Analyzing the Deployment Architecture
In this deployment example, messages are exchanged using the SOAP protocol to transfer security tokens between the communicating web service client and web service provider entities. The web service security providers can work independently of the OpenSSO Enterprise instance which is deployed as security token service. Web service security providers can secure the SOAP message by obtaining the security tokens from a vendor-neutral security token service.
The following are the major components in this deployment example:
-
OpenSSO Enterprise configured as a security token service
-
OpenSSO Enterprise configured as a web service security provider on a web service client
-
OpenSSO Enterprise configured as a web service security provider on a web service provider
-
Browser
The following figure illustrates the deployment architecture for using OpenSSO Enterprise to secure a web-based calendar service.
Figure 11–3 Deployment Architecture for Web Service Security Using Secure Token Service
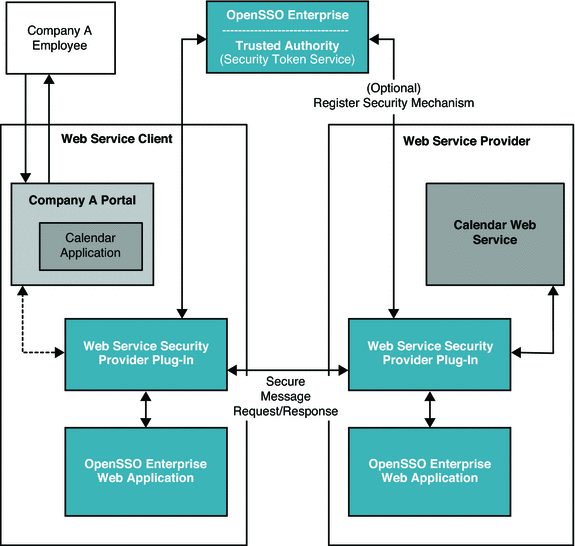
In this deployment example, a company employee has a user account in the Example Company identity system. The employee wants to access an internal calendar application to view a calendar service. The calendar application is part of the Example Company portal. All Example Company employees are required to authenticate themselves before accessing this internal portal. Additionally, the individual employee's credentials, such as role or group membership, must be validated before the employee can access the calendar application service.
The calendar application, on the employee's behalf, securely supplies the employee's credentials to the remote calendar web service.
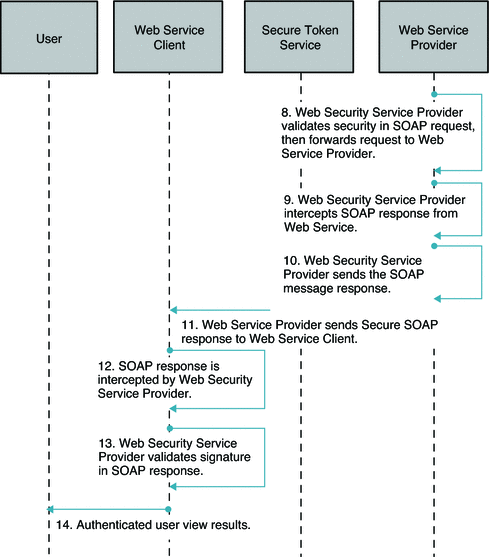
The following two figures illustrate the process flow for a Web Service Security using Secure token Service.
Figure 11–4 Process Flow for Web Service Security Using Secure Token Service (Continued on next page)
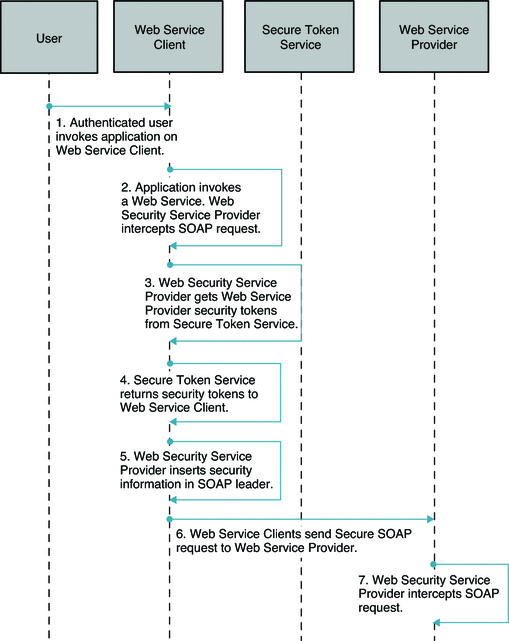
Figure 11–5 Process Flow for Web Service Security Using Secure Token Service (Continued)
- © 2010, Oracle Corporation and/or its affiliates
