1 Understanding Oracle Privileged Account Manager
This chapter introduces you to Oracle Privileged Account Manager. The topics in this chapter include
1.1 What is Oracle Privileged Account Manager?
Oracle Privileged Account Manager manages privileged accounts that are not being managed by any other Oracle Identity Management components.
Accounts are considered "privileged," if they can access sensitive data, can grant access to sensitive data, or can both access and grant access to that data. Privileged accounts are your company's most powerful accounts and they are frequently shared.
Accounts come under Oracle Privileged Account Manager's purview if they are associated with elevated privileges, are used by multiple end-users on a task-by-task basis, and must be controlled and audited.
For example, these accounts require security and may fall under compliance regulations:
-
UNIX root, Windows administrator, and Oracle Database SYSDBA system accounts
-
Application accounts, such as the database user accounts used by an application server when it connects to a Human Resources application
-
Traditional shared and elevated privilege user accounts, such as system administrators and database administrators
Administrators determine which accounts are privileged within a particular deployment, and they must configure Oracle Privileged Account Manager to manage those accounts.
While Oracle Privileged Account Manager most commonly manages shared and elevated privileged accounts, administrators can also use it to manage passwords for any type of account. For example, if an employee is on extended leave and you have a business reason for allowing another employee to access the system using that person's email account, Oracle Privileged Account Manager can manage that privilege.
1.2 Why Use Oracle Privileged Account Manager?
Oracle Privileged Account Manager enables you to administer and provide better security for privileged accounts and passwords that are traditionally difficult to manage for several reasons.
First, privileged accounts generally have more access rights than a regular user's account. Because these accounts are not typically associated with one specific employee, they are often difficult to audit with existing tools and processes. Consequently, when employees leave the company, they might retain privileged account passwords that are still in use, which is a very serious compliance and security issue.
Also, changing privileged account passwords on a regular basis is difficult. If many people depend on the account, changing the password and notifying everyone requires a coordinated effort.
Finally, you typically do not want to store passwords in a central or well-known location, such as an external repository (like LDAP) or in application configuration files, because you cannot control access to those passwords.
Oracle Privileged Account Manager delivers a complete solution for securely managing privileged accounts and passwords because it provides
-
Centralized password management for privileged and shared accounts, including UNIX and Linux root accounts, Oracle Database SYSDBA, application accounts, and LDAP admin accounts
-
Interactive, policy-based account check-out and check-in
Oracle Privileged Account Manager requires all authorized users to check out an account before using it, and then to check that account back in when they are finished with it. Oracle Privileged Account Manager audits account check outs and check ins by tracking the real identity (the person's name) of every shared administrator user at any given moment in time. By using this information, Oracle Privileged Account Manager can provide a complete audit trail that shows who accessed what, when, and where.
-
Automatic password changes using the Identity Connector Framework (ICF)
Oracle Privileged Account Manager modifies passwords when they are checked out and checked in (when configured to do so). Consequently, when a user checks out a password and then subsequently checks it back in, that user can no longer use the previously checked out password.
In addition, Oracle Privileged Account Manager can change application privileged account passwords at specified intervals, such as every 90 days, with no changes to those applications and Oracle Privileged Account Manager synchronizes those passwords on the target systems. For example, Oracle Privileged Account Manager can update service and scheduled task credentials.
-
User and group management and workflow integration using Oracle Identity Manager
1.2.1 Features
Oracle Privileged Account Manager's key features include:
-
Multiple access points, including the Oracle Privileged Account Manager web-based user interface (called the Console), RESTful APIs, and Oracle Privileged Account Manager's command line tool (CLI)
Oracle Privileged Account Manager's simple RESTful APIs can access Oracle Privileged Account Manager functionality from applications and scripts.
-
Administrator and Self-Service user interfaces that are accessed from Oracle Privileged Account Manager's web-based user interface
-
Integration with Oracle technologies, including
-
Oracle Platform Security Services (OPSS) Policy Store for storing metadata and authorizing functionality
-
Oracle Platform Security Services (OPSS) Trust Service to authenticate and propagate identities from the Oracle Privileged Account Manager user interface to the Oracle Privileged Account Manager server
-
Credential Store Framework (CSF) to securely store passwords to target systems and privileged accounts, and to enable regular updates to application privileged account passwords for compliance, with no changes to applications running in Oracle WebLogic Server (WLS)
-
Identity Connector Framework (ICF) to connect to targets and to discover, update, or discover and update the passwords for privileged accounts on those systems
-
-
Support for multiple target types; including operating systems, databases, LDAP directories, and Oracle Fusion Middleware applications
In addition, because ICF is an open standard, you can write your own connectors against other types of targets for which Oracle has not yet created an ICF connector.
For more information about ICF and about developing your own connector, see "Understanding the Identity Connector Framework" and "Developing Identity Connectors Using Java" or "Developing Identity Connectors Using .Net" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
-
Advanced reporting capabilities
-
Oracle Privileged Account Manager's out-of-the box audit reports are integrated with Oracle Business Intelligence Publisher 11g (BI Publisher) so you know who is using your privileged accounts. BI Publisher also enables you to create and manage formatted reports from different data sources.
-
The Oracle Fusion Middleware Audit Framework logs audit events in a centralized database. Oracle Privileged Account Manager uses these events to generate audit reports.
-
Events related to privileged account access roll up into Oracle Identity Manager and Oracle Identity Analytics for audit and attestation.
-
-
Policy-driven access to privileged accounts
-
Ability to manage attended (a person is present) and unattended (no person is present) accounts
An unattended account, also called a service account, is an account that Oracle Privileged Account Manager uses when it connects to a target system. For example, this is the account and password you must provide when adding and registering a new target system.
Oracle Privileged Account Manager uses service accounts to perform all Oracle Privileged Account Manager-related operations (such as discovering accounts, resetting passwords, and so forth) on that system, which is why service accounts must have some special privileges and properties. End users are not expected to ever use service accounts.
1.2.2 Functionality
In addition to the functionality described in Section 1.2, "Why Use Oracle Privileged Account Manager?," Oracle Privileged Account Manager
-
Associates privileged accounts with targets
-
Grants users and roles access to privileged accounts, and removes that access
-
Provides role-based access to passwords maintained in the Oracle Privileged Account Manager password request system
-
Provides password check out and check in to control access to accounts
-
Eliminates the potential of having unmanaged privileged accounts when your unattended applications use client-certificate authentication
-
Resets passwords to a random value on check in and check out by default
You can configure Oracle Privileged Account Manager to automatically check in privileged accounts after a specified time to protect against users who check out that privileged account and do not bother to explicitly check in the account.
You can also constrain how long users can check out a privileged account.
-
Manages password resets on supported targets
-
Makes authorization decisions to determine
-
Which targets, privileged accounts, and policies are exposed to an end user or administrator
-
Which operations (add, modify, check-in, and check-out) end users and administrators can perform
-
-
Associates policies with privileged accounts
-
Performs and supports Create, Read, Update, Delete, and Search (CRUDs) operations on targets, privileged accounts, and policies
This core functionality is exposed through Oracle Privileged Account Manager's RESTful APIs. Check ins, check outs, and so forth are also supported through the RESTful interface.
-
Uses Oracle's common auditing, logging, and reporting to monitor and report access
-
Oracle Privileged Account Manager offers multiple high availability capabilities
1.2.3 Architecture and Topology
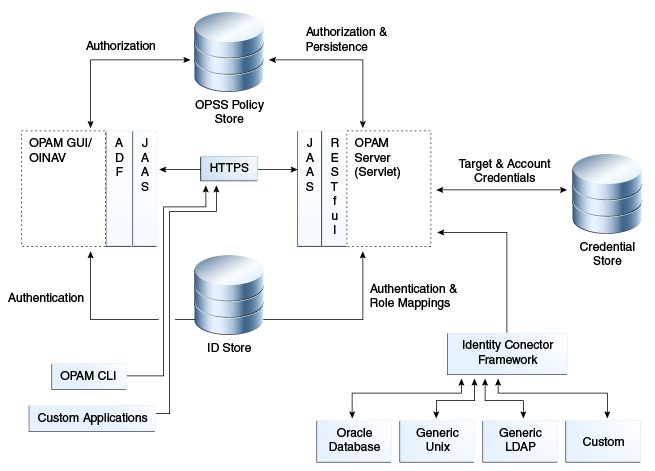
The following diagram illustrates Oracle Privileged Account Manager's architecture and topology:
As you examine this figure, it is important to note the following points:
-
All of Oracle Privileged Account Manager's core logic resides on the Oracle Privileged Account Manager server. This functionality is exposed through a Representational State Transfer (REST or RESTful) service, where the data is encoded as JavaScript Object Notation (JSON).
Note:
Oracle Privileged Account Manager provides a web-based user interface (known as the Console) in Oracle Identity Navigator and an Oracle Privileged Account Manager command line tool (CLI). Both interfaces are essentially clients of the Oracle Privileged Account Manager server.
However, third parties can write their own clients, such as custom applications, by leveraging the open RESTful service. For more information, refer to Appendix B, "Working with Oracle Privileged Account Manager's RESTful Interface."
-
Oracle Privileged Account Manager authentication relies on Java Authentication & Authorization Service (JAAS) support in WebLogic.
Refer to "WebLogic Security Service Architecture" in Oracle Fusion Middleware Understanding Security for Oracle WebLogic Server for more information about JAAS support in WebLogic.
For more information about Oracle Privileged Account Manager authentication, see Section 2.2, "Understanding Oracle Privileged Account Manager Authentication."
-
All communication with, and between, Oracle Privileged Account Manager-related components (including Oracle Privileged Account Manager's Console, command-line interface, and server) occurs over SSL
-
Oracle Privileged Account Manager relies on and transparently uses the ID Store, Policy Store, and Credential Store configured for the WebLogic domain in which Oracle Privileged Account Manager is deployed.
All of the passwords needed by Oracle Privileged Account Manager at run time (such as passwords to target systems, transient passwords for accounts, and so forth), are stored in the Credential Store through the Credential Store Framework.
Refer to Section 1.3, "How Oracle Privileged Account Manager is Deployed in Oracle Fusion Middleware" for more information.
-
The Oracle Privileged Account Manager Console leverages, and is rendered by, Oracle Application Development Framework (ADF).
For more information about ADF, refer to the following website:
http://www.oracle.com/technetwork/developer-tools/adf/overview/index.html -
Oracle Privileged Account Manager connects to targets by using ICF connectors.
For additional information, see "Understanding the Identity Connector Framework" in the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
1.2.4 Oracle Privileged Account Manager-Managed CSF Credentials
The Credential Store Framework (CSF) is an OPSS component that primarily provides secure storage for credentials. For example, many applications use CSF as a mechanism for storing application credentials.
Oracle Privileged Account Manager enables administrators to identify account credentials to be secured, shared, audited, and managed. In addition, Oracle Privileged Account Manager supports account lifecycle management activities such as periodic password modification.
Though many application developers use CSF to store application credentials for required targets (such as RDBMS and LDAP), there are certain aspects about how CSF is used that can potentially be improved, including:
-
Applications storing their credentials in CSF do not expect these credentials to be shared. Therefore, a given instance of CSF can have multiple references to the same credential. For example, multiple applications could be relying on the same physical credential and yet have multiple logical references.
-
Periodically modifying application credentials is necessary to satisfy compliance and internal IT policy requirements. However, modifying credentials (on the target and thereafter the CSF reference) remains a manual task, which is further complicated by the fact that there may be multiple references to the same credential in CSF. So, you must change the password or credential on the target and then manually update all references to that password in CSF.
Oracle Privileged Account Manager can automate this process, but automating the periodic modification of credentials is also complicated by the potential for multiple references that cannot be accurately traced.
Oracle Privileged Account Manager leverages its account lifecycle management feature to empower lifecycle management of application credentials stored in CSF.
1.2.4.1 Provisioning
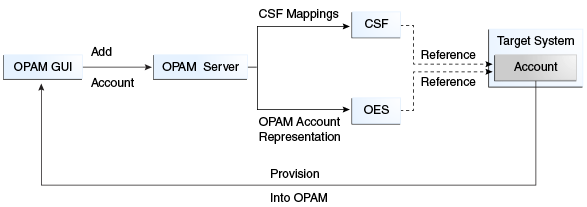
If you decide that Oracle Privileged Account Manager will manage a particular account credential, then that credential must be provisioned through Oracle Privileged Account Manager. The following figure illustrates this provisioning process.
The administrator
-
Adds an Oracle Privileged Account Manager target (if required).
-
Adds the Oracle Privileged Account Manager privileged account or credential to the target, which must include the necessary CSF mappings.
Note:
CSF mappings are the mechanism by which a specific credential instance is uniquely identified within CSF.
The Oracle Privileged Account Manager server stores the CSF mappings along with its representation of the Privileged Account. The Oracle Privileged Account Manager server creates instances of the credential in CSF that correspond to the provided mappings.
1.2.4.2 Lifecycle Management
An account provisioned as described in Section 1.2.4.1, "Provisioning" can have an associated Password Policy that governs password construction, periodic modification requirements, and so forth.
Oracle Privileged Account Manager normally honors and performs actions on the policy. However, whenever an administrator modifies an account credential that has associated CSF-mappings, Oracle Privileged Account Manager also updates the credential instances stored in CSF with those mappings. This update ensures that all relevant parties have access to the latest credential and allows the seamless management of password lifecycle events such as periodic modification.
1.2.4.3 Application Consumption
Using Oracle Privileged Account Manager to manage an application's credentials places no additional burden on that application. The only process change that occurs is that the credential must first be provisioned through Oracle Privileged Account Manager into Oracle Privileged Account Manager and CSF.
Oracle Privileged Account Manager pushes the credential to CSF with the administrator-provided mappings. If those mappings remain constant, the application can continue to access the credentials directly through CSF.
1.3 How Oracle Privileged Account Manager is Deployed in Oracle Fusion Middleware
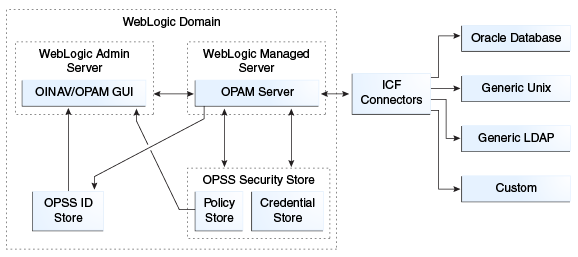
The following figure illustrates how Oracle Privileged Account Manager is deployed within Oracle Fusion Middleware.
As you examine this figure, note the following points:
-
All components are deployed within a single WebLogic domain.
-
Oracle Identity Navigator and the Oracle Privileged Account Manager web-based user interface are both deployed in the WebLogic Admin Server.
-
The OPSS ID Store and the OPSS Security Store (which includes the Policy Store and Credential Store) are WebLogic domain-wide constructs, so there is one of each per domain.
Oracle Privileged Account Manager simply works with what is configured for that domain. You are not required to use an Oracle Privileged Account Manager-specific configuration to use these constructs and services. In addition, Oracle Privileged Account Manager abstracts out the use of these constructs and services so that you do not have to understand what goes on "under the covers" in great detail.
-
The OPSS ID Store can point to the LDAP embedded in WebLogic (out of the box) or to an external LDAP server.
Refer to "Configuring the Identity Store Service" in the Oracle Fusion Middleware Application Security Guide for configuration instructions.
-
The OPSS Security Store can point to an XML file based store (out of the box), to an external RDBMS, or to an external LDAP server.
Refer to "Configuring the OPSS Security Store" in the Oracle Fusion Middleware Application Security Guide for configuration instructions.
-
For information about managing the Policy Store and the Credential Store, see "Managing the Policy Store" and "Managing the Credential Store" in the Oracle Fusion Middleware Application Security Guide.
-