|
|
| Sun ONE Directory Server 5.2 Getting Started Guide |
Chapter 3 A Quick Look at Directory Server Console
This chapter provides practical examples (using Directory Server Console) of the features described in the previous chapter. It walks you through the essential tasks you need to perform to have an overview of how Directory Server works. Information on how the command-line utilities are used to perform these tasks is provided in the next chapter.
Note that this chapter does not attempt to provide comprehensive installation or administration information. Detailed installation and configuration procedures are described in the Sun ONE Directory Server Installation and Tuning Guide and in the Solaris System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP). Detailed administration procedures are described in the Sun ONE Directory Server Administration Guide.
This chapter includes the following sections:
- Installing and Configuring Directory Server
- Using Directory Server Console
- Managing Entries
- Understanding the Schema
- Working with Groups and Roles
- Working With Class of Service (CoS)
- Working With ACIs
- Setting Up Replication
Installing and Configuring Directory Server
The method used to install and configure Sun ONE Directory Server will differ, depending on whether the software is bundled with your operating system. For detailed instructions on how to install Directory Server unbundled version, refer to the Sun ONE Directory Server Installation and Tuning Guide. For instructions on how to configure the bundled version, refer to the Solaris System Administration Guide: Naming and Directory Services (DNS, NIS, and LDAP).
Before You Start
In configuring Sun ONE Directory Server, you will provide certain information. The examples that follow assume the information as summarized in the following table. If you supply different variables in the installation, make a note of these so that you can use them in the examples.
When Directory Server is minimally configured and started, you are ready to proceed with the examples in this guide. The installation program indicates the host and port numbers used by the Administration Server.
Using Directory Server Console
You perform most Directory Server administrative tasks through the Administration Server, a second server provided to help you manage Directory Server (and all other Sun ONE servers). Sun ONE Server Console is the graphical interface to the Administration Server. Directory Server Console is a part of Sun ONE Server Console, and is designed specifically for use with Sun ONE Directory Server.
You can perform most Directory Server administrative tasks from the Directory Server Console. You can also perform administrative tasks manually by editing the configuration files or by using command-line utilities. The command-line utilities are discussed in the next chapter.
Note All the commands described in this section can be accessed via the directoryserver command in the Solaris packaged version. For more information, refer to the directoryserver(1) man page.
Starting Directory Server Console
To start Directory Server Console:
- Check that the directory server daemon, slapd-serverID is running (using the ps command, or an equivalent command for your operating system.) If it is not, enter the following command to start it:
% ServerRoot/slapd-serverID/start-slapd
- Check that the administration server daemon, admin-serv is running (using the ps command, or an equivalent command for your operating system.) If it is not, enter the following command to start it:
% ServerRoot/start-admin
- Start Sun ONE Server Console by entering the following command
% ServerRoot/startconsole
The Console login window is displayed. If your configuration directory (the directory that contains the o=NetscapeRoot suffix) is stored in a separate instance of Directory Server, a window is displayed requesting the administrator user DN, password, and the URL of the Admin Server for that directory server.
- Log in using the bind DN and password of a user with sufficient access permissions for the operations you want to perform. For example, use cn=Directory Manager, and the appropriate password.
Sun ONE Server Console is displayed.
- Navigate through the tree in the left-hand pane to find the machine hosting your Directory Server and click on its name or icon to display its general properties.
- Double-click the name of your Directory Server in the tree or click the Open button to display Directory Server Console for managing this Directory Server instance.
Directory Server Console for example.com is shown in Figure 3-1.
Figure 3-1 Directory Server Console
Managing Entries
It is unlikely that you will use the console to add, delete or modify bulk entries. These processes are generally performed using the command-line utilities. To understand how entries are stored in the directory, however, it is useful to use the console to add a single entry.
Adding an Entry
As a simple exercise, add a user to the default database userRoot.
- In Directory Server Console, select the Directory tab.
- Expand the example node. This is the default suffix that you created at installation.
The example node contains three subnodes: Groups, People and Special Users. Select the People node.
- From the Object menu, select New > User. You can also right-click on the People node and select New > User.
- Enter the First Name and Last Name of the new user. For the purposes of this example, use the name Barbara Jensen.
- Click OK.
- Select View > Refresh and click on the People node to check that your new user has been added.
Finding Entries
Use the Directory tab of Directory Server Console to browse the contents of the directory tree and search for specific entries in the directory.
- On Directory Server Console, select the Directory tab.
Depending on the DN you used to authenticate to the directory, this tab displays the contents of the directory that you have access permissions to view. You can browse through the contents of the tree or right-click an entry and select Search from the pop-up menu.
- The Search dialog provides a simple interface for finding entries in the directory. This dialog performs a search from the node in the directory that was selected when the dialog was invoked. Search from the highest level of the directory for a wider search, or from a lower subtree for a quicker search.
The Advanced Search allows you to refine your search to certain attributes and their values. The Filtered Search is available if you want to search with your own LDAP filter string.
See the online help for further information on using this feature.
Understanding the Schema
The schema defines the size, range and format of entries that are stored in the directory. When you add or change an entry in the directory, the schema determines whether the object class is valid. It also determines the required attributes and the optional attributes for the object class.
Looking at the Schema in the Console
- In the Directory Server Console, select the Configuration tab.
- Click on the Schema node and select the Object Classes tab.
- In the Standard Object Classes pane, scroll down and select the person Object Class.
Note that the required attributes are cn (common name), sn (surname) and objectClass. This means that when you add an entry of type person, you must add the cn, sn and objectClass attributes.
Note The console prevents you from adding entries that violate the schema.
Working with Groups and Roles
As discussed in the previous chapter, groups provide associations between entries. Static groups explicitly name their member entries. Dynamic groups specify a filter and all entries that match are members of the group.
Roles are designed to be more efficient and easier to use for applications. Roles are defined and administered like groups, but in addition, member entries also have a generated attribute that indicates the roles in which they participate.
In the following exercises, we will add the person created previously to one of the default groups in the example database. We will also create a new managed role.
Adding a Member to a Static Group
- In Directory Server Console, select the Directory tab.
- Expand the example node. This is the default suffix that you created at installation.
The example node contains three subnodes: Groups, People and Special Users.
- Select the Groups node to display the four default groups that appear in the example database.
- Double-click the HR Managers group.
- Click the Members node to display the members of the group. There should be no members defined for the group.
- On the Static Group tab click Add to add a new member.
- Select Users from the Search dropdown list and click Search.
The only user entry we have added to the directory (Barbara Jensen) is displayed.
- Click OK.
Barabara Jensen is now added as a member of the static group HR Managers.
- Click OK to return to the Directory tab.
Creating a Managed Role
Managed roles allow you to create an explicit enumerated list of members (much like a static group). Managed roles are added to entries by adding the nsRoleDN attribute to the entry.
To create and add members to a managed role:
- In Directory Server Console, select the Directory tab.
- Browse the directory tree and select the parent entry for your new role.
For the purposes of simplicity, we will select the People entry in this exercise, although this may not be realistic in an actual deployment.
- From the Object menu, select New > Role. You can also right click the entry and select New > Role.
The Create New Role dialog box is displayed.
- Click General in the left pane. Type a name for your new role in the "Role Name" field. For the purposes of this exercise, use myCorpAdminRole as the role name.
The role name is required.
- Enter a description of the new role in the "Description" field. For the purposes of this exercise, enter "corporate administrators" here.
- Click Members in the left pane.
- In the right pane, select Managed Role. Click Add to add new entries to the list of members.
The standard "Search users and groups" dialog box is displayed.
- Select Users from the Search dropdown list, then click Search. Select the only user entry currently in the directory (Barbara Jensen) and click OK.
- Click OK again to dismiss the Create New Role window.
Barbara Jensen is now a member of the role myCorpAdminRole. The new role appears in the directory with the icon for a managed role.
Checking Role Membership
Because managed roles add the nsRoleDN attribute to an entry, it is easy to see the managed roles to which an entry user belongs. To check Barbara Jensen's membership of myCorpAdminRole:
- In Directory Server Console, select the Directory tab.
- Expand the example node and click the People node.
- Select Barabara Jensen's entry in the right pane.
- Select Edit With Generic Editor from the Object menu.
The Generic Editor window is displayed.
- Note that Barbara Jensen's entry now has an nsRoleDN attribute whose value is cn=myCorpAdminRole,ou=People,dc=example,dc=COM.
Working With Class of Service (CoS)
The Class of Service (CoS) mechanism allows you to create virtual attributes not stored in the entries. Instead, they are generated by the CoS mechanism as the entry is sent to the client application. CoS simplifies entry management and reduces storage requirements.
Note CoS functionality is subject to certain restrictions. See the Sun ONE Directory Server Administration Guide and the Sun ONE Directory Server Deployment Guide for a complete understanding of CoS.
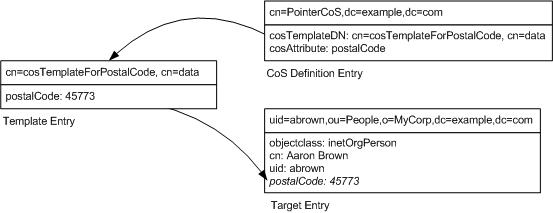
In brief, a CoS defines a virtual attribute and its value for all of its target entries, any entry within the scope of the CoS. Each CoS is comprised of a CoS Definition Entry and a CoS Template Entry. Creating a new CoS implies creating a definition entry and a template entry.
In the following exercise, we will create a CoS that defines a common postal code for all of the entries stored under dc=example,dc=com. The following diagram shows the entries that would be affected by this example.
Figure 3-2 Pointer CoS Definition, Template and Target Entries
Creating a CoS Template Entry
- In the Directory Server Console, select the Directory tab.
- Browse the directory tree and select the parent entry under which you wish to store the template entry. For the purposes of this exercise, select People.
- From the Object menu (or the right-click context menu), select New > Other, and then select costemplate from the list in the New Object dialog.
- Click OK.
The Generic Editor dialog opens with default values for certain attributes in the new template.
- Edit the new template object as follows:
- Click any value next to the Object class attribute and click Add Value to add the ldapsubentry and extensibleobject values to the objectclass attribute.
- Click Add Attribute to add the cn attribute (the attribute appears as Full Name in the list of attributes). Click in the text area to the right of the attribute and enter a value that will identify the template. For this example, we will use cosTemplateForPostalCode.
- Change the naming attribute to the new cn attribute. To do this, click the Change button, clear the In Naming Attribute checkbox for the cospriority attribute, and select the In Naming Attribute checkbox for the cn attribute.
- Click OK.
- Delete the cosPriority attribute. It is not required for the purposes of this example. To do this, select the cosPriority attribute and click Delete Attribute.
- Add the attribute and its value to generate on target entries by the CoS mechanism. Since we are creating a CoS that will specify the postal code of entries, add the postalcode attribute and enter the value of the postal code. We will use 45773.
The Generic Editor dialog appears, as shown in Figure 3-3:
Figure 3-3 Generic Editor Dialog
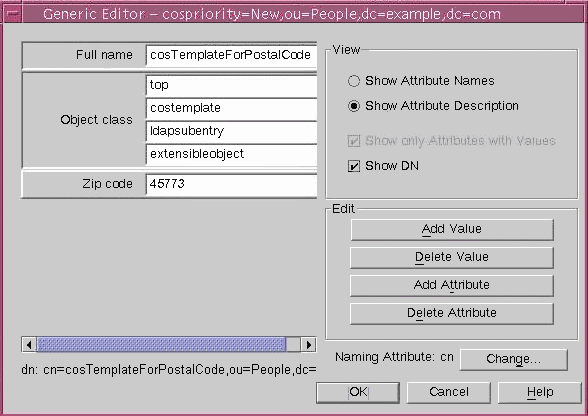
- Click OK in the Generic Editor dialog to create the template entry.
The new CoS appears in the right pane.
- To define a pointer CoS for this template, select the new template entry in directory tree and select Copy DN from the Edit menu.
Creating a CoS Definition Entry
- Browse the directory tree and select the parent entry under which you wish the new Class of Service to take effect. For the purposes of this exercise, select People.
- From the Object menu or the right-click context menu, select New > Class of Service.
The Create New Class of Service dialog is displayed.
- Select General in the left pane. In the right pane, enter the name of your new Class of Service in the "Class Name" field. The name will appear in the cn naming attribute for the CoS definition entry. Since we are creating a CoS that will generate the postal code, we will call this CoS cosGeneratePostalCode. Enter a description in the "Description" field.
- Click Attributes in the left pane. The right pane displays the list of attributes that will be generated by the CoS mechanism on the target entries.
- Click Add to locate the postalcode attribute and add it to the list.
- Once you have added an attribute to the list, the "Class of Service Behavior" column contains a drop-down list. Click in this cell and select "Overrides target entry attribute". The value of the attribute generated by the CoS will now override any value for that attribute in the target entry.
- Click Template in the left pane. In the right pane, select how the template entry is identified and then fill in the corresponding fields. This will determine the type of CoS you wish to define.
For this exercise, select "By its DN". This will define a pointer CoS. Type Ctrl-V to paste the DN that you copied after creating the template entry.
- Click OK to create the CoS definition entry.
The CoS template and the CoS definition are now displayed in the right pane when you select the People node.
Working With ACIs
Access Control is one of the primary methods of making a directory secure. Using access control, you can control access to the entire directory, a subtree of the directory, specific entries in the directory (including entries defining configuration tasks), or a specific set of entry attributes. You can set permissions for a specific user, all users belonging to a specific group or role, or all users of the directory. Finally, you can define access for a specific location such as an IP address or a DNS name.
Creating a New ACI
In this exercise, we will create an ACI that gives full access rights to Barabara Jensen, the user we created previously. Note that this exercise does not explain the steps in detail. Refer to the Sun ONE Directory Server Administration Guide for a complete explanation of this process and the theory behind each step.
- In Directory Server Console, select the Directory tab.
- Select the People entry and select Set Access Permissions from the Object menu.
- In the Manage Access Control dialog, select Allow self entry modification in the left pane and click New to create a new ACI.
- Type a name for the ACI in the ACI name text box.
The name can be any string you want to use to identify the ACI. For this exercise, use the name Full rights for Barabara.
- On the Users/Groups tab, select All users and click Remove. Click the Add button to the one user to whom this ACI will apply.
- In the Add Users and Groups window:
- Select the Users and Groups search area from the drop-down list, enter BJensen in the Search field, and click the Search button.
- Highlight Barabara Jensen's entry in the search result list, and click the Add button to add it to the list of entries which have access permission.
- Click OK to dismiss the Add Users and Groups window.
Barabara Jensen's entry is now listed on the Users/Groups tab in the Edit ACI dialog.
- Select the Rights tab, and click the Check All button to specify that this user should be given full rights. Note that, as a security precaution, the proxy checkbox is not selected when you click Check All. For the purposes of this example, it is not necessary to add proxy authorization to the ACI.
- Click the Targets tab, then click This Entry to display the node targeted by the ACI.
- Click OK to save the new ACI.
The new ACI is listed in the ACI Manager window.
Setting Up Replication
As described in the previous chapter, replication is the mechanism that automatically copies directory data from one Directory Server instance to another. In this section, we will set up a basic multi-master replication scenario.
To set up replication in our sample installation, we will create a second Directory Server instance on the same host. Note that this setup is for the purposes of demonstrating the replication functionality. In a standard deployment scenario it is unlikely that you would set up replication between two Directory Server instances on the same server.
Creating a New Server Instance
- In the Sun ONE Server Console, select the Server Group node.
- Select Create Instance Of > Sun ONE Directory Server from the Object menu.
- In the Create New Instance window, enter the Server Identifier and Network Port for the new server instance. For this example, use myServer2 for the Server Identifier and 5202 for the Network Port.
- For the remaining fields, use the same information that you used when installing Sun ONE Directory Server.
- Click OK to continue.
The Status window indicates that the new server instance has been created and that the server has been started.
- Click OK to close the status window.
The two Directory Server instances should now be visible under the Server Group node. For the purposes of this example, we will refer to the first server instance as myServer and the second as myServer2.
Creating a New Suffix
To demonstrate the replication functionality, create a new suffix on each server instance.
- In the Directory Server Console of myServer, select the Configuration tab.
- Select the Data node and select New Suffix from the Object menu.
- In the New Suffix window, enter the following as the suffix DN: dc=repl,dc=example,dc=com.
- Click OK.
A status window is displayed, indicating the progress of the suffix creation.
- Expand the Data node and check that the new suffix has been created.
- Repeat this process for the myServer2 server instance (using the same suffix DN).
Creating the Data Object
The new suffix on each server instance does not yet exist as an object in the directory. To create a new object in the directory, you must log in as the Directory Manager:
- In the Directory Server Console of myServer, select Log in as New User from the Console menu.
- Enter the Distinguished Name (cn=directory manager) and the password (password) that you set up when you installed Directory Server.
To set the suffix up as a data object:
- Select the Directory tab.
- Select the server instance node (myServer.example.com).
- Select New Root Object from the Object menu and select the suffix you created in the previous procedure (dc=repl,dc=example,dc=com).
- In the New Object window, select domain and click OK.
The new object is displayed in the Generic Editor.
- Click OK to continue.
Note that the object (repl) appears as a new node in the left pane. Repeat this process for the myServer2 server instance.
Enabling Replication
When you first create a new suffix, replication is disabled by default. In the Directory Server console of myServer, expand the new suffix node (under the Data node). You will notice that the Replication node is marked Disabled. To enable replication:
- Select the Replication node below the suffix name.
- Click Enable Replication in the right-hand pane.
- As we are setting up a multi-master replication scenario (both the server instances will be masters), select Master Replica and click Next.
- Enter an ID for the replica. The replica ID is a 16 bit integer between 1 and 65534 and must be unique for all master replicas. Consumer replicas always have the same replica ID (65535.) For this example, enter 1 and click Next.
- Specify the location of the change log database. For this example, accept the default (/ServerRoot/slapd-myServer/changelogdb) and click Next.
- Enter a password for the replication manager. The replication manager is the bind DN that will be used to bind to the other server instance during replication. For this example, enter the password replpword.
- Enter the password again to confirm it and click Next.
A status box is displayed, indicating that replication is being enabled.
- Click Close.
Note that the Replication node no longer states that replication is disabled.
- Repeat this process for the myServer2 server instance, using a replica ID of 2.
Setting up the Replication Agreement
Once you have set up the master replica, you must specify the replicas to which that master will send updates. This specification is called the Replication Agreement.
- On the Configuration tab of myServer, expand the new suffix node (under the Data node) and select the Replication node.
- Click New on the right-hand pane.
- In the Replication Agreement window, select myServer2.example.com:5202 as the consumer replica to which updates will be sent.
- In the Authentication frame, accept the default DN (cn=replication manager,cn=replication,cn=config) and enter the replication password you chose previously (replpword).
- Click OK.
A confirmation message is displayed, asking whether you want to check the authentication details you have entered.
- Click Yes to check that the master server can indeed contact the consumer.
An informational message is displayed, indicating that the master server can contact the consumer server.
- Click OK.
The consumer replica has now been set up.
- Repeat this process for the myServer2 server instance, selecting myServer.example.com:5201 as the consumer replica.
Initializing the Consumer
Once the Replication Agreement has been set up, you can initialize the consumer replica. Initializing the consumer copies the data that is on the master replica to the consumer replica. Once this has been done, only changes made to the master replica will be copied to the consumer replica.
To initialize the consumer:
- On the Configuration tab of myServer, expand the new suffix node (under the Data node) and select the Replication node.
- Select the consumer in the right hand pane (myServer2.example.com:5202) and click Action.
- Select Initialize remote replica.
- Click Yes to confirm that you want the existing content on the remote replica to be cleared.
The consumer replica has now been initialized.
Testing the Replication
To test whether the replication setup has been successful:
- Add an entry to the repl database on myServer. For information on how to do this, see "Adding an Entry".
- Check the same database on myServer2 and notice that the change you made has been replicated to the second server instance.
Now add an entry to the database on myServer2. Because this is a multi-master replication scenario, changes are accepted on both servers and are replicated to both consumers.