Federated Single Sign-On Use Cases
The SAML, ID-FF, and WS-Federation protocols provide cross-domain single sign-on among multiple trusted business entities. These protocols are also used in Identity Federation. Identity Federation involves an Identity Provider, also known as an authentication provider, and a Service Provider where the user authentication session at the Identity Provider is consumed. The following are common use cases in which Oracle Access Manager is enabled for federation protocols:
-
Enabling Oracle Access Manager for federation protocols in a Service Provider environment
-
Enabling Oracle Access Manager for federation protocols in an Identity Provider environment
The deployment examples in this chapter are built upon simple single sign-on integration. You must set up single sign-on before enabling federation. For more information about setting up simple single sign-on, see the Deployment Example: Single Sign-On. After setting up simple single sign-on, you can enable Oracle Access Manager for Federation in either the Identity Provider environment or in the Service Provider environment.
In the following examples, both Identity Provider and Service Provider are configured for transient federation. In most use cases, bulk federation is configured between the Identity Provider and Service Provider.
In transient federation, users exist only in the Identity Provider environment. The Service Provider honors the user authentication at the Identity Provider, and then creates an anonymous session. The anonymous session enables the Service Provider applications, protected by single sign-on, to be accessed. During SAML interactions, there is a possibility of exchanging user attribute information back to the Service Provider for authorization and other purposes. But that scenario is beyond the scope of this document.
Using OpenSSO Enterprise to Enable Oracle Federation in an Identity Provider Environment
In this example, Oracle Access Manager is the authentication provider in an Identity Provider environment and protects some of the intranet applications. OpenSSO Enterprise in this deployment resolves the single sign-on issues among enterprise applications in partner environments while Oracle Access Manager provides authentication.
Figure 3–3 Oracle Access Manager Federation in an Identity Provider Environment
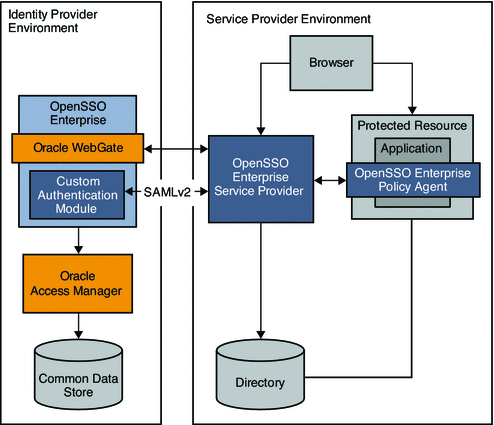
The following two figures illustrate the process flow among components in the Identity Provider environment and Service Provider environment.
Figure 3–4 Process flow for Oracle Access Manager Federation in an Identity Provider Environment
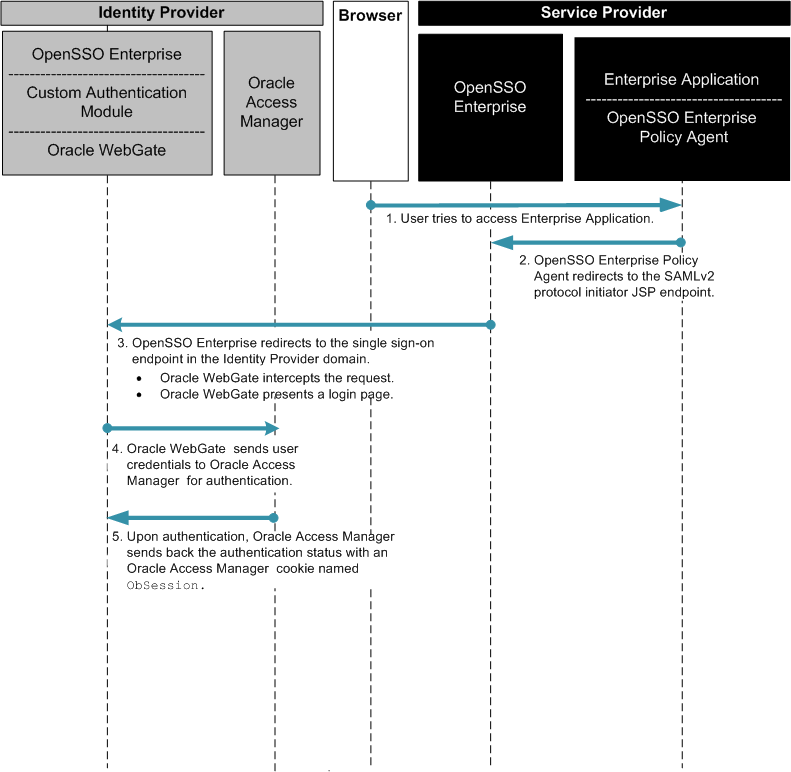
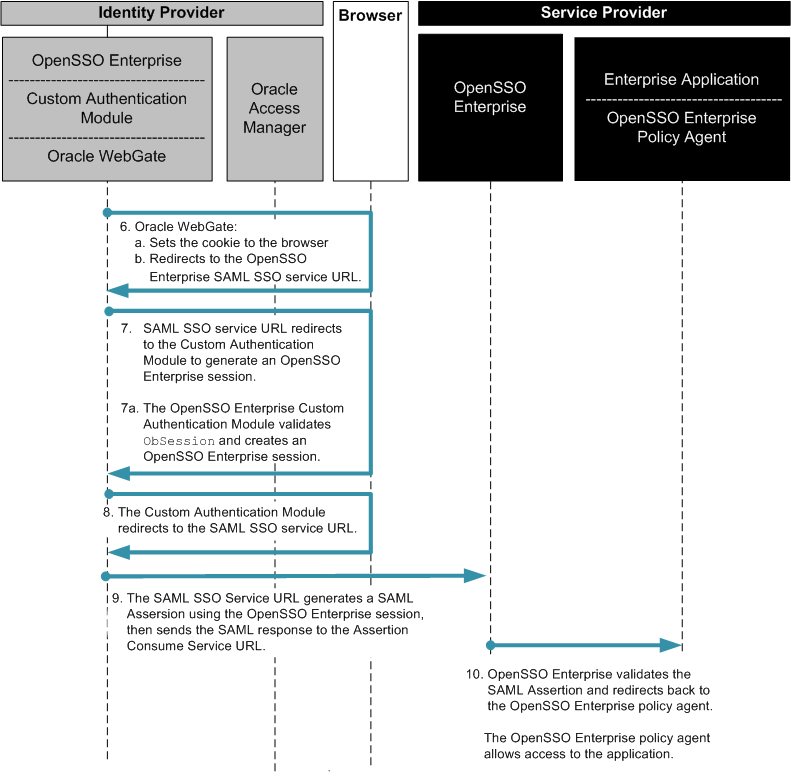
Figure 3–5 Process flow for Oracle Access Manager Federation in an Identity Provider Environment (continued)
Using OpenSSO Enterprise to Enable Oracle Federation in a Service Provider Environment
In this deployment, Oracle Access Manager is installed and configured in Service Provider Environment to protect legacy applications.
Figure 3–6 Oracle Access Manager Federation in a Service Provider Environment
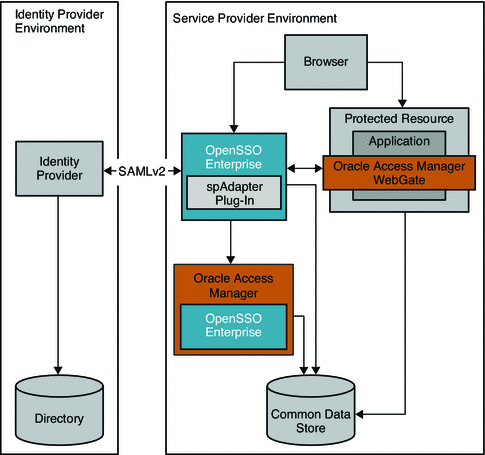
The following two figures illustrate the process flow among components in the Identity Provider environment and Service Provider environment.
Figure 3–7 Process Flow for Oracle Access Manager Federation in a Service Provider Environment
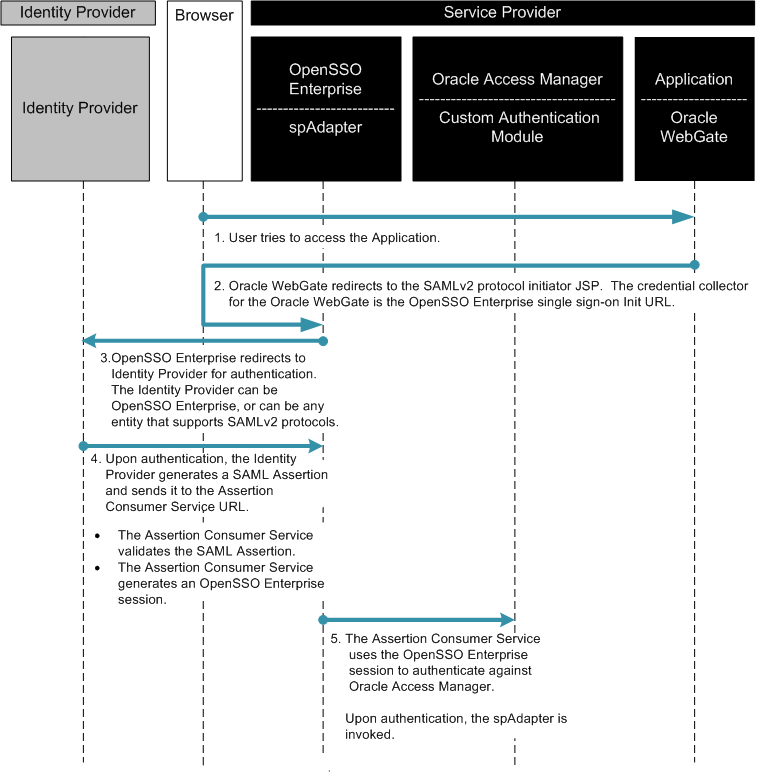
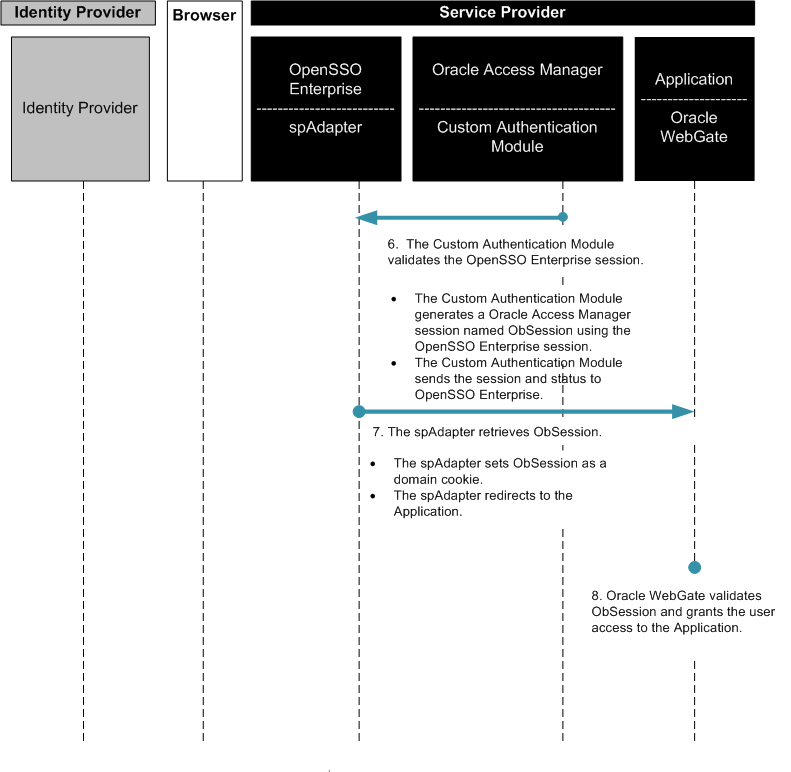
Figure 3–8 Process Flow for Oracle Access Manager Federation in a Service Provider Environment (continued)
- © 2010, Oracle Corporation and/or its affiliates
