25 Configuring EnterpriseOne Security Auditing
This chapter contains the following topics:
25.1 Overview of EnterpriseOne Auditing Tools
Oracle recommends that you regularly run security reports to review existing security records and ensure that users have the appropriate level of access to system objects and data. EnterpriseOne contains a set of reports and tools than enable you to audit security records and other security-related information. The auditing mechanisms include:
-
Security Analyzer Reports
Run these reports to review the sign-in security records by data source and by user or role.
-
Security Workbench Records Reports
Run these reports to review the object security records by object type and user or
role.
-
Auditing Tools for Administering 21 CFR Part 11 Auditing
Oracle's JD Edwards EnterpriseOne auditing and electronic signature tools provide a solution to the Food and Drug Administration's (FDA) acceptance of electronic signatures and audit records for FDA-required records such as product submissions, batch records, and complaints. These tools enable your organization to comply with the FDA 21 CFR Part 11 regulation for submitting electronic records. See the JD Edwards EnterpriseOne Tools Auditing Administration Including 21 CFR Part 11 Administration Guide for instructions on how to administer auditing for 21 CFR Part 11.
25.2 Running a Security Analyzer Report
This section contains the following topics:
-
Running the Security Analyzer by Data Source Report (R98OWSECA)
-
Running the Security Analyzer by User or Group Report (R98OWSECB)
25.2.1 Understanding the Security Analyzer Report
This process generates two separate reports that provide you with an analysis of JD Edwards EnterpriseOne security. The first report is the Security Analyzer by Data Source (R98OWSECA); it is organized and sorted by data source. A blank data source means that security for the System User ID is applicable to all data sources. The Security Analyzer by Data Source report is based on data that it reads from the F98OWSEC table.
The second report is the Security Analyzer by User or Group (R98OWSECB); it is organized by user or role. The Security Analyzer by User or Role report is also based on data that it reads from the F98OWSEC table.
25.2.2 Form Used to Run a Security Analyzer Report
| Form Name | FormID | Navigation | Usage |
|---|---|---|---|
| Work With Batch Versions - Available Versions | W98305A | Report Management (GH9111), Batch Versions (P98305) | Run the Security Analyzer by Data Source (R98OWSECA) and Security Analyzer by User or Group (R98OWSECB) reports. |
25.2.3 Running the Security Analyzer by Data Source Report (R98OWSECA)
This report presents security analysis information for each data source, each user ID, and each role. The report is sorted by data source and then by user ID. This columnar data appears in the report:
-
Data Source
The data source to which the user is secured. Blank indicates all data sources.
-
User ID
-
User / Role
An identification code for a user profile.
-
System User ID
The actual user that JD Edwards EnterpriseOne uses to connect to the DBMS that you specified as the data source. This system user must match the user value that is defined in the DBMS.
-
Change Frequency
The number of days before the system requires that a user change their password. This data can be set by individual user ID or by role.
-
Source Password Changed
The date when a user's password was last changed.
-
Invalid Signons
The number of invalid sign-in attempts by a user. If the retry count value exceeds the number of allowed attempts, the user profile is disabled.
-
Allowed Attempts
The number of sign-in attempts that a user can make before that user profile is disabled.
-
User Status
A value that indicates whether the user can sign in to JD Edwards EnterpriseOne. Values are 01 (enabled) and 02 (disabled).
-
Status
The display status of the User Status field.
Access the Work With Batch Versions - Available Versions form to run the Security Analyzer by Data Source Report (R98OWSECA).
-
Select a version and then click Select.
The default version is XJDE0001. It creates a report for all user IDs for all data sources.
-
On the Version Prompting form, click Submit.
-
On the Report Output Destination form, select any of these options:
-
On Screen
-
To Printer
-
Export to CSV
-
-
If desired, select the OSA Interface Name option and enter a name in the box that appears.
25.2.4 Running the Security Analyzer by User or Group Report (R98OWSECB)
The Security Analyzer by User or Group Report (R98OWSECB) report presents security analysis information for each user ID, each group, and each data source. The report is sorted either by user ID or user group, depending on which processing option you select. This columnar data appears in the report:
-
User ID
-
Role
-
Password Change Frequency
The number of days before a user must change their password. This data can be set by individual user ID or by group.
-
Data Source
The data source to which the user is secured. A blank indicates all data sources.
-
System User
The actual user that the software uses to connect to the DBMS that you specified as the data source. The system user that is defined here must match the user value that is defined in the DBMS.
Access the Work With Batch Versions - Available Versions form to run the Security Analyzer by User or Group Report (R98OWSECB).
-
Select a version and click Select.
The default version is XJDE0001. It creates a report for all user IDs for all data sources.
By default, the XJDE0001 version has the processing option for this report set to 1. This option generates a report by user ID.
To generate a report by role, you can prompt for processing options and then, on the User Setup tab, change the value to 2.
-
On the Version Prompting form, click Submit.
-
Complete the processing options as necessary, and then click OK.
-
On Report Output Destination, select any of these options:
-
On Screen
-
To Printer
-
Export to CSV
-
-
If desired, select the OSE Interface Name option and type a name in the field that appears.
25.3 Running Security Workbench Records Reports
This section provides an overview of the Security Workbench Records reports and discusses how to:
-
Run the Security Audit Report by Object version (R009501, XJDE0001).
-
Run the Security Audit Report by User version (R009502, XJDE0001).
-
Run the Security Audit Report by Role version (R009502, XJDE0002).
25.3.1 Understanding the Security Workbench Records Reports
JD Edwards EnterpriseOne provides two Security Workbench Records reports—Security by Object (R009501) and Security by User/Role (R009502)—that you can run to review the current security records by object type and user or role. The Security Workbench Records reports list security records for these objects:
-
Interactive and batch applications.
-
Tables (rows and columns).
-
Published business services.
Before choosing which report to run, you should consider the data that you want the report to produce. Run the Security by Object report (R009501) to generate a report that lists the security records based on a particular object, object type, or product code. You can refine the data selection for this report to list only records for a particular user ID, role, or a combination of user ID and role. Run the Security by User/Role report (R009502) to generate a report that lists all the application, row, column, and published business service security records for a particular user ID, role, or *PUBLIC.
Each report contains processing options that you can use to define the output of the report. Along with the processing options, you can use the Data Selection form in the Batch Version application (P98305W) to further refine the data that the report produces.
Each security record in the report indicates the level of security, or type of security, that is applied to the object. For application security, each record indicates if a user or role has permission to install, run, or both install and run the application. For row security, each record indicates if view, add, change, or delete security have been applied. For column security, each record indicates if view, add, or change security have been applied. For published business service security, each record indicates whether a user or role has access to the published business service object.
How you set up your report determines how readily you can find gaps in your security plan. For example, if you have a highly sensitive application and you want to ensure that only the appropriate users have access to it, you can refine the R009501 report (Security Audit Report by Object) to list only the security records for that particular application.
25.3.1.1 Example of Security by Object Report (R009501)
This example shows the results of running the R009501 report. The report has been set up to list all the security records for the P00950 application.
Figure 25-1 Example of Security by Object Report.
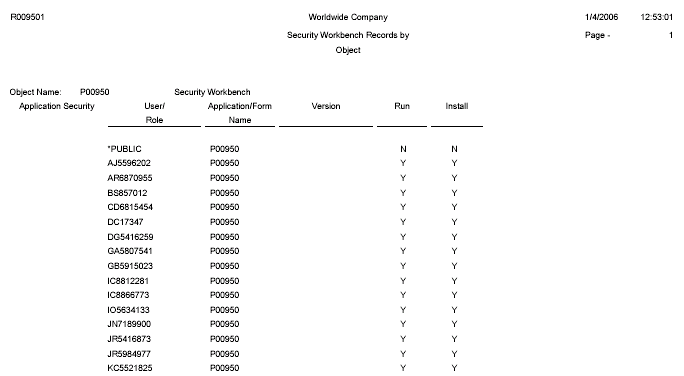
Description of ''Figure 25-1 Example of Security by Object Report.''
25.3.1.2 Example of Security Audit Report by User (R009502, XJDE0001)
This example shows the results of running the Security Audit Report by User version of the R009502 report. The report lists the security records for a particular user in order of application, row, and then column. This example shows only the first page of the report, which lists the application security records for the user ID.
Figure 25-2 Example of Security Audit Report by User Report
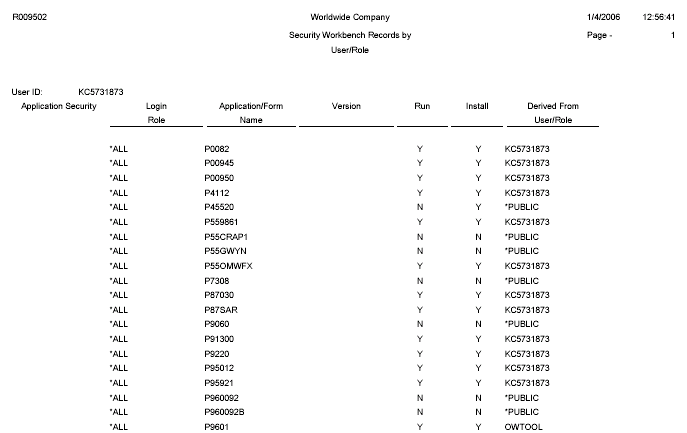
Description of ''Figure 25-2 Example of Security Audit Report by User Report''
25.3.1.3 Example of Security Audit Report by Role (R009502, XJDE0002)
This example shows the results of running the Security Audit Report by Role version of the R009502 report. The data selection of the report has been defined to list security records for the OWTOOL role. This example shows the third page of the report, which lists the row and column security records for the OWTOOL role.
Figure 25-3 Example of Security Audit Report by Role
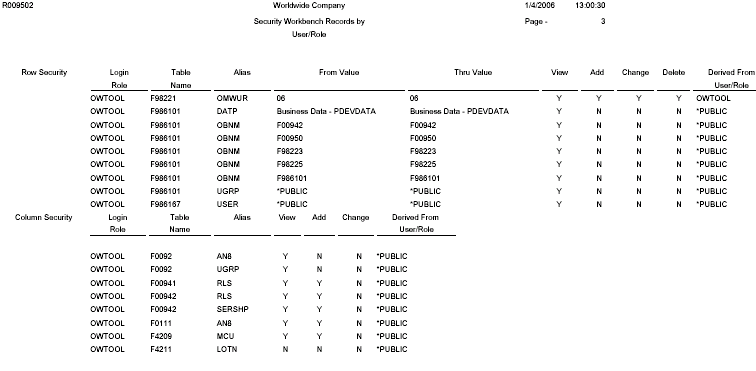
Description of ''Figure 25-3 Example of Security Audit Report by Role''
25.3.2 Run the Security Audit Report by Object Version (R009501, XJDE0001)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
-
In the Batch Application field, enter R009501 and click the Find button.
-
Select the Security Audit Report by Object version.
-
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
-
User ID or Role (optional)
Enter a user ID or role to refine the report to generate only records based on that particular user ID or role.
-
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
-
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
-
Report on Column Security
Leave blank if you want the report to list application security records. Enter 1 to exclude application security records.
-
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
Note:
In addition, to generate a report that displays published business service security records, you need to add an additional condition in the Data Selection form, as discussed below.
-
-
On the Work With Batch Versions - Available Versions form, click Select.
-
On the Versions Detail form, select the Data Selection check box and click the Submit button.
-
On the Data Selection form, you can add a condition to filter on a particular object, object type, or product code.
If the processing option is set to list published business service security records, you must add the following condition after the default
Wherecondition:And BC Source Language (F9860) (SRCLNG) [BC] is equal to "SBF"
-
Click the OK button.
-
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.
25.3.3 Run the Security Audit Report by User Version (R009502, XJDE0001)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
-
In the Batch Application field, enter R009502 and click the Find button.
-
Select the Security Audit Report by User version.
-
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
-
Role (optional)
To refine the report to generate only records based on a particular role of the user, enter a role.
-
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
-
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
-
Report on Column Security
Leave blank if you want the report to list column security records. Enter 1 to exclude column security records.
-
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
-
-
On the Work With Batch Versions - Available Versions form, click Select.
-
On the Versions Detail form, select the Data Selection check box and click the Submit button.
-
On the Data Selection form, use the User ID left operand to define the user ID that you want the report to list security records for.
-
Click OK.
-
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.
25.3.4 Run the Security Audit Report by Role Version (R009502, XJDE0002)
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
-
In the Batch Application field, enter R009502 and click the Find button.
-
Select the Security Audit Report by Role version.
-
To define processing options for the report, select Processing Options from the Row menu, and then complete the processing options as appropriate:
-
Role (optional)
Do not use this option for this report. Instead, enter the role in the Data Selection form.
-
Report on Application Security
Leave blank if you want the report to include application security records. Enter 1 to exclude application security records.
-
Report on Row Security
Leave blank if you want the report to include row security records. Enter 1 to exclude row security records.
-
Report on Column Security
Leave blank if you want the report to list application security records. Enter 1 to exclude application security records.
-
Report on Published BSSV Security
Leave blank if you want the report to list published business service security records. Enter 1 to exclude published business service security records.
-
-
On the Work With Batch Versions - Available Versions form, click Select.
-
On the Versions Detail form, select the Data Selection check box and click the Submit button.
-
On the Data Selection form, use the User ID left operand to define the role that you want the report to list security records for.
-
Click OK on the Data Selection form.
-
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.
25.3.5 Running a Report that Lists Published Business Service Security Records
You can use the Security Workbench Records reports to generate a list of published business service security records by object, user, or role. However, before you run the report, you must use the Data Selection form to specify the published business service object type.
Access the Work With Batch Versions - Available Versions form. To do so, enter P98305W in the Fast Path.
-
In the Batch Application field, enter either R009501or R009502 and click the Find button.
-
Select the version of the report that you want to run.
-
On the Work With Batch Versions - Available Versions form, click Select.
-
On the Versions Detail form, select the Data Selection check box and click the Submit button.
-
On the Data Selection form, enter these conditions and then click OK:
Where BC Object Type (F9860) (FUNO) is equal to "BSFN" And BC Source Language (F9860) (SRCLNG) [BC] is equal to "SBF"
-
On the Printer Selection form, define the location for the output of the report and then click OK to submit it.