| Oracle® Fusion Middleware Administrator's Guide for Oracle Internet Directory 11g Release 1 (11.1.1) Part Number E10029-04 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Administrator's Guide for Oracle Internet Directory 11g Release 1 (11.1.1) Part Number E10029-04 |
|
|
PDF · Mobi · ePub |
This chapter explains how to configure Secure Sockets Layer (SSL) for use with Oracle Internet Directory. If you use Secure Sockets Layer (SSL), you may also configure strong authentication, data integrity, and data privacy.
This chapter contains these topics:
Section 26.1, "Introduction to Configuring Secure Sockets Layer (SSL)"
Section 26.2, "Configuring SSL by Using Fusion Middleware Control"
Section 26.5, "Testing SSL Connections by Using Oracle Directory Services Manager"
Section 26.6, "Testing SSL Connections From the Command Line"
See Also:
Section 3.7, "Security" for a conceptual overview of SSL in relation to Oracle Internet Directory
The SSL Configuration Service chapter in Oracle Fusion Middleware Administrator's Guide.
The SSL Automation Tool chapter in Oracle Fusion Middleware Administrator's Guide. The SSL Automation Tool enables you to configure SSL for multiple components using a domain-specific CA.
Oracle Internet Directory ensures that data has not been modified, deleted, or replayed during transmission by using Secure Sockets Layer (SSL). SSL generates a cryptographically secure message digest—through cryptographic checksums using either the MD5 algorithm or the Secure Hash Algorithm (SHA)—and includes it with each packet sent across the network. SSL provides authentication, encryption, and data integrity using message digest.
This introduction contains the following topics:
Oracle Internet Directory ensures that data is not disclosed during transmission by using public key encryption available with SSL. In public-key encryption, the sender of a message encrypts the message with the public key of the recipient. Upon delivery, the recipient decrypts the message using the recipient's private key.
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network nodes. During an SSL handshake, the two nodes negotiate to determine which cipher suite they will use when transmitting messages back and forth.
Table 26-1 lists the SSL cipher suites supported by Oracle Internet Directory and their corresponding authentication, encryption, and data integrity mechanisms. These are stored in the attribute orclsslciphersuite in the instance-specific configuration entry.
Table 26-1 SSL Cipher Suites Supported in Oracle Internet Directory
| Cipher Suite | Authentication | Encryption | Data Integrity |
|---|---|---|---|
|
SSL_RSA_WITH_3DES_EDE_CBC_SHA |
RSA |
3DES |
SHA |
|
SSL_RSA_WITH_RC4_128_SHA |
RSA |
RC4 |
SHA |
|
SSL_RSA_WITH_RC4_128_MD5 |
RSA |
RC4 |
MD5 |
|
SSL_RSA_WITH_DES_CBC_SHA |
RSA |
DES |
SHA |
|
SSL_RSA_EXPORT_WITH_RC4_40_MD5 |
RSA |
RC4_40 |
MD5 |
|
SSL_RSA_EXPORT_WITH_DES40_CBC_SHA |
RSA |
DES40 |
SHA |
|
SSL_DH_anon_WITH_3DES_EDE_CBC_SHA |
None |
3DES |
SHA |
|
SSL_DH_anon_WITH_RC4_128_MD5 |
None |
RC4 |
MD5 |
|
SSL_DH_anon_WITH_DES_CBC_SHA |
None |
DES |
SHA |
|
SSL_RSA_WITH_AES_128_CBC_SHA |
RSA |
AES |
SHA |
|
SSL_RSA_WITH_AES_256_CBC_SHA |
RSA |
AES |
SHA |
Oracle Internet Directory supports the following TLS/SSL protocols:
SSLv3
TLSv1
SSLv3 with SSLv2 Hello
Oracle Internet Directory does not support SSLv2.
TLSv1 can use all of the cipher suites listed in Table 26-1. SSLv3 and SSLv3 with SSLv2 Hello can use the first 10 cipher suites listed inTable 26-1. They cannot use the AES ciphers.SL_RSA_WITH_AES_128_CBC_SHA or SSL_RSA_WITH_AES_256_CBC_SHA.
The SSL protocol provides transport layer security with authenticity, integrity, and confidentiality, for a connection between a client and server. Three authentication modes are supported, as described in Table 26-2. The SSL authentication mode is controlled by the attribute orclsslauthentication in the instance-specific configuration entry.
Table 26-2 SSL Authentication Modes
| SSL Authentication Method | Value of orclsslauthentication | Authentication Behavior |
|---|---|---|
|
SSL No Authentication Mode, Confidentiality mode |
|
Neither the client nor the server authenticates itself to the other. No certificates are sent or exchanged. Only SSL encryption and decryption is used. |
|
SSL Server Authentication Only Mode |
|
The directory server authenticates itself to the client. The directory server sends the client a certificate asserting the server's identity. |
|
SSL Client and Server Authentication Mode |
|
The client and server authenticate themselves with each other and send certificates to each other. |
By default, Oracle Internet Directory uses SSL No Authentication Mode (orclsslauthentication=1).
When both a client and server authenticate themselves with each other, SSL derives the identity information it requires from the X509v3 digital certificates.
See Also:
Chapter 32, "Managing Authentication".Notes:
By default, the SSL authentication mode is set to authentication mode 1 (encryption only, no authentication). Be sure at least one Oracle Internet Directory server instance has this default authentication mode. Otherwise, you break Oracle Delegated Administration Services and other applications that expect to communicate with Oracle Internet Directory on the encrypted SSL port.
Replication does not work with SSL Server Authentication or SSL Client and Server Authentication.
During start-up of a directory server instance, the directory reads a set of configuration parameters, including the parameters for the SSL profile.
To run a server instance in secure mode, configure a single listening endpoint to communicate using LDAPS. To allow the same instance to run non-secure connections concurrently, configure a second listening endpoint to communicate using LDAP.
During installation of Oracle Internet Directory, Oracle Identity Management 11g Installer follows specific steps in assigning the SSL and non-SSL port. First, it attempts to use 3060 as the non-SSL port. If that port is unavailable, it tries ports in the range 3061 to 3070, then 13060 to 13070. Similarly, it attempts to use 3131 as its SSL port, then ports in the range 3132 to 3141, then 13131 to 13141.
Note:
If you perform an upgrade from an earlier version of Oracle Internet Directory to 11g Release 1 (11.1.1), your port numbers from the earlier version are retained.You can create and modify multiple Oracle Internet Directory instances with differing values, using a different SSL parameters. This is a useful way to accommodate clients with different security needs.
See Also:
Chapter 8, "Managing Oracle Internet Directory Instances"for information about creating a new server instance.The Oracle directory replication server cannot communicate directly with an SSL-enabled LDAP server that supports two way (mutual) authentication. The replication server startup fails and hangs if the LDAP server is configured for SSL mutual authentication.
Oracle Wallet is a secure software container that is used to store X509 certificates, Private key, and trusted CA certificates A self-signed certificate can be stored in Oracle Wallet that can be within an enterprise.
Before removing the reference to the wallet from the instance-specific configuration, you must disable SSL by setting orclsslenable to 0.
See Also:
Oracle Fusion Middleware Administrator's Guide for information on using Oracle wallets with middleware components.Never delete a wallet currently in use, as defined in the attribute orclsslwalleturl, from the file system. Doing so prevents the server from starting successfully. Remove the reference to the wallet from the instance-specific configuration entry attribute orclsslwalleturl before you delete the file.
In 11g, you do not need to directly manipulate orclsslwalleturl because the SSL configuration service abstracts this out, both in WLST and Oracle Enterprise Manager Fusion Middleware Control. The SSL configuration service traps any attempts to delete a wallet that is currently in use, provided you do so by using the SSL configuration service.
At installation, Oracle Internet Directory starts up in dual mode. That is, some components can access Oracle Internet Directory using non-SSL connections, while others use SSL when connecting to the directory. By default, Oracle Application Server components are configured to run in this dual mode environment when communicating with Oracle Internet Directory. If you want, you can remove the non-SSL mode and change all middleware instances to use SSL.
Enterprise User Security or a customer application might need an SSL channel with a different configuration from the default. For example, it might need SSL server authentication mode or SSL mutual authentication mode. In this case, you must create another Oracle Internet Directory component instance listening on a different SSL mode and port.
See Also:
Chapter 8, "Managing Oracle Internet Directory Instances" for instructions on how to configure server instancesFor more information about Enterprise User Security SSL configuration, please see the section on enterprise user security configuration in Oracle Database Enterprise User Administrator's Guide.
In no-auth mode, Oracle components developed before 11g Release 1 (11.1.1) can only connect with Oracle Internet Directory using an instance that has interoperability mode enabled (orclsslinteropmode = 1). For compatibility with those components, SSL interoperability mode is enabled by default.
New clients using JSSE (Java Secure Socket Extensions), and non-Oracle clients, need an SSL instance with the interopmode disabled. Oracle Internet Directory is fully compliant with the Sun JDK's SSL, provided SSL interoperability mode is disabled (orclsslinteropmode = 0).
If Oracle Internet Directory is set to the wrong mode for a client, you might observe rare an non-deterministic failures of client SSL connections to the server.
See Also:
"Configuring SSL Interoperability Mode".Beginning with 11g Release 1 (11.1.1), Oracle Internet Directory supports startTLS. This feature enables the on-demand negotiation of an SSL session on a non-SSL port. No special configuration is required for the non-SSL port. If Oracle Internet Directory has an SSL endpoint configured, a client can use startTLS on the non-SSL port to negotiate an SSL connection on the non-SSL port with the same configuration that is on the SSL port. That is, if the SSL port uses mutual authentication, startTLS tries to negotiate mutual authentication on the non-SSL port.
Configuring SSL by using Fusion Middleware Control consists of three basic tasks:
Configuring SSL Parameters by Using Fusion Middleware Control
Restarting Oracle Internet Directory.
See Also:
Chapter 8, "Managing Oracle Internet Directory Instances" for instructions on how to stop and start the server.
"Configuring Certificate Authentication Method by Using Fusion Middleware Control"
Oracle Fusion Middleware Reference for Oracle Identity Management for descriptions of the SSL parameters
To create a self-signed wallet to use when configuring SSL, perform the following steps:
From the Oracle Internet Directory menu, select Security, then Wallets. If any wallets exist, you see a list.
To create a new wallet, click Create Self-signed Wallet. The Create Self-Signed Wallet page appears.
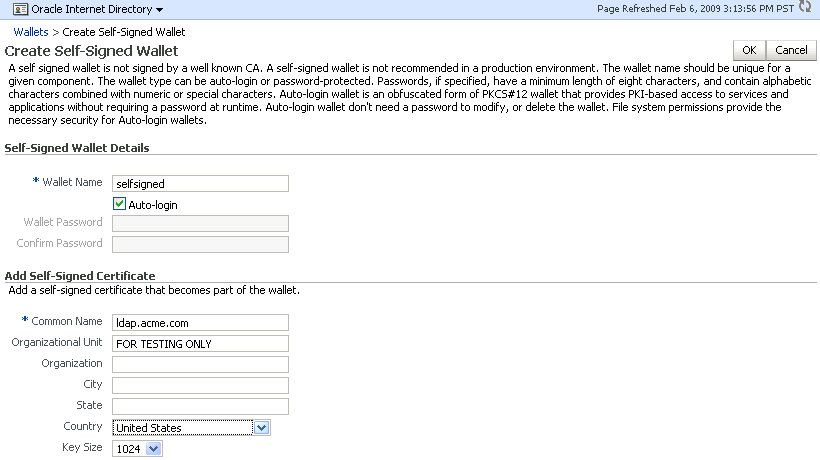
On the Create Self-Signed Wallet page, enter a name for the new wallet, using lower-case letters only.
Select Auto Login for an auto login wallet. Deselect Auto Login for a password-protected wallet.
If you have deselected Auto Login, enter the password in the two fields.
For Common Name, enter the hostname of the instance.
Select a Key Size from the list.
Click Submit.
A confirmation message is displayed and the new wallet appears in the list of wallets.
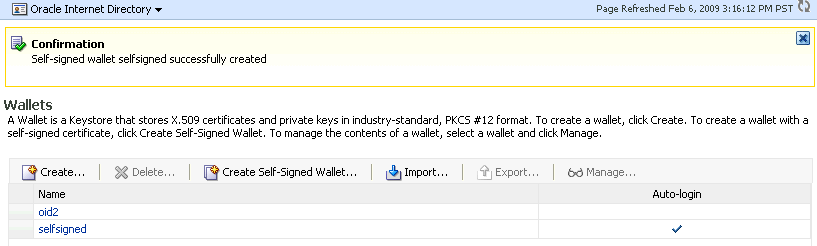
See Also:
Oracle Fusion Middleware Administrator's Guide for more information about Oracle wallets.After you have a wallet to use for configuring SSL, perform the following steps:
From the Oracle Internet Directory menu, select Administration, then Server Properties.
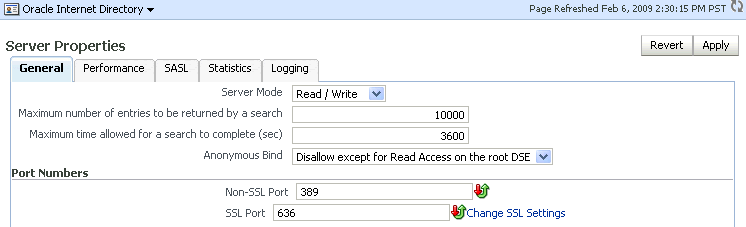
Click Change SSL Settings.
On the SSL Settings dialog:
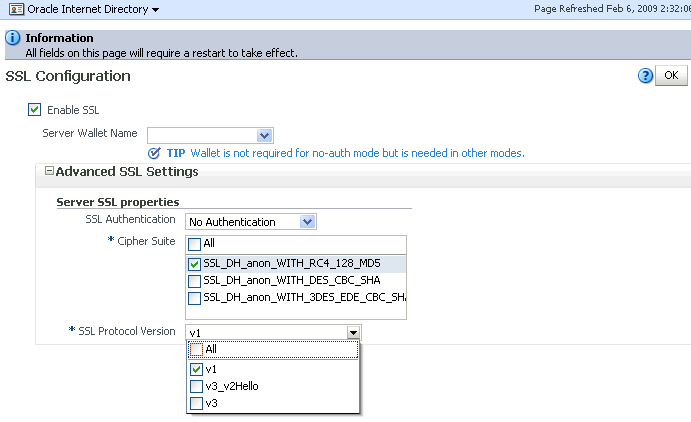
Select Enable SSL.
Select a wallet.
If this is a non auto login wallet, supply the wallet password in the Server Wallet Password field.
If necessary, expand Advanced SSL Settings.
Set SSL Authentication to Server.
Set Cipher Suite to All.
Set SSL protocol version to the appropriate version, usually v3.
Click OK.
Restart the Oracle Internet Directory instance by navigating to Oracle Internet Directory, then Availability, then Restart.
The steps for SSL-enabling in mutual-auth mode are the same, except that in the SSL Settings dialog, you would set SSL Authentication to Mutual instead of Server.
Table 26-3 lists the SSL parameters in Oracle Enterprise Manager Fusion Middleware Control that are applicable to Oracle Internet Directory. All of them are in the instance-specific configuration entry, which has a DN of the form:
"cn=componentname,cn=osdldapd,cn=subconfigsubentry."
SSL Attributes
Table 26-3 SSL-Related Attributes in Fusion Middleware Control
| Field or Heading | Configuration Attribute |
|---|---|
You must restart the server for SSL configuration changes to take effect.
You must perform the following steps to configure SSL:
Create an Oracle wallet.
Configure SSL parameters.
Restart Oracle Internet Directory.
To create an Oracle wallet and configure SSL parameters by using wlst, perform the following steps:
Invoke wlst and connect to the host, specifying the username, password, and port of the WebLogic administration server.
ORACLE_COMMON_HOME/common/bin/wlst.sh connect('username', 'password', 'localhost:7001')
Navigate to the custom mbean tree, then to the specific mbean oracle.as.oid, as described in Section 9.3, "Managing System Configuration Attributes by Using WLST."
custom()
ls()
cd('oracle.as.oid')
ls()
Determine what certificates, if any, you already have in the Key Store MBean. See Table 9-7, "Oracle Internet Directory-Related MBeans".
listWallets('app_server_instance', 'oid_component', 'oid')
For example:
listWallets('inst1', 'oid1', 'oid')
If Necessary, create a new self-signed certificate.
createWallet('inst1',
'oid1',
'oid',
'WALLET_NAME',
'WALLET_PASSWORD')
Add a self-signed certificate to the wallet for use as the server certificate.
addSelfSignedCertificate('inst1',
'oid1',
'oid',
'WALLET_NAME',
'WALLET_PASSWORD',
'cn=INSTANCE_HOST_NAME',
'key_size',
'alias=server-cert')
If you want to use a third-party or custom Certificate Authority-issued certificate, instead of a self-signed certificate, you must first import the certificate. See the chapter on managing keystores, wallets, and certificates in Oracle Fusion Middleware Administrator's Guide for instructions.
Configure the oid1 component node's listener/port for SSL, specifying the appropriate authentication mode:
configureSSL('app_server_instance',
'oid_component',
'oid',
'sslport1',
'property_file.prop')
For an Oracle Internet Directory component the listener port is always sslport1 and the component type is always oid. For example:
configureSSL('inst1',
'oid1',
'oid',
'sslport1',
'myfile.prop')
where myfile.prop contains:
KeyStore=WALLET_NAME AuthenticationType=auth-type SSLVersions=version Ciphers=cipher SSLEnabled=true
See Oracle Fusion Middleware Administrator's Guide for information about property files for SSL.
Restart Oracle Internet Directory, as described in Chapter 8, "Managing Oracle Internet Directory Instances," to activate the changes
Run opmnctl updatecomponentregistration, as described in Section 8.3.4, "Updating the Component Registration of an Oracle Instance by Using opmnctl"
Verify that SSL is enabled by using the methods described in Section 26.5, "Testing SSL Connections by Using Oracle Directory Services Manager" and Section 26.6, "Testing SSL Connections From the Command Line."
Note:
WLST manages Oracle Internet Directory through its SSL port. The Oracle Internet Directory SSL port must be configured for no authentication or server authentication. If the Oracle Internet Directory SSL port is configured for mutual authentication, you will not be able to change Oracle Internet Directory parameters by using WLST. See Section 26.1.3, "SSL Authentication Modes."See Also:
Oracle Fusion Middleware Administrator's Guide for more information about wlst commands.
Oracle Fusion Middleware Administrator's Guide for information on using Oracle wallets with middleware components.
You must perform the following steps to configure SSL:
Create an Oracle wallet.
Configure SSL parameters.
Restart Oracle Internet Directory.
See Also:
Chapter 8, "Managing Oracle Internet Directory Instances" for instructions on how to stop and start the server.
Section 32.4, "Configuring Certificate Authentication Method by Using Command-Line Tools"
Oracle Fusion Middleware Reference for Oracle Identity Management for descriptions of the SSL parameters
Note:
You can also useorapki to configure a wallet. See Oracle Fusion Middleware Administrator's GuideIf you already have created a wallet, you can use the ldapmodify command instead of wlst to change SSL parameters.
For example, to change the value of orclsslinteropmode to 1 for the instance oid1, you would type:
ldapmodify -D cn=orcladmin -q -p portNum -h hostname -f ldifFile
where ldifFile contains:
dn: cn=oid1,cn=osdldapd,cn=subconfigsubentry changetype: modify replace: orclsslinteropmode orclsslinteropmode: 1
SSL parameters are attributes of an instance-specific configuration entry. These configuration entries have DNs of the form:
cn=componentname,cn=osdldapd,cn=subconfigsubentry
for example:
cn=oid1,cn=osdldapd,cn=subconfigsubentry
The SSL attributes are shown in Table 26-4.
You can use the ldapsearch command to list the SSL attributes and their values. For example, to list attributes containing the string orclssl in the instance oid1, you would type:
ldapsearch -p 3060 -D cn=orcladmin -q \
-b "cn=oid1,cn=osdldapd,cn=subconfigsubentry" \
-s base "objectclass=*" | grep -i orclssl
After you have configured SSL Parameters, restart Oracle Internet Directory., as described in Chapter 8, "Managing Oracle Internet Directory Instances."
Note:
Do not setorclsslenable to 1 (SSL only) if you use Oracle Enterprise Manager Fusion Middleware Control or WLST to manage Oracle Internet Directory. Those utilities manage the server through MBeans, which use SASL over a non-SSL connection.To test the SSL connection by using Oracle Directory Services Manager:
Invoke ODSM as described in Section 7.4.5, "Invoking Oracle Directory Services Manager."
Connect to the Oracle Internet Directory server. On the login screen, enable SSL and specify the SSL port.
If you can connect, the SSL connection is working correctly.
You can use the ldapbind command to test SSL connections. On UNIX, the syntax is:
ldapbind -D cn=orcladmin -q -U authentication_mode -h host -p SSL_port \ -W "file://DIRECTORY_CONTAINING_WALLET" -Q
and on Windows, the syntax is:
ldapbind -D cn=orcladmin -q -U authentication_mode -h host -p SSL_port \ -W "file:device:\DIRECTORY_CONTAINING_WALLET" -Q
where authentication_mode is one of:
| Number | Authentication |
|---|---|
| 1 | SSL No authentication required. |
| 2 | One-way (server only) SSL authentication required. |
| 3 | Two-way (client and server) SSL authentication required. |
See Also:
Theldapbind command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.Use this method to test an SSL configuration with SSL no authentication required. The syntax is:
ldapbind -D cn=orcladmin -q -U 1 -h host -p SSL_Port
Use this method to test an SSL configuration with SSL server authentication configured. A client can request either server authentication or no authentication.
For an anonymous bind with server authentication, the syntax is:
ldapbind -U 2 -h host -p port -W "file:DIRECTORY_CONTAINING_WALLET" -Q
For a bind with user cn=orcladmin, wallet file ORACLE_INSTANCE/OID/admin/mywallet, and server authentication, the syntax is:
ldapbind -D cn=orcladmin -q -U 2 -h host -p port \ -W "file:ORACLE_INSTANCE/OID/admin/mywallet" -Q
For a bind without SSL authentication, the syntax is:
ldapbind -D cn=orcladmin -q -U 1 -h host -p SSL_Port
Use this method to test an SSL configuration with SSL client and server authentication configured.
Oracle Internet Directory supports the Certificate Matching Rule. The DN and password passed on the ldapbind command line are ignored. Only the DN from the certificate or the certificate hash is used for authorization.
See Also:
Section 32.1.1, "Direct Authentication."To use the bind DN (Distinguished Name) from the client certificate, the syntax is:
ldapbind -U 3 -h host -p port -W "file:DIRECTORY_CONTAINING_WALLET" -Q
See Section 26.1.7, "SSL Interoperability Mode" for a description of interoperability mode.
To set SSL interoperability mode for compatibility with Oracle components developed before 11g Release 1 (11.1.1) use the command:
ldapmodify -D cn=orcladmin -q -p portNum -h hostname -f ldifFile
where ldifFile contains:
dn: cn=oid1,cn=osdldapd,cn=subconfigsubentry changetype: modify replace: orclsslinteropmode orclsslinteropmode: 1
After you have configured SSL Parameters, restart Oracle Internet Directory, as described in Chapter 8, "Managing Oracle Internet Directory Instances."