Chapter 25 Mobile IP Files and Commands (Reference)
This chapter describes the components that are provided with the Solaris implementation of Mobile IP. To use Mobile IP, you must first configure the Mobile IP configuration file by using the parameters and commands that are described in the following sections.
This chapter contains the following information:
Overview of the Solaris Mobile IP Implementation
The mobility agent software incorporates home agent and foreign agent functionality. The Solaris Mobile IP software does not provide a client mobile node. Only the agent functionality is provided. Each network with mobility support should have at least one static (non-mobile) host running this software. The following RFC functions are supported in the Solaris implementation of Mobile IP:
- RFC 1918
-
Address Allocation for Private Internets
- RFC 2002
-
(Agent only) IP Mobility Support
- RFC 2003
-
IP Encapsulation Within IP
- RFC 2794
-
Mobile IP Network Access Identifier Extension for IPv4
- RFC 3012
-
Mobile IP Challenge/Response Extensions
- RFC 3024
-
Reverse Tunneling for Mobile IP
The base Mobile IP protocol (RFC 2002) does not address the problem of scalable key distribution and treats key distribution as an orthogonal issue. The Solaris Mobile IP software utilizes only manually configured keys, specified in a configuration file.
The functionality in the following IETF drafts is also supported in the Solaris implementation of Mobile IP:
-
draft-ietf-mobileip-rfc2002–bis-03.txt – IP Mobility Support for IPv4, revised
-
draft-ietf-mobileip-vendor-ext-09.txt – Mobile IP Vendor/Organization-Specific Extensions
The following RFC functions are not supported in the Solaris implementation of Mobile IP:
- RFC 1700
-
General Routing Encapsulation
- RFC 1701
-
General Routing Encapsulation
- RFC 2004
-
Minimal Encapsulation Within IP
The following functions are not supported in the Solaris implementation of Mobile IP:
-
The forwarding of multicast or broadcast traffic by the home agent to the foreign agent for a mobile node that is visiting a foreign network
-
The routing of broadcast and multicast datagrams through reverse tunnels
-
Private care-of addresses or private home agent addresses
See mipagent(1M) man page for additional information.
Mobile IP Configuration File
The mipagent command reads configuration information from the /etc/inet/mipagent.conf configuration file at startup. Mobile IP uses the /etc/inet/mipagent.conf configuration file to initialize the Mobile IP mobility agent. When configured and deployed, the mobility agent issues periodic router advertisements and responds to router discovery solicitation messages as well as Mobile IP registration messages.
See the mipagent.conf(4) man page for a description of file attributes and the mipagent(1M) man page for a description of its usage.
Configuration File Format
The Mobile IP configuration file consists of sections. Each section has a unique name and is enclosed in square brackets. Each section contains one or more labels. You assign values to the labels by using the following format:
[Section_name]
Label-name = Value-assigned
|
Configuration File Sections and Labels describes the section names, labels, and possible values.
Sample Configuration Files
The default Solaris installation provides the following sample configuration files in the /etc/inet directory:
-
mipagent.conf-sample – Contains a sample configuration for a Mobile IP agent that provides both foreign and home agent functionality.
-
mipagent.conf.fa-sample – Contains a sample configuration for a Mobile IP agent that provides only foreign agent functionality.
-
mipagent.conf.ha-sample – Contains a sample configuration for a Mobile IP agent that provides only home agent functionality.
These sample configuration files contain mobile node address and security settings. Before you can implement Mobile IP, you must create a configuration file with the name mipagent.conf and place it in the /etc/inet directory. This file contains the configuration settings that satisfy your Mobile IP implementation requirements. You can also choose one of the sample configuration files, modify it with your addresses and security settings, and copy it to /etc/inet/mipagent.conf.
How to Create the Mobile IP Configuration File shows the procedures to perform.
mipagent.conf-sample File
The following listing shows the sections, labels, and values that are contained in the mipagent.conf-sample file. Configuration File Sections and Labels describes the syntax, sections, labels, and values.
[General]
Version = 1.0 # version number for the configuration file. (required)
[Advertisements hme0]
HomeAgent = yes
ForeignAgent = yes
PrefixFlags = yes
AdvertiseOnBcast = yes
RegLifetime = 200
AdvLifetime = 200
AdvFrequency = 5
ReverseTunnel = no
ReverseTunnelRequired = no
[GlobalSecurityParameters]
MaxClockSkew = 300
HA-FAauth = yes
MN-FAauth = yes
Challenge = no
KeyDistribution = files
[Pool 1]
BaseAddress = 10.68.30.7
Size = 4
[SPI 257]
ReplayMethod = none
Key = 11111111111111111111111111111111
[SPI 258]
ReplayMethod = none
Key = 15111111111111111111111111111111
[Address 10.1.1.1]
Type = node
SPI = 258
[Address mobilenode@sun.com]
Type = node
SPI = 257
Pool = 1
[Address Node-Default]
Type = node
SPI = 258
Pool = 1
[Address 10.68.30.36]
Type = agent
SPI = 257
[Address 10.68.30.36]
Type = agent
SPI = 257
IPsecRequest = apply {auth_algs md5 sa shared}
IPsecReply = permit {auth_algs md5}
IPsecTunnel = apply {encr_algs 3des sa shared}
|
Example–mipagent.conf.fa-sample File
The following listing shows the sections, labels, and values that are contained in the mipagent.conf.fa-sample file. Configuration File Sections and Labels describes the syntax, sections, labels, and values. The mipagent.conf.fa-sample file shows a configuration that provides only foreign agent functionality. This sample file does not contain a Pool section, because pools are used only by a home agent. Otherwise, this file is the same as the mipagent.conf-sample file.
[General]
Version = 1.0 # version number for the configuration file. (required)
[Advertisements hme0]
HomeAgent = no
ForeignAgent = yes
PrefixFlags = yes
AdvertiseOnBcast = yes
RegLifetime = 200
AdvLifetime = 200
AdvFrequency = 5
ReverseTunnel = yes
ReverseTunnelRequired = no
[GlobalSecurityParameters]
MaxClockSkew = 300
HA-FAauth = yes
MN-FAauth = yes
Challenge = no
KeyDistribution = files
[SPI 257]
ReplayMethod = none
Key = 11111111111111111111111111111111
[SPI 258]
ReplayMethod = none
Key = 15111111111111111111111111111111
[Address 10.1.1.1]
Type = node
SPI = 258
[Address 10.68.30.36]
Type = agent
SPI = 257
[Address 10.68.30.36]
Type = agent
SPI = 257
IPsecRequest = apply {auth_algs md5 sa shared}
IPsecReply = permit {auth_algs md5}
IPsecTunnel = apply {encr_algs 3des sa shared}
|
Example–mipagent.conf.ha-sample File
The following listing shows the sections, labels, and values that are contained in the mipagent.conf.ha-sample file. Configuration File Sections and Labels describes the syntax, sections, labels, and values. The mipagent.conf.ha-sample file shows a configuration that provides only home agent functionality. Otherwise, this file is the same as the mipagent.conf-sample file.
[General]
Version = 1.0 # version number for the configuration file. (required)
[Advertisements hme0]
HomeAgent = yes
ForeignAgent = no
PrefixFlags = yes
AdvertiseOnBcast = yes
RegLifetime = 200
AdvLifetime = 200
AdvFrequency = 5
ReverseTunnel = yes
ReverseTunnelRequired = no
[GlobalSecurityParameters]
MaxClockSkew = 300
HA-FAauth = yes
MN-FAauth = yes
Challenge = no
KeyDistribution = files
[Pool 1]
BaseAddress = 10.68.30.7
Size = 4
[SPI 257]
ReplayMethod = none
Key = 11111111111111111111111111111111
[SPI 258]
ReplayMethod = none
Key = 15111111111111111111111111111111
[Address 10.1.1.1]
Type = node
SPI = 258
[Address mobilenode@sun.com]
Type = node
SPI = 257
Pool = 1
[Address Node-Default]
Type = node
SPI = 258
Pool = 1
[Address 10.68.30.36]
Type = agent
SPI = 257
IPsecRequest = apply {auth_algs md5 sa shared}
IPsecReply = permit {auth_algs md5}
IPsecTunnel = apply {encr_algs 3des sa shared}
|
Configuration File Sections and Labels
The Mobile IP configuration file contains the following sections:
-
General (Required)
-
Advertisements (Required)
-
GlobalSecurityParameters (Optional)
-
Pool (Optional)
-
SPI (Optional)
-
Address (Optional)
The General and GlobalSecurityParameters sections contain information relevant to the operation of the Mobile IP agent and can appear only once in the configuration file.
General Section
The General section contains only one label: the version number of the configuration file. The General section has the following syntax:
[General]
Version = 1.0
|
Advertisements Section
The Advertisements section contains the HomeAgent and ForeignAgent labels, as well as other labels. You must include a different Advertisements section for each interface on the local host that provides Mobile IP services. The Advertisements section has the following syntax:
[Advertisements Interface-name]
HomeAgent = <yes/no>
ForeignAgent = <yes/no>
.
.
|
Typically, your system has a single interface (le0, hme0, and so on) and supports both home agent and foreign agent operations. If this is the situation for the example hme0, then the yes value is assigned to both the HomeAgent and ForeignAgent labels as follows:
[Advertisements hme0]
HomeAgent = yes
ForeignAgent = yes
.
.
|
For advertisement over dynamic interfaces, use '*' for the device id part. For example, Interface-name ppp* actually implies all ppp interfaces that are configured after mipagent has been started. All the attributes in the advertisement section of a dynamic interface type remain the same.
The following table describes the labels and values that you can use in the Advertisements section.
Table 25–1 Advertisements Section Labels and Values
GlobalSecurityParameters Section
The GlobalSecurityParameters section contains the maxClockSkew, HA-FAauth, MN-FAauth, Challenge, and KeyDistribution labels. This section defines the security parameters. The GlobalSecurityParameters section has the following syntax:
[GlobalSecurityParameters]
MaxClockSkew = n
HA-FAauth = <yes/no>
MN-FAauth = <yes/no>
Challenge = <yes/no>
KeyDistribution = files
|
The Mobile IP protocol provides message replay protection by allowing timestamps to be present in the messages. If the clocks differ, the home agent returns an error to the mobile node with the current time and the mobile node can re-register by using the current time. You use the MaxClockSkew label to configure the maximum number of seconds that differ between the home agent and the mobile node's clocks. The default value is 300 seconds.
The HA-FAauth and MN-FAauth labels enable or disable the requirement for home-foreign and mobile-foreign authentication, respectively. The default value is disabled. You use the challenge label so that the foreign agent issues challenges to the mobile node in its advertisements. The label is used for replay protection. The default value is disabled here, also.
The following table describes the labels and values that you can use in the GlobalSecurityParameters section.
Table 25–2 GlobalSecurityParameters Section Labels and Values
Pool Section
Mobile nodes can be assigned dynamic addresses by the home agent. The dynamic address assignment is done within the mipagent independently of DHCP. You can create an address pool that can be used by mobile nodes by requesting a home address. Address pools are configured through the Pool section in the configuration file.
The Pool section contains the BaseAddress and Size labels. The Pool section has the following syntax:
[Pool Pool-identifier]
BaseAddress = IP-address
Size = size
|
Note –
If you use a Pool identifier, then it must also exist in the mobile node's Address section.
You use the Pool section to define address pools that can be assigned to the mobile nodes. You use the BaseAddress label to set the first IP address in the pool. You use the Size to specify the number of addresses available in the pool.
For example, if IP Addresses 192.168.1.1 through 192.168.1.100 are reserved in pool 10, the Pool section has the following entry:
[Pool 10]
BaseAddress = 192.168.1.1
Size = 100
|
Note –
Address ranges should not encompass the broadcast address. For example, you should not assign BaseAddress = 192.168.1.200 and Size = 60, because this range encompasses the broadcast address 192.168.1.255.
The following table describes the labels and values that are used in the Pool section.
Table 25–3 Pool Section Labels and Values|
Label |
Value |
Description |
|---|---|---|
|
BaseAddress |
n.n.n.n |
First address in the address pool |
|
Size |
n |
Number of addresses in the pool |
SPI Section
Because the Mobile IP protocol requires message authentication, you must identify the security context by using a Security Parameter Index (SPI). You define the security context in the SPI section. You must include a different SPI section for each security context that is defined. A numerical ID identifies the security context. The Mobile IP protocol reserves the first 256 SPIs. Therefore, you should use only SPI values greater than 256. The SPI section contains security-related information, such as shared secrets and replay protection.
The SPI section also contains the ReplayMethod and Key labels. This section defines the security contexts. The SPI section has the following syntax:
[SPI SPI-identifier]
ReplayMethod = <none/timestamps>
Key = key
|
Two communicating peers must share the same SPI identifier. You must configure them with the same key and replay method. You specify the key as a string of hex digits. The maximum length is 16 bytes. For example, if the key is 16 bytes long, and contains the hex values 0 through f, the key string might resemble the following:
Key = 0102030405060708090a0b0c0d0e0f10 |
Keys must have an even number of digits, corresponding to the two digits per byte representation.
The following table describes the labels and values that you can use in the SPI section.
Table 25–4 SPI Section Labels and Values|
Label |
Value |
Description |
|---|---|---|
|
ReplayMethod |
none or timestamps |
Specifies the type of replay authentication used for the SPI |
|
Key |
x |
Authentication key in hexadecimal |
Address Section
The Solaris implementation of Mobile IP enables you to configure mobile nodes in one of three methods. Each method is configured in the Address section. The first method follows the traditional Mobile IP protocol, and requires that each mobile node have a home address. The second method enables a mobile node to be identified through its Network Access Identifier (NAI). The last method enables you to configure a default mobile node, which can be used by any mobile node that has the proper SPI value and related keying material.
Mobile Node
The Address section for a mobile node contains the Type and SPI labels that define the address type and SPI identifier. The Address section has the following syntax:
[Address address]
Type = node
SPI = SPI-identifier
|
You must include an Address section in a home agent's configuration file for each mobile node that is supported.
If Mobile IP message authentication is required between the foreign and home agent, you must include an Address section for each peer with which an agent needs to communicate.
The SPI value that you configure must represent an SPI section that is present in the configuration file.
You can also configure private addresses for a mobile node.
The following table describes the labels and values that you can use in the Address section for a mobile node.
Table 25–5 Address Section Labels and Values—Mobile Node|
Label |
Value |
Description |
|---|---|---|
|
Type |
node |
Specifies that the entry is for a mobile node |
|
SPI |
n |
Specifies the SPI value for the associated entry |
Mobility Agent
The Address section for a mobility agent contains the Type and SPI labels that define the address type and SPI identifier. This section also contains IPsec request, reply, and tunnel labels. The Address section has the following syntax:
[Address address]
Type = agent
SPI = SPI-identifier
IPsecRequest = action {properties} [: action {properties}]
IPsecReply = action {properties} [: action {properties}]
IPsecTunnel = action {properties} [: action {properties}]
|
You must include an Address section in a home agent's configuration file for each mobility agent that is supported.
If Mobile IP message authentication is required between the foreign and home agent, you must include an Address section for each peer with which an agent needs to communicate.
The SPI value that you configure must represent an SPI section that is present in the configuration file.
The following table describes the labels and values that you can use in the Address section for a mobility agent.
Table 25–6 Address Section Labels and Values—Mobility Agent|
Label |
Value |
Description |
|---|---|---|
|
Type |
agent |
Specifies that the entry is for a mobility agent |
|
SPI |
n |
Specifies the SPI value for the associated entry |
|
IPsecRequest |
apply or permit (see following note) |
IPsec properties to invoke for registration requests to and from this mobility agent peer |
|
IPsecReply |
apply or permit (see following note) |
IPsec properties to invoke for registration replies to and from this mobility agent peer |
|
IPsecTunnel |
apply or permit (see following note) |
IPsec properties to invoke for tunnel traffic to and from this mobility agent peer |
Note –
The apply values correspond to outbound datagrams. The permit values correspond to inbound datagrams. Therefore, IPsecRequest apply values and IPsecReply permit values are used by the foreign agent to send and receive registration datagrams. The IPsecRequest permit values and the IPsecReply apply values are used by the home agent to receive and send registration datagrams.
Mobile Node Identified by its NAI
The Address section for a mobile node that is identified by its NAI contains the Type, SPI, and Pool labels. The NAI parameter enables you to identify mobile nodes through their NAI. The Address section, using the NAI parameter, has the following syntax:
[Address NAI]
Type = Node
SPI = SPI-identifier
Pool = Pool-identifier
|
In order to use pools, you identify mobile nodes through their NAI. The Address section permits you to configure an NAI, as opposed to a home address. An NAI uses the format user@domain format. You use the Pool label to specify which address pool to use in order to allocate the home address to the mobile node.
The following table describes the labels and values that you can use in the Address section for a mobile node that is identified by its NAI.
Table 25–7 Address Section Labels and Values—Mobile Node Identified by Its NAI|
Label |
Value |
Description |
|---|---|---|
|
Type |
node |
Specifies entry for a mobile node |
|
SPI |
n |
Specifies SPI value for the associated entry |
|
Pool |
n |
Allocates the pool from which an address is assigned to a mobile node |
You must have corresponding SPI and Pool sections for the SPI and Pool labels that are defined in an Address section with a mobile node that is identified by its NAI, as shown in the following illustration.
Figure 25–1 Corresponding SPI and Pool Sections for Address Section With Mobile Node Identified by Its NAI
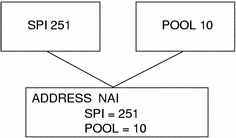
Default Mobile Node
The Address section for a default mobile node contains the Type, SPI, and Pool labels. The Node-Default parameter enables you to permit all mobile nodes to get service if they have the correct SPI (defined in this section). The Address section, using the Node-Default parameter, has the following syntax:
[Address Node-Default]
Type = Node
SPI = SPI-identifier
Pool = Pool-identifier
|
The Node-Default enables you to reduce the size of the configuration file. Otherwise, each mobile node requires its own section. However, the Node-Default does pose a security risk. If a mobile node is no longer trusted for any reason, you need to update the security information on all trusted mobile nodes. This task can be very tedious. However, you can use the Node-Default in networks that consider security risks unimportant.
The following table describes the labels and values that you can use in the Address section for a default mobile node.
Table 25–8 Address Section Labels and Values—Default Mobile Node|
Label |
Value |
Description |
|---|---|---|
|
Type |
node |
Specifies entry for a mobile node |
|
SPI |
n |
Specifies SPI value for the associated entry |
|
Pool |
n |
Allocates the pool from which an address is assigned to a mobile node |
You must have corresponding SPI and Pool sections for the SPI and Pool labels that are defined in the Address section with a default mobile node, as shown in the following illustration.
Figure 25–2 Corresponding SPI and Pool Sections for Address Section With a Default Mobile Node
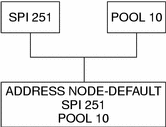
Configuring the Mobility IP Agent
You can use the mipagentconfig command to configure the mobility agent. This command enables you to create or modify any parameter in the /etc/inet/mipagent.conf configuration file. Specifically, you can change any setting, and add or delete mobility clients, pools, and SPIs. The mipagentconfig command has the following syntax:
# mipagentconfig <command> <parameter> <value> |
The following table describes the commands that you can use with mipagentconfig to create or modify parameters in the /etc/inet/mipagent.conf configuration file.
Table 25–9 mipagentconfig Commands|
Command |
Description |
|---|---|
|
add |
Used to add advertisement parameters, security parameters, SPIs, and addresses to the configuration file |
|
change |
Used to change advertisement parameters, security parameters, SPIs, and addresses in the configuration file |
|
delete |
Used to delete advertisement parameters, security parameters, SPIs, and addresses from the configuration file |
|
get |
Used to display current settings in the configuration file |
See the mipagentconfig(1M) man page for a description of command parameters and acceptable values. Modifying the Mobile IP Configuration File provides procedures that use the mipagentconfig command.
Mobile IP Mobility Agent Status
You can use the mipagentstat command to display a foreign agent's visitors list and a home agent's binding table. You can also display the security associations with an agent's mobility agent peers. To display the foreign agent visitor list, you use the mipagentstat command's -f option. To display the home agent binding table, you use the mipagentstat command's -h option. To display the security associations with an agent's mobility agent peers, you use the mipagentstat command's -p option. The following examples show typical output when using the mipagentstat command with these options.
Example 25–1 Foreign Agent Visitor List
Mobile Node Home Agent Time (s) Time (s) Flags
Granted Remaining
--------------- -------------- ------------ --------- -----
foobar.xyz.com ha1.xyz.com 600 125 .....T.
10.1.5.23 10.1.5.1 1000 10 .....T.
|
Example 25–2 Home Agent Binding Table
Mobile Node Home Agent Time (s) Time (s) Flags
Granted Remaining
--------------- -------------- ------------ --------- -----
foobar.xyz.com fa1.tuv.com 600 125 .....T.
10.1.5.23 123.2.5.12 1000 10 .....T.
|
Example 25–3 Mobility Agent Peer Security Association Table
Foreign ..... Security Association(s)..... Agent Requests Replies FTunnel RTunnel ---------------------- -------- -------- -------- -------- forn-agent.eng.sun.com AH AH ESP ESP Home ..... Security Association(s) ..... Agent Requests Replies FTunnel RTunnel ---------------------- -------- -------- -------- -------- home-agent.eng.sun.com AH AH ESP ESP ha1.xyz.com AH,ESP AH AH,ESP AH,ESP |
See mipagentstat(1M) command for more information about the command's options. Displaying Mobility Agent Status provides procedures that use the mipagentstat command.
Mobile IP State Information
On shutdown, the mipagent daemon stores internal state information in /var/inet/mipagent_state. This occurs only when the mipagent provides services as a home agent. This state information includes the list of mobile nodes that are being supported as a home agent, their current care-of addresses, and remaining registration lifetimes. This state information also includes the security association configuration with mobility agent peers. If the mipagent program is terminated (for maintenance) and restarted, mipagent_state is used to re-create as much of the mobility agent's internal state as possible in an effort to minimize service disruption for mobile nodes that might be visiting other networks. If mipagent_state exists, it is read immediately after mipagent.conf every time mipagent is started or restarted.
netstat Extensions for Mobile IP
Mobile IP extensions have been added to the netstat(1M) command to identify Mobile IP forwarding routes. Specifically, you can use the netstat(1M) command to display a new routing table that is called “Source-Specific.” See the netstat(1M) man page for more information.
The following example shows the output of netstat when you use the -nr flags.
Example 25–4 Output From netstat Command
Routing Table: IPv4 Source-Specific
Destination In If Source Gateway Flags Use Out If
-------------- ------- ------------ --------- ----- ---- -------
10.6.32.11 ip.tun1 -- 10.6.32.97 UH 0 hme1
-- hme1 10.6.32.11 -- U 0 ip.tun1
|
The example shows the routes for a foreign agent that uses a reverse tunnel. The first line indicates that the destination IP address 10.6.32.11 and the incoming interface ip.tun1 select hme1 as the interface that forwards the packets. The next line indicates that any packet that originates from interface hme1 and source address 10.6.32.11 must be forwarded to ip.tun1.
snoop Extensions for Mobile IP
Mobile IP extensions have been added to the snoop(1M) command to identify Mobile IP traffic on the link. See the snoop(1M) man page for more information.
The following example shows the output of snoop that runs on the mobile node, mip-mn2.
Example 25–5 Output From snoop Command
mip-mn2# snoop
Using device /dev/hme (promiscuous mode)
mip-fa2 -> 224.0.0.1 ICMP Router advertisement (Lifetime 200s [1]:
{mip-fa2-80 2147483648}), (Mobility Agent Extension), (Prefix Lengths),
(Padding)
mip-mn2 -> mip-fa2 Mobile IP reg rqst
mip-fa2 -> mip-mn2 Mobile IP reg reply (OK code 0)
|
This example shows that the mobile node received one of the periodically sent mobility agent advertisements from the foreign agent, mip-fa2. Then mip-mn2 sent a registration request to mip-fa2, and in response, received a registration reply. The registration reply indicates that the mobile node successfully registered with its home agent.
The snoop(1M) command also supports IPsec extensions. Consequently, you can show how registration and tunnel packets are being protected.
- © 2010, Oracle Corporation and/or its affiliates
