| Skip Navigation Links | |
| Exit Print View | |
|
System Administration Guide: IP Services Oracle Solaris 11 Express 11/10 |
| Skip Navigation Links | |
| Exit Print View | |
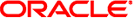
|
System Administration Guide: IP Services Oracle Solaris 11 Express 11/10 |
1. Planning an IPv4 Addressing Scheme (Tasks)
2. Planning an IPv6 Addressing Scheme (Overview)
3. Planning an IPv6 Network (Tasks)
4. Configuring TCP/IP Network Services and IPv4 Addressing (Tasks)
5. Enabling IPv6 on a Network (Tasks)
6. Administering a TCP/IP Network (Tasks)
8. Troubleshooting Network Problems (Tasks)
9. TCP/IP and IPv4 in Depth (Reference)
12. Planning for DHCP Service (Tasks)
13. Configuring the DHCP Service (Tasks)
14. Administering DHCP (Tasks)
15. Configuring and Administering the DHCP Client
16. Troubleshooting DHCP (Reference)
17. DHCP Commands and Files (Reference)
18. IP Security Architecture (Overview)
Encapsulating Security Payload
Security Considerations When Using AH and ESP
Authentication and Encryption Algorithms in IPsec
Authentication Algorithms in IPsec
Encryption Algorithms in IPsec
Transport and Tunnel Modes in IPsec
Virtual Private Networks and IPsec
20. IP Security Architecture (Reference)
21. Internet Key Exchange (Overview)
23. Internet Key Exchange (Reference)
24. IP Filter in Oracle Solaris (Overview)
Part IV Networking Performance
26. Integrated Load Balancer Overview
27. Configuration of Integrated Load Balancer Tasks
28. Virtual Router Redundancy Protocol (Overview)
29. VRRP Configuration (Tasks)
30. Implementing Congestion Control
Part V IP Quality of Service (IPQoS)
31. Introducing IPQoS (Overview)
32. Planning for an IPQoS-Enabled Network (Tasks)
33. Creating the IPQoS Configuration File (Tasks)
34. Starting and Maintaining IPQoS (Tasks)
35. Using Flow Accounting and Statistics Gathering (Tasks)
Figure 18-1 shows how an IP addressed packet, as part of an IP datagram, proceeds when IPsec has been invoked on an outbound packet. The flow diagram illustrates where authentication header (AH) and encapsulating security payload (ESP) entities can be applied to the packet. How to apply these entities, as well as how to choose the algorithms, are described in subsequent sections.
Figure 18-2 shows the IPsec inbound process.
Figure 18-1 IPsec Applied to Outbound Packet Process
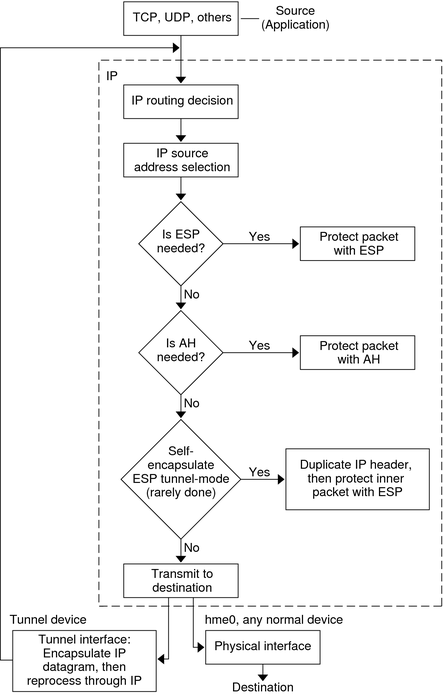
Figure 18-2 IPsec Applied to Inbound Packet Process