9 Securing Environment Specific Resources
This chapter contains information on how to secure resources using specific Security Modules. The following sections contain detailed information.
9.1 Choosing a Security Module Type
An Oracle Entitlements Server administrator chooses a Security Module type based on the type of resource being protected. The Security Module type is defined when the Security Module is instantiated using the OES Client's SMConfig Tool (as documented in Chapter 8, "Managing Security Module Configurations").
Note:
See the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for OES Client installation instructions.
Instantiation of a Security Module using the SMConfig Tool defines parameters such as the Security Module type, configuration ID and a path to the appropriate container. Table 9-2 lists the Security Module types that can be instantiated. (The SMType attribute value is defined in parentheses in the Security Module column.)
The Security Module types documented in Table 9-1 do not protect resources specific to the environment. They are a Policy Decision Point (PDP) that receives Java calls for authorization. The Security Modules simply provide the authorization API for the application to call.
Table 9-1 General Protection Security Module Types
| Security Module | Purpose | Proxy Mode | Container Support |
|---|---|---|---|
|
Java (java) |
Policy Decision Point (PDP) that receives Java calls for authorization |
Supported |
Used for Java, Standard Edition (JSE) applications and complex integrations |
|
Websphere (was) |
Java Security Module that receives authorization requests directly from the application |
Supported |
WebSphere Application Server |
|
Web Services (ws) |
Multi-Protocol Security Module that accepts Web Services calls; configure other Security Modules (Java, WLS) in proxy mode to communicate with Web Services Security Module using the XACML Gateway or SOAP. |
Not supported |
Supported as a JSE standalone process or as a web service running on a WebLogic Server container; can be used by other Security Modules in proxy mode; can be used as long as a Web Services request can be built or when an application is built in a non-standard programming language (Python, for example) |
|
RMI (rmi) |
Multi-Protocol Security Module is a Java Security Module that is enhanced to accept Remote Method Invocation (RMI) calls |
Not supported |
Use only for JSE applications if Web Services is too heavy |
|
.NET (dotnet) |
Allows applications written in C# to send authorization requests to the Web Services Security Module by calling the PEP API in C# |
Supported in Proxy Mode only; .NET Security Module serves as a proxy that communicates with the Web Services Security Module |
.NET containers |
|
JBoss (jboss) |
Java Security Module that receives authorization requests directly from the application |
Supported |
JBoss Application Server |
|
Tomcat (tomcat) |
Java Security Module that receives authorization requests directly from the application; does not support Oracle Platform Security Services authentication/login module or |
Supported |
Apache Tomcat Application Server |
The Security Modules documented in Table 9-2 allow the protection of resources that are specific to the environment in which they are deployed in addition to processing direct authorization calls from the application.
Table 9-2 Environment Specific Security Module Types
| Security Module | Purpose | Proxy Mode | Container Support |
|---|---|---|---|
|
Sharepoint (moss) |
Protects Microsoft Sharepoint Server resources by intercepting Sharepoint requests for content; see Section 9.2, "Securing Microsoft Office SharePoint Server Resources" |
Supported only in Proxy Mode; Sharepoint Security Module itself serves as a proxy (written in C#) that communicates with the Web Services Security Module |
.NET containers |
|
WebLogic Server (wls) |
Security Module that behaves exactly as Java Security Module unless the Oracle Entitlements Server security providers are enabled (as documented in Section 9.4.1, "Integrating with WebLogic Server") in which case the Security Module can also process WebLogic Server calls; see Section 9.4, "Securing WebLogic Server Resources" |
Supported - unless the Oracle Entitlements Server security providers are enabled to intercept WebLogic Server requests. |
WebLogic Server |
|
Oracle Service Bus (osb) |
WebLogic Security Module with Oracle Entitlements Server security providers enabled that intercepts authorization requests from the Oracle Service Bus; see Section 9.3, "Securing Oracle Service Bus Resources" |
Supported |
See Chapter 8, "Managing Security Module Configurations" for details on these Security Modules and how to configure them. Details on how they work can be found in Section 1.3, "Overview of the Oracle Entitlements Server Architecture" and Chapter 7, "Deploying the Policy Decision Point."
9.2 Securing Microsoft Office SharePoint Server Resources
Oracle Entitlements Server enables enterprises to manage MOSS portal environments. Integration with MOSS is provided through the MOSS Security Module plug-in that intercepts authorization calls within the SharePoint Server and sends them to its integrated Web Services Security Module (the PDP). The PDP then returns the authorization decision back to the MOSS Security Module plug-in and the decision is enforced. The following sections have more information.
9.2.1 Protecting SharePoint Resources
SharePoint components that can be secured include web sites, web pages, web parts, list items, navigation bar items and the like. Based on the component, the resource is protected differently. SharePoint resources are categorized according to the following list.
-
Items are the smallest SharePoint components; for example, a Document, a Task, a Contact, a Page or an Announcement.
-
Lists are a collection of a single type of SharePoint component. Document Lists, Contacts Lists, Task Lists and the like can be created.
-
Folders exist in Lists and serve as a container for multiple Items and sub Folders.
-
Sites are a collection of Lists. For example, the default SharePoint Document Center Site is made up of three Lists: Announcements, Documents and Tasks.
-
Navigation Bar Items on SharePoint site pages can be used to manipulate MOSS components.
Note:
There is only one Resource Type for all MOSS resources. In this section, we use the name MossResourceType.
The following sections contain more information.
9.2.1.1 Protecting Web Sites and Web Pages
MOSS web sites are composed of one or more web pages. An organization generally organizes one web site in MOSS to denote one department in the company. MOSS comes with a main Web Site within which there are default sub sites. Sub sites appear on the top or side navigation bar or as links on other web pages. All these web sites have their own unique URLs.
The URL of a MOSS Web site or Web page defines the Resource instance created in Oracle Entitlements Server. In the case of a URL defined as http://Sharepoint_Server_Name/TestSite, the corresponding Resource is created by defining a /TestSite Resource as an instance of the MossResourceType Resource Type under the MossApp Application. Policies are then created using the Oracle Entitlements Server objects.
A Custom HTTP Module is implemented by Oracle Entitlements Server to secure the MOSS web sites. When a user tries to access a protected component, the request is intercepted by the Custom HTTP Module and forwarded to Oracle Entitlements Server for policy evaluation. The decision is returned to the Custom HTTP Module and if the user is denied access, a Custom Error Page with a message indicating a lack of permissions to view this location is displayed.
Note:
Custom HTTP Modules are enabled by defining the HttpModules elements in the web.config MOSS Site configuration file. See Section 9.2.4, "Configuring for SharePoint Security."
9.2.1.2 Protecting Web Parts
A MOSS Web Part is similar to a portlet in that it is used to publish content within web pages. A Web page may contain one or more Web Parts. Web Parts are represented in Oracle Entitlements Server by defining their unique MOSS Display Name as the Resource instance name. The Resource instance is created as a child of the parent web page's Resource.
When a user tries to access these protected components the request is intercepted by a MOSS Delegate Control created for Oracle Entitlements Server. In short, a Delegate Control allows you to put any custom .NET code into a SharePoint page without modifying the page itself. This custom code is used to retrieve the decision from Oracle Entitlements Server and remove unauthorized Web Parts from the page. There are no error messages displayed in this case.
Note:
Delegate OES Authorization Control is explicitly added to the Web Part pages or implicitly defined in the web site's master page. See Section 9.2.4, "Configuring for SharePoint Security."
9.2.1.3 Protecting Lists
A MOSS List is a collection of items within a Web Part on a Web page. When creating a MOSS Web site, a set of lists is also created depending upon the template used. Each list item is identified by a URL and represented as an Oracle Entitlements Server Resource. These lists are incorporated into Oracle Entitlements Server based on whether they are document lists or non-document lists.
-
Document Lists can be displayed by going to
http://Sharepoint_Server_Name/TestSite/SharedDocuments/Forms/AllItems.aspx. Create a top-level Resource named/TestSite/SharedDocuments/Forms/AllItems.aspx. Next create individual Resource objects for each item on the list as a sub resource to the top-level Resource. For example, a sub Resource named/TestSite/SharedDocuments/Scott.sqlcan be created for an item on the list namedScott.sql. -
Non-document Lists can be displayed by going to
http://Sharepoint_Server_Name/TestSite/Lists/Announcements/AllItems.aspx. Create a Resource named/TestSite/Lists/Announcements/AllItems.aspx. Next create a/TestSite/Lists/Announcements/EditForm.aspxResource and a/TestSite/Lists/Announcements/DispForm.aspxResource at the same level. Now click on any item in the list; the URL appears ashttp://Sharepoint_Server_Name/web1/Lists/Announcements/DispForm.aspx?ID=2&Source=http%3A%2F%2Fsharepoint01%2FTestSite%2FLists%2FAnnouncements%2FAllItems%2Easpx. Note the ID defined as a URL parameter in the URL. This ID will be used as the name of the non-document item and is created as a sub Resource of bothEditForm.aspxandDispForm.aspx. This must be done for all items within a Non-document List. Alternately, hover the mouse over the link of the item and note the ID from the URL displayed in the status bar of the browser.Note:
For list items only, you don't need to write policy on
EditForm.aspx. You may grant view or ANY on the sameDispForm.aspx. If view, ReadOnly access is granted; if ANY, full access (edit, delete, and the like) is granted.
9.2.1.4 Protecting Sensitive Content Within Web Pages
The SharePoint server allows administrators to publish custom pages which have sensitive information that need access control. The developer may enclose the sensitive information within ASP tags corresponding to the Oracle Entitlements Server Tag Library. The tag library communicates with Oracle Entitlements Server to retrieve the access decision and, as a result, the content is shown only to authorized users.
Note:
The ASP tag library is a server side web control used by a MOSS page developer who registers the namespace, tag-prefix and assembly in the MOSS page and uses the tag to enclose the sensitive content. The library is invoked when an end user tries to access a custom content page on which the tags have been used to provide access control.
9.2.2 Instantiating the MOSS and Web Services Security Modules
The MOSS Security Module works with the Web Services Security Module to provide fine grained authorization for MOSS resources. Before instantiating the Security Modules, ensure that the pre-requisite MOSS environment is already setup. This includes installation of the MOSS and creation of the web application to be protected.
Note:
Environment details of the web application (port number, URL and the like) will be needed in this procedure.
The MOSS Security Module and the Web Services Security Module can be deployed on the same or different servers. Instantiation of both Security Modules is achieved using the SMConfig Tool found in the $ORACLE_CLIENT_HOME/oessm/SMConfigTool/bin directory.
-
To instantiate both the MOSS Security Module and the Web Services Security Module at once, run
config.shwith the parameter-smType mossws. -
To instantiate the Security Modules separately, run
config.shtwice, first with the parameter-smType mossand then with -smType ws.
Additionally, run the SMConfigTool based on your deployment choices. For example, to instantiate the Security Modules when they are deployed on the same Windows machine as the MOSS, use the following command:
config.sh –smType mossws –prpFileName file_name –mossprpFileName file_name –smConfigId -WSListeningPort –pdServer –pdPort
where prpFileName refers to the smconfig.prp used to create the Web Services Security Module and mossprpFileName refers to the properties file used to configure the MOSS server.
Note:
The mossprpFileName template is located at $ORACLE_CLIENT_HOME/oessm/mosssm /adm/configtool/moss_config.properties. moss_config.properties has mandatory properties that must be defined according to your environment and optional properties that, if not defined, use default values.
To instantiate the Security Modules when they are on separate Windows machines, first instantiate the Web Services Security Module (no special instructions). Then use the following command to configure the MOSS Security Module.
config.sh –smType moss –prpFileName file_name –mossprpFileName file_name
See the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for detailed OES Client installation instructions.
9.2.3 Integrating and Disintegrating the MOSS Security Module
The value of the moss.enableOES property in the mossprpFileName template can be used to integrate Oracle Entitlements Server with, or disintegrate Oracle Entitlements Server from, the MOSS application.
-
If
moss.enableOES=true, executingconfig.shwith the-smType mossparameter will integrate the MOSS application with Oracle Entitlements Server. -
If
moss.enableOES=false, executingconfig.shwith the-smType mossparameter will configure the MOSS application to use its default authorization process.
9.2.4 Configuring for SharePoint Security
The following procedure documents the steps to manually configure authorization for a MOSS application rather than the automatic configuration initiated by SMConfigTool. These steps are the same as those automatically executed by the config.sh script in Section 9.2.2, "Instantiating the MOSS and Web Services Security Modules" and can be used instead, by those who prefer not to use the SMConfigTool.
This procedure assumes that the Security Modules have been instantiated. After instantiation, note the generated configuration ID and service registry URL. In the following procedure, the configID is MOSS and the service registry URL is http://hostname:port/ServiceRegistry.
-
Use the Oracle Entitlements Server Administration Console to complete the following steps.
-
Create the Web Services Security Module definition.
-
Create an Application policy object to represent the MOSS application being protected.
The name of the Application must be consistent with the value of the
moss.app.nameproperty defined in themoss_config.propertiesfile. -
Bind this Application to the Web Services Security Module profile.
-
-
Drag and drop
OES.SharePoint.dllandlog4net.dllfrom the $OES_CLIENT_HOME/oes_sm_instances/MOSS_SM_Name/libdirectory to theC:/WINDOWS/assemblydirectory.This registers the assemblies in the Windows Global Assembly Cache and makes them available to all .NET applications on the host machine.
-
If using MOSS 2007 (IIS 6), declare the Oracle Entitlements Server Delegate Control by adding the following code to the HTML HEAD section of the
default.masterfile.<SharePoint:DelegateControl runat="server" ControlId="PageHeader"/>
The default.master file is located in the
C:\Program Files\Common Files\Microsoft Shared\web server extensions\12\TEMPLATE\GLOBAL\directory. This step is not required when using MOSS 2010 (IIS 7).Caution:
When
default.masteris opened with Wordpad, question mark (?) characters sporadically replace existing characters. Ensure that this is corrected before saving your modified file. Alternately, open the file with Notepad. -
Add the Custom Error Page to display a message when the user is not authorized to access the MOSS component.
CustError.aspxandcustError2010.aspxare the custom Oracle Entitlements Server error pages for MOSS. They are located in the $OES_CLIENT_HOME/oes_sm_instances/MOSS_SM_Name/adm/pagesdirectory.-
If using MOSS 2007 (IIS 6), copy
custError.aspxtoC:\ Program Files\Common Files\Microsoft Shared\web server extensions\12\template\layouts. -
If using MOSS 2010 (IIS 7), copy
custError2010.aspxtoC:\Program Files\Common Files\Microsoft Shared\web server extensions\14\template\layoutsand change the name tocustError.aspx.
-
-
Edit the Sharepoint Server
web.configconfiguration file to enable Oracle Entitlements Server-MOSS integration.web.configis located in the virtual directory of the SharePoint application; for example,C:\Inetpub\wwwroot\wss\VirtualDirectories\port-numberwhereport-numberis the application's port.Caution:
When
web.configis opened with Wordpad, question mark (?) characters sporadically replace existing characters. Ensure that this is corrected before saving your modified file. Alternately, open the file with Notepad.-
Add the properties documented in Table 9-3 to the
appSettingssection. Example 9-1 illustrates the appSettings section. Values are taken from the file defined asmossprpFileName.Example 9-1 appSettings Section of Sharepoint web.config File
<add key="SsmUrl" value="${moss.SmUrl}/ServiceRegistry"/> <add key="SsmId" value="${oracle.security.jps.runtime.pd.client.sm_name}"/> <add key="ApplicationID" value="${application.id}"/> <add key="PolicyDomain" value="${policy.domain}"/> <add key="ResourceType" value="${moss.resourcetype}"/> <add key="log4NetXmlfile" value="${moss.log4NetXmlfile}”/> <add key="sharepointSite" value="${moss.sharepointSite}"/> <add key="EnableOES" value="${moss.EnableOES}"/> <add key="IgnoredExtensions" value="${moss.IgnoredExtensions}"/> <add key="IgnoredURLExpression" value=”${moss.IgnoredURLExpression}"/>Table 9-3 appSettings Properties for the MOSS Application
Property Value SsmUrl
Registry URL of the Web Service SM; for example,
http://oesw2k8:9400/ServiceRegistrySsmId
The name of this Security Module; for example, MOSS
IdentityAsserterName
The name of the identity asserter configured in Oracle Entitlements Server. At this time, only
OESIdentityAssertionis supported.ApplicationID
The name of the configured Oracle Entitlements Server Application that represents the protected MOSS resource.
ResourceType
The Resource Type of all MOSS resources; for example,
MossResourceType. The Resource Type of all MOSS components to be protected must be consistent with the value of themoss.resource.typeproperty defined in themoss_config.propertiesfile.log4NetXmlfile
Fully qualified path to the
log4Net.xmlconfiguration file. The log file defined in thelog4Net.xmlfile must be located in an existing directory for which Read/Write access has been given to Everyone to allow log messages to be written.sharepointSite
Top level SharePoint site; for example,
http://alesw2k8:9581/Enable OES
Flag to enable the OES integration; takes true or false as a value
IgnoredExtensions
A comma-separated list of file extension patterns to be ignored by OES Access Control; for example,
png,js,css,axd
Access will always be granted to these resources when requested.
IgnoredURLExpression
A comma-separated list of file name patterns to be ignored by OES Access Control; for example,
/_layouts/Authenticate.aspx,/_login/default.aspx,/_forms/default.aspx
Access will always be granted to these resources when requested.
-
Add the
SafeControl Assemblyentries documented in Table 9-3 to theSafeControlssection.Example 9-2 SafeControl Assembly Entries
<SafeControls> ... <SafeControl Assembly="OES.Sharepoint, Version=1.0.0.0, Culture=neutral, PublicKeyToken=68b08a2fa869dfdc" Namespace="OES.Sharepoint.Controls" TypeName="*" Safe="True" /> <SafeControl Assembly="OES.Sharepoint, Version=1.0.0.0, Culture=neutral, PublicKeyToken=68b08a2fa869dfdc" Namespace="OES.Sharepoint.Modules" TypeName="*" Safe="True" /> </SafeControls> -
Define custom
httpModulesbased on the server used.If using MOSS 2007 (IIS 6), add the following to the
httpModulessection.<add name="CustHTTPModule" type="OES.Sharepoint.Modules.CustHTTPModule, OES.Sharepoint, Version=1.0.0.0, Culture=neutral, PublicKeyToken=68b08a2fa869dfdc " />
If using MOSS 2010 (IIS 7), add Example 9-3 to the
assembliessection and Example 9-4 to themodulessection (after the last<remove>and before the first<add>). -
Update the
PageParserPaths(in theSafeModesection) with the virtual path to which custom content is required to be published. The custom content may be authorized via the tag library provided with the solution. Example 9-5 is an example. -
Replace the MOSS PortalSiteMapProvider details (illustrated in Example 9-6) with the Oracle Entitlements Server PortalSiteMapProvider details (illustrated in Example 9-7).
The custom Oracle Entitlements Server PortalSiteMapProvider secures the Navigation Bar items.
Example 9-6 MOSS PortalSiteMapProvider
<SiteMap> <Providers> … <add name="GlobalNavigation" description="Provider for MOSS Global Navigation" type="Microsoft.SharePoint.Publishing.Navigation.PortalSiteMapProvider, Microsoft.SharePoint.Publishing, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" NavigationType="Combined" Version="14" /> <add name="CurrentNavigation" description="Provider for MOSS Current Navigation" type="Microsoft.SharePoint.Publishing.Navigation.PortalSiteMapProvider, Microsoft.SharePoint.Publishing, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" NavigationType="Current" Version="14" /> … </Providers> </SiteMap>Example 9-7 Oracle Entitlements Server PortalSiteMapProvider
<SiteMap> <Providers> … <add NavigationType="Combined" Version="1" description="Provider for MOSS Global Navigation" name="GlobalNavigation" type="OES.Sharepoint.Controls.OESPortalSiteMapProvider, OES.Sharepoint, Version=1.0.0.0, Culture=neutral, PublicKeyToken=68b08a2fa869dfdc"/> <add NavigationType="Current" Version="1" description="Provider for MOSS Current Navigation" name="CurrentNavigation" type="OES.Sharepoint.Controls.OESPortalSiteMapProvider, OES.Sharepoint, Version=1.0.0.0, Culture=neutral, PublicKeyToken=68b08a2fa869dfdc"/> … </Providers> </SiteMap> -
Restart IIS server for above changes to reflect in IIS server.
-
-
Copy the
OESAuthorizationFeaturedirectory to the MOSSFEATURESdirectory.-
If using MOSS 2007 (IIS 6), copy the
$OES_CLIENT_HOME/oes_sm_instances/MOSS_SM_Name/lib/OESAuthorizationFeaturedirectory to theC:\Program Files\Common Files\Microsoft Shared\web server extensions\12\TEMPLATE\FEATURESdirectory. -
If using MOSS 2010 (IIS 7), copy the
$OES_CLIENT_HOME/oes_sm_instances/MOSS_SM_Name/lib/OESAuthorizationFeature2010directory to theC:\Program Files\Common Files\Microsoft Shared\web server extensions\14\TEMPLATE\FEATURESdirectory and change the directory name toOESAuthorizationFeature.
-
-
Install and activate OESAuthorizationFeature for the specified site using one of the following commands.
The OES Authorization Feature can be activated separately for each web and sub-web site by going to Site Settings ->Modify All Site Settings-> Site Features. If it is activated against a sub-web, all web parts in the web pages inside the sub-web may be access controlled.
-
If using MOSS 2007 (IIS 6), open a command prompt and execute the following commands.
“C:\Program Files\Common Files\Microsoft Shared\web server extensions\12\BIN\STSADM.EXE” –o installfeature –name OESAuthorizationFeature “C:\Program Files\Common Files\Microsoft Shared\web server extensions\12\BIN\STSADM.EXE” –o activatefeature –name OESAuthorizationFeature –url http://alesw2k3:9581
-
If using MOSS 2010 (IIS 7), open a command prompt and execute the following commands:
“C:\Program Files\Common Files\Microsoft Shared\web server extensions\14\BIN\STSADM.EXE” –o installfeature –name OESAuthorizationFeature “C:\Program Files\Common Files\Microsoft Shared\web server extensions\14\BIN\STSADM.EXE” –o activatefeature –name OESAuthorizationFeature –url http://aleswin2k8:9581
-
-
Restart the IIS Server.
-
Obtain a list of all the SharePoint server protected resources using
MOSSResourceDiscovery.exelocated in the%OES_CLIENT_HOME%\oessm\mosssm\libdirectory.Note:
MOSS resources are mapped hierarchically to resources in Oracle Entitlements Server. Thus, all discovered resources need not to be defined in the policy store. For example, rather than copying 10,000 individual document names, copy the name of the folder in which these documents are located and write policies using a Resource Name Expression; for example,
/lib/*.The MOSS Security Module contains this executable to generate a plain text file named
object1and an XML file nameddiscovered-jazn-data.xml. Both files define the MOSS resources. TheMOSSResourceDiscovery.exeexecutable prompts for the following information.-
The path to a directory in which the files will be created; for example,
c:\inetpub\wwwroot\wss\VirtualDirectories\9581\policy. This directory must be created beforehand. -
The path to the directory in which the Admin Url file is located; for example, $OES_CLIENT_HOME
/oessm/mosssm/adm/Discovery/AdmUrls.txt. -
The Sharepoint Server site URL; for example,
http://amw2k8:9581. Do not append the URL with a forward slash (/). -
The name of the Oracle Entitlements Server Application object that represents the MOSS application; for example,
MossApp. -
The name of the Oracle Entitlements Server Resource Type; this value should always be
MossResourceType.
The XML file can be used by the policy migration tool. See Section 13.5, "Migrating Policies" for details. The text file is used to import the resources into the Oracle Entitlements Server policy store in the next step.
-
-
Import the MOSS resources into the Oracle Entitlements Server policy store by using the text file as input to
manage-policy.cmd|sh, the policy management tool.manage-policy.cmd|shis located in the%OES_CLIENT_HOME%\oessm\bindirectory. The import appends the MOSS resources to the policy store; any existing MOSS Applications (and related policies) will not be deleted. The input values (Application name, Resource Type and generated resource file) should be consistent with the input used by MOSSResourceDiscovery.exe in the previous step.Before running
manage-policy.cmd|sh, modify the script as follows:-
Change the
OES_CLIENT_HOMEandOES_INSTANCE_NAMEvariables to reflect the user's environment. -
Configure the
jps-config.xmlPolicy Store attributes as defined in Appendix A, "Policy Store Service Configuration."
This tool is only run once. New resources are manually created using the Administration Console.
-
-
Distribute the policies using the Administration Console.
9.3 Securing Oracle Service Bus Resources
Oracle Service Bus (OSB) is designed to centrally manage and control many distributed service endpoints. Oracle Entitlements Server enables an enterprise to control access to OSB runtime resources, allowing them to become accessible only after authorization. In general, OSB runtime resources are those resources passed to the isAccessAllowed() authorization API.
Note:
Oracle Entitlements Server does not secure resources used during OSB configuration such as the OSB console.
The following sections contain detailed information on the OSB resource object and how to map its values to Oracle Entitlements Server policy objects.
-
Section 9.3.2, "Mapping Secure OSB Resources to Oracle Entitlements Server"
-
Section 9.3.3, "Mapping Non-secure OSB Resources to Oracle Entitlements Server"
9.3.1 Examining the OSB Resource Object
OSB runtime resources are represented as objects. The object representing the resource contains a string array of KEYS that define values representing the object's context; for example, the OSB project or task. In order to secure OSB resources, the creation of Oracle Entitlements Server security objects used to define an Authorization Policy must mirror the values that will be passed in the resource object's KEYS. The following list are the KEYS that will be defined in an OSB resource object. The type of this OSB resource object is always <alsb-proxy-service>.
-
proxy defines the name of the OSB proxy service associated with the protected resource. The value uniquely identifies one OSB proxy service.
-
path defines the full path to the OSB proxy service; for example,
Project-name/Folder-namewhere:-
Project-name is the name of the OSB project with which the proxy service is associated.
-
Folder-name is an optionally defined directory structure for the proxy service. Multiple directories may be defined using the
/string separator as in/folder_name/sub_folder_name.
The value uniquely identifies the same OSB proxy service as the one referenced for proxy.
-
-
action defines whether entry to the OSB proxy service will be secure or not and takes one of the following values:
-
invoke represents access control on entry to an OSB proxy service.
-
wss-invoke represents secure access control on entry to an operation of an OSB proxy service. With this action, OSB Web Service Security is configured.
-
-
operation defines the name of the Web service operation being invoked. If the action is invoke, this value is null.
Note:
When the OSB proxy service uses Web Service Security, OSB performs security checks at the transport layer and the message layer. At the transport layer, OSB checks if the user is allowed to access the proxy service; at the message layer, it checks if the user is allowed to do the specified proxy service operation. Thus, if no user information is passed into the transport layer, an additional policy will be needed to grant access privileges to the Anonymous role.
Mapping OSB resources to Oracle Entitlements Server policy objects is dependent on the chosen secure or non-secure action. See Section 9.3.2, "Mapping Secure OSB Resources to Oracle Entitlements Server" and Section 9.3.3, "Mapping Non-secure OSB Resources to Oracle Entitlements Server" for details.
9.3.2 Mapping Secure OSB Resources to Oracle Entitlements Server
When the OSB resource object defines a wss-invoke action, the applicable OSB proxy service uses OSB Web Service Security. Let's assume an OSB proxy service named SampleProxyService is associated with the OSB project named SampleProject and is configured to use OSB Web Service Security. This service resource is in the Mortgage/ProxyService folder. Thus, the KEYS values are as follows:
-
path: SampleProject/Mortgage/ProxyService
-
proxy: SampleProxyService
-
action: wss-invoke
-
operation:
sayHello(Suppose the Web Service action is sayHello)
Based on the KEYS values, the Oracle Entitlements Server object values are:
-
Application - It is mandatory to name the Application used for securing OSB resources as
alsbProxyServices. -
Resource Type - This value should always be the OSB object type
alsb-proxy-service. Also select yes as the value of the Supports Resource Hierarchy parameter.Note:
It is not necessary to add
wss-invokeas an action for thealsb-proxy-serviceResource Type; just select the operation for the policy. -
Resource - SampleProject/Mortgage/ProxyService/SampleProxyService/sayHello (takes a value equal to the values of the OSB resource object's path/proxy
KEYSvalues) -
Action -
access(access, the default Oracle Entitlements Server privilege, is always used)
9.3.3 Mapping Non-secure OSB Resources to Oracle Entitlements Server
When the OSB resource object defines an invoke action, the applicable OSB proxy service does not use OSB Web Service Security. Let's assume an OSB proxy service resource named SampleProxyService that is associated with the OSB project named SampleProject. This service resource is in the Mortgage/ProxyService folder. Thus, the KEYS values are as follows:
-
path: SampleProject/Mortgage/ProxyService
-
proxy: SampleProxyService
-
action: invoke
-
operation: null
Based on the KEY values, if not configured with OSB Web Service Security, the Oracle Entitlements Server object values are:
-
Application - alsbProxyServices (the OSB resource object does not have a defined value so this default value is used)
-
Resource Type - This value should always be the OSB object type
alsb-proxy-service. Also select yes as the value of the Supports Resource Hierarchy parameter. -
Resource - SampleProject/Mortgage/ProxyService/SampleProxyService (takes a value equal to the values of the OSB resource object's path/proxy
KEYSvalues) -
Action - access (if operation has a value, this value is used; if not, access, the default Oracle Entitlements Server privilege, is used)
9.3.4 Enabling the WebLogic Server Providers
The Oracle Entitlements Server Proxy Provider must be enabled to secure and protect OSB runtime resources as well. Section 9.4.1, "Integrating with WebLogic Server" contains the procedure for accomplishing this.
9.4 Securing WebLogic Server Resources
Besides providing the authorization API to accept authorization requests, the WebLogic Server Security Module allows protection of WebLogic Server-specific resources after configuring the specific Oracle Entitlements Server Authorization and Role Mapping providers. The following high-level procedure documents the tasks to secure WebLogic Server resources.
-
Enable the Authorization and Role Mapping providers.
-
Discover the resources to be protected with Discovery Mode.
-
Define the WebLogic Server-specific resources as Oracle Entitlements Server objects.
See Section 9.4.3, "Converting WebLogic Server Resources" and Section 9.4.4, "Mapping WebLogic Server Resources to Policy Objects."
-
Configure the appropriate Authorization and Role Mapping policies.
-
Distribute the policies to the Security Module.
9.4.1 Integrating with WebLogic Server
As discussed in Section 1.3.2.2, "Security Module as Combination PDP / PEP," WebLogic Server can automatically intercept authorization requests after enabling the Role Mapping and Authorization providers. The following procedure explains how to do this; it assumes the WebLogic Server is installed in the $WLS directory in the $DOMAIN domain. Replace the values based on your installation when following the procedure.
-
Start the
$DOMAINdomain using the following command.$DOMAIN/startWeblogic.sh
-
Add the Authorization Proxy and Role Mapping providers to the realm that protects the domain.
Figure 9-1 is a screenshot of the WebLogic Server console that illustrates this.
Figure 9-1 Adding Providers to the WebLogic Server Domain's Realm
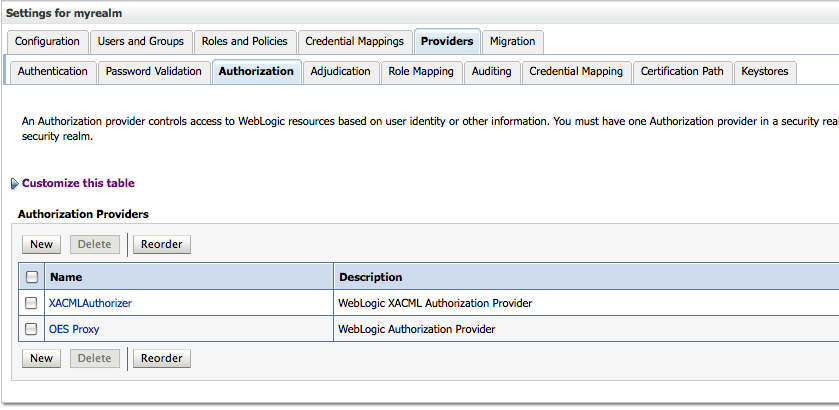
Description of "Figure 9-1 Adding Providers to the WebLogic Server Domain's Realm"
-
Restart the domain.
After enabling the providers, see Section A.2.5, "WebLogic Server Security Module" for the configuration parameters.
9.4.2 Discovering WebLogic Server Resources
When writing policy to secure an application's resources, all resources that must be secured must be discovered. By running the WebLogic Server Security Module in Discovery Mode and opening one or more user sessions (to track usage), the application's resources can be defined. (Discovery Mode does not authorize; it discovers objects to be protected.) Based on the activities performed during the user session, Oracle Entitlements Server will generate an initial policy set (that defines all resources to be protected); this policy set can then be imported into the policy store.
Note:
The generated files are meant to serve as a starting point for defining a policy set to fully secure the application. In particular:
-
The recorded policy data is based only on requests made during the user session; no policy data will be generated for parts of the application that are not used.
-
Depending on the Resource hierarchy you use to define the application's resources, the imported policy set may contain more Resources than actually needed.
Resource discovery is enabled when the Authorization and Role Mapping providers run in Discovery Mode. In this mode, these providers always return true when evaluating user requests and generate the initial policy files based on those requests. Discovery Mode may find Applications, Resource Types (and corresponding actions), the Resource Type matcherClass name, and Resources. The following sections contain more information.
9.4.2.1 Enabling Discovery Mode
By default, Discovery Mode is off. Setting the oracle.security.jps.discoveryMode property to true (in jps-config.xml) enables the feature. Adding a directory value for the oracle.security.jps.discoveredPolicyDir property defines where the policy set will be written.
Note:
Discovery Mode does not generate parent Resources for hierarchical Resource Types. If the administrator knows that all Resource Types to be discovered are hierarchical, add the appropriate values to the optional oracle.security.jps.discoveredResourceIsHierarchical and oracle.security.jps.discoveredResourceNameDelimiter properties.
See Appendix A, "Installation and Configuration Parameters" for additional details on these configuration parameters.
9.4.2.2 Loading Discovered Resources
The resulting Discovery Mode file follows the jazn-data.xml schema and is a standard XML policy store file as illustrated in Example 9-8. Use the Oracle Entitlements Server API to create the discovered objects as Authorization Policy objects in the policy store. See Section 13.5, "Migrating Policies" for information.
Example 9-8 Sample File Of Discovered Resources
<?xml version = '1.0' encoding = 'UTF-8' standalone = 'yes'?>
<jazn-data xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:noNamespaceSchemaLocation=
"http://xmlns.oracle.com/oracleas/schema/jazn-data-11_0.xsd">
<policy-store>
<applications>
<application>
<name>addConfRes#V2.0</name>
<resource-types>
<resource-type>
<name>FileResourceType</name>
<matcher-class>oracle.security.jps.JpsPermission</matcher-class>
<actions-delimiter>,</actions-delimiter>
<actions>delete,write,read</actions>
</resource-type>
<resource-type>
<name>ResType1</name>=
<actions-delimiter>,</actions-delimiter>
<actions>write,read</actions>
</resource-type>
</resource-types>
<resources>
<resource>
<name>EmpInfo</name>
<type-name-ref>FileResourceType</type-name-ref>
</resource>
<resource>
<name>resource1</name>
<type-name-ref>ResType1</type-name-ref>
</resource>
</resources>
</application>
</applications>
</policy-store>
</jazn-data>
9.4.3 Converting WebLogic Server Resources
This section describes how Oracle Entitlements Server converts the different resource types supported by WebLogic Server and how they are represented in the Oracle Entitlements Server Administration Console. A WebLogic Server resource is an object that the WebLogic Security Service creates to represent an underlying WebLogic Server entity; it is used to determine who can access the entity.
An Authorization Policy defines, among other objects, a top-level Application, a Resource Type and the actual Resource to be protected. The objects may include those documented in Table 9-4.
Table 9-4 WebLogic Server Authorization Policy Objects
| Node | Description |
|---|---|
|
Application |
The Application corresponds to the application with which the Resource is associated. Not every resource belongs to a specific Application; for example, a JDBC resource does not. In these cases, |
|
Resource Type |
The Resource Type corresponds to the supported WebLogic Server resource types as defined in Section 9.4.4. The Resource Type name is defined when the Resource Type is created using the Administration Console; for example, |
|
Resource |
The Resource is the instance of the Resource Type that is being protected. The Resource can be hierarchical (as a directory in which protection is afforded to all contents) or a specific file. The Resource Type from which the Resource instance is created must first be defined as hierarchical. |
9.4.4 Mapping WebLogic Server Resources to Policy Objects
This section describes how to map Oracle Entitlements Server policy objects to WebLogic Server resources defined for common external resources. WebLogic Server supports the following Resource Type values: adm, app, com, eis, ejb, jdbc, jms, jndi, ld, svr, url, web, webservices. It contains information on the following types of resources.
9.4.4.1 Enterprise Java Bean Resources
When defining objects for a policy that will be used to protect an Enterprise Java Bean (EJB) resource, policy objects should be named based on values defined in the standard EJB deployment descriptor, ejb-jar.xml. Example 9-9 illustrates how one EJB named AccountService might be defined.
Example 9-9 Defining an EJB Resource in ejb-jar.xml
<enterprise-beans>
<!-- Session Beans -->
<session>
<display-name>AccountService</display-name>
<ejb-name>AccountService</ejb-name>
<home>com.bea.security.examples.ejb.AccountServiceHome</home>
<remote>com.bea.security.examples.ejb.AccountService</remote>
<ejb-class>ejb.AccountServiceSession</ejb-class>
<session-type>Stateless</session-type>
<transaction-type>Bean</transaction-type>
</session>
</enterprise-beans>
Table 9-5 contains the mappings that should be used when defining policy objects for use with an EJB resource.
Table 9-5 Mapping EJB Definitions to Policy Objects
| Policy Object Name | EJB Definition |
|---|---|
|
Application |
Same as the EJB name; in this case, |
|
Resource Type |
Use the value |
|
Resource name |
ejb_name/method_name where:
The EJB method is part of the resource URL. The Resource action is always |
The following list documents the attributes supported by JNDI resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
-
application: name of the application
-
module: name of the module
-
ejb: name of the EJB
-
method: name of the method
-
methodinterface: Takes as a value Home, Remote, LocalHome, or Local
-
ParamN: A value of the Nth parameter in the method; for example, Param1, Param2…
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
9.4.4.2 Java Naming and Directory Interface Resources
When defining objects for a policy that will be used to protect Java Naming and Directory Interface (JNDI) based resources, policy objects should be named based on values defined in theWebLogic-specific deployment descriptor, weblogic-ejb-jar.xml. Example 9-10 illustrates how an EJB named AccountService might be defined with a JNDI name.
Example 9-10 Defining a JNDI Resource in weblogic-ejb-jar.xml
<weblogic-ejb-jar>
<weblogic-enterprise-bean>
<ejb-name>AccountService</ejb-name>
<stateless-session-descriptor></stateless-session-descriptor>
<reference-descriptor></reference-descriptor>
<jndi-name>AccountService</jndi-name>
</weblogic-enterprise-bean>
</weblogic-ejb-jar>
Table 9-6 contains the mappings that should be used when defining policy objects for use with a JNDI based resource.
Table 9-6 Mapping JNDI Definitions to Policy Objects
| Policy Object Name | JNDI Definition |
|---|---|
|
Application |
shared |
|
Resource Type |
jndi |
|
Resource |
Not used |
The action for a JNDI call is the JNDI action name. The value can be one of the following.
-
modifyis required whenever an application modifies (add, remove, change) the JNDI tree in any way. This includes thebind(),rebind(),createSubContext(),destroySubContext(), andunbind()methods. -
lookupis required whenever an application looks up an object in the JNDI tree. This includes thelookup()andlookupLink()methods. -
listis required whenever an application lists the contents of a context in JNDI. This includes thelist()andlistBindings()methods.
The following list documents the attributes supported by JNDI resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
-
application - Always shared
-
path - The JNDI resource path
-
action - the JNDI action name (modify | lookup | list)
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
9.4.4.3 URL Resources
A URL (Web) resource is a specific WebLogic Server resource related to Web applications. To secure Web applications, create Authorization Policies for a Web Application aRchive (WAR) or for individual components of the Web application (such as servlets and JSPs). Table 9-7 describes how to name the Oracle Entitlements Server objects when securing a URL resource. These values are defined when the objects are created using the Oracle Entitlements Server Adminstration Console.
Table 9-7 URL Resource Values Mapped to Oracle Entitlements Server Objects
| OES Object Name | URL Resource Value |
|---|---|
|
Application |
Takes as a value the web application name (defined in the WebLogic Server configuration file) that is (or contains) the resource; for example, |
|
Resource Type |
Takes as a value one of the supported resource types; in this case, |
|
Resource parent |
Takes as a value the context path of the web application as defined in the WebLogic Server configuration file. In the following examples, the context path is defined as |
|
Resource |
Takes as a value the resource URI after the context path. In this case, |
To illustrate how to create an Authorization Policy for a URL resource, let's assume we want to protect Web resources accessible through different banking related JSP. The WebLogic Server configuration file references the web application name as bankapp with the context path /currencyExchange (for the first two policies) and /mybroker (for the last two policies). In the case of a URL resource, the action name is mapped to the HTTP request method name (GET, POST, PUT, HEAD, DELETE, TRACE, CONNECT, and the like).
The first Authorization Policy example grants any unauthorized user (anonymous) permission to view current currency exchange rates (currentRates.jsp) if the connection through which the page is being accessed is secure (HTTPS). Create the following objects using the Administration Console:
-
Application = bankapp
-
Resource Type = url
-
Resource = currencyExchange/currentRates.jsp
-
Action = GET
-
User = anonymous (unauthorized)
-
Condition = if issecure=yes
Notice the GET action is part of the Authorization Policy; it is not the action of the Authorization Policy. The full range of actions allowed on the Resource Type are always defined as part of the Resource Type profile. The policy action is always equal to GRANT or DENY.
The second Authorization Policy example grants any member of the Manager role permission to post new currency exchange rates (postNewRates.jsp) if the user updates the data from the local machine. Create the following objects using the Administration Console:
-
Application = bankapp
-
Resource Type = url
-
Resource = currencyExchange/postNewRates.jsp
-
Action = POST
-
Role = Manager
-
Condition = if remotehost="localhost"
Notice the POST action is part of the Authorization Policy; it is not the action of the Authorization Policy. The full range of actions allowed on the Resource Type are always defined as part of the Resource Type profile. The policy action is always equal to GRANT or DENY.
The third Authorization Policy example grants access to buyStocks.jsp if the customer has positive purchasing power. The page will not be displayed if a customer's purchasing power is not positive. To decipher purchasing power, when the customer clicks on the buyStocks.jsp link, the browser sends an HTTP request mapped to a Java servlet. The servlet sets a request attribute named purchasingPower and forwards the request to a second page that is responsible for fetching balances from all of the customer's accounts, calculating the amount of money that can be spent on buying new stocks (purchasing power) and populating the purchasingPower attribute with a value. Create the following objects using the Administration Console:
-
Application = bankapp
-
Resource Type = url
-
Resource = mybroker/buyStocks.jsp
-
Action = GET
-
Role = Client
-
Condition = if purchasingPower>0
Notice the GET action is part of the Authorization Policy; it is not the action of the Authorization Policy. The full range of actions allowed on the Resource Type are always defined as part of the Resource Type profile. The policy action is always equal to GRANT or DENY.
The fourth Authorization Policy allows a customer to open an account for trading stocks only if the Trading Agreement has been accepted (by ticking the checkbox). After clicking the openAccount.jsp link, the first page displayed contains the Trading Agreement and asks the customer to accept it. The checkbox is linked to an HTML form parameter named customerAgreed. When the HTML form is posted, this parameter is set to true if the customer has accepted the trading agreement. The policy checks for this value in the customerAgreed HTTP request parameter. Create the following objects using the Administration Console:
-
Application = bankapp
-
Resource Type = url
-
Resource = mybroker/openAccount.jsp
-
Action = POST
-
Role = Client
-
Condition = if Not customerAgreed="true"
Notice the POST action is part of the Authorization Policy; it is not the action of the Authorization Policy. The full range of actions allowed on the Resource Type are always defined as part of the Resource Type profile. The policy action is always equal to GRANT or DENY.
Table 9-8 documents the dynamic attributes supported by URL resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
Table 9-8 Dynamic Attributes Supported by URL Resources
| Attribute Name | Value |
|---|---|
|
application |
The name of the web application. |
|
contextpath |
The context path of the web application. |
|
uri |
The URI of the resource. |
|
httpmethod |
The HTTP method (same as action). |
|
transporttype |
The transport guarantee required to access the URL resource, as it appears in the corresponding <transport-guarantee> element in the deployment descriptor. The value can be one of INTEGRAL or CONFIDENTIAL. |
|
authtype |
The name of the authentication scheme used to protect the servlet. The value can be one of: BASIC, FORM, CLIENT_CERT or DIGEST. |
|
pathInfo |
Extra path information associated with the URL sent by the client when it made a request. |
|
pathtranslated |
Extra path information after the servlet name but before the query string is translated to a real path. |
|
querystring |
The query string that is contained in the request URL after the path. |
|
remoteuser |
The login of the user making the request, if the user has been authenticated. |
|
requestedsessionid |
The session ID specified by the client. |
|
requesturi |
The part of this request's URL from the protocol name up to the query string in the first line of the HTTP request. |
|
requesturl |
The URL used by the client to make the request. The returned URL contains a protocol, server name, port number, and server path, but it does not include query string parameters. |
|
servletpath |
The part of this request's URL that calls the servlet. |
|
characterencoding |
The character encoding used in the body of the request. |
|
contenttype |
The MIME type of the body of the request. |
|
locale |
The preferred Locale of the client. |
|
protocol |
The name and version of the protocol, for example, HTTP/1.1. |
|
remoteaddr |
The Internet Protocol address of the client or last proxy that sent the request. |
|
remotehost |
The fully qualified name of the client or the last proxy that sent the request. |
|
scheme |
The name of the scheme used to make this request, for example, http, https, or ftp. |
|
servername |
The host name of the server to which the request was sent. |
|
serverport |
The port number to which the request was sent. |
|
issecure |
A boolean indicating whether this request was made using a secure channel, such as HTTPS. |
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
HTTP requests may contain elements such as servlet attributes, URL query parameters, HTTP request headers and cookies. These elements, available as name/value pairs, can be mapped to dynamic attributes.
Note:
The attributes that correspond to servlet attributes, URL query parameters, HTTP request headers and cookies are case insensitive; however, an assumption that the attribute names are case sensitive will slightly improve the performance.
The order in which the framework searches for a matching attribute is:
-
URL query parameters - are name/value pairs appended to a URL. The attribute names that correspond to the parameters in a URL query string are the same as the parameter names. The names are represented as strings and are case insensitive. The attributes refer to the query string variable encoded within the request. For example, if a URL includes a query such as
?test=endcoded%20char, the parameter can be accessed in the Condition of an Authorization Policy as:"if test= "encoded char" -
Servlet attributes - are name/value pairs that can be added to a request internally by a servlet container. Usually this is accomplished by calling the
setAttributemethod of theServletRequestinterface. The policy attribute names correspond to the names of servlet attributes, and are represented as strings and case insensitive. -
HTTP request headers - The attribute name of an HTTP request header corresponds to the name of the header. The name is returned as a string and is case insensitive. Examples of the available headers are: date, if-modified-since, referrer, or user-agent. (The date header, usually a date type, is returned as a string.)
-
cookies - The attribute names that correspond to cookies in an HTTP request are the same as the cookie name in the request. The names are returned as strings and case insensitive. The value of the cookie returned is application-specific and may need further decoding.
Note:
If the names of a servlet attribute, URL query parameter, HTTP request header or cookie collide, only one attribute will be available in policy constraints.
9.4.4.4 JDBC Resources
A Java DataBase Connectivity (JDBC) resource is a WebLogic Server resource that is related to JDBC. You can secure JDBC resources that are deployed as a service or as an application. To secure JDBC database access, create Authorization Policies for all data sources as a group, individual data sources, and multiple data sources. Example 9-11 shows how a JDBC resource named MyJDBCConnectionPool could be defined in the WebLogic Server configuration file, config.xml.
Example 9-11 Defining a JDBC Resource in config.xml
<JDBCConnectionPool DriverName="oracle.jdbc.driver.OracleDriver"
Name="MyJDBCConnectionPool"
PasswordEncrypted="{3DES}B2Bl+tp70Eh3D1pT53/anw=="
Properties="user=wles" Targets="myserver"
TestTableName="SQL SELECT 1 FROM DUAL"
URL="jdbc:oracle:thin:@localhost:1521:ASI"/>
<JDBCTxDataSource JNDIName="MyDataSource"
Name="MyJDBCDataSourceName"
PoolName="MyJDBCConnectionPool"
Targets="myserver"/>
Table 9-9 describes how to name the Oracle Entitlements Server objects in the case of securing the JDBC resource, MyJDBCConnectionPool. These values are defined when the objects are created using the Oracle Entitlements Server Adminstration Console
Table 9-9 JDBC Values Mapped to Oracle Entitlements Server Objects
| OES Object Name | JDBC Value |
|---|---|
|
Application |
A JDBC resource does not belong to a specific Application. In these cases, |
|
Resource Type |
Takes as a value one of the supported resource types; in this case, |
|
Resource parent |
Takes as a value the module name (if any) plus the pool type (ConnectionPool or MultiPool); in this case, ConnectionPool. |
|
Resource |
Takes as a value the name of the JDBC resource as defined in |
To illustrate how to create policy objects using Oracle Entitlements Server for a JDBC resource, let's assume we want to grant members of the ExternalApplication role permission to reserve (open) a JDBC connection from a connection pool called ExternalDataPool. Create the following objects using the Administration Console:
-
Application = shared
-
Resource Type = jdbc
-
Resource = ConnectionPool/ExternalDataPool
-
Action = reserve
This second group of objects will be used in a policy to grant members of the Admin role permission to shut down any JDBC resource except the resource named SystemJdbcPool. Create the following objects using the Administration Console:
-
Application = shared
-
Resource Type = jdbc
-
Resource = ConnectionPool/ExternalDataPool
Note that the//app/policy/mybank/shared/jdbcresource must be a virtual one. -
Action = admin
-
Condition = if Not resource="SystemJdbcPool"
Notice the reserve and admin actions are part of the Authorization Policies; it is not the action of the Authorization Policy. The full range of actions allowed on the Resource Type are always defined as part of the Resource Type profile. The policy action is always equal to GRANT or DENY. Table 9-10 documents the specific actions that can be performed on a JDBC resource and thus must be defined as actions of the Resource Type.
Table 9-10 JDBC Resource Action Options
| Action Name | Operation |
|---|---|
|
admin |
Action to perform the admin operations such as clearStatementCache, suspend, forceSuspend, resume, shutdown, forceShutdown, start, getProperties, and poolExists. |
|
reserve |
Action to reserve a connection in the data source by looking up the data source and then calling getConnection. |
|
shrink |
Action to shrink the number of connections in the data source. |
|
reset |
Action to reset the data source connections by shutting down and re-establishing all physical database connections. |
Example 9-12 is sample code that uses the JDBC resource previously defined. It calls the getConnection() method on the data source instance. This initiates an authorization check to verify the reserve action against the //app/policy/AppParentNode/shared/jdbc/ConnectionPool/MyJDBCConnectionPool resource.
Example 9-12 Initiating Authorization on JDBC Resource
javax.naming.InitialContext initialContext = new javax.naming.InitialContext();
javax.sql.DataSource ds = (javax.sql.DataSource)
initialContext.lookup("MyDataSource");
java.sql.Connection conn = ds.getConnection();
PreparedStatement statement =
conn.prepareStatement("SELECT accountName FROM accounts WHERE balance < 0");
ResultSet result = statement.executeQuery();
if (result.next()) {
String accountName = result.getString(1);
System.out.println("The first account with negative balance is " + accountName);
}
Table 9-11 documents the attributes supported by JDBC resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
Table 9-11 Dynamic Attributes Supported by JDBC Resources
| Attribute Name | Element |
|---|---|
|
application |
The name of an application that hosts the resource |
|
module |
The name of a module to which the resource belongs |
|
category |
The resource type (ConnectionPool | MultiPool) |
|
resource |
The name of the resource |
|
action |
The JDBC operation name (admin | reserve | shrink | reset) |
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
9.4.4.5 JMS Resources
A Java Messaging Service (JMS) resource is a WebLogic Server resource related to JMS. You can secure JMS resources that are deployed as a service or as an application. To secure JMS destinations, create Authorization Policies for all destinations (JMS queues and JMS topics) as a group, or individually (one JMS queue or JMS topic on a JMS server). Table 9-12 describes how to name the Oracle Entitlements Server objects in the case of securing a JMS resource. These values are defined when the objects are created using the Oracle Entitlements Server Adminstration Console.
Table 9-12 JMS Values Mapped to Oracle Entitlements Server Objects
| OES Object Name | JMS Value |
|---|---|
|
Application |
A JMS resource does not belong to a specific Application. In these cases, |
|
Resource Type |
Takes as a value one of the supported resource types; in this case, |
|
Resource parent |
The destination type (topic or queue) |
|
Resource |
The resource name |
Example 9-13 configures a JMS queue named MyJMSQueue in the WebLogic Server configuration file, config.xml.
Example 9-13 Defining a JMS Queue Resource in config.xml
<JMSServer Name="WSStoreForwardInternalJMSServermyserver"
Store="FileStore" Targets="myserver">
<JMSQueue CreationTime="1150241964468"
JNDIName="JMSQueue" Name="MyJMSQueue"/>
</JMSServer>
<JMSConnectionFactory JNDIName="JmsConnectionFactory"
Name="MyJMSConnectionFactory" Targets="myserver"/>
Example 9-14 illustrates a JMS client that uses the JMS queue previously declared. The client sends a text message to MyJMSQueue.
Example 9-14 JMS Client Example
//Instantiate the inital context
javax.naming.InitialContext initialContext = new javax.naming.InitialContext();
//Look up the JMS connection factory and the message queue
Queue messageQueue = (Queue) initialContext.lookup("JMSQueue");
JMSConnectionFactory factory =
(JMSConnectionFactory) initialContext.lookup("JmsConnectionFactory");
//Create the queue connection and session
QueueConnection queueConnection = factory.createQueueConnection();
QueueSession session =
queueConnection.createQueueSession(false, Session.AUTO_ACKNOWLEDGE);
//Create a text message
TextMessage textMessage = session.createTextMessage();
textMessage.setText("Hello from the client!");
//Send message to the queue
QueueSender sender = session.createSender(messageQueue);
sender.send(textMessage);
To illustrate how to create an Authorization Policy for a JMS resource, let's assume we want to grant members of the Client role permission to send messages to a JMS queue named FeedbackQueue. Create the following objects using the Administration Console:
-
Application = shared
-
Resource Type = jms
-
Resource = queue/FeedbackQueue
-
Action = send
-
Role = Client
This second Authorization Policy grants the FeedbackProcessor user permission to receive messages from a JMS queue named FeedbackQueue.
-
Application = shared
-
Resource Type = jms
-
Resource = queue/FeedbackQueue
-
Action = send
-
user = myusers/FeedbackProcessor
Notice the actions (send and receive) are part of the Authorization Policies. The policy outcome is always equal to GRANT or DENY. Table 9-13 documents the specific actions that can be performed on a JMS resource.
Table 9-13 JMS Resource Action Options
| Action | Description |
|---|---|
|
send |
Required to send a message to a queue or a topic. This includes calls to the |
|
receive |
Required to create a consumer on a queue or a topic. This includes calls to the |
|
browse |
Required to view the messages on a queue using the QueueBrowser interface. |
Table 9-14 documents the attributes supported by JMS resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
Table 9-14 Dynamic Attributes Supported by JMS Resources
| Attribute Name | Description |
|---|---|
|
application |
The name of an application that hosts the resource |
|
destinationtype |
The JMS destination type (queue | topic) |
|
resource |
The name of the resource |
|
action |
The JDBC operation name (send | receive | browse). |
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
9.4.4.6 Web Services Resources
A Web Services resource is a WebLogic Server resource related to a Web service. To secure Web services, create Authorization Policies for the entire Web Service resource, for a subset of the Web Service resource operations, for the stateless session EJB that implements the Web Service resource, or for a subset of the methods within the stateless session EJB. Example 9-15 shows the configuration of a web application named BasicWS that contains a Web service implementation named BasicWS_Component.
Example 9-15 Web Application Configuration
<application Name="BasicWS"
Path="applications/BasicWS.ear"
StagedTargets="myserver"
<WebServiceComponent Name="BasicWS_Component"
Targets="myserver"
URI="BasicWS.war"/>
</application>
Example 9-16 shows how the application.xml file within the BasicWS.ear defines the web application context.
Example 9-16 Web Application Context Configuration
<module>
<web>
<web-uri>basic_javaclass.war</web-uri>
<context-root>myservices</context-root>
</web>
</module>
Example 9-17 shows the configuration of a Web Service named HelloWorld. It is defined in the web-services.xml descriptor file inside the web application WAR file.
Example 9-17 Web Service Configuration
<web-services>
<web-service useSOAP12="false"
name="HelloWorld"
style="rpc"
uri="/HelloWorld">
<operations>
<operation name="sayHello"
method="sayHello(int,java.lang.String)"/>
</operations>
</web-service>
</web-services>
Table 9-15 describes how to name the Oracle Entitlements Server objects in the case of securing a Web resource. These values are defined when the objects are created using the Oracle Entitlements Server Adminstration Console.
Table 9-15 Web Services Values Mapped to Oracle Entitlements Server Objects
| OES Object Name | Web Services Value |
|---|---|
|
Application |
The name of the application as defined in the |
|
Resource Type |
Takes as a value one of the supported resource types; in this case, |
|
Resource parent |
Takes as a value the context path of the web service as defined in the |
|
Resource |
The Web Service name as defined in |
To call the sayHello() method in the HelloWorld Web service, the client must be granted the action sayHello. Some clients may also require access to the Web Services Definition Language (WSDL) file that defines the Web service; the WSDL file is defined as a URL resource. Example 9-18 is code that allows the client to, before calling the sayHello() method, access the WSDL file at the defined URL.
Example 9-18 Client Code For Accessing WSDL
String wsdlUrl = "http://localhost:7001//HelloWorld?WSDL"; HelloWorld service = new HelloWorld_Impl(wsdlUrl); HelloWorldPort port = service.getHelloWorldPort(); String result = port.sayHello(34, "Josh");
To successfully execute this code, the client must be granted GET permission on the WSDL file (URL resource). (Note that for the URL Resource name is lower case.) Additionally, the client must be granted GET permission on the Web Service resource. (Note that for the Web Services Resource name has initial capitalization.) Create the following objects for the URL Resource Authorization Policy using the Administration Console:
-
Application = BasicWS
-
Resource Type = url
-
Resource = myservices/helloworld
-
Action = GET
-
Role = SomeUser
Create the following objects for the Web Services Resource Authorization Policy using the Administration Console:.
-
Application = BasicWS
-
Resource Type = webservices
-
Resource = myservices/HelloWorld
-
Action = sayHello
-
Role = SomeUser
Notice the actions (GET and sayHello) are part of the Authorization Policies. The policy outcome is always equal to GRANT or DENY.
Table 9-16 documents the attributes supported by Web Services resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
Table 9-16 Dynamic Attributes Supported by Web Services Resources
| Attribute Name | Value |
|---|---|
|
application |
The name of the application |
|
contextpath |
The context part of the web application |
|
webservice |
The name of the web service |
|
method |
The name of the web service operation called |
|
ParamN |
A value of the Nth parameter in the method, for example, Param1, Param2… |
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.
9.4.4.7 Server Resources
A Server resource determines who can control the state of a WebLogic Server instance. When users start server instances by invoking the weblogic.Server class in a Java command, the policy on the Server resource is the only security check that occurs. You can create Authorization Policies that apply to all WebLogic Server instances in a domain or to individual servers. Example 9-19 is an example of how a WebLogic Server instance named myserver might be configured.
Example 9-19 Configuration of WebLogic Server Instance
<Server ListenAddress=""
ListenPort="7001"
Machine="mymachine"
Name="myserver"
NativeIOEnabled="true"
ReliableDeliveryPolicy="RMDefaultPolicy"
ServerVersion="8.1.5.0">
<SSL Enabled="false" HostnameVerificationIgnored="false"
IdentityAndTrustLocations="KeyStores" Name="myserver"/>
</Server>
Table 9-17 describes how to name the Oracle Entitlements Server objects in the case of securing the a Server resource. These values are defined when the entities are created using the Oracle Entitlements Server Adminstration Console
Table 9-17 Server Resource Values Mapped to Oracle Entitlements Server Objects
| OES Object Name | Server Resource Value |
|---|---|
|
Application |
A Server resource does not belong to a specific Application. In these cases, |
|
Resource Type |
Takes as a value one of the supported resource types; in this case, |
|
Resource |
The server instance name as defined in XXXX |
To illustrate how to create an Authorization Policy for a Server resource, let's assume we want to grant members of the Admin role permission to boot all WebLogic Server instances. Create the following objects using the Administration Console:
-
Application = shared
-
Resource Type = svr
-
Resource = /lib/*
-
Action = boot
-
Role = Admin
This second Authorization Policy grants members of the Admin role permission to shutdown or suspend a WebLogic Server instance named CentralServer. The policy is constrained in that permission is granted only on Sundays or other days between 2 AM and 4 AM.
-
Application = shared
-
Resource Type = svr
-
Resource = CentralServer
-
Action = shutdown / suspend
-
Role = Admin
-
Condition = Only on Sunday or other days between 2 AM and 4 AM
Notice the actions (boot and shutdown/suspend) are part of the Authorization Policies. The policy outcome is always equal to GRANT or DENY. Table 9-18 documents the specific actions that can be performed on a Server resource.
Table 9-18 Server Resource Action Options
| Action | Description |
|---|---|
|
boot |
Action required to start a WebLogic Server instance, either an Administration Server or Managed Server. |
|
shutdown |
Action required to shut down a running WebLogic Server instance, either an Administration Server or Managed Server. |
|
suspend |
Action required to prohibit additional logins (logins other than for privileged administrative actions) to a running WebLogic Server instance, either an Administration Server or Managed Server. |
|
resume |
Action required to re-enable non-privileged logins to a running WebLogic Server instance, either an Administration Server or Managed Server. |
Table 9-19 documents the attributes supported by Server resources that can be used as a part of a Condition in an Authorization Policy. See Section 4.6, "Using the Condition Builder" for details.
Table 9-19 Dynamic Attributes Supported by Server Resource
| Attribute Name | Value |
|---|---|
|
server |
Name of the server with which the resource is associated. |
|
action |
Name of an operation performed on the server instance (boot | shutdown | suspend | resume). |
Note:
Before using the Condition Builder, the dynamic attributes first have to be created using the Oracle Entitlements Server Administration Console. See Section 4.5.9, "Managing Attributes and Functions as Extensions" for more details.