Chapter 1 Components and Features
Deployment Example: Single Sign-On, Load Balancing and Failover Using Sun OpenSSO Enterprise 8.0 includes procedures for installing, deploying and configuring a number of host machines and applications. This chapter contains introductory information on the deployment example and includes the following sections:
1.1 Deployment Architecture and Components
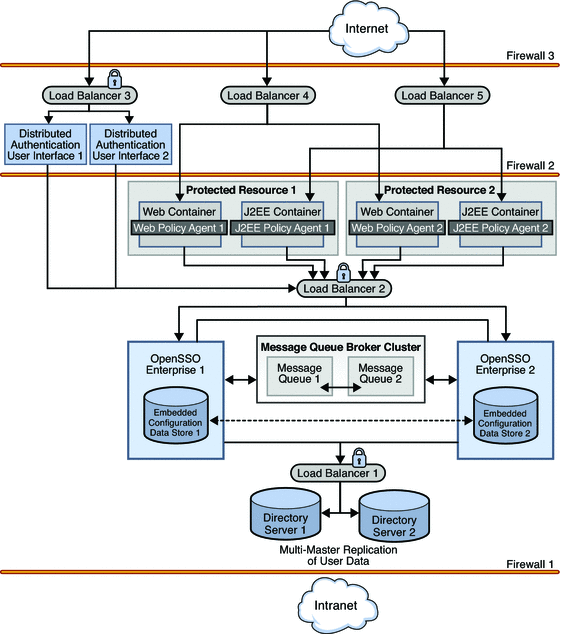
The following graphic illustrates the deployment architecture — where the components will be situated when the deployment is complete. A list of the components that comprise the architecture follows.
Figure 1–1 Deployment Architecture
Note –
Although referred to in the illustration, firewalls are not used in this deployment. For general information on integrating firewalls into this deployment, see 2.5 Firewall Rules.
The following list of components will be installed and configured in using the procedures documented in Part II, Building the Environment.
- Sun OpenSSO Enterprise
-
Two instances of OpenSSO Enterprise provide the core functionality. Each instance is configured with its own embedded configuration data store. Configuration data includes information about services, administrative users, realms, policies, and more. User data is accessed through a single load balancer deployed in front of two instances of Sun Java System Directory Server.
- Distributed Authentication User Interface
-
The Distributed Authentication User Interface is a component of OpenSSO Enterprise that provides a thin presentation layer for user authentication. During user authentication, the Distributed Authentication User Interface interacts with OpenSSO Enterprise to retrieve credentials from the user data store, thus protecting the OpenSSO Enterprise servers from direct user access.
Note –The Distributed Authentication User Interface does not directly interact with the user data store.
- Sun Java System Directory Server
-
Two instances of Directory Server provide storage for the OpenSSO Enterprise user data. User entries will be created for testing this deployment. Both instances of Directory Server are masters that engage in multi-master replication. Multi-master replication allows data to be synchronized in real time between two directories, providing high availability to the OpenSSO Enterprise layer.
Note –The command line is used for all Directory Server configurations in this guide.
- Sun OpenSSO Enterprise Policy Agents 3.0
-
Policy agents are used to restrict access to hosted content or applications. The policy agents intercept HTTP requests from external users and redirect the request to OpenSSO Enterprise for authentication. Web policy agents protect any resources under the doc root of the web container. J2EE policy agents protect a variety of hosted J2EE applications; in this deployment, agentsample is used. The agents communicate with the OpenSSO Enterprise instances through one of two configured load balancers.
- Protected Resource Host Machines
-
The protected resources host machines contain the content for which access is restricted. Towards this end, web servers, application servers and policy agents will be installed. Two load balancers are configured in front of the host machines to balance traffic passing through the policy agents.
- Sun Java System Message Queue
-
OpenSSO Enterprise uses two instances of Message Queue to form a cluster for distributing client connections and delivering messages. The Berkeley Database by Sleepycat Software, Inc. is the session store database. When an instance of OpenSSO Enterprise goes down and session failover is enabled, the user's session token can be retrieved from one of the Message Queues by the available instance of OpenSSO Enterprise. This ensures that the user remains continuously authenticated, allowing access to the protected resources without having to reauthenticate.
- Load Balancers
-
The load balancer hardware and software used for this deployment is BIG-IP® manufactured by F5 Networks. They are deployed as follows:
Distributed Authentication User Interface Load Balancer. This external-facing load balancer exposes the remote, web-based Distributed Authentication User Interface for user authentication and self-registration.
OpenSSO Enterprise Load Balancer. This internal-facing load balancer exposes the web-based OpenSSO Enterprise console to internal administrators. Alternatively, internal administrators can bypass this load balancer and log in directly.
J2EE Policy Agents Load Balancer. The load balancer in front of the J2EE policy agents installed on the Protected Resource machines provides round-robin load balancing and a single virtual server by balancing traffic passing through the agents.
Web Policy Agents Load Balancer. The load balancer in front of the web policy agents installed on the Protected Resource machines provides round-robin load balancing and a single virtual server by balancing traffic passing through the agents.
Directory Server Load Balancer. The load balancer in front of the Directory Server instances provide round-robin load balancing and a single virtual Directory Server host name for the instances of OpenSSO Enterprise. It detects individual Directory Server failures and recoveries, taking failed servers off the load balancer list.
Note –In this Deployment Example, we use BIG-IP and it's supported passive-cookie mechanism to address session persistence with the backend OpenSSO Enterprise servers. The intent is to enable persistence of requests to the backend servers depending upon the value of amlbcookie, the OpenSSO Enterprise cookie. Stickiness can then be maintained for all OpenSSO Enterprise related requests from browsers or agents. Different load balancers might support different mechanisms to achieve session persistence. It is the responsibility of the end users to determine and map this functionality to their own choice of load balancer.
1.2 Key Features of Deployment
-
All components (including installations of OpenSSO Enterprise and Directory Server, the Distributed Authentication User Interface, and policy agents) are redundant to achieve high availability.
-
All components use ZIP-based installation.
-
All components use load-balancing for session failover and high performance.
-
Each instance of OpenSSO Enterprise is installed with an embedded configuration data store.
-
Each instance of Directory Server contains am-users to serve as the user data store.
-
OpenSSO Enterprise instances are configured to run as non-root users.
-
The environment is configured for system failover capability, ensuring that when one instance of OpenSSO Enterprise goes down, requests are redirected to the second instance.
 Caution –
Caution – It is important to note that system failover, by itself, does not ensure OpenSSO Enterprise session failover which is configured separately.
-
The environment is configured for session failover capability. Session failover ensures that when the instance of OpenSSO Enterprise where the user's session was created goes down, the user's session token can still be retrieved from a backend session database. Thus, the user is continuously authenticated, and does not have to log into the system again unless the session is invalidated as a result of logout or session expiration.
-
Communications to the OpenSSO Enterprise load balancer, to the Distributed Authentication User Interface load balancer, and to the Directory Server load balancer are in Secure Sockets Layer (SSL).
-
Policy agents are configured with a unique agent profile to authenticate to OpenSSO Enterprise.
-
The Distributed Authentication User Interface uses a custom user profile to authenticate to OpenSSO Enterprise instead of the default amadmin or UrlAccessAgent.
1.3 Sequential Component Interactions
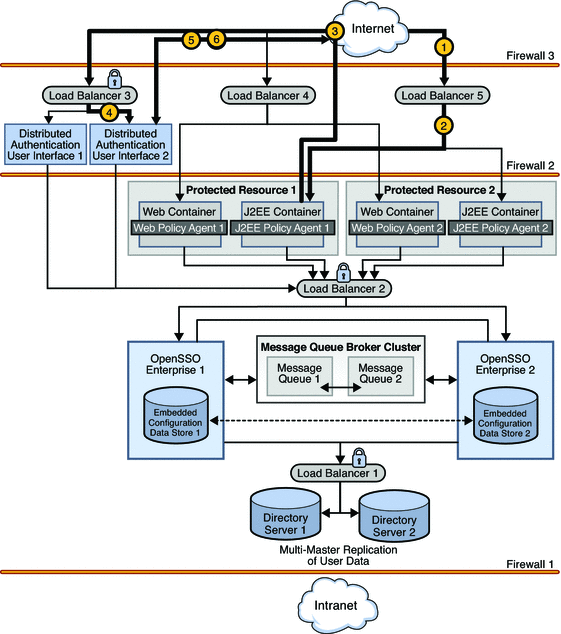
The following sequence describes the interactions between the various components in this deployment. The interactions are illustrated and the numbered steps correspond to the numbers in the diagrams.
-
A user attempts to access a J2EE application hosted on both Protected Resource 1 and Protected Resource 2.
-
Load Balancer 5 directs the user to Protected Resource 1 where J2EE Policy Agent 1 intercepts the request.
-
J2EE Policy Agent 1 checks for an OpenSSO Enterprise cookie (SSOToken). In this scenario, no cookie is found and the request is returned to the browser which redirects the request to Load Balancer 3, the load balancer for the instances of the Distributed Authentication User Interface.
-
Load Balancer 3 routes the user request to Distributed Authentication User Interface 2.
-
Distributed Authentication User Interface 2 displays a login page to the user.
-
The user enters credentials on the login page which are returned to Distributed Authentication User Interface 2.
-
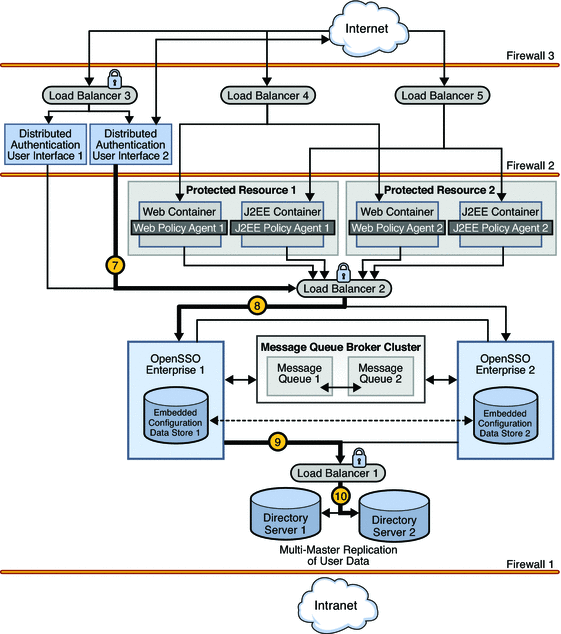
Distributed Authentication User Interface 2 passes the credentials to Load Balancer 2.
-
Load Balancer 2 routes the credentials to OpenSSO Enterprise 1.
-
OpenSSO Enterprise 1 sends a request for validation of the credentials to Load Balancer 1 in front of the Directory Server instances.
-
Load Balancer 1 routes the request to Directory Server 2.
-
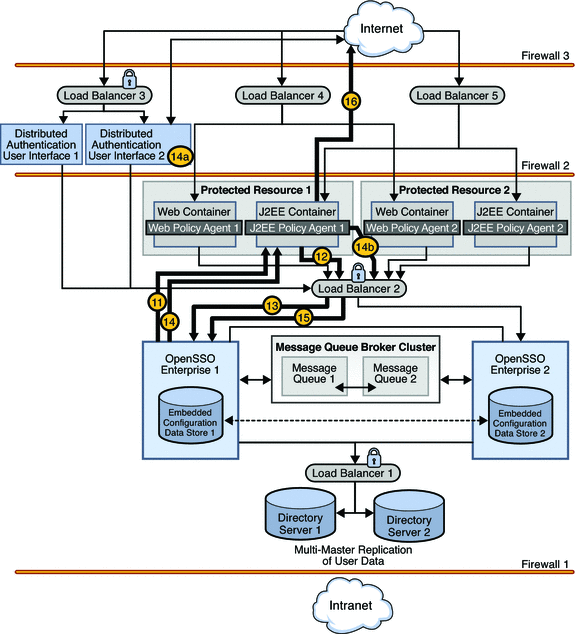
Authentication occurs using the Distributed Authentication User Interface. Assuming successful authentication, OpenSSO Enterprise Distributed Authentication User Interface 1 sends the response back to J2EE Policy Agent 1 which receives the request and checks again for the OpenSSO Enterprise cookie.
-
When a cookie is found, J2EE Policy Agent 1 sends a session validation request to the OpenSSO Enterprise Load Balancer 2.
-
The OpenSSO Enterprise Load Balancer 2 forwards the request to OpenSSO Enterprise 1 where the session originated. Cookie-based persistency enables proper routing.
-
OpenSSO Enterprise 1 sends a response back to J2EE Policy Agent 1.
-
If the session is not valid, J2EE Policy Agent 1 redirects the user back to Distributed Authentication User Interface 2.
-
If the session is valid, J2EE Policy Agent 1 receives the response and sends a request for policy evaluation to Load Balancer 2.
-
-
As the session is valid, the request is directed to OpenSSO Enterprise 1 to conduct the policy evaluation.
-
Based on the outcome of the policy evaluation, J2EE Policy Agent 1 allows or denies access to the resource. In this scenario, the user is allowed access.
- © 2010, Oracle Corporation and/or its affiliates
