| Oracle® Communications Service Broker Security Guide Release 6.0 Part Number E26766-01 |
|
|
View PDF |
| Oracle® Communications Service Broker Security Guide Release 6.0 Part Number E26766-01 |
|
|
View PDF |
This chapter describes the security model for Oracle Communications Service Broker and explains how to configure it.
Service Broker is a flexible product designed to community with a wide variety of other network nodes and applications. Consequently the there are also a wide variety of security concerns when dealing with Service broker security that explained in "Implementing Service Broker Securely".
This chapter assumes that you have already installed the operating system required by Service Broker, and then installed Service Broker itself. For details see Oracle Communications Service Broker Installation Guide.
By default Service Broker is configured to be as secure as possible. If you disabled any of these security settings to create a test and evaluation system, be sure enable them before starting a productions implementation
This section describes recommended deployment configurations for a secure Service Broker implementation. Configure Service Broker security with these steps:
Install the operating system that Service Broker runs on.
The first step in creating a Service Broker implementation is to install the operation system it runs on. See your operating system documentation for instructions on how to install it securely. Also see "Basic Security Considerations"
Install Service Broker.
See Oracle Communications Service Broker Installation Guide for details on installation. By default Service Broker is configured to be as secure as possible. You may have disabled these security settings when you created a test and evaluation system. Be sure enable the security settings before starting a productions implementation.
Change the default ports. See "Changing Default Ports" for details.
Maintain a high level of password security. See "Securing Passwords" for details.
(As needed) Secure clusters. See "Securing Clusters" for details.
Configure domain security settings with the Service Broker properties files. See "Configuring Domain Security in the Service Broker Property Files" for information.
Secure the Service Broker Managed Servers. See "Securing Managed Servers" for details.
Set up a Public Key Infrastructure to store SSL/TLS credentials. See "Set Up the Public Key Infrastructure" for information.
(As needed) Set up Credential Store for storing non-keystore credentials. See "Set Up a Credential Store" for information.
Set up telecom protocol traffic security. See "Set Up Network Communication End Points" for details.
Configure your server firewalls. See "Securing Service Broker with Firewalls" for details.
Configure your Service Broker network entry points, routing, and aliases (IMs, OE, and SSUs). See "Set Up Network Communication End Points" for details.
(As needed) Configure protocol security support. See "Securing Network Traffic with Protocol-Specific Security" for details.
Configure security for other Oracle products. See "Related Documents" for details.
These steps are explained in the sections that follow.
After installing Service Broker be sure to change all the default ports, and continue doing so as you complete the post installation steps listed in Oracle Communications Service Broker Installation Guide.
Table 2-1 lists the default server port numbers that Service Broker uses by default and where to change them.
Table 2-1 Service Broker Default Server Ports
| Component/Protocol | Port Number | Description |
|---|---|---|
|
Administration Console (Web) |
9001 for HTTPS 9000 for HTTP |
Set in the hosting.properties and web.properties property files. See the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide for details. |
|
Policy Designer Interface |
8091 for HTTPS 8090 for HTTP |
Set in the oracle.ocsb.app.rcc.pcrf.gui.port or pcrf.gui.http.port.secure system properties. For details see the discussion on configuring Service Broker for Policy Controller in Oracle Communications Service Broker Policy Controller Implementation Guide. |
|
Admin Port (for Administrator Console to Managed Server communication) |
8901 for HTTPS 8900 for HTTP |
Set in the Admin Port entry when creating a Managed Server. For details see the discussion on post installation tasks in Oracle Communications Service Broker Installation Guide. |
|
Managed Server JMX JRMP port |
10003 |
Set in the JMX JRMP port entry when creating a Managed Server. For details see the discussion on post installation tasks in Oracle Communications Service Broker Installation Guide |
|
JMX Registry port |
10103 |
Set in the JMX Registry port entry when creating the Managed Server. For details see the discussion on post installation tasks in Oracle Communications Service Broker Installation Guide |
|
Log4J socket server port |
4096 |
The common.properties property file. See the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide for details. |
|
IP Multicast port |
1024 |
Set in the common.properties property file. See the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide for details. |
|
Multicast Port |
1025 |
The common.properties property file. See the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide for details. |
|
Profile Database Server IP |
1521 |
Set in SSU WEB SERVICES. For details see the discussion on enabling subscriber profile service connectivity in Oracle Communications Service Broker Subscriber Store User's Guide. |
|
Diameter |
3588 |
Set in the SSU DIAMETER. For details see the discussion on configuring Diameter signaling server units in Oracle Communications Service Broker Signaling Domain Configuration Guide. |
|
Radius |
1812-Authentication 1813- Accounting |
You set a range of NAS ports to use in the Radius SSU. For details see the discussion on configuring RADIUS signaling server units in Oracle Communications Service Broker Signaling Domain Configuration Guide. |
|
HTTP |
None |
Set in SSU WEB SERVICES. For details see the discussion on configuring the web services signaling server units in Oracle Communications Service Broker Signaling Domain Configuration Guide. |
|
SMPP |
None |
Set in the SSU SMPP. For details see the discussion on configuring SMPP signaling server units in Oracle Communications Service Broker Signaling Domain Configuration Guide. |
|
SS7 |
None |
Set in one of the SS7 SSU, depending on the SS7 protocol used. For details see the discussion on configuring the SS7 Signaling Server Unit for your protocol in Oracle Communications Service Broker Signaling Domain Configuration Guide. |
|
SIP |
5060 |
Set in the SIP SSU. For details see the discussion on configuring SIP signaling server units in Oracle Communications Service Broker Signaling Domain Configuration Guide |
There are no default password that you need to change. Passwords are all created by you during installation.
Service Broker provides a high level of flexibility in securing the Web Administration Console password by using the common.properties file settings. For example, you can change required password length, or its requirement to include an integer. See the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide for details on the settings.
You secure the Coherence cluster using the standard Coherence configuration settings.
Oracle recommends that you secure the cluster by creating a Coherence configuration override file, packaging it as an OSGI bundle fragment and deploying it.
For more information on concepts of the Coherence security, refer to Oracle Coherence 3.7 Security Guide.
For information on how to create a Coherence configuration override file and details on the available security options, see Oracle Coherence Release 3.7 Developer's Guide, section Operational Configuration Elements, and Oracle Coherence Security Guide.
Both documents are available from Oracle Coherence Knowledge Base:
http://coherence.oracle.com/display/COH/Oracle+Coherence+Knowledge+Base+Home
The Coherence operational override configuration file must be named tangosol-coherence-override-axia.xml in order to complement, rather than replace, the override settings already defined by Service Broker.
For information on how to create an OSGi bundle fragment, refer to OSGi Service Platform Release 4 Core specification, section 3.14 Fragment Bundles. The specification can be downloaded from:
http://www.osgi.org/Release4/Download
The fragment host for the OSGi fragment bundle must be oracle.axia.storage.provider.coherence.
Service Broker collects it's processing and signalling servers into domains the are protected first by the firewalls that secure your physical server, second by HTTPS security, and finally using file system-level security within the server.
In Oracle Communications Service Broker System Administrator's Guide, see the discussion about domains for general information about domains, and the discussions on domain configuration security and hosted domain security for specifics on protecting Service Broker domains.
Most of Service Broker's application-facing security settings are contained in these property files:
Oracle_home/ocsb60/admin_console/properties
common.properties - Contains property settings that control all actions associated with the Administration Console, which means this is where most of Service Broker's security settings are.
hosting.properties - Contains properties settings that control hosted domains. See the discussion on security for the domain configuration in Oracle Communications Service Broker System Administrator's Guide for details.
script.properties - Contains properties settings for the scripting engine
standalone.properties - Contains property settings for a standalone Web Administration Console.
web.properties - Contains property settings for the web Administration Console server.
Domain_home/Domain_name/domain.properties - contains domain-specific properties settings. Do not change any of these settings, they are not configurable.
Oracle_home/ocsb60/managed_server/server.properties - Contains properties settings for the Managed Server.
For a listing and descriptions of the security settings in these files, see:
The system administrators reference appendix in Oracle Communications Service Broker System Administrator's Guide.
The properties files themselves.
Each Managed Server contains a server.properties file in Oracle_home/managed_server that contains security settings such as a truststore name to use hostname verification. Make changes to these settings before starting and running a production Service Broker implementation. For details see the system administrator's reference in Oracle Communications Service Broker System Administrator's Guide.
You use the keytool program to create the public key infrastructure (PKI) keystores and truststores required for Service Broker to communicate with applications and web entities that support SSL. For details on setting up the PKI see these discussions on configuring security between Service Broker components in Oracle Communications Service Broker System Administrator's Guide.
Service Broker provides a Credential Store feature to store credentials for applications and protocols that use username/password credentials or keystores for access. For details on setting up the Credential Store, see securing credentials with Credential Store for in Oracle Communications Service Broker System Administrator's Guide.
Service Broker communicates with Telecom networks using a variety of supported IMS and SS7-based protocols. You secure communication with network elements by creating Signaling Server Units (SSUs) that are network communication end points for the network traffic. Each protocol SSU has its own security features based on the individual precool. See "Securing Network Communication" for details on securing traffic for individual protocols.
Figure 2-1 shows a typical Service Broker production deployment. Oracle recommends that you protect Service Broker from security risks by configuring firewalls between each the Service Broker processing layers, and between Service Broker and any network traffic. See your firewall product documentation for information on how to set them up with Service Broker.
Because Service Broker supports a variety of Protocols, it relies on the security features of those individual protocols for higher-level security support. The combination of firewall protection and protocol-level security support protect Service Broker from network security risks.
The Service Broker Service controller features mediate between various telecom network protocols. Securing communication protocols mainly involves creating virtual “white lists” of trusted systems to communicate with.
You have the option of using either HTTP or HTTPS for test and evaluation Service Broker implementations, but production implementations must use the security provided by HTTPS/SSL/TLS. All web applications that you use with Service Broker must support HTTPS/SSL/TLS features.
The HTTPS/SSL/TLS network traffic that passes to Service Broker is protected by HTTPS/SSL/TLS security, and all applications and internet entities must support HTTPS to work with Service Broker.
During installation, you configure the keystores and truststores that Service Broker uses to authenticate HTTPS traffic. Figure 2-2 shows how the Service Broker SSU and PN servers share the stores. See Oracle Communications Service Broker System Administrator's Guide for details on setting the keystores and truststores up.
Service Broker also includes a Credential Store feature for programs that use username/password credentials instead of HTTPS-style certificates (for example, LDAP servers). See Oracle Communications Service Broker System Administrator's Guide for details on setting up Credential Stores.
Figure 2-2 Service Broker HTTPS Keystores and Truststores
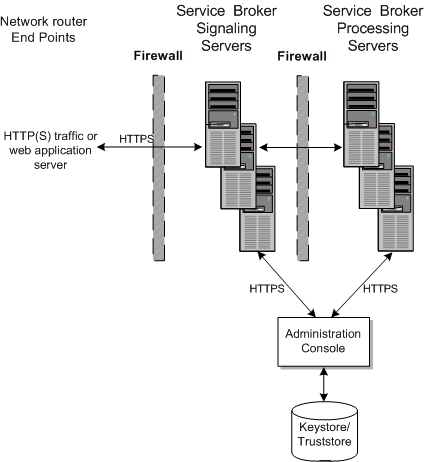
The Service Broker SVC feature application runs inside of Service Broker so it is protected from your web application server and Internet nodes by two layers of firewall and HTTPS support.
Figure 2-3 shows a Service Broker implementation with the SVC and VPN features configured. Both of these features run inside Service Broker in a Processing Server. The Processing Server executes the RESTful interface that these features are base on. Once set up, your subscribers access the SVC/VPN features through a web interface that you create and run on a web application server. This diagram illustrates the firewalls required to secure them. Your subscribers access the web interface using the HTTPS protocols. See "Set Up the Public Key Infrastructure" for details on setting up the PKI required to use HTTPS.
Figure 2-3 Service Broker SVC/VPN Security Overview
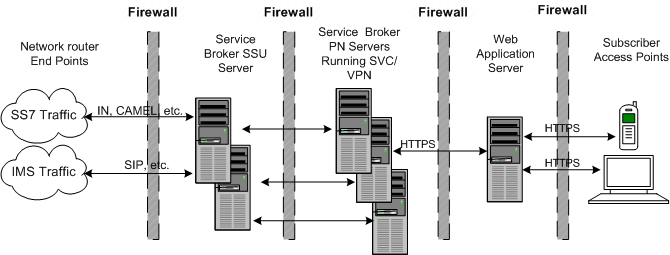
Other than requiring HTTPS and an additional firewall to protect the web application server, there are no special security considerations for using this feature. See Oracle Communications Service Broker SVC Implementation Guide for details on how to set up and use this feature, and the remainder of this chapter for instructions on how to implement a secure Service Broker.
If you use the Online Mediation Controller to mediate between Service Broker and your online charging application, see these documents for instructions on how to set it up securely:
Your online charging application's documentation.
The "Securing Network Communication" section.
The discussion on setting up RADIUS Mediation for Authentication and Authorization in the Radius in Oracle Communications Service Broker Online Mediation Controller Implementation Guide.
This section explains the protocol-specific security features that Service Broker uses to communicate securely over networks using supported protocols. Service Broker implements protocol security features in the signaling domain. Service Broker provides a Signaling Server Unit (SSU) for each supported protocol that you use to configure the protocol, including security. An SSU might contain session timers, encryption choices, client port number or other protocol-specific security parameters. parameters. The SSUs include:
SS7 - SIGTRAN M3UA
SS7 - TDM
SIP
Diameter
Radius
SMPP
PCP (Oracle Communications BRM)
Web Services (HTTP using SOAP or REST)
You configure these SSUs using either the Administration Console or the corresponding Java MBeans exposed for this purpose.
For details on these SSUs and how to configure them, see Oracle Communications Service Broker System Administrator's Guide.
The following sections list the security options that you configure for each protocol.
You use the SSU SS7 SIGTRANN or the Java MBeans operations and parameters to set up security by specifying M3UA layer, trusted SCCP sites, and incoming routing rules for SIGTRAN network traffic. See the discussion on configuring SIP Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details.
You use the SSU SS7 SIGTRANN or the Java MBeans to set up security by specifying MTP connectivity and mapping, SCCP addresses, and incoming routing rules for TDM network traffic. See configuring the SS7 Signaling Server Units for TDM in Oracle Communications Service Broker Signaling Domain Configuration Guide for details.
You use the SSU SS7 SIGTRAN or the corresponding Java MBeans to set up security by specifying trusted SIP network entities that use SIP network channels you specify. See configuring SIP Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details.
In addition, Oracle recommends that you implement security measures appropriate to your implementation, such as:
Implement the IPsec protocol between the system running Service Broker and the network nodes.
Use TLS tunneling between the network node and Service Broker by implementing a load balancer/firewall (such as an F5 load balancer) at the DMZ that performs hardware acceleration/offloading on the secured connection from the firewall to the external network element.
You use the SSU Diameter or the corresponding Java MBeans to set up security by specifying trusted nodes and peers, and creating routing rules for their network traffic. See configuring Diameter Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details.
In addition, Oracle recommends that you implement security measures appropriate to your implementation, such as:
Implement the IPsec protocol between the system running Service Broker and the network nodes.
Use TLS tunneling between the network node and Service Broker by implementing a load balancer/firewall (such as an F5 load balancer) at the DMZ that performs hardware acceleration/offloading on the secured connection from the firewall to the external network element.
You use the Service Broker SSU Radius or the corresponding Java MBeans to set up security by specifying trusted clients to accept accounting and authentication requests from. The SSU Radius also supports the Service Broker Credential Store feature for storing username/password credentials for Radius users.
See configuring Diameter Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details on configuring the SSU Radius. See securing credentials with Credential Store in Oracle Communications Service Broker System Administrator's Guide for details on using the Credential Store.
You use the Service Broker SMPP SSU or the corresponding MBeans to set up security by specifying trusted Short Message Service Centers (SMSCs) and the Extended Short Message Entities (ESMEs) they connect to.
See configuring SMPP Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details. See securing credentials with Credential Store in Oracle Communications Service Broker System Administrator's Guide for details on using the Credential Store.
You use the Service Broker SSU PCP or the corresponding MBeans to set up security by specifying a trusted Oracle BRM connection manager (CM) to connect Service Broker to. You specify the specific CM pool ID, host, port, etc., that identifies the CM. The SSU PCP also support the Service Broker Credential Store feature for storing username/password credentials the BRM requires.
See configuring PCP Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details. See securing credentials with Credential Store in Oracle Communications Service Broker System Administrator's Guide for details on using the Credential Store
You use the Service Broker SSU Web Services to specify trusted web entities that Service Broker communicates with by specifying incoming and outgoing routing rules. You also set up HTTP network access points (addresses and ports) for your trusted nodes to use, and SSL security (keystore and truststores to use for authenticating connections). The SOAP and HTTP protocols support the Service Broker Credential Store feature for storing username/password credentials to authenticate traffic.
See configuring Web Services Signaling Server Units in Oracle Communications Service Broker Signaling Domain Configuration Guide for details. See securing credentials with Credential Store in Oracle Communications Service Broker System Administrator's Guide for details on using the Credential Store
You may choose to monitor Service Broker events, such as creating a VPN administrative user, or changing user permissions, using its runtime MBeans. For details on setting up monitoring, see the monitoring Service Broker discussion in Oracle Communications Service Broker System Administrator's Guide.