| Oracle® Enterprise Manager Cloud Control Administrator's Guide 12c Release 1 (12.1.0.1) Part Number E24473-09 |
|
|
PDF · Mobi · ePub |
| Oracle® Enterprise Manager Cloud Control Administrator's Guide 12c Release 1 (12.1.0.1) Part Number E24473-09 |
|
|
PDF · Mobi · ePub |
This chapter describes how to configure Oracle Enterprise Manager Security. Specifically, this chapter contains the following sections:
Oracle Enterprise Manager provides tools and procedures to help you ensure that you are managing your Oracle environment in a secure manner. The goals of Oracle Enterprise Manager security are:
To ensure that only users with the proper privileges have access to critical monitoring and administrative data.
This goal is met by requiring username and password credentials before users can access the Enterprise Manager consoles and appropriate privileges for accessing the critical data.
To ensure that all data transferred between Enterprise Manager components is transferred in a secure manner and that all data gathered by each Oracle Management Agent can be transferred only to the Oracle Management Service for which the Management Agent is configured.
This goal is met by enabling Enterprise Manager Framework Security. Enterprise Manager Framework Security automates the process of securing the Enterprise Manager components installed and configured on your network.
To ensure that sensitive data such as credentials used to access target servers are protected.
This goal is met by Enterprise Manager's encryption support. The sensitive data is encrypted with an emkey. By following the best practice, even the repository owner and the SYSDBA will not be able to access the sensitive data.
To ensure that access to managed targets is controlled through user authentication and privilege delegation.
This goal is met by configuring the Management Agent with PAM and LDAP for user authentication and using privilege delegation tools like Sudo and PowerBroker.
Enterprise Manager authentication is the process of determining the validity of the user accessing Enterprise Manager. The authentication feature is available across the different interfaces such as Enterprise Manager console and Enterprise Manager Command Line Interface (EM CLI).
Enterprise Manager's authentication framework consists of pluggable authentication schemes that let you use the type of authentication protocol best suited to your environment.
The following authentication schemes are available:
Oracle Access Manager (OAM) SSO - Oracle Access Manager is the Oracle Fusion Middleware single sign-on solution. The underlying identity stores will be the Enterprise Directory Identity Stores being supported by Oracle Access Manager. For more information about OAM, see Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager 12c Release 1 (11.1.1).
Repository-Based Authentication: This is the default authentication option. An Enterprise Manager administrator is also a repository (database) user. By using this option, you can take advantage of all the benefits that this authentication method provides like password control via password profile, enforced password complexity, password life time, and number of failed attempts allowed. During the password grace period, the administrator is prompted to change the password but when the password has expired, it must be changed.For more details, refer to Repository-Based Authentication.
SSO-Based Authentication: The single sign-on based authentication provides strengthened and centralized user identity management across the enterprise. After you have configured Enterprise Manager to use the Oracle Application Server Single Sign-On, you can register any single sign-on user as an Enterprise Manager administrator. You can then enter your single sign-on credentials to access the Oracle Enterprise Manager console. For more details, refer to Single Sign-On Based Authentication.
Enterprise User Security Based Authentication: The Enterprise User Security (EUS) option enables you to create and store enterprise users and roles for the Oracle database in an LDAP-compliant directory server. Once the repository is configured with EUS, you can configure Enterprise Manager to use EUS as its authentication mechanism as described in Enterprise User Security Based Authentication. You can register any EUS user as an Enterprise Manager administrator.
EUS helps centralize the administration of users and roles across multiple databases. If the managed databases are configured with EUS, the process of logging into these databases is simplified. When you drill down to a managed database, Enterprise Manager will attempt to connect to the database using Enterprise Manager credentials. If successful, Enterprise Manager will directly connect you to the database without displaying a login page.
Oracle Internet Directory (OID) Based Authentication - When using an authentication scheme based on Oracle Internet Directory as the identity store, you can plug in the OID-based authentication scheme to have your applications authenticate users against the OID.
Microsoft Active Directory Based Authentication - When using a Microsoft Active Directory as an identity store, you can plug in this scheme to have your applications authenticate users against the Microsoft Active Directory.
Enterprise Manager allows you to create and manage new administrator accounts. Each administrator account includes its own login credentials as well as a set of roles and privileges that are assigned to the account. You can also assign a password profile to the administrator. To create, edit, or view an administrator account:
From the Setup menu, select Security, then select Administrators.
Click the appropriate task button on the Administrators page. The following screen is displayed:
On this page, you can specify the type of administrator account being created and select the password profile. The password cannot be changed by the administrator if the Prevent Password Change checkbox is selected.
If you select the Expire Password Now checkbox, the password for administrator account will be set to an expired state. If the password has expired, when you login the next time, the following screen is displayed and you are prompted to change the password.
Enter your current password and the new password and click Apply. You can now start using Enterprise Manager.
When using an Oracle Access Manager Single Sign-On authentication scheme, the underlying identity stores will consist of Enterprise Directory Identity Stores supported by Oracle Access Manager. This section provides instructions on how to configure OAM SSO-based authentication schemes.
Prerequisites
Oracle access manager is installed.
The Oracle Access Manager Single Sign-On server is configured with Oracle HTTP server, Web Gate, and the Oracle Access Manager Identity Store.
Run the emctl config auth command.
emctl config auth oam [-sysman_pwd <pwd>] -oid_host <host> -oid_port <port> -oid_principal <principal> [-oid_credential <credential>] -user_base_dn <dn> -group_base_dn <dn> -oam_host <host< -oam_port <port> [-logout_url <url>] [-is_oam10g] [-user_dn <dn>] [-group_dn <dn>]
Note: Pass -is_oam10g option only if the OAM version is 10g.
Stop each OMS.
emctl stop oms -all
Restart each OMS.
emctl start oms
If you are currently using Oracle Application Server Single Sign-On to control access and authorization for your enterprise, you can extend those capabilities to the Enterprise Manager console.
By default, Enterprise Manager displays the main login page. However, you can configure Enterprise Manager so it uses Oracle Application Server Single Sign-On to authenticate your Enterprise Manager users. Instead of seeing the Enterprise Manager login page, users will see the standard Oracle Application Server Single Sign-On login page. From the login page, administrators can use their Oracle Application Server Single Sign-On credentials to access the Oracle Enterprise Manager 12c Cloud Control console.
Note:
You can configure Enterprise Manager to use one of the default Oracle Application Server Single Sign-On or Enterprise User Security features, but not multiple.
When Enterprise Manager is configured to use Single Sign-On with Server Load Balancer, make sure that the correct monitoring settings have been defined. For details, refer to the chapter on Cloud Control Common Configurations.
The following sections describe how to configure Enterprise Manager as an OracleAS Single Sign-On Partner Application:
To register Enterprise Manager as a partner application manually, follow these steps:
Stop all OMSs by running emctl stop oms on each OMS.
Enter the following URL to navigate to the SSO Administration page.
https://sso_host:sso_port/pls/orasso
Login as orcladmin user and click on SSO Server Administration.
Click Administer Partner Applications and then click Add Partner Application.
Enter the following information on the Add Partner Application page.
Name: <EMPartnerName> Home URL: protocol://em_host:em_port Success URL: protocol://em_host:em_port/osso_login_success Logout URL: protocol://em_host:em_port/osso_logout_success Administrator Email: user@host.com
Note1: host, port, and protocol refer to the Enterprise Manager Host, port and the protocol (http or https) used.
Note2: The em_host, em_port, email and Enterprise Manager PartnerName need to be replaced appropriately and not typed as shown in this example.
Go back to Administer Partner Applications page and click on the Edit icon for <EMPartnerName>.
Record the values of ID, Token, Encryption Key, Login URL, Single Sign-Off URL, Home URL and write the following in a file osso.txt:
sso_server_version= v1.2 cipher_key=<value of EncryptionKey> site_id=<value of ID> site_token=<value of Token> login_url=<value of Login URL> logout_url=<value of Single Sign-Off URL> cancel_url=<value of Home URL> sso_timeout_cookie_name=SSO_ID_TIMEOUT sso_timeout_cookie_key=9E231B3C1A3A808A
Set the ORACLE_HOME environment variable to WebTier Oracle Home location.
setenv ORACLE_HOME /scratch/12c/MWHome/Oracle_WT
Then, run the following:
$ORACLE_HOME/ohs/bin/iasobf <location of osso.txt> <location of osso.conf>
Run the following command on each OMS:
emctl config auth sso -ossoconf <osso.conf file loc> -dasurl <DAS URL> [-unsecure] [-sysman_pwd <pwd>] [-domain <domain>]-ldap_host <ldap host> -ldap_port <ldap port> -ldap_principal <ldap principal> [-ldap_credential <ldap credential>] -user_base_dn <user base DN> -group_base_dn <group base DN> [-logout_url <sso logout url>]
where ldap_host, ldap_port, ldap_principal and ldap_credential are the details of SSO's LDAP.
The sample output for this command is shown below:
Oracle Enterprise Manager Cloud Control 12c Release 12.1.0.1.0 Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. SSO Configuration done successfully. Please restart Admin & Managed Servers.
Run the following commands on each OMS:
emctl stop oms -all emctl start oms
To remove the single sign-on configuration, perform the following:
Run the following command on each OMS:
emctl config auth repos [-sysman_pwd <pwd>]
Sample command output:
Oracle Enterprise Manager Cloud Control 12c Release 12.1.0.1.0 Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Configuring Repos Authentication ... Started Configuring Repos Authentication ... Successful If you have updated files like httpd.conf (for example, while installing WebGate), rollback them. If this is a multi-OMS environment, execute this command on remaining servers. After that, restart OMS(s) using: 'emctl stop oms -all' and 'emctl start oms'
Bounce all OMSs by issuing the following on each OMS:
emctl stop oms -all emctl start oms
After you have configured Enterprise Manager to use the Single Sign-On logon page, you can register any Single Sign-On user as an Enterprise Manager administrator. You can register single sign-on users using:
Enterprise Manager Graphical User Interface
Enterprise Manager Command Line Interface
You can use the graphical user interface to register single sign-on users by following these steps:
Go the Enterprise Manager Console URL.
The browser is redirected to the standard Single Sign-On Logon page.
Enter the credentials for a valid Single Sign-On user. Note: This step requires that an SSO user is already registered with Enterprise Manager.
If no SSO user is yet registered as Enterprise Manager user, you can create them using the following procedure:
1. Log in to Enterprise Manager by connecting to Managed Server (MS) directly. eg: https://ms_host:ms_https_port/em.2. Log in as a Repository user.3. From the Setup menu, select Security then select Administrator
4. Create SSO users.
Log in to Enterprise Manager as a Super Administrator.
From the Setup menu, select Security, then select Administrators to display the Administrators page.
Because Enterprise Manager has been configured to use Single Sign-On, the first page in the Create Administrator wizard now offers you the option of creating an administrator either as an External User or as Repository User.
Select External User Identity Store and advance to the next page in the wizard.
Enter the name and e-mail address of the External User Identity Store user, or click the flashlight icon to search for a user name in the Oracle Internet Directory.
Use the rest of the wizard pages to define the roles, system privileges, and other characteristics of the Enterprise Manager administrator and then click Finish.
Enterprise Manager displays a summary page that lists the characteristics of the administrator account.
Click Finish to create the new Enterprise Manager administrator.
The External User Identity Store user is now included in the list of Enterprise Manager administrators. You can now verify the account by logging out of the Cloud Control console and logging back in using the External User Identity Store user credentials on the Single Sign-On logon page.
s
You can use the following EM CLI command to create Single Sign-On users:
emcli create_user -name=ssouser -type=EXTERNAL_USER
This command creates a user with the name ssouser who is authenticated against the single sign-on user.
| Argument | Description |
|---|---|
| -name | Name of the administrator. |
| -type | The type of user. The default value for this parameter is EM_USER. The other possible values are:
|
| -password | The password for the administrator. |
| -roles | The list of roles that can be granted to this administrator. |
| The list of email addresses for this administrator. | |
| -privilege | The system privileges that can be granted to the administrator. This option can be specified more than once. |
| -profile | The name of the database profile. This is an optional parameter. The default profile used is DEFAULT. |
| -desc | The description of the user being added. |
| -expired | This parameter is used to set the password to "expired" status. This is an optional parameter and is set to False by default. |
| -prevent_change_password | When this parameter is set to True, the user cannot change the password. This is an optional parameter and is set to False by default. |
| -input_file | This parameter allows the administrator to provide the values for any of these arguments in an input file. The format of value is name_of_argument:file_path_with_file_name. |
Example 1
emcli create_user
-name="new_admin"
-email="first.last@oracle.com;joe.shmoe@shmoeshop.com"
-roles="public"
-privilege="view_job;923470234ABCDFE23018494753091111"
-privilege="view_target;<host>.com:host"
This example creates an Enterprise Manager administrator named new_admin. This administrator has two privileges: the ability to view the job with ID 923470234ABCDFE23018494753091111 and the ability to view the target <host>.com:host. The administrator new_admin is granted the PUBLIC role.
Example 2
emcli create_user
-name="User1"
-type="EXTERNAL_USER"
-input_file="privilege:/home/user1/priv_file"
Contents of priv_file are:
view_target;<host>.com:host
This example makes user1 which has been created externally as an Enterprise Manager user. user1 will have view privileges on <host>.com:host.
Example 3
emcli create_user
-name="User1"
-desc="This is temp hire."
-prevent_change_password="true"
-profile="MGMT_ADMIN_USER_PROFILE"
This example sets user1 as an Enterprise Manager user with some description. The prevent_change_password is set to true to indicate that the password cannot be changed by user1 and the profile is set to MGMT_ADMIN_USER_PROFILE.
Example 4
emcli create_user
-name="User1"
-desc="This is temp hire."
-expire="true"
This example sets user1 as an Enterprise Manager with some description. Since the password is set to expire immediately, when the user logs in for the first time, he is prompted to change the password.
If the OMS is configured with SSO or OAM or some other authentication method, you may want to by-pass the Single Sign-On or OAM authentication under certain circumstances.To bypass the SSO logon page, connect to the following URL:
Connect to https://ms_host:ms_https_port/em
ms_host & ms_https_port are WLS-managed server's hostname & port#. These parameters can be found in the EM_INSTANCE_HOME/emgc.properties file. They are listed as EM_INSTANCE_HOST & MS_HTTPS_PORT in this file.
Log in using a repository user's credentials.
Run the following command on each OMS:
emctl config auth repos [-sysman_pwd <pwd>]
Sample command output:
Oracle Enterprise Manager Cloud Control 12c Release 12.1.0.1.0 Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Configuring Repos Authentication ... Started Configuring Repos Authentication ... Successful If you have updated files like httpd.conf (for example, while installing WebGate), rollback them. If this is a multi-OMS environment, execute this command on remaining servers. After that, restart OMS(s) using: 'emctl stop oms -all' and 'emctl start oms'
Run the following commands on each OMS:
emctl stop oms -all emctl start oms
Enterprise User Security enables you to create and store Oracle database information as directory objects in an LDAP-compliant directory server. For example, an administrator can create and store enterprise users and roles for the Oracle database in the directory, which helps centralize the administration of users and roles across multiple databases.
See Also:
Enterprise User Security Configuration Tasks and Troubleshooting in the Oracle Database Advanced Security Administrator's GuideIf you currently use Enterprise User Security for all your Oracle databases, you can extend this feature to Enterprise Manager. Configuring Enterprise Manager for use with Enterprise User Security simplifies the process of logging in to database targets you are managing with the Oracle Enterprise Manager console.
To configure Enterprise Manager for use with Enterprise User Security:
Ensure that you have enabled Enterprise User Security for your Oracle Management Repository database, as well as the database targets you will be managing with the Cloud Control console. Refer to Oracle Database Advanced Security Administrator's Guide for details.
Using the emctl set property command, set the following properties:
oracle.sysman.emSDK.sec.DirectoryAuthenticationType=EnterpriseUser oracle.sysman.emSDK.sec.eus.Domain=<ClientDomainName> (For example:mydomain.com) oracle.sysman.emSDK.sec.eus.DASHostUrl=<das_url> (For example: oracle.sysman.emSDK.sec.eus.DASHostUrl=http://my.dashost.com:7777 )
For example:
emctl set property -name oracle.sysman.emSDK.sec.DirectoryAuthenticationType -value EnterpriseUser
Stop the Oracle Management Service.
Start the Management Service.
The next time you use the Oracle Enterprise Manager console to drill down to a managed database, Enterprise Manager will attempt to connect to the database using Enterprise User Security. If successful, Enterprise Manager will connect you to the database without displaying a login page. If the attempt to use Enterprise User Security fails, Enterprise Manager will prompt you for the database credentials.
After you have configured Enterprise Manager to use Enterprise Users, you can register existing enterprise users as Enterprise Manager Users and grant them the necessary privileges so that they can manage Enterprise Manager effectively.
You can register existing enterprise users by using:
Enterprise Manager Graphic User Interface
Enterprise Manager Command Line Interface
You can use the graphical user interface to register enterprise users by following these steps:
Log into Enterprise Manager as a Super Administrator.
From the Setup menu, select Security then select Administrators to display the Administrators page. Since Enterprise Manager has been configured to use Enterprise Users, the first page of the Create Administrator wizard will provide the option to create an administrator based on a registered Oracle Internet Directory user or a normal database user.
Select Oracle Internet Directory and click Continue to go to the next page in the wizard.
Enter the name and e-mail address of the Oracle Internet Directory user or click the flashlight icon to search for a user name in the Oracle Internet Directory.
Use the rest of the wizard pages to define the roles, system privileges, and other characteristics of the Enterprise Manager administrator and then click Finish. Enterprise Manager displays a summary page that lists the characteristics of the administrator account.
Click Finish to create the new Enterprise Manager administrator.
The OID user is now included in the list of Enterprise Manager administrators. You can now verify the account by logging out of the Cloud Control console and logging back in using the OID user credentials on the Single Sign-On logon page.
To register Enterprise Users as Enterprise Manager users using EM CLI, enter the following command:
emcli create_user -name=eususer -type=DB_EXTERNAL_USER
This command registers the eususer as an Enterprise Manager user where eususer is an existing Enterprise User. For more details, refer to Registering Single Sign-On Users Using EM CLI.
Enterprise Manager uses the authentication capabilities provided by the Oracle WebLogic Server that is part of the OMS. If you are using Microsoft Active Directory as an identity store, you will need to configure it with the Oracle WebLogic Server which is part of the OMS. The following procedure demonstrates how to set up Enterprise Manager authentication using Microsoft Active Directory.
Prerequisites
Ensure Enterprise Manager Cloud Control 12c is installed and configured properly and that you can log in as a user with Super Admin privileges.
Ensure Microsoft Active Directory is installed and configured properly.
Obtain te following from your Microsoft Active Directory administrator. Below is an example of a simple configuration. More complex configurations can be implemented with additional knowledge of LDAP search filters.
Active Directory Port
Active Directory Prinicpal (User created to authenticate with Active Directory for the Oracle WebLogic Server.
Active Directory Principal Password
User Base Distinguised Name (DN)
Group Base DN
| Example | Your Value | ||
|---|---|---|---|
| Host | The Active Directory host | server.oracle.com | |
| Port | The Active Directory Port | 389 (LDAP) or 636 (LDAPS) | |
| Principal User/Password | The Principal User created in Active Directory that will be used to authenticate WebLogic Server. It must be in the Administrators group and belong to the correct Organizational Unit designated in the User base DN. Ensure the "User must change password at next logon" is not checked during setup. | emgcadmin/Welcome11 | |
| User Base DN | The User Base Distinguished Name is the container location of valid users who will be granted access to ENTERPRISE MANAGER. Using the default Users container will allow all Active Directory Users to login to ENTERPRISE MANAGER (though they may not have permissions to see/do anything). Using an Organizational Unit will allow you to further restrict access. | ||
| User Base Filter From Name | |||
| User Name Attribute: | sAMAccountName | ||
| User From Name Filter: | (&(sAMAccountName=%u)(objectclass=user)) |
Use the following procedure to update
As the Weblogic/Enterprise Manager administrator, back up the WLS config.xml file at the following location:
../gc_inst/user_projects/domains/GCDomain/config/config.xml
Log in to the WebLogic Admin Console as weblogic. The WebLogic Admin Console URL can be found in the setupinfo.txt file at the following location:
$ORACLE_HOME/install/setupinfo.txt
Under Domain Structure, click Security Realms.
Click myrealm and then click the Providers tab.
Click Lock & Edit to enable editing.
Click New to add a Provider.
Enter a Name for your Provider (for example, MS Active Directory).
Select ActiveDirectoryAuthenticator for Type and then click OK.
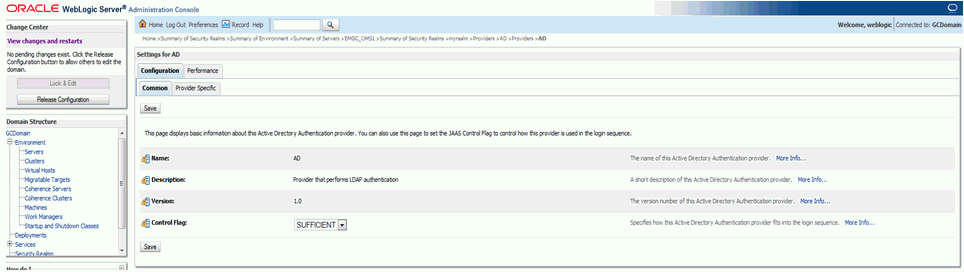
On the Providers screen, click the New Provider link to begin editing.
Set the Control Flag to Sufficient and then click Save.
Click the Provider Specific tab
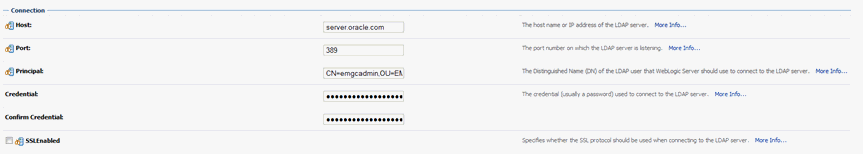
In the Connection section, enter the following:
Host: AD Server Host
Port: 389 (default for LDAP, or 636 for LDAPS)
Principal:CN=EMGCADMIN,CN=Users,DC=Cloudcontrol,DC=local
Note:
This is the User created in AD steps above and added to Administrators group. The CN/DC string must be confirmed with your Active Directory administrator.Credential: pwd for principal
In the Users section, set the User Base DN to the value provided by your Active Directory administrator. This is the Group or Organization Unit that will have access to Enterprise Manager. To restrict access to a specific set of users, you must use an Organization Unit.
User Base DN: cn=users,dc=Cloudcontrol,dc=local
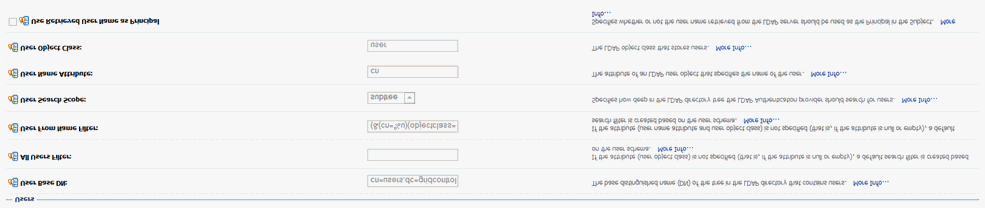
Note:
This information must be obtained from the AD Administrator.If you want to use the Login Name instead of the Account Name (which is typically First Last) then you need to set the User From Name Filter and User Name Attribute as follows:
User Name Attribute: sAMAccountName
User From Name Filter: (&(sAMAccountName=%u)(objectclass=user))
In the Groups section, enter the following:
Group Base dn: cn=Users,dc=Cloudcontrol,dc=local
Note: This information must be obtained from the AD Administrator
In the General section, click Propagate Cause For Login Exception.
Click Save.
In the Authenticaiton Providers section, click Reorder and move your new provider to the top of the list.
Click Apply & Activate Changes.
There are two options to provision users to Enterprise Manager. You can set a flag to auto-provision all users, or you can manually create them as external users using EM CLI.
To set Auto Provisioning to true, run the following:
$ bin/emctl set property -name "em.security.auth.autoprovisioning" -value "true" Oracle Enterprise Manager Cloud Control 12c Release 12.1.0.1.0Copyright (c) 1996, 2012 Oracle Corporation. All rights reserved. SYSMAN password:
The property em.security.auth.autoprovisioning for the OMS server.oracle.com:4890_Management_Service has been set to value true
OMS restart is required to reflect the new property value.
If you do not want all users created automatically, you must manually create them using the EM CLI (after restart).
$ bin/emcli create_user -name='TEST' -type='EXTERNAL_USER' User "TEST" created successfully
Restart the OMS.
$ bin/emctl stop oms -all $ bin/emctl start oms
The users will not show up in the Enterprise Manager Administrators UI until they have logged in once.
To assign a group of privileges to the LDAP users, you can create an external role with the same name as the LDAP group. Once the users are authenticated, they will inherit the permissions and privileges granted to the external role automatically.
Create a Group in the Active Directory and assign users to the group.
From the Setup menu, select Security, then select Roles.
Click Create .
Enter the name of the Active Directory group and a brief description.
Check the box for External, and then click Next.
Assign additional Roles, and then click Next.
Assign target privileges, and then click Next.
Assign resource privileges, and then click Next.
Review the settings and click Finish.
Password management for Active Directory users must be handled through Active Directory. Password changes are not allowed via Enterprise Manager or WebLogic Server.
An Active Directory user must be deleted from Enterprise Manager to remove access to Cloud Control. If the user remains in Active Directory, they should be removed from any Groups assigned privileges through External Roles to ensure they cannot login again if auto-provisioning is enabled.
Removing Active Directory authentication will remove all Active Dirctory user accounts from Enterprise Manager.
Log in to the WebLogic Server console.
Under Domain Structure, click on Security Realms.
Click myrealm, then click on the Providers tab.
Click Lock & Edit to enable editing.
Click the NT Authenticator provider.
Click Delete.
Click Save and Activate.
Restart the OMS.
Giving the same level of access to all systems to all administrators is dangerous, but individually granting access to tens, hundreds, or even thousands of targets to every new member of the group is time consuming. With Enterprise Manager's administrator privileges and roles feature, this task can be performed within seconds, instead of hours. Authorization controls the access to the secure resources managed by Enterprise Manager via system, target, and object level privileges and roles.
This section describes Enterprise Manager's Authorization model including user classes, roles, and privileges assigned to each user class. The following topics are described:
Classes of Users
Privileges and Roles
An authentication scheme is the type of authentication supported by a target type. For example, a host can support a username/password-based authentication, Public Key authentication or Kerberos authentication. In fact, each target type in an enterprise may support different authentication schemes. To accommodate the many authentication schemes that can exist in a managed environment, Enterprise Manger allows you to configure the credentials for these authentication schemes as well.
Oracle Enterprise Manager supports different classes of Oracle users, depending upon the environment you are managing and the context in which you are using Oracle Enterprise Manager.
The Enterprise Manager administrators you create and manage in the Could Control console are granted privileges and roles to log in to the Cloud Control console and to manage specific target types and to perform specific management tasks. The default super administrator for the Cloud Control Console is the SYSMAN user, which is a database user associated with the Oracle Management Repository. You define the password for the SYSMAN account during the Enterprise Manager installation procedure.
By restricting access to privileged users and providing tools to secure communications between Oracle Enterprise Manager 12c components, Enterprise Manager protects critical information in the Oracle Management Repository.
The Management Repository contains management data that Enterprise Manager uses to help you monitor the performance and availability of your entire enterprise. This data provides you with information about the types of hardware and software you have deployed, as well as the historical performance and specific characteristics of the applications, databases, applications servers, and other targets that you manage. The Management Repository also contains information about the Enterprise Manager administrators who have the privileges to access the management data.
You can create and manage Enterprise Manager administrator accounts. Each administrator account includes its own login credentials, as well as a set of roles and privileges that are assigned to the account. There are three administrator access categories:
Super Administrator: Powerful Enterprise Manager administrator with full access privileges to all targets and administrator accounts within the Enterprise Manager environment. The Super Administrator, SYSMAN is created by default when Enterprise Manager is installed. The Super Administrator can create other administrator accounts.
Administrator: Regular Enterprise Manager administrator.
Repository Owner: Database administrator for the Management Repository. This account cannot be modified, duplicated, or deleted.
The types of management tasks that the administrator can perform and targets that he can access depends on the roles, system privileges, and target privileges that he is granted. The Super Administrator can choose to let certain administrators perform only certain management tasks, or access only certain targets, or perform certain management tasks on certain targets. In this way, the Super Administrator can divide the workload among his administrators.
User privileges provide a basic level of security in Enterprise Manager. They are designed to control user access to data and to limit the kinds of SQL statements that users can execute. When creating a user, you grant privileges to enable the user to connect to the database, to run queries and make updates, to create schema objects, and more.
When Enterprise Manager is installed, the SYSMAN user (super administrator) is created by default. The SYSMAN Super Administrator then creates other administrator accounts for daily administration work. The SYSMAN account should only be used to perform infrequent system wide, global configuration tasks.The Super Administrator divides workload among his administrators by filtering target access, or filtering access to management task, or both through the roles, System Privileges, and Target Privileges he grants them. For example, he can allow some administrators to view any target and to add any target in the enterprise and other administrators to only perform specific operations such as maintaining and cloning on a target for which they are responsible.
A role is a collection of Enterprise Manager resource privileges, or target privileges, or both, which you can grant to administrators or to other roles. These roles can be based upon geographic location (for example, a role for Canadian administrators to manage Canadian systems), line of business (for example, a role for administrators of the human resource systems or the sales systems), or any other model. Administrators do not want to perform the task of individually granting access to tens, hundreds, or even thousands of targets to every new member of their group.By creating roles, an administrator needs only to assign the role that includes all the appropriate privileges to his team members instead of having to grant many individual privileges. He can divide workload among his administrators by filtering target access, or filtering access to management task, or both.
Out-of-Box Roles: Enterprise Manager Cloud Control 12c comes with predefined roles to manage a wide variety of resource and target types. The following table lists these roles along with their function.
Table 10-1 Out-of-the-Box Roles
| Roles | Description |
|---|---|
|
EM_ALL_ADMINISTRATOR |
Role has privileges to perform Enterprise Manager administrative operations. It provides Full privileges on all secure resources (including targets) |
|
EM_ALL_DESIGNER |
Role has privileges to design Enterprise Manager operational entities such as Monitoring Templates. |
|
EM_ALL_OPERATOR |
Role has privileges to manage Enterprise Manager operations. |
|
EM_ALL_VIEWER |
Role has privileges to view Enterprise Manager operations. |
|
EM_CBA_ADMIN |
Role to manage Chargeback Objects. It gives the capability to create and view chargeback plans, chargeback consumers, assign chargeback usage, and view any CaT targets. |
|
EM_CLOUD_ADMINISTRATOR |
Enterprise Manager user for setting up and managing the infrastructure cloud. This role could be responsible for deploying the cloud infrastructure (servers, pools, zones) and infrastructure cloud operations for performance and configuration management. |
|
EM_COMPLIANCE_DESIGNER |
Role has privileges for create, modify and delete compliance entities. |
|
EM_COMPLIANCE_OFFICER |
Role has privileges to view compliance framework definition and results. |
|
EM_CPA_ADMIN |
Role to manage Consolidation Objects. It gives the capability to create and view consolidation plans, consolidation projects and view any CaT targets. |
|
EM_HOST_DISCOVERY_OPERATOR |
Role has privileges to execute host discovery |
|
EM_INFRASTRUCTURE_ADMIN |
Role has privileges to manage the Enterprise Manager infrastructure such as managing plugin lifecycle or managing self update. |
|
EM_PATCH_ADMINISTRATOR |
Role for creating, editing, deploying, deleting and granting privileges for any patch plan. |
|
EM_PATCH_DESIGNER |
Role for creating and viewing for any patch plan |
|
EM_PATCH_OPERATOR |
Role for deploying patch plans |
|
EM_PLUGIN_AGENT_ADMIN |
Role to support plug-in lifecycle on Management Agent |
|
EM_PLUGIN_OMS_ADMIN |
Role to support plug-in lifecycle on Management Server |
|
EM_PLUGIN_USER |
Role to support view plug-in console |
|
EM_PROVISIONING_DESIGNER |
Role has privileges for provisioning designer |
|
EM_PROVISIONING_OPERATOR |
Role has privileges for provisioning operator |
|
EM_SSA_ADMINISTRATOR |
EM user with privilege to set up the Self Service Portal. This role can define quotas and constraints for self service users and grant them access privileges. |
|
EM_SSA_USER |
This role grants EM user the privilege to access the Self Service Portal. |
|
EM_TARGET_DISCOVERY_OPERATOR |
Role has privileges to execute target discovery. |
|
EM_TC_DESIGNER |
Role has privileges for creating Template Collections |
|
EM_USER |
Role has privilege to access Enterprise Manager Application. |
|
PUBLIC |
PUBLIC role is granted to all administrators. This role can be customized at site level to group privileges that need to be granted to all administrators. |
Public Role: Enterprise Manager creates one role by default called Public. This role is unique in that it is automatically assigned to all new non-super administrators when they are created. By default it has no privileges assigned to it. The Public role should be used to define default privileges you expect to assign to a majority of non-super administrators you create. Privileges need not be assigned to Public initially - they can be added at any time. The role may be deleted if your enterprise does not wish to use it. If deleted, it can be added back in later if you later decide to implement it.
A privilege is a right to perform management actions within Enterprise Manager. Privileges can be divided into two categories:
Target Privileges
Resource Privileges
Target Privileges: These privileges allow an administrator to perform operations on a target. The Target Privileges page shows a list of targets for which privileges can be granted. Select the check box to specify the privileges that are to be granted and click Next.
Table 10-2 Target Privileges Applicable to All Targets
| Privilege Name | Privilege Display Name | Description |
|---|---|---|
|
FULL_ANY_TARGET |
Full any Target |
Ability to do all operations on all the targets, including delete the target |
|
PERFORM_OPERATION_AS_ANY_AGENT |
Execute Command as any Agent |
Execute any OS Command as the Agent User at any Agent |
|
PUT_FILE_AS_ANY_AGENT |
Put File as any Agent |
Put any File to any Agent's Filesystem as the Agent User |
|
PERFORM_OPERATION_ANYWHERE |
Execute Command Anywhere |
Execute any OS Command at any Agent |
|
OPERATOR_ANY_TARGET |
Operator any Target |
Privilege to grant operator access on all targets |
|
CONNECT_ANY_VIEW_TARGET |
Connect to any viewable target |
Ability to connect and manage any of the viewable target |
|
USE_ANY_BEACON |
Use any beacon |
Ability to register with any Beacon |
|
EM_MONITOR |
EM Monitor |
Ability to view any EM Repository targets |
|
VIEW_ANY_TARGET |
View any Target |
Ability to view any target |
|
GRANT_VIEW_ORACLE_VM_MANAGER |
Grant View Oracle VM Manager Privilege |
Ability to grant View Oracle VM Manager privilege |
|
GRANT_VIEW_ORACLE_VM_ZONE |
Grant View Zone Privilege |
Ability to grant View Zone privilege |
|
GRANT_VIEW_ORACLE_CLOUD_ZONE |
Grant View Database Zone Privilege |
Ability to grant view privilege on Database Zone targets |
|
CREATE_PROPAGATING_GROUP |
Create Privilege Propagating Group |
Ability to create privilege propagating groups.Privileges granted on a privilege propagating group will be automatically granted on the members of the group |
|
CREATE_TARGET |
Create Target |
Ability to create a target |
Table 10-3 Target Privileges Applicable to Specific Targets
| Privilege Name | Privilege Display Name | Description |
|---|---|---|
|
GROUP_ADMINISTRATION |
Group Administration |
Ability to administor groups |
|
FULL_TARGET |
Full Target |
Ability to do all operations on the target, including delete the target |
|
FMW_DEPLOY_APP_TARGET |
Deploy Fusion Middleware |
Ability to deploy Fusion Middleware components |
|
CONNECT_READONLY_TARGET |
Connect Target Readonly |
Ability to connect to target in readonly mode |
|
CONNECT_TARGET |
Connect Target |
Ability to connect and manage target |
|
MANAGE_TARGET_COMPLIANCE |
Manage Target Compliance |
Ability to manage compliance of the target |
|
PERFORM_OPERATION_AS_AGENT |
Execute Command as Agent |
Execute any OS Command as the Agent User |
|
PUT_FILE_AS_AGENT |
Put File as Agent |
Put any File to the Agent's Filesystem as the Agent User |
|
MANAGE_TARGET_ALERTS |
Manage Target Events |
Ability to clear events, re-evaluate metric alert events, create incidents, add events to incidents, and define what actions the administrator can perform on individual incidents, such as acknowledgment or escalation. |
|
PERFORM_OPERATION |
Execute Command |
Execute any OS Command |
|
CONFIGURE_TARGET |
Configure target |
Ability to edit target properties and modify monitoring configuration |
|
MANAGE_TARGET_PATCH |
Manage Target Patch |
Privilege to Analyze, Apply and Rollback patches on the target |
|
MANAGE_TC_OPERATION |
Manage Template Collection Operations |
Ability to associate a template collection to a admiministration group and Sync targets with the associated template collections. |
|
MANAGE_TARGET_METRICS |
Manage Target Metrics |
Ability to edit threshold for metric and policy setting, apply monitoring templates, and manage User Defined Metrics |
|
BLACKOUT_TARGET |
Blackout Target |
Ability to create, edit, schedule and stop a blackout on the target |
|
OPERATOR_TARGET |
Operator Target |
Ability to do normal administrative operations on the target, such as configure a blackout and edit the target properties |
|
FMW_OPERATOR_PRIV |
Operator Fusion Middleware |
"Ability to perform operations, such as start and shutdown and view logs for Fusion Middleware targets |
|
FMW_PROCESS_CONTROL_TARGET |
Process Control Fusion Middleware |
Ability to start or shutdown Fusion Middleware target |
|
FMW_VIEW_LOG_DATA_TARGET |
View Fusion Middleware logs |
Ability to view Fusion Middleware diagnostics data |
|
VIEW_ORACLE_CLOUD_ZONE |
View Database Zone |
Ability to view Database Zone |
|
VIEW_ORACLE_VM_MANAGER |
View Oracle VM Manager |
Ability to view Oracle VM Manager |
|
VIEW_ORACLE_VM_ZONE |
View Oracle VM Zone |
Ability to view Oracle VM Zone |
|
VIEW_TARGET |
View Target |
Ability to view properties, inventory and monitor information about a target |
Resource: These privileges allow a user to perform operations against specific types of resources. To set Resource Privileges, from the Setup menu, choose Administrators. Select an administrator from the list and click Edit. The Edit Administrator wizard is displayed. Click Next to navigate through the wizard to see the System Privileges page. The following table lists all available resource privileges.
| Resource Type | Display Name | Description | Privileges Required to Grant |
|---|---|---|---|
| ACCESS | Access Enterprise Manager | Ability to access Enterprise Manager interfaces | ACCESS |
| AD4J | JVM Diagnostics User | Gives capability to view the JVM Diagnostic data | SUPER_USER |
| AD4J | JVM Diagnostics Administrator | Gives capability to manage all JVM Diagnostic Administrative operations | SUPER_USER |
| ASREPLAY_ENTITY_MGMT | Application Replay Operator | View, create, and edit any Application Replay entity. | SUPER_USER |
| ASREPLAY_ENTITY_MGMT | Application Replay Viewer | View any Application Replay entity. | SUPER_USER |
| BTM | Request Monitoring User | Gives capability to view the Request Monitoring Data | SUPER_USER |
| BTM | Request Monitoring Administrator | Gives capability to manage all Request Monitoring Administrative Operations | SUPER_USER |
| CA | Full Corrective Action | Internal privilege, not for granting | |
| CA | View Corrective Action | Internal privilege, not for granting | VIEW |
| CCS_SECURE_CLASS | Manage custom configurations owned by any user | Ability to create new and edit/delete Custom Configuration specification owned by any user | |
| CCS_SECURE_CLASS | Manage custom configurations owned by the user | Ability to create new and edit/delete Custom Configuration specification owned by the user | |
| CHANGE_PLAN | Manage change plans | Create and delete Change Manager Change Plans | FULL |
| CHANGE_PLAN | Edit change plan | Edit a Change Manager Change Plan | EDIT |
| CHANGE_PLAN | View change plan | View a Change Manager Change Plan | VIEW |
| CHARGEBACK_AND_CONSOLIDATION | Manage Chargeback Plans | Ability to Create and Modify Chargeback Plans. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Manage Any Consolidation Plan | Ability to Manage any Consolidation Plans. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Chargeback and Consolidation Target | Ability to View Chargeback and Consolidation Target. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Any Chargeback and Consolidation Target | Ability to View Any Chargeback and Consolidation Target. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Manage Chargeback and Consolidation Target | Ability to Manage a Chargeback and Consolidation Target. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Manage Any Chargeback and Consolidation Target | Ability to Add/Delete Target to Chargeback and Assign Chargeplan to Target or Add Target to Consolidation Project. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Setup Chargeback and Consolidation | Ability to Setup CAT. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Any Chargeback Consumers | Ability to View Any Chargeback Consumers. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Manage Chargeback Consumers | Ability to Create and Modify Chargeback Consumers. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Assign Chargeback Usage | Ability to Assign Chargeback Usage to Consumers. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Assign Chargeback Plan | Ability to Assign Chargeback Plan to CAT Targets. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Any Chargeback Plan | Ability to view all the Chargeback Plans. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Any Consolidation Plan | Ability to view the Consolidation Plans. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | View Any Consolidation Project | Ability to View any Consolidation Project. | SUPER_USER |
| CHARGEBACK_AND_CONSOLIDATION | Manage Any Consolidation Project | Ability to Manage any Consolidation Project. | SUPER_USER |
| CLOUDPOLICY | Full Policy | Privilege required to View, Modify, Delete a Policy | FULL |
| CLOUDPOLICY | Modify Policy | Ability to Modify a Policy | EDIT |
| CLOUDPOLICY | View Policy | Ability to View a Policy | VIEW |
| CLOUDPOLICY | View any Policy | Ability to View any Policy | VIEW |
| CLOUDPOLICY | Create any Policy | Ability to Create any Policy | CREATE |
| CLOUDPOLICYGROUP | Full Policy Group | Privilege required to View, Modify, Delete a Policy Group | FULL |
| CLOUDPOLICYGROUP | Modify Policy Group | Ability to Modify a Policy Group | EDIT |
| CLOUDPOLICYGROUP | View Policy Group | Ability to View a Policy Group | VIEW |
| CLOUDPOLICYGROUP | View any Policy Group | Ability to View any Policy Group | VIEW |
| CLOUDPOLICYGROUP | Create Policy Group | Ability to Create Policy Group | CREATE |
| COMPLIANCE_FWK | Create Compliance Entity | Ability to create compliance framework, standard, rules | CREATE |
| COMPLIANCE_FWK | Full any Compliance Entity | Ability to edit/delete compliance framework, standard, rules | FULL |
| COMPLIANCE_FWK | View any Compliance Framework | Ability to view compliance framework definition and results | VIEW |
| DISCOVERY | Can Scan Network | Privilege to create, edit and delete host discovery configuration | |
| DISCOVERY | View Any Discovered Hosts | Privilege to view any discovered hosts | |
| DISCOVERY | View Any Discovered Targets On Host | Privilege to view any discovered targets on host | |
| DP | Grant full privilege | Ability to grant upto full privilege on deployment procedures. | GRANT |
| DP | Grant launch privilege | Ability to grant launch privilege on deployment procedures. | GRANT |
| DP | Import | Ability to create deployment procedures and ability to import/export customized deployment procedures. | CREATE |
| DP | Full | Ability to perform launch, create like, edit structure and delete operations on a Deployment Procedure. | GRANT_FULL_DP |
| DP | Create | Ability to create deployment procedures. | CREATE |
| DP | Launch | Ability to perform launch and create like operations on a Deployment Procedure. | GRANT_LAUNCH_DP |
| EMHA_SECURE_CLASS | Enterprise Manager High Availability Administration | Gives access to manage Enterprise Manager High Availability | ADMIN |
| EVENT | Manage Events | Manage events privilege object | MANAGE_EVENT |
| EVENT | View Events | View events privilege object | VIEW |
| FMW_DIAG_SEC_CLASS | Create Object | Ability to manage the offline diagnostic object lifecycle | SUPER_USER |
| FMW_DIAG_SEC_CLASS | View object | Ability to view the offline diagnostics objects | SUPER_USER |
| ISSUE | Manage Problems | Manage problems privilege object | MANAGE_PROBLEM |
| ISSUE | Manage Incidents | Manage incidents privilege object | MANAGE_INCIDENT |
| ISSUE | View Issues - (Incidents and Problems) | View issues - Incidents and Problems privilege object | VIEW |
| JOB | Full | Ability to perform all the valid operations on job, library job, deployment procedure configuration and on deployment procedure instance. | FULL |
| JOB | Grant view privilege | Ability to grant view privilege on jobs. | GRANT |
| JOB | Manage | Ability to perform various operations except edit and delete on job, library job, deployment procedure configuration and on deployment procedure instance. | EDIT |
| JOB | View | Ability to view, do create like on a job, launch deployment procedure configuration and view deployment procedure instance. | GRANT_VIEW_JOB |
| JOB | Create | Ability to submit jobs, create library jobs, create deployment procedure instance and create deployment procedure configuration. | CREATE |
| MEXT_SECURE_CLASS | Full MEXT | Gives complete access to edit, and delete metric extension object | |
| MEXT_SECURE_CLASS | Edit MEXT | Can edit or create the next version of a metric extension object, but cannot delete it | |
| MEXT_SECURE_CLASS | Create New Metric Extension | Create or import new metric extensions | |
| NAMED_CREDENTIALS | Create new Named Credential | Ability to create new named credentials | |
| NAMED_CREDENTIALS | View Credential | View Credential | |
| NAMED_CREDENTIALS | Edit Credential | User can update credential but cannot delete it. | |
| NAMED_CREDENTIALS | Full Credential | Full Credential | |
| PATCH | Privileges for Patch Setup | Privilege to grant privileges any Patching plan object | |
| PATCH | Manage privileges on any Patching Plan | Privilege to grant or revoke privileges on any Patching plan object | MANAGE |
| PATCH | Full privileges on any Patching Plan | Privilege to view, modify, execute and delete any Patching plan object | FULL |
| PATCH | Manage privileges on a Patching Plan | Privilege to grant or revoke privileges on a Patching plan object | MANAGE |
| PATCH | View any Patching Plan | Privilege to view any Patching plan object | VIEW |
| PATCH | Full Patch Plan | Privilege to view, modify, execute and delete a Patching plan object | MANAGE_PRIV_ANY_PATCH_PLAN |
| PATCH | View any Patching Plan Template | Privilege to view any Patching Plan Template object | VIEW |
| PATCH | Create Patch Plan | Privilege for creating a Patching Plan object | |
| PATCH | View Patching Plan | Privilege to View a Patching Plan Object | MANAGE_PRIV_ANY_PATCH_PLAN |
| PATCH | Create Patch Plan Template | Privilege for creating a Patching Plan Template object | |
| PLUGIN | Plug-in view privilege | Gives access to manage Enterprise Manager plug-in life cycle console | USER |
| PLUGIN | Plug-in Agent Administrator | Gives access to manage Enterprise Manager plug-in on Agent | ADMIN |
| PLUGIN | Plug-in OMS Administrator | Gives access to manage Enterprise Manager plug-in on Management Server | ADMIN |
| REPORT_DEF | View Report | Ability to view report definition and stored reports, generate on demand reports and do a create like | VIEW |
| REPORT_DEF | Publish Report | Ability to publish reports for public viewing | |
| RULESET_SEC | Edit Business Ruleset | Edit Business Ruleset | EDIT |
| RULESET_SEC | Create Business Ruleset | Create Business Ruleset | CREATE |
| SBRM_BACKUP_CONFIG | Create Backup Configuration | Ability to create a backup configuration. | SUPER_USER |
| SBRM_BACKUP_CONFIG | Use Backup Configuration | Ability to use a backup configuration. | SUPER_USER |
| SBRM_BACKUP_CONFIG | Edit Backup Configuration | Ability to edit a backup configuration. | SUPER_USER |
| SBRM_BACKUP_CONFIG | Full Access | Full access to a backup configuration. | SUPER_USER |
| SELFUPDATE_SECURE_CLASS | Self Update Administrator | Gives access to manage Enterprise Manager Update | FULL |
| SELFUPDATE_SECURE_CLASS | View any Enterprise Manager Update | Gives access to view any Enterprise Manager Update | VIEW |
| SSA | Access Cloud Self Service Portal | Users with this privilege have access to Cloud Self Service Portal. | SUPER_USER |
| SSA | Setup Cloud Self Service Portal | Privilege to perform Cloud Self Service Portal setup like defining quotas for roles, publishing assemblies etc. | SUPER_USER |
| SWLIB_ADMINISTRATION | Software Library Storage Administration | Ability to manage upload and reference file storage locations, import and export entities, and purge deleted entities | FULL |
| SWLIB_ENTITY_MGMT | View any Assembly Entity | View any Assembly Entity | SWLIB_GRANT_ANY_ENTITY_PRIV |
| SWLIB_ENTITY_MGMT | View any Template Entity | View any Template Entity | SWLIB_GRANT_ANY_ENTITY_PRIV |
| SWLIB_ENTITY_MGMT | Grant Any Entity Privilege | Ability to grant view, edit and delete privilege on any Software Library entity. This privilege is required if the user granting the privilege on an entity is not a super administrator or owner of the entity. | GRANT |
| SWLIB_ENTITY_MGMT | Manage Entity | Ability to view, edit and delete a Software Library entity | SWLIB_GRANT_ANY_ENTITY_PRIV |
| SWLIB_ENTITY_MGMT | View Software Library Entity | Ability to view a Software Library entity | SWLIB_GRANT_ANY_ENTITY_PRIV |
| SWLIB_ENTITY_MGMT | Edit an Software Library Entity | Ability to edit a Software Library entity | SWLIB_GRANT_ANY_ENTITY_PRIV |
| SWLIB_ENTITY_MGMT | Create Any Software Library Entity | Ability to create any Software Library entity | CREATE |
| SWLIB_ENTITY_MGMT | View Any Software Library Entity | Ability to view any Software Library entity | VIEW |
| SWLIB_ENTITY_MGMT | Edit Any Software Library Entity | Ability to edit any Software Library entity | EDIT |
| SWLIB_ENTITY_MGMT | Manage Any Software Library Entity | Ability to create, view, edit and delete any Software Library entity | FULL |
| SWLIB_ENTITY_MGMT | Import Any Software Library Entity | Ability to import any Software Library entity from a Provisioning Archive (PAR) file | IMPORT |
| SWLIB_ENTITY_MGMT | Export Any Software Library Entity | Ability to view and export any Software Library entity to a Provisioning Archive (PAR) file | EXPORT |
| SYSTEM | Super User | Provides all the privileges to any target in the system | |
| TEMPLATE | View Template | Ability to access a template and apply it to any target on which you have Manage Target Metrics | |
| TEMPLATE | View Template | Ability to view a template and apply it to any target on which you have Manage Target Metrics | VIEW |
| TEMPLATE | View any Monitoring Template | View any Monitoring Template. | VIEW |
| TEMPLATECOLLECTION | Full Template Collection | Ability to edit and delete Template Collection | FULL |
| TEMPLATECOLLECTION | View Template Collection | Ability to view Template Collection | VIEW |
| TEMPLATECOLLECTION | View any Template Collection | Ability to view any Template Collection | VIEW |
| TEMPLATECOLLECTION | Create any Template Collection | Ability to create any Template Collection | CREATE |
Select the check box to select the resource privilege to be granted to the administrator and click Next.
This section contains the following topics:
Enterprise Manager Framework Security provides safe and secure communication channels between the components of Enterprise Manager. For example, Framework Security provides secure connections between your Oracle Management Service and its Management Agents.
See Also:
Oracle Enterprise Manager Concepts for an overview of Enterprise Manager componentsEnterprise Manager Framework Security implements the following types of secure connections between the Enterprise Manager components:
HTTPS and Public Key Infrastructure (PKI) components, including signed digital certificates, for communications between the Management Service and the Management Agents.
See Also:
Oracle Security Overview for an overview of Public Key Infrastructure features, such as digital certificates and public keysOracle Advanced Security for communications between the Management Service and the Management Repository.
See Also:
Oracle Database Advanced Security Administrator's GuideTo enable Enterprise Manager Framework Security for the Management Service, you use the emctl secure oms utility, which is located in the following subdirectory of the Management Service home directory:
ORACLE_HOME/bin
The emctl secure oms utility performs the following actions:
Generates a Root Key within your Management Repository. The Root Key is used during distribution of Oracle Wallets containing unique digital certificates for your Management Agents.
Modifies your WebTier to enable an HTTPS channel between your Management Service and Management Agents, independent from any existing HTTPS configuration that may be present in your WebTier.
Enables your Management Service to accept requests from Management Agents using Enterprise Manager Framework Security.
To run the emctl secure oms utility you must first choose an Agent Registration Password. The Agent Registration password is used to validate that future installation of Oracle Management Agents are authorized to load their data into this Enterprise Manager installation.
To enable Enterprise Manager Framework Security for the Oracle Management Service:
Stop the Management Service, the WebTier, and the other application server components using the following command:
OMS_ORACLE_HOME/bin/emctl stop oms
Enter the following command:
OMS_ORACLE_HOME/bin/emctl secure oms
You will be prompted for the Enterprise Manager Root Password. Enter the SYSMAN password.
You will be prompted for the Agent Registration Password, which is the password required for any Management Agent attempting to secure with the Management Service. Specify an Agent Registration Password for the Management Service.
Restart the OMS.
After the Management Service restarts, test the secure connection to the Management Service by browsing to the following secure URL using the HTTPS protocol:
https://hostname.domain:https_console_port/em
Note: The Enterprise Manager console URL can be found by running the "emctl status oms -details" command.
For example:
https://mgmthost1.acme.com:7799/em
If the Management Service security has been enabled, your browser displays the Enterprise Manager Login page.
Example 10-1 Sample Output of the emctl secure oms Command
emctl secure oms Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Securing OMS... Started. Securing OMS... Successful
Example 10-2 Usage of the emctl secure oms Command (II)
emctl secure oms [-sysman_pwd <sysman password>] [-reg_pwd <registration password>] [-host <hostname>] [-slb_port <slb port>] [-slb_console_port <slb console port>] [-reset] [-console] [-lock] [-lock_console] [-secure_port <secure_port>] [-upload_http_port <upload_http_port>] [-root_dc <root_dc>] [-root_country <root_country>] [-root_email <root_email>] [-root_state <root_state>] [-root_loc <root_loc>] [-root_org <root_org>] [-root_unit <root_unit>] [-wallet <wallet_loc> -trust_certs_loc <certs_loc>] [-key_strength <strength>] [-cert_validity <validity>] [-protocol <protocol>] [-force_newca] [-ms_hostname <Managed Server hostname>] [-sign_alg <md5|sha1|sha256|sha384|sha512>]
Valid values for <protocol> are the allowed values for Apache's SSLProtocol directive
The parameters are explained below:
sysman_pwd - Oracle Management Repository user password.
reg_pwd - The Management Agent registration password.
host - The host name to be used in the certificate used by the Oracle Management Service. You may need to use the SLB host name if there is an SLB before the Management Service.
reset - A new certificate authority will be created. All the Agents and Oracle Management Services need to be resecured.
secure_port - Specify this to change HTTPS Upload port on WebTier
upload_http_port - Specify this to change HTTP Upload port on WebTier
slb_port - This parameter is required when Server Load Balancer is used. It specifies the secure upload port configured in the Server Load Balancer.
slb_console_port - This parameter is required when Server Load Balancer is used. It specifies the secure console port configured in the Server Load Balancer.
root_dc - The domain component used in the root certificate. The default value is com.
root_country - The country to be used in the root certificate. The default value is US.
root_state - The state to be used in the root certificate. The default value is CA.
root_loc - The location to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_org - The organization name to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_unit - The organizational unit to be used in the root certificate. The default value is EnterpriseManager on <hostname>.
root_email - The email address to be used in the root certificate. The default value is EnterpriseManager@<hostname>.
wallet: This is the location of the wallet containing the third party certificate. This parameter should be specified while configuring third party certificates.
trust_certs_loc - The location of the trusted_certs.txt (required when third party certificates are used).
key_strength: The strength of the key to be used. Valid values are 512, 1024, 2048, and 4096.
cert_validity: The number of days for which the self-signed certificate is valid. The valid range is between 1 to 3650.
protocol: This parameter is used to configure Oracle Management Service in TLSv1-only or SSLv3-only or mixed mode (default). Valid values are the allowed values as per Apache's SSLProtocol directive.
Note:
Thekey_strength and cert_validity parameters are applicable only when the -wallet option is not used.force_newca - If specified, any Agents that are still configured with an older Certificate Authority are ignored.
ms_hostname - Managed Server's hostname.
sign_alg - Signature algorithm.
lock: Locks the Upload
lock_console: Locks the Console
console: If specified, certificate is re-created for HTTPS console port as well
You may need to create a new Certificate Authority (CA) if the current CA is expiring or if you want to change the key strength. A unique identifier is assigned to each CA. For instance, the CA created during installation may have an identifier as ID 1, subsequent CAs will have the IDs 2,3, and so on. At any given time, the last created CA is active and issues certificates for OMSs and Agents.
Example 10-3 Creating a New Certificate Authority
emctl secure createca [-sysman_pwd <pwd>] [-host <hostname>] [-key_strength<strength>] [-cert_validity <validity>] [-root_dc <root_dc>] [-root_country <root_country>] [-root_email <root_email>] [-root_state <root_state>] [-root_loc <root_loc>] [-root_org <root_org>] [-root_unit <root_unit>] Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Creating CA... Started. Successfully created CA with ID 2
Example 10-4 Viewing Information about a Certificate Authority
emcli get_ca_info -ca_id="1;2" -details Info about CA with ID: 1 CA is not configured DN: CN=myhost.example.com, C=US Serial# : 3423643907115516586 Valid From: Tue Mar 16 11:06:20 PDT 2011 Valid Till: Sat Mar 14 11:06:20 PDT 2020 Number of Agents registered with CA ID 1 is 1 myhost.mydomain.com:3872 Info about CA with ID: 2 CA is configured DN: CN=myhost.example.com, C=US, ST=CA Serial# : 1182646629511862286 Valid From: Fri Mar 19 05:17:15 PDT 2011 Valid Till: Tue Mar 17 05:17:15 PDT 2020 There are no Agents registered with CA ID 2
The WebLogic Administrator and Node Manager passwords are stored in the Administration Credentials Wallet. This is present in the EM_INSTANCE_HOME/sysman/config/adminCredsWallet directory. To recreate Administrator Credentials wallet, run the following command on each machine on which the Management Service is running:
emctl secure create_admin_creds_wallet [-admin_pwd <pwd>] [-nodemgr_pwd <pwd>]
To view the security status and OMS port information, use the following command
Example 10-5 emctl status oms -details
> emctl status oms -details Oracle Enterprise Manager Cloud Control 12c Release 12.1.0.1.0 Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Enter Enterprise Manager Root (SYSMAN) Password : ****** Console Server Host : omshost1.example.com HTTP Console Port : 7802 HTTPS Console Port : 5416 HTTP Upload Port : 7654 HTTPS Upload Port : 4473 OMS is not configured with SLB or virtual hostname Agent Upload is locked. OMS Console is locked. Active CA ID: 1 Console URL: https://omshost1.example.com:5416/em Upload URL: https://omshost1.example.com:4473/empbs/upload WLS Domain Information Domain Name : EMGC_DOMAIN Admin Server Host: omshost1.example.com Managed Server Information Managed Server Instance Name: EMGC_OMS1 Managed Server Instance Host: omshost1.example.com
The Oracle Management Service can be configured in the following modes:
TLSv1-only mode: To configure the OMS to use only TLSv1 connections, do the following:
Stop the OMS by entering the following command:
OMS_ORACLE_HOME/bin/emctl stop oms
Enter the following command:
emctl secure oms -protocol TLSv1
Append -Dweblogic.security.SSL.protocolVersion=TLS1 to JAVA_OPTIONS in Domain_Home/bin/startEMServer.sh/cmd. If this property already exists, update the value to TLS1.
Restart the OMS with the following command:
OMS_ORACLE_HOME/bin/emctl start oms
SSLv3 Only Mode: To configure the OMS to use SSLv3 connections only, do the following:
Stop the OMS by entering the following command:
OMS_ORACLE_HOME/bin/emctl stop oms
Enter the following command:
emctl secure oms -protocol SSLv3
Append -Dweblogic.security.SSL.protocolVersion=SSL3 to JAVA_OPTIONS in Domain_Home/bin/startEMServer.sh or startEMServer.cmd on Windows. If this property already exists, update the value to SSL3.
Restart the OMS with the following command:
OMS_ORACLE_HOME/bin/emctl start oms
Mixed Mode: To configure the OMS to use both SSLv3 and TLSv1 connections, do the following:
Stop the OMS by entering the following command:
OMS_ORACLE_HOME/bin/emctl stop oms
Enter the following command:
emctl secure oms
Append -Dweblogic.security.SSL.protocolVersion=ALL to JAVA_OPTIONS in Domain_Home/bin/startEMServer.sh. If this property already exists, update the value to ALL.
Restart the OMS with the following command:
OMS_ORACLE_HOME/bin/emctl start oms
Note:
By default, the OMS is configured to use the Mixed Mode. To configure the Management Agent in TLSv1 only mode, setallowTLSOnly=true in the emd.properties file and restart the Agent.When you install the Management Agent on a host, you must identify the Management Service that will be used by the Management Agent. To enable Enterprise Manager Framework Security for the Management Agent, use the emctl secure agent utility, which is located in the following directory of the Management Agent home directory:
AGENT_HOME/bin (UNIX) AGENT_HOME\bin (Windows)
The emctl secure agent utility performs the following actions:
Obtains an Oracle Wallet from the Management Service that contains a unique digital certificate for the Management Agent. This certificate is required in order for the Management Agent to conduct SSL communication with the secure Management Service.
Obtains an Agent Key for the Management Agent that is registered with the Management Service.
Configures the Management Agent so it is available on your network over HTTPS and so it uses the Management Service HTTPS upload URL for all its communication with the Management Service.
To enable Enterprise Manager Framework Security for the Management Agent:
Ensure that your Management Service and the Management Repository are up and running.
Change directory to the following directory:
AGENT_HOME/bin (UNIX) AGENT_HOME\bin (Windows)
Stop the Management Agent:
emctl stop agent
Enter the following command:
emctl secure agent (UNIX) emctl secure agent (Windows)
The emctl secure agent utility prompts you for the Agent Registration Password, authenticates the password against the Management Service, and reconfigures the Management Agent to use Enterprise Manager Framework Security.
shows sample output of the emctl secure agent utility.
Restart the Management Agent:
emctl start agent
Confirm that the Management Agent is secure by checking the Management Agent home page.
Note:
You can also check if the Agent Management is secure by running theemctl status agent -secure command, or by checking the Agent and Repository URLs in the output of the emctl status agent command.In the Management Agent home page , the Secure Upload field indicates whether or not Enterprise Manager Framework Security has been enabled for the Management Agent.
Example 10-6 Sample Output of the emctl secure agent Utility
emctl secure agent Oracle Enterprise Manager 12c Release 1 Cloud Control. Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Securing agent... Started Securing agent... Successful.
Example 10-7 Sample Output of the emctl status agent secure Command
emctl status agent -secure Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. Checking the security status of the Agent at location set in /private/home/oracle/product/102/em/agent10g/sysman/config/emd.properties... Done. Agent is secure at HTTPS Port 3872. Checking the security status of the OMS at https://cloudcontrol.oraclecorp.com:4889/em/upload/... Done. OMS is secure on HTTPS Port 4888
Because you have already established at least one Agent Registration Password and a Root Key in your Management Repository, they must be used for your new Management Service. Your secure Management Agents can then operate against either Management Service.
All the registration passwords assigned to the current Management Repository are listed on the Registration Passwords page in the Oracle Enterprise Manager 12c Cloud Control Console.
If you install a new Management Service that uses a new Management Repository, the new Management Service is considered to be a distinct enterprise. There is no way for the new Management Service to partake in the same security trust relationship as another Management Service that uses a different Management Repository. Secure Management Agents of one Management Service will not be able to operate against the other Management Service.
Note:
The Oracle Management Service is locked (both console & upload) by default begining with Enterprise Manager 12c.It is important that only secure Management Agent installations that use the Management Service HTTPS channel are able to upload data to your Management Repository and Cloud Control console is accessible via HTTPS only.
To restrict access so Management Agents can upload data to the Management Service only over HTTPS:
Stop the Management Service, the WebTier, and the other application server components:
cd ORACLE_HOME/opmn/bin emctl stop oms
Change directory to the following location in the Management Service home:
ORACLE_HOME/bin
Enter the following command to prevent Management Agents from uploading data to the Management Service over HTTP:
emctl secure lock -upload
To lock the console and prevent HTTP access to the console, enter the following command:
emctl secure lock -console
To lock both, enter either of the following commands:
emctl secure lock or emctl secure lock -upload -console
To lock both the console access and uploads from Agents while enabling security on the Management Service, enter the following command:
emctl secure oms -lock [other options]
Restart the Management Service, the WebTier, and the other application server components:
cd ORACLE_HOME/bin emctl start oms
Verify that you cannot access the OMS upload URL using the HTTP protocol:
For example, navigate to the following URL:
http://hostname.domain:4889/empbs/upload
You should receive an error message similar to the following:
ForbiddenYou are not authorised to access this resource on the server.
Verify that you can access the Management Agent Upload URL using the HTTPS protocol:
For example, navigate to the following URL:
https://hostname.domain:4888/empbs/upload
You should receive the following message, which confirms the secure upload port is available to secure Management Agents:
Http XML File receiverHttp Recceiver Servlet active!
To allow the Management Service to accept uploads from unsecure Management Agents, use the following command:
emctl secure unlock -upload
Note:
The OMS need to be stopped before running 'secure unlock', and then restarted afterwards.
To unlock the console and allow HTTP access to the console, enter the following command:
emctl secure unlock -console
To unlock both, enter either of the following command:
emctl secure unlock emctl secure unlock -console -upload
Example 10-8 Sample Output of the emctl secure lock Command
emctl secure lock Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. OMS Console is locked. Access the console over HTTPS ports. Agent Upload is locked. Agents must be secure and upload over HTTPS port. Restart OMS
Example 10-9 Sample Output of the emctl secure unlock Command
emctl secure unlock Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. OMS Console is unlocked. HTTP ports too can be used to access console. Agent Upload is unlocked. Unsecure Agents may upload over HTTP. Restart OMS
Enterprise Manager uses the Agent Registration password to validate that installations of Oracle Management Agents are authorized to load their data into the Oracle Management Service.
The Agent Registration password is created during installation when security is enabled for the Oracle Management Service. You can add/edit/delete registration passwords directly from the Enterprise Manager console.
Note:
If you want to avoid new Agents from being registered with the OMS, delete all registration passwords.'You can use the Cloud Control Console to manage your existing registration passwords or create additional registration passwords:
From the Setup menu, select Security, then select Registration Passwords.
Enterprise Manager displays the Registration Passwords page (Figure 10-3). The registration password you created when you ran the emctl secure oms command appears in the Registration Passwords table.
Use the Registration Passwords page to change your registration password, create additional registration passwords, or remove registration passwords associated with the current Management Repository.
When you create or edit an Agent Registration Password on the Registration Passwords page, you can determine whether the password is persistent and available for multiple Management Agents or to be used only once or for a predefined period of time.
For example, if an administrator requests to install a Management Agent on a particular host, you can create a one-time-only password that the administrator can use to install and configure one Management Agent.
On the other hand, you can create a persistent password that an administrator can use for the next two weeks before it expires and the administrator must ask for a new password.
To add a new Agent Registration Password, use the following emctl command on the machine on which the Management Service has been installed:
emctl secure setpwd [sysman pwd] [new registration pwd]
The emctl secure setpwd command requires that you provide the password of the Enterprise Manager super administrator user, sysman, to authorize the addition of the Agent Registration Password.
If you change the Agent Registration Password, you must communicate the new password to other Enterprise Manager administrators who need to install new Management Agents, enable Enterprise Manager Framework Security for existing Management Agents, or install additional Management Services.
As with other security passwords, you should change the Agent Registration Password on a regular and frequent basis to prevent it from becoming too widespread.
When you deploy a Management Service that is available behind a Server Load Balancer (SLB), special attention must be given to the DNS host name over which the Management Service will be available. Although the Management Service may run on a particular local host, for example myhost.mycompany.com, your Management Agents will access the Management Service using the host name that has been assigned to the Server Load Balancer. For example, oracleoms.mycompany.com.
As a result, when you enable Enterprise Manager Framework Security for the Management Service, it is important to ensure that the Server Load Balancer host name is embedded into the Certificate that the Management Service uses for SSL communications. To do so, enter the following commands:
This may be done by using emctl secure oms and specifying the host name in the with an extra -host parameter as follows:
Enable security on the Management Service by entering the following command:
emctl secure oms -host <slb_hostname> [-slb_console_port <slb UI port>] [-slb_port <slb upload port>] [other params]
Run this command on each OMS. You will need to restart each OMS after running the 'emctl secure oms' command.
Create virtual servers and pools on the Server Load Balancer.
Verify that the console can be accessed using the following URL:
https://slbhost:slb_console_port/em
Re-secure the Agents with Server Load Balancer by using the following command:
emctl secure agent -emdWalletSrcUrl <SLB Upload or UI URL>
For example:
Agent_Home/bin/emctl secure agent -emdWalletSrcUrl https://slbost:slb_upload_port/em
This section describes how to enable Security for the Oracle Management Repository. This section includes the following topics:
About Oracle Advanced Security and the sqlnet.ora Configuration File
Configuring the Management Service to Connect to a Secure Management Repository Database
Enabling Oracle Advanced Security for the Management Repository
Enabling Security for a Management Agent Monitoring a Secure Management Repository or Database
You enable security for the Management Repository by using Oracle Advanced Security. Oracle Advanced Security ensures the security of data transferred to and from an Oracle database.
See Also:
Oracle Database Advanced Security Administrator's GuideTo enable Oracle Advanced Security for the Management Repository database, you must make modifications to the sqlnet.ora configuration file. The sqlnet.ora configuration file is used to define various database connection properties, including Oracle Advanced Security parameters.
The sqlnet.ora file is located in the following subdirectory of the Database home:
ORACLE_HOME/network/admin
After you have enabled Security for the Management Repository and the Management Services that communicate with the Management Repository, you must also configure Oracle Advanced Security for the Management Agent by modifying the sqlnet.ora configuration file in the Management Agent home directory.
See Also:
"Enabling Security for a Management Agent Monitoring a Secure Management Repository or Database"It is important that both the Management Service and the Management Repository are configured to use Oracle Advanced Security. Otherwise, errors will occur when the Management Service attempts to connect to the Management Repository. For example, the Management Service might receive the following error:
ORA-12645: Parameter does not exist
To correct this problem, be sure both the Management Service and the Management Repository are configured as described in the following sections.
Note:
The procedures in this section describe how to manually modify the sqlnet.ora configuration file to enable Oracle Advanced Security. Alternatively, you can make these modifications using the administration tools described in the Oracle Database Advanced Security Administrator's Guide.If you have enabled Oracle Advanced Security for the Management Service database—or if you plan to enable Oracle Advanced Security for the Management Repository database—use the following procedure to enable Oracle Advanced Security for the Management Service:
Stop the Management Service:
ORACLE_HOME/bin/emctl stop oms
Set Enterprise Manager operational properties by using the emctl set property command.
Restart the Management Service.
ORACLE_HOME/bin/emctl start oms
Table 10-4 Oracle Advanced Security Properties in the Enterprise Manager Properties File
| Property | Description |
|---|---|
|
Defines whether or not Enterprise Manager will use encryption between Management Service and Management Repository.Possible values are TRUE and FALSE. The default value is TRUE.For example:
|
|
|
Defines the Management Service encryption requirement.Possible values are REJECTED, ACCEPTED, REQUESTED, and REQUIRED.The default value is REQUESTED. In other words, if the database supports secure connections, then the Management Service uses secure connections, otherwise the Management Service uses insecure connections. For example:
|
|
|
Defines the different types of encryption algorithms the client supports.Possible values should be listed within parenthesis. The default value is For example:
|
|
|
Defines the Client's checksum requirements. Possible values are REJECTED, ACCEPTED, REQUESTED, and REQUIRED. The default value is REQUESTED. In other words, if the server supports checksum enabled connections, then the Management Service uses them, otherwise it uses normal connections. For example:
|
|
|
This property defines the different types of checksums algorithms the client supports. Possible values should be listed within parentheses. The default value is ( MD5 ). For example:
|
To be sure your database is secure and that only encrypted data is transferred between your database server and other sources, review the security documentation available in the Oracle Database documentation library.
See Also:
Oracle Database Advanced Security Administrator's GuideThe following instructions provide an example of how you can confirm that Oracle Advanced Security is enabled for your Management Repository database and its connections with the Management Service:
Locate the sqlnet.ora configuration file in the following directory of the database Oracle Home:
ORACLE_HOME/network/admin
Using a text editor, look for the following entries (or similar entries) in the sqlnet.ora file:
SQLNET.ENCRYPTION_SERVER = REQUESTED SQLNET.CRYPTO_SEED = "abcdefg123456789"
See Also:
"Configuring Network Data Encryption and Integrity for Oracle Servers and Clients in the Oracle Application Server 10g Administrator's Guide.Save your changes and exit the text editor.
After you have enabled Oracle Advanced Security for the Management Repository, you must also enable Advanced Security for the Management Agent that is monitoring the Management Repository:
Locate the sqlnet.ora configuration file in the following directory inside the home directory for the Management Agent that is monitoring the Management Repository:
AGENT_HOME/network/admin (UNIX) AGENT_HOME\network\admin (Windows)
Using a text editor, add the following entry to the sqlnet.ora configuration file:
SQLNET.CRYPTO_SEED = "abcdefg123456789"
The SQLNET.CRYPTO_SEED can be any string between 10 to 70 characters.
See Also:
"Configuring Network Data Encryption and Integrity for Oracle Servers and Clients in the Oracle Application Server Administrator's Guide.Save your changes and exit the text editor.
Restart the Management Agent.
You can configure third party certificates for:
HTTPS Upload Virtual Host
HTTPS Console Virtual Host
Note:
Only Single Sign-On wallets are supported.You can configure the third party certificate for the HTTPS Upload Virtual Host in two ways:
Method I
Create a wallet for each OMS in the Cloud.
While creating the wallet, specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Load Balancer for Common Name.
Write the certificates of all the Certificate Authorities in the certificate chain (like the Root Certificate Authority, Intermediate Certificate Authority) into a file named trusted_certs.txt.
Download or copy the trusted_certs.txt file to the host machines on which each Agent that is communicating with the OMS is running.
Run the add_trust_cert command on each Agent and then restart that Agent.
emctl secure add_trust_cert -trust_certs_loc <location of the trusted_certs.txt file>
Secure the OMS and restart it.
emctl secure oms -wallet <location of wallet> -trust_certs_loc <loc of trusted_certs.txt> [any other options]
Method 2
Create a wallet for each OMS in the Cloud.
Specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Server Load Balancer for Common Name (CN).
Write the certificates of all the Certificate Authorities in the certificate chain (like the Root Certificate Authority, Intermediate Certificate Authority) into a file named trusted_certs.txt.
Restart the OMS after it has been secured.
emctl secure oms -wallet <location of wallet> -trust_certs_loc <loc of trusted_certs.txt> [any other options]
Either re-secure the Agent by running the emctl secure agent command (should be run on all Agents) or import the trust points by running the emctl secure add_trust_cert -trust_certs_loc <location of the trusted_certs.txt file> command. The -trust_certs_loc parameter must contain the path and the filename of the trusted_certs.txt file.
Note:
This file must only contain certificates in base64 format and no special characters or empty lines.To configure the third party certificate for HTTPS WebTier Virtual Host:
Create a wallet for each OMS in the Cloud. Specify the host name of the machine where the OMS is installed or the Load Balancer Name if the OMS is behind the Server Load Balancer for Common Name.
Run the following command on each OMS and the restart that OMS:
emctl secure console -wallet <location of wallet>
Note:
Only single-sign-on wallets are supported.The following topics are discussed in this section:
Credential Subsystem
Pluggable Authentication Modules (PAM) Support
Sudo and Powerbroker Support
Credentials like user names and passwords are typically required to access targets such as databases, application servers, and hosts. Credentials are encrypted and stored in Enterprise Manager. Beginning with Enterprise Manager 12c, the credential subsystem supports, in addition to basic username-password, strong authentication schemes such as PKI, SSH-keys and Kerberos. SSH-key based host authentication, used by jobs, deployment procedures and other Enterprise Manger subsystems, is now supported.
By using appropriate credentials, you can:
Collect metrics in the background as well as real-time
Perform jobs such as backup, patching, and cloning
Perform real-time target administration such as start, and stop
Connect to My Oracle Support
Based on their usage, credentials can be classified into the following categories:
Credentials are stored within Enterprise Manager as "named" entities. Administrators define and store credentials within Enterprise Manager and refer to the credential by a credential name. Named credentials can be a username/password, or a public key-private key pair. An Enterprise Manager administrator can then use the named credential for performing operations like running jobs, patching and other system management tasks. For example, an administrator can store the username and password they want to use for patching as "MyPatchingCreds". He can later submit a patching job that uses "MyPatchingCreds" to patch a production databases.
There are two categories of named credentials:
Global Named Credential
A global named credential is an entity, which is not associated with any Enterprise Manager object. Global named credentials consist of the authentication scheme along with any authentication parameters. Because these are independent entities, an Enterprise Manger administrator can associate these credentials with objects at a later time.
Target Named Credentials
Target named credential is an entity which are associated with individual targets at the time of creation. This entity will also contain authentication scheme along with authentication parameters for a specific target.
Access Control for Named Credentials
The access control model for credentials adhere to the following rules:
Only credential owners can grant privileges on their credential objects to other users.
Enterprise Manager Super Administrators cannot obtain any privileges on a newly created credential until he is explicitly granted privileges on the credential object.
Enterprise Manager administrators, regardless of privilege level, cannot see the sensitive fields such as passwords and private keys from the console UI.
Credentials privileges cannot be assigned to a role. This eliminates back door entry by Enterprise Manager Super Administrators to grant themselves privileges on the credentials for which they do not have explicit access.
An Enterprise Manager administrator cannot view other administrators' credentials unless an explicit grant is provided. Even Enterprise Manager Super Administrators cannot view other users' credentials.
Any Enterprise Manager administrator can create his own credentials and have FULL privileges on the credentials owned.
Enterprise Manager Administrators will be able to grant privileges to other administrators while creating the credential or by granting the privileges when editing the credential.
All the credentials owned by an Enterprise Manager administrator will be deleted if that administrator is deleted from Enterprise Manager. Since access to shared credentials is not automatically granted to Super Administrators, re-assigning named credentials belonging to a regular Enterprise Manager administrator by a Super Administrator is not allowed.
Credential Privilege Levels
The following privilege levels are available for all credentials:
VIEW: An administrator with VIEW privileges on other administrator's credentials will be able to view the structure and username of the credential. Sensitive information of the credential such as the password will never be shown. Administrators with VIEW privilege on a credential will also be able to use the credentials for running jobs, patching and other system management operations within Enterprise Manager.
EDIT: Allows an Enterprise Manager administrator to change a sensitive information such as the password, or the public/private key pair of the credential. The administrator will not be able to change the Authentication Scheme of the credential. The username for the credential cannot be changed.
FULL: Allows an Enterprise Manager administrator to change the credential username, sensitive information such as the password or the public/private key pair, and authentication scheme. An administrator with FULL privilege on a named credential will be able to delete the named credential.
To create or edit a named credential, from the Setup menu, choose Security and then Named Credential. The Named Credential page displays as shown in the following figure.
From the Named Credential page, you can Create a new named credential, Edit an existing credential, Manage Access (grant/revoke privileges), Delete, Test, View References, or click the Query by Example icon to filter the list of named credentials.
The job system uses the credential subsystem to retrieve the credentials required to submit a job on the targets. The administrator can define their preferred and default credentials from the Setup menu, choose Security and then Preferred Credentials page. As an administrator, you can:
1. Use Preferred Credentials
2. Use Named Credentials
3. Create new credentials
while submitting the job.
Note:
If the user chooses to use preferred credentials, these credentials will be used when the user submits the job. If the preferred credentials are not available, the default credentials will be used. If default credentials are not present, the job cannot be submitted.These credentials are used by the Management Agent to monitor certain types of targets. For example, most database monitoring involves connecting to the database, which requires a username, password, and optionally, a role. Monitoring credentials, if stored in the repository, can also be potentially used by management applications to connect directly to the target from the OMS.
To create or edit a monitoring credentials, from the Setup menu, choose Security and then Monitoring Credentials. The Monitoring Credentials page displays as shown in the following figure.
To modify monitoring credentials, select the desired target type and click Manage Monitoring Credentials. The monitoring credentials page for the selected target type displays.
These credentials are associated with metric extensions and older user-defined metrics.
Preferred credentials are used to simplify access to managed targets by storing target login credentials in the Management Repository. With preferred credentials set, users can access an Enterprise Manager target that recognizes those credentials without being prompted to log into the target. Preferred credentials are set on a per user basis, thus ensuring the security of the managed enterprise environment.
Default Credentials: Default credentials can be set for a particular target type and will be available for all the targets of the target type. It will be overridden by target preferred credentials.
Target Credentials: Target credentials are preferred credentials set for a particular target. They could be used by applications such as the job system, notifications, or patching. For example, if the user chooses to use preferred credentials while submitting a job, then the preferred credentials set for the target (target credentials) will be used. If the target credentials are not present, the default credentials (for the target type) will be used. If the default credentials are not present, the job will fail. If not specified, by default, preferred credentials refer to preferred target credentials"
For example, to set the host preferred credentials, from the Setup menu, choose Security and then Preferred Credential. In the Preferred Credentials page, select the Host target type from the table and click Manage Preferred Credentials. The Host Preferred Credentials are displayed.
On this page, you can set both default and explicit preferred credentials for the host target types.
You can manage passwords using EM CLI verbs. Using EM CLI, you can:
Change the database user password in both the target database and Enterprise Manager.
emcli update_db_password -change_at_target=Yes|No -change_all_reference=Yes|No
Update a password which has already been changed at the host target.
emcli update_host_password -change_all_reference=Yes|No
Set preferred credentials for given users.
emcli set_preferred_credential -set_name="set_name" -target_name="target_name" -target_type="ttype" -credential_name="cred_name" [-credential_owner ="owner]"
And
emcli set_preferred_credential -set_name="set_name" -target_name="target_name" -target_type="ttype" -credential_name="cred_name" [-credential_owner ="owner]"
For detailed descriptions of these verbs, refer to Enterprise Manager Command Line Interface guide.
Secure Shell or SSH allows data to be exchanged over the network using a secure channel between two devices. SSH is used primarily on Linux and Unix based systems. SSH was designed as a replacement for FTP, telnet and other unsecure remote shells, which send information, notably passwords in plaintext, leaving them open for interception. The encryption used by SSH provides confidentiality and integrity of data over an insecure network. SSH also protects the system against DNS spoofing attacks. This makes SSH a better choice in production environments over telnet/FTP and other username/password based authentications.
You can configure Enterprise Manager to use SSH while performing management operations, thus allowing Enterprise Manager administrators to leverage the security features provided by SSH along with the management capabilities of Enterprise Manager. When authenticating in this mode, the Agent acts as a Java SSH client and connect to the host using the username/password provided in the credential.
Enterprise Manager allows you to store a public-private key pair for administrators and allows them to view and install the public key on the hosts. Administrators can then submit jobs/patching operations in which they specify the credential that refers to the private key to perform the operation. The OMS passes the private key to the Agent along with the commands and the command parameters. Agent invokes the Java SSH client and attempts to connect to the host using the private key. Since the host already has the public key installed, it identifies the private key and successfully authenticates the Agent's Java SSH client. The Agent can now run the commands via the SSH client on the host to perform the requested operations.
Setup Example Session
Note:
The procedure shown in this example assumes that you have a firm understanding of SSH setup procedures and user and host equivalence using public private key pair using SSH.To generate, manage, or convert SSH authentication keys, you use the SSH-keygen utility available on UNIX systems. This utility SSH-keygen tool provides different options to create with different strengths RSA keys for SSH protocol version 1 and RSA or DSA keys for use by SSH protocol version 2.
Example 10-10 Setting Up SSH key-based Authentication
$ ssh-keygen -t rsa
The command options instruct the utility to generate SSH keys (RSA key pair).
Generating public/private rsa key pair. Enter file in which to save the key (/home/myhome/.ssh/id_rsa):
The path specified is the standard path to the location where SSH keys are stored ($HOME/.ssh).
Enter passphrase (empty for no passphrase) Enter same passphrase again: Your identification has been saved in /home/admin1/.ssh/id_rsa. Your public key has been saved in /home/admin1/.ssh/id_rsa.pub. The key fingerprint is: bb:da:59:7a:fc:24:c6:9a:ee:dd:af:da:1b:1b:ed:7f admin1@myhost2170474
The ssh-regkey utility has now generated two files in the .ssh directory.
$ ls id_rsa id_rsa.pub
To permit access to the host without having SSH prompt for a password, copy the public key to the authorized_keys file on that system.
$ cp id_rsa.pub authorized_keys
From this point, all keys listed in that file are allowed access.
Next, perform a remote login using SSH. The system will not prompt you for a password.
$ ssh myhost The authenticity of host 'myhost (10.229.147.184)' can't be established. RSA key fingerprint is de:a0:2a:d5:23:f0:8a:72:98:74:2c:6f:bf:ad:5b:2b. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'myhost,10.229.147.184' (RSA) to the list of known hosts. Last login: Mon Aug 29 16:48:45 2011 from anotherhost.example.com $
You are now ready to add the credential to Enterprise Manager.
From the Setup menu, select Security, then select Named Credentials.
On the Named Credentials page, click Create.
Select Host from the Authenticating Target Type drop-down menu.
Select SSH Key Credentials from the Credential Type drop-down menu as shown in the following figure.
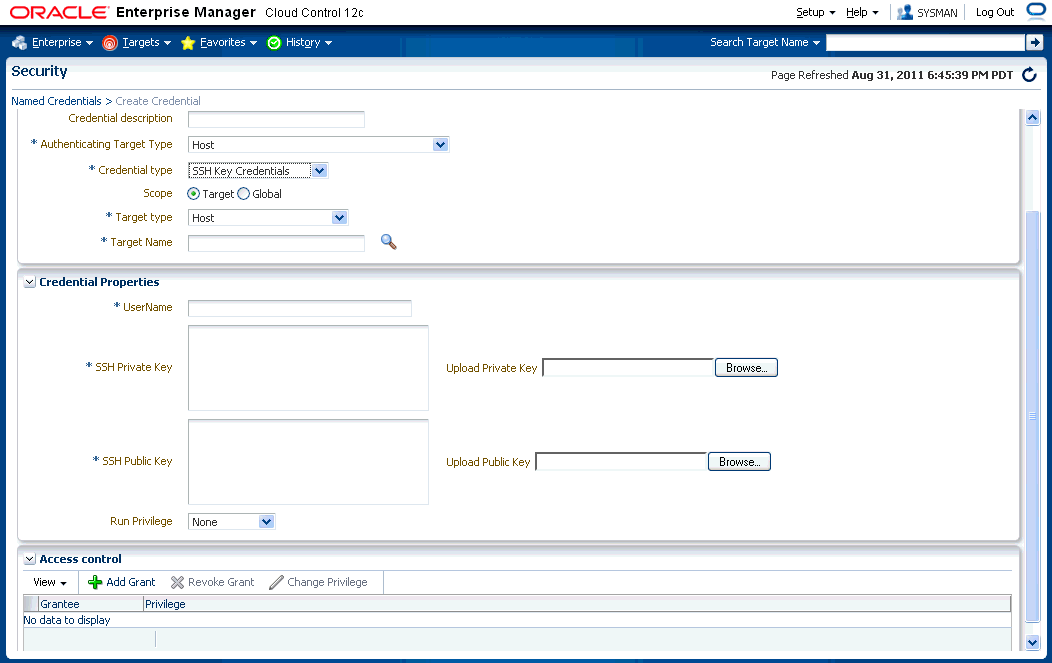
Ensure that the SSH private key/public key files have been copied to the host on which the browser is running.
From the Credential Properties region, click Browse for Public Key and Private Key to upload the generated public key/private key files.
Click Test and Save to verify the credentials and save them.
Pluggable authentication modules, or PAM, is a mechanism to integrate multiple low-level authentication schemes into a high-level application programming interface (API). It allows programs that rely on authentication to be written independently of the underlying authentication scheme. By using PAM, instead of using the local password file to authenticate the user accessing the host, you can take advantage of other authentication mechanisms such as LDAP, RADIUS and Kerberors. If your host authentication is configured over PAM, the Management Agent needs to be configured accordingly to enable PAM Authentication. Refer to note 422073.1 for deployment details.
Note:
The local password file (usually/etc/passwd) will be checked and used first. This should be synchronized with the LDAP password if it is being used. If this fails, the Management Agent will switch to the external authentication module.For users on RHEL4, the PAM file configuration is as follows:
#%PAM-1.0 auth required pam_ldap.so account required pam_ldap.so password required pam_ldap.so session required pam_ldap.so
For more details, see https://www.redhat.com/docs/manuals/enterprise/RHEL-4-Manual/ref-guide/s1-pam-format.html
For AIX users, use the edit/etc/pam.conf file and add the following lines:
emagent auth required /usr/lib/security/pam_aix emagent account required /usr/lib/security/pam_aix emagent password required /usr/lib/security/pam_aix emagent session required /usr/lib/security/pam_aix
After editing the file, apply patch 5527130 and run root.sh
Privilege delegation allows a logged-in user to perform an activity with the privileges of another user. Sudo and PowerBroker are privilege delegation tools that allow a logged-in user to be assigned these privileges. Typically, the privileges that are granted to a specific user are administered centrally. For example, the sudo command can be used to run a script that requires root access:
sudo root root.sh
In the invocation of sudo in the example above, an administrator can use the sudo command to run a script as root provided he has been granted the appropriate privileges by the system administrator. Enterprise Manager preferred credentials allow you to use two types of privilege delegation tools: Sudo and PowerBroker. You can use EM CLI or the Manage Privilege Delegation Settings page to set/edit privilege delegation settings for a host. See the Enterprise Manager Command Line Interface guide for more information on using the command line.
Sudo: sudo allows a permitted user to execute a command as the super user or another user, as specified in the sudoers file. If the invoking user is root or if the target user is the same as the invoking user, no password is required. Otherwise, sudo requires that users authenticate themselves with a password by default. Once a user has been authenticated, a timestamp is updated and the user may then use sudo without a password for a short period of time (5 minutes unless overridden in sudoers). sudo determines who is an authorized user by consulting the file /etc/sudoers file. For more information, see the manual page on sudo (man sudo) on Unix. Enterprise Manager authenticates the user using sudo, and executes the script as sudo. For example, if the command to be executed is foo -arg1 -arg2, it will be executed as sudo -S foo -arg1 -arg2.
PowerBroker: BeyondTrust Powerbroker enables UNIX system administrators to specify the circumstances under which other people may run certain programs such as root (or other important accounts). The result is that responsibility for such actions as adding user accounts, fixing line printer queues, and so on, can be safely assigned to the appropriate people, without disclosing the root password. The full power of root is thus protected from potential misuse or abuse-for example, modifying databases or file permissions, erasing disks, or more subtle damage. BeyondTrust PowerBroker can access existing programs as well as its own set of utilities that execute common system administration tasks. Utilities being developed to run on top of BeyondTrust PowerBroker can manage passwords, accounts, backups, line printers, file ownership or removal, rebooting, logging people out, killing their programs, deciding who can log in to where from where, and so on. They can also provide TCP/IP, Load Balancer, cron, NIS, NFS, FTP, rlogin, and accounting subsystem management. Users can work from within a restricted shell or editor to access certain programs or files as root. See your Sudo or PowerBroker documentation for detailed setup and configuration information.
Enterprise Manager allows you to create privilege delegation settings either by creating the setting directly on a host target, or by creating a Privilege Delegation Setting Template that you can apply to multiple hosts.
To create a privilege delegation setting directly on a host:
From the Setup menu, select Security, then select Privilege Delegation. The following screen is displayed:
For any host target appearing in the table, click Edit. Enterprise Manager takes you to the Host Privilege Delegation Setting page.
Select a privilege delegation type (Sudo or PowerBroker).
Enter the privilege delegation command to be used and, in the case of PowerBroker, the optional Password Prompt.
Click Update to apply the settings to the host. The following figure shows the Host Privilege Delegation Setting window that you can use to create a PowerBroker setting.
Once you have created a privilege delegation setting, you must apply this setting to selected targets. This setting can be applied to one more hosts or to a composite (Group) target (the group must contain at least one host target). You can apply a Privilege Delegation setting using the Cloud Control console. From the Setup menu, choose Security and then Privilege Delegation.
To protect the integrity of sensitive data in Enterprise Manager, a signing on verification method known as the emkey is used. Encryption key is the master key that is used to encrypt/decrypt sensitive data, such as passwords and preferred credentials that are stored in the Repository. The key is originally in stored in repository. It is removed from repository and copied to the Credential Store during installation of the first OMS. (the emkey is secured out-of-the-box). A backup is created in OMS_ORACLE_HOME/sysman/config/emkey.ora. It is recommended to create a backup of this file on some other machine. When starting up, OMS reads the emkey from Credential Store and repository. If the emkey is not found or is corrupted, it fails to start. By storing the key separately from Enterprise Manager schema, we ensure that the sensitive data such as Named Credentials in the Repository remain inaccessible to the schema owner and other SYSDBA users (Privileged users who can perform maintenance tasks on the database) in the Repository. Moreover, keeping the key from the schema will ensure that sensitive data remain inaccessible while Repository backups are accessed. Further, the schema owner should not have access to the OMS/Repository Oracle homes.
The emkey is an encryption key that is used to encrypt and decrypt sensitive data in Enterprise Manager such as host passwords, database passwords and others.
WARNING:
If the emkey.ora file is lost or corrupted, all of the encrypted data in the Management Repository becomes unusable. Maintain a backup copy of this file on another system.
During startup, the Oracle Management Service checks the status of the emkey. If the emkey has been properly configured, it uses it encrypting and decrypting data. If the emkey has not been configured properly, the following error message is displayed.
Example 10-11 emctl start oms Command
Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. emctl start omsStarting HTTP Server ...Starting Oracle Management Server ...Checking Oracle Management Server Status ...Oracle Management Server is not functioning because of the following reason:The Enterprise Manager Key is not configured properly. Run "emctl status emkey" for more details.
The emctl commands related to emkey are given below:
emctl status emkey [-sysman_pwd <pwd>]
emctl config emkey -copy_to_credstore [-sysman_pwd <pwd>]
emctl config emkey -copy_to_repos [-sysman_pwd <pwd>]
emctl config emkey -remove_from_repos [-sysman_pwd <pwd>]
emctl config emkey -copy_to_file_from_credstore -admin_host <host> -admin_port <port> -admin_user <username> [-admin_pwd <pwd>] [-repos_pwd <pwd>] -emkey_file <emkey file>
emctl config emkey -copy_to_file_from_repos (-repos_host <host> -repos_port <port> -repos_sid <sid> | -repos_conndesc <conn desc>) -repos_user <username> [-repos_pwd <pwd>] [-admin_pwd <pwd>] -emkey_file <emkey file>
emctl config emkey -copy_to_credstore_from_file -admin_host <host> -admin_port <port> -admin_user <username> [-admin_pwd <pwd>] [-repos_pwd <pwd>] -emkey_file <emkey file>
emctl config emkey -copy_to_repos_from_file (-repos_host <host> -repos_port <port> -repos_sid <sid> | -repos_conndesc <conn desc>) -repos_user <username> [-repos_pwd <pwd>] [-admin_pwd <pwd>] -emkey_file <emkey file>
This command shows the health or status of the emkey. Depending on the status of the emkey, the following messages are displayed:
When the emkey has been correctly configured in the Credential Store, the following message is displayed.
When the emkey has been correctly configured in the Credential Store and has been removed from the Management Repository, the following message is displayed.
When the emkey is corrupted in the Credential Store and removed from the Management Repository, the following message is displayed.
Example 10-14 emctl status emkey - Example 3
Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey is not configured properly or is corrupted in the credential store and does not exist in the Management Repository. To correct the problem:1) Get the backed up emkey.ora file. 2) Configure the emkey by running "emctl config emkey -copy_to_credstore_from_file"
This command copies the emkey from the Management Repository to the Credential Store.
Example 10-15 Sample Output of the emctl config emkey -copy_to_credstore Command
emctl config emkey -copy_to_credstore [-sysman_pwd <pwd>] Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey has been copied to the Credential Store.
This command copies the emkey from the Credential Store to Management Repository.
Example 10-16 Sample Output of the emctl config emkey -copy_to_repos Command
emctl config emkey -copy_to_repos [-sysman_pwd <pwd>]Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved.The EMKey has been copied to the Management Repository. This operation will cause the EMKey to become unsecure.After the required operation has been completed, secure the EMKey by running "emctl config emkey -remove_from_repos".
This command copies the emkey from the Credential Store to a specified file.
Example 10-17 Sample Output of the emctl config emkey -copy_to_file_from_credstore Command
emctl config emkey -copy_to_file_from_credstore -admin_host <host> -admin_port <port> -admin_user <username> [-admin_pwd <pwd>] [-repos_pwd <pwd>] -emkey_file <emkey file> Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey has been copied to file.
This command copies the emkey from the Management Repository to a specified file.
Example 10-18 Sample Output of the emctl config emkey -copy_to_file_from_repos Command
emctl config emkey -copy_to_file_from_repos (-repos_host <host> -repos_port <port> -repos_sid <sid> | -repos_conndesc <conn desc>) -repos_user <username> [-repos_pwd <pwd>] [-admin_pwd <pwd>] -emkey_file <emkey file>Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved.The EMKey has been copied to file.
This command copies the emkey from a specified file to the Credential Store.
Example 10-19 Sample Output of the emctl config emkey -copy_to_credstore_from_file Command
emctl config emkey -copy_to_credstore_from_file -admin_host <host> -admin_port <port> -admin_user <username> [-admin_pwd <pwd>] [-repos_pwd <pwd>] -emkey_file <emkey file> Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey has been copied to the Credential Store.
This command copies the emkey from a specified file to the repository.
Example 10-20 Sample Output of the emctl config emkey -copy_to_repos_from_file Command
emctl config emkey -copy_to_repos_from_file (-repos_host <host> -repos_port <port> -repos_sid <sid> | -repos_conndesc <conn desc>) -repos_user <username> [-repos_pwd <pwd>] [-admin_pwd <pwd>] -emkey_file <emkey file> Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey has been copied to the Management Repository. This operation will cause the EMKey to become unsecure. After the required operation has been completed, secure the EMKey by running "emctl config emkey -remove_from_repos".
This command removes the emkey from the repository.
Example 10-21 Sample Output of emctl config emkey -remove_from_repos Command
emctl config emkey -remove_from_repos [-sysman_pwd <pwd>] Oracle Enterprise Manager 12c Release 1 Cloud Control Copyright (c) 1996, 2011 Oracle Corporation. All rights reserved. The EMKey has been removed from the Management Repository.
Note:
If the emkey is corrupted in the Credential Store, you will not be able to remove it from the Management Repository.This section explains the install and upgrade scenarios for emkey.
A new emkey is generated as a strong random number when the Management Repository is installed.
When the Oracle Management Service is installed, the Installer copies the emkey to Credential Store and removes it from repository (emkey is secured out-of-box).
The Management Repository is upgraded as usual. When upgrading the OMS, the omsca (OMS Configuration Assistant) copies the emkey to Credential Store and removes from repository. If the emkey is already secured before upgrade or has been removed from repository, then omsca reads the emkey from emkey.ora file present in old OMS Oracle Home and copies it to Credential Store.
Note:
After all the Oracle Management Service have been upgraded, you can secure the emkey, that is, remove it from the Management Repository by running the following command:emctl config emkey -remove_from_repos
When the Management Repository is recreated, a new emkey is generated. This new key will not be in synchronization with the existing emkey in the Credential Store.
Copy the new emkey to Credential Store by using the emctl config emkey -copy_to_credstore command.
Take a backup by entering the emctl config emkey -copy_to_file_from_repos command or the emctl config emkey -copy_to_file_from_credstore command.
Secure the emkey by using the emctl config emkey -remove_from_repos command.
All operations performed by Enterprise Manager users such as creating users, granting privileges, starting a remote job like patching or cloning, need to be audited to ensure compliance with the Sarbanes-Oxley Act of 2002 (SAS 70). This act defines standards an auditor must use to assess the contracted internal controls of a service organization. Auditing an operation enables an administrator to monitor, detect, and investigate problems and enforce enterprise wide security policies.
Irrespective of how the user has logged into Enterprise Manager, when auditing is enabled, each user action is audited and the audit details are stored in a record.
For Enterprise Manager 12c, BASIC auditing is enabled by default, thus creating an audit trail of credentials being created, edited, accessed, associated and deleted. Named credentials are first-class security objects on which privileges can be granted or revoked privileges. This means that multiple Enterprise Manager administrators will be able to use and modify the credential objects. Because credentials are sensitive data that can be used to perform various operations on the systems, there is a need to audit the operations on credentials.
Enterprise Manger audits all the operations performed on credentials. The auditing information includes, but is not be limited to, the current username, credential name, operation performed, operation status success or failure. The audit logs contain information about the credential owner, action initiator, credential name, user name, and target name, job names along with the date time of the operation. Credential fields like password, private keys are never logged.
The following operations are audited:
Creating a Named Credential: Creating new Enterprise Manager credentials will be audited.
Editing a Named Credential: Editing a credential may consist of changing the username and/or the sensitive credential attributes. Credential edits may also include changing the authentication scheme for the credential.
Delete a Named Credential: Deleting a credential from Enterprise Manager will be audited.
Associating a Named Credential: A named credential can be set as a preferred credential for a credential set at the target level or at target type level. The named credential can also be reference directly from a job. All operations involving the setting of the named credentials as preferred credentials and using it in a job or deployment procedure will be audited.
Accessing a Named Credential: Enterprise Manager subsystems request credentials from the credential store to perform various system management tasks
You can configure the Enterprise Manager Audit System by using the following EM CLI commands:
enable_audit: Enables auditing for all user operations.
disable_audit: Disables auditing for all user operations.
show_operations_list: Shows a list of the user operations being audited.
show_audit_settings: Shows the audit status, operation list, externalization service details, and purge period details.
Audit data needs to be protected and maintained for several years. The volume of audit data may become very large and impact the performance of the system. To limit the amount of data stored in the repository, the audit data must be externalized or archived at regular intervals. The archived audit data is stored in an XML file complying with the ODL format. To externalize the audit data, the EM_AUDIT_EXTERNALIZATION API is used. Records of the format <file-prefix>.NNNNN.xml, where NNNN is a number are generated. The numbers start with 00001 and continue to 99999.
You can set up the audit externalization service for exporting audit data into the file system by using the update_audit_setting -externalization_switch command.
The update_audit_settings command updates the current audit settings in the repository and restarts the Management Service.
Example 10-22 Usage of the update_audit_setting command
emcli update_audit_settings
-audit_switch="ENABLE/DISABLE"
-operations_to_enable="name of the operations to enable, for all oprtations
use ALL"
-operations_to_disable="name of the operations to disable, for all
oprtations use ALL"
-externalization_switch="ENABLE/DISABLE"
-directory_name="directory_name (DB Directory)"
-file_prefix="file_prefix"
-file_size="file_size (Bytes)"
-data_retention_period="data_retention_period (Days)"
-audit_switch: Enables auditing across Enterprise Manager. The possible values are ENABLE/DISABLE. Default value is DISABLE.
-operations_to_disable: Enables auditing for specified operations. Enter All to enable all operations.
-operations_to_disable: Disables auditing for specified operations. Enter All to disable all operations.
-externalization_switch: Enables the audit data export service. The possible values are ENABLE/DISABLE. Default value is DISABLE.
-directory: The database directory that is mapped to the OS directory where the export service archives the audit data files.
-file_prefix: The file prefix to be used by the export service to create the file in which audit data is to be stored.
-file_size: The size of the file on which the audit data is to be stored. The default value is 5000000 bytes.
data_retention_period: The period for which the audit data is to be retained inside the repository. The default value is 365 days.
You can search for audit data that has been generated over a specified period. You can also search for the following:
Audit details of a specific user operation or all user operations.
Audit details of operations with a Success or Failure status or All operations.
From the Setup menu, select Management Services and Repository. The Overview page is displayed. Click the Audit Data link under the Audit section. The Audit Data page is displayed. Specify the search criteria in the fields and click Go. The results are displayed in the Summary table.
To view the details of each record that meets the search criteria, select Detailed in the View drop-down list. To drill down to the full record details, click on the Timestamp. The Audit Record page is displayed.
| Field Name | Description |
|---|---|
| General | |
| Operation Timestamp | The date and time on which the operation took place. |
| Administrator | The id of the administrator who has logged into Enterprise Manager. |
| Operation | The type of operation being audited. |
| Status | The status of the operation which can be success or failure. |
| Message | A descriptive message indicating the status of the operation. |
| Normalized Timestamp | This is the UTC timestamp. |
| Client Information | |
| Session | This can either be the HTTP Session ID or the DBMS Session ID. |
| IP Address | The IP address of the client's host machine. |
| Hostname | The name of the client's host machine. |
| Upstream Component Type | The type of client, Console, Web Service, EM CLI, being used. |
| Authentication Type | The nature of the session (HTTP Session, DB Session). |
| Upstream Component Name | The name of the client being used. |
| OMS Information | |
| Hostname | The host name of the Oracle Management Service. |
| IP Address | The IP address of the Oracle Management Service. |
| Instance ID | The Instance ID of the Oracle Management Service. |
| Operation Specific Information | |
| Object Name | The operation being performed on an object |
The following table lists the names of operation and their description.
Table 10-5 List of Operations Audited
| Operation Name | Description |
|---|---|
|
TCAUD_ADD_TEMPLATE_ENTITY |
Add entity to Template Collection |
|
ADD_AGENT_REGISTRATION_PASSWORD |
Add Registration Password |
|
SWLIBADDLOCATION |
Configuring a new storage location in Software Library |
|
ADD_CS_TARGET_ASSOC |
Add Standard-Target Association |
|
APPLY_TEMPLATE |
APPLY_TEMPLATE |
|
APPLY_UPDATE |
Apply the update |
|
TCAUD_ASSOC_TO_AG |
Associate Template Collection to AG |
|
ATTACH_MEXT |
Attach Metric Extension |
|
AUDIT_EXPORT_SETTINGS |
Audit Export Settings to externalize audit data |
|
AUDIT_SETTINGS |
Audit Settings to enable or Disable auditing |
|
CHANGE_CONNECTOR_SETTINGS |
enable/disable a Connector |
|
CHANGE_PASSWORD |
Change Password |
|
CHANGE_PREFERRED_CREDENTIAL |
change_pref_cred |
|
CONFIG_CONNECTOR |
Configure a Connector Instance |
|
CREATE_CHANGE_MANAGEMENT_SETTING |
Create the change management settings for the Real-time Monitoring rule. |
|
CREATE_CONNECTOR |
Create a Connector Instance |
|
CCS_CREATE_MD |
Create (or import) Custom Configuration Specification |
|
CCS_CREATE_PARSER |
Create Custom Configuration Specification Parser |
|
CCS_CREATE_CUSTOM_TARGET_TYPE |
Create Custom Target Type |
|
CREATE_FACET |
Create a new facet. |
|
CREATE_FACET_PARAMETER |
Create a new facet parameter. |
|
CREATE_FACET_PATTERN |
Create a new facet pattern. |
|
CREATE_CSG |
Create Framework |
|
CREATE_MEXT |
Create Metric Extension |
|
CREATE_TEMPLATE |
CREATE_TEMPLATE |
|
CREATE_NAMED_CREDENTIAL |
Create Named Credential |
|
CREATE_PG_SCHED |
Create Policy Group Schedule |
|
CREATE_CCC_RULE |
Create a Real-time Monitoring rule. |
|
RES_STATE_CREATE_OP |
Resolution State created |
|
CREATE_ROLE |
Create Role |
|
CREATE_RULE |
Create Rule |
|
CREATE_CS |
Create Standard |
|
TCAUD_CREATE |
Create Template Collection |
|
CREATE_USER |
Create User |
|
CREATE_UDP |
Create User Defined Policy |
|
CREATE_UDPG |
Create User Defined Policy Group |
|
DB_LOGIN |
Audit Database user Login |
|
DB_LOGOUT |
Audit Database user Logout |
|
DELETE_CONNECTOR |
Delete a Connector Instance |
|
CCS_DELETE_MD |
Delete Custom Configuration Specification |
|
CCS_DELETE_PARSER |
Delete Custom Configuration Specification Parser |
|
DELETE_FACET |
Delete a facet. |
|
DELETE_FACET_PARAMETER |
Delete a facet parameter. |
|
DELETE_FACET_PATTERN |
Delete a facet pattern. |
|
DELETE_CSG |
Delete framework |
|
DELETE_JOB |
Delete job. |
|
DELETE_MEXT |
Delete Metric Extension |
|
DELETE_TEMPLATE |
Delete a monitoring template. |
|
DELETE_NAMED_CREDENTIAL |
Delete Named Credential |
|
DELETE_PG_EVAL |
Delete Policy Group Evaluation Results |
|
DELETE_PG_SCHED |
Delete Policy Group Schedule |
|
DELETE_CCC_RULE |
Delete a Real-time Monitoring rule. |
|
DELETE_AGENT_REGISTRATION_PASSWORD |
Delete Registration Password |
|
RES_STATE_DELETE_OP |
Resolution State deleted |
|
DELETE_ROLE |
Drop Role |
|
DELETE_RULE |
Delete Rule |
|
SWLIBDELETEFOLDER |
Deleting a directory in Software Library |
|
SWLIBDELETEENTITY |
Deleting an entity in Software Library |
|
DELETE_CS |
Delete Standard |
|
TCAUD_DELETE |
Delete Template Collection |
|
DELETE_UPDATE |
Delete the update |
|
DELETE_USER |
Delete User |
|
DELETE_UDP |
Delete User Defined Policy |
|
DELETE_UDPG |
Delete User Defined Policy Group |
|
CCS_DEPLOY |
Deploy Custom Configuration Specification |
|
DETACH_MEXT |
Detach Metric Extension |
|
DISABLE_CS_TARGET_ASSOC |
Disable Standard-Target Association |
|
TCAUD_DEASSOC_FROM_AG |
Disassociate Template Collection from AG |
|
DOWNLOAD_UPDATE |
Download an available update |
|
EDIT_CSG |
Edit Framework |
|
EDIT_JOB |
edit_job |
|
EDIT_TEMPLATE |
EDIT_TEMPLATE |
|
EDIT_PG_SCHED |
Edit Policy Group Schedule |
|
EDIT_AGENT_REGISTRATION_PASSWORD |
Edit Registration Password |
|
EDIT_RULE |
Edit Rule |
|
EDIT_CS |
Edit Standard |
|
EDIT_CS_TARGET_ASSOC |
Edit Standard-Target Association |
|
TCAUD_EDIT |
Edit Template Collection |
|
EDIT_UDP |
Edit User Defined Policy |
|
EDIT_UDPG |
Edit User Defined Policy Group |
|
LOGIN |
logon |
|
LOGOUT |
logoff |
|
ENABLE_CS_TARGET_ASSOC |
Enable Standard-Target Association |
|
EVALUATE_UDP |
Evaluate User Defined Policy |
|
PERFORM_OPERATION_AS_AGENT |
Execute any OS Command as the Agent User (uncredentialed) |
|
FILE_TRANSFER |
file_transfer |
|
GET_FILE |
get_file |
|
GET_NAMED_CREDENTIAL |
Get Named Credential |
|
GRANT_JOB_PRIVILEGE |
Grant Job Privilege |
|
GRANT_PRIVILEGE |
Grant Privilege |
|
GRANT_ROLE |
Grant Role |
|
GRANT_SYSTEM_PRIVILEGE |
Grant System Privilege |
|
GRANT_TARGET_PRIVILEGE |
Grant Target Privilege |
|
IMPORT_FACET |
Import a facet. |
|
IMPORT_CSG |
Import Framework |
|
IMPORT_CCC_RULE |
Import a Real-time Monitoring rule. |
|
IMPORT_RULE |
Import Rule |
|
IMPORT_CS |
Import Standard |
|
IMPORT_UDP |
Import User Defined Policy |
|
INCLUDE_ACTION_TO_MONITOR |
Include an action to monitor for the Real-time Monitoring rule. |
|
INCLUDE_FILTER_FACET |
Include a filter facet into the Real-time Monitoring rule. |
|
INCLUDE_MONITORING_FACET |
Include a monitoring facet into the Real-time Monitoring rule. |
|
JOB_OUTPUT |
Job output obtained after job execution |
|
MODIFY_CHANGE_MANAGEMENT_SETTING |
Modify the change management settings for the Real-time Monitoring rule. |
|
MODIFY_FACET |
Update a facet. |
|
MODIFY_FACET_CONTENT |
Update the basic facet information. |
|
MODIFY_FACET_PARAMETER |
Update a facet parameter. |
|
MODIFY_FACET_PATTERN |
Update a facet pattern. |
|
MODIFY_METRIC_SETTINGS |
MODIFY_METRIC_SETTINGS |
|
UPDATE_NAMED_CREDENTIAL |
Modify Named Credential |
|
MODIFY_POLICY_SETTINGS |
Modify Policy Settings |
|
MODIFY_CCC_RULE |
Update a Real-time Monitoring rule. |
|
RES_STATE_MODIFY_OP |
Resolution State modified |
|
MODIFY_ROLE |
Modify Role |
|
MODIFY_USER |
Modify User |
|
SWLIBMOVEENTITY |
Moving all revisions of an entity in Software Library to another directory |
|
PUBLISH_MEXT |
Publish Metric Extension |
|
SWLIBPURGELOCATION |
Purging a storage location in Software Library |
|
PUT_FILE_AS_AGENT |
Put any File to the Agent's Filesystem as the Agent User (uncredentialed) |
|
PUT_FILE |
put_file |
|
REFRESH_UPDATE |
Refresh from EM Store |
|
AGENT_REGISTRATION_PASSWORD_USAGE |
Registration Password Usage |
|
REMOTE_OPERATION_JOB |
remote_op |
|
REMOVE_ACTION_FROM_MONITOR |
Remove an action from monitor for the Real-time Monitoring rule. |
|
REMOVE_CHANGE_MANAGEMENT_SETTING |
Remove the change management settings for the Real-time Monitoring rule. |
|
TCAUD_REMOVE_TEMPLATE_ENTITY |
Remove entity from Template Collection |
|
REMOVE_FILTER_FACET |
Remove a filter facet from the Real-time Monitoring rule. |
|
REMOVE_MONITORING_FACET |
Remove a monitoring facet from the Real-time Monitoring rule. |
|
REMOVE_PRIVILEGE_DELEGATION_SETTING |
Remove Privilege Delegation Setting |
|
SWLIBDELETELOCATION |
Removing a storage location in Software Library |
|
REMOVE_CS_TARGET_ASSOC |
Remove Standard-Target Association |
|
REMOVE_UPDATE |
Remove the update |
|
TCAUD_RENAME |
Rename Template Collection |
|
AGENT_RESYNC |
Agent resynchronization operation |
|
REPOSITORY_RESYNC |
Repository resynchronization operation |
|
RETRY_JOB |
|
|
REVOKE_JOB_PRIVILEGE |
Revoke Job Privilege |
|
REVOKE_PRIVILEGE |
Revoke Privilege |
|
REVOKE_ROLE |
Revoke Role |
|
REVOKE_SYSTEM_PRIVILEGE |
Revoke System Privilege |
|
REVOKE_TARGET_PRIVILEGE |
Revoke Target Privilege |
|
SAVE_MONITORING_SETTINGS |
SAVE_MONITORING_SETTINGS |
|
SET_PRIVILEGE_DELEGATION_SETTING |
Set Privilege Delegation Setting |
|
STOP_JOB |
|
|
SUBMIT_JOB |
submit_job |
|
SUBSCRIBE_UPDATE |
Subscribe to an Update Type |
|
SUSPEND_JOB |
Suspend job |
|
CCS_UNDEPLOY |
Undeploy Custom Configuration Specification |
|
UNSUBSCRIBE_UPDATE |
Unsubscribe an Update Type |
|
CCS_UPDATE_MD |
Update Custom Configuration Specification |
|
UPDATE_DB_PASSWORD |
Update Database Password |
|
INSERT_UPDATE |
Show the update on self update home |
|
UPDATE_MEXT |
Update Metric Extension |
|
UPDATE_PASSWORD |
Update Password |
After you enable security for the Enterprise Manager components and framework, there are additional security considerations. This section provides the following topics:
This section describes the commands used to change the SYSMAN and MGMT_VIEW passwords.
To change the password of the SYSMAN user, you use the following command:
emctl config oms -change_repos_pwd [-old_pwd <old_pwd>] [-new_pwd <new_pwd>] [-use_sys_pwd [-sys_pwd <sys_pwd>]]
| Parameter | Description |
|---|---|
| -change_repos_pwd | . |
-old_pwd |
This is the current SYSMAN password. |
-new_pwd |
This is the new password. |
-use_sys_pwd |
This parameter is optional and is used to connect to the database as a SYS user. Use this option if SYSMAN account on the database has expired/locked. |
-sys_pwd |
This is the password for the SYS user. |
Stop all OMS instances.
emctl stop oms
For each OMS, run the following command:
emctl config oms -change_repos_pwd'
Restart the Administration Server and all OMS instances.
emctl stop oms -all
emctl start oms
To change the password of the MGMT_VIEW user, you use the following command:
emctl config oms -change_view_user_pwd [-sysman_pwd <sysman_pwd>] [-user_pwd <user_pwd>] [-auto_generate]
| Parameter | Description |
|---|---|
-change_view_user_pwd |
Used to change MGMT_VIEW user's password. |
-sysman_pwd |
The password for the SYSMAN user. |
-user_pwd |
The new password for theMGMT_VIEW user.. |
-auto_generate |
If this option is specified, the password is auto generated. |
Important: In order to change the MGMT_VIEW password, you must ensure that the password of the WebLogic administrative user in the credential store matches the actual password of the user SYSMAN. If the credentials do not match, the connection to the Repository Database fails and the SYSMAN password cannot be modified
Stop all OMS instances.
emctl stop oms -all
Execute the following command to update the WebLogic and nodemanager passwords in the Credential store:
cd <OMS_HOME>/bin emctl secure create_admin_creds_wallet -admin_pwd <existing weblogic pwd> -nodemgr_pwd <existing nodemanager pwd>
Log into the Management Repository database as a DBA user and execute the following to manually modify the password of the sysman_mds schema to the new password that will be set for the sysman user:
SQL> alter user sysman_mds identified by <new_pwd of sysman user>;
For ONE of the OMSs, run the following command to modify the SYSMAN password::
cd <OMS_HOME>/bin emctl config oms -change_repos_pwd -change_in_db -old_pwd <new_pwd> -new_pwd <new_pwd>
Restart the AdminServer and all the OMSs.
emctl stop oms -all
emctl start oms
This section describes how to respond to browser-specific security alert dialog boxes when you are using Enterprise Manager in a secure environment.
The security alert dialog boxes described in this section appear because Enterprise Manager Framework Security is enabled, but you have not secured your web tier properly.
This section contains the following topics:
Responding to the Internet Explorer Security Alert Dialog Box
Responding to Mozilla Firefox New Site Certificate Dialog Box
Security is enabled by default for the Management Service. However, if you have not enabled the more extensive security features of your web tier, you will likely receive the following warning: "There is a problem with this Web site's security certificate." This occurs when you first attempt to display the Cloud Control console using the HTTPS URL in Internet Explorer.
When Internet Explorer displays the certificate warning page, use the following instructions to install the certificate and avoid viewing this page again in future Enterprise Manager sessions:
From the certificate warning page, click Continue to this Web site (not recommended).
Internet Explorer displays a Security Warning dialog.
Click Yes. Internet Explorer may display a Security Alert dialog if you have not selected "In the future, do not show this warning." in a previous Internet Explorer session. Click OK to dismiss the dialog.
The Enterprise Manager console login page displays.
At the top of the browser, Click Certificate Error to display the Security Report pop-up.
Click View Certificates. The Certificates dialog appears.
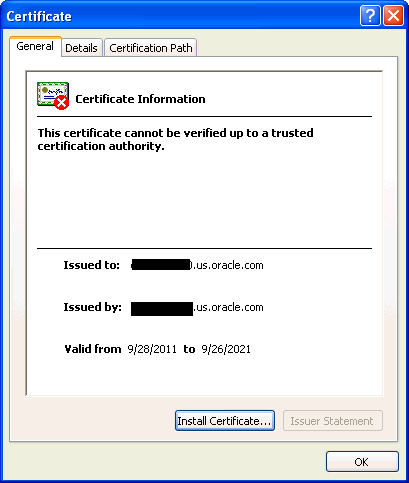
Click the Certificate Path tab and select the first entry in the list of certificates as shown in the following graphic.
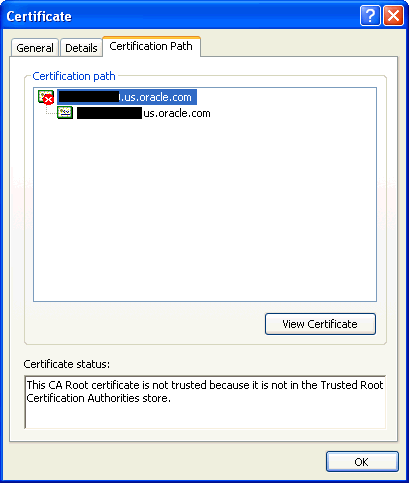
Click View Certificate to display a second Certificate dialog box.
Click Install Certificate to display the Certificate Import wizard.
Accept the default settings in the wizard, click Finish when you are done.
Internet Explorer displays a Security Warning asking if you want to install the certificate. Click Yes. Internet Explorer will display a message stating that the certificate was imported successfully.
Click OK to close each of the security dialog boxes and click Yes on the Security Alert dialog box to continue with your browser session.
You should no longer receive the Security Alert dialog box in any future connections to Enterprise Manager when you use this browser.
Firefox will also issue a connection warning if you have not enabled its more extensive security features. When you first attempt to display the Cloud Control console using the HTTPS URL in Mozilla Firefox, you will recieve a warning because the connection is untrusted.
When Firefox displays the Untrusted Connection page, use the following instructions to install the certificate and avoid viewing this page again in future Enterprise Manager sessions:
Review the instructions and information. Click I Understand the Risks. Firefox displays additional information and the opportunity to add the certificate.
Click Add Exception... . Firefox displays the Add Security Exception dialog.
Ensure that the Permanently store this exception option is selected.
You should no longer receive the New Site Certificate dialog box when using the current browser.
Click Confirm Security Exception. The Enterprise Manager console displays.
You will no longer receive the untrusted connection warning in any future connections to Enterprise Manager when you use this browser
Oracle Beacons provide application performance availability and performance monitoring. They are part of the Application Service Level Management features of Enterprise Manager.
See Also:
"About Application Service Level Management" in the Enterprise Manager Online HelpWhen a Beacon is used to monitor a URL over Secure Sockets Layer (SSL) using an HTTPS URL, the Beacon must be configured to recognize the Certificate Authority that has been used by the Web site where that URL resides.
See Also:
"The Public Key Infrastructure Approach to Security" in the Oracle Security Overview for an overview of Public Key Infrastructure features, such as Certificate AuthoritiesThe Beacon software is preconfigured to recognize most commercial Certificate Authorities that are likely to be used by a secure Internet Web Site. However, you may encounter Web Sites that, although available over HTTPS, do not have a Certificate that has been signed by a commercial Certificate Authority recognized by the Beacon. The following are out-of-box certificates recognized by Beacons:
Class 1 Public Primary Certification Authority by VeriSign, Inc.
Class 2 Public Primary Certification Authority by VeriSign, Inc.
Class 3 Public Primary Certification Authority by VeriSign, Inc.
Secure Server Certification Authority by RSA Data Security, Inc.
GTE CyberTrust Root by GTE Corporation
GTE CyberTrust Global Root by GTE CyberTrust Solutions, Inc.
Entrust.net Secure Server Certification Authority by Entrust.net ((c) 1999
Entrust.net Limited, www.entrust.net/CPS incorp. by ref. (limits liab.))
Entrust.net Certification Authority (2048) by Entrust.net ((c) 1999
Entrust.net Limited, www.entrust.net/CPS_2048 incorp. by ref. (limits liab.))
Entrust.net Secure Server Certification Authority by Entrust.net ((c) 2000
Entrust.net Limited, www.entrust.net/SSL_CPS incorp. by ref. (limits liab.))
In those cases, for example, if you attempt to use the Test section of the Beacon Performance page to test the HTTP Response of the secure URL, the following error appears in the Status Description column of the Response Metrics table on the URL Test Page:
javax.net.ssl.SSLException: SSL handshake failed: X509CertChainIncompleteErr--https://mgmtsys.acme.com/OracleMyPage.Home
See Also:
"Using Beacons to Monitor Remote URL Availability" in the Enterprise Manager online helpTo correct this problem, you can either set the service test "Authenticate SSL Certificates" property to "No"; or add the certificate authority to the list of Certificate Authorities recognized by Beacon.
Setting the Service Test "Authenticate SSL Certifications" Property:
From the Target menu, choose Services.
Select the desired service and click Configure. The Monitoring Configuration tab displays by default.
Click Service Tests and Beacons. The Service Tests and Beacons page displays.
Select the desired service test and click Edit. The Edit Service Test page displays.
In the Transaction region, select the desired service test.
Click on the Advanced Properties tab.
In the Test Parameters region, expand Validation.
For the Authenticate SSL Certificates property, choose No from the drop-down menu.
Configuring the Beacon to Recognize the Certificate Authority:
Obtain the Certificate of the Web Site's Certificate Authority, as follows:
In Microsoft Internet Explorer, connect to the HTTPS URL of the Web Site you are attempting to monitor.
Double-click the lock icon at the bottom of the browser screen, which indicates that you have connected to a secure Web site.
The browser displays the Certificate dialog box, which describes the Certificate used for this Web site. Other browsers offer a similar mechanism to view the Certificate detail of a Web Site.
Click the Certificate Path tab and select the first entry in the list of certificates.
Click View Certificate to display a second Certificate dialog box.
Click the Details tab on the Certificate window.
Click Copy to File to display the Certificate Manager Export wizard.
In the Certificate Manager Export wizard, select Base64 encoded X.509 (.CER) as the format you want to export and save the certificate to a text file with an easily-identifiable name, such as beacon_certificate.cer.
Open the certificate file using a text editor.
The content of the certificate file will look similar to the content shown in .
Update the list of Beacon Certificate Authorities as follows:
Locate the b64InternetCertificate.txt file in the following directory of Agent Home of the Beacon host:
agent_instance_home/sysman/config/
This file contains a list of Base64 Certificates.
Edit the b64InternetCertificate.txt file by appending the certificate text you exported using the Certificate Manager Export wizard to the end of the file.
Add only the certificate and not the peripheral text generated by the wizard. Do not include: "...base64 certificate content...", "-----BEGIN CERTIFICATE-----", or "-----END CERTIFICATE-----".
Restart the Management Agent.
After you restart the Management Agent, the Beacon detects your addition to the list of Certificate Authorities recognized by Beacon and you can successfully monitor the availability and performance of the secure Web site URL.
To patch an Oracle Home used by a user "Oracle" and the user is locked:
Edit the default patching script and prepend sudo or sudo -u or pbrun -u to the default patching step. You need to set a policy (by editing the sudoers file) to allow the user submitting the job (who must be a valid operating system user) to be able to run sudo or pbrun without being prompted for password.
Note:
You cannot patch Oracle Homes without targets. This must be done by using the Patching wizard.The cloning application is wizard-driven. The source of the Oracle Home being cloned may be either an installed Oracle Home or a Software Library. Following are the steps in the cloning process:
If the source is an installed Oracle Home, then, after selecting the Oracle Home, a user will need to specify the Oracle Home credentials. These credentials once specified for an Oracle Home are stored in the repository. The next time a user clones the same Oracle Home, these credentials are automatically populated. Other parameters queried from the user at this point is a temporary location (on the source computer) and the list of files to be excluded from the Oracle Home. If the cloning source is a Software Library, the source Oracle Home credentials will not be queried for.
The user needs to specify the target location and provide the required credentials for each target location. These credentials will be the Oracle Home credentials for each of these target locations. Subsequently, if a user selects any of these cloned Oracle Homes as a source, the Oracle Home credentials are automatically populated.
Depending on the product being cloned, the user can view the Enterprise Manager page where query parameters required for the particular product being cloned are displayed.
The user can, then, view the execution of user-supplied pre-cloning and post-cloning scripts and the root.sh script. The root.sh script will always be run with sudo privileges, but the user has the option to decide if the pre-cloning and post-cloning scripts run with sudo privileges.Finally, the user can schedule the cloning job at a convenient time.
For more information on cloning, refer to the Enterprise Manager Online Help.