| Oracle® Enterprise Data Quality for Product Data Oracle DataLens Server Administration Guide Release 5.6.2 Part Number E23614-02 |
|
|
View PDF |
| Oracle® Enterprise Data Quality for Product Data Oracle DataLens Server Administration Guide Release 5.6.2 Part Number E23614-02 |
|
|
View PDF |
Lightweight Directory Access Protocol (LDAP) contains the functions to provide user authentication. It you use LDAP, then users do not need to be separately created in the Oracle DataLens Server Administration Web pages and assigned roles and passwords.
When LDAP is used, the Oracle DataLens Server contacts the LDAP server, and attempt to login with the provided credentials. If login is successful, it will find the group objects corresponding to its internal roles, and determine which of these groups the user is a member of in order to assign the appropriate rights.
There are two files that need to be placed in the server /config directory (defined in web.xml):
ldap.keystore
ldap.xml
The Oracle DataLens Server will check for these two files in the config directory and will use LDAP user authentication if these files are found. The admin user within the DLS server will always be checked internally to prevent lockouts.
The ldap.keystore file needs to be created by your local IT Administrator with the Java keystore utility. Oracle Consulting Services can also create this file for you given the CA root certificate file generated by the LDAP directory server (for example, by Active Directory). The DLS supports LDAP and LDAPs connections, not SASL or negotiated TLS.
The ldap.xml file needs to be manually edited based on your local LDAP settings.
Following is an example ldap.xml file, configured for use with Microsoft Active Directory
<LdapInfo><!-- Connection Information --><host>AD-LDAP</host><port>636</port><!-- Security information --><keystoreFile>ldap.keystore</keystoreFile><!-Proxy Information à<proxyUser>cn=proxytest,cn=users,dc=ad-ldap,dc=datalens,dc=com </proxyUser><proxyPass>password</proxyPass><displayNameAttribute>sAMAccountName</displayNameAttribute><!-- Users --><userPrefix>cn=</userPrefix><userSuffix>ou=dlsusers,dc=ad-ldap,dc=com</userSuffix><!-- Roles --><rolePrefix>cn=</rolePrefix><roleSuffix>ou=datalens,dc=ad-ldap,dc=datalens,dc=com</roleSuffix><memberAttribute>member</memberAttribute></LdapInfo>
The entries control the directory lookup behavior as follows:
host
This should be the LDAP server name or address. Host names must be able to be resolved on the Oracle DataLens Server.
port
Use port 389 for unencrypted, 636 for SSL connections.
keystoreFile
If a keystore file entry is included, SSL connections will be used to connect and make all queries against LDAP.
proxyUser (optional)
If a proxy user is included, an initial connection will be made as the proxy user to search recursively through the directory for a user whose entered name is found in the directory with a matching displayNameAttribute.
proxyPassword (optional)
Login password for the proxy user.
displayNameAttribute (optional)
If a proxy user is used, this will be the criteria used to search for the username entered in the login screens. For example, sAMAccountName is used for Active Directory, or UID in many other systems.
userPrefix
This is the attribute prefix on user objects, typically cn= or uid=
userSuffix (optional)
The base container in which to search for users. If a proxy user is not used, searches are conducted in this scope only, and are not recursive. If a proxy user is used, this tag is ignored.
rolePrefix
The attribute prefix for group objects, typically cn=.
roleSuffix
The base container in which to search for groups. This is a single scope search, and group names must exactly match the roles in the Oracle DataLens Server.
memberAttribute
The attribute of the group objects, which will contain the list of users within the group.
The LDAP administrator must define roles (groups) that are used by the Oracle DataLens Server. These roles are mapped from LDAP to the Oracle DataLens Roles based on the name only. New roles can be created and used with LDAP, as long as corresponding groups are created in the LDAP directory.
Standard role names for the Oracle DataLens Server include the following.
Server Admin
Knowledge Studio
Application Studio
Governance Studio User
First, make a new OU (organization unit) to house your users:
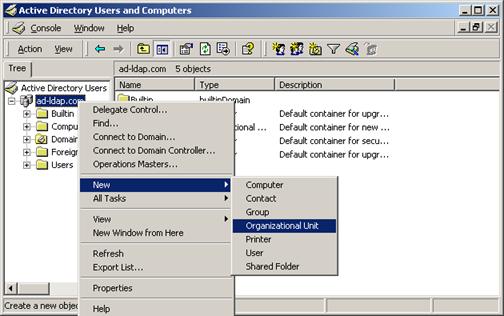
Description of the illustration image081.jpg
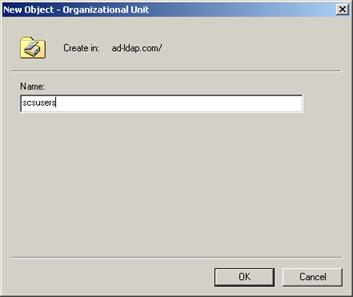
Description of the illustration image082.jpg
Now, make some users in that OU:
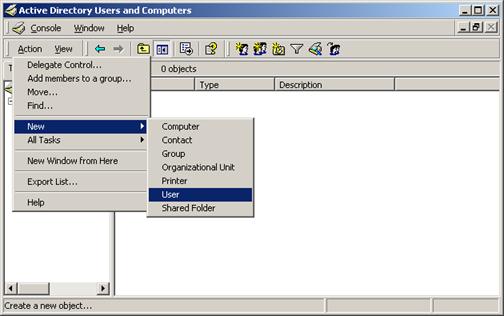
Description of the illustration image083.jpg
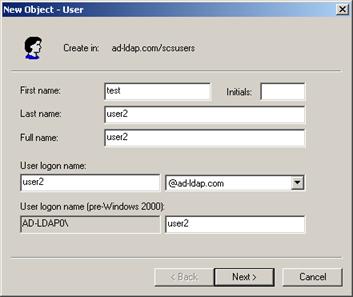
Description of the illustration image084.jpg
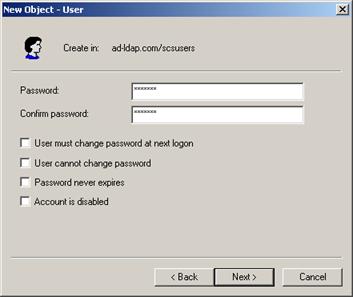
Description of the illustration image085.jpg
Then, make an OU for the Oracle DataLens roles:
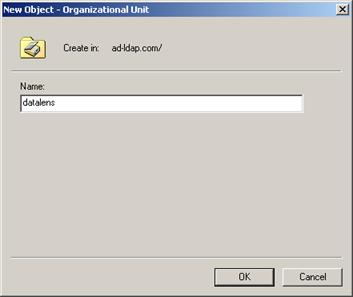
Description of the illustration image086.jpg
Create new groups for the Oracle DataLens Server roles:
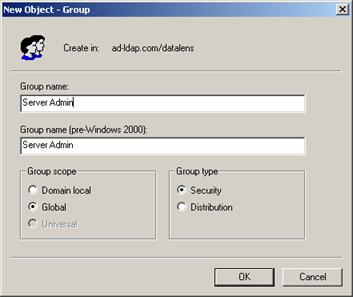
Description of the illustration image087.jpg
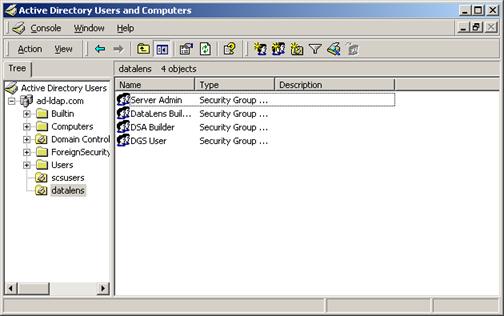
Description of the illustration image088.jpg
Then add users to the corresponding role groups.
Note:
Most likely, you will already have your network users set up. If this is the case, just add you existing users to the new Oracle DataLens Server group.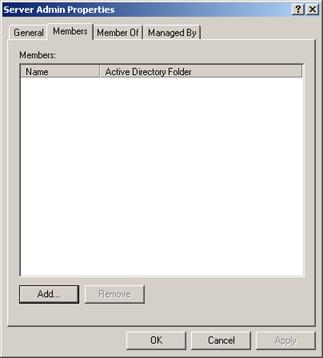
Description of the illustration image089.jpg
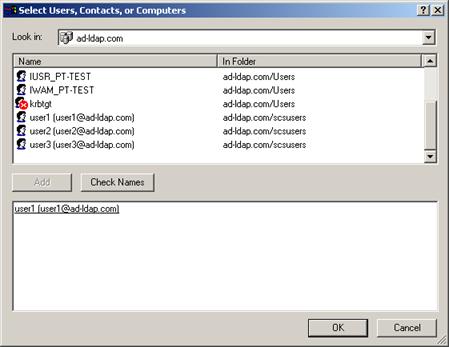
Description of the illustration image090.jpg
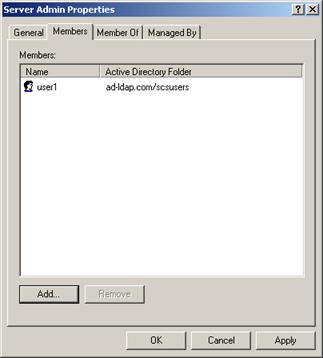
Description of the illustration image091.jpg
After configuring the Oracle DataLens Server with an appropriate ldap.xml and ldapstore.xml, the users will now be able to login with their Active Directory credentials.