Using OpenSSO Enterprise to Enable SiteMinder Federation in a Service Provider Environment
The following is a high-level overview of the sequence you must follow to enable SiteMinder with OpenSSO Enterprise in a Service Provider Environment:
-
Install and Configure SiteMinder in Service Provider Domain.
-
Configure OpenSSO Enterprise Identity Provider and Service Provider for SAML2 protocols.
 To Install OpenSSO Enterprise Instances
To Install OpenSSO Enterprise Instances
-
Install OpenSSO Enterprise in the Identity Provider Environment.
OpenSSO Enterprise is not the only supported access control software that can be used in the Identity Provider. But for optimum protocol interoperability, choosing OpenSSO Enterprise is a good practice. For detailed installation and configuration information, see the Sun OpenSSO Enterprise 8.0 Installation and Configuration Guide.
Ideally, Service Provider and Identity Provider are deployed in two different domains. At minimum, the cookie domains should be different to ensure cookie validation consistency.
-
Install OpenSSO Enterprise in the Service Provider Environment.
The OpenSSO Enterprise in the Service Provider environment is the SAML2 protocols initiator. The SiteMinder Web Agent can protect the enterprise application, but will still redirect to OpenSSO Enterprise for single sign-on purposes.
 To Install and Configure SiteMinder in the
Service Provider Domain
To Install and Configure SiteMinder in the
Service Provider Domain
Before You Begin
Before proceeding, be sure to read the general instructions in Installing SiteMinder and in Configuring SiteMinder After Installation. The following steps provide additional installation information specific only to this use case.
-
Install SiteMinder.
This is the domain that protects its enterprise applications using their SiteMinder agents. For the installation of SiteMinder and SiteMinder agents, see the CA SiteMinder product documentation.
-
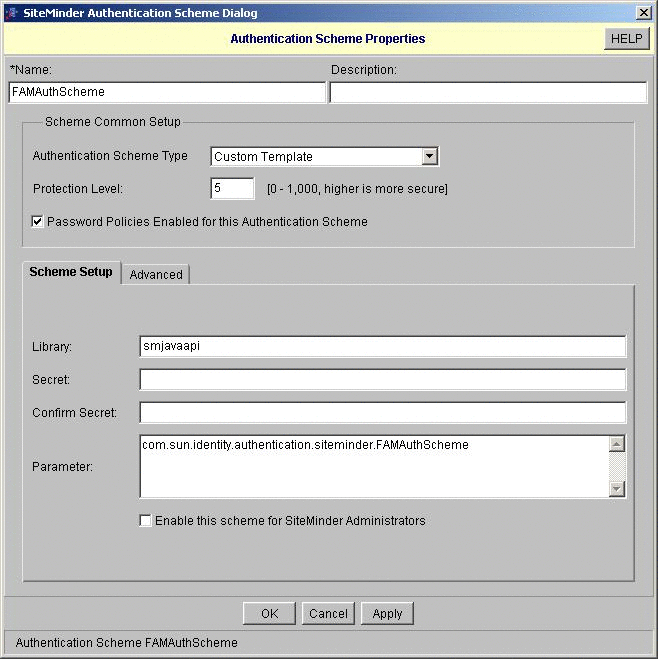
Create a custom authentication scheme.
-
Copy the compiled SiteMinder authentication scheme JAR files into the SiteMinder lib directory.
After you unzip the OpenSSO Enterprise binary, the SiteMinder custom authentication module is located under the directory unzip-directory/integrations/siteminder/. The README.html provides steps for building a custom authentication module. The OpenSSO Enterprise authentication module is a Java-based authentication scheme in SiteMinder. The README.html explains the steps for configuring the SiteMinder authentication scheme.
-
In the SiteMinder console, click Authentication Scheme, and then click “Create Custom Authentication Scheme.”
-
-
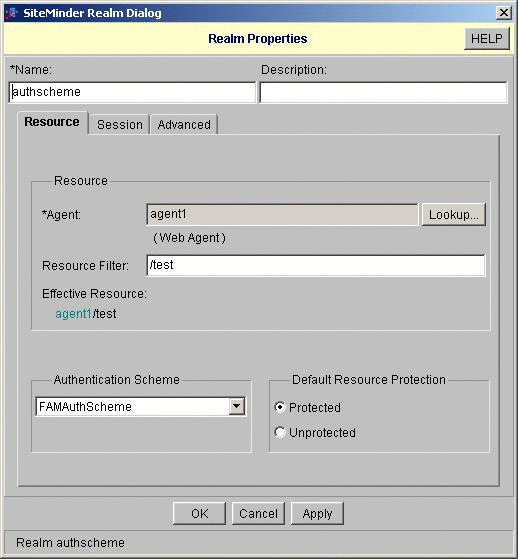
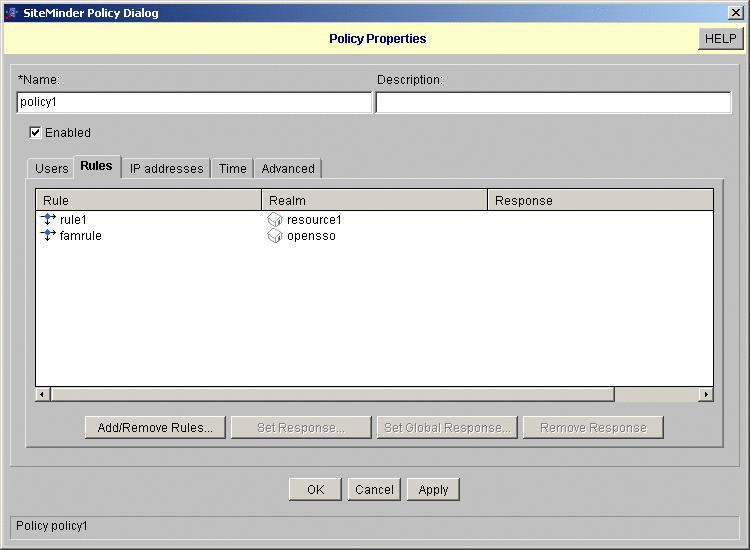
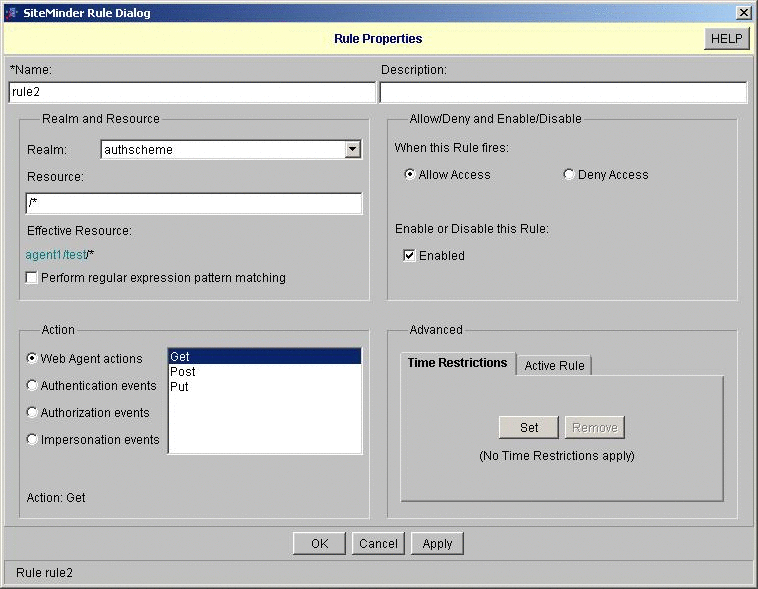
Configure a resource and a policy to trigger the OpenSSO Enterprise authentication module.
 To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
To Configure the OpenSSO Enterprise Identity
Provider and Service Provider for SAML2 protocols
For these configurations, you must have the following:
-
Identity Provider metadata
-
Identity Provider extended metadata
-
Service Provider metadata
-
Service Provider extended metadata
In Identity Provider, import Identity Provider metadata and Identity Provider extended metadata as hosted metadata. Import Service Provider metadata and Service Provider extended metadata as remote entity metadata.
Before You Begin
Before loading metadata, read through the following steps for the changes that you must make to the metadata. See the SAML2 samples for detailed instructions on how to setup SAML2, See the OpenSSO website for commands and syntax.
-
Edit the extended metadata XML element <EntityConfig>.
Change the hosted attribute from true to false.
-
Generate the metadata templates in both Identity Provider and Service Provider environments.
You can generate the metadata templates in one of two ways:
-
Use the browser-based URL http://host:port/opensso/famadm.jsp
-
Use the famadm command.
At the Identity Provider, where idp_meta_alias is /idp:
famadm create-metadata-templ -y idp_entity_id -u amadmin -f admin_password_file_name -m idp_standard_metadata -x idp_extended_metadata -i idp_meta_alias
At the Service Provider, where sp_meta_alias is /sp:
famadm create-metadata-templ -y sp_entity_id -u amadmin -f admin_password_file_name -msp_standard_metadata -x sp_extended_metadata -s sp_meta_alias
-
-
Customize the extended metadata at the Service Provider.
Add the Service Provider extended metadata as an attribute. This attribute is used by the SAML protocols to do any post-SSO Authentication process. In this example, the attribute is named spAdapter. In the architecture diagram, this is the SiteMinder Plug-In. The SiteMinder Plug-In uses the OpenSSO Enterprise session to authenticate against SiteMinder and to establish the SiteMinder session. The Service Provider metadata must have the following attributes:
<Attribute name="spAdapter"> <Value>com.sun.identity.saml2.plugins.SMAdapter</Value> </Attribute> <Attribute name="spAdapterEnv"> <Value>AgentIP=192.18.120.65</Value> <Value>AgentID=agent1</Value> <Value>PolicyServerIPAddress=192.18.120.65</Value> <Value>AuthorizationPort=44443</Value> <Value>AuthenticationPort=44442</Value> <Value>AccountingPort=44441</Value> <Value>AgentHostName=HostName.example.com</Value> <Value>ConnectionMinimum=2</Value> <Value>ConnectionMaximum=20</Value> <Value>ConnectionStep=2</Value> <Value>RequestTimeout=60</Value> <Value>FAMCookieName=iPlanetDirectoryPro</Value> <Value>SMCookieName=SMSESSION</Value> <Value>CookieDomain=.red.example.com</Value> <Value>Resource=/test/index.html</Value> <Value>SharedSecret={RC2}1r976MPOVq5JPpKzxFsXxIlut/YkgtUeklaceAoONCN mFJKDY+W8CkVpGY0to+x6apsIQAMPWLsgrm6NcdvyXv7K9Vf0vEALeWOy5BqLAhw fgKp4TbFRQspgv4w24ZOWsk57rwJ0N4kUJdM9lsLRu5hGKXArRJNpF80vS/U53TZ vM/qE5I3DcCOWKY4lJBZh</Value> </Attribute> -
Set the Service Provider extended metadata attribute transientUser to your anonymous user.
<Attribute name="transientUser"> <Value>anonymous</Value> </Attribute>Also verify that the OpenSSO Enterprise Service Provider is enabled for Anonymous authentication. See the OpenSSO Enterprise product documentation for more information.
-
Add the Circle of Trust through the OpenSSO Enterprise administration console.
Before loading, verify that the hosted attribute in the extended metadata has been changed to false.
-
Load the hosted metadata in both the Identity Provider and the Service Provider.
You can use the famadm command or the OpenSSO Enterprise administration console.
-
Exchange the Service Provider metadata with the Identity Provider.
-
Exchange the Identity Provider metadata with the Service Provider metadata.
-
Load the metadata.
-
After successful metadata exchange, verify through OpenSSO Enterprise administration console that metadata is properly configured.
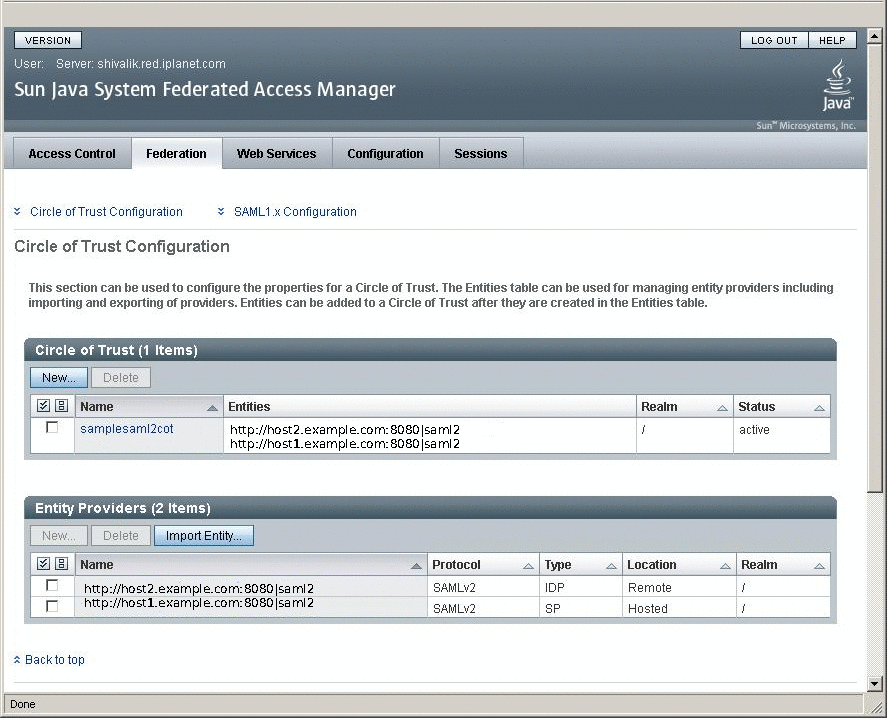
-
Verify that Single Sign-On works properly.
Access the enterprise application protected by SiteMinder Service Provider Agent. This should redirect to the OpenSSO Enterprise for authentication where the SAML2 SSO is initiated.
Sample Service Provider Interactions
This section provides sample output from the following interactions:
1. Invocation of SAML SSO request
http://HostName.example.com:8080/opensso/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= http://ide-13.red.example.com:8080/opensso&NameIDFormat=transient GET /opensso/saml2/jsp/spSSOInit.jsp?metaAlias=/sp&idpEntityID= http://ide-13.red.example.com:8080/opensso&NameIDFormat=transient HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=5fa8300161a1d5dc746ad8f9fb31 |
2. Redirection to Identity Provider
HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Location: http://ide-13.red.example.com:8080/opensso/SSORedirect/ metaAlias/idp?SAMLRequest=nVRfb9owEH%2Fvp4j8DnESaMECJAaahtRtDOge9 maSy7Dm2JnvQtm3rx0oYmqFVF7P57vfP3uEstK1mDa0Myv42wBSFB0qbVC0J2PWOCO sRIXCyApQUC7W06%2BPIu1yUTtLNrea3S3mY4bpYJvxLNsW5Rb60O89DNNhWQ4l7yV 8cJ8kUAzT7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9xPujwtMN7m2Qoej3Rf%2FjFo rmHpoyk9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe2BoNo4%2FX6%2BwoK5SCnuAK SU60k%2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp%2BUKZT5fV2Q7bEJxZfNZtmZO lKlzIlFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B1%2BnOdzuuACy5Ys8ndKNglWi HdhYHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX%2FuyVDwY5K0vXuUFFFp2xbBTl pUIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6Ta4BNjiz%2F53Ume3orULTx8a YQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2KttucjDaF8OsX%2B2rghx908Fik3 QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:57 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/SSORedirect/metaAlias/ idp?SAMLRequest=nVRfb9owEH%2Fvp4j8DnESaMECJAaahtRtDOge9maSy7Dm2Jn vQtm3rx0oYmqFVF7P57vfP3uEstK1mDa0Myv42wBSFB0qbVC0J2PWOCOsRIXCyApQ UC7W06%2BPIu1yUTtLNrea3S3mY4bpYJvxLNsW5Rb60O89DNNhWQ4l7yV8cJ8kUAz T7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9xPujwtMN7m2Qoej3Rf%2FjFormHpoyk 9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe2BoNo4%2FX6%2BwoK5SCnuAKSU60k% 2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp%2BUKZT5fV2Q7bEJxZfNZtmZOlKlzI lFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B1%2BnOdzuuACy5Ys8ndKNglWiHdh YHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX%2FuyVDwY5K0vXuUFFFp2xbBTlp UIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6Ta4BNjiz%2F53Ume3orULTx8 aYQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2KttucjDaF8OsX%2B2rghx908F ik3QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D GET /opensso/SSORedirect/metaAlias/idp?SAMLRequest=nVRfb9owEH%2Fvp 4j8DnESaMECJAaahtRtDOge9maSy7Dm2JnvQtm3rx0oYmqFVF7P57vfP3uEstK1mDa 0Myv42wBSFB0qbVC0J2PWOCOsRIXCyApQUC7W06%2BPIu1yUTtLNrea3S3mY4bpYJv xLNsW5Rb60O89DNNhWQ4l7yV8cJ8kUAzT7J5nKYt%2BgkNlzZj5MSxaIDawMEjSkC9 xPujwtMN7m2Qoej3Rf%2FjFormHpoyk9taOqBZxrAroJFnXQdFVtZYGqJvbSgz4gMe 2BoNo4%2FX6%2BwoK5SCnuAKSU60k%2Bps1iz5bl0NLfcxKqRECkqVEVHs4V5Ynjp% 2BUKZT5fV2Q7bEJxZfNZtmZOlKlzIlFU0RwAfrMGmwqcGtwe5XD0%2BrxTAZ3ai%2B 1%2BnOdzuuACy5Ys8ndKNglWiHdhYHX4cpXWGzyERCj%2BGLZaXUtvvnxi%2FnSapX% 2FuyVDwY5K0vXuUFFFp2xbBTlpUIHxCq%2BXYf%2BPxoMvFbiPqeoN0to%2BzxxI8s6 Ta4BNjiz%2F53Ume3orULTx8aYQHOgW0jNb1dIpDKmGQwjL5Gjl5eCZ9k6toLzF2Ktt ucjDaF8OsX%2B2rghx908Fik3QtraOTm6%2Fh%2Bes0btyeLHit9%2FL5AU%3D HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive |
3. Redirection to Login
HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; Path=/opensso Location: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso% 2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a 04108611ed9236032 Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:43:58 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/UI/Login?realm=/&goto= http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 GET /opensso/UI/Login?realm=/&goto=http%3A%2F%2Fide-13.red.example.com% 3A8080%2Fopensso%2FSSORedirect%2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfb e5e547929ff9a04108611ed9236032 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3 HTTP/1.x 200 OK X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Cache-Control: private Pragma: no-cache Expires: 0 X-DSAMEVersion: 8.0 (2007-November-29 01:17) AM_CLIENT_TYPE: genericHTML Set-Cookie: AMAuthCookie=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/ E=@AAJTSQACMDE=#; Domain=ide-13.red.example.com; Path=/ Set-Cookie: amlbcookie=01; Domain=ide-13.red.example.com; Path=/ Content-Type: text/html;charset=UTF-8 Transfer-Encoding: chunked Date: Mon, 04 Feb 2008 19:43:58 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/UI/Login?AMAuthCookie= AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU%2FE%3D%40AAJTSQACMDE%3D%23 POST /opensso/UI/Login?AMAuthCookie=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14v ekWbCSzRU%2FE%3D%40AAJTSQACMDE%3D%23 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm=/ &goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; AMAuthCookie=AQIC5wM2LY4 SfczOj691d2eiNkQCzmceO14vekWbCSzRU/E=@AAJTSQACMDE=#; amlbcookie=01 Content-Type: application/x-www-form-urlencoded Content-Length: 254 IDToken0=&IDToken1=amadmin&IDToken2=admin123&IDButton=Log+In&goto= aHR0cDovL2lkZS0xMy5yZWQuaXBsYW5ldC5jb206ODA4MC9vcGVuc3NvL1NTT1JlZGlyZWN0L2 1ldGFBbGlhcy9pZHA%2FUmVxSUQ9czI4YjMwMzNiZGZiZTVlNTQ3OTI5ZmY5YTA0MTA4NjExZW Q5MjM2MDMy&encoded=true&gx_charset=UTF-8 HTTP/1.x 302 Moved Temporarily X-Powered-By: Servlet/2.5 Server: Sun Java System Application Server 9.1 Cache-Control: private Pragma: no-cache Expires: 0 X-DSAMEVersion: 8.0 (2007-November-29 01:17) AM_CLIENT_TYPE: genericHTML X-AuthErrorCode: 0 Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/ E=@AAJTSQACMDE=#; Domain=ide-13.red.example.com; Path=/ Set-Cookie: AMAuthCookie=LOGOUT; Domain=ide-13.red.example.com; Expires=Thu, 01-Jan-1970 00:00:10 GMT; Path=/ Location: http://ide-13.red.example.com:8080/opensso/SSORedirect/ metaAlias/idp?ReqID=s28b3033bdfbe5e547929ff9a04108611ed9236032 Content-Type: text/html; charset=iso-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:05 GMT ---------------------------------------------------------- http://ide-13.red.example.com:8080/opensso/SSORedirect/metaAlias/ idp?ReqID=s28b3033bdfbe5e547929ff9a04108611ed9236032 GET /opensso/SSORedirect/metaAlias/idp?ReqID=s28b3033bdfbe5e54792 9ff9a04108611ed9236032 HTTP/1.1 Host: ide-13.red.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5f9f32d1896460b979b16ac14fb3; amlbcookie=01; iPlanetDirectoryPro=AQIC5wM2LY4SfczOj691d2eiNkQCzmceO14vekWbCSzRU/E=@AAJTSQACMDE=# HTTP/1.x 302 Moved Temporarily X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Location: http://HostName.example.com:8080/opensso/Consumer/metaAlias/ sp?SAMLart=AAQAAI4sWYpfoDDYJrHzsMnG%2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D Content-Type: text/html;charset=ISO-8859-1 Content-Length: 0 Date: Mon, 04 Feb 2008 19:44:05 GMT |
4. Redirection to Service Provider Assertion Consumer Service
http://HostName.example.com:8080/opensso/Consumer/metaAlias/sp?SAMLart= AAQAAI4sWYpfoDDYJrHzsMnG%2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D GET /opensso/Consumer/metaAlias/sp?SAMLart=AAQAAI4sWYpfoDDYJrHzsMnG% 2BjyNM94p5ejn49a%2BnZ0s3ylY7knQ6tkLMDE%3D HTTP/1.1 Host: HostName.example.com:8080 User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.2; en-US; rv:1.8.1.11) Gecko/20071127 Firefox/2.0.0.11 Accept: text/xml,application/xml,application/xhtml+xml,text/html;q= 0.9,text/plain;q=0.8,image/png,*/*;q=0.5 Accept-Language: en-us,en;q=0.5 Accept-Encoding: gzip,deflate Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7 Keep-Alive: 300 Connection: keep-alive Referer: http://ide-13.red.example.com:8080/opensso/UI/Login?realm= /&goto=http%3A%2F%2Fide-13.red.example.com%3A8080%2Fopensso%2FSSORedirect% 2FmetaAlias%2Fidp%3FReqID%3Ds28b3033bdfbe5e547929ff9a04108611ed9236032 Cookie: JSESSIONID=5fa8300161a1d5dc746ad8f9fb31 |
5. Check the SMSESSION Creation
HTTP/1.x 200 OK X-Powered-By: JService Provider/2.1 Server: Sun Java System Application Server 9.1 Set-Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcwFsRqmpq0e6m+iL+tjmqYhTDsKeABb4Eg= @AAJTSQACMDE=#; Domain=HostName.example.com; Path=/Set-Cookie: SMSESSION=jnNJdOyhPMa6A7FKeD0tCgHyq3yt8Tsvtmj6G4NjbP05ftAMggw+ hqolfo32FJ8iOnggFoZ19qXVAJyqf0DvMqhM+X0oUVw3P3R83sBAT4uKtUaib7OxyTSi8W5pBI+hLexr NczdpVWN9vCGDU97uBlJgpI8L9aeSNBgCSwo+gluvd1I72KGyFVgMLkIkfLMJhctpz+zKVt252yEf5Oh QZlGhzT/DzNqBc+142eek5VwMzxABLhwuEQ1jI1VAGOYAeyQpSmikgNfWphDSV3X36L3+ZQqHZmzCwjb 8QKSrBZnMdGuZKCYc9U6N8VJ1Ft5zwi/lotOU198apSU2bI5nQzWnGjpz60Dxc6Ycy83bjOqby/ZYHrl 3OLv2wJ0RtEN8FPYFjbHLGg=; Domain=.red.example.com Content-Type: text/html;charset=ISO-8859-1 Transfer-Encoding: chunked Date: Mon, 04 Feb 2008 19:45:04 GMT |
- © 2010, Oracle Corporation and/or its affiliates
