| Oracle® Audit Vault Administrator's Guide Release 10.2.3.2 Part Number E14459-11 |
|
|
PDF · Mobi · ePub |
| Oracle® Audit Vault Administrator's Guide Release 10.2.3.2 Part Number E14459-11 |
|
|
PDF · Mobi · ePub |
You must perform the following general tasks to add source databases to Oracle Audit Vault and then deploy collectors:
For Linux and UNIX platforms, check and set environment variables in the shells in which you will be interacting with the Audit Vault Server and the Audit Vault Collection Agent.
See Section 2.2.
Add an Oracle source database and collectors using the AVORCLDB command-line utility.
See Section 2.3.
To add a Microsoft SQL Server source database and collector, use the AVMSSQLDB command-line utility
See Section 2.4.
To add a Sybase ASE source database and collector, use the AVSYBDB command-line utility
See Section 2.5.
To add an IBM DB2 source database and collector, use the AVDB2DB command-line utility.
See Section 2.6.
Start the collection agents and collectors using the AVCTL command-line utility.
See Section 2.7 and Section 2.8.
Periodically ensure that the collectors are running and collecting audit data.
See Section 2.9 and Section 2.10.
This section contains:
About Checking and Setting Linux and UNIX Environment Variables
Setting the Audit Vault Server Linux and UNIX Environment Variables
Setting the Collection Agent Linux and UNIX Environment Variables
Setting the Oracle Source Database Linux and UNIX Environment Variables
For Linux and UNIX platforms, you must set environment variables before you begin the procedures in this chapter. You set these variables in the three shells that you will use to perform the configuration. Keep these shells open throughout the configuration process. You will need to access them periodically as you complete the configuration steps. If you close and then reopen a shell, then you must reset its environment variables.
Throughout this manual, when you are instructed to open a shell for the Audit Vault Server or the collection agent, remember to set the appropriate environment variables.
You use the Audit Vault Server shell to interact with the Audit Vault Server. To set the environment variables for the Audit Vault Server, you can run either of two scripts, coraenv (for the C shell) or oraenv (for the Bourne, Bash, or Korn shell).
Table 2-1 describes how the coraenv and oraenv scripts set the environment variables.
Table 2-1 Audit Vault Server Environment Variable Settings
To set environment variables for the Audit Vault Server shell:
In the server where you installed the Oracle Audit Vault Server, open a shell.
Run one of the following scripts, which are located in the /usr/local/bin directory:
C shell: coraenv
Bourne, Bash, or Korn shell: oraenv
To test that the script was successful, try invoking the following command:
$ avctl -help
It should return help information for the AVCTL utility, and the only way it can do that is if the ORACLE_HOME and PATH environment variables are correctly set. If the scripts fail, then manually set the environment variables listed in Table 2-1.
If you plan to add Microsoft SQL Server, Sybase ASE, or IBM DB2 source databases to Oracle Audit Vault, then set the LANG and NLS_LANG environment variables.
For example:
C shell:
setenv LANG de_DE.UTF-8 setenv NLS_LANG GERMAN_GERMANY.AL32UTF8
Bourne, Bash, or Korn shell:
LANG=de_DE.UTF-8 NLS_LANG=GERMAN_GERMANY.AL32UTF8 export LANG NLS_LANG
See Oracle Database Globalization Support Guide for more information about the NLS_LANG environment variable, including supported character sets and languages.
Oracle Audit Vault supports the following languages for the LANG environment variable:
en: English |
ja: Japanese |
|
de: German |
ko: Korean |
|
es: Spanish |
pt_BR: Brazilian Portuguese |
|
fr: French |
zh_CN: Simplified Chinese |
|
it: Italian |
zh_TW: Traditional Chinese |
Optionally, you can set the LANG environment variable in the .profile or .cshrc file.
You do not need to set this variable for the Oracle Database AVORCLDB utility. This utility automatically uses the NLS_LANG environment variable setting, which is set during installation. See Oracle Database Globalization Support Guide for more information about language support for Oracle Database.
Leave the Audit Vault Server shell open for the remaining procedures in this chapter.
To set environment variables for the Audit Vault collection agent shell:
In the server where you installed the Audit Vault collection agent, open a shell.
Check and manually set the ORACLE_HOME environment variable to the Audit Vault collection agent home directory.
For example:
$ echo $ORACLE_HOME /opt/oracle/av $ setenv /opt/oracle/av_agent
Check and set the LD_LIBRARY_PATH environment variable to include $ORACLE_HOME/lib.
For example:
$ setenv LD_LIBRARY_PATH ${LD_LIBRARY_PATH}:$ORACLE_HOME/lib
Check and set the PATH environment variable to include $ORACLE_HOME/bin. Be sure that you append this information to the existing PATH information.
For example:
$ setenv PATH ${PATH}:$ORACLE_HOME/bin
Ensure that the following environment variables are not set: ORACLE_SID, TNS_ADMIN, and TWO_TASK.
For C shell:
$ unsetenv ORACLE_SID $ unsetenv TNS_ADMIN $ unsetenv TWO_TASK
For Bourne, Bash, or Korn:
$ unset ORACLE_SID $ unset TNS_ADMIN $ unset TWO_TASK
To test that you correctly set these environment variables, try invoking the following command:
$ avctl -help
It should return help information for the AVCTL utility, and the only way it can do that is if the ORACLE_HOME and PATH environment variables are correctly set.
If you plan to add Microsoft SQL Server, Sybase ASE, or IBM DB2 databases to Oracle Audit Vault, then set the LANG and NLS_LANG environment variables.
See Step 4 under Section 2.2.2 for instructions.
Leave the Audit Vault collection agent shell open for the remaining procedures in this chapter.
If you installed the Audit Vault Server or the collection agent on Microsoft Windows, then you do not need to set any environment variables. Instead, run the Oracle Audit Vault command-line utilities from the Audit Vault home directory, which is ORACLE_HOME\bin.
To set the environment variables for the source database, you can run the same scripts, corenv or oraenv, that you used to set the Audit Vault Server environment variables. Table 2-1 describes how these scripts set the environment variables, except that for the source database, they set the ORACLE_SID variable to orcl, unless you have given it a different name during installation.
To set environment variables for the source database:
In the server where you installed the Oracle source database, open a shell.
From the /usr/local/bin directory, run one of the following scripts:
C shell: coraenv script
Bourne, Bash, or Korn shell: oraenv script
Leave the Oracle source database shell open for the remaining procedures in this chapter.
Step 2: Verify That the Source Database Is Compatible with the Collectors
Step 3: Register the Oracle Source Database with Oracle Audit Vault
Step 5: Enable the Audit Vault Agent to Run the Oracle Database Collectors
The collectors that you will configure later must use this user account to access audit data from the Oracle source database, such as audit trail settings. For an Oracle Real Application Clusters environment, create one user, for the Oracle RAC database.
To create the user account:
Open a shell for the Oracle source database.
Log in to SQL*Plus as a user who has been granted the CREATE USER privilege.
If the source database is protected by Oracle Database Vault, log in as a user who has been granted the DV_ACCTMGR (Database Vault Account Manager) role.
For example:
sqlplus trbokuksa
Enter password: password
Connected.
Create the Oracle source database user account.
For example:
SQL> CREATE USER srcuser_ora IDENTIFIED BY password;
Connect as user SYS with the SYSDBA privilege.
SQL> CONNECT SYS/AS SYSDBA
Enter password: password
Run the zarsspriv.sql script from either the Audit Vault Server or Audit Vault collection agent on Oracle source database.
This script grants the Oracle source database user account the privileges needed to enable the collectors to access audit data. By default, this script is located in the $ORACLE_HOME/av/scripts/streams/source directory in both the Audit Vault Server and the Audit Vault collection agent Oracle home directories.
Use the following syntax:
zarsspriv.sql srcusr mode
In this specification:
srcusr: Enter the name of the source database user account that you created in Step 3.
mode: Specify one of the following modes. Enter the modes in uppercase letters.
For example, to specify the SETUP mode for user srcuser_ora:
SQL> @/oracle/product/10.2.3/av_server/av/scripts/streams/source/zarsspriv.sql Enter value for 1: srcuser_ora Enter value for 2: SETUP Granting privileges to SRCUSER_ORA ... Done.
If the source database has Oracle Database Vault installed, then log in as a user who has been granted the DV_OWNER (Database Vault Owner) role and add the source database user to the Oracle Data Dictionary realm.
For example:
SQL> CONNECT preston
Enter password: password
Connected.
SQL> EXEC DBMS_MACADM.ADD_AUTH_TO_REALM('Oracle Data Dictionary', 'SRCUSER_ORA', null, dbms_macutl.g_realm_auth_participant);
SQL> COMMIT;
If the source database has Oracle Database Vault installed, then grant the Oracle source database user account the DV_SECANALYST role.
The DV_SECANALYST role enables the user to run Oracle Database Vault reports and monitor Oracle Database Vault. This role also enables the Oracle source database user to collect Database Vault audit trail data from the source database.
For example:
SQL> GRANT DV_SECANALYST TO srcuser_ora;
Exit SQL*Plus.
Do not close this shell.
Now you are ready to verify that the Oracle source database is compatible with the collector type in the Audit Vault collection agent home.
To verify the Oracle source database compatibility:
For the source database, run the following command and note the host, port, and service settings:
lsnrctl status
Alternatively, you can check the tnsnames.ora file.
cat $ORACLE_HOME/network/admin/tnsnames.ora
Log in to the source database and verify the type of auditing that has been configured.
For example, the following command confirms that you would need the DBAUD collector for this database:
sqlplus sys/as sysdba
Enter password: password
Connected.
SQL> SHOW PARAMETER AUDIT_TRAIL
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
audit_trail string DB
If you are unsure of which collector you should select, then see Section 1.6.2.
Open a shell or command prompt for the Audit Vault Server or collection agent.
UNIX: Set the environment variables, as described in Section 2.2.2 for the Audit Vault Server, or Section 2.2.3 for the collection agent.
Microsoft Windows: Go to the Audit Vault Server or collection agent ORACLE_HOME\bin directory.
Run the avorcldb verify command, using the values that the LSNRCTL utility returned.
You must specify the host name, port number, and service name. Typically, for Oracle Database, the host is the fully qualified domain name or the IP address of the server on which the Oracle source database is running, and the port number is 1521.
For example, assuming that the host is hrdb.example.com, the port number is 1521, the service name is orcl, and the user account is srcuser_ora:
avorcldb verify -src hrdb.example.com:1521:orcl -colltype ALL
Enter Source user name: srcuser_ora
Enter Source password: password
Output similar to the following should appear:
source ORCL verified for Aud$/FGA_LOG$ Audit Collector collector
If instead errors are displayed, see the examples that follow this procedure.
See Section 8.10 for detailed information about the avorcldb verify command.
Do not close this shell or command prompt.
The AVORCLDB utility checks if an Audit Vault collector can be run against the source database configuration.
Example 2-1 shows what happens if the Oracle source database is not properly configured. In this case, you must set the initialization parameters listed in the output before you can use the REDO log collector.
Example 2-1 Partially Successful Verify Operation of Source Compatibility with the Collectors
avorcldb verify -src hrdb.example.com:1521:orcl -colltype ALL
Enter Source user name: srcuser_ora
Enter Source password: password
source ORCL verified for OS File Audit Collector
source ORCL verified for Aud$/FGA_LOG$ Audit Collector
Source database must be in ARCHIVELOG mode to use REDO Log collector
Incorrect database compatibility 9.2.0; recommended value is 10.2.0.0.0
Parameter _JOB_QUEUE_INTERVAL not set; recommended value range [1 - ANY_VALUE]
Parameter JOB_QUEUE_PROCESSES = 0 not in recommended value range [4 - ANY_VALUE]
Parameter AQ_TM_PROCESSES = 0 is not in required value range [4 - ANY_VALUE]
Parameter UNDO_RETENTION = 900 not in recommended value range [3600 - ANY_VALUE]
Parameter GLOBAL_NAMES = false not set to recommended value true
Please set the above init.ora parameters to recommended values
By default, the init.ora file resides in the $ORACLE_HOME/dbs directory.
After you correct the problems (in this case, setting all those missing or incorrect initialization parameters), rerun the avorcldb verify command to ensure that the result is as you want it. Example 2-2 shows what happens after this source database has been properly configured. See also Chapter 12, "REDO Collector Database Reference."
To register the Oracle source database with Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avorcldb add_source command.
For example:
avorcldb add_source -src hrdb.example.com:1521:orcl
-srcname hr_db
-desc 'HR Database'
Enter Source user name: srcuser_ora
Enter Source password: password
Adding source...
Source added successfully.
source successfully added to Audit Vault
remember the following information for use in avctl
Source name (srcname): hr_db
Credential stored successfully.
Mapping Source to Agent...
In this example:
-src: Enter the source database connection information: host name, port number, and service name, separated by a colon. If you are unsure of this information, run the lsnrctl status command on the computer where you installed the source database, or check the tnsnames.ora file.
-srcname: Enter a name for the source database. If you omit this option, then Oracle Audit Vault names the source database after the global database name, which in this example is ORCL. Remember that the source database name is case sensitive.
-desc: Optionally, enter a brief description for the source database.
Source user name and password: Enter the user account information that you created in Section 2.3.1.
Mapping Source to Agent: This message in the output refers to the agent that you created just before you installed the Oracle Audit Vault agent.
See Section 8.3 for detailed information about the avorcldb add_source command.
Note the source name return value from the output.
You will need this value, which represents the global database name, for subsequent steps in this section. In this example, the return value is hr_db.
Do not close this shell or command prompt.
You can add one or more collectors to Oracle Audit Vault, depending on your needs. The available collector types are listed in Table 1-5. For an Oracle Real Application Clusters environment, you can create collectors for each Oracle RAC node. If you plan to write the .aud or .xml audit file to a shared file system, then you only need one OSAUD collector for the Oracle RAC database.
To add a collector to Oracle Audit Vault:
If you plan to use the OSAUD collector, access the shell used for the Oracle source database.
If you plan to use either of the other collector types (DBAUD and REDO), then go to Step 4 of this procedure.
Log in to SQL*Plus as SYS with the SYSDBA privilege.
sqlplus sys as sysdba
Enter password: password
Set the maximum operating system file size to a setting equal to or less than 204800.
If the operating system file grows larger than 2 GB, then the OSAUD collector ignores all audit records created past this size. Use the following SQL statement to set the maximum size to 102400 KB, which translates as 2 GB.
BEGIN DBMS_AUDIT_MGMT.SET_AUDIT_TRAIL_PROPERTY( AUDIT_TRAIL_TYPE => DBMS_AUDIT_MGMT.AUDIT_TRAIL_OS, AUDIT_TRAIL_PROPERTY => DBMS_AUDIT_MGMT.OS_FILE_MAX_SIZE, AUDIT_TRAIL_PROPERTY_VALUE => 204800); END; /
Afterwards, if the operating system exceeds 2 GB, then Oracle Database stops appending audit records to the current file, and creates a new file to resume the audit data collection.
For reference information about the DBMS_AUDIT_MGMT PL/SQL package, see Oracle Database PL/SQL Packages and Types Reference.
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avorcldb add_collector command to add the collectors you want.
For example:
avorcldb add_collector -srcname hr_db
-agentname agent1
-colltype OSAUD
-orclhome /u01/app/oracle/product/10.2.0/db_1
In this example:
-srcname: Enter the source name for this source database, which Oracle Audit Vault will refer to when collecting audit data. Remember that the source name is case-sensitive. This name was displayed when you ran the avorcldb add_source command in Section 2.3.3.
-agentname: Enter the name for the agent that you created using the avca add_agent command before you installed the Audit Vault collection agent, as described in Oracle Audit Vault Collection Agent Installation Guide. If you are not sure of the agent name, then you can find it as follows: Log in to the Audit Vault Console, click the Configuration tab, and then click the Agent tab to display the Agents page. The name of the agent is displayed in the Agent column.
-colltype: Enter OSAUD, DBAUD, or REDO. If you plan to specify REDO, you must include the -av argument, which specifies the connection information for the database link from the source database to Oracle Audit Vault. See Section 8.2 more information about the -av argument.
-orclhome: Enter the Oracle source database home directory. For Microsoft Windows installations of Oracle Database, enter the path using forward slashes, or if you want to use back slashes, enclose the path in double quotation marks. For the DBAUD and REDO collectors, this parameter is optional.
See Section 8.2 for detailed information about the avorcldb add_collector command. Examples of running the avorcldb add_collector command follow this procedure.
Note the collector name return from the output.
You will need this value whenever you configure settings for the collector. In this example, the return value in this example is OSAUD_Collector.
Optionally, modify the attributes associated with the collector.
The collector has a set of default attributes. You can modify these by using the avorcldb alter_collector command. See Section 8.4.
Do not close this shell or command prompt.
Example 2-3 shows how to add the OSAUD collector to Oracle Audit Vault for UNIX platforms. You must include the -orclhome orclhome parameter to specify the location of the source database as an absolute path, if u01/app is the Oracle base directory.
Example 2-3 Adding the OSAUD Collector to Oracle Audit Vault for UNIX Platforms
avorcldb add_collector -srcname hr_db
-agentname agent1
-colltype OSAUD
-orclhome /u01/app/oracle/product/10.2.0/db_1
source hr_db verified for OS File Audit Collector collector
Adding collector...
Collector added successfully.
collector successfully added to Audit Vault
remember the following information for use in avctl
Collector name (collname): OSAUD_Collector
Example 2-4 shows how to add the OSAUD collector to Oracle Audit Vault on Microsoft Windows for the event log and XML audit trail. You must include the -orclhome orclhome parameter to specify the location of the source database. Use slashes (/) instead of backslashes (\) for the Microsoft Windows path. If you want to use backslashes, enclose the path in double quotation marks. For example:
-orclhome "c:\oracle\product\10.2.0\db_1"
Example 2-4 Adding the OSAUD Collector to Oracle Audit Vault on Microsoft Windows
avorcldb add_collector -srcname hr_db
-agentname agent1
-colltype OSAUD
-orclhome c:/oracle/product/10.2.0/db_1
source hr_db verified for Windows Event Log Audit Collector collector
Adding collector...
Collector added sucessfully.
collector successfully added to Audit Vault
remember the following information for use in avctl
Collector name (collname): OSAUD_Collector
Example 2-5 shows how to add the DBAUD collector to Oracle Audit Vault.
Example 2-5 Adding the DBAUD Collector to Oracle Audit Vault
avorcldb add_collector -srcname hr_db
-agentname agent1 -colltype DBAUD
source hr_db verified for Aud$/FGA_LOG$ Audit Collector collector
Adding collector...
Collector added successfully.
collector successfully added to Audit Vault
remember the following information for use in avctl
Collector name (collname): DBAUD_Collector
Example 2-6 shows how to add the REDO collector to Oracle Audit Vault. Note that you must supply the -av argument for this collector type.
Example 2-6 Adding the REDO Collector to Oracle Audit Vault
avorcldb add_collector -srcname hr_db
-agentname agent1
-colltype REDO
-orclhome hrdb.example.com:1521:orcl
source hr_db verified for REDO Log Audit Collector collector
Adding collector...
Collector added successfully.
collector successfully added to Audit Vault
remember the following information for use in avctl
Collector name (collname): REDO_Collector
initializing REDO Collector
setting up APPLY process on Audit Vault server
setting up CAPTURE process on source database
Note:
If the REDO collector does not initialize, theAPPLY process on the Audit Vault Server and CAPTURE process on the source database cannot start. This problem happens if the source user account does not have the correct privileges. Ensure that you ran the zarsspriv.sql script, described in Section 2.3.1.You are now ready to add the collection agent credentials to the Oracle source database. This process adds the source user credentials to the wallet, creates a database alias in the wallet for the source user, and verifies the connection to the source using the wallet. This way, the Audit Vault collection agent can run the Oracle Database collectors. You must complete this step so that the collectors can start properly.
To enable to Audit Vault agent to run the Oracle Database collectors:
Access the shell or command prompt for the Audit Vault collection agent.
UNIX: If necessary, set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Use the avorcldb setup command to add the collection agent credentials.
For example:
avorcldb setup -srcname hr_db
Enter Source user name: srcuser_ora
Enter Source password: password
adding credentials for user srcuser_ora for connection [SRCDB1]
Credential stored successfully.
updated tnsnames.ora with alias [SRCDB1] to source database
verifying SRCDB1 connection using wallet
In this example:
-srcname: Enter the name of the source database that you plan to use.
Source user name and Source password prompts: Enter the source database user name and password that you created in Section 2.3.1.
See Section 8.9 for detailed information about the avorcldb setup command.
This step completes the registration for the Oracle source database and its collectors. Next, you must start the collection agents and collectors. See Section 2.7 and Section 2.8 for more information.
Step 2: Create a User Account on the Microsoft SQL Server Database Instance
Step 3: Verify That the Database Instance Is Compatible with the Collector
Step 4: Register the SQL Server Source Database Instance with Audit Vault
Step 6: Enable the Audit Vault Agent to Run the MSSQLDB Collector
Step 7: Optionally, Schedule an Audit Trail Cleanup for SQL Server Audit Files
Oracle Audit Vault requires a JDBC connection to the SQL Server database. Audit Vault supports Microsoft SQL Server JDBC Driver version 1.2. Ensure that you have downloaded the JDBC driver (sqljdbc.jar) to the $ORACLE_HOME/jlib directories in both the Audit Vault Server and Audit Vault collection agent homes. This driver provides high performance native access to Microsoft SQL Server 2000, 2005, 2008 database data sources. Verify that the .jar file is present in the Oracle Audit Vault collection agent before you start the collection agent.See the following Web sites for more information about the Microsoft SQL Server JDBC drivers and download.
See Also:
Oracle Audit Vault Server Installation Guide for Linux x86 for information about downloading and copying JDBC driver files for Microsoft SQL Server
Oracle Audit Vault Collection Agent Installation Guide for information about downloading and copying JDBC driver files for Microsoft SQL Server
Oracle Audit Vault Collection Agent Installation Guide to ensure that the sqljdbc.jar file is present in the Oracle Audit Vault OC4J before starting the agent OC4J
The collector that you will configure later must use this user account to access audit data from the Microsoft SQL Server source database instance. After you create the user account, the privileges that you assign to this user depend on whether the source database instance is Microsoft SQL Server 2000, 2005, or 2008.
To create the user account:
Log in to the Microsoft SQL Server source database instance.
Create a user account.
For example, to create a user account named srcuser_mss:
EXEC sp_addlogin srcuser_mss, password
For a Microsoft SQL Server 2005 or 2008 database, grant this user the alter_trace privilege.
Log in as the SYSADMIN user.
Run the following command to grant the alter trace privilege to the user.
For example:
GRANT ALTER TRACE TO srcuser_mss
For a Microsoft SQL Server 2000 database instance, grant the user the SYSADMIN fixed server role.
Click Security.
Click Logins.
Right-click the login you created (for example, srcuser_mss).
Click Properties.
On the left pane, click Server Roles.
Select the sysadmin option setting, and then click OK.
You can verify that the Microsoft SQL Server source database instance is compatible with the collector type in the Audit Vault collection agent home.
To verify the source database instance compatibility:
Access the shell or command prompt for the Audit Vault Server or collection agent.
UNIX: Set the environment variables, as described in Section 2.2.2 for the Audit Vault Server, or Section 2.2.3 for the collection.
Microsoft Windows: Go to the Audit Vault Server or collection agent ORACLE_HOME\bin directory.
Run the avmssqldb verify command.
You must specify the host name and database instance, or the host name and port number. Typically, for Microsoft SQL Server, the host is the fully qualified domain name or the IP address of the server on which the SQL Server source database instance is running, and the port number is 1433.
For example, assume that the host is hrdb.example.com, the database instance is hr_db, and the user account is srcuser_mss:
avmssqldb verify -src 'hrdb.example.com\hr_db'
Enter a username : srcuser_mss
Enter a password: password
***** Source Verified *****
Enclose the -src value in single quotation marks, as shown in this example. If you specify the host name and port number, use the following convention, which omits the quotation marks and separates the host and port with a colon:
avmssqldb verify -src host:port
See Section 9.10 for detailed information about the avmssqldb verify -src command.
Do not close this shell or command prompt.
To register the SQL Server source database instance with Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avmssqldb add_source command.
For example:
avmssqldb add_source -src 'hrdb.example.com\hr_db' -srcname mssqldb4 -desc 'HR Database'
Enter a username: srcuser_mss
Enter a password : password
***** Source Verified *****
***** Source Added Successfully *****
In this example:
-src: Enter the fully qualified domain name (or IP address) and database instance name, or the domain name and port number for the source database instance that you specified in Section 2.4.3.
-srcname: Create a name for the source database instance, which. Oracle Audit Vault will refer to when it collects audit data.
-desc: Optionally, enter a brief description for the source database instance.
username and password: Enter the user name and password that you created in Section 2.4.2.
See Section 9.3 for detailed information about the avmssqldb add_source command.
Do not close this shell or command prompt.
Now you are ready to add the MSSQLDB collector to Oracle Audit Vault. By default, the MSSQLDB collector collects audit records from all audit trails that have been enabled in the source database: C2 audit logs, server-side trace logs, and the Windows Event log.
To add the MSSQLDB collector to Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avmssqldb add_collector command.
For example:
avmssqldb add_collector -srcname mssqldb4 -agentname agent1
Enter a username: srcuser_mss
Enter a password: password
***** Collector Added Successfully*****
In this example:
-srcname: Enter the name of the SQL Server source database instance that you verified in Section 2.4.3.
-agentname: Enter the name for the agent that you created using the avca add_agent command before you installed the Audit Vault collection agent, as described in Oracle Audit Vault Collection Agent Installation Guide. If you are not sure of the agent name, then you can find it as follows: Log in to the Audit Vault Console, click the Configuration tab, and then click the Agent tab to display the Agents page. The name of the agent is displayed in the Agent column.
See Section 9.2 for detailed information about the avmssqldb add_collector command.
Run the avmssqldb alter_collector command to alter the collector to specify the name of the file from which to collect the audit records.
For example:
avmssqldb alter_collector -srcname mssqldb4 -collname MSSQLCollector SERVERSIDE_TRACE_FILEPATH="c:\SQLAuditFile*.trc"
See Section 9.4 for more information about the avmssqldb alter_collector command.
Optionally, modify the attributes associated with the MSSQLDB collector.
The MSSQLDB collector has a set of default attributes. You can modify these by using the avssqldb alter_collector command. See Section 9.4.
Do not close this shell or command prompt.
Next, you must add the collection agent credentials to the Microsoft SQL Server source database instance. This process adds the source user credentials to the wallet, creates a database alias in the wallet for the source database instance user, and verifies the connection to the source database instance using the wallet. This way, the Oracle Audit Vault collection agent can run the MSSQLDB collector. You must complete this step so that the collectors can start properly.
To enable the Oracle Audit Vault agent to run the MSSQLDB collector:
On Windows, open a command prompt for the Audit Vault collection agent and then go to the ORACLE_HOME\bin directory.
(You cannot perform this procedure in a UNIX environment.)
Run the avmssqldb setup command.
For example:
avmssqldb setup -srcname mssqldb4
Enter a username : srcuser_mss
Enter a password : password
***** Credentials Successfully added *****
In this example:
-srcname: Enter the source database instance name that you specified in Section 2.4.3.
username and password prompts: Enter the user name and password that you created in Section 2.4.2.
See Section 8.9 for detailed information about the avmssqldb setup command.
This step completes the registration for the Microsoft SQL Server source database and its collector. Next, you must start the collection agent and collector. See Section 2.7 and Section 2.8 for more information.
If the MSSQLDB collector has collected data from a trace file and the trace file is inactive, then you can clean up this file. The MSSQLDB collector writes the names of the SQL Server audit text files to a plain text file with the .atc extension. The .atc file resides in the ORACLE_HOME/av/log directory on the computer on which the agent is installed.
To manually clean up files that Oracle Audit Vault has completed extracting audit records from:
Go to the ORACLE_HOME/bin directory of the computer where the collection agent is installed.
Ensure that the ORACLE_HOME environment variable is correctly set.
Run the following utility:
c:\ORACLE_HOME\bin> SQLServerCleanupUtil -srcname source_name -collname collector_name
For example:
c:\ORACLE_HOME\bin> SQLServerCleanupUtil -srcname mssqldb4 -collname MSSQLCollector
To automate the cleanup of SQL Server trace files, you can use the Windows Scheduler.
Note:
If the SQL Server trace definition is redefined or reinitialized, then you must ensure that the file names of the trace files do not overlap with trace files that were created earlier.For example, suppose you start SQL Server with a trace definition in which the trace files names use the following format:
c:\serversidetraces.trc c:\serversidetraces_1.trc c:\serversidetraces_2.trc ... c:\serversidetraces_259.trc
Then you restart the SQL Server with a new trace definition. This new trace definition must use a different file name from the current trace files (for example, the current one named c:\serversidetraces.trc). If you do not, then when you purge the audit trail (as described in Section 4.10), the new trace files that have same names as the old ones will be deleted.
Step 2: Create a User Account on the Sybase ASE Source Database
Step 3: Verify That the Source Database Is Compatible with the Collector
Step 4: Register the Sybase ASE Source Database with Oracle Audit Vault
Step 6: Enable the Audit Vault Agent to Run the SYBDB Collector
Ensure that you have downloaded the jConnect 6 JDBC driver (jconn3.jar) to the $ORACLE_HOME/jlib directories in both the Audit Vault Server and Audit Vault Agent homes. This driver provides high performance native access to Sybase ASE database data sources. Ensure that this jar file is present in the Oracle Audit Vault OC4J before starting the collection agent. The SYBDB collector uses this driver to collect audit data from Sybase ASE databases.
See Also:
Oracle Audit Vault Server Installation Guide for Linux x86 for information about downloading and copying JDBC driver files for Sybase ASE
Oracle Audit Vault Collection Agent Installation Guide for information about downloading and copying JDBC driver files for Sybase ASE
Oracle Audit Vault Collection Agent Installation Guide to ensure that the sqljdbc.jar file is present in the Oracle Audit Vault OC4J before starting the agent OC4J
The collector that you will configure later must use this user account to access audit data from the Sybase ASE source database.
To create the user account:
Log in to the Sybase ASE source database.
Create a user account.
For example:
sp_addlogin srcuser_syb, password
Add this user to the Sybase ASE source database.
sp_adduser srcuser_syb
Grant the SSO_role privilege to the source user.
grant role sso_role to srcusr_syb
Now you are ready to verify that the Sybase ASE source database is compatible with the collector type in the Audit Vault collection agent home:
To verify the Sybase ASE source database compatibility:
Open a shell or command prompt for the Audit Vault Server or collection agent.
UNIX: Set the environment variables, as described in Section 2.2.2 for the Audit Vault Server, or Section 2.2.3 for the collection agent.
Microsoft Windows: Go to the Audit Vault Server or collection agent ORACLE_HOME\bin directory.
Run the avsybdb verify command.
You must specify the host name and port number. Typically, for Sybase ASE, the host is the fully qualified domain name or IP address of the server on which the Sybase ASE source database is running, and the port number is 5000.
For example, assume that the host is hrdb.example.com and the port number is 5000, and the user account is srcuser_syb:
avsybdb verify -src hrdb.example.com:5000
Enter a username: srcuser_syb
Enter a password: password
***** Source Verified *****
See Section 10.10 for detailed information about the avsybdb verify command.
Do not close this shell or command prompt.
To register the Sybase ASE source database with Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avsybdb add_source command.
For example:
avsybdb add_source -src hrdb.example.com:5000 -srcname sybdb4
Enter a username: srcuser_syb
Enter a password: password
***** Source Verified *****
***** Source Added Successfully *****
In this example:
-src: Enter the fully qualified domain name (or IP address) and port number for the source database that you verified in Section 2.6.3.
-srcname: Create a name for this source database. Oracle Audit Vault refers to this name when it collects audit data.
username and password prompts: Enter the user name and password that you created in Section 2.5.2.
See Section 10.3 for detailed information about the avsybdb add_source command.
Do not close this shell or command prompt.
To add the SYBDB collector to Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avsybdb add_collector command.
For example:
avsybdb add_collector -srcname sybdb4 -agentname agent1
Enter a username: srcuser_syb
Enter a password: password
***** Collector Added Successfully*****
In this example:
-srcname: Create a name for the source database. Oracle Audit Vault refers to this name when collecting audit data.
-agentname: Enter the name for the agent that you created using the avca add_agent command before you installed the Audit Vault collection agent, as described in Oracle Audit Vault Collection Agent Installation Guide. If you are not sure of the agent name, then you can find it as follows: Log in to the Audit Vault Console, click the Configuration tab, and then click the Agent tab to display the Agents page. The name of the agent is displayed in the Agent column.
username and password: Enter the user name and password that you created in Section 2.5.2.
See Section 10.2 for detailed information about the avsybdb add_collector command.
Optionally, modify the attributes associated with the collector.
The collector has a set of default attributes. You can modify these by using the avsybdb alter_collector command. See Section 10.4.
Do not close this shell or command prompt.
You now are ready to configure the collection agent credentials to the Sybase ASE source database. This process adds the source user credentials to the wallet, creates a database alias in the wallet for the source user, and verifies the connection to the source using the wallet. This way, the Oracle Audit Vault collection agent can run the SYBDB collector. You must complete this step so that the collectors can start properly.
To enable the Oracle Audit Vault collection agent to run the SYBDB collector:
Access the shell or command prompt for the Audit Vault collection agent.
UNIX: If necessary, set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Run the avsybdb setup command.
For example:
avsybdb setup -srcname sybdb4
Enter a username: srcuser_syb
Enter a password: password
***** Credentials Successfully added *****
In this example:
-srcname: Enter the source database name that you created in Section 2.5.5.
username and password: Enter the user name and password that you created in Section 2.5.2.
See Section 10.9 for detailed information about the avsybdb setup command.
This step completes the registration for the Sybase ASE source database and its collector. Next, you must start the collection agent and collector. See Section 2.7 and Section 2.8 for more information.
Step 1: Copy the DB2 JDBC and SQLJ Driver to the Audit Vault Homes
Step 2: Designate a User Account on the IBM DB2 Source Database
Step 3: Verify That the Source Database Is Compatible with the Collector
Step 4: Register the IBM DB2 Source Database with Oracle Audit Vault
Step 6: Convert the Binary DB2 Audit File to an ASCII Text File
Copy the IBM Data Server Driver for JDBC and SQLJ (db2jcc.jar) to the $ORACLE_HOME/jlib directories in both the Audit Vault Server and Audit Vault Agent homes. Oracle Audit Vault requires driver version 3.50 or later. This version of the db2jcc.jar file is available in either IBM DB2 UDB version 9.5 or IBM DB2 Connect version 9.5 or later.
This driver provides high performance native access to IBM DB2 database data sources. The DB2 collector uses this driver to collect audit data from IBM DB2 databases, so the driver must be present in Oracle Audit Vault OCFJ before you can start the collection agent.
You can verify the version of this .jar file that is currently installed as follows:
Ensure that the directory path to the db2jcc.jar file is included in the CLASSPATH environment variable setting.
Run the following command:
java com.ibm.db2.jcc.DB2Jcc -version
Designate an IBM DB2 user account to be used for the AVDB2DB utility, which you will use later to configure collectors for your DB2 database. This user must have privileges to run the IBM DB2 SYSPROC.ENV_GET_PROD_INFO procedure.
Note:
If you are using IBM DB2 Version 8.2, ensure that you have installed FixPak 9. Otherwise, theSYSPROC.ENV_GET_PROD_INFO procedure is not available.Now you are ready to verify that the IBM DB2 source database is compatible with the collector type in the Audit Vault collection agent home.
To verify the IBM DB2 source database compatibility:
Open a shell or command prompt for the Audit Vault Server or collection agent.
UNIX: Set the environment variables, as described in Section 2.2.2 for the Audit Vault Server, or Section 2.2.3 for the collection agent.
Microsoft Windows: Go to the Audit Vault Server or collection agent ORACLE_HOME\bin directory.
Run the avdb2db verify command.
You must specify the host name and port number. Typically, for IBM DB2, the host is the fully qualified domain name or IP address of the server on which the IBM DB2 source database is running, and the port number is 50000.
For example, assume that the host is hrdb.example.com, the port number is 50000, the source database is sales_db, and the user account is srcuser_db2:
avdb2db verify -src hrdb.example.com:50000:sales_db
Enter a username: srcuser_db2
Enter a password: password
***** Source Verified *****
See Section 11.9 for detailed information about the avdb2db verify command.
Do not close this shell or command prompt.
To register the IBM DB2 source database with Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avdb2db add_source command.
For example:
avdb2db add_source -src hrdb.example.com:50000 -srcname db2db4
Enter a username: srcuser_db2
Enter a password: password
***** Source Verified *****
***** Source Added Successfully *****
In this example:
-src: Enter the fully qualified domain name (or IP address), port number, and optionally, the database name, for the source database that you verified in Section 2.6.3.
-srcname: Create a name for this source database. Oracle Audit Vault refers to this name when it collects audit data.
username and password: Enter the user name and password that you designated in Section 2.6.2.
See Section 11.3 for detailed information about the avdb2db add_source command.
Do not close this shell or command prompt.
To add the DB2 collector to Oracle Audit Vault:
Access the shell or command prompt for the Audit Vault Server.
UNIX: If necessary, set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avdb2db add_collector command.
For example:
avdb2db add_collector -srcname db2db4 -agentname agent1
Enter a username: srcuser_db2
Enter a password: password
***** Collector Added Successfully*****
In this example:
-srcname: Create a name for the source database. Oracle Audit Vault refers to this name when collecting audit data.
-agentname: Enter the name for the agent that you created using the avca add_agent command before you installed the Audit Vault collection agent, as described in Oracle Audit Vault Collection Agent Installation Guide. If you are not sure of the agent name, then you can find it as follows: Log in to the Audit Vault Console, click the Configuration tab, and then click the Agent tab to display the Agents page. The name of the agent is displayed in the Agent column.
username and password prompts: Enter the user name and password that you designated in Section 2.6.2.
See Section 11.2 for detailed information about the avdb2db add_collector command.
Modify the SINGLE_FILEPATH attribute of the avdb2db alter_collector command to point to the location of the DB2 audit directory. This is the directory where the DB2 collector will collect audit data. You must specify an absolute path, not a relative path.
For example:
avdb2db alter_collector -srcname db2db4 -collname DB2Collector
SINGLE_FILEPATH=DB2_HOME/sqlib/security/auditdata
***** Collector Altered Successfully *****
See Section 11.4 for more information about the avdb2db alter_collector command.
Do not close this shell or command prompt.
IBM DB2 creates its audit files in a binary file format that is separate from the DB2 database. You must convert the binary file to an ASCII file before each time Oracle Audit Vault collects audit data from a DB2 database. Ideally, schedule the script to run periodically. If the script finds older text files that have already been collected by the DB2 collector, then the script deletes them. It creates a new, timestamped ASCII text file each time you run it. Optionally, you can set the script to purge the output audit files.
Follow these steps:
Identify a user who has privileges to run the db2audit command.
This user will extract the binary files to the text files.
Access the shell or command prompt for the Audit Vault collection agent.
UNIX: If necessary, set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Grant the user you identified in Step 1 execute privileges to run the conversion script from the Oracle Audit Vault directory.
Alternatively, you can copy the appropriate conversion script located in the $ORACLE_HOME/bin directory to a location where this user can run them. These scripts are as follows:
DB2 release 8.2 databases: DB282ExtractionUtil (for Microsoft Windows, this file is called DB282ExtractionUtil.bat.)
DB2 9.5 release databases: DB295ExtractionUtil (for Microsoft Windows, this file is called DB295ExtractionUtil.bat.)
Grant the user you identified in Step 1 read permission for the $ORACLE_HOME/av/log directory and its contents.
This user needs read permission for this directory as part of the process of generating the text files that are extracted by the extraction utility.
Follow these steps:
In the server where you installed the IBM DB2 database, open a shell as the SYSADM DB2 user.
Set the following variables:
ORACLE_HOME
DB2AUDIT_HOME (this directory points to the main directory that contains the db2audit command)
Ensure that the Oracle Audit Vault owner of the agent process has read permissions for the audit text files that will be generated by the extraction utility.
Log in as the DB2 user that you identified in Step 1 in Section 2.6.6.1.
Make a note of the directory that you identified in Step 3 in Section 2.6.5.
You will need to provide this directory path when you run the conversion script.
Run one of the following scripts, depending on the version of DB2 that you have installed:
DB2 release 8.2 databases: Run the script as follows:
DB282ExtractionUtil -extractionpath default_DB2_audit_directory -audittrailcleanup yes_or_no
In this specification:
extractionpath: Enter the full directory path to the location of the DB2 audit directory. Typically, this directory is in the following locations:
UNIX: DB2_HOME/sqlib/security/auditdata
Microsoft Windows: DB2HOME\instance\security\auditdata
Ensure that this path is the same as the path that you specified for the avdb2db alter_collector SINGLE_FILEPATH attribute in Step 3 in Section 2.6.5.
audittrailcleanup: Enter yes or no, to enable or disable the audit trail cleanup. Entering yes deletes the IBM DB2 audit file up to the latest audit record which has been collected by the Oracle Audit Vault DB2 collector. If you omit this value, then the default is no.
This script creates the ASCII text file in the auditdata directory, using the following format, which indicates the time the file was created:
db2audit.instance.log.0.YYYYDDMMHHMMSS.out
DB2 release 9.5 databases: Run the script as follows:
DB295ExtractionUtil -archivepath default_DB2_audit_directory -extractionpath output_directory -audittrailcleanup yes_or_no
In this specification:
archivepath is the same as the directory that is used for DB2 release 8.2.
extractionpath is a directory specified by the avdb2db alter_collector SINGLE_FILEPATH attribute. See Table 11-2 in Section 11.4 for more information. This file is created in using the db2audit.instance.log.0.YYYYDDMMHHMMSS.out format.
audittrailcleanup: Enter yes or no, to enable or disable the audit trail cleanup. Entering yes deletes the archived IBM DB2 audit files that were collected by the Oracle Audit Vault DB2 collector. If you omit this value, then the default is no.
These two directory paths can be the same, or optionally, you can specify different directories for each location.
To schedule the script to run automatically, follow these guidelines:
UNIX: Use the crontab UNIX utility. Provide the same information that you would provide using the parameters described previously when you normally run the script.
Microsoft Windows: Use the Windows Scheduler. Provide the archive directory path (for release 9.5 databases only), extraction path, and source database name in the scheduled task.
This step completes the registration for the IBM DB2 source database and its collector. Next, you must start the collection agent and collector. See Section 2.7 and Section 2.8 for more information.
This section contains:
Starting the Oracle Audit Vault Release 10.2.3.2 Collection Agents
Starting the Oracle Audit Vault Release 10.2.3.1 or Earlier Collection Agents
When you create a new Release 10.2.3.2 collection agent or upgrade an earlier one, by default it will be started. You can check the status of the collection agents by running the avctl show_agent_status command, described in Section 7.4.
If the collection agent has not started, then follow these steps:
Open a shell or command prompt for the Audit Vault collection agent.
UNIX: Set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Run the avctl start_agent command, which starts the collection agent.
For example:
avctl start_agent Starting Agent... Agent started successfully.
See Section 7.9 for more information.
To start the collection agents that were created in Oracle Audit Vault Release 10.2.3.1 or earlier but have not yet been upgraded:
Open a shell or command prompt for the Audit Vault collection agent.
UNIX: Set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Run the avctl start_oc4j command, which starts the collection agent.
avctl start_oc4j Starting OC4J... OC4J started successfully.
See Section 7.15.2 for additional avctl start_oc4j parameters.
This section contains:
To start the collectors from the Audit Vault Console:
Log in to the Audit Vault Console as a user who has been granted the AV_ADMIN role.
See Section 3.2.3 for login instructions.
Click the Management tab, then Collectors to display the Collectors page.
The Collectors page appears with a table containing the following columns.
Collector: Name of the collector
Agent: The name of the collection agent for this collector
Audit Source: The name of the audit data source
Status: The current running status of the collector: a green up arrow indicates that the collector is running, a red down arrow indicates that the collector is not running, an error indicates that the collector is in an error state
Records Per Second: The number of records per second being collected for the current time period
Bytes Per Second: The number of bytes per second in audit records being collected for the current time period
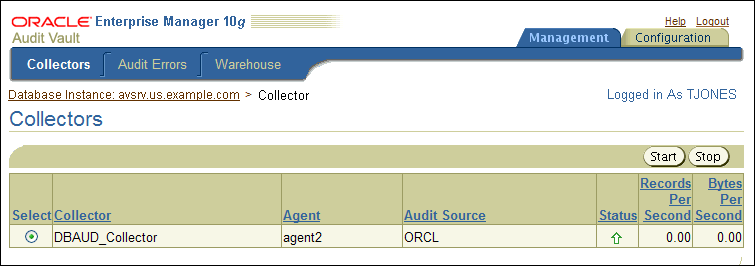
Select the collector that you want to start.
This page also indicates whether the collector is running. A green up arrow indicates the collector is running; a red down arrow indicates it is not running.
Click Start.
In a moment, a message indicating that the collector has started should appear.
To start the collectors from a shell:
Open a shell or command prompt for the Audit Vault Server.
UNIX: Set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avctl start_collector command.
For example:
avctl start_collector -collname DBAUD_Collector -srcname hr_db Starting collector... Collector started successfully.
See Section 7.11 for more information about the avctl start_collector command.
If the startup is successful, then Oracle Audit Vault moves the collector to a RUNNING state.
If the startup fails, then ensure that the collection agent is running:
Open shell or command prompt for the Audit Vault collection agent.
UNIX: Set the environment variables, as described in Section 2.2.3.
Microsoft Windows: Go to the collection agent ORACLE_HOME\bin directory.
Check the status of the collection agent.
For Release 10.2.3.2:
avctl show_agent_status
For Release 10.2.3.1 or earlier collection agents that have not yet been upgraded:
avctl show_oc4j_status
If the collection agent is not running, then enter the following command:
For Release 10.2.3.2:
avctl start_agent Starting Agent... Agent started successfully.
See Section 7.9 for additional parameters avctl start_agent parameters.
For Release 10.2.3.1 or earlier collection agents that have not yet been upgraded:
avctl start_oc4j Starting OC4J... OC4J started successfully.
See Section 7.15.2 for additional parameters avctl start_oc4j parameters.
This section contains:
Log in to the Audit Vault Console as a user who has been granted the AV_ADMIN role.
See Section 3.2.3 for login instructions.
Select the Management tab, and then select the Collectors tab.
In the Collectors page, check the list of collectors.
If the collector is running, its Status is set to an up arrow. If it is not, it is set to a red arrow pointing downward.
This page also lists the names of the agents associated with the collectors.
To check the status of collectors from the command line:
Open a shell or command prompt for the Audit Vault Server.
UNIX: Set the environment variables, as described in Section 2.2.2.
Microsoft Windows: Go to the Audit Vault Server ORACLE_HOME\bin directory.
Run the avctl show_collector_status command.
For example:
avctl show_collector_status -collname DBAUD_Collector -srcname hr_db Getting collector metrics... -------------------------------- Collector is running Records per second = 0.00 Bytes per second = 0.00 --------------------------------
See Section 7.6 for detailed information about the avctl show_collector_status command.
If the collection agents are not active (for example, they were disabled), then no audit data is lost, as long as the source database continues to collect the audit data. When you restart the collection agent, it captures the audit data that the source database had collected during the time the collection agent was inactive.
To ensure that audit records are being collected, inspect the contents of the log files in the Audit Vault collection agent $ORACLE_HOME/av/log directory. The log file names for command-line utilities are as follows:
Oracle Database AVORCLDB utility: collname_srcname_src_id.log and srcname-collname-#.log
Microsoft SQL Server AVMSSQLDB utility: srcname-mssqldb-#.log
Sybase ASE AVSYBDB: srcname-sybdb-#.log
IBM DB2 AVDB2DB utility: srcname-db2db-#.log
The log file keeps a running record of its audit record collection operations and will indicate when collection has occurred, or if a problem was encountered in the collection operation. See Table A-2 for more information about these log files, and troubleshooting collector setup and collector startup operations.