| Skip Navigation Links | |
| Exit Print View | |
|
System Administration Guide: Security Services Oracle Solaris 10 1/13 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
System Administration Guide: Security Services Oracle Solaris 10 1/13 Information Library |
1. Security Services (Overview)
Part II System, File, and Device Security
2. Managing Machine Security (Overview)
3. Controlling Access to Systems (Tasks)
4. Controlling Access to Devices (Tasks)
5. Using the Basic Audit Reporting Tool (Tasks)
6. Controlling Access to Files (Tasks)
7. Using the Automated Security Enhancement Tool (Tasks)
Part III Roles, Rights Profiles, and Privileges
8. Using Roles and Privileges (Overview)
9. Using Role-Based Access Control (Tasks)
10. Role-Based Access Control (Reference)
Part IV Cryptographic Services
13. Oracle Solaris Cryptographic Framework (Overview)
14. Oracle Solaris Cryptographic Framework (Tasks)
15. Oracle Solaris Key Management Framework
Part V Authentication Services and Secure Communication
16. Using Authentication Services (Tasks)
19. Using Secure Shell (Tasks)
21. Introduction to the Kerberos Service
22. Planning for the Kerberos Service
23. Configuring the Kerberos Service (Tasks)
Configuring the Kerberos Service (Task Map)
Configuring Additional Kerberos Services (Task Map)
How to Manually Configure a Master KDC
How to Configure a KDC to Use an LDAP Data Server
How to Manually Configure a Slave KDC
How to Refresh the Ticket Granting Service Keys on a Master Server
Configuring Cross-Realm Authentication
How to Establish Hierarchical Cross-Realm Authentication
How to Establish Direct Cross-Realm Authentication
Configuring Kerberos Network Application Servers
How to Configure a Kerberos Network Application Server
Configuring Kerberos NFS Servers
How to Configure Kerberos NFS Servers
How to Create a Credential Table
How to Add a Single Entry to the Credential Table
How to Provide Credential Mapping Between Realms
How to Set Up a Secure NFS Environment With Multiple Kerberos Security Modes
Configuring Kerberos Clients (Task Map)
How to Create a Kerberos Client Installation Profile
How to Automatically Configure a Kerberos Client
How to Interactively Configure a Kerberos Client
How to Manually Configure a Kerberos Client
How to Disable Verification of the Ticket Granting Ticket (TGT)
How to Access a Kerberos Protected NFS File System as the root User
How to Configure Automatic Migration of Users in a Kerberos Realm
Swapping a Master KDC and a Slave KDC
How to Configure a Swappable Slave KDC
How to Swap a Master KDC and a Slave KDC
Administering the Kerberos Database
Backing Up and Propagating the Kerberos Database
How to Back Up the Kerberos Database
How to Restore the Kerberos Database
How to Convert a Kerberos Database After a Server Upgrade
How to Reconfigure a Master KDC to Use Incremental Propagation
How to Reconfigure a Slave KDC to Use Incremental Propagation
How to Configure a Slave KDC to Use Full Propagation
How to Verify That the KDC Servers Are Synchronized
How to Manually Propagate the Kerberos Database to the Slave KDCs
Setting Up Parallel Propagation
Configuration Steps for Setting Up Parallel Propagation
Managing a KDC on an LDAP Directory Server
How to Mix Kerberos Principal Attributes in a Non-Kerberos Object Class Type
How to Destroy a Realm on an LDAP Directory Server
Increasing Security on Kerberos Servers
How to Enable Only Kerberized Applications
How to Restrict Access to KDC Servers
How to Use a Dictionary File to Increase Password Security
24. Kerberos Error Messages and Troubleshooting
25. Administering Kerberos Principals and Policies (Tasks)
26. Using Kerberos Applications (Tasks)
27. The Kerberos Service (Reference)
Part VII Auditing in Oracle Solaris
28. Oracle Solaris Auditing (Overview)
29. Planning for Oracle Solaris Auditing
30. Managing Oracle Solaris Auditing (Tasks)
All hosts that participate in the Kerberos authentication system must have their internal clocks synchronized within a specified maximum amount of time (known as clock skew). This requirement provides another Kerberos security check. If the clock skew is exceeded between any of the participating hosts, client requests are rejected.
The clock skew also determines how long application servers must keep track of all Kerberos protocol messages, in order to recognize and reject replayed requests. So, the longer the clock skew value, the more information that application servers have to collect.
The default value for the maximum clock skew is 300 seconds (five minutes). You can change this default in the libdefaults section of the krb5.conf file.
Note - For security reasons, do not increase the clock skew beyond 300 seconds.
Because maintaining synchronized clocks between the KDCs and Kerberos clients is important, you should use the Network Time Protocol (NTP) software to synchronize them. NTP public domain software from the University of Delaware is included in the Oracle Solaris software.
Note - Another way to synchronize clocks is to use the rdate command and cron jobs, a process that can be less involved than using NTP. However, this section focuses on using NTP. And, if you use the network to synchronize the clocks, the clock synchronization protocol must itself be secure.
NTP enables you to manage precise time or network clock synchronization, or both, in a network environment. NTP is basically a server-client implementation. You pick one system to be the master clock (the NTP server). Then, you set up all your other systems (the NTP clients) to synchronize their clocks with the master clock.
To synchronize the clocks, NTP uses the xntpd daemon, which sets and maintains a UNIX system time-of-day in agreement with Internet standard time servers. The following shows an example of this server-client NTP implementation.
Figure 23-1 Synchronizing Clocks by Using NTP
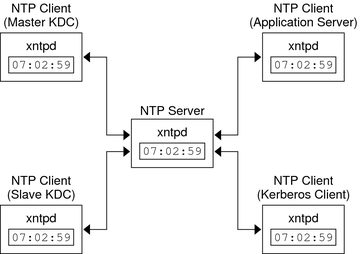
Ensuring that the KDCs and Kerberos clients maintain synchronized clocks involves implementing the following steps:
Setting up an NTP server on your network. This server can be any system, except the master KDC. See Managing Network Time Protocol (Tasks) in System Administration Guide: Network Services to find the NTP server task.
As you configure the KDCs and Kerberos clients on the network, setting them up to be NTP clients of the NTP server. See Managing Network Time Protocol (Tasks) in System Administration Guide: Network Services to find the NTP client task.