requests that are targeted at LDAP server 1, the Directory Proxy Server forwards the request without performing additional binds.
-
The client sends a SEARCH request targeted at LDAP server 2
-
The Directory Proxy Server authenticates the client to LDAP server 2 by using the client's credentials obtained in Step 1. An entry for the client exists in LDAP server 2 and the BIND request is granted.
-
The Directory Proxy Server forwards the SEARCH request to LDAP server 2, reusing connection 3.
If the client is not authenticated to Directory Proxy Server, the BIND request is forwarded as anonymous.
If the client identity is mapped onto another identity, Directory Proxy Server uses the mapped identity to bind to the LDAP server. All requests on that connection are processed with the authorization for the mapped identity. For information about user mapping, see Directory Proxy Server Configured to Forward Requests As an Alternate User.
When Directory Proxy Server is configured for BIND replay, authentication by SASL external bind cannot be used . In BIND replay, Directory Proxy Server authenticates the client to a backend LDAP server by using the client DN and password. In SASL external bind, no password is provided by the client. Furthermore, the password that is stored in the user entry cannot be read in clear text.
For performance reasons, you should configure Directory Proxy Server to use BIND replay only when the extra configuration required for proxy authorization is not feasible, or where proxy authorization is not supported. For information about proxy authorization, see Directory Proxy Server Configured for Proxy Authorization
- © 2010, Oracle Corporation and/or its affiliates
