| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions Configuration Guide Oracle Solaris 10 8/11 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions Configuration Guide Oracle Solaris 10 8/11 Information Library |
1. Security Planning for Trusted Extensions
2. Configuration Roadmap for Trusted Extensions
3. Adding Trusted Extensions Software to the Oracle Solaris OS (Tasks)
4. Configuring Trusted Extensions (Tasks)
Setting Up the Global Zone in Trusted Extensions
Check and Install Your Label Encodings File
Enable IPv6 Networking in Trusted Extensions
Configure the Domain of Interpretation
Create ZFS Pool for Cloning Zones
Reboot and Log In to Trusted Extensions
Initialize the Solaris Management Console Server in Trusted Extensions
Configure the Network Interfaces in Trusted Extensions
Copy or Clone a Zone in Trusted Extensions
Adding Network Interfaces and Routing to Labeled Zones
Add a Network Interface to Route an Existing Labeled Zone
Add a Network Interface That Does Not Use the Global Zone to Route an Existing Labeled Zone
Configure a Name Service Cache in Each Labeled Zone
Creating Roles and Users in Trusted Extensions
Create Rights Profiles That Enforce Separation of Duty
Create the Security Administrator Role in Trusted Extensions
Create a Restricted System Administrator Role
Create Users Who Can Assume Roles in Trusted Extensions
Verify That the Trusted Extensions Roles Work
Enable Users to Log In to a Labeled Zone
Creating Home Directories in Trusted Extensions
Create the Home Directory Server in Trusted Extensions
Enable Users to Access Their Home Directories in Trusted Extensions
Adding Users and Hosts to an Existing Trusted Network
Add an NIS User to the LDAP Server
Troubleshooting Your Trusted Extensions Configuration
netservices limited Was Run After Trusted Extensions Was Enabled
Cannot Open the Console Window in a Labeled Zone
Labeled Zone Is Unable to Access the X Server
Additional Trusted Extensions Configuration Tasks
How to Copy Files to Portable Media in Trusted Extensions
How to Copy Files From Portable Media in Trusted Extensions
How to Remove Trusted Extensions From the System
5. Configuring LDAP for Trusted Extensions (Tasks)
6. Configuring a Headless System With Trusted Extensions (Tasks)
B. Using CDE Actions to Install Zones in Trusted Extensions
Before setting up the global zone, you must make decisions about your configuration. For the decisions, see Collecting Information and Making Decisions Before Enabling Trusted Extensions.
|
Your encodings file must be compatible with any Trusted Extensions host with which you are communicating.
Note - Trusted Extensions installs a default label_encodings file. This default file is useful for demonstrations. However, this file might not be a good choice for your use. If you plan to use the default file, you can skip this procedure.
If you are familiar with encodings files, you can use the following procedure.
If you are not familiar with encodings files, consult Trusted Extensions Label Administration for requirements, procedures, and examples.
 | Caution - You must successfully install labels before continuing, or the configuration will fail. |
Before You Begin
You are the security administrator. The security administrator is responsible for editing, checking, and maintaining the label_encodings file. If you plan to edit the label_encodings file, make sure that the file itself is writable. For more information, see the label_encodings(4) man page.
# /usr/sbin/chk_encodings /full-pathname-of-label-encodings-file
If the command reports errors, the errors must be resolved before continuing. For assistance, see Chapter 3, Making a Label Encodings File (Tasks), in Trusted Extensions Label Administration
# cp /full-pathname-of-label-encodings-file \ /etc/security/tsol/label.encodings.site # cd /etc/security/tsol # cp label_encodings label_encodings.tx.orig # cp label.encodings.site label_encodings
 | Caution - Your label_encodings file must pass the chk_encodings test before you continue. |
Click mouse button 3 on the background.
In the dialog box, type the full path name to the file:
/full-pathname-of-label-encodings-file
The chk_encodings command is invoked to check the syntax of the file. The results are displayed in the Check Encodings dialog box.
If the Check Encodings action reports errors, the errors must be resolved before continuing. For assistance, see Chapter 3, Making a Label Encodings File (Tasks), in Trusted Extensions Label Administration.
The Check Encodings action creates a backup copy of the original file, then installs the checked version in /etc/security/tsol/label_encodings. The action then restarts the label daemon.
 | Caution - Your label_encodings file must pass the Check Encodings test before you continue. |
Use the command line.
# /usr/sbin/chk_encodings /full-pathname-of-label-encodings-file
If the command reports errors, the errors must be resolved before continuing. For assistance, see Chapter 3, Making a Label Encodings File (Tasks), in Trusted Extensions Label Administration
# cp /full-pathname-of-label-encodings-file \ /etc/security/tsol/label.encodings.site # cd /etc/security/tsol # cp label_encodings label_encodings.tx.orig # cp label.encodings.site label_encodings
 | Caution - Your label_encodings file must pass the Check Encodings test before you continue. |
Example 4-1 Checking label_encodings Syntax on the Command Line
In this example, the administrator tests several label_encodings files by using the command line.
# /usr/sbin/chk_encodings /var/encodings/label_encodings1 No errors found in /var/encodings/label_encodings1 # /usr/sbin/chk_encodings /var/encodings/label_encodings2 No errors found in /var/encodings/label_encodings2
When management decides to use the label_encodings2 file, the administrator runs a semantic analysis of the file.
# /usr/sbin/chk_encodings -a /var/encodings/label_encodings2 No errors found in /var/encodings/label_encodings2 ---> VERSION = MYCOMPANY LABEL ENCODINGS 2.0 10/10/2006 ---> CLASSIFICATIONS <--- Classification 1: PUBLIC Initial Compartment bits: 10 Initial Markings bits: NONE ---> COMPARTMENTS AND MARKINGS USAGE ANALYSIS <--- ... ---> SENSITIVITY LABEL to COLOR MAPPING <--- ...
The administrator prints a copy of the semantic analysis for her records, then moves the file to the /etc/security/tsol directory.
# cp /var/encodings/label_encodings2 /etc/security/tsol/label.encodings.10.10.06 # cd /etc/security/tsol # cp label_encodings label_encodings.tx.orig # cp label.encodings.10.10.06 label_encodings
Finally, the administrator verifies that the label_encodings file is the company file.
# /usr/sbin/chk_encodings -a /etc/security/tsol/label_encodings | head -4 No errors found in /etc/security/tsol/label_encodings ---> VERSION = MYCOMPANY LABEL ENCODINGS 2.0 10/10/2006
CIPSO options do not have an Internet Assigned Numbers Authority (IANA) number to use in the IPv6 Option Type field of a packet. The entry that you set in this procedure supplies a number to use on the local network until IANA assigns a number for this option. Trusted Extensions disables IPv6 networking if this number is not defined.
To enable an IPv6 network in Trusted Extensions, you must add an entry in the /etc/system file.
set ip:ip6opt_ls = 0x0a
Troubleshooting
If error messages during boot indicate that your IPv6 configuration is incorrect, correct the entry:
Check that the entry is spelled correctly.
Check that the system has been rebooted after adding the correct entry to the /etc/system file.
If you install Trusted Extensions on an Oracle Solaris system that currently has IPv6 enabled, but you fail to add the IP entry in /etc/system, you see the following error message: t_optmgmt: System error: Cannot assign requested address time-stamp
If you install Trusted Extensions on an Oracle Solaris system that does not have IPv6 enabled, and you fail to add the IP entry in /etc/system, you see the following types of error messages:
WARNING: IPv6 not enabled via /etc/system
Failed to configure IPv6 interface(s): hme0
rpcbind: Unable to join IPv6 multicast group for rpc broadcast broadcast-number
All communications to and from a system that is configured with Trusted Extensions must follow the labeling rules of a single CIPSO Domain of Interpretation (DOI). The DOI that is used in each message is identified by an integer number in the CIPSO IP Option header. By default, the DOI in Trusted Extensions is 1.
If your DOI is not 1, you must add an entry to the /etc/system file and modify the doi value in the default security templates.
set default_doi = n
This positive, non-zero number must match the DOI number in the tnrhtp database for your node and for the systems that your node communicates with.
Trusted Extensions provides two templates in the tnrhtp database, cipso and admin_low. If you have added entries for local addresses, also modify these entries.
# /usr/dt/bin/trusted_edit /etc/security/tsol/tnrhtp
In Solaris Trusted Extensions (CDE), you can instead use the Admin Editor action in the Trusted_Extensions folder in the Application Manager.
cipso:host_type=cipso;doi=1;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH cipso:host_type=cipso;doi=1;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH
#cipso:host_type=cipso;doi=1;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH cipso:host_type=cipso;doi=1;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH
Make this value the same as the default_doi value in the /etc/system file.
#cipso:host_type=cipso;doi=1;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH cipso:host_type=cipso;doi=n;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH
#admin_low:host_type=unlabeled;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH;doi=1;def_label=ADMIN_LOW admin_low:host_type=unlabeled;min_sl=ADMIN_LOW;max_sl=ADMIN_HIGH;doi=n;def_label=ADMIN_LOW
You are finished when every doi value in every entry in the tnrhtp database is the same.
Troubleshooting
If the /etc/system file sets a default_doi value other than 1, and a security template for this system sets a value that does not match this default_doi value, then messages similar to the following are displayed on the system console during interface configuration:
NOTICE: er10 failed: 10.17.1.12 has wrong DOI 4 instead of 1
Failed to configure IPv4 interface(s): er10
Interface configuration failure can result in login failure:
Hostname: unknown
unknown console login: root
Oct 10 10:10:20 unknown login: pam_unix_cred: cannot load hostname Error 0
To correct the problem, boot the system into single-user mode and correct the security templates as described in this procedure.
See Also
For more information about the DOI, see Network Security Attributes in Trusted Extensions in Trusted Extensions Administrator’s Procedures.
To change the doi value in the security templates that you create, see How to Construct a Remote Host Template in Trusted Extensions Administrator’s Procedures.
To use the editor of your choice as the trusted editor, see How to Assign the Editor of Your Choice as the Trusted Editor in Trusted Extensions Administrator’s Procedures.
If you plan to use an ZFS snapshot as your zone template, you need to create a ZFS pool from a ZFS file or a ZFS device. This pool holds the snapshot for cloning each zone. You use the /zone device for your ZFS pool.
Before You Begin
You have set aside disk space during Oracle Solaris installation for a ZFS file system. For details, see Planning Your Labeled Zones in Trusted Extensions.
During installation, you created a /zone partition with sufficient disk space of about 2000 MBytes.
# umount /zone
# rmdir /zone
Open the vfstab file in an editor. Prefix the /zone entry with a comment sign.
#/dev/dsk/cntndnsn /dev/dsk/cntndnsn /zone ufs 2 yes -
# zpool create -f zone cntndnsn
For example, if your /zone entry used disk slice c0t0d0s5, then the command would be the following:
# zpool create -f zone c0t0d0s5
Use one of the following commands:
# zpool status -x zone pool 'zone' is healthy
# zpool list NAME SIZE USED AVAIL CAP HEALTH ALTROOT /zone 5.84G 80K 5.84G 7% ONLINE -
In this example, the initial setup team reserved a 6000 MByte partition for zones. For more information, see the zpool(1M) man page.
At most sites, two or more administrators, who serve as an initial setup team, are present when configuring the system.
Before You Begin
Before you first log in, become familiar with the desktop and label options in Trusted Extensions. For details, see Chapter 2, Logging In to Trusted Extensions (Tasks), in Trusted Extensions User’s Guide.
# /usr/sbin/reboot
If your system does not have a graphical display, go to Chapter 6, Configuring a Headless System With Trusted Extensions (Tasks).
The Trusted CDE desktop contains actions that are useful when configuring the system. Starting in the Solaris 10 10/08 release, the txzonemgr script is the preferred program for configuring the system.
Users must not disclose their passwords to another person, as that person might then have access to the data of the user and will not be uniquely identified or accountable. Note that disclosure can be direct, through the user deliberately disclosing his/her password to another person, or indirect, such as through writing it down, or choosing an insecure password. Trusted Extensions software provides protection against insecure passwords, but cannot prevent a user disclosing his/her password or writing it down.
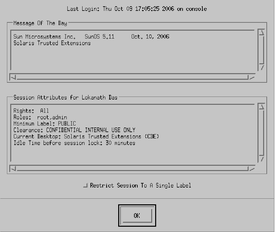
Then click OK to dismiss the box.
Click OK to accept the default label.
Once the login process is complete, the Trusted Extensions screen appears briefly, and you are in a desktop session with four workspaces. The Trusted Path symbol is displayed in the trusted stripe.
Note - You must log off or lock the screen before leaving a system unattended. Otherwise, a person can access the system without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
This procedure enables you to administer users, roles, hosts, zones, and the network on this system. On the first system that you configure, only the files scope is available.
Before You Begin
You must be superuser.
To use the LDAP toolbox on the LDAP server from a Solaris Management Console that is running on a client, you must complete all of the tasks in Configuring the Solaris Management Console for LDAP (Task Map).
# /usr/sbin/smc &
Note - The first time the Solaris Management Console is started, it performs several registration tasks. These tasks can take a few minutes.
Figure 4-1 Solaris Management Console Initial Window
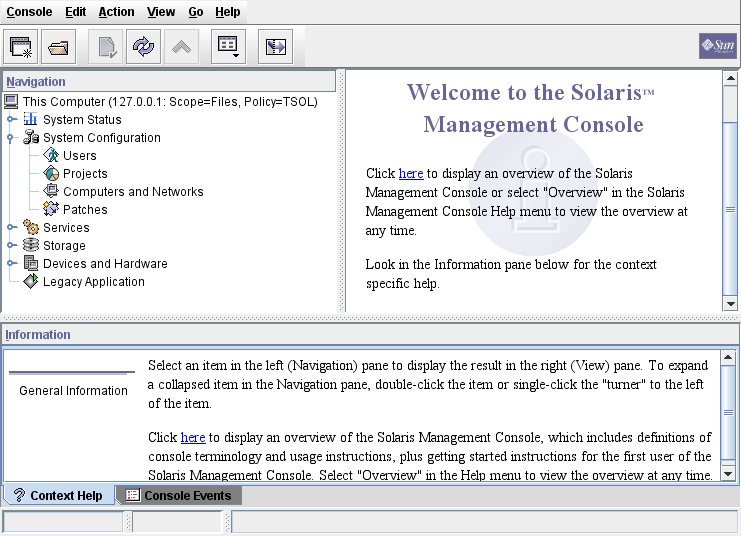
If this system does not have the recommended amount of memory and swap, it might take a few minutes for the toolboxes to display. For recommendations, see Installing or Upgrading the Oracle Solaris Operating System for Trusted Extensions.
Figure 4-2 shows a This Computer (this-host: Scope=Files, Policy=TSOL) toolbox. Trusted Extensions modifies tools under the System Configuration node.
 | Caution - Do not choose a toolbox that has no policy. Toolboxes without a listed policy do not support Trusted Extensions. |
Your toolbox choice depends on which scope you want to influence.
To edit local files, choose the Files scope.
To edit LDAP databases, choose the LDAP scope.
After you complete all of the tasks in Configuring the Solaris Management Console for LDAP (Task Map), the LDAP scope is available.
# /usr/sbin/smc &
The following figure shows a This Computer (this-host: Scope=Files, Policy=TSOL) toolbox. Trusted Extensions modifies tools under the System Configuration node.
Figure 4-2 Trusted Extensions Tools in the Solaris Management Console
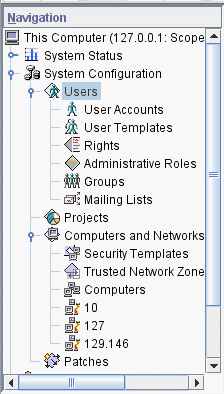
Saving a Policy=TSOL toolbox enables a Trusted Extensions toolbox to load by default. Preferences are saved per role, per host. The host is the Solaris Management Console server.
The Home toolbox is selected.
Put the current toolbox in the Location field by clicking the Use Current Toolbox button.
See Also
For an overview of the Trusted Extensions additions to the Solaris Management Console, see Solaris Management Console Tools in Trusted Extensions Administrator’s Procedures. To use the Solaris Management Console to create security templates, see Configuring Trusted Network Databases (Task Map) in Trusted Extensions Administrator’s Procedures.
For LDAP, this procedure establishes the naming service configuration for the global zone. If you are not using LDAP, you can skip this procedure.
Starting in the Solaris 10 5/08 release, if you are in a Solaris Trusted Extensions (CDE) workspace, you can use the txzonemgr script or a Trusted CDE action to create an LDAP client. If you are in a Solaris Trusted Extensions (JDS) workspace, you must use the txzonemgr script.
Note - If you plan to set up a name server in each labeled zone, you are responsible for establishing the LDAP client connection to each labeled zone.
Before You Begin
The Sun Java System Directory Server, that is, the LDAP server, must exist. The server must be populated with Trusted Extensions databases, and this system must be able to contact the server. So, the system that you are configuring must have an entry in the tnrhdb database on the LDAP server, or this system must be included in a wildcard entry before you perform this procedure.
If an LDAP server that is configured with Trusted Extensions does not exist, you must complete the procedures in Chapter 5, Configuring LDAP for Trusted Extensions (Tasks) before you perform this procedure.
The standard naming service switch file for LDAP is too restrictive for Trusted Extensions.
# cd /etc # cp nsswitch.ldap nsswitch.ldap.orig
The correct entries are similar to the following:
hosts: files dns ldap ipnodes: files dns ldap networks: ldap files protocols: ldap files rpc: ldap files ethers: ldap files netmasks: ldap files bootparams: ldap files publickey: ldap files services: files
Note that Trusted Extensions adds two entries:
tnrhtp: files ldap tnrhdb: files ldap
# cp nsswitch.ldap nsswitch.conf
The Create LDAP Client menu item configures the global zone only.
The title of the dialog box is Labeled Zone Manager.
Enter Domain Name: Type the domain name Enter Hostname of LDAP Server: Type the name of the server Enter IP Address of LDAP Server servername: Type the IP address Enter LDAP Proxy Password: Type the password to the server Confirm LDAP Proxy Password: Retype the password to the server Enter LDAP Profile Name: Type the profile name
Proceed to create LDAP Client?
When you confirm, the txzonemgr script adds the LDAP client. Then, a window displays the command output.
This folder contains actions that set up interfaces, LDAP clients, and labeled zones.
Answer the following prompts:
Domain Name: Type the domain name Hostname of LDAP Server: Type the name of the server IP Address of LDAP Server: Type the IP address LDAP Proxy Password: Type the password to the server Profile Name: Type the profile name
The following completion message appears:
global zone will be LDAP client of LDAP-server System successfully configured. *** Select Close or Exit from the window menu to close this window ***
# ldapclient -v mod -a enableShadowUpdate=TRUE \ > -a adminDN=cn=admin,ou=profile,dc=domain,dc=suffix System successfully configured
The Create LDAP Client action and the txzonemgr script run the ldapclient init command only. In Trusted Extensions, you must also modify an initialized LDAP client to enable shadow updates.
# ldapclient list
The output looks similar to the following:
NS_LDAP_FILE_VERSION= 2.0 NS_LDAP_BINDDN= cn=proxyagent,ou=profile,dc=domain-name ... NS_LDAP_BIND_TIME= number
If you get an error, create the LDAP client again and supply the correct values. For example, the following error can indicate that the system does not have an entry on the LDAP server:
LDAP ERROR (91): Can't connect to the LDAP server. Failed to find defaultSearchBase for domain domain-name
To correct this error, you need to check the LDAP server.
Example 4-2 Using Host Names After Loading a resolv.conf File
In this example, the administrator wants a particular set of DNS servers to be available to the system. The administrator copies a resolv.conf file from a server on a trusted net. Because DNS is not yet active, the administrator uses the server's IP address to locate the server.
# cd /etc # cp /net/10.1.1.2/export/txsetup/resolv.conf resolv.conf
After the resolv.conf file is copied and the nsswitch.conf file includes dns in the hosts entry, the administrator can use host names to locate systems.