Analyzing the Deployment Architecture
The following figure illustrates a basic deployment architecture that includes the OpenSSO Windows Desktop SSO Authentication module.
Figure 18–1 Deployment Architecture for OpenSSO Windows Desktop SSO Authentication Module
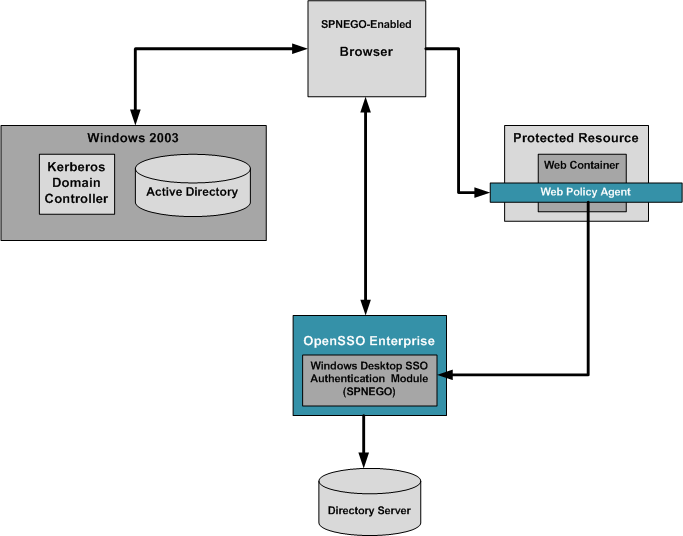
An OpenSSO Windows Desktop SSO Authentication deployment includes the following components:
- Windows 2003 Server with Domain Controller
-
The Windows Domain Controller contains configuration information for the Windows XP workstation and the workstation users. If the configured domain-user authenticates to the domain with proper user principal and credentials, the Windows Domain Controller generates a TGT Kerberos ticket and sends the ticket to the authenticated user account.
- Windows XP with SPNEGO-supported Browser
-
When the user accesses a resource that is protected with an authentication, an Authenticate:Negotiate response is sent to the browser. The browser obtains the Keberos Service ticket with the TGT that was generated in authentication time. This Service Kerberos ticket can be validated by the OpenSSO Enterprise server.
- Sun Directory Server 6.3
-
Contains user profile information.
- OpenSSO Windows Desktop SSO Authentication Module
-
The OpenSSO Windows Desktop SSO Authentication module is a server-side SPNEGO implementation that uses the Java GSS-API to process a Kerberos token sent by a SPNEGO-supported browser.
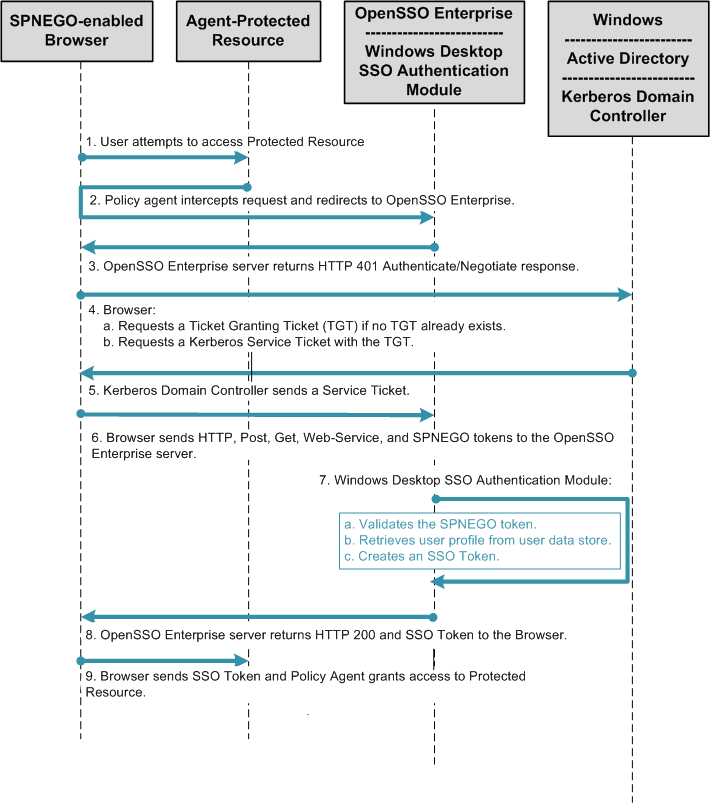
The following figure illustrates a typical process flow for Kerberos authentication using the Windows Desktop SSO Authentication module.
Figure 18–2 Process Flow for Windows Desktop SSO Authentication
- © 2010, Oracle Corporation and/or its affiliates
