13 Adding Compliance Standards
The Oracle Enterprise Manager Compliance Management solution provides the capability to define, customize, and manage compliance frameworks and compliance standards.
To view a visual demonstration about the Compliance Management framework, access the following URL and click Begin Video.
https://apex.oracle.com/pls/apex/f?p=44785:24:0::NO:24:P24_CONTENT_ID,P24_PREV_PAGE:5773,1
This chapter contains the following sections:
13.1 Introduction to Adding Compliance Standards
As a plug-in developer, you are responsible for the following steps when adding compliance standards:
-
Define compliance standard rules.
Compliance standard rules can be either of the following:
-
Repository check-based rules
-
Real-time monitoring rules.
For information about defining compliance standard rules, see Section 13.2, "About the Compliance Standard Rules".
-
-
Define a compliance standard.
For more information, see Section 13.3, "Defining Compliance Standards".
-
Define a compliance framework.
For more information, see Section 13.4, "Defining a Compliance Framework".
-
Package the compliance standard rules, standards, and framework as metadata XML.
For more information, see Section 13.8, "Packaging Compliance XML".
-
Set up and test the compliance content.
For more information, see Section 13.9, "Setting Up and Testing Compliance Standards and Rules".
-
Deploy the plug-in.
For information about deploying plug-ins, see Chapter 14, "Validating, Packaging, and Deploying the Plug-in".
13.1.1 Assumptions and Prerequisites
This chapter assumes you are familiar with the following:
-
Plug-in development overview, including how to package a plug-in and its XML files.
-
If you are installing compliance data with the
emctl register oms metadata -service gccompliancecommand, it will require anEM_COMPLIANCE_UTIL.trigger_rule_dependency_jobcallback. You must enter the following commands through SQL*Plus as theSYSMANuser:begin EM_COMPLIANCE_UTIL.trigger_rule_dependency_job; end; /
Note:
This is necessary only if you are using theemctl register oms metadata -service gccompliancecommand to install compliance content.If you are installing the plug-in, then you do not have to enter the previous SQL.
For more information about the
emctl register oms metadatacommand, see Section 14.7, "Updating Deployed Metadata Files Using the Metadata Registration Service (MRS)".
13.2 About the Compliance Standard Rules
This section provides a description of the following:
13.2.1 Defining Repository Check-based Rules
A repository check-based rule checks the configuration state of one or more targets. A rule is compliant if the test fails to identify a violation. In other words, the test determines that the configuration item is in the required state or has the prescribed value. Any rule that uncovers a violation is noncompliant.
The data source that is evaluated by a rules test condition can be based on a repository query. A rules test condition can be implemented using a threshold condition based on the underlying metrics or queries column value, or SQL expression, or a PL/SQL function. (The policies are similar to Oracle Enterprise Manager 10g Release 5).
The key points in this area include:
-
Defining Compliance Standard Rules, Compliance Standards, and Compliance Frameworks
-
Replacing out-of-box policy groups (10.2.x/11.10) with Compliance Standards that you create referring to Compliance Standard Rules
-
Mapping your compliance standards to the appropriate Compliance Frameworks
-
Defining Oracle Business Intelligence Publisher (BI Publisher) reports for compliance
Example 13-1 provides the syntax for defining repository rules and Example 13-2 provides an example of a repository rule definition.
Note:
For the complete compliance XML Schema Definitions (XSDs), see the following JAR file:$ORACLE_HOME/sysman/jlib/gccomplianceCommon.jar
See Also:
For additional examples, see Section 13.10, "More Compliance Examples".Example 13-1 Repository Rule Definition Syntax
<xsd:complexType name="RuleT">
<xsd:sequence>
<xsd:element name="DisplayName" type="std:DisplayString256Def" minOccurs="0"/>
<xsd:element name="TargetType" type="std:Name256Def"/>
<xsd:element name="IsSystem" type="std:BooleanDef" minOccurs="0" default="false"/>
<xsd:element name="IsHidden" type="std:BooleanDef" minOccurs="0" default="false"/>
<xsd:element name="evaluateAlways" type="std:BooleanDef" default="false" minOccurs="0"/>
<!-- E.g. target version, platform based filter -->
<xsd:element ref="std:TargetPropertyFilter" minOccurs="0"/>
<xsd:element name="Description" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Impact" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Recommendation" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="FixLinkList" type="std:FixLinkListT" minOccurs="0"/>
<xsd:element name="ViolationContextList" type="std:ViolationContextListT"/>
<xsd:element name="CheckSource" type="std:CheckSourceT" minOccurs="1" maxOccurs="1"/>
<xsd:element name="Severity" default="MinorWarning" minOccurs="0">
<xsd:simpleType>
<xsd:restriction base="xsd:string">
<xsd:enumeration value="MinorWarning"/>
<xsd:enumeration value="Warning"/>
<xsd:enumeration value="Critical"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>
<xsd:element name="LifeCycleStatus" default="Development" minOccurs="0">
<xsd:simpleType>
<xsd:restriction base="xsd:string">
<xsd:enumeration value="Development"/>
<xsd:enumeration value="Production"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>
<xsd:element name="KeywordList" type="std:KeywordListT" minOccurs="0"/>
<xsd:element name="UrlLink" type="std:String4000Def" minOccurs="0"/>
<xsd:element name="ViolationMessage" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="ClearViolationMessage" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Author" type="std:Name256Def" minOccurs="0"/>
<xsd:element name="LastUpdatedBy" type="std:Name256Def" minOccurs="0"/>
</xsd:sequence>
<xsd:attribute name="name" type="std:Name256Def" use="required"/>
<xsd:attribute name="oms_version" type="std:Name32Def" use="required"/>
</xsd:complexType>
Example 13-2 is defined for oracle_database target_type, which is part of the database plug-in.
You can define a rule for any target type registered with Enterprise Manager.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule1">
<DisplayName nlsid="SAMPLE_RULE_1_NAME">Sample Rule 1</DisplayName>
<TargetType>oracle_database</TargetType>
<IsSystem>true</IsSystem>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_operating_system</PropertyName>
<ValueList>
<Value>Windows</Value>
</ValueList>
</PropertyItem>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Description nlsid="SAMPLE_RULE_1_DESC">Checks for use of a single control file</Description>
<Impact nlsid="SAMPLE_RULE_1_IMPACT">The control file is one of the most
important files in an Oracle database. It maintains many physical characteristics
and important recovery information about the database. If you lose the only copy
of the control file due to a media error, there will be unnecessary down time and
other risks.</Impact>
<Recommendation nlsid="SAMPLE_RULE_1_RECO">Use at least two control files that are multiplexed on different disks.</Recommendation>
<ViolationContextList>
<Column type="String" name="FILE_LIST">
<DisplayLabel nlsid="SAMPLE_RULE_1_COL_1">FILE_LIST</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
<Column type="Number" name="CONTROL_FILE_COUNT">
<DisplayLabel nlsid="SAMPLE_RULE_1_COL_2">CONTROL_FILE_COUNT</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>oracle_database</TargetType>
<MetricName>sample_rule1</MetricName>
<SourceType>SQL</SourceType>
<Source>select CONTROL_FILE_COUNT, FILE_LIST, TARGET_GUID from MGMT$CS_DB_CONTROL_FILE_COUNT</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>FILE_LIST</ColumnName>
<ColumnType>String</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_1_COL_1">FILE_LIST</ColumnLabel>
</MetricColumnInfo>
<MetricColumnInfo>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_1_COL_2">CONTROL_FILE_COUNT</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<MinorWarnThreshold>1</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<ThresholdCriteria>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<TestOperator>EQ</TestOperator>
<ThresholdValue>1</ThresholdValue>
<ThresholdType>Number</ThresholdType>
</ThresholdCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>MinorWarning</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_1_VIOL_MSG">The database has an insufficient number of control files.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_1_VIOL_CLEAR_MSG">The database has sufficient number of control files.</ClearViolationMessage>
<Author>SYSMAN</Author>
</Rule>
Table 13-1 provides a description of the tags used to define a repository rule:
Table 13-1 Key Tags for Defining Repository Rules
| Tag | Subtag | Description |
|---|---|---|
|
|
The display name of the rule. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The type of target to which this rule is can be associated |
|
|
|
True for out-of-the-box rules. Otherwise, False |
|
|
|
False by default. When set to True, the IsHidden rules are not visible in the UI and no events are generated. This element should be set to true for out-of-the-box rules |
|
|
|
The description of the rule. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Impact if the rule violates (when rule is noncompliant). It provides the |
|
|
|
Violation context defines a violation to a rule uniquely. Violation context lists columns from <Source> Query, which will be visible as a part of the violation. Each column must mark as key or non-key. The mandatory target_guid column from <Source> query is implicitly added to the violation context and should not be included in the violation context explicitly. |
|
|
|
Metric Column name. Uses Attributes name and type
|
|
|
|
Defines the data source for Rule evaluation. |
|
|
.. |
Defines data source for a repository rule. |
|
|
|
Defines data source query.
|
|
|
|
List of parameters Note: If parameters are specified and used in a where clause, then you can customize the parameter value at compliance standard rule and target type level or compliance standard rule and target instance level. This enables the user to customize or control the check definition behavior per target instance or at the target type level. |
|
|
|
Parameter definition |
|
|
|
Name of parameter |
|
|
|
parameter Type (String or number) |
|
|
|
Default values for parameters |
|
|
|
Define a default value for a parameter:
|
|
|
|
The TestCondition tag operates over the data source fetched by running the Metric's <Source> Query. Any data source row that satisfies the condition is a violation to the rule |
|
|
|
Requires a column from Source Query, a threshold value, and operator (=,<,>, and so on) to relate the column value and threshold value. |
|
|
|
Requires a SQL condition over the columns from <Source> query. Optionally, this condition can include one or more parameters. |
|
|
|
Severity of Rule (Critical, Warning, MinorWarning) |
|
|
|
Lifecycle status of rule, (Development or Production) |
|
|
|
Detail URL for the Rule, containing details about the rule |
|
|
|
Message recorded with violation (for rule). Used for notifications. It provides the nlsid attribute to support the translation of messages |
|
|
|
Message recorded with clearing of violation (for rule). Used for notifications. It provides the nlsid attribute to support the translation of messages. |
|
|
|
List of keywords associated with the Rule. |
|
|
Keyword |
Keywords applicable to the compliance standard |
|
|
|
Rule Author. |
13.2.2 Defining Real-time Monitoring Rules
You can use a real-time monitoring rule to monitor any action that can happen against a file, a database object, or a Microsoft Windows Registry key. It can also monitor the starting and stopping of processes, and the logging in, logging out, and switching user (su) activity of users. The real-time aspect of the monitoring means that it captures the exact time the action occurred along with the user that performed the action.
Results from real-time monitoring can be reconciled with a Change Management system such as BMC Remedy. This reconciliation can automatically determine if an action was supposed to happen (authorized) or not (unauthorized). If a customer does not have a Change Management server, this audit status annotation can be made manually through the UI.
A major part of any IT compliance initiative is to ensure that your IT operations staff are making changes and managing the environment according to corporate policies. By reconciling what is happening in the environment to the customer's change management process, real-time monitoring helps to identify out-of-policy actions that will either lead to a high risk environment, or a compliance control that will fail audits.
Creating a real-time monitoring rule involves the following steps. These are explained further below.
-
Choose the target type and entity type being monitored. A rule can also be limited based on certain target type properties (OS, target version, hardware platform, and target lifecycle)
-
Choose one or more target type facets to monitor
-
Choose one or more observations to watch for
-
Choose zero or more facets to filter the results that are monitored
-
Choose the change management reconciliation options
Integration points in this area include:
-
Defining (one or more) facets for your target types. Facets define the low level artifacts that will be monitored
-
Defining new compliance standard rules for new or existing compliance standards
-
Mapping your compliance standard rules and compliance standards to the out-of-box compliance frameworks that are related to industry standard frameworks.
-
Creating connectors to support new ticketing systems (including definition of custom region). This can also be used to extend out-of-box change reconciliation support (currently limited to Remedy 7.x). For information about the process for creating new connectors, see the Oracle Enterprise Manager Connector Integration Guide.
13.2.2.1 What Entity Types Can I Monitor?
When you define a real-time monitoring rule, the first thing you have to decide is what entity type on a host to monitor. For Oracle Enterprise Manager Cloud Control 12c, the following entity types can be monitored with Real-time Monitoring Rules:
-
OS File
-
OS Process
-
OS User
-
Microsoft Windows Registry
-
Microsoft Active Directory User
-
Microsoft Active Directory Computer
-
Microsoft Active Directory Group
-
Oracle Database Table
-
Oracle Database View
-
Oracle Database Procedure
-
Oracle Database User
-
Oracle Database Index
-
Oracle Database Sequence
-
Oracle Database Function
-
Oracle Database Package
-
Oracle Database Library
-
Oracle Database Trigger
-
Oracle Database Tablespace
-
Oracle Database Materialized View
-
Oracle Database Cluster
-
Oracle Database Link
-
Oracle Database Dimension
-
Oracle Database Profile
-
Oracle Database Public DB Link
-
Oracle Database Synonym
-
Oracle Database Public Synonym
-
Oracle Database Segment
-
Oracle Database Type
-
Oracle Database Role
-
Oracle Database SQL Query Statement
These entity types are fixed by the capabilities of the current release and cannot be extended. However, you can use them when creating facets and Real-Time monitoring rules.
In addition to facets defining what can be monitored, there is a set of entities that can be used for filtering also. The following list includes the most commonly used filtering entity types:
-
OS Process
-
OS User
-
Oracle Database User
-
Time Window
-
Host
When you create a Real-time monitoring rule, choose what to monitor (that is, what files). Then choose if you want to use filtering so that only actions performed by certain users, or at certain periods of time are monitored.
13.2.2.2 About Real-time Monitoring Facets
Target Type Facets are used to specify the list of entities to monitor. These facets can be used again at a later time in any number of rules. They can be created on their own, or created inline with a Real-time Monitoring rule.
In the case of OS File monitoring, a facet could be a list of distinct single files, patterns with wildcards that would include many files, or simply an entire directory.
These patterns can also include parameters with a default, but can be overridden as required for each target.
The following are some examples of facets that may be defined for a HOST target type and an OS FILE entity type:
User Credential Files
-
/etc/passwd -
/etc/shadow -
/etc/mail/trusted-users
Network Configuration Files
-
/etc/hosts -
/etc/resolv.conf -
/etc/hosts.* -
/etc/defaultrouter -
/etc/nsswitch.conf -
/etc/netmasks{app_install_directory}/network/config
Here are some examples of facets that might be defined for a HOST target type and an OS PROCESS entity type. These might be monitored in real-time because any of these processes started on a production server could lead to a significant security risk.
Network Configuration Tools
-
ifconfig -
xhost
The following table provides a list of hypothetical facets that you might create for your given target type. The facet name can be anything you choose. For some plug-in developers, there might be many more facets than these limited examples. For each facet, there is a description of the included patterns.
| Target-Type Facet | Description |
|---|---|
| Log files | List each log file the target type has.
Customers want to monitor when regular users modify a log file (not a system user) |
| Binary Files | List each binary the target type has.
Rules can be created to monitor if a binary is tampered with or when a binary is patched. Instead of listing each individual binary, it can also list a whole directory, but exclude frequently changing files |
| Library Files | List each library the target type has.
Rules can be created to monitor if a library is tampered with or when a library is patched. Instead of listing each individual library, it can also list a whole directory, but exclude frequently changing files |
| General Configuration Files | List any configuration files that are user changeable normally, but the user might want to capture changing. |
| Security Key Files | List any files that store certificates, keys, and so on.
This can be a whole directory also, but exclude files that change regularly. This is to monitor if any users read the files in an attempt to get the content of the certificates. |
| Security Configuration Files | List any files that configure how security works in the target type, such as encryption configuration, and so on |
| Application Users | List the typical application users (that is, Oracle, root), and so on.
Users can use this facet to filter monitoring changes where they do not care if the application user makes the change |
| Utility Processes | Any utility processes that normally run during a maintenance period, but should not be run during production |
| Registry Keys | Any Microsoft Windows registry keys that affect the configuration of the target |
| Configuration Tables | Any database tables that store configuration data. |
13.2.2.3 Creating Real-time Monitoring Facets
This section provides an overview of the XML tags used in creating a real-time monitoring facet and an example of XML fragment showing facet creation. Facets can be created on their own as shown in this example, or inline with a real-time monitoring rule creation.
Table 13-2 provides descriptions of the tags used to define a Real-time monitoring facet:
Table 13-2 Key Tags Used to Define a Real-Time Monitoring Facet
| Tag | Subtag | Description |
|---|---|---|
|
|
The internal name of the facet. This must be unique across all facets that exist and is not visible on the UI. |
|
|
|
The display name of the facet. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The type of target to which this rule can be associated. |
|
|
|
The entity type for which you are creating the facet (such as |
|
|
|
True, for out-of-the-box rules. Otherwise, False. |
|
|
|
The description of the facet. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The Enterprise Manager user that is the author of the facet. |
|
|
|
The Enterprise Manager user that last updated the facet. This should be same as the author for your initially created data. |
|
|
|
Container holding the pattern definition that makes up the facet |
|
|
|
Collection of patterns that define the facet. A single facet can be made up of include and exclude patterns.
|
|
|
|
Collection of pattern default values for each parameter introduced in the patterns. Parameters are not shared across facets. If you use the same parameter name in two facets, each facet must define its own default value.
|
Example 13-3 Sample Facet Definition
<Facet xmlns="http://www.oracle.com/DataCenter/ConfigStd/" is_time_window="0">
<Name>network_configuration_files</Name>
<DisplayName nlsid=”SAMPLE_FACET_DNAME”>Networking configuration files</DisplayName>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsSystem>1</IsSystem>
<Description nlsid=”SAMPLE_FACET_DESC”>Files on a standard UNIX operating system that contain configuration relevant to the networking operations.</Description>
<Author>SYSMAN</Author>
<LastUpdatedBy>SYSMAN</LastUpdatedBy>
<SourcePattern>
<GeneralPattern>
<Patterns>
<Pattern>
<Value>{ETCDIR}/hosts</Value>
<Description nlsid=”SAMPLE_FACET_PATTERN_1_DESC”>Contains IP to hostname mappings</Description>
<IsIncluded>1</IsIncluded>
</Pattern>
<Pattern>
<Value>{ETCDIR}/resolv.conf</Value>
<Description nlsid=”SAMPLE_FACET_PATTERN_2_DESC”>Contains local name resolution mappings.</Description>
<IsIncluded>1</IsIncluded>
</Pattern>
<Pattern>
<Value>{ETCDIR}/appsecurity/*</Value>
<Description nlsid=”SAMPLE_FACET_PATTERN_3_DESC”>All files in a directory used for my custom application.</Description>
<IsIncluded>1</IsIncluded>
</Pattern>
<Pattern>
<Value>{ETCDIR}/appsecurity/sample.conf</Value>
<Description nlsid=”SAMPLE_FACET_PATTERN_4_DESC”>Excluding one file that is not a production configuration file that does not need to be monitored.</Description>
<IsIncluded>0</IsIncluded>
</Pattern>
<Parameters>
<Parameter>
<Name>ETCDIR</Name>
<Description nlsid=”SAMPLE_FACET_PARAMETER_1_DESC”>Location where all base Unix configuration files sit.</Description>
<Value>/etc</Value>
<IsActive>1</IsActive>
</Parameter>
</Parameters>
</GeneralPattern>
</SourcePattern>
</Facet>
13.2.2.4 Creating Real-time Monitoring Facets for Time Windows
Time windows are a special type of facet that is used for filtering real-time monitoring. Typically, the Enterprise Manager end user creates time window facets since they are specific to their own operations schedules, but this document includes the content for reference purposes.
Table 13-3 provides a description of the tags of a time window facet:
Table 13-3 Key Tags Used to Define a Time Window Facet
| Tag | Subtag | Description |
|---|---|---|
|
|
The internal name of the facet. This must be unique across all facets that exist and is not visible on the UI. |
|
|
|
The display name of the facet. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The type of target to which this rule is associated |
|
|
|
The entity type for which you are creating the facet. For this example, it is timewindow |
|
|
|
True, for out-of-the-box rules. Otherwise, False. |
|
|
|
The description of the facet. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The Enterprise Manager user that is the author of the facet. |
|
|
|
The Enterprise Manager user that last updated the facet. This should be same as the author for your initially created data. |
|
|
|
||
|
|
The display name of the time zone in English. For example Greenwich Mean Time (UTC+0). |
|
|
|
|
|
|
|
|
Example 13-4 Sample Time Window Facet Definition
<Facet is_time_window="1>
<Name>general_working_hours</Name>
<DisplayName>General Working Hours</DisplayName>
<TargetType>host</TargetType>
<EntityType>timewindow</EntityType>
<IsSystem>0</IsSystem>
<Description>Define the work hour from 9:00 am to 5:00 pm</Description>
<Author>SYSMAN</Author>
<LastUpdatedBy>SYSMAN</LastUpdatedBy>
<SourcePattern>
<SchedulePattern>
<TZDisplayName/>
<Duration>
<DurStartMinute>540</DurStartMinute>
<DurEndMinute>1020</DurEndMinute>
<DurMinute>480</DurMinute>
</Duration>
<Recurrence>
<RecStartDate>2010-07-26</RecStartDate>
<RecurrencePattern>
<RecPattern>WEEKLY</RecPattern>
<RecPatternDays>1,2,5</RecPatternDays>
<RecPatternFrequency>1</RecPatternFrequency>
</RecurrencePattern>
</Recurrence>
</SchedulePattern>
</SourcePattern>
</Facet>
13.2.2.5 Creating Real-time Monitoring Rules
This section provides an overview of the XML tags used in creating a real-time monitoring rule and an example XML fragment showing rule creation. This XML fragment assumes that the facet has been created already and is referenced in this rule.
Table 13-4 provides a description of the tags used to define a real-time rule:
Table 13-4 Key Tags Used to Define a Real-time Rule
| Tag | Subtag | Description |
|---|---|---|
|
|
The display name of the rule. It provides the nlsid attribute to support the translation of messages. |
|
|
|
The type of target to which this rule is associated |
|
|
|
True, for out-of-the-box rules. Otherwise, False. |
|
|
|
The description of the rule. It provides the |
|
|
|
Impact if the rule violates (when rule is noncompliant). It provides the nlsid attribute to support the translation of messages |
|
|
|
Violation context defines a violation to a rule uniquely. Violation context lists columns from <Source> Query, which will be visible as a part of the violation. Each column must mark as key or non-key. The mandatory target_guid column from <Source> query is implicitly added to the violation context and should not be included in the violation context explicitly. |
|
|
|
Metric Column name. Uses Attributes name and type:
|
|
|
|
Defines the data source for Rule evaluation. |
|
|
|
Defines data source for Real-time Monitoring Rule |
|
|
|
The type of monitoring performed (that is, |
|
|
|
The collection of facets to refer to in this rule. Some facets can be monitoring facets and some might be filtering facets.
|
|
|
|
The types of observations you want to monitor in real-time.
|
|
|
|
|
|
|
|
Advanced rule settings
|
|
|
|
Additional options that can be configured based on the entity type. Some entity types will not have options.
|
|
|
|
Severity of the rule (Critical, Warning, or MinorWarning) |
|
|
|
Lifecycle status of the rule (Development or Production) |
|
|
|
Detail URL for the rule, containing details about the rule |
|
|
|
Message recorded with violation (for the rule). Used for notifications. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Message recorded with clearing of violation (for the rule). Used for notifications. It provides the nlsid attribute to support the translation of messages. |
|
|
|
List of keywords associated with the rule |
|
|
|
Keywords applicable to the compliance standard |
|
|
|
Rule author |
Example 13-5 Sample Rule Definition
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" Name="monitor_critical_os_config_files">
<DisplayName nlsid=”SAMPLE_RULE_NAME”>Monitor critical OS configuration files</DisplayName>
<TargetType>host</TargetType>
<IsSystem>True</IsSystem>
<Description nlsid=”SAMPLE_RULE_DESC”>Monitor several critical
configuration areas of a Linux host to ensure no configuration changes are
happening out of bounds. Monitoring is only done during production
hours.</Description>
<Impact nlsid=”SAMPLE_RULE_IMPACT”>Capturing real-time changes to these files may indicate a serious security issue.</Impact>
<Recommendation nlsid=”SAMPLE_RULE_RECO”>Ensure that change management policy documents how and when changes should be made in production.
Create compensating controls to address these out of bound issues.</Recommendation>
<ViolationContextList/>
<CheckSource>
<RealTimeMonitoringLogicDefinition>
<EntityType>osfile</EntityType>
<Facets>
<FacetReference>
<Name>network_configuration_files</Name>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsFilteredFacet>0</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
<FacetReference>
<Name>maild_configuration_files</Name>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsFilteredFacet>0</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
<FacetReference>
<Name>sshd_configuration_files</Name>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsFilteredFacet>0</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
<FacetReference>
<Name>crontab_configuration_files</Name>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsFilteredFacet>0</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
<FacetReference>
<Name>kernel_configuration_files</Name>
<TargetType>host</TargetType>
<EntityType>osfile</EntityType>
<IsFilteredFacet>0</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
<FacetReference>
<Name>production_hours</Name>
<TargetType>host</TargetType>
<EntityType>timewindow</EntityType>
<IsFilteredFacet>1</IsFilteredFacet>
<InvertFilteredFacet>0</InvertFilteredFacet>
</FacetReference>
</Facets>
<ObservationTypes>
<ObservationType>
<Name>osfile_create_suc</Name>
</ObservationType>
<ObservationType>
<Name>osfile_content_modified_suc</Name>
</ObservationType>
<ObservationType>
<Name>osfile_delete_suc</Name>
</ObservationType>
<ObservationType>
<Name>osfile_content_mod_archive_suc</Name>
</ObservationType>
</ObservationTypes>
<Settings>
<CMSetting auto_authorized="0">
<CMConnector></CMConnector>
<AnnotateAuthObservation></AnnotateAuthObservation>
</CMSetting>
<AdvancedSetting>
<GroupSetting>
<ObsGroupIdleTimeout>15</ObsGroupIdleTimeout>
<ObsGroupMaxAge>30</ObsGroupMaxAge>
<ObsGroupMaxObservations>1000</ObsGroupMaxObservations>
</GroupSetting>
<GenerateEventByManualAuth>0</GenerateEventByManualAuth>
</AdvancedSetting>
</Settings>
<Options>
<Option value="10" name="osfile_archivenumber"/>
<Option value="50000" name="osfile_polling_maxfilealert"/>
<Option value="100" name="osfile_archive_maxsrcfilealert"/>
</Options>
</RealTimeMonitoringLogicDefinition>
</CheckSource>
<Severity>MinorWarning</Severity>
<LifeCycleStatus>Development</LifeCycleStatus>
<KeywordList>
<Keyword nlsid=”CONFIGURATION”>Configuration</keyword>
<Keyword nlsid=”SECURITY”>Security</keyword>
</KeywordList>
<ViolationMessage nlsid=”SAMPLE_RULE_VIOL_MSG”>Violation due to change in critical OS configuration files during production hours.</ViolationMessage>
<ClearViolationMessage nlsid=”SAMPLE_RULE_VIOL_CLRMSG”>Cleared violation due to change in critical OS configuration files during production hours.</ClearViolationMessage>
<Author>SYSMAN</Author>
</Rule>
13.3 Defining Compliance Standards
Compliance Standards are mapped to Compliance Standard Rules (Repository Rules or Real-time Monitoring Rules) in a hierarchical fashion.
Example 13-6 provides the syntax for defining compliance standards and Example 13-7 provides an example of a Compliance Standard Definition.
Note:
For the complete compliance XSDs, see the following JAR file:$ORACLE_HOME/sysman/jlib/gccomplianceCommon.jar
See Also:
For additional examples, see Section 13.10, "More Compliance Examples".Example 13-6 Compliance Standard Definition Syntax
<xsd:complexType name="StandardT">
<xsd:sequence>
<xsd:element name="DisplayName" type="std:DisplayString128Def" minOccurs="0"/>
<xsd:element name="TargetType" type="std:Name128Def" minOccurs="1" maxOccurs="1"/>
<xsd:element ref="std:TargetPropertyFilter" minOccurs="0"/>
<xsd:element name="Author" type="std:Name256Def" default="ORACLE" minOccurs="0"/>
<xsd:element name="Version" type="xsd:nonNegativeInteger" default="1" minOccurs="0"/>
<xsd:element name="LifeCycleStatus" default="Development" minOccurs="0">
<xsd:simpleType>
<xsd:restriction base="xsd:string">
<xsd:enumeration value="Development"/>
<xsd:enumeration value="Production"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>
<xsd:element name="IsHidden" type="std:BooleanDef" minOccurs="0" default="false"/>
<xsd:element name="IsSystem" type="std:BooleanDef" minOccurs="0" default="false"/>
<xsd:element name="IsAutoEnable" type="std:BooleanDef" minOccurs="0" default="false"/>
<xsd:element name="Description" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="KeywordList" type="std:KeywordListT" minOccurs="0"/>
<xsd:element name="ReferenceURL" type="std:String4000Def" minOccurs="0"/>
<xsd:element name="FrontMatter" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="RearMatter" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Notice" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Body" type="std:BodyT" minOccurs="0"/>
<xsd:element name="ExtraInfo" type="xsd:string" minOccurs="0" maxOccurs="1"/>
</xsd:sequence>
<xsd:attribute name="name" type="std:NameDef" use="required"/>
<xsd:attribute name="oms_version" type="std:Name32Def" use="required"/>
</xsd:complexType>
Table 13-5 provides a description of the tags used in defining Compliance Standards:
Table 13-5 Key Tags Used in Defining Compliance Standards
| Tag | Subtag | Description |
|---|---|---|
|
|
The display name of the compliance standard. It provides the nlsid attribute to support the translation of messages. Note: The nlsid attribute is not applicable to metadata plug-ins. |
|
|
|
The type of target to which this compliance standard can be associated |
|
|
|
Compliance standard author |
|
|
|
The version of the compliance standard |
|
|
|
Lifecycle status of compliance standard (Development or Production) |
|
|
|
True, if the compliance standard is provided out-of-the-box. Otherwise, False. |
|
|
|
Description of the compliance standard. It provides the nlsid attribute to support the translation of messages. |
|
|
|
If set to True, the compliance standard will be associated with all exiting targets for the defined target type. (Defined using TargetType) |
|
|
|
A list of keywords applicable to the compliance standard |
|
|
|
Keywords applicable to the compliance standard |
|
|
|
The reference URL of the compliance standard |
|
|
|
Front matter message. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Rear matter message. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Notice message. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Body of the compliance standard. Can have one or more of the following listed elements |
|
|
|
Defines a rule folder. A RuleFolder can have the following:
|
|
|
|
Include another compliance standard reference to the including compliance standard |
|
|
|
Include rule reference to the compliance standard |
Example 13-7 Sample Compliance Standard 1
<Standard xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_cs1">
<DisplayName nlsid="SAMPLE_CS_1_NAME">Sample Compliance Standard 1</DisplayName>
<TargetType>oracle_database</TargetType>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_CS_1_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Body>
<RuleFolder name="sample_RF_1">
<DisplayName nlsid="SAMPLE_RF_1_NAME">Sample Rulefolder</DisplayName>
<Description nlsid="SAMPLE_RF_1_DESC">This includes rules that checks for use of a single control file</Description>
<ReferenceURL>http://www.oracle.com/db_rf1</ReferenceURL>
<Importance>Normal</Importance>
<RuleReference>
<Name>sample_rule1</Name>
<TargetType>oracle_database</TargetType>
<Importance>Normal</Importance>
</RuleReference>
</RuleFolder>
</Body>
</Standard>
13.4 Defining a Compliance Framework
Note:
Although the Compliance Framework term is used throughout this document, the XML API uses the termGroup or SubGroup. This is an internal name used for the XML structure that is not exposed on the Enterprise Manager UI.Example 13-8 provides the syntax for defining a compliance framework and Example 13-9 provides an example of a compliance framework definition.
Note:
For the complete compliance XSDs, see the following JAR file:$ORACLE_HOME/sysman/jlib/gccomplianceCommon.jar
See Also:
For additional examples, see Section 13.10, "More Compliance Examples".Example 13-8 Compliance Framework Definition Syntax
<xsd:complexType name="StandardGroupT">
<xsd:sequence>
<xsd:element name="DisplayName" type="std:DisplayString128Def" minOccurs="0"/>
<xsd:element name="Author" type="std:Name256Def" default="ORACLE" minOccurs="0"/>
<xsd:element name="Version" type="xsd:nonNegativeInteger" default="1" minOccurs="0"/>
<xsd:element name="LifeCycleStatus" default="Development"minOccurs="0">
<xsd:simpleType>
<xsd:restriction base="xsd:string">
<xsd:enumeration value="Development"/>
<xsd:enumeration value="Production"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>
<xsd:element name="Description" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="KeywordList" type="std:KeywordListT" minOccurs="0"/>
<xsd:element name="ReferenceURL" type="std:String4000Def" minOccurs="0"/>
<xsd:element name="FrontMatter" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="RearMatter" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="Notice" type="std:DisplayString800Def" minOccurs="0"/>
<xsd:element name="IsHidden" type="std:BooleanDef" minOccurs="0"default="false"/>
<xsd:element name="IsSystem" type="std:BooleanDef" minOccurs="0"default="false"/>
<xsd:element name="GroupBody" type="std:GroupBodyT" minOccurs="0"/>
<xsd:element name="ExtraInfo" type="xsd:string" minOccurs="0"maxOccurs="1"/>
</xsd:sequence>
<xsd:attribute name="name" type="std:NameDef" use="required"/>
<xsd:attribute name="oms_version" type="std:Name32Def" use="required"/>
</xsd:complexType>
Table 13-6 provides a description of the tags used in defining a Compliance Framework:
Table 13-6 Key Tags Used in Defining a Compliance Framework
| Tag | Subtag | Description |
|---|---|---|
|
|
The display name of the compliance framework. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Author of the compliance framework |
|
|
|
The version of the compliance framework |
|
|
|
The lifecycle status of the compliance framework (Development or Production) |
|
|
|
True, if compliance framework is provided out-of-the box. Otherwise, False. |
|
|
|
Description of compliance framework. It provides the nlsid attribute to support the translation of messages. Note: The |
|
|
|
List of keywords applicable to compliance framework |
|
|
|
Keywords applicable to the compliance standard |
|
|
|
The reference URL of the compliance framework |
|
|
|
Front matter message. It provides the nlsid attribute to support the translation of messages |
|
|
|
Rear matter message. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Notice message. It provides the nlsid attribute to support the translation of messages. |
|
|
|
Additional information about the compliance framework. |
|
|
|
Defines the body of the compliance framework. It can have one or more of the following elements: |
|
|
|
Defines a child framework element. A child framework element can include the following: Child framework Include Standard Reference.
|
|
|
|
Includes the compliance standard reference to the compliance framework |
Example 13-9 Sample Compliance Framework
<StandardGroup xmlns="http://www.oracle.com/DataCenter/ConfigStd/" name="sample_csg" oms_version="12.1.0.1.0">
<DisplayName nlsid="SAMPLE_CSG_NAME">Sample Compliance Framework</DisplayName>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<Description nlsid="SAMPLE_CSG_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<IsHidden>false</IsHidden>
<IsSystem>true</IsSystem>
<GroupBody>
<SubGroup name="SampleSubgroup">
<DisplayName nlsid="SAMPLE_CSG_SUBGROUP_NAME">Sample Child Framework</DisplayName>
<Description nlsid="SAMPLE_CSG_SUBGROUP_DESC">Sample Child framework Description</Description>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Importance>Normal</Importance>
<StandardReference>
<Name>sample_cs3</Name>
<Author>SYSTEM</Author>
<Version>1</Version>
<Importance>Normal</Importance>
</StandardReference>
</SubGroup>
</GroupBody>
</StandardGroup>
13.5 Defining Compliance Content
Example 13-10 provides the syntax for defining compliance content and Example 13-11 provides an example of XML compliance metadata.
See Also:
For additional examples, see Section 13.10, "More Compliance Examples".Example 13-10 Compliance Content Definition Syntax
<xsd:complexType name="ComplianceContentT">
<xsd:sequence>
<!-- Cummulative change since the first release.-->
<xsd:element ref="std:ChangeList" minOccurs="0" maxOccurs="1"/>
<!-- End Cummulative change since the first release -->
<!-- Current state of entities -->
<xsd:element ref="std:Facet" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="std:Rule" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="std:Standard" minOccurs="0" maxOccurs="unbounded"/>
<xsd:element ref="std:StandardGroup" minOccurs="0" maxOccurs="unbounded"/>
<!-- Current state of entities -->
</xsd:sequence>
<xsd:attribute name="oms_version" type="std:Name32Def" use="required"/>
<xsd:attribute name="name" type="std:Name64Def" use="required"/>
<!-- content_version of compliance content should be equal to version of last change tag if any. -->
<xsd:attribute name="content_version" type="std:Name64Def" use="optional" default = "12.1.0.0.0"/>
<xsd:attribute name="IsCompareEnabled" type="std:BooleanDef" use="optional" default = "true"/>
</xsd:complexType>
<xsd:element name="ComplianceContent" type="std:ComplianceContentT"/>
Table 13-7 provides a description of some of the attributes used in defining compliance content:
Table 13-7 Compliance Content Attributes
| Attribute | Description |
|---|---|
|
|
Version of Oracle Management Service (OMS) |
|
|
Name of the compliance content |
|
|
Version of the compliance content |
|
|
Specifies whether a rule or compliance standard is updated incrementally or if the entire rule or compliance standard is regenerated. Possible Values:
Note: If you set Oracle recommends that you always summarize the changes in each version even if the |
Example 13-11 Sample XML Compliance Metadata
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!DOCTYPE ComplianceContent [
<!ENTITY rule SYSTEM "SampleRuleThresholdCondition.xml">
<!ENTITY standard SYSTEM "SampleComplianceStandard.xml">
<!ENTITY standardgroup SYSTEM "SampleComplianceStandardGroup.xml">
]>
<ComplianceContent xmlns="http://www.oracle.com/DataCenter/ConfigStd/" name="Sample Compliance Framework" oms_version="11.2.0.1.0">
<ChangeList>
<Change version="12.2.0.0.0">
<UpdateRule>
<RuleName>sample_rule</RuleName>
<TargetType>oracle_database</TargetType>
</UpdateRule>
<UpdateStandardGroup>
<StandardGroupName>sample_csg</StandardGroupName>
<StandardGroupAuthor>SYSTEM</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
</UpdateStandardGroup>
</Change>
</ChangeList>
&rule;
&standard;
&standardgroup;
</ComplianceContent>
13.6 Removing Compliance Content
To remove or delete compliance content, enter the following command:
emctl deregister oms metadata -sysman_pwd sysman -core -service gccompliance -file DeleteComplianceContent.xml
In the previous command, DeleteComplianceContent.xml represents the name of the Delete Compliance Content XML file.
Example 13-12 provides the syntax for defining Delete Compliance Content and Example 13-13 provides an example of a Delete Compliance Content XML file.
Example 13-12 Delete Compliance Content Syntax
<!-- delete compliance metadata corresponding to the compliance content name provided. -->
<xsd:complexType name="DeleteComplianceContentT">
<xsd:attribute name="name" type="std:Name64Def" use="required"/>
</xsd:complexType>
<xsd:element name="DeleteComplianceContent" type="std:DeleteComplianceContentT"/>
13.7 Supporting Translation
For each nlsid attribute in the XML samples, you must specify a Data Loading Format (DLF) map entry. A DLF file contains the English string for each defined nlsid attribute. These strings are available for translation.
<?xml version="1.0" encoding="UTF-8"?>
<table name="MGMT_MESSAGES">
<!-- lookup-key indicates which columns are used by
TransX to recognize a row as a duplicate -->
<lookup-key>
<column name="MESSAGE_ID"/>
<column name="SUBSYSTEM"/>
<column name="LANGUAGE_CODE"/>
<column name="COUNTRY_CODE"/>
</lookup-key>
<!-- columns field indicates which columns will be loaded as
part of processing the dataset and which should be
translated by the Translation Group -->
<columns>
<column name="MESSAGE_ID" type="string" maxsize="64"/>
<column name="SUBSYSTEM" type="string" maxsize="64"/>
<column name="LANGUAGE_CODE" type="string" language="%l"/>
<column name="COUNTRY_CODE" type="string" language="%Cs"/>
<column name="MESSAGE" type="string" maxsize="1000" translate="yes"/>
</columns>
<!-- dataset specifies the data to be loaded into the repository -->
<dataset>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_NAME</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Rule</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_DESC</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Checks for use of a single control file</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_IMPACT</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">The control file is one of the most important files in an
Oracle database. It maintains many physical characteristics and important
recovery information about the database. If you lose the only copy of the control
file due to a media error, there will be unnecessary down time and other risks.</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_RECO</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Use at least two control files that are multiplexed on different disks.</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_COL_1</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">FILE_LIST</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_COL_2</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">CONTROL_FILE_COUNT</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_VIOL_MSG</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">The database has an insufficient number of control files.</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RULE_VIOL_CLEAR_MSG</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">The database has sufficient number of control files.</col>
</row>
<!-- Standard NLSID Mappings -->
<row>
<col name="MESSAGE_ID">SAMPLE_CS_NAME</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Compliance Standard</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_CS_DESC</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Description</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RF_NAME</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Rulefolder</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_RF_DESC</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">This includes rules that checks for use of a single control file.</col>
</row>
<!-- Standard Group NLSID Mappings -->
<row>
<col name="MESSAGE_ID">SAMPLE_CSG_NAME</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Compliance Framework</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_CSG_DESC</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Description</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_CSG_SUBGROUP_NAME</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Child Framework</col>
</row>
<row>
<col name="MESSAGE_ID">SAMPLE_CSG_SUBGROUP_DESC</col>
<col name="SUBSYSTEM">POLICY</col>
<col name="MESSAGE">Sample Child Framework Description</col>
</row>
</dataset>
</table>
Note:
If the DLF entry is for a real-time monitoring facet or pattern, then the subsystem is GCCOMPLIANCE_CCC. For all other rules, the subsystem is POLICY.13.8 Packaging Compliance XML
This section indicates the location of the XML and DLF files.
-
XML Files
Store all the XML files in the following directory:
plugin_stage/oms/metadata/gccompliance/In the previous directory path, plugin_stage is the plug-in staging directory.
For more information about the plug-in staging directory, see Section 14.2, "Staging the Plug-in".
-
DLF Files
Store all the DLF files in the following directory:
plugin_stage/oms/rsc/area/gccompliance
In the previous directory path, plugin_stage is the plug-in staging directory and area represents the subcomponent such as
dbfor database orecmfor configuration management.
13.9 Setting Up and Testing Compliance Standards and Rules
To test your compliance standards or rules, do the following:
13.9.1 Install Compliance Content
To install compliance content:
-
Use the following command to install the compliance content:
emctl register oms metadata -sysman_pwd password -core -service gccompliance -file ComplianceContent.xml -
Submit the following job for back-end processing:
begin em_compliance_util.trigger_rule_dependency_job;end;
13.9.2 Test Compliance Standard
To test your compliance standard:
-
Log in to the Cloud Control console.
-
From the Enterprise menu, select Compliance, then select Library.
The Compliance Library page appears.
-
Click Compliance Standards.
-
Select the required compliance standard, then click Associate Targets.
The Target Association for Compliance Standard: Compliance Standard Name page appears, where Compliance Standard Name is the name of your selected compliance standard.
-
Click Add.
The Search and Select: Targets window appears.
-
Select the target that you want to evaluate, then click Select.
-
From the Target Association for Compliance Standard: Compliance Standard Name page, click OK.
-
Click Yes to the Save Association message.
The Compliance Standards page appears.
The previous steps trigger the evaluation, which occurs in a background job.
-
After a few minutes, from the Enterprise menu, select Compliance, then select Results.
The Compliance Standards Evaluation Results page appears.
-
Select your compliance standard, then click Show Details.
The Compliance Standard Result Detail page appears.
-
From the left-hand side of the page, expand Compliance Standard Name to view any nodes, then click a node to view the results for that node.
Figure 13-1 Compliance Standard Result Detail
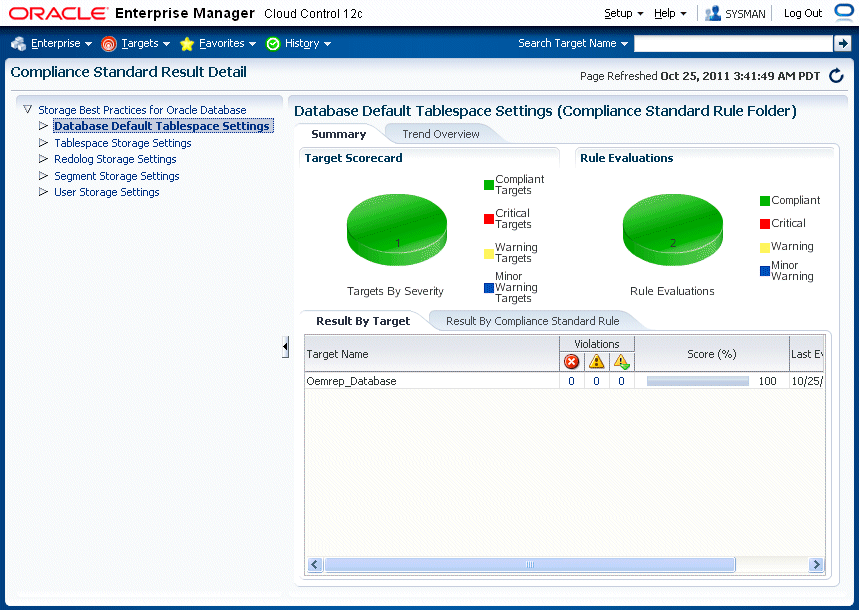
Description of ''Figure 13-1 Compliance Standard Result Detail''
13.9.3 Constraints for Testing
Note the following constraints when you are testing your compliance standards or rules:
-
The MGMT_VIEW user must have the SELECT privilege on the views used in the query
-
target_guid must be one of the SELECT attributes in the query
-
Alias names or select clause names must be less than 64 characters
-
Ensure that the standard references from a compliance standard are imported first. Place the standard references first in the compliance content list.
-
At least one column from the SELECT clause of the SQL source must be marked as a non-key column in the violation context definition and metric definition.
-
The target_guid column must not be specified for violation context columns or for metric definitions.
-
If the query references views from outside of the enclosing plug-in, then the views must be exposed by the EDK to the plug-in (at the plug-in EDK level).
-
If the SQL source query of a repository rule refers to a PLSQL function, then ensure that it refers to global PLSQL functions only, and not package functions (that is, if those PLSQL functions depend on tables whose update triggers a rule evaluation). This is required to generate the list of tables which the rule evaluation outcome depends on correctly. Execute privileges must be granted to the mgmt_view user on this function.
-
The target type of the rule included in a compliance standard must be the same as that of the immediate parent standard.
-
Key columns of STRING type must contain less than 64 characters.
13.10 More Compliance Examples
This section provides additional examples of compliance content, rules, compliance standards, and compliance framework.
Example 13-15 provides an example of compliance content version 1 and Example 13-26 provides an example of compliance content version 2. Version 1 is the initial version of the compliance content. Note that the content version number is 12.1.0.1.0, while the content version in Example 13-26 is 12.1.0.2.0.
Compliance content contains a ChangeList element. The ChangeList element describes the changes that have occurred since the first version of compliance content, such as updated rules, standards, and so on.
Example 13-15 Compliance Content Version 1
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!DOCTYPE ComplianceContent [
<!ENTITY rule1 SYSTEM "SampleRule1.xml">
<!ENTITY rule2 SYSTEM "SampleRule2.xml">
<!ENTITY rule3 SYSTEM "SampleRule3.xml">
<!ENTITY rule4 SYSTEM "SampleRule4.xml">
<!ENTITY rule5 SYSTEM "SampleRule5.xml">
<!ENTITY rule6 SYSTEM "SampleRule6.xml">
<!ENTITY standard1 SYSTEM "SampleComplianceStandard1.xml">
<!ENTITY standard2 SYSTEM "SampleComplianceStandard2.xml">
<!ENTITY standard3 SYSTEM "SampleComplianceStandard3.xml">
<!ENTITY standardgroup SYSTEM "SampleComplianceFramework.xml">]
]>
<ComplianceContent xmlns="http://www.oracle.com/DataCenter/ConfigStd/" name="SampleComplianceContent" oms_version="12.1.0.1.0" content_version="12.1.0.1.0">
<ChangeList>
<!-- ChangeList tag process each of the Change Tag with respect to the version of the ComplianceContent installed in repository. -->
<Change version="12.1.0.1.0">
<!-- AddSubGroupWithinStandardGroup will introduce a subgroup within an existing compliance framework/standard group in repository. -->
<!-- AddStandardReferenceToStandardGroup will introduce a reference to a standard within an existing compliance framework/standard group in repository. -->
<AddSubGroupWithinStandardGroup order="2">
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroup name="sampleSubgroup1">
<DisplayName>sub1</DisplayName>
<ReferenceURL>http://sampleAddedSubgroup.com</ReferenceURL>
<Importance>High</Importance>
</SubGroup>
</AddSubGroupWithinStandardGroup>
<AddStandardReferenceToStandardGroup>
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroupListInfo>
<SubGroupElem>oracle_pci_ctrlobj_a</SubGroupElem>
</SubGroupListInfo>
<StandardReference>
<Name>sample_cs1</Name>
<Author>SYSTEM</Author>
<Version>1</Version>
</StandardReference>
</AddStandardReferenceToStandardGroup>
</Change>
</ChangeList>
<!--List of compliance standard rules -->
&rule1;
&rule2;
&rule3;
&rule4;
&rule5;
&rule6;
<!--List of compliance standards -->
&standard1;
&standard2;
&standard3;
<!--List of compliance standard groups/frameworks-->
&standardgroup;
</ComplianceContent>
Example 13-16 provides an example of a compliance rule that checks for use of a single control file
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule1">
<DisplayName nlsid="SAMPLE_RULE_1_NAME">Sample Rule 1</DisplayName>
<TargetType>oracle_database</TargetType>
<IsSystem>true</IsSystem>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_operating_system</PropertyName>
<ValueList>
<Value>Windows</Value>
</ValueList>
</PropertyItem>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Description nlsid="SAMPLE_RULE_1_DESC">Checks for use of a single control file</Description>
<Impact nlsid="SAMPLE_RULE_1_IMPACT">The control file is one of the most
important files in an Oracle database. It maintains many physical characteristics
and important recovery information about the database. If you lose the only copy
of the control file due to a media error, there will be unnecessary down time and
other risks.</Impact>
<Recommendation nlsid="SAMPLE_RULE_1_RECO">Use at least two control files that are multiplexed on different disks.</Recommendation>
<ViolationContextList>
<Column type="String" name="FILE_LIST">
<DisplayLabel nlsid="SAMPLE_RULE_1_COL_1">FILE_LIST</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
<Column type="Number" name="CONTROL_FILE_COUNT">
<DisplayLabel nlsid="SAMPLE_RULE_1_COL_2">CONTROL_FILE_COUNT</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>oracle_database</TargetType>
<MetricName>sample_rule1</MetricName>
<SourceType>SQL</SourceType>
<Source>select CONTROL_FILE_COUNT, FILE_LIST, TARGET_GUID from MGMT$CS_DB_CONTROL_FILE_COUNT</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>FILE_LIST</ColumnName>
<ColumnType>String</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_1_COL_1">FILE_LIST</ColumnLabel>
</MetricColumnInfo>
<MetricColumnInfo>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_1_COL_2">CONTROL_FILE_COUNT</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<MinorWarnThreshold>1</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<ThresholdCriteria>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<TestOperator>EQ</TestOperator>
<ThresholdValue>1</ThresholdValue>
<ThresholdType>Number</ThresholdType>
</ThresholdCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>MinorWarning</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_1_VIOL_MSG">The database has an insufficient number of control files.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_1_VIOL_CLEAR_MSG">The database has sufficient number of control files.</ClearViolationMessage>
<Author>SYSMAN</Author>
</Rule>
Example 13-17 provides an example of a sample compliance rule that checks for use of a single control file.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule2">
<DisplayName nlsid="SAMPLE_RULE_2_NAME">Sample Rule 2</DisplayName>
<TargetType>oracle_database</TargetType>
<IsSystem>true</IsSystem>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_operating_system</PropertyName>
<ValueList>
<Value>Windows</Value>
</ValueList>
</PropertyItem>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Description nlsid="SAMPLE_RULE_2_DESC">Checks for use of a single control file</Description>
<Impact nlsid="SAMPLE_RULE_2_IMPACT">The control file is one of the most important files in an Oracle database.
It maintains many physical characteristics and important recovery information
about the database. If you lose the only copy of the control file due to a media
error, there will be unnecessary down time and other risks.</Impact>
<Recommendation nlsid="SAMPLE_RULE_2_RECO">Use at least two control files that are multiplexed on different disks.</Recommendation>
<ViolationContextList>
<Column type="String" name="FILE_LIST">
<DisplayLabel nlsid="SAMPLE_RULE_2_COL_1">FILE_LIST</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
<Column type="Number" name="CONTROL_FILE_COUNT">
<DisplayLabel nlsid="SAMPLE_RULE_2_COL_2">CONTROL_FILE_COUNT</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>oracle_database</TargetType>
<MetricName>sample_rule2</MetricName>
<SourceType>SQL</SourceType>
<Source>select CONTROL_FILE_COUNT, FILE_LIST, TARGET_GUID from MGMT$CS_DB_CONTROL_FILE_COUNT</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>FILE_LIST</ColumnName>
<ColumnType>String</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_2_COL_1">FILE_LIST</ColumnLabel>
</MetricColumnInfo>
<MetricColumnInfo>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_2_COL_2">CONTROL_FILE_COUNT</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<MinorWarnThreshold>1</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<ThresholdCriteria>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<TestOperator>EQ</TestOperator>
<ThresholdValue>1</ThresholdValue>
<ThresholdType>Number</ThresholdType>
</ThresholdCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>MinorWarning</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_2_VIOL_MSG">The database has an insufficient number of control files.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_2_VIOL_CLEAR_MSG">The database has sufficient number of control files.</ClearViolationMessage>
<Author>SYSMAN</Author>
</Rule>
Example 13-18 provides an example of a compliance rule that checks for use of a single control file.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule3">
<DisplayName nlsid="SAMPLE_RULE_3_NAME">Sample Rule 3</DisplayName>
<TargetType>oracle_database</TargetType>
<IsSystem>true</IsSystem>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_operating_system</PropertyName>
<ValueList>
<Value>Windows</Value>
</ValueList>
</PropertyItem>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Description nlsid="SAMPLE_RULE_3_DESC">Checks for use of a single control file</Description>
<Impact nlsid="SAMPLE_RULE_3_IMPACT">The control file is one of the most important files in an Oracle database.
It maintains many physical characteristics and important recovery information
about the database. If you lose the only copy of the control file due to a media
error, there will be unnecessary down time and other risks.</Impact>
<Recommendation nlsid="SAMPLE_RULE_3_RECO">Use at least two control files that are multiplexed on different disks.</Recommendation>
<ViolationContextList>
<Column type="String" name="FILE_LIST">
<DisplayLabel nlsid="SAMPLE_RULE_3_COL_1">FILE_LIST</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
<Column type="Number" name="CONTROL_FILE_COUNT">
<DisplayLabel nlsid="SAMPLE_RULE_3_COL_2">CONTROL_FILE_COUNT</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>false</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>oracle_database</TargetType>
<MetricName>sample_rule3</MetricName>
<SourceType>SQL</SourceType>
<Source>select CONTROL_FILE_COUNT, FILE_LIST, TARGET_GUID from MGMT$CS_DB_CONTROL_FILE_COUNT</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>FILE_LIST</ColumnName>
<ColumnType>String</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_3_COL_1">FILE_LIST</ColumnLabel>
</MetricColumnInfo>
<MetricColumnInfo>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>false</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_3_COL_2">CONTROL_FILE_COUNT</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>CONTROL_FILE_COUNT</ParamName>
<MinorWarnThreshold>1</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<ThresholdCriteria>
<ColumnName>CONTROL_FILE_COUNT</ColumnName>
<TestOperator>EQ</TestOperator>
<ThresholdValue>1</ThresholdValue>
<ThresholdType>Number</ThresholdType>
</ThresholdCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>MinorWarning</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_3_VIOL_MSG">The database has an insufficient number of control files.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_3_VIOL_CLEAR_MSG">The database has sufficient number of control files.</ClearViolationMessage>
<Author>SYSMAN</Author>
</Rule>
Example 13-19 provides an example of a compliance rule that checks that no unintended ports are left open.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule4">
<DisplayName nlsid="SAMPLE_RULE_4_NAME">Sample Rule 4</DisplayName>
<TargetType>host</TargetType>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_RULE_4_DESC">Ensure that no unintended ports are left open</Description>
<Impact nlsid="SAMPLE_RULE_4_IMPACT">Open ports may allow a malicious user to take over the host.</Impact>
<Recommendation nlsid="SAMPLE_RULE_4_RECOMM">Do not open insecure ports.</Recommendation>
<ViolationContextList>
<Column type="Number" name="port">
<DisplayLabel nlsid="SAMPLE_RULE_4_PORT_COL">Port Number</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>true</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>host</TargetType>
<MetricName>sample_rule4</MetricName>
<SourceType>SQL</SourceType>
<Source>SELECT target_guid, port as port, port as dummy FROM MGMT$ESM_PORTS_LATEST</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>port</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>true</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_4_LABEL">Port Number</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName nlsid="SAMPLE_RULE_4_DFLT_PORT_PNAME">DFLT_PORT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>DFLT_PORT</ParamName>
<MinorWarnThreshold>655</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<SqlWhereClauseCriteria>
<WhereClause>:port < :DFLT_PORT</WhereClause>
</SqlWhereClauseCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>Critical</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_4_MESG">The host is in an insecure state. Port %port% is open.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_4_CLR_MESG">Port %port% is not open.</ClearViolationMessage>
<Author>ORACLE</Author>
<LastUpdatedBy><SYSTEM></LastUpdatedBy>
</Rule>
Example 13-20 provides an example of a compliance rule that checks that no unintended ports are left open.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule5">
<DisplayName nlsid="SAMPLE_RULE_5_NAME">Sample Rule 5</DisplayName>
<TargetType>host</TargetType>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_RULE_5_DESC">Ensure that no unintended ports are left open</Description>
<Impact nlsid="SAMPLE_RULE_5_IMPACT">Open ports may allow a malicious user to take over the host.</Impact>
<Recommendation nlsid="SAMPLE_RULE_5_RECOMM">Do not open insecure ports.</Recommendation>
<ViolationContextList>
<Column type="Number" name="port">
<DisplayLabel nlsid="SAMPLE_RULE_5_PORT_COL">Port Number</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>true</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>host</TargetType>
<MetricName>sample_rule5</MetricName>
<SourceType>SQL</SourceType>
<Source>SELECT target_guid, port as port, port as dummy FROM MGMT$ESM_PORTS_LATEST</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>port</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>true</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_5_LABEL">Port Number</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName nlsid="SAMPLE_RULE_5_DFLT_PORT_PNAME">DFLT_PORT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>DFLT_PORT</ParamName>
<MinorWarnThreshold>655</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<SqlWhereClauseCriteria>
<WhereClause>:port < :DFLT_PORT</WhereClause>
</SqlWhereClauseCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>Critical</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_5_MESG">The host is in an insecure state. Port %port% is open.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_5_CLR_MESG">Port %port% is not open.</ClearViolationMessage>
<Author>ORACLE</Author>
<LastUpdatedBy><SYSTEM></LastUpdatedBy>
</Rule>
Example 13-21 provides an example of a compliance rule that checks that no unintended ports are left open.
<Rule xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_rule6">
<DisplayName nlsid="SAMPLE_RULE_6_NAME">Sample Rule 6</DisplayName>
<TargetType>host</TargetType>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_RULE_6_DESC">Ensure that no unintended ports are left open</Description>
<Impact nlsid="SAMPLE_RULE_6_IMPACT">Open ports may allow a malicious user to take over the host.</Impact>
<Recommendation nlsid="SAMPLE_RULE_6_RECOMM">Do not open insecure ports.</Recommendation>
<ViolationContextList>
<Column type="Number" name="port">
<DisplayLabel nlsid="SAMPLE_RULE_6_PORT_COL">Port Number</DisplayLabel>
<IsHidden>false</IsHidden>
<IsKey>true</IsKey>
</Column>
</ViolationContextList>
<CheckSource>
<RepositoryCheckDefinition>
<Metric>
<TargetType>host</TargetType>
<MetricName>sample_rule6</MetricName>
<SourceType>SQL</SourceType>
<Source>SELECT target_guid, port as port, port as dummy FROM MGMT$ESM_PORTS_LATEST</Source>
<MetricColumnList>
<MetricColumnInfo>
<ColumnName>port</ColumnName>
<ColumnType>Number</ColumnType>
<isKey>true</isKey>
<ColumnLabel nlsid="SAMPLE_RULE_6_LABEL">Port Number</ColumnLabel>
</MetricColumnInfo>
</MetricColumnList>
</Metric>
<ParameterList>
<RuleParameter>
<ParamName nlsid="SAMPLE_RULE_6_DFLT_PORT_PNAME">DFLT_PORT</ParamName>
<ParamType>Number</ParamType>
</RuleParameter>
</ParameterList>
<ParameterDefaultSettings>
<ParamValue>
<ParamName>DFLT_PORT</ParamName>
<MinorWarnThreshold>655</MinorWarnThreshold>
</ParamValue>
</ParameterDefaultSettings>
<TestCondition>
<SqlWhereClauseCriteria>
<WhereClause>:port < :DFLT_PORT</WhereClause>
</SqlWhereClauseCriteria>
</TestCondition>
</RepositoryCheckDefinition>
</CheckSource>
<Severity>Critical</Severity>
<LifeCycleStatus>Production</LifeCycleStatus>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ViolationMessage nlsid="SAMPLE_RULE_6_MESG">The host is in an insecure state. Port %port% is open.</ViolationMessage>
<ClearViolationMessage nlsid="SAMPLE_RULE_6_CLR_MESG">Port %port% is not open.</ClearViolationMessage>
<Author>ORACLE</Author>
<LastUpdatedBy><SYSTEM></LastUpdatedBy>
</Rule>
Example 13-22 provides an example of a compliance standard that includes rules to check for use of a single control file.
Example 13-22 Sample Compliance Standard 1
<Standard xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_cs1">
<DisplayName nlsid="SAMPLE_CS_1_NAME">Sample Compliance Standard 1</DisplayName>
<TargetType>oracle_database</TargetType>
<TargetPropertyFilter>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>Windows</Value>
</ValueList>
</PropertyItem>
<PropertyItem>
<PropertyName>orcl_gtp_target_version</PropertyName>
<ValueList>
<Value>8.1.6+</Value>
</ValueList>
</PropertyItem>
</TargetPropertyFilter>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_CS_1_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="CONFIGURATION">Configuration</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Body>
<RuleFolder name="sample_RF_1">
<DisplayName nlsid="SAMPLE_RF_1_NAME">Sample Rulefolder</DisplayName>
<Description nlsid="SAMPLE_RF_1_DESC">This includes rules that checks for use of a single control file</Description>
<ReferenceURL>http://www.oracle.com/db_rf1</ReferenceURL>
<Importance>Normal</Importance>
<RuleReference>
<Name>sample_rule1</Name>
<TargetType>oracle_database</TargetType>
<Importance>Normal</Importance>
</RuleReference>
</RuleFolder>
</Body>
</Standard>
Example 13-23 provides an example of a compliance standard that includes rules to check for open unsecured ports.
Example 13-23 Sample Compliance Standard 2
<Standard xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_cs2">
<DisplayName nlsid="SAMPLE_CS_2_NAME">Sample Compliance Standard 2</DisplayName>
<TargetType>host</TargetType>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_CS_2_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Body>
<RuleFolder name="sample_RF_2">
<DisplayName nlsid="SAMPLE_RF_2_NAME">Sample Rulefolder</DisplayName>
<Description nlsid="SAMPLE_RF_2_DESC">This includes rules that checks for open insecure ports.</Description>
<ReferenceURL>http://www.oracle.com/db_rf1</ReferenceURL>
<Importance>Normal</Importance>
<RuleReference>
<Name>sample_rule4</Name>
<TargetType>host</TargetType>
<Importance>Normal</Importance>
</RuleReference>
</RuleFolder>
</Body>
</Standard>
Example 13-24 provides an example of a compliance standard that includes rules to check for open unsecured ports.
Example 13-24 Sample Compliance Standard 3
<Standard xmlns="http://www.oracle.com/DataCenter/ConfigStd/" oms_version="12.1.0.1.0" name="sample_cs3">
<DisplayName nlsid="SAMPLE_CS_3_NAME">Sample Compliance Standard 3</DisplayName>
<TargetType>host</TargetType>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<IsSystem>true</IsSystem>
<Description nlsid="SAMPLE_CS_3_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Body>
<RuleFolder name="sample_RF_3">
<DisplayName nlsid="SAMPLE_RF_3_NAME">Sample Rulefolder</DisplayName>
<Description nlsid="SAMPLE_RF_3_DESC">This includes rules that checks for open insecure ports.</Description>
<ReferenceURL>http://www.oracle.com/db_rf1</ReferenceURL>
<Importance>Normal</Importance>
<RuleReference>
<Name>sample_rule5</Name>
<TargetType>host</TargetType>
<Importance>Normal</Importance>
</RuleReference>
</RuleFolder>
</Body>
</Standard>
]]
Example 13-25 provides an example of a compliance framework.
Example 13-25 Sample Compliance Framework
<StandardGroup xmlns="http://www.oracle.com/DataCenter/ConfigStd/" name="sample_csg" oms_version="12.1.0.1.0">
<DisplayName nlsid="SAMPLE_CSG_NAME">Sample Compliance Framework</DisplayName>
<Author>SYSTEM</Author>
<Version>1</Version>
<LifeCycleStatus>Production</LifeCycleStatus>
<Description nlsid="SAMPLE_CSG_DESC">Sample Description</Description>
<KeywordList>
<Keyword nlsid="SECURITY">Security</Keyword>
</KeywordList>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<IsHidden>false</IsHidden>
<IsSystem>true</IsSystem>
<GroupBody>
<SubGroup name="SampleSubgroup">
<DisplayName nlsid="SAMPLE_CSG_SUBGROUP_NAME">Sample Child Framework</DisplayName>
<Description nlsid="SAMPLE_CSG_SUBGROUP_DESC">Sample Child framework Description</Description>
<ReferenceURL>http://sampleurl.com</ReferenceURL>
<Importance>Normal</Importance>
<StandardReference>
<Name>sample_cs3</Name>
<Author>SYSTEM</Author>
<Version>1</Version>
<Importance>Normal</Importance>
</StandardReference>
</SubGroup>
</GroupBody>
</StandardGroup>
Example 13-26 provides an example of compliance content.
Example 13-26 Compliance Content Version 2
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<!DOCTYPE ComplianceContent [
<!ENTITY rule1 SYSTEM "SampleRule1.xml">
<!ENTITY rule2 SYSTEM "SampleRule2.xml">
<!ENTITY rule3 SYSTEM "SampleRule3.xml">
<!ENTITY rule5 SYSTEM "SampleRule5.xml">
<!ENTITY rule6 SYSTEM "SampleRule6.xml">
<!ENTITY standard1 SYSTEM "SampleComplianceStandard1.xml">
<!ENTITY standard3 SYSTEM "SampleComplianceStandard3.xml">
<!ENTITY standardgroup SYSTEM "SampleComplianceFramework.xml">
]>
<ComplianceContent xmlns="http://www.oracle.com/DataCenter/ConfigStd/" name="SampleComplianceContent" oms_version="12.1.0.1.0" content_version="12.1.0.2.0">
<ChangeList>
<!-- ChangeList tag process each of the Change Tag with respect to the version of the ComplianceContent installed in repository. -->
<Change version="12.1.0.1.0">
<!-- AddSubGroupWithinStandardGroup/AddStandardReferenceToStandardGroup tags will modify StandardGroup definition. -->
<!-- AddSubGroupWithinStandardGroup will introduce a subgroup within an existing compliance framework/standard group in repository. -->
<!-- AddStandardReferenceToStandardGroup will introduce a reference to a standard within an existing compliance framework/standard group in repository. -->
<AddSubGroupWithinStandardGroup order="2">
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroup name="sampleSubgroup1">
<DisplayName>sub1</DisplayName>
<ReferenceURL>http://sampleAddedSubgroup.com</ReferenceURL>
<Importance>High</Importance>
</SubGroup>
</AddSubGroupWithinStandardGroup>
<AddStandardReferenceToStandardGroup>
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroupListInfo>
<SubGroupElem>oracle_pci_ctrlobj_a</SubGroupElem>
</SubGroupListInfo>
<StandardReference>
<Name>sample_cs1</Name>
<Author>SYSTEM</Author>
<Version>1</Version>
</StandardReference>
</AddStandardReferenceToStandardGroup>
</Change>
<Change version="12.1.0.2.0">
<!-- Delete will be remove rule/standard from repository if present, else it will be noop. -->
<DeleteStandard>
<StandardName>sample_cs2</StandardName>
<StandardAuthor>SYSTEM</StandardAuthor>
<StandardVersion>1</StandardVersion>
</DeleteStandard>
<DeleteRule>
<RuleName>sample_rule4</RuleName>
<TargetType>host</TargetType>
</DeleteRule>
<!-- Entities with Update tag will override definitions if they exist in the repository. -->
<!-- Please note that if standard/rule is updated then old results are
replaced by new results based on standard/rule definition after update. -->
<UpdateRule>
<RuleName>sample_rule5</RuleName>
<TargetType>host</TargetType>
</UpdateRule>
<UpdateStandard>
<StandardName>sample_cs3</StandardName>
<StandardAuthor>SYSTEM</StandardAuthor>
<StandardVersion>1</StandardVersion>
</UpdateStandard>
<UpdateStandardGroup>
<StandardGroupName>sample_csg</StandardGroupName>
<StandardGroupAuthor>SYSTEM</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
</UpdateStandardGroup>
<!-- AddSubGroupWithinStandardGroup will introduce a subgroup within an existing compliance framework/standard group in repository. -->
<!-- AddStandardReferenceToStandardGroup will introduce a reference to a standard within an existing compliance framework/standard group in repository. -->
<AddSubGroupWithinStandardGroup order="2">
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroup name="sampleSubgroup2">
<DisplayName>sub2</DisplayName>
<ReferenceURL>http://sampleAddedSubgroup.com</ReferenceURL>
<Importance>High</Importance>
</SubGroup>
</AddSubGroupWithinStandardGroup>
<AddStandardReferenceToStandardGroup>
<StandardGroupName>oracle_pci</StandardGroupName>
<StandardGroupAuthor>ORACLE</StandardGroupAuthor>
<StandardGroupVersion>1</StandardGroupVersion>
<SubGroupListInfo>
<SubGroupElem>oracle_pci_ctrlobj_a</SubGroupElem>
</SubGroupListInfo>
<StandardReference>
<Name>sample_cs3</Name>
<Author>SYSTEM</Author>
<Version>1</Version>
</StandardReference>
</AddStandardReferenceToStandardGroup>
</Change>
</ChangeList>
<!--List of compliance standard rules -->
&rule1;
&rule2;
&rule3;
&rule5;
&rule6;
<!--List of compliance standards -->
&standard1;
&standard3;
<!--List of compliance standard groups/frameworks -->
&standardgroup;
</ComplianceContent>
13.11 Publishing Compliance Content Using Self Update
If you want to publish compliance content without having to deploy the plug-in, than use the Self Update console.
To publish and apply compliance content from the Self Update console:
-
Create a compliance content JAR file from the XML content using the following command:
-jar cvfM compliancecontent.jar compliance_content_filesNote:
Similarly, multiple DLF files can be combined in a JAR file. -
Create a manifest file to specify the name of the compliance content, label, and the version of the compliance content to be published. This manifest file specifies compliancecontent.jar and compliancedlf.jar in order respectively.
Example 13-27 Sample Manifest File
<?xml version="1.0" encoding="utf-8"?> <tns:EntityInstance xmlns:tns="http://www.oracle.com/EnterpriseGridControl/SelfUpdateManifest/" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" EntityType="param" EntityTypeVersion="12.1.0.1.0" Vendor="Oracle" Maturity="TEST"> <tns:Description><![CDATA[<param>]]></tns:Description> <tns:AttributeList> <tns:Version>12.1.0.1.0</tns:Version> <tns:Attribute Name="name" Value="<param>" Label="display_name"/> </tns:AttributeList> <tns:Readme><![CDATA[ <param>]]> </tns:Readme> <tns:CustomParamList/> <tns:DependsOn/> <tns:ArchiveList> <tns:Archive Filename="param"/> <tns:Archive Filename="param"/> </tns:ArchiveList> <tns:CustomData/> </tns:EntityInstance>
-
Create a SAR (self update archive) file from the manifest file, compliancecontent.jar, and compliancedlf.jar using the following command:
edkutil prepare_update -manifest manifest_file_name -archivedir directory_containing_compliancecontent.jar_and_compliancedlf.jar -out sar_file_name
Note:
Before you import the SAR file into Enterprise Manager, make sure that the Software Library is configured.For more information, see Section 14.5.1.1, "Setting Up the Software Library".
-
Import the SAR file into Enterprise Manager using the following command:
emcli import_update -omslocal -file=complete_path_to_sar_fileNote:
Using the-omslocalflag means that the file must be placed on the Oracle Management Server (OMS) file system. -
Log in to Enterprise Manager. From the Setup menu, select Extensibility, and then Self Update.
The Self Update page appears.
-
From the Status area, check that Downloaded Updates is set to 1 for Compliance Content.
-
In the Type column, click Compliance Content.
The Self Update: Compliance Content page appears.
-
Select the row with downloaded in the Status column, then Apply. Follow the steps in the wizard that appears.
-
From the Actions list, select Apply and check that the Status column reads succeeded.
-
Verify the imported compliance content from the Compliance Library. To view the Compliance Library, from the Enterprise menu, select Compliance, then select Library.