Access Control List (ACL) Using SunScreen SKIP
The ACL feature allows you to limit and control who uses your host systems and applications through your network. Each entity--host, network, or nomadic system, with which you communicate over your network when using SKIP--must be identified and authenticated so that access to your system is controlled. Clear-text hosts are not authenticated. Once communication is established, data can be exchanged in the clear, integrity protected, or encrypted.
SunScreen SKIP can provide mobile remote (nomadic) users with access through the ability to separate an entity from its physical address by means of a key identifier (key ID).
SunScreen SKIP's ACL is based on the requesting system's IP address, if this is fixed and known, or on the key ID, if the SKIP user is nomadic (that is, does not have a fixed address).
When a system tries to connect to a host running SunScreen SKIP, the order of processing for the host is as follows:
-
Search for an entry specifying a remote host by IP address. If the entry exists and it meets the established criteria, the host allows traffic from the remote host; otherwise, it continues to the next search action. If the entry exists, but does not meet the established criteria (in case of incoming traffic), the connection (packet) is refused.
-
Search for a network entry that matches the remote entry. If the entry exists and it meets the established criteria, the host allows traffic from the remote host; otherwise, it continues to the next search action.
-
If an entry for a host or network is not found, search for a nomadic ACL entry containing the sender's key identifier in the SKIP protocol header. If the entry is found and the packet is authenticated, the host stores the sender's IP address until it is replaced with a new value. If it exists and meets these criteria, the host allows traffic from the remote host; otherwise, the host continues to the next search action.
-
Finally, if no match can be found, a catchall ACL entry (named "default") will be used if it is present.
Note -
These rules may be used to prevent a host or network from obtaining access to the system.
Here is an example of how ACL works. Suppose there are two network nodes A and B that wish to communicate securely using DES-to-DES encryption. The three cases that can occur are
Figure B-1 Example of Case One--Access Control

-
Nodes A and B (Figure B-1) may be on a network where their IP addresses are known and can be identified as specific host entries in their ACLs.
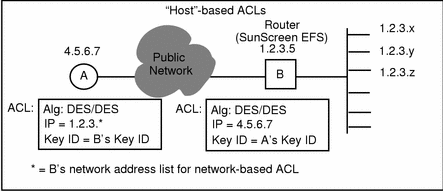
Figure B-2 Example of Case Two--Access Control
-
Node B may be a router (Figure B-2) that has a list of IP addresses, one of which is the host, with which Node A wishes to communicate with as part of a network ACL.
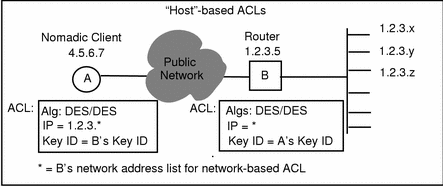
Figure B-3 Example of Case Three--Access Control
-
Node A may be nomadic. Node A will find the sender's key identifier in the SKIP protocol header when it searches for an ACL entry. The packet is authenticated and the sender's IP address is stored until the nomadic entity tries to communicate with the host node again.
The ACL searches through these cases to authenticate the nodes. Node B can have the same options as Node A.
In Case One, or the host ACL, the ACL search for each node finds that they are to use DES/DES to communicate and that they have each other's IP addresses and certificates.
In Case Two, or network ACL, Node B is a router; Node A has the same information as before, but instead of the IP address of 1.2.3.5, it has the router's network address list (1.2.3.*) so it can communicate with any of the nodes in that list.
The main difference is that Node A does not have the certificates of the list of individual hosts on Node B's network, it just has Node B's certificate. So, the whole set of addresses behind Node B is protected; data are encrypted up to Node B and then are sent in the clear behind Node B to the individual hosts on Node B's network.
In Case Three, or the nomadic ACL, a nomadic ACL entry containing the sender's key identifier in the SKIP protocol header is found. The router has an address of "*" for the nomadic system. The entry is found and the packet is authenticated, it stores the sender's IP address until the nomadic entity tries to communicate with the host node again.
Transport and Tunnel Modes
Each IP packet can be encrypted or authenticated in two ways:
-
Transport Mode--Only the data part of the IP packet can be encrypted.
-
Tunnel Mode--The whole IP packet is protected.
Topology Hiding
SKIP supports topology hiding through the use of a tunnel address. The tunnel address field contains the IP address of the host that serves as the intermediary between any or all hosts or systems on a network whose topology is to remain hidden from the rest of the world. The source host is not hidden; only the destination address can be hidden (that is, replaced with a tunnel address that the user specified). To hide the topology, the remote system must be configured using Tunnel Mode and the same router must be used for the tunnel destination as the original destination.
- © 2010, Oracle Corporation and/or its affiliates
