18 Integrating Components
This chapter contains the following topics:
-
Section 18.1, "Integrating Oracle Identity Manager and Oracle Access Manager 11g"
-
Section 18.2, "Integrating Oracle Adaptive Access Manager with Oracle Access Manager 11g"
-
Section 18.3, "Integrating Oracle Adaptive Access Manager 11g with Oracle Identity Manager 11g"
-
Section 18.4, "Integrating Oracle Identity Federation with Oracle Access Manager 11g"
18.1 Integrating Oracle Identity Manager and Oracle Access Manager 11g
This section describes how to integrate Oracle Identity Manager and Oracle Access Manager 11g.
This section contains the following topics:
-
Section 18.1.2, "Copying OAM Keystore Files to OIMHOST1 and OIMHOST2"
-
Section 18.1.3, "Configuring Oracle Access Manager for Oracle Identity Manager Integration"
-
Section 18.1.4, "Updating Existing LDAP Users with Required Object Classes"
-
Section 18.1.5, "Integrating Oracle Access Manager 11g with Oracle Identity Manager 11g"
-
Section 18.1.6, "Updating Oracle Virtual Directory Authenticator"
-
Section 18.1.8, "Managing the Password of the xelsysadm User"
18.1.1 Prerequisites
-
Ensure that OIM11g has been installed and configured as described in Chapter 14, "Extending the Domain with Oracle Identity Manager."
-
Ensure that the Oracle Access Manager 11g has been installed and configured as described in Chapter 11, "Extending the Domain with Oracle Access Manager 11g."
-
Ensure that OHS has been installed and configured as described in Chapter 4, "Installing Oracle HTTP Server."
-
Ensure that the JTA Transaction Timeout for the domain is 600 seconds or greater. If required update the timeout value by following these steps:
-
Open a browser and go to the WebLogic Administration Console at:
http://admin.mycompany.com/console -
Log in to the WebLogic Administrative Console as an administrative user.
-
Navigate to Services -> JTA.
-
If the value for Timeout Seconds less than
600, click Lock and Edit, then update the value to600. -
Click Save.
-
Click Activate Changes.
-
Stop the Administration Server and the Managed Servers as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
-
Start the Administration Server using Node Manager as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
-
Start the Managed Servers in your domain using the WebLogic Administration Console as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
-
18.1.2 Copying OAM Keystore Files to OIMHOST1 and OIMHOST2
If you are using Oracle Access Manager with the Simple Security Transport model, you must copy the OAM keystore files that were generated in Section 11.11, "Creating Oracle Access Manager Key Store" to OIMHOST1 and OIMHOST2. Copy the keystore files ssoKeystore.jks and oamclient-truststore.jks to the directory DOMAIN_HOME/config/fmwconfig on OIMHOST1 and OIMHOST2.
18.1.3 Configuring Oracle Access Manager for Oracle Identity Manager Integration
Before integrating Oracle Identity Manager with Oracle Access Manager 11g, you must extend Oracle Access Manager 11g to support Oracle Identity Manager.
To do this, perform the following tasks on IDMHOST1
-
Set the environment variables:
MW_HOME,JAVA_HOME,IDM_HOMEandORACLE_HOME.Set
IDM_HOMEtoIDM_ORACLE_HOME.Set
ORACLE_HOMEtoIAM_ORACLE_HOME. -
Create a properties file called
config_oam2.propswith the following contents:WLSHOST: adminvhn.mycompany.com WLSPORT: 7001 WLSADMIN: weblogic WLSPASSWD: weblogic password IDSTORE_HOST: idstore.mycompany.com IDSTORE_PORT: 389 IDSTORE_BINDDN: cn=orcladmin IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_OAMSOFTWAREUSER: oamLDAP IDSTORE_OAMADMINUSER: oamadmin PRIMARY_OAM_SERVERS: idmhost1.mycompany.com:5575,idmhost2.mycompany.com:5575 WEBGATE_TYPE: ohsWebgate10g ACCESS_GATE_ID: Webgate_IDM OAM11G_IDM_DOMAIN_OHS_HOST:sso.mycompany.com OAM11G_IDM_DOMAIN_OHS_PORT:443 OAM11G_IDM_DOMAIN_OHS_PROTOCOL:https OAM11G_WG_DENY_ON_NOT_PROTECTED: false OAM_TRANSFER_MODE: simple OAM11G_OAM_SERVER_TRANSFER_MODE:simple OAM11G_IDM_DOMAIN_LOGOUT_URLS: /console/jsp/common/logout.jsp,/em/targetauth/emaslogout.jsp OAM11G_OIM_WEBGATE_PASSWD: webgate password OAM11G_SERVER_LOGIN_ATTRIBUTE: uid COOKIE_DOMAIN: .mycompany.com OAM11G_IDSTORE_ROLE_SECURITY_ADMIN: OAMAdministrators OAM11G_SSO_ONLY_FLAG: false OAM11G_OIM_INTEGRATION_REQ: true OAM11G_SERVER_LBR_HOST:sso.mycompany.com OAM11G_SERVER_LBR_PORT:443 OAM11G_SERVER_LBR_PROTOCOL:https COOKIE_EXPIRY_INTERVAL: 120 OAM11G_OIM_OHS_URL:https://sso.mycompany.com:443/
Where:
-
WLSHOSTandWLSPORTare, respectively, the host and port of your administration server, created in Chapter 6, "Creating the WebLogic Server Domain for Identity Management." This is the virtual name. -
WLSADMINandWLSPASSWDare, respectively, the WebLogic administrative user and password you use to log in to the WebLogic console. -
IDSTORE_HOSTandIDSTORE _PORTare, respectively, the host and port of your Identity Store directory. -
IDSTORE_BINDDNis an administrative user in the Identity Store directory. -
IDSTORE_USERSEARCHBASEis the container under which Oracle Access Manager searches for the users. -
IDSTORE_GROUPSEARCHBASEis the location in the directory where Groups are stored. -
IDSTORE_SEARCHBASEis the location in the directory where Users and Groups are stored. -
IDSTORE_OAMSOFTWAREUSERis the name of the user you created in Section 10.4.2, "Creating Users and Groups for Oracle Access Manager" to be used to interact with LDAP. -
IDSTORE_OAMADMINUSERis the name of the user you created in Section 10.4.2, "Creating Users and Groups for Oracle Access Manager" to access your OAM Console. -
PRIMARY_OAM_SERVERSis a comma separated list of your Oracle Access Manager Servers and the proxy ports they use.Note:
To determine the proxy ports your OAM Servers use:
-
Log in to the OAM console at
http://admin.mycompany.com:7001/oamconsole -
Click the System Configuration tab.
-
Expand Server Instances under the Common Configuration section
-
Click an Oracle Access Manager server, such as WLS_OAM1, and click Open.
-
Proxy port is the one shown as Port.
-
-
ACCESS_GATE_IDis the name you want to assign to the WebGate. -
OAM11G_OIM_WEBGATE_PASSWDis the password you want to assign to the WebGate. -
OAM11G_IDM_DOMAIN_OHS_HOSTis the name of the load balancer which is in front of the OHS's. -
OAM11G_IDM_DOMAIN_OHS_PORTis the port that the load balancer listens on. -
OAM11G_IDM_DOMAIN_OHS_PROTOCOLis the protocol to use when directing requests at the load balancer. -
OAM11G_OAM_SERVER_TRANSFER_MODEis the security model that the Oracle Access Manager servers function in, as defined in Section 11.6.1, "Changing Oracle Access Manager Security Model." -
OAM11G_IDM_DOMAIN_LOGOUT_URLSis set to the various logout URLs. -
OAM11G_SSO_ONLY_FLAGconfigures Oracle Access Manager 11g as authentication only mode or normal mode, which supports authentication and authorization.If
OAM11G_SSO_ONLY_FLAGistrue, the Oracle Access Manager 11g server operates in authentication only mode, where all authorizations return true by default without any policy validations. In this mode, the server does not have the overhead of authorization handling. This is recommended for applications which do not depend on authorization policies and need only the authentication feature of the Oracle Access Manager server.If the value is
false, the server runs in default mode, where each authentication is followed by one or more authorization requests to the Oracle Access Manager server. WebGate allows the access to the requested resources or not, based on the responses from the Oracle Access Manager server. -
OAM11G_SERVER_LBR_HOSTis the name of the load balancer fronting your site. This and the following two parameters are used to construct your login URL. -
OAM11G_SERVER_LBR_PORTis the port that the load balancer is listening on. -
OAM11G_SERVER_LBR_PROTOCOLis the URL prefix to use. -
COOKIE_DOMAINis the domain in which the WebGate functions. -
WEBGATE_TYPEis the type of WebGate agent you want to create. Valid values areohsWebgate10gandohsWebgate11g. -
OAM11G_IDSTORE_NAMEis the name of the Identity Store. If you already have an Identity Store in place which is different from the default created by this tool, set this parameter to the name of that Identity Store. -
OAM11G_OIM_OHS_URLis the URL used to access OIM when accessing through the load balancer.
-
-
Configure Oracle Access Manager using the command
idmConfigTool, which is located atIAM_ORACLE_HOME/idmtools/bin.Note:
When you run the
idmConfigTool, it creates or appends to the fileidmDomainConfig.param. This file is generated in the same directory that theidmConfigToolis run from. To ensure that each time the tool is run, the same file is appended to, always run theidmConfigToolfrom the directory:IAM_ORACLE_HOME/idmtools/binThe syntax of the command on Linux is:
idmConfigTool.sh -configOAM input_file=configfileThe syntax on Windows is:
idmConfigTool.bat -configOAM input_file=configfileFor example:
idmConfigTool.sh -configOAM input_file=config_oam2.props
When the command runs, you are prompted to enter the password of the account you are connecting to the Identity Store with. You are also asked to specify the passwords you want to assign to the accounts:
-
IDSTORE_PWD_OAMSOFTWAREUSER -
IDSTORE_PWD_OAMADMINUSER
Sample command output:
Enter ID Store Bind DN password: Enter User Password for IDSTORE_PWD_OAMSOFTWAREUSER: Confirm User Password for IDSTORE_PWD_OAMSOFTWAREUSER: Enter User Password for IDSTORE_PWD_OAMADMINUSER: Confirm User Password for IDSTORE_PWD_OAMADMINUSER: The tool has completed its operation. Details have been logged to automation.log
-
-
Check the log file for any errors or warnings and correct them
-
Restart WebLogic Administration Server, as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
18.1.4 Updating Existing LDAP Users with Required Object Classes
You must update existing LDAP users with the object classes OblixPersonPwdPolicy, OIMPersonPwdPolicy, and OblixOrgPerson.
Note:
This is not required in the case of a fresh setup where you do not have any existing users.
On IDMHOST1, create a properties file for the integration called user.props, with the following contents:
IDSTORE_HOST: idstore.mycompany.com IDSTORE_PORT: 389 IDSTORE_ADMIN_USER: cn=orcladmin IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com PASSWORD_EXPIRY_PERIOD: 7300
Set the environment variables: MW_HOME, JAVA_HOME, IDM_HOME and ORACLE_HOME.
Set IDM_HOME to IDM_ORACLE_HOME.
Set ORACLE_HOME to IAM_ORACLE_HOME.
Upgrade existing LDAP, using the command idmConfigTool, which is located at: IAM_ORACLE_HOME/idmtools/bin
Note:
When you run the idmConfigTool, it creates or appends to the file idmDomainConfig.param. This file is generated in the same directory that the idmConfigTool is run from. To ensure that each time the tool is run, the same file is appended to, always run the idmConfigTool from the directory:
IAM_ORACLE_HOME/idmtools/bin
The syntax of the command is:
idmConfigTool.sh - upgradeLDAPUsersForSSO input_file=configfile
on Linux and UNIX-based operating systems and
idmConfigTool.bat -upgradeLDAPUsersForSSO input_file=configfile
on Windows.
For example:
idmConfigTool.sh -upgradeLDAPUsersForSSO input_file=user.props
When prompted, enter the following information:
-
The password of the user you are using to connect to your Identity Store.
-
The directory type:
OVDif you are using Oracle Virtual Directory, otherwiseOID
Sample output:
Enter LDAP admin user password: ********* Upgrading LDAP Users With OAM ObjectClasses ********* Enter Directory Type[OID]: OVD Completed loading user inputs for - LDAP connection info Completed loading user inputs for - LDAP Upgrade Upgrading ldap users at - cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=readOnlyUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=readOnlyUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=readOnlyUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=readOnlyUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=readOnlyUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=readWriteUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=readWriteUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=readWriteUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=readWriteUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=readWriteUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=weblogic,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=weblogic,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=weblogic,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=weblogic,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=weblogic,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=oamMasterAdminUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=oamMasterAdminUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=oamMasterAdminUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=oamMasterAdminUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=oamSoftwareUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=oamSoftwareUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=oamSoftwareUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=oamSoftwareUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=oamSoftwareUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=PolStoreROUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=PolStoreROUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=PolStoreROUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=PolStoreROUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=PolStoreROUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=PolStoreRWUser,cn=Users,dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=PolStoreRWUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=PolStoreRWUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=PolStoreRWUser,cn=Users,dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=PolStoreRWUser,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=PUBLIC, cn=Users, dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=PUBLIC, cn=Users, dc=us,dc=oracle,dc=com. Seeding it objectclass OblixOrgPerson not present in cn=PUBLIC, cn=Users, dc=us,dc=oracle,dc=com. Seeding it objectclass OblixPersonPwdPolicy not present in cn=PUBLIC, cn=Users, dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=PUBLIC, cn=Users, dc=us,dc=oracle,dc=com Parsing - cn=orcladmin, cn=Users, dc=us,dc=oracle,dc=com objectclass OIMPersonPwdPolicy not present in cn=orcladmin, cn=Users, dc=us,dc=oracle,dc=com. Seeding it obpasswordexpirydate added in cn=orcladmin, cn=Users, dc=us,dc=oracle,dc=com Parsing - cn=xelsysadm,cn=Users,dc=us,dc=oracle,dc=com Parsing - cn=xelsysadmin,cn=Users,dc=us,dc=oracle,dc=com Finished parsing LDAP LDAP Users Upgraded. ********* ********* *********
See Also:
Oracle Fusion Middleware Integration Overview for Oracle Identity Management Suite for more information about the idmConfigTool command.
18.1.5 Integrating Oracle Access Manager 11g with Oracle Identity Manager 11g
This section describes how to integrate Oracle Access Manager 11g with Oracle Identity Manager
18.1.5.1 Remove Security Providers
If you have previously performed the tasks in Section 19, "Configuring Single Sign-on for Administration Consoles," you must delete the security providers you created in that section.
To do this:
-
Log in to the WebLogic Administration Console at:
http://admin.mycompany.com/console -
Click Security Realms from the Domain structure menu.
-
Click Lock and Edit in the Change Center.
-
Click myrealm.
-
Select the Providers tab.
Select the following providers:
-
OVDAuthenticator
-
OIDAuthenticator
-
OAMIDAssertor
-
-
Click Delete.
-
Click Yes to confirm deletion.
-
Restart the administration server and all managed servers, as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
18.1.5.2 Integrating Oracle Access Manager with Oracle Identity Manager by Using idmConfigTool
To integrate Oracle Access Manager 11g with Oracle Identity Manager perform the following steps on IDMHOST1:
-
Set the Environment Variables:
MW_HOME,JAVA_HOME,IDM_HOME, andORACLE_HOME, for example:export IDM_HOME=IDM_ORACLE_HOME export ORACLE_HOME=IAM_ORACLE_HOME
-
Create a properties file for the integration called
oimitg.props, with the following contents:LOGINURI: /${app.context}/adfAuthentication LOGOUTURI: /oamsso/logout.html AUTOLOGINURI: None ACCESS_SERVER_HOST: OAMHOST1.mycompany.com ACCESS_SERVER_PORT: 5575 ACCESS_GATE_ID: Webgate_IDM COOKIE_DOMAIN: .mycompany.com COOKIE_EXPIRY_INTERVAL: 120 OAM_TRANSFER_MODE: simple WEBGATE_TYPE: ohsWebgate10g SSO_ENABLED_FLAG: true IDSTORE_PORT: 389 IDSTORE_HOST: idstore.mycompany.com IDSTORE_DIRECTORYTYPE: OID or OVD IDSTORE_ADMIN_USER: cn=oamLDAP,cn=Users,dc=mycompany,dc=com IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com MDS_DB_URL: jdbc:oracle:thin:@(DESCRIPTION=(LOAD_BALANCE=on)(FAILOVER=on)(ADDRESS_LIST=(ADDRESS=(protocol=tcp)(host=OIDDBHOST1-vip.mycomapny.com)(port=1521))(ADDRESS=(protocol=tcp)(host=OIDDBHOST2-vip.mycompany.com)(port=1521)))(CONNECT_DATA=(SERVER=DEDICATED)(SERVICE_NAME=oidedg.mycompany.com))) MDS_DB_SCHEMA_USERNAME: edg_mds WLSHOST: adminvhn.mycompany.com WLSPORT: 7001 WLSADMIN: weblogic DOMAIN_NAME: IDMDomain OIM_MANAGED_SERVER_NAME: WLS_OIM1 DOMAIN_LOCATION: ORACLE_BASE/admin/IDMDomain/aserver/IDMDomainNotes:
-
Set
IDSTORE_HOSTto your Oracle Internet Directory host or load balancer name if you are using Oracle Internet Directory as your Identity Store. If not, set it to your Oracle Virtual Directory host or load balancer name. -
Set
IDSTORE_DIRECTORYTYPEtoOVDif you are using Oracle Virtual Directory server to connect to either a non-OID directory or Oracle Internet Directory. Set it toOIDif your Identity Store is in Oracle Internet Directory and you are accessing it directly rather than through Oracle Virtual Directory. -
If your access manager servers are configured to accept requests using the simple mode, set
OAM_TRANSFER_MODEtosimple. Otherwise setOAM_TRANSFER_MODEtoopen -
Set
IDSTORE_PORTto your Oracle Internet Directory port if you are using Oracle Internet Directory as your Identity Store. If not, set it to your Oracle Virtual Directory port. -
If you are using a single instance database, then set
MDS_URLto:jdbc:oracle:thin:@DBHOST:1521:SID
-
-
Change location to:
IAM_ORACLE_HOME/servercd IAM_ORACLE_HOME/server -
Integrate Oracle Access Manager with Oracle Identity Manager using the command
idmConfigTool, which is located at:IAM_ORACLE_HOME/idmtools/binNote:
When you run the
idmConfigTool, it creates or appends to the fileidmDomainConfig.param. This file is generated in the same directory that theidmConfigToolis run from. To ensure that each time the tool is run, the same file is appended to, always run theidmConfigToolfrom the directory:IAM_ORACLE_HOME/idmtools/binThe syntax of the command is
idmConfigTool.sh -configOIM input_file=configfileon Linux and UNIX-based systems, and
idmConfigTool.bat -configOIM input_file=configfileon Windows.
For example:
IAM_ORACLE_HOME/idmtools/bin/idmConfigTool.sh -configOIM input_file=oimitg.propsWhen the script runs you are prompted for:
-
Access Gate Password
-
SSO Keystore Password
-
Global Passphrase
-
Idstore Admin Password
-
MDS Database schema password
-
Admin Server User Password
Sample output:
Enter sso access gate password: Enter mds db schema password: Enter idstore admin password: Enter admin server user password: ********* Seeding OAM Passwds in OIM ********* Enter ssoKeystore.jks Password: Enter SSO Global Passphrase: Completed loading user inputs for - CSF Config Updating CSF with Access Gate Password... WLS ManagedService is not up running. Fall back to use system properties for configuration. Updating CSF ssoKeystore.jks Password... Updating CSF for SSO Global Passphrase Password... ********* ********* ********* ********* Activating OAM Notifications ********* Completed loading user inputs for - MDS DB Config Initialized MDS resources Apr 11, 2011 4:57:45 AM oracle.mds NOTIFICATION: transfer operation started. Apr 11, 2011 4:57:46 AM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed: 1, total number of documents failed: 0. Upload to DB completed Releasing all resources Notifications activated. ********* ********* ********* ********* Seeding OAM Config in OIM ********* Completed loading user inputs for - OAM Access Config Validated input values Initialized MDS resources Apr 11, 2011 4:57:46 AM oracle.mds NOTIFICATION: transfer operation started. Apr 11, 2011 4:57:47 AM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed: 1, total number of documents failed: 0. Download from DB completed Releasing all resources Updated /u01/app/oracle/product/fmw/iam/server/oamMetadata/db/oim-config.xml Initialized MDS resources Apr 11, 2011 4:57:47 AM oracle.mds NOTIFICATION: transfer operation started. Apr 11, 2011 4:57:47 AM oracle.mds NOTIFICATION: transfer is completed. Total number of documents successfully processed: 1, total number of documents failed: 0. Upload to DB completed Releasing all resources OAM configuration seeded. Please restart oim server. ********* ********* ********* ********* Configuring Authenticators in OIM WLS ********* Completed loading user inputs for - Dogwood Admin WLS Completed loading user inputs for - LDAP connection info Connecting to t3://adminvhn.mycompany.com:7001 Connection to domain runtime mbean server established Starting edit session Edit session started Connected to security realm. Validating provider configuration Validated desired authentication providers Validated authentication provider state successfuly. Created OAMIDAsserter successfuly Created OIDAuthenticator successfuly Created OIMSignatureAuthenticator successfuly Setting attributes for OID Authenticator All attributes set. Configured in OID Authenticator now lDAP details configured in OID authenticator Control flags for authenticators set sucessfully Reordering of authenticators done sucessfully Saving the transaction Transaction saved Activating the changes Changes Activated. Edit session ended. Connection closed sucessfully ********* ********* *********
Notes:
-
If you have already enabled single sign-on for your WebLogic Administration Consoles as described in Section 19.1, "Configuring Single Sign-On for Administration Consoles with Oracle Access Manager 11g" when this script is run, you might see the following errors when this script is run:
ERROR: Desired authenticators already present. [Ljava.lang.String;@7fdb492] ERROR: Error occurred while configuration. Authentication providers to be configured already present. ERROR: Rolling back the operation..
These errors can be ignored.
-
Note: You might see errors in the log file that look like this:
ALL: Error seeding SSOGlobalPP credential
This is a bug and the workaround is described in the next section.
-
-
Check the log file for errors and correct them if necessary.
-
Restart
WLS_OIM1,WLS_OIM2, and the WebLogic Administration Server, as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
18.1.6 Updating Oracle Virtual Directory Authenticator
When configOIM has finished, it will have created an Oracle Virtual Directory authenticator (if you are using Oracle Virtual Directory). This authenticator must be updated, as follows.
-
Log in to WebLogic console at
http://admin.mycompany.com/console -
Click Security Realms from the domain structure.
-
Click My Realm.
-
Click the Providers tab.
-
Click the OVDAuthenticator provider.
-
Click Lock and Edit.
-
Click Provider Specific tab.
-
Change the following values:
-
All Users Filter:
(&(uid=*)(objectclass=person)) -
User From Name Filter:
(&(uid=%u)(objectclass=person))
-
-
Click Save.
-
Click Activate Changes.
-
Restart the Administration Servers
WLS_OAM1,WLS_OAM2,WLS_OIM1, andWLS_OIM2, and any other managed servers that are running.
18.1.7 Manually Creating CSF Keys
-
Log into Oracle Enterprise Manager Fusion Middleware Control at:
http://admin.mycompany.com/em -
Navigate to FARM_IDMDomain - Weblogic Domain
-
Click IDMDomain.
-
When the summary screen is displayed, select Security - Credentials from the list.
-
Click the credential key oim and click Create Key.
Create the following keys:
-
SSOKeystoreKey
Field Value Map
oimKey
SSOKeystoreKeyType
PasswordUser Name
SSOKeystoreKey
Password
Key store password as entered in Section 11.11, "Creating Oracle Access Manager Key Store"
Description
OAMSSOKeystorepassword -
SSOGlobalPP
Field Value Map
oimKey
SSOGlobalPPType
PasswordUser Name
SSOGlobalPPPassword
Value of Global Passphrase entered in Section 11.6.1, "Changing Oracle Access Manager Security Model," Step 10
Description
OAMGlobalPP -
SSOAccessKey
Field Value Map
oimKey
SSOAccessKeyType
PasswordUser Name
SSOAccessKeyPassword
Value of
OAM11G_OIM_WEBGATE_PASSWDentered in Section 11.6.2, "Configuring Oracle Access Manager by Using the IDM Automation Tool"Description
OAMAccessGatePassword
SSOKeystoreKey and SSOGlobalPP are only required if you are using the Simple transport model.
-
18.1.8 Managing the Password of the xelsysadm User
After you integrate Oracle Identity Manager with Oracle Access Manager, two xelsysadm accounts exist. One is the internal account created by Oracle Identity Manager. The other is the account you created in the Identity Store in Section 10.4.4, "Creating Users and Groups for Oracle Identity Manager."
The xelsysadm account located in the LDAP store is the one used to access the OIM console. If you want to change the password of this account, change it in LDAP. You can use ODSM to do this. Do not change it through the OIM console.
18.1.9 Validating Integration
To validate integration, you must assign Identity Management administrators to WebLogic security groups and install WebGate as described in Chapter 19, "Configuring Single Sign-on for Administration Consoles."
To validate that the wiring of Oracle Access Manager 11g with Oracle Identity Manager 11g was successful, attempt to log in to the Oracle Identity Manager Self Service Console, as follows:
-
Using a browser, navigate to
https://sso.mycompany.com/oim. This redirects you to the OAM11g single sign-on page. -
Log in using the
xelsysadmuser account created in Section 10.4.4, "Creating Users and Groups for Oracle Identity Manager." -
If you see the OIM Self Service Console Page, the integration was successful.
18.2 Integrating Oracle Adaptive Access Manager with Oracle Access Manager 11g
This section describes how to integrate OAAM with Oracle Access Manager and Oracle Identity Manager. Once OAAM has been integrated with Oracle Access Manager, you can use OAAM instead of the standard Oracle Access Manager login to validate access to resources. Even though OAAM is performing the authentication, it is authenticating against users in Oracle Access Manager.
When OAAM is integrated with Oracle Identity Manager, Oracle Identity Manager is used to help users who have forgotten their username or password.
This section contains the following topics:
-
Section 18.2.2, "Copying OAM Keystore Files to OAAMHOST1 and OAAMHOST2"
-
Section 18.2.3, "Registering OAAM as a Third Party Application"
-
Section 18.2.6, "Setting OAAM properties for Oracle Access Manager"
-
Section 18.2.8, "Validating OAAM-Oracle Access Manager Integration"
18.2.1 Prerequisites
Before starting this association, ensure that the following tasks have been performed:
-
Install and configure Oracle Access Manager (OAM) as described in Chapter 11, "Extending the Domain with Oracle Access Manager 11g."
-
Configure Oracle Access Manager to work with an LDAP store as described in Chapter 11, "Extending the Domain with Oracle Access Manager 11g."
-
Install Oracle Adaptive Access Manager as described in Chapter 12, "Extending the Domain with Oracle Adaptive Access Manager."
18.2.2 Copying OAM Keystore Files to OAAMHOST1 and OAAMHOST2
If you are using Oracle Access Manager with the Simple Security Transport model, you must copy the OAM keystore files oamclient-truststore.jks and ssoKeystore.jks that were generated in Section 11.11, "Creating Oracle Access Manager Key Store" to OAAMHOST1 and OAAMHOST2. Copy these files to the directory DOMAIN_HOME/config/fmwconfig on OAAMHOST1 and OAAMHOST2.
18.2.3 Registering OAAM as a Third Party Application
If you have configured Oracle Access Manager to use the Simple Security Transportation protocol, you must register OAAM as a third-party application.
To do this, proceed as follows:
-
From IDMHOST1, start the
wlstshell from theIAM_ORACLE_HOME/common/bindirectory. For example, on Linux and UNIX-based systems, you would type:./wlst.sh
On Windows you would type:
./wlst.cmd
-
Connect to the WebLogic Administration Server using the following
wlstconnect command:connect('AdminUser',"AdminUserPassword",t3://hostname:port')For example:
connect("weblogic","admin_password","t3://ADMINVHN.mycompany.com:7001") -
Run the
registerThirdPartyTAPPartnercommand as follows:registerThirdPartyTAPPartner(partnerName = "partnerName", keystoreLocation= "path to keystore" , password="keystore password", tapTokenVersion="v2.0", tapScheme="TAPScheme", tapRedirectUrl="OAAM login URL")
Where
-
partnerNameis a unique name. If the partner exists in Oracle Access Manager, the configuration will be overwritten. -
keystoreLocationis an existing Key Store location. If the directory path you specified is not present, you get an error. On Windows, the patch needs to be escaped, for example:"C:\\oam-oaam\\tap\keystore\store.jks"
-
passwordis the password specified to encrypt the key store. Remember this, as you will need it later. -
tapTokenVersionis alwaysv2.0. -
tapSchemeis the authentication scheme to be updated. -
tapRedirectUrlis a reachable URL. If it is not, registration fails with the message:Error! Hyperlink reference not valid.Note:
Due to a bug,
tapRedirectURLmust be an http url. This is changed to https later. -
tapRedirectUrlis constructed as follows:http://OAAM_SERVER_HOST:OAAM_SERVER_PORT/oaam_server/oamLoginPage.jsp
For example:
registerThirdPartyTAPPartner(partnerName = "OAAMTAPPartner", keystoreLocation= "IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jks" , password="password", tapTokenVersion="v2.0", tapScheme="TAPScheme", tapRedirectUrl="http://oaamhost1.mycompany.com:14300/oaam_server/oamLoginPage.jsp")
-
-
Copy the file
IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jksto the same location onOAAMHOST1andOAAMHOST2. For example:scp IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jks OAAMHOST2:IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jks
Note:
mykeystore.jksis always created on the WebLogic Administration Server host. -
Log in to the OAM Admin Console at:
http://admin.mycompany.com:80/oamconsole. -
Click TAPScheme under Authentication Schemes.
Click Open.
-
Change the Challenge URL to:
https://sso.mycompany.com:443/oaam_server/oamLoginPage.jsp.Add the following Challenge Parameter:
MatchLDAPAttribute=uid -
Click Apply.
-
Restart
WLS_OAAM1andWLS_OAAM2as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
18.2.4 Adding Password to IAMSuiteAgent Profile
When Oracle Access Manager is installed, a default agent profile called IAMSuiteAgent is created. This profile is used by OAAM when integrating with OAM.
When the IAMSutieAgent profile is first created, it has no password. You must set a password before the profile can be used by OAAM for integration. To do this, proceed as follows:
-
Log in to the OAM console at:
http://admin.mycompany.com/oamconsole -
Click the System Configuration tab.
-
Expand Access Manager Settings - SSO Agents.
-
Click OAM Agents and click Open.
-
In the search window, click Search.
-
Click IAMSuiteAgent in the search results. The Agent Properties are displayed.
-
In the Primary Server list, click
+and add any missing Oracle Access Manager servers. -
Enter a password into the Access Client Password Field and click Apply.
Note:
Also check that the security setting matches that of your OAM servers.
18.2.5 Validation
To ensure that this integration has been completed successfully, launch the OAM test tool as described in Section 11.10, "Validating Oracle Access Manager." Then proceed as follows:
-
Connect using the following values:
-
Primary OAM Host:
OAMHOST1 -
Port:
5575 -
Agent ID:
IAMSuiteAgent -
Agent Password: Password you assigned to the
IAMSuiteAgentprofile -
Mode: Choose OAM security Mode
-
Global Passphrase: OAM Pass phrase, if simple mode is used.
-
-
Provide Protected Resource URI
-
Scheme:
http -
Host:
IAMSuiteAgent -
Port: Leave blank
-
Resource:
/oamTAPAuthenticate
Click Validate.
-
-
Provide User Identity
oamadminand the password foroamadmin.Click Authenticate. If the authentication is successful, integration has been completed successfully.
Perform the same validation on OAMHOST2.
18.2.6 Setting OAAM properties for Oracle Access Manager
Follow these steps on IDMHOST1:
-
Copy
IAM_ORACLE_HOME/oaam/clito a temporary location. For example:cp -r IAM_ORACLE_HOME/oaam/cli /u01/app/oracle/oaam -
Edit the file
oaam_cli.properties, which is located in the directory:/u01/app/oracle/oaam/conf/bharosa_properties.Set the following property values in the file:
Parameter Value oaam.adminserver.hostnameADMINVHN.mycompany.comoaam.adminserver.port7001oaam.adminserver.usernameweblogicoaam.adminserver.passwordPassword for the
weblogicuseroaam.db.urlThe DBC URL for the OAAM Database. Format: j
dbc:oracle:thin:@(DESCRIPTION=(LOAD_BALANCE=on)(ADDRESS=(PROTOCOL=TCP)(HOST=host1) (PORT=1521))(ADDRESS=(PROTOCOL=TCP)(HOST=host2) (PORT=1521))(CONNECT_DATA=(SERVICE_NAME=service)))oaam.uio.oam.tap.keystoreFileThe location of the keystore that was created in Section 18.2.3, "Registering OAAM as a Third Party Application." For example:
IAM_ORACLE_HOME/TAP/TapKeyStore/mykeystore.jksOn Windows, you must escape the path. For example:
"C:\\oam-oaam\\tap\keystore\mystore.jks"oaam.uio.oam.tap.partnernameOAAMTAPPartneroaam.uio.oam.hostidmhost1.mycompany.comoaam.uio.oam.portThe Oracle Access Manager server proxy port. For example:
5575.oaam.uio.oam.webgate_idIAMSuiteAgentoaam.uio.oam.secondary.hostidmhost2.mycompanyoaam.uio.oam.secondary.host.portThe Oracle Access Manager server proxy port on the second Oracle Access Manager server. For example:
5575.oaam.uio.oam.security.modeThis depends on the OAM security transport mode in use. The value can be
1(for Open),2(for Simple), or3(for Cert). The default, if not specified, is1(Open).oam.uio.oam.rootcertificate.keystore.filepathThe location of the Keystore file generated for the root certificate:
DOMAIN_HOME/config/fmwconfig/oamclient-truststore.jksThis is required only for security modes
2(Simple) and3(Cert).oam.uio.oam.privatekeycertificate.keystore.filepathThe location of the Keystore file generated for private key:
DOMAIN_HOME/config/fmwconfig/ssoKeystore.jksThis is required for security modes
2(Simple) and3(Cert).Save the file
-
Execute the OAAM CLI tool by issuing the command
setupOAMTapIntegration.sh, which is located in the directory:/u01/app/oracle/oaamexport ORACLE_MW_HOME=/u01/app/oracle/product/fmw export JAVA_HOME=$MW_HOME/jrockit_version chmod +x /u01/app/oracle/oaam/setupOAMTapIntegration.sh /u01/app/oracle/oaam/setupOAMTapIntegration.sh /u01/app/oracle/oaam/conf/bharosa_properties/oaam_cli.propertiesWhen the command runs, it prompts you for the following information:
-
OAAM database username:
EDG_OAAM. -
OAAM database password: Password for the OAAM database user.
-
OAM Webgate Credentials to be stored in CSF: Enter WebGate password.
-
OAM TAP Key store file password: The password you assigned when you generated the third-party application in Section 18.2.3, "Registering OAAM as a Third Party Application."
-
OAM Private Key certificate Key store file password: The password you assigned to the Private keystore file in Section 18.2, "Integrating Oracle Adaptive Access Manager with Oracle Access Manager 11g."
-
OAM Global Pass phrase: If you are using the OAAM Simple security model then this is the OAM global passphrase.
-
18.2.7 Updating Secondary Host Parameter
Log in to the OAAM Admin Console at http://admin.mycompany.com:80/oaam_admin, using the oaamadmin account you created in Section 10.4.3, "Creating Users and Groups for Oracle Adaptive Access Manager."
Then proceed as follows:
-
In the Navigation Tree, click Environment and click Properties.
-
Select List Properties from the Actions menu.
The properties search page is displayed.
-
Enter
oaam.uio.oam.secondary.host.portin the Name field and click Search.The current value is shown in the search results window.
-
In the value field, set the entry to
5575and click Save. -
Restart
WLS_OAM1,WLS_OAM2,WLS_OAAM1, andWLS_OAAM2as described in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
18.2.8 Validating OAAM-Oracle Access Manager Integration
To perform this validation, first create a test resource.
Create a test page called oaam_sso.html on WEBHOST1 and WEBHOST2. The easiest way to do this is to create a file called oaam_sso.html in the directory ORACLE_INSTANCE/config/OHS/component/htdocs with the following:
<html> <body> <center> <p> <h2> OAAM Protected Resource </h2> </p> </center> </body> </html>
18.2.8.1 Creating Oracle Adaptive Access Manager Policy Groups
These groups are only required if you are planning to include OAAM in your topology.
-
Log in to the OAM console at
http://admin.mycompany.com/oamconsole, using theoamadminaccount created previously -
From the Navigation Window expand: Application Domains > IAM Suite.
-
Click Authentication Policies.
-
Click Create on the tool bar (below the Browse tab.
Enter the following information:
-
Name:
OAAM Protected Resources -
Authentication Scheme:
TAPScheme
-
-
Click Apply.
-
Repeat Steps 1-4 to create a new policy group with:
-
Name:
TAP Scheme -
Authentication Scheme:
LDAPScheme
-
18.2.8.2 Creating a Resource in Oracle Access Manager
Now that you have something to protect, you must create a resource in Oracle Access Manager and assign it to one of the policy groups you just created.
-
Log in to the OAM console at:
http://admin.mycompany.com/oamconsoleusing theoamadminaccount created previously. -
From the Navigation window expand: Application Domains > IAM Suite.
-
Click Resources.
-
Click Open on the tool bar below the Browse tab.
-
Click New Resource.
Enter the following information:
-
Type:
http -
Host Identifier:
IAMSuiteAgent -
Resource URL:
/oaam_sso.html -
Protection Level:
Protected -
Authentication Policy:
OAAM Protected Resources -
Authorization Policy:
Protected Resource Policy
-
-
Click Apply.
18.2.8.3 Moving TAP Resource to TAP Policy
-
Log in to the OAM console at:
http://admin.mycompany.com/oamconsoleusing theoamadminaccount created previously. -
From the Navigation window expand: Application Domains > IAM Suite > Authentication Policies.
-
Click Protected Higher Level Policy.
-
Click Open on the tool bar below the Browse tab.
-
In the Resources window click /oamTAPAuthenticate.
-
Click Delete.
-
Click Apply.
-
From the Navigation window expand: Application Domains > IAM Suite > Authentication Policies.
-
Click TAP Scheme.
-
Click Open on the tool bar below the Browse tab.
-
In the Resources window, click Add.
-
Select the resource /oamTAPAuthenticate.
-
Click Apply.
18.2.8.4 Validating Oracle Adaptive Access Manager
Install Oracle WebGate as described in Section 19.5, "Installing and Configuring WebGate."
Access your protected resource using the URL: https://sso.mycompany.com:443/oaam_sso.html. The OAAM Protected Resource is displayed. Log in using an authorized Oracle Access Manager user such as oamadmin. Once you are logged in, the oaam protected resource is displayed.
18.3 Integrating Oracle Adaptive Access Manager 11g with Oracle Identity Manager 11g
OAAM provides a comprehensive set of challenge questions. Its functionality includes:
-
Challenging the user before and after authentication, as required, with a series of questions.
-
Presenting the questions as images and seeking answers through various input devices.
-
Asking questions one after another, revealing subsequent questions only if correct answers are provided.
Oracle Identity Manager also has basic challenge question functionality. It enables users to answer a set of configurable questions and reset their password if they forgot the password. Unlike OAAM, Oracle Identity Manager also has a rich set of password validation capabilities, and it enables policies to be set based on the accounts owned, in addition to simple attributes.
In an Identity Management deployment, best practice is to register only a single set of challenge questions, and to use a single set of password policies. OAAM can be integrated with Oracle Identity Manager so that OAAM provides the challenge questions and Oracle Identity Manager provides password validation, storage and propagation. This enables you to use OAAM fraud prevention at the same time you use Oracle Identity Manager for password validation. When OAAM is integrated with Oracle Identity Manager, Oracle Identity Manager is used to help users who have forgotten their username or password.
This section contains the following topics:
-
Section 18.3.2, "Configuring Oracle Identity Manager Encryption Keys in CSF"
-
Section 18.3.3, "Setting OAAM properties for Oracle Identity Manager"
-
Section 18.3.4, "Setting Oracle Identity Manager properties for OAAM"
-
Section 18.3.6, "Restarting Oracle Adaptive Access Manager and Oracle Identity Manager"
-
Section 18.3.7, "Validating Oracle Identity Manager-OAAM Integration"
18.3.1 Prerequisites
Before starting this association, ensure that the following tasks have been performed:
-
Install and configure Oracle Identity Management.
-
Install Oracle Adaptive Access Manager.
-
Install and configure Oracle Access Manager.
-
Integrate Oracle Identity Manager with Oracle Access Manager, as described in Section 18.1, "Integrating Oracle Identity Manager and Oracle Access Manager 11g."
-
Integrate Oracle Access Manager with Oracle Adaptive Access Manager as described in Section 18.2, "Integrating Oracle Adaptive Access Manager with Oracle Access Manager 11g."
18.3.2 Configuring Oracle Identity Manager Encryption Keys in CSF
-
Go to Oracle Enterprise Manager Fusion Middleware Control at
http://admin.mycompany.com/emusing a web browser. -
Log in using the WebLogic administrator account, for example
weblogic_idm. -
Expand the
weblogic_domainicon in the navigation tree in the left pane. -
Select the IDMDomain, right click, and select the menu option Security and then the option Credentials in the sub menu.
-
Click oaam to select the map and then click Create Key.
-
In the pop-up window, ensure Select Map is oaam.
-
Enter:
-
Key Name:
oim.credentials -
Type:
Password -
UserName:
xelsysadm -
Password: Password for
xelsysadmaccount,
-
-
Click OK to save the secret key to the Credential Store Framework.
18.3.3 Setting OAAM properties for Oracle Identity Manager
Go to the OAAM Administration Console at: http://admin.mycompany.com/oaam_admin. Log in using the oaamadmin account you created in Section 10.4.3, "Creating Users and Groups for Oracle Adaptive Access Manager." Then proceed as follows:
-
In the navigation tree, click Environment and double click Properties. The properties search page is displayed.
-
To set a property value, enter its name in the Name field and click Search. The current value is shown in the search results window.
-
Click Value. Enter the new value and click Save.
-
Set the following properties to enable OAAM to integrate with Oracle Identity Manager:
-
bharosa.uio.default.user.management.provider.classname:com.bharosa.vcrypt.services.OAAMUserMgmtOIM -
bharosa.uio.default.signon.links.enum.selfregistration.url:https://sso.mycompany.com:443/oim/faces/pages/USelf.jspx?E_TYPE=USELF&OP_TYPE=SELF_REGISTRATION&backUrl=https://sso.mycompany.com:443/oim/faces/pages/Self.jspx -
bharosa.uio.default.signon.links.enum.trackregistration.enabled:true -
bharosa.uio.default.signon.links.enum.selfregistration.enabled:true -
bharosa.uio.default.signon.links.enum.trackregistration.url:https://sso.mycompany.com:443/oim/faces/pages/USelf.jspx?E_TYPE=USELF&OP_TYPE=UNAUTH_TRACK_REQUEST&backUrl=https://sso.mycompany.com:443/oim/faces/pages/Self.jspx -
oaam.oim.csf.credentials.enabled:true -
oaam.oim.url:t3://oimhost1.mycompany.com:14000,oimhost2.mycompany.com:14000
-
18.3.4 Setting Oracle Identity Manager properties for OAAM
-
Log in to the OIM administrative console at:
https://sso.mycompany.com:443/oim/self -
Click the Advanced link on the self-service console
-
Click Search System Properties in the System Management Box.
-
Click Advanced Search below the System Configuration search box.
-
When the advanced search screen appears click the right arrow (->). Perform a general search. Do not provide a search string.
-
Click each of the properties shown, then select Open from the Actions menu. Set the value of each property as shown and click Save to save the value.
Note:
The property name appears in the keyword column.
-
OIM.DisableChallengeQuestions:TRUE -
OIM.ChangePasswordURL:https://sso.mycompany.com:443/oaam_server/oimChangePassword.jsp -
OIM.ChallengeQuestionModificationURL:https://sso.mycompany.com:443/oaam_server/oimResetChallengeQuestions.jsp
-
18.3.5 Changing Domain to TAP Scheme Protection
Log in to the OAM console at: http://admin.mycompany.com/oamconsole
-
From the Navigation Window, expand: Application Domains > IAM Suite.
-
Click Authentication Policies.
-
Double click the policy Protected HigherLevel Policy.
-
Change Authentication Scheme to TAPScheme.
-
Click Apply.
18.3.6 Restarting Oracle Adaptive Access Manager and Oracle Identity Manager
Restart the following Managed Servers as described in Chapter 20, "Starting and Stopping Oracle Identity Management Components."
-
WebLogic Administration Server
-
WLS_OAM1 and WLS_OAM2
-
WLS_OIM1 and WLS_OIM2
-
WLS_OAAM1 and WLS_OAAM2
18.3.7 Validating Oracle Identity Manager-OAAM Integration
Validate that Oracle Identity Manager is integrated with OAAM as follows:
-
Log in to OIM console at the URL:
https://sso.mycompany.com:443/oim/self.The OAAM login page is displayed.
-
Log in to the OIM console as the
xelsysadmuser.You are prompted to set up challenge questions and OAAM-specific security pictures.
18.4 Integrating Oracle Identity Federation with Oracle Access Manager 11g
Oracle Identity Federation supports two integration modes with Oracle Access Manager: authentication mode and SP mode.
In the authentication mode, Oracle Identity Federation delegates authentication of the user to Oracle Access Manager.
The user is redirected to an Oracle Identity Federation resource protected by WebGate, that triggers the Oracle Access Manager authentication flow. Once the user is identified, it will access the resource, and WebGate will provide to Oracle Identity Federation an HTTP header containing the user's identity.
In the SP mode, Oracle Access Manager delegates user authentication to Oracle Identity Federation, which uses the Federation Oracle Single Sign-On protocol with a remote Identity Provider. Once the Federation Oracle Single Sign-On flow is performed, Oracle Identity Federation will create a local session and then propagates the authentication state to Oracle Access Manager, which maintains the session information.
This section provides the steps to integrate OIF with OAM11g in authentication mode and SP mode.
This section contains the following topics:
-
Section 18.4.3, "Integrating Oracle Identity Federation with Oracle Access Manager in SP Mode"
-
Section 18.4.4, "Validating Oracle Identity Federation Integration with Oracle Access Manager"
18.4.1 Prerequisites
Before starting this integration, ensure that the following tasks have been performed:
-
Install and configure Oracle Identity Federation as described in Chapter 15, "Extending the Domain with Oracle Identity Federation."
-
Install and configure Oracle Access Manager as described in Chapter 11, "Extending the Domain with Oracle Access Manager 11g."
-
Install and configure Oracle HTTP Server as described in Section 4.4, "Installing Oracle HTTP Server."
-
Install and configure WebGate as described in Section 19.5, "Installing and Configuring WebGate."
18.4.2 Integrating Oracle Identity Federation with Oracle Access Manager in Authentication Mode
This section covers the following topics:
-
Section 18.4.2.1, "Creating an Authorization Policy in Oracle Access Manager"
-
Section 18.4.2.2, "Creating a Resource in Oracle Access Manager"
-
Section 18.4.2.3, "Configuring the Oracle Access Manager Authentication Engine"
18.4.2.1 Creating an Authorization Policy in Oracle Access Manager
Create an Authorization Policy in Oracle Access Manager to enable local authorization for Oracle Identity Federation. To create an authorization policy, log in to the OAM console at http://admin.mycompany.com/oamconsole as the OAM administration user. Then perform the following steps:
-
Click the Policy Configuration tab.
-
Expand IAM Suite under the Application Domains section.
-
Click Authorization Policies, and then select Create from the menu.
-
On the Authorization Policy page, provide the following details:
-
Name: The name of the authorization policy, for example:
OIF Local Authorization -
Description: The description for the policy
-
-
Click the Responses tab, then click
+to add the HTTP Header Attributes. Enter the following information:-
Name: Enter
OAM_REMOTE_USERas the name. Make a note of this name, as it is used when configuring the Authentication Engines in the next section. -
Type:
Header -
Value:
$user.attr.uid
-
-
Click Apply.
18.4.2.2 Creating a Resource in Oracle Access Manager
Create a resource for the OIF URL to be protected by Oracle Access Manager for authentication. To create a resource, log in to the OAM console at http://admin.mycompany.com/oamconsole as the OAM administration user. Then perform the following steps:
-
Click the Policy Configuration tab.
-
Expand IAM Suite under the Application Domains section.
-
Click Resources, and then select Open from the menu.
-
On the IAM Suite Resources page, Click New Resource to bring up the Resources page.
-
On the Resources Page, provide the following details:
-
Type: Select
HTTP -
Host Identifier:
IAMSuiteAgent -
Resource URL:
/fed/user/authnoam -
Query String: Leave blank
-
Protection Level:
Protected -
Authorization Policy: Select the Authorization Policy created in Section Section 18.4.2.1, "Creating an Authorization Policy in Oracle Access Manager," for example:
OIF Local Authorization. -
Authentication Policy: Protected Higher Level Policy.
-
-
Click Apply.
18.4.2.3 Configuring the Oracle Access Manager Authentication Engine
Configure Oracle Identity Federation's Oracle Access Manager Authentication engine to protect Oracle Identity Federation with an Oracle Access Manager 11g WebGate. To configure the authentication engine, log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Authentication Engines.
-
Select
Oracle Access Manageras the Default Authentication Engine from the list. -
Click Oracle Access Manager tab.
-
Select Enable Authentication Engine to enable the Oracle Access Manager Authentication engine.
-
Enter
OAM_REMOTE_USERas the User Unique ID Header. -
Do not select Logout Enabled, since the logout will be performed with the Oracle Single Sign-On SP Engine.
-
Click Apply to apply the changes.
18.4.2.4 Configuring the OSSO SP Engine
You must configure the OSSO SP Engine, even though none of the SP functionality is used. This is required because the Logout flow between Oracle Identity Federation and Oracle Access Manager uses the OSSO SP Engine.
Configure the OSSO SP Engine as described in Section 18.4.3.1, "Configuring the OSSO SP Engine."
18.4.3 Integrating Oracle Identity Federation with Oracle Access Manager in SP Mode
This section covers the following topics:
18.4.3.1 Configuring the OSSO SP Engine
In SP mode, Oracle Identity Federation uses federation protocols to authenticate a user, and then requests the authentication module to create an authenticated session at Oracle Access Manager. Oracle Identity Federation's Single Sign-On SP engine is used for this purpose. The SSO SP engine also provides logout integration. The Oracle Single Sign-On SP engine must be updated with the OAM Server details to enable OIF to send assertion tokens and direct session management to OAM.
To update the Oracle Single Sign-On SP engine, log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Service Provider Integration Modules.
-
Select the Oracle Single Sign-On tab.
-
Select Enable SP Module to enable the Oracle Single Sign-On SP engine.
-
Provide the following details:
-
Username Attribute:
uid -
Login URL:
https://sso.mycompany.com/oam/server/dap/cred_submit -
Logout URL:
https://sso.mycompany.com/oam/server/logout
-
-
Select Logout Enabled.
-
Click Apply to update the Oracle Single Sign-On SP Engine.
-
Click Regenerate to generate a keystore file. This keystore contains the keys used to encrypt and decrypt the tokens that are exchanged between the Oracle Access Manager and Oracle Identity Federation servers.
-
Save the keystore file using the Save As dialog.
-
Copy the keystore file to a user defined location on
IDMHOST1, for example,MW_HOME/keystores. This keystore will be used to register Oracle Identity Federation as Delegated Authentication Protocol (DAP) partner in the next section.
18.4.3.2 Updating the Oracle Identity Federation Authentication Scheme in Oracle Access Manager
Oracle Access Manager ships with an Oracle Identity Federation Authentication Scheme. This scheme needs to be updated before it can be used. To update the scheme, log in to the OAM console at http://admin.mycompany.com/oamconsole as the OAM administration user. Then perform the following steps:
-
Click the Policy Configuration tab.
-
Expand Authentication Schemes under the Shared Components tree.
-
Select OIFScheme from under the Authentication Schemes and then select Open from the menu.
-
On the Authentication Schemes page, provide the following information
-
Challenge URL:
https://sso.mycompany.com:443/fed/user/sposso -
Context Type: Select external from the list.
Accept the defaults for all other values
-
-
Click Apply to update the
OIFScheme.
18.4.3.3 Creating an Oracle Identity Federation Authentication Policy in Oracle Access Manager
Create an authentication policy in Oracle Access Manager to enable OIF to authenticate the user. To create an authentication policy, log in to the OAM console at http://admin.mycompany.com/oamconsole as the OAM administration user. Then perform the following steps:
-
Click the Policy Configuration tab.
-
Expand IAM Suite under the Application Domains section.
-
Click Authentication Policies, and then select Create from the menu.
-
On the Authentication Policy page, provide the following details:
-
Name: The name of the authentication policy, for example:
OIF Policy. -
Description: The description for the policy
-
Authentication Scheme: Select OIF Scheme from the menu
-
-
Click Apply.
18.4.3.4 Creating a Test Page
Create a test page to validate that Oracle Identity Federation is integrated with Oracle Access Manager.
Create a file called oif_sso.html on WEBHOST1 and WEBHOST2, in the directory ORACLE_INSTANCE/config/OHS/component/htdocs with the following content:
<html> <body> <center> <p> <h2> OIF Protected Resource </h2> </p> </center> </body> </html>
18.4.3.5 Creating a Resource in Oracle Access Manager
Create a resource for the Oracle Identity Federation URL to be protected by Oracle Access Manager. In SP mode, Oracle Identity Federation authenticates the user and then propagates the authentication state to Oracle Access Manager. The resource created here is for the purposes of testing.
To create a resource, log in to the OAM console at http://admin.mycompany.com/oamconsole as the OAM administration user. Then perform the following steps:
-
Click the Policy Configuration tab.
-
Expand IAM Suite under the Application Domains section.
-
Click Resources, and then select Open from the menu.
-
On the IAM Suite Resources page, click New Resources to bring up the Resources page.
-
On the Resources page, provide the following details:
-
Type: Select HTTP
-
Host Identifier:
IAMSuiteAgent -
Resource URL:
/oif_sso.html -
Protection Level: Protected
-
Authorization Policy: Protected Resource Policy
-
Authentication Policy: Select the Authentication Policy created in Section 18.4.3.3, "Creating an Oracle Identity Federation Authentication Policy in Oracle Access Manager," for example: OIF Policy.
-
-
Click Apply.
18.4.3.6 Configuring Oracle Access Manager to Delegate Authentication to Oracle Identity Federation
The Oracle Identity Federation resources protected by Oracle WebGate are directed to Oracle Access Manager for authentication. In SP Mode, Oracle Identity Federation authenticates the user and propagates the authentication state to Oracle Access Manager. To enable Oracle Identity Federation to authenticate the user, Oracle Access Manager must be configured to redirect the user to Oracle Identity Federation for authentication. This is done by registering Oracle Identity Federation as Delegated Authentication Protocol (DAP) partner with Oracle Access Manager.
Proceed as follows on IDMHOST1 to register Oracle Identity Federation as DAP Partner with Oracle Access Manager:
-
Ensure that the keystore generated in the previous section is available on
IDMHOST1. -
Start the
wlstshell from theIAM_ORACLE_HOME/common/bindirectory. For example, on Linux and UNIX-based systems, you would type:./wlst.sh
On Windows you would type:
./wlst.cmd
-
Connect to the WebLogic Administration Server using the following
wlst connectcommand:connect('AdminUser',"AdminUserPassword",t3://hostname:port')For example:
connect("weblogic","admin_password","t3://ADMINVHN.mycompany.com:7001") -
Use the
registerOIFDAPPartnercommand to register Oracle Identity Federation as a DAP partner with Oracle Access Manager.The syntax is:
registerOIFDAPPartner(keystoreLocation="path_to_keystore", logoutURL="OIF_logout_URL", rolloverTime="")
where:
-
path_to_keystoreis the location of the Keystore file onIDMHOST1, for example:/u01/app/oracle/product/fmw/keystores/keystore -
OIF_logout_URLis the OIF Server's logout URL. Usehttps://oifhost:oifport/fed/user/spsloosso?doneURL=https://oamhost:oam port/oam/logout.jspas the logout URLUse
sso.mycompany.comas the value foroifhostandoamhost.Use
443as the value foroifportandoamport. -
rollover_timeis the rollover interval for the keys used to encrypt ordecrypt SASSO tokens.
For example:
wls:/IDMDomain/serverConfig> registerOIFDAPPartner(keystoreLocation="/u01/app/oracle/product/fmw/keystores/keystore", logoutURL="https://sso.mycompany.com/fed/user/spsloosso?doneURL=https://sso.mycompany.com/oam/logout.jsp") Registration Successful
-
-
Restart the Administration Server and the Oracle Access Manager and Oracle Identity Federation Managed Servers by following the steps in Section 20.1, "Starting and Stopping Oracle Identity Management Components."
Note:
Once all of the Oracle Access Manager managed servers are shut down, it is not possible to access the WebLogic Administration console. Once single sign-on has been configured, access to the WebLogic Administration console is controlled through Oracle Access Manager, which requires at least one Oracle Access Manager managed server to be running.
18.4.4 Validating Oracle Identity Federation Integration with Oracle Access Manager
Before the configuration can be validated, obtain the provider metadata and register the providers. For the purposes of validating, Oracle Identity Federation will act as both an Identity Provider and a Service Provider.
18.4.4.1 Generating Provider Metadata
Proceed as follows to generate the IdP and SP metadata.
Log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Security and Trust.
-
Select the Provider Metadata tab.
-
Under the Generate Metadata section:
-
Select Service Provider from the Provider Type list.
-
Click to Generate metadata for the service provider.
-
Save the generated file using the Save File option.
-
Select Identity Provider from the Provider Type list.
-
Click to Generate metadata for the identity provider.
-
Save the generated file using the Save File option.
-
18.4.4.2 Registering the Providers
Proceed as follows to register the IdP and SP providers using the metadata generated in the previous section.
Log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Federations.
-
Under Trusted Providers, click Add to add the Trusted Provider.
-
On the Add Trusted Provider page:
-
Select Load Metadata.
-
Click Choose File and select the SP and IdP metadata files generated in Section 18.4.4.1, "Generating Provider Metadata."
-
-
On the Federations page, verify that both the providers appear in the list of Trusted Providers.
18.4.4.3 Setting the Default Identity Provider
Proceed as follows to set the Identity Provider registered in the previous section as the default IdP.
Log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em
as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Service Provider.
-
For the Default SSO Identity Provider, select the IdP registered above from the list. The Default SSO Identity Provider is under the Protocol Settings section.
-
Click Apply.
18.4.4.4 Updating the Default Authentication Engine to LDAP Engine
When testing integration with Oracle Access Manager in the SP Mode, you cannot configure Oracle Identity Federation as both the Service Provider and IdentityC Provider for the same resource at the same time. When you test the SP mode configuration, you must set the Default Authentication Engine to the LDAP Engine. You reset it to the Oracle Access Manager once the testing is complete.
This step is not required when configuring the Oracle Identity Federation instances to protect a resource only in the SP mode or in the IdP mode.
To set the Default Authentication Engine, log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Authentication Engines.
-
Select LDAP Directory as the Default Authentication Engine from the list.
-
Click Apply to save the changes.
18.4.4.5 Updating the Default SSO Response Binding
By default, the Default SSO Response Binding is set to use the SOAP protocol. For ease of testing, Oracle recommends updating this parameter to HTTP POST.
To set the Default SSO Response Binding, log in to Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Navigate to Administration, then Service Provider.
-
On the Service Provider page, select the SAML 2.0 tab.
-
Change the value for Default SSO Response Binding to HTTP POST. The Default SSO Response Binding is under the Protocol Settings section.
-
Click Apply to save the changes.
18.4.4.6 Validating SP Mode Configuration
Follow these steps to validate the SP mode configuration
-
Using a browser, access the protected resource created in Section 18.4.2.2, "Creating a Resource in Oracle Access Manager," for example:
https://sso.mycompany.com/oif_sso.html. -
Enter the credentials of the
weblogic_idmuser on the Login page.Note:
This user must have an email address in the
mailattribute of the LDAP user record, because the email address is the defaultNameIDformat used. -
The protected resource is displayed.
18.4.4.7 Updating the Default Authentication Engine to Oracle Access Manager
In Section 18.4.4.4, "Updating the Default Authentication Engine to LDAP Engine," you set the Default Authentication Engine to LDAP Engine for validating the SP Mode configuration. You must set it back to Oracle Access Manager.
This step is not required when the Oracle Identity Federation instances are configured to protect a resource only in the SP mode or in the IdP mode.
To set the Default Authentication Engine, log in to the Oracle Enterprise Manager Fusion Middleware Control at http://admin.mycompany.com/em as the WebLogic administration user. Then perform the following steps:
-
Locate and select the Oracle Identity Federation instance under Identity and Access.
-
Navigate to Administration, then Authentication Engines.
-
Select Oracle Access Manager as the Default Authentication Engine from the list.
-
Click Apply to save the changes.
18.4.4.8 Validating Authentication Mode Configuration
Follow these steps to validate the Authentication mode configuration:
-
Access the Test SP SSO page at:
https://sso.mycompany.com/fed/user/testspsso -
Make the following selections on the Initiate Federation SSO page:
-
Set the value for the IdP Provider ID from the list, for example: Default
-
Set the value for Authn Request Binding to HTTP POST from the list.
-
Select Use Default Configuration.
-
-
Click Start SSO.
-
Enter the credentials of the
weblogic_idmuser on the Oracle Access Manager login page. -
The Federation SSO Operation Result page is displayed. Validate that the SSO Authentication Result is successful for the user.
18.5 Auditing Identity Management
Oracle Fusion Middleware Audit Framework is a new service in Oracle Fusion Middleware 11g, designed to provide a centralized audit framework for the middleware family of products. The framework provides audit service for platform components such as Oracle Platform Security Services (OPSS) and Oracle Web Services. It also provides a framework for JavaEE applications, starting with Oracle's own JavaEE components. JavaEE applications are able to create application-specific audit events. For non-JavaEE Oracle components in the middleware such as C or JavaSE components, the audit framework also provides an end-to-end structure similar to that for JavaEE applications.
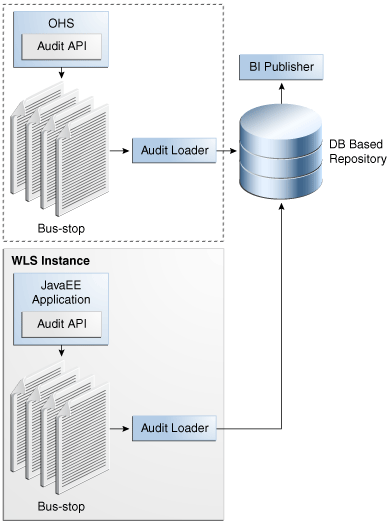
Figure 18-1 is a high-level architectural diagram of the Oracle Fusion Middleware Audit Framework.
The Oracle Fusion Middleware Audit Framework consists of the following key components:
-
Audit APIs
These are APIs provided by the audit framework for any audit-aware components integrating with the Oracle Fusion Middleware Audit Framework. During run-time, applications may call these APIs where appropriate to audit the necessary information about a particular event happening in the application code. The interface enables applications to specify event details such as username and other attributes needed to provide the context of the event being audited.
-
Audit Events and Configuration
The Oracle Fusion Middleware Audit Framework provides a set of generic events for convenient mapping to application audit events. Some of these include common events such as authentication. The framework also enables applications to define application-specific events.
These event definitions and configurations are implemented as part of the audit service in Oracle Platform Security Services. Configurations can be updated through Enterprise Manager (UI) and WLST (command-line tool).
-
The Audit Bus-stop
Bus-stops are local files containing audit data before they are pushed to the audit repository. In the event where no database repository is configured, these bus-stop files can be used as a file-based audit repository. The bus-stop files are simple text files that can be queried easily to look up specific audit events. When a DB-based repository is in place, the bus-stop acts as an intermediary between the component and the audit repository. The local files are periodically uploaded to the audit repository based on a configurable time interval.
-
Audit Loader
As the name implies, audit loader loads the files from the audit bus-stop into the audit repository. In the case of platform and JavaEE application audit, the audit loader is started as part of the JavaEE container start-up. In the case of system components, the audit loader is a periodically spawned process.
-
Audit Repository
Audit Repository contains a pre-defined Oracle Fusion Middleware Audit Framework schema, created by Repository Creation Utility (RCU). Once configured, all the audit loaders are aware of the repository and upload data to it periodically. The audit data in the audit repository is expected to be cumulative and grow over time. Ideally, this should not be an operational database used by any other applications - rather, it should be a standalone RDBMS used for audit purposes only. In a highly available configuration, Oracle recommends that you use an Oracle Real Application Clusters (Oracle RAC) database as the audit data store.
-
Oracle Business Intelligence Publisher
The data in the audit repository is exposed through pre-defined reports in Oracle Business Intelligence Publisher. The reports enable users to drill down the audit data based on various criteria. For example:
-
Username
-
Time Range
-
Application Type
-
Execution Context Identifier (ECID)
-
For more introductory information for the Oracle Fusion Middleware Audit Framework, see the "Introduction to Oracle Fusion Middleware Audit Framework" chapter in the Oracle Fusion Middleware Application Security Guide.
For information on how to configure the repository for Oracle Fusion Middleware Audit Framework, see the "Configuring and Managing Auditing" chapter in the Oracle Fusion Middleware Application Security Guide.
The EDG topology does not include Oracle Fusion Middleware Audit Framework configuration. The ability to generate audit data to the bus-stop files and the configuration of the audit loader are available once the products are installed. The main consideration is the audit database repository where the audit data is stored. Because of the volume and the historical nature of the audit data, it is strongly recommended that customers use a separate database from the operational store or stores being used for other middleware components.