| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions User's Guide Oracle Solaris 11 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions User's Guide Oracle Solaris 11 Information Library |
1. Introduction to Trusted Extensions
2. Logging In to Trusted Extensions (Tasks)
3. Working in Trusted Extensions (Tasks)
4. Elements of Trusted Extensions (Reference)
Device Security in Trusted Extensions
Files and Applications in Trusted Extensions
Password Security in the Oracle Solaris OS
After you have successfully completed the login process, as explained in Chapter 2, Logging In to Trusted Extensions (Tasks), you can work within Trusted Extensions. Your work is subject to security restrictions. Restrictions that are specific to Trusted Extensions include the label range of the system, your clearance, and your choice of a single-level or multilevel session. As the following figure illustrates, several features distinguish a system that is configured with Trusted Extensions from an Oracle Solaris system.
Figure 4-1 Trusted Extensions Multilevel Desktop
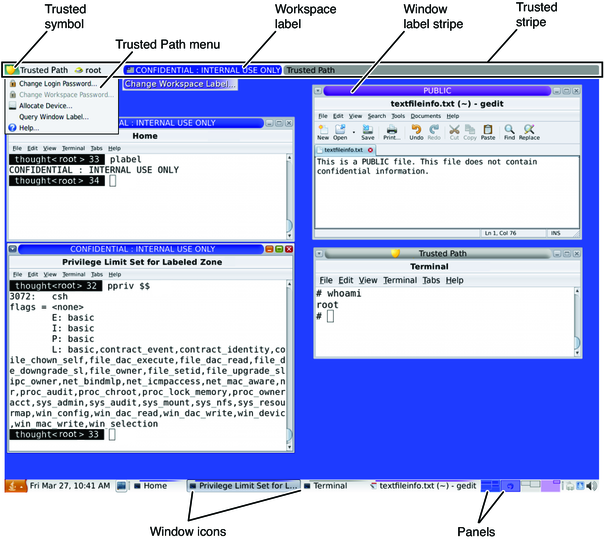
Label displays – All windows, workspaces, files, and applications have a label. The desktop provides label stripes and other indicators for viewing an entity's label.
Trusted stripe – This stripe is a special graphical security mechanism. In every workspace, the stripe is displayed at the top of the screen.
Limited access to applications from the workspace – The workspace provides access to only those applications that are permitted in your account.
Trusted Path menu – The trusted symbol provides access to the menu.
As discussed in Mandatory Access Control, all applications and files in Trusted Extensions have labels. Trusted Extensions displays labels in the following locations:
Window label stripes above the window title bar
Label color stripe above the window icon in the window list
Window label indicator in the trusted stripe
Query window label indicator from the Trusted Path menu that displays the label of the window or window icon that is specified by the pointer location
In addition, the color of the panels indicate the label of the workspace.
Figure 4-2 Panels Indicating Workspaces at Different Labels
Figure 4-1 shows how labels display on a Trusted Extensions desktop. Also, the Query Window Label menu item can be used to display the label of a window. For an illustration, see Figure 3-2.
The trusted stripe appears at the top of the screen.
Figure 4-3 Trusted Stripe on the Desktop
The purpose of the trusted stripe is to provide a visual confirmation that you are in a legitimate Trusted Extensions session. The stripe indicates when you are interacting with the trusted computing base (TCB). The stripe also displays the labels of your current workspace and current window. The trusted stripe cannot be moved or obscured by other windows or dialog boxes.
The trusted stripe has the following elements:
The trusted symbol – Displays when the screen focus is security-related
The window label – Displays the label of the active window when the screen focus is not security-related
A role marker – At the right of the trusted symbol, before the account name, displays a hat icon if the account is a role account
The current account name – At the right of the trusted symbol, displays the name of the owner of new processes in the workspace
Labeled windows – Displays the labels of all windows in the workspace
Whenever you access any portion of the TCB, the trusted symbol appears at the left of the trusted stripe area.
The trusted symbol is not displayed when the mouse pointer is focused in a window or area of the screen that does not affect security. The trusted symbol cannot be forged. If you see the symbol, you can be sure that you are safely interacting with the TCB.
 | Caution - If the trusted stripe is missing from your workspace, contact the security administrator. The problem with your system could be serious. The trusted stripe must not appear during login or when you lock your screen. If the trusted stripe shows, contact the administrator immediately. |
The Window Label indicator displays the label of the active window. In a multilevel session, the indicator can help identify windows with different labels in the same workspace. The indicator can also show that you are interacting with the TCB. For example, when you change your password, the Trusted Path indicator displays in the trusted stripe.