16 Diagnosing Problems
This chapter contains the following sections:
Diagnosing Problems with Oracle WSM Policy Manager
The Oracle WSM Policy Manager manages all Oracle WSM policies and needs to be running to use the Oracle WSM policy framework. You can check the current state of the Policy Manager and review its response time, load, and other data from the Oracle WSM Policy Manager page in Oracle Enterprise Manager Fusion Middleware Control.
To view the Oracle WSM Policy Manager page:
-
In the Navigator pane, expand Application Deployments.
-
Under Application Deployments, expand Internal Applications.
-
Select wsm-pm.
The Oracle WSM Policy Manager home page is displayed.
Figure 16-1 Oracle WSM Policy Manager Page
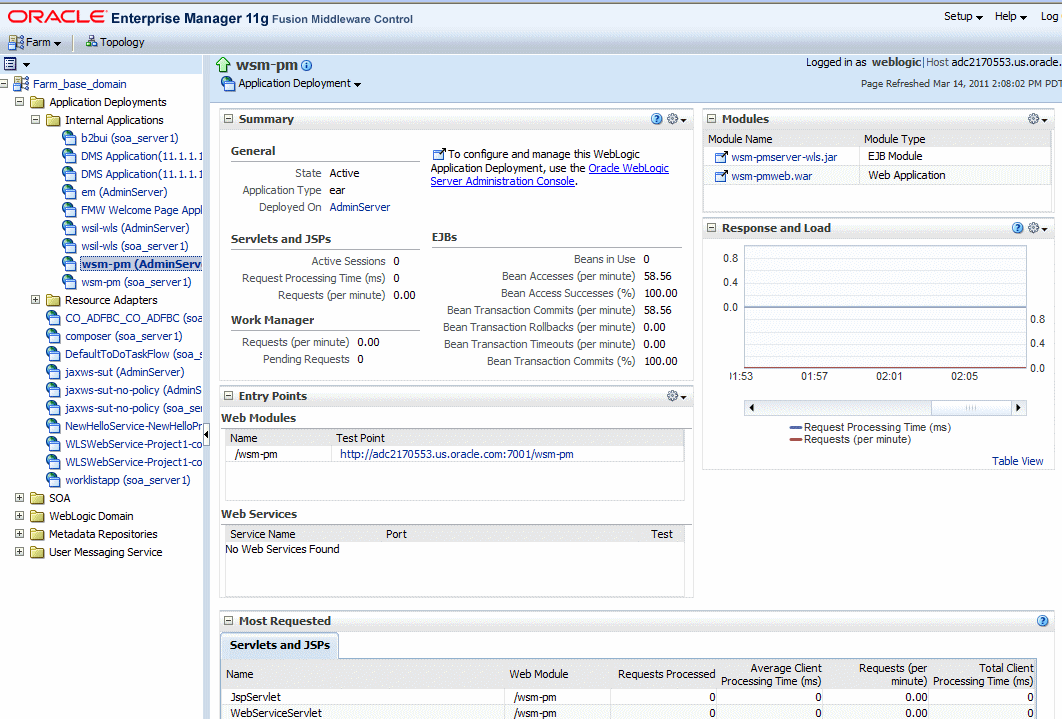
Description of "Figure 16-1 Oracle WSM Policy Manager Page"
-
From the Policy Manager page, you can perform one or more of the following tasks:
-
In the General area of the page, you can check the current state of the Policy Manager and identify the server to which it is deployed.
-
In the Response and Load section of the page, you can view the response time and current load. To view this information in tabular form, click Table View.
-
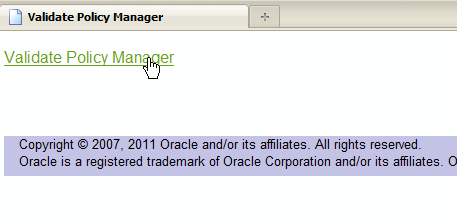
In the Entry Points section of the page, you can validate the connection to the Policy Manager. To do so, in the Web Modules table, click the Test Point URL for wsm-pm. On the Validate Policy Manager page, click the Validate Policy Manager link, as shown in Figure 16-2.
You can also access the Validator page in a Web browser using the following URL:
http://host:port/wsm-pm/validatorIn this URL,
hostandportrepresent the host and port number on which the Policy Manager is running.If the connection to the Policy Manager fails, an error message is displayed. If the connection to the Policy Manager is successful, the Policy Manager Validator page displays the following information:
-
The status of the Policy Manager.
-
The total number of Oracle WSM policies in the Oracle WSM repository
-
The name, latest version, and description of all the Oracle WSM policies in the Oracle WSM repository.
-
The total number of Oracle WSM assertion templates in the repository
-
The name, latest version, and description of all the Oracle WSM assertion templates in the Oracle WSM repository.
-
The creation date and build label of the repository.
A sample Policy Manager Validator page is shown in Figure 16-3.
Figure 16-3 Policy Manager Validator Page
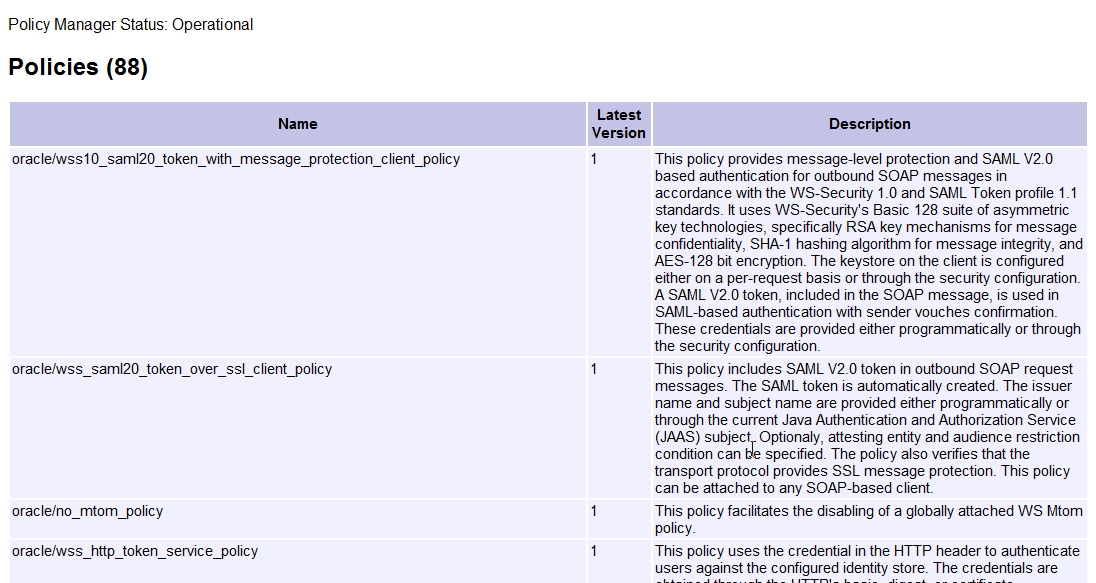
Description of "Figure 16-3 Policy Manager Validator Page"
For details about the Oracle WSM repository, see Chapter 17, "Maintaining the Oracle WSM Repository."
-
Diagnosing Common Problems with Oracle WSM
The following sections describe some common problems you may encounter while using Oracle WSM, as well as possible solutions:
-
Key or Credential Store Error After an Application Invokes Web Service
-
Trust Certificate Error After Application Invokes Web Service
-
Policy Access Error After an Application Invokes Web Service
-
Authorization Error After an Application Invokes Web Service
-
Multiple Authentication Security Policy Error After an Application Invokes Web Service
Unable to Connect to the Policy Manager
The following errors appear when you attempt to connect the Policy Manager:
-
WSM-06157: The repository database is not configured correctly or not running. -
WSM-06160: The policy manager application has not been deployed or is not running. -
WSM-06161: The policy manager application has not been deployed. -
WSM-06162: The policy manager application is not running or is not configured correctly. -
WSM-06159: Cannot connect to the policy manager due to credential issue.
The problem may be:
-
The Policy Manager is down. You can determine if the Policy Manager is down as follows:
-
The state of the Policy Manager in the General area of the Oracle WSM Policy Manager home page, as described in "Diagnosing Problems with Oracle WSM Policy Manager" is shown as shutdown.
-
The status of the wsm-pm internal application on the Farm home page in Enterprise Manager is Down, as shown in Figure 16-4. To access the Farm home page, select Farm_em_domain in the Navigator pane, or select Home from the Farm menu in the left-hand corner of the page.
Figure 16-4 Oracle WSM Policy Manager Shutdown (Farm Page)
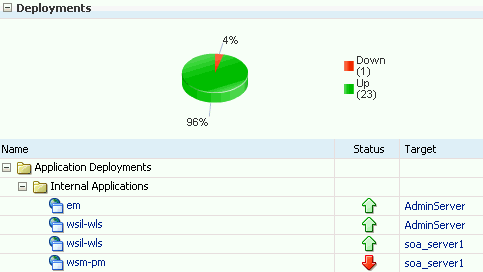
Description of "Figure 16-4 Oracle WSM Policy Manager Shutdown (Farm Page)"
-
An error dialog box similar to the following displays when you attempt to access the Oracle WSM policy management pages in Enterprise Manager. This error information is also written to the diagnostic log file, as described in "Reviewing Sample Logs".
Figure 16-5 Error Message—Oracle WSM Policy Manager Unavailable
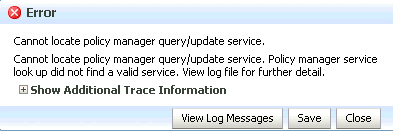
Description of "Figure 16-5 Error Message—Oracle WSM Policy Manager Unavailable"
-
-
The Policy Manager is targeted to an SSL server.
Oracle Web Services Manager (WSM) supports an auto-discovery feature that it uses to locate and connect to an Oracle WSM Policy Manager within the same WebLogic domain. If the domain includes an SSL-configured server that has a Policy Manager deployed, the auto-discovery logic will connect to that Policy Manager and will not try to connect to any Policy Managers deployed on non-SSL servers. To ensure that the secure connection is maintained, the auto-discovery logic will not attempt to connect to a Policy Manager on a non-SSL server, even if the SSL-enabled server goes down. Therefore, even though there is a Policy Manager running, because it is running on a non-SSL enabled server, it is ignored and an error message is displayed.
-
The credential required to access the Policy Manager is invalid or is not authorized.
-
The repository may not be configured correctly.
If the Policy Manager is down:
Restart the wsm-pm application as described in "Starting and Stopping Applications" in Oracle Fusion Middleware Administrator's Guide.
If the Policy Manager is targeted to an SSL Server:
-
Verify that the wsm-pm Policy Manager application is targeted to an SSL server. You can do so using the WebLogic Server Administration Console as described in "Target an Enterprise application to a server" in the Oracle WebLogic Server Administration Console Help.
-
Verify that SSL has been configured correctly and that there are no SSL certificate issues. For additional information, see "Configuring Keystores for SSL".
-
If the SSL-enabled server is down, restart it, and the Policy Manager application, as described in "Starting and Stopping Oracle Fusion Middleware" in Oracle Fusion Middleware Administrator's Guide.
-
If you want to use the Policy Manager on the non-SSL enabled server, untarget the Policy Manager application from the SSL-enabled server. For information about targeting applications to a server, see Managing Deployed Applications in Deploying Applications to Oracle WebLogic Server. To change the target server using the WebLogic Server Administration Console, see "Change target servers" in Oracle WebLogic Server Administration Console Help.
If there is a credential issue when attempting to access the Policy Manager:
By default, the Oracle WSM run time uses the OracleSystemUser account. If you are not using the default user accounts, you need to modify the configuration as described in "Modifying the Default User".
If there is a problem with the repository configuration:
-
Verify that the database and MDS schema are setup correctly. This configuration is performed as part of the installation process. For more information, see Oracle Fusion Middleware Repository Creation Utility User's Guide.
-
Verify that the JDBC configuration is correct. The JDBC configuration is defined when you create the domain using the Oracle Fusion Middleware Configuration Wizard. For more information, see Creating Domains Using the Configuration Wizard.
Key or Credential Store Error After an Application Invokes Web Service
After an application invokes a Web service, a key store or credential store error such as the following appears:
-
WSM-00056: The key <alias_name> is not retrieved -
WSM-00256: The property "Keystore Sign Alias" is not set
The problem may be:
-
The alias for the signature key or encryption key in the Oracle WSM keystore configuration does not exist in the Oracle WSM keystore.
-
The signature key, encryption key, or Oracle WSM keystore password is not synchronized between the keystore file and the keystore configuration for Oracle WSM. That is, at least one of the passwords does not have identical values in both locations.
To verify the alias for the signature key and encryption key in the Oracle WSM keystore configuration exist in the Oracle WSM keystore file:
-
Use Fusion Middleware Control to identify the alias for the signature key and encryption key in the Oracle WSM keystore configuration by performing the procedure in "Configuring the Oracle WSM Keystore".
-
Verify the aliases identified in step 1 exist in the Oracle WSM keystore file. To do so, use the
keytool -listcommand on the Oracle WSM keystore file, as described in step 4 of "Generating Private Keys and Creating the Java Keystore". For detailed information about using the keytool utility, see the keytool - Key and Certificate Management Tool document at the following URL:http://download.oracle.com/javase/6/docs/technotes/tools/windows/keytool.htmlNote:
If you are unable to locate the document at the above URL, you can access it by searching for it on the Search Java SE Technical Documentation Web page at:-
Ensure each alias is synchronized in both the keystore file and the Oracle WSM keystore configuration in the credential store. If they are not, you can edit the alias in the Oracle WSM keystore configuration by performing the procedure described in "Configuring the Oracle WSM Keystore". You can edit the alias in the Oracle WSM keystore file using the
keytool -changealiascommand.Note:
Before you edit an alias, be sure that doing so will not affect any other Web service. -
If the alias for the signature key or encryption key does not exist in the Oracle WSM keystore file, add it as described in "Generating Private Keys and Creating the Java Keystore".
Note:
If you make any changes to the Oracle WSM keystore file usingkeytool, you must restart all Managed Servers in the domain.
-
To ensure that the signature key, encryption key, and Oracle WSM keystore file passwords are each synchronized in the keystore file and the keystore configuration for Oracle WSM:
-
Use
keytoolto reset the passwords in the Oracle WSM keystore file. Because the passwords are not visible, resetting them is the only method to ensure that they have identical respective values in both locations.-
Use the
keytool -storepasswdcommand to reset the Oracle WSM keystore file password. -
Use the
keytool -keypasswdcommand to reset the signature key password and encryption key password.
Note:
After resetting passwords in the Oracle WSM keystore file usingkeytool, you must restart all Managed Servers in the domain. -
-
Use Fusion Middleware Control to reset the passwords in the Oracle WSM keystore configuration to the same respective values you set in step 1, as described in "Configuring the Oracle WSM Keystore".
Trust Certificate Error After Application Invokes Web Service
After an application invokes a Web service, a trust certificate error such as the following appears:
WSM-00138: The path to the certificate is invalid due to exception
The problem may be, if the Web service is advertising its certificate in the Web Services Description Language (WSDL), the client may not be configured correctly to trust that certificate or its issuer.
To verify the client is configured to trust the Web service's certificate advertised in the WSDL or its issuer:
-
Verify the client keystore has either the certificate of the Web service or the certificate of its issuer.
Use the
keytool –listcommand to identify the certificates in the client keystore. If either of the certificates is missing from the client keystore, use thekeytool –importcertcommand to add them.Refer to the keytool - Key and Certificate Management Tool document on the Java SE Technical Documentation Web site for more information about using
keytool. You can access this document at the following URL:http://download.oracle.com/javase/6/docs/technotes/tools/windows/keytool.html -
If the certificate is not published in the service's WSDL, verify that the value for the
keystore.recipient.aliasoverride property of the client policy is identical to the alias of the certificate in the Oracle WSM keystore file.For more information, see "Attaching Client Policies Permitting Overrides".
SAML Assertion Error Appears During Identity Propagation
After an application attempts to propagate a user's identity by calling a different application using Oracle SOA, InvalidSecurityToken, FailedAuthentication, and SAML assertion issuer related errors appear.
The problem may be:
-
The SAML issuer name for the SAML token is not configured or is configured incorrectly.
-
The subject.precedence configuration override is set incorrectly.
-
A user is not logged in on the client. The following error is a symptom of this problem:
WSM-00263: Failed to create SAML token as 'anonymous' user principal found in Subject
To troubleshoot the SAML issuer name configuration:
Verify that the SAML Issuer Name that the client is using is among the issuers configured in the Oracle WebLogic Server domain. To do so, perform the steps described in "Adding an Additional SAML Assertion Issuer Name".
If the SAML Issuer Name that the client is using is not configured as an issuer in the Oracle WebLogic Server domain, Oracle recommends changing the issuer name on the client by updating its saml.issuer.name override to one of the issuers configured in the domain.
If you cannot change the issuer name on the client, you can add its issuer name to the Oracle WebLogic Server domain by performing the steps in the "Adding an Additional SAML Assertion Issuer Name".
Note:
If you make any changes to the issuers configured in the Oracle WebLogic Server domain, you must restart the Managed Server where Oracle WSM is deployed.To troubleshoot the subject.precedence configuration override:
-
Set the subject.precedence override value in your current client policy to false to change the identity to a different user. By default, the subject.precedence override is set to true.
-
Set the appropriate Credential Store Framework key override on the client policy that contains the user name and password of the user you want to send to the service. If an entry for this user does not exist in the Credential Store Framework, you must add it. For more information, see "Configuring the Credential Store"
-
Ensure the appropriate Web Services Identity Permission is set for the client application by performing the steps in "Configuring SAML Web Service Clients for Identity Switching".
If you encountered the "WSM-00263: Failed to create SAML token as 'anonymous' user principal found in Subject" error:
Ensure the client has been authenticated before invoking the Web service. If the Web service is invoked from a Web application, ensure that you have logged into the Web application as an authenticated user, not as a guest user.
Policy Access Error After an Application Invokes Web Service
After an application attempts to invoke a Web service, a policy access error such as the following appears:
-
WSM-06156: The policy URI is missing, empty or contains invalid characters. -
WSM-06158: The referenced policy does not exist in the repository. -
WSM-02017: The document was not found in the repository.
The problem may be:
-
The policy URI is missing or the policy name is misspelled.
-
The Policy Manager is down
-
The policy does not exist in the repository
-
The policy attachment is not in effect due to a cache delay.
To diagnose and solve policy access issues:
-
Verify that the Policy Manager is running as described in "Diagnosing Problems with Oracle WSM Policy Manager" and "Unable to Connect to the Policy Manager".
-
Verify that the mds-owsm datasource connection is reachable and available. For more information, see "Understanding and Managing Data Sources" in Oracle Fusion Middleware Administrator's Guide.
-
Verify that the policy exists in the Oracle WSM repository by viewing the contents of the repository using the Policy Manager Validator page. For details about accessing the Validator page and viewing the contents of the repository, see "Diagnosing Problems with Oracle WSM Policy Manager".
-
If the policy exists in the repository, verify that the policy URI is consistent with the policy URI in the repository.
-
If the policy does not exist in the Oracle WSM repository, do one of the following:
-
For predefined policies:
-
Verify that the repository has been upgraded with all of the latest predefined policies using the
upgradeWSMPolicyRepository()command as described in "Upgrading the Oracle WSM Policies in the Repository". -
Reset the contents of the repository using the
resetWSMPolicyRepositorycommand as described in "Rebuilding the Oracle WSM Repository".
-
-
For a custom policy:
-
Import it into the repository as described in "Importing Web Service Policies". For information on creating a custom policy, see "Creating Web Service Policies".
-
-
-
Check if the user is in a role that has the right permission granted. To modify any roles or permissions, refer to "Modify the User's Group or Role".
-
Verify the policy accessor and cache delay.
The amount of time it takes for a policy attachment to take effect is determined by the Oracle WSM policy accessor and policy cache property settings. By default, this delay can be up to a maximum of 11 minutes. To reduce the amount of the delay, if necessary, you can tune the following cache property settings:
-
Policy Accessor
cache.refresh.initial, default 600000 milliseconds (10 minutes)cache.refresh.repeat, default 600000 milliseconds (10 minutes) -
Policy Cache
cache.tolerance, default is 60000 milliseconds (1 minute)
For details about tuning these properties, see "Configuring Platform Policy Properties".
-
Unable to Access User in Credential Store
When Oracle WSM attempts to access a user in the credential store, an error such as the following occurs:
WSM-00015: The user name is missing
Problem
Oracle WSM cannot locate the user name in the credential store. This can be caused by any of the following:
-
The credential map
oracle.wsm.securitydoes not exist in the credential store. -
The user is not listed in the map used by Oracle WSM.
-
The csf key for the entry does not exist in the credential store.
Solution
Verify that the credential map oracle.wsm.security exists in the credential store. Oracle WSM only reads from this credential store map.
To determine if the oracle.wsm.security credential map exists in the credential store, refer to the procedure in "Configuring the Credential Store".
If your application uses a credential map other than oracle.wsm.security, ensure that any users that Oracle OWSM needs to access are duplicated in the oracle.wsm.security credential map.
Authorization Error After an Application Invokes Web Service
After an application attempts to invoke a Web service, an error such as the following appears:
java.security.AccessControlException: access denied (oracle.wsm.security.WSFunctionPermission
Generally this is not really a problem rather intended behavior; that is, the system was unable to authorize the user for the action that the user is attempting. To debug check the calling server diagnostic log for the authorization error. The error may look similar to the following:
2011-01-06T22:15:43.691-08:00] [SalesServer_2] [ERROR] [] [oracle.jbo.server.svc.ServicePermissionCheckInterceptor_w2f8f5_Impl] [tid: [ACTIVE].ExecuteThread: '7' for queue: 'weblogic.kernel.Default (self-tuning)'] [userId: FMW_APPS_CRM_SELFSERVICE_ADF_APPID] [ecid: 004aIPwzJDGE8TQRyaI7T00001WJ00EJ8f,0:1:3:1:11:0x5f5e189:6:1] [WEBSERVICE_PORT.name: PartnerServiceSoapHttpPort] [APP: SalesApp#V2.0] [J2EE_MODULE.name: partnerCenterCorePublicModel] [WEBSERVICE.name: PartnerService] [J2EE_APP.name: SalesApp_V2.0] [URI: /partnerCenterCorePublicModel/PartnerService] [[ java.security.AccessControlException: access denied (oracle.wsm.security.WSFunctionPermission http://xmlns.oracle.com/apps/partnerMgmt/partnerCenter/PartnerService#updatePartner invoke) at java.security.AccessControlContext.checkPermission(AccessControlContext.java:323) at java.security.AccessController.checkPermission(AccessController.java:546) at oracle.jbo.server.svc.ServicePermissionCheckInterceptor.checkPermission(ServicePermissionCheckInterceptor.java:103) at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
Pay careful attention to the following information in the log, which is shown in bold text in the example above.
-
The application stripe name – which is
SalesApp#V2.0in the above log. Make sure it matches what you configured for your application. For information about how to configure the stripe name, see "Configuring the Servlet Filter and the EJB Interceptor" in Oracle Fusion Middleware Application Security Guide. -
The permission grant, which is comprised of the following:
-
Resource name , which is
http://xmlns.oracle.com/apps/partnerMgmt/partnerCenter/PartnerService#updatePartnerin the above log. -
Action, which is
invokein the above log.
Both of these pieces of information must be specified correctly in your permission grant. For more information, see "How Authorization Permissions Are Determined".
-
If your application uses an LDAP-based authenticator and stores all roles in the LDAP, ensure that Oracle WSM can access the users and roles as described in "Modifying the Default User".
Timestamp Error After an Application Invokes Web Service
After an application invokes a Web service, a timestamp or clockSkew error such as the following occurs:
WSM-00060: Error validating timestamp
The problem will either manifest itself as a timestamp validation or clockSkew error as shown below:
Caused By: FAULT CODE: InvalidSecurityToken FAULT MESSAGE: Found invalid condition "on or after" in SAML assertion. Current Time:Fri Feb 11 22:16:42 IST 2011, clockSkew:300000 milli seconds, NotOnOrAfter Time:Fri Feb 11 14:21:42 IST 2011.
This problem usually happens if your server and client clocks are more than five minutes apart after they are converted to the same time zone.
Change your client or server clock in one of the following ways so that they are within five minutes, both set to the correct time:
-
Adjust the clockSkew as described in "Tuning Web Service Security Policy Enforcement".
-
Set the system clock
-
Use an ntp server to maintain the time
Multiple Authentication Security Policy Error After an Application Invokes Web Service
After an application invokes a Web service, a multiple authentication policy error such as the following appears:
WSM-01778: Attaching multiple authentication security policies is not supported. Only one authentication security policy can be attached to a policy subject.
More than one authentication policy was attached to a subject. This can happen if you have two policy sets that each attach an authentication policy to the same resource type, such as a Web service. For example, if you have two policy sets defined in the Oracle WSM repository for your domain and one defines the policy scope as Domain("domain_name") and the other as Domain ("*"). The following listing illustrates an example of this scenario.
wls:/soa_domain/serverConfig> displayPolicySet('default-domain-ws-domain_gpa')
Policy Set Details:
Name: default-domain-ws-domain_gpa
Type of Resources: Web Service Endpoint
Scope of Resources: Domain("fusion_domain_gpa")
Description: Global policy attachments for Web Service Endpoint resources.
Enabled: true
Policy Reference: security : oracle/wss_saml_or_username_token_service_policy, enabled=true
wls:/soa_domain/serverConfig> displayPolicySet('default-domain-ws-domain')
Policy Set Details:
Name: default-domain-ws-domain
Type of Resources: Web Service Endpoint
Scope of Resources: Domain("* ")
Description: Global policy attachments for Web Service Endpoint resources.
Enabled: true
Policy Reference: security : oracle/wss_saml_or_username_token_service_policy, enabled=true.
In this example, there are two policy sets with different names pointing to same resource type on the domain.
To verify if you have multiple policy sets attempting to attach authentication policies:
-
Use the
listPolicySets()command to display a list of the policy sets in the domain. For more information about this command, see "Displaying a List of Policy Sets Using WLST". -
Use the
displayPolicySetcommand to view the contents of each of the policy sets and view the attached policies and the type and scope of resources. For information about using this command, see "Viewing the Configuration of a Policy Set", "Using WLST". -
If a conflict is found, do one of the following:
-
Delete one of the policy sets as described in "Deleting a Policy Set".
-
Disable one of the policy sets as described in "Enabling and Disabling a Policy Set".
-
Diagnosing Policy Attachment Issues Using WLST
To ensure that there are no conflicts between directly-attached policies and policies attached globally using policy sets, use the following WLST commands:
-
listWebServices (detail="true")— Displays a list of the Web services in a domain including endpoint configuration, the effective set of policies attached to each endpoint, the secure status of the endpoint, and if the endpoint has a valid configuration. For information about using this command, see "Viewing the Web Services in a Domain Using WLST". -
listWebServiceClients (detail="true")— Displays a list of the Web service clients in a domain including endpoint configuration, the effective set of policies attached to each endpoint, the secure status of the endpoint, and if the endpoint has a valid configuration. For information about using this command, see "Viewing Web Service Clients", "Using WLST"Note:
An endpoint is considered secure if the policies attached to it (either directly, or externally using a policy set) enforce authentication, authorization, or message protection behaviors.
If your configuration includes policies attached globally using policy sets, you can view information about the policy sets using the following commands:
-
listPolicySets()— Displays a list of the policy sets in the repository. For information about using this command, see "Displaying a List of Policy Sets Using WLST". -
displayPolicySet()— Displays the configuration of a specific policy set. For information about using this command, see "Viewing the Configuration of a Policy Set", "Using WLST".
To view the effective policies for an endpoint using Fusion Middleware Control, see "Viewing the Policies That are Attached to a Web Service".
Sample Valid Configuration Output with Globally Attached Policies
The following example shows sample output from the listWebServices(detail="true") command for a valid configuration. The globally attached policy is shown in bold text.
/jrfServer_domain/jrfServer/jaxws-sut-no-policy:
moduleName=jaxws-service, moduleType=web, serviceName=TestService
enableTestPage: true
enableWSDL: true
TestPort http://host.oracle.com:1234/jaxws-service/TestService
enable: true
enableREST: false
enableSOAP: true
maxRequestSize: -1
loggingLevel: NULL
(global) security: oracle/wss11_message_protection_service_policy, enabled=true
/policysets/global/all-domains-default-web-service-policies: Domain("*")
Attached policy or policies are valid; endpoint is secure.
Sample Valid Configuration Output with Directly Attached Policies Only
The following example shows sample output from the listWebServices(detail="true") command for a valid configuration. The directly attached policy is shown in bold text.
/jrfServer_domain/jrfServer/jaxws-sut:
moduleName=jaxws-sut-service, moduleType=web, serviceName=TestService
enableTestPage: true
enableWSDL: true
TestPort http://host.oracle.com:1234/jaxws-sut-service/TestService
enable: true
enableREST: false
enableSOAP: true
maxRequestSize: -1
loggingLevel: NULL
management: oracle/log_policy, enabled=true
security: oracle/wss_username_token_service_policy, enabled=true
Attached policy or policies are valid; endpoint is secure.
Diagnosing Problems Using Logs
Oracle Fusion Middleware components, including Web services, generate log files containing messages that record all types of events, including startup and shutdown information, errors, warning messages, access information on HTTP requests, and so on. Each log message includes specific information such as time, component ID, and user to assist you in pinpointing and diagnosing problems that arise.
You can review log messages to diagnose problems with specific components, such as Web services. There are two categories of log files that you can reference to assist in diagnosing problems with Web services:
-
Diagnostic logs—Enable you to access diagnostic data about specific feature components in Oracle Fusion Middleware. For more information, see "Using Diagnostic Logs for Web Services".
There is a set of predefined diagnostic loggers. You can configure your own diagnostic logger, as described in "Configuring Log Files for a Web Service".
-
Message logs—Enable you to view elements of the SOAP message request. You control message log creation using policies. For more information, see "Using Message Logs for Web Services".
For more information about logging in Oracle Fusion Middleware, see "Managing Log Files and Diagnostic Data" in Oracle Fusion Middleware Administrator's Guide.
The following sections describe how to use diagnostic and message logs to diagnose problems. A set of sample logs is provided at the end of this section.
Using Diagnostic Logs for Web Services
Diagnostic logs enable you to access diagnostic data about specific feature components in Oracle Fusion Middleware.
The following sections describe how to view and manage diagnostic log files:
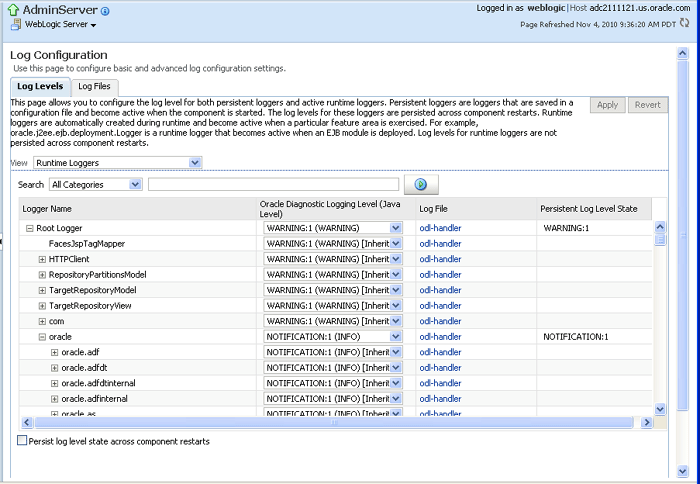
Setting the Log Level for Diagnostic Logs
You set the logging level for Web service and Oracle WSM components at the WebLogic Server level, using the Log Configuration page.
In addition, you can override the log levels set at the server level for a specific Web service endpoint from the Web Service Endpoint page. The logging level set at the Web service endpoint level must be "finer grained" than the level set at the WebLogic Server level. Otherwise, the logging level set at the WebLogic Server level will be used.
The following procedures describe how to set the log level for diagnostic logs at the WebLogic Server and Web service endpoint levels. For more information, see "Setting the Level of Information Written to Log Files" in Oracle Fusion Middleware Administrator's Guide.
To set the log level for diagnostics logs at the WebLogic Server level:
-
Navigate to the WebLogic Server for which you want to configure a logger.
-
In the navigator pane, expand WebLogic Domain.
-
Expand the domain.
-
Select the desired server from the list.
The WebLogic Server home page is displayed.
-
-
From the WebLogic Sever menu, select Logs > Log Configuration.
The Log Configuration page is displayed.
-
Select the Log Levels tab.
The list of loggers is displayed, as shown in Figure 16-6.
The Log Levels page shows the name of the logger, the current logging level, which you can edit, and the associated log file (for example, olh-handler). For information about configuring the log files, see "Configuring Log Files for a Web Service".
-
Expand Root Logger.
-
Expand oracle.
-
Set the logging level for one or more of the following components:
-
oracle.webservices—Web service components.
-
oracle.wsm—Oracle WSM components.
You can fine tune the logging level by expanding either of the above components and specifying the logging level at the subcomponent level.
To change the logging level for a logger, navigate to the logger in the Logger Name column and select the desired logging level from the Oracle Diagnostic Logging Level (Java Level) dropdown menu.
For example, select TRACE:32 from the dropdown menu associated with the oracle.wsm logger.
By default, the logging levels are inherited from the parent and set to NOTIFICATION: 1 (INFO) for the Web service and Oracle WSM components and subcomponents.
-
-
Click Apply to store the new logging level.
To set the log level for diagnostic logs at the Web service endpoint level:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint".
-
Click the Configuration tab.
-
Set the Logging Level field to one of the following settings: Severe, Warning, Information, Configuration, Fine, Finer, Finest or NULL.
Note:
You can also set the log level at the Web service endpoint using thesetWebServiceConfigurationWLST command. Set theloggingLevelproperty of theitemPropertiesargument to one of the following settings: SEVERE, WARNING, INFO, CONFIG, FINE, FINER, FINEST, or NULL. For details about using this command, see "Using WLST" in "Configuring the Web Service Endpoint".
Viewing Diagnostic Logs
You can view the diagnostic log files for an ADF and WebCenter Web service endpoint from the Log Messages page.
To view diagnostic logs for a Web service endpoint:
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint", and in the Quick Links section of the Web Services Endpoint page (top right), click Diagnostic Logs.
Note:
You can view a summary of all faults incurred by the Web services in your application. For more information, see "Monitoring the Performance of Web Services".The Log Messages page is displayed, as shown in the following figure.
Click on a message in the message area to view more details at the bottom of the page. If desired, you can export a message to a text, XML, or CSV file by selecting the messages on the list and clicking Export Messages to File.
You can control the message content displayed using the following controls:
-
Search—Modify the search criteria. For more information, see "Filtering Diagnostic Logs".
-
View menu—Select the columns to display in the table. Click on a particular column to sort contents up or down.
-
Show menu—Group messages by type or ID, or view them in chronological order.
-
View Related Messages—View messages related to those selected on the list.
-
Broaden Target Scope—Broaden the scope of messages displayed. You can broaden the scope to include all messages for the domain, WebLogic Server, or Farm.
-
Refresh menu—Specify an automatic or manual refresh rate.
To view the contents of a generated log file:
-
Click the log file icon associated with a message to view the contents of that log file.
-
Click Target Log Files... to display the Log Files page and view or download the contents of all generated log files.
For more information, see "Viewing and Searching Log Files" in Oracle Fusion Middleware Administrator's Guide.
Filtering Diagnostic Logs
By default, the Log Messages page displays a summary of diagnostic messages logged over the last hour.
-
Filter the messages that are displayed by updating the search criteria using the following fields:
-
Date Range—Set the date range to one of the following:
-
Most Recent—Set the amount of time to define the duration.
-
Time Interval—Set the start and end dates to define the interval.
-
-
Message Types—Select the message types that you want to display.
-
Add Fields—Add other message fields to your search criteria, such as Message ID, Component, and so on.
-
-
Click Search once you have set the fields, as desired.
The messages area is updated with the filtered results.
For more information, see "Viewing and Searching Log Files" in Oracle Fusion Middleware Administrator's Guide.
Logging Oracle WSM Debug Messages
To debug Oracle WSM, pass one of the following properties when starting WebLogic Server, as required. For more information, see "Starting and Stopping Servers" in Managing Server Startup and Shutdown for Oracle WebLogic Server.
Note:
Enabling one or more of these properties may negatively impact performance for very large messages. When enabled, Oracle WSM creates temporary buffers which will result in additional load on the Java garbage collector.Table 16-1 Startup Properties for Logging Oracle WSM Debug Messages
| Startup Property | Description |
|---|---|
|
|
Logs the sequence of bytes produced during a signature verification failure. Verification errors are output to |
|
|
Verifies that the sequence of bytes produced during signature generation canonicalization and signature verification match. Verification errors are output to |
|
|
Logs the sequence of bytes produced following a decryption failure before XML parsing. Verification errors are output to |
Using Message Logs for Web Services
Message logs enable you to access the contents of the SOAP message requests and responses for ADF and WebCenter Web services and clients. Messages logs are stored in a log file separate from the diagnostic messages, by default.
The following sections describe how to view and manage message log files:
Configuring Message Logs
You configure message logs for a Web service or client in one of the following ways:
-
Attach a policy that contains a logging assertion to the Web service or client.
There is one predefined logging assertion template: oracle/security_log_template, described in "oracle/security_log_template". This template is configured to log the entire SOAP message for the Web service request and response. By default, all predefined Web service security policies use this logging assertion to capture the entire SOAP message before and after the primary security assertion is executed. By default, the log assertion is not enforced. You must enable it in order for the SOAP message to be logged in message logs, as described in "Enabling or Disabling Assertions Within a Policy". It is recommended that the logging assertion be enabled for debugging and auditing purposes only.
-
Attach the oracle/log_policy policy to the Web service or client. For more information, see "oracle/log_policy".
-
Create your own logging policy or assertion template to further refine the elements of the SOAP message that are logged for the Web service request and response.
For example, you may wish to view only the SOAP body of the request message. To create a new policy, following the procedure described in "Creating Web Service Policies". You may wish to create a copy of the oracle/security_log_template assertion template and configure it for use in the new policy. For more information about creating a new assertion template, see "Creating an Assertion Template".
Viewing Message Logs
You can view the message log files for an ADF and WebCenter Web service endpoint from the Log Messages page.
To view message logs for a Web service endpoint:
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint", and in the Quick Links section of the Web Services Endpoint page (top right), click Message Logs.
The Log Messages page is displayed, similar to Figure 16-7. For more details about the contents of the Log Messages page, see "Viewing Diagnostic Logs".
Filtering Message Logs
By default, the Log Messages page displays a summary of SOAP messages logged over the last hour. You can filter the messages that are displayed by updating the search criteria. The process is the same as for diagnostic logs; for more information, see "Filtering Diagnostic Logs".
By default, the Component and Module message fields are included as part of the Search criteria for message logs. The Component field is set to the WebLogic Server name; the Module field is set to oracle.wsm.msg.logging, which is the name of the message logging component.
Reviewing Sample Logs
The following sections provide excerpts from sample logs, demonstrating how to diagnose specific problems using the log entries.
Sample Log: Oracle WSM Policy Manager Not Available
The following sample log excerpt indicates that the Oracle WSM Policy Manager is down. To resolve this issue, restart the wsm-pm application, as described in "Starting and Stopping Applications Using" in Oracle Fusion Middleware Administrator's Guide.
2009-02-16 16:21:28,029 [[ACTIVE] ExecuteThread: '4' for queue: 'weblogic.kernel.Default (self-tuning)'] ERROR policymgr.PolicyManagerModelBean logp.251 - Service lookup failed with URL:t3://stadk13.us.oracle.com:7001/wsm-pm oracle.wsm.policymanager.PolicyManagerException: WSM-02118 : The query service cannot be created. ...
Sample Log: Security Keystore Not Configured
The following sample log excerpt indicates that an Oracle WSM security policy with message protection was applied, but the keystore was not configured. To resolve this security fault, configure the keystore, as described in "Configuring Keystores for Message Protection".
Feb 16, 2009 5:29:56 PM oracle.wsm.common.logging.WsmMessageLogger logSevere SEVERE: The specified Keystore file /scratch/sbollapa/stage131/user_projects/domains/sai131_domain/config/fmwconfig/default-keystore.jks cannot be found; it either does not exist or its path is not included in the application classpath. Feb 16, 2009 5:29:56 PM oracle.wsm.common.logging.WsmMessageLogger logSevere SEVERE: Keystore is not properly configured in jps config. Feb 16, 2009 5:29:56 PM oracle.wsm.common.logging.WsmLogUtil log SEVERE: failure in OWSM Agent processRequest, category=security, function=agent.function.client, application=default, composite=pe3test3, modelObj=Service1, + policy=null, policyVersion=null, assertionName=null oracle.wsm.common.sdk.WSMException: WSM-00101 : The specified Keystore file /scratch/sbollapa/stage131/user_projects/domains/sai131_domain/config/fmwconfig/default-keystore.jks cannot be found; it either does not exist or its path is not included in the application classpath. ...
Sample Log: Certificate Not Available
The following sample log excerpt indicates that an Oracle WSM security policy with message protection was applied that required a security certificate that was not available in the keystore. To resolve this security fault, configure the keystore with a certificate, as described in "Obtaining a Trusted Certificate and Importing it into the Keystore".
[2009-04-15T04:07:02.821-07:00] [jrfServer] [ERROR] [WSM-000062] [oracle.wsm.resources.security] [tid: [ACTIVE].ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'] [userId: <anonymous>] [ecid: 0000I2dTFG7DScT6uBe9UH19tRyv000000,0:1] [WEBSERVICE_PORT.name: NonCAAsCAMessageProtectionPolicyPort] [APP: jaxwsservices] [J2EE_MODULE.name: NonCAAsCAMessageProtectionPolicy] [WEBSERVICE.name: NonCAAsCAMessageProtectionPolicyService] [J2EE_APP.name: jaxwsservices] [arg: oracle.wsm.security.SecurityException: WSM-00062 : The path to the certificate used for the signature is invalid.] [2009-04-15T04:07:02.810-07:00] [jrfServer] [NOTIFICATION] [] [oracle.wsm.security.policy.scenario.processor.Wss11X509TokenProcessor] [tid: [ACTIVE].ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'] [userId: <anonymous>] [ecid: 0000I2dTFG7DScT6uBe9UH19tRyv000000,0:1] [WEBSERVICE_PORT.name: NonCAAsCAMessageProtectionPolicyPort] [APP: jaxwsservices] [J2EE_MODULE.name: NonCAAsCAMessageProtectionPolicy] [WEBSERVICE.name: NonCAAsCAMessageProtectionPolicyService] [J2EE_APP.name: jaxwsservices] Certificate path validation failed for signing certificate [2009-04-15T04:07:02.821-07:00] [jrfServer] [ERROR] [WSM-00006] [oracle.wsm.resources.security] [tid: [ACTIVE].ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'] [userId: <anonymous>] [ecid: 0000I2dTFG7DScT6uBe9UH19tRyv000000,0:1] [WEBSERVICE_PORT.name: NonCAAsCAMessageProtectionPolicyPort] [APP: jaxwsservices] [J2EE_MODULE.name: NonCAAsCAMessageProtectionPolicy] [WEBSERVICE.name: NonCAAsCAMessageProtectionPolicyService] [J2EE_APP.name: jaxwsservices] [arg: oracle.wsm.security.SecurityException: WSM-00062 : The path to the certificate used for the signature is invalid.] Error in receiving the request: oracle.wsm.security.SecurityException: WSM-00062 : The path to the certificate used for the signature is invalid.
Configuring Log Files for a Web Service
To further organize your logging data, you can configure the log files for a Web service. You can configure log files for SOA, ADF, and Web Center services.
The following table defines the default log files that are relevant to Oracle WSM.
Table 16-2 Default Log Files for Oracle WSM
| Default Log File | Description |
|---|---|
|
odl-handler |
Logs general diagnostic data for the Java EE components in the server. |
|
owsm-message-handler |
Logs SOAP messages as per Oracle WSM logging policies. |
The following procedure describes how to set the log level for diagnostic logs at the WebLogic Server and Web service endpoint levels.
For more information about using Fusion Middleware Control or WLST to set the log levels, see "Setting the Level of Information Written to Log Files" in Oracle Fusion Middleware Administrator's Guide.
To configure the log files for a Web service:
-
Navigate to the WebLogic Server for which you want to configure a logger.
-
In the navigator pane, expand WebLogic Domain.
-
Expand the domain.
-
Select the desired server from the list.
The WebLogic Server home page is displayed.
-
-
From the WebLogic Sever menu, select Logs > Log Configuration.
The Log Configuration page is displayed.
-
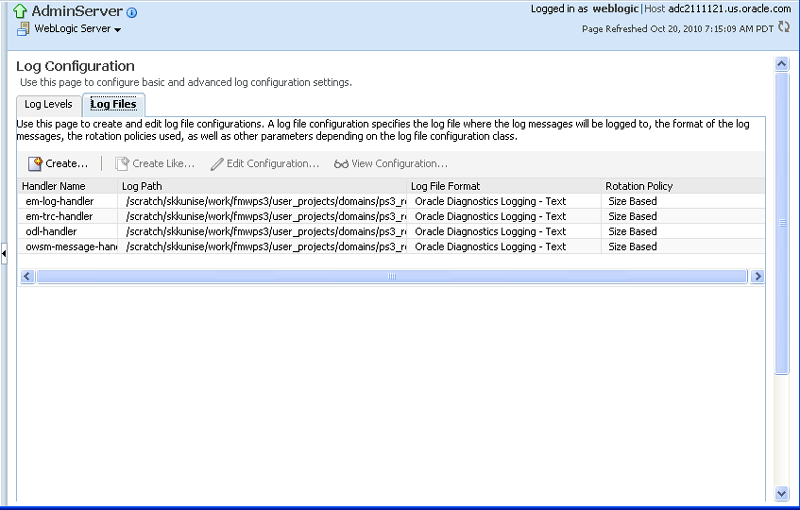
Select the Log Files tab.
The current list of log files is displayed, as shown in Figure 16-8. The Log Configuration page shows the currently configured log path, file format, and rotation policy.
-
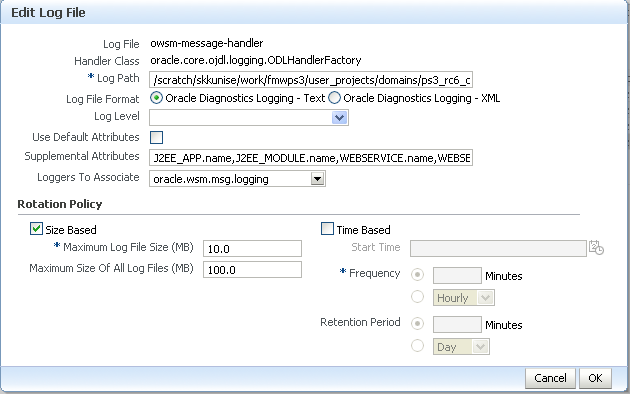
If you wish to edit the log policy configuration, select the log file in the list and click Edit Configuration . . ..
The Edit Log File page is displayed.
-
Edit the log file information, as required.
Table 16-3 Fields in Edit Log File Page
Field Description Log Path
Path to the log file. This field is required.
Log File Format
Format of the log file. Valid values are text or XML.
Log Level
Default log level for the logger. Select a log level from the list. Valid values include:
-
INCIDENT_ERROR:1 (SEVERE+100)
-
ERROR:1 (SEVERE)
-
WARNING:1 (WARNING)
-
NOTIFICATION:1 (INFO)
-
NOTIFICATION:16 (CONFIG)
-
TRACE:1 (FINE)
-
TRACE:16 (FINER)
-
TRACE:32 (FINEST)
Use Default Attributes
Flag that specifies whether to use default attributes for the logger.
Supplemental Attributes
Supplemental attributes required.
Loggers to Associate
Components to associate with the logger.
Rotation Policy
Specify whether you wish to rotate log files based on file size of length of time. For more information, see "Configuring Log File Rotation" in Oracle Fusion Middleware Administrator's Guide.
If Size Based is selected as the rotational policy, Maximum Log Files Size is a required field. If Time Based is selected as the rotational policy, Frequency is a required field.
-
-
Click OK to edit the log file configuration.