50 Securing Oracle Service Bus with Oracle Web Services Manager
This chapter describes how to use Oracle Service Bus in conjunction with Oracle Web Services Manager (WSM) to provide a scalable, standards-based, centrally managed approach to securing your service integration environment with WS-Security policies while leveraging your existing security providers.
Oracle WSM is a runtime framework for security policy creation, management, and governance. You create policies, attach them to services in Oracle Service Bus, and enforce those policies at various points in the messaging life cycle with Oracle WSM agents.
Note:
In future releases of Oracle Service Bus, Oracle WSM policies will replace and enhance the functionality of WLS 9 security policies. While this version of Oracle Service Bus continues to support WLS 9 policies, you should consider using Oracle WSM policies for new service creation to prepare for the eventual deprecation of WLS 9 policy support.
This chapter includes the following sections:
-
Section 50.1, "About Oracle Web Services Manager Integration with Oracle Service Bus"
-
Section 50.2, "Setting Up and Using Oracle Web Services Manager with Oracle Service Bus"
-
Section 50.3, "Use Cases: Oracle Service Bus and WLS 9 Policies with Oracle Web Services Manager"
For more information about Oracle Web Services Manager, see the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
50.1 About Oracle Web Services Manager Integration with Oracle Service Bus
Oracle WSM is a component of the Oracle Enterprise Manager Fusion Middleware Control, a runtime framework that provides centralized management and governance of Oracle SOA Suite environments and applications. You create and configure Oracle WSM policies in Oracle Enterprise Manager, and those policies are persisted in a policy store (a database is recommended). Oracle WSM lets you define policies against an LDAP directory and generate standard security tokens (such as SAML tokens) to propagate identities across multiple Web services used in a single transaction.
In Oracle Service Bus, when defining a business or proxy service that lets you attach security policies, you can attach available Oracle WSM policies.
Because Oracle WSM is a runtime component, attaching policies to Oracle Service Bus services requires a connection to an Oracle Service Bus domain that has Oracle WSM enabled. For example, when creating and managing services that use Oracle WSM policies in Eclipse, your Oracle Service Bus configuration must be deployed on an Oracle WSM-enabled domain to attach the policies. With no runtime connection to Oracle WSM from the development environment, you can only view or remove policies previously attached to services.
Oracle WSM support in Oracle Service Bus is not available automatically. Enable Oracle WSM support in Oracle Service Bus by selecting the "Oracle Service Bus Oracle WSM] Extension" template when you create or extend an Oracle Service Bus domain. Once Oracle WSM support is enabled in an Oracle Service Bus domain, you cannot disable it. See Section 50.2.1, "Adding Oracle Web Services Manager and Oracle Enterprise Manager to an Oracle Service Bus Domain."
50.1.1 Security Providers
This section describes the security services that Oracle Service Bus and Oracle WSM use for authentication and authorization.
Oracle Web Service Manager uses Java Platform Security (JPS), so Oracle Service Bus uses JPS providers for Oracle WSM policies. Oracle Service Bus also uses Oracle Common Security Services (CSS) for other aspects of message security.
For more information about Oracle security services, see "Introduction to Oracle Platform Security Services" in the Oracle Fusion Middleware Application Security Guide.
The following points describe which security providers Oracle Service Bus and Oracle WSM use for different security areas.
50.1.1.1 JPS Providers
When using Oracle Web Services Manager policies:
-
Oracle WSM policies use SAML providers from JPS and not from Oracle WebLogic Server. For information on configuring SAML with Oracle WSM, see "Configuring SAML" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
-
For authentication, Oracle WSM uses the JPS Login Module, which in turn calls authentication providers configured on Oracle WebLogic Server.
-
Oracle WSM and Oracle Service Bus support the Java Keystore (JKS) and the Farm Level Keystore (FKS) provided by Oracle Platform Security Services. For Oracle WSM policies, a best practice is to configure the keystore on JPS, with both the Oracle WebLogic Server and the JPS keystore referencing the same kind of keystore. For example, if you use a JKS file keystore, JPS and Oracle WebLogic Server should point to the same file. If you use an FKS keystore, JPS and Oracle WebLogic Server should point to the same FKS configuration. For more information, see Section 50.2.1, "Adding Oracle Web Services Manager and Oracle Enterprise Manager to an Oracle Service Bus Domain."
-
A JPS keystore serves as both a keystore and a truststore for Oracle WSM policies.
50.1.1.2 CSS Providers
Oracle Service Bus uses:
-
CSS providers to enforce WLS 9 policies
-
CSS providers to enforce transport security
-
Oracle WebLogic Server authorization providers for authorization policies
-
Custom Oracle WebLogic Server authentication providers and identity asserters for custom authentication policies
-
Oracle WebLogic Server credential providers and mappers
-
Oracle WebLogic Server keystore and truststore for WLS 9 policies
-
Authentication and identity assertion through Oracle Web Services Manager agents
50.2 Setting Up and Using Oracle Web Services Manager with Oracle Service Bus
This section includes the following topics:
-
Section 50.2.2, "Attaching Oracle Web Services Manager Policies to Oracle Service Bus Services"
-
Section 50.2.8, "Supported Seed Policies and Unsupported Assertions"
50.2.1 Adding Oracle Web Services Manager and Oracle Enterprise Manager to an Oracle Service Bus Domain
To use Oracle WSM policies in Oracle Service Bus, you must create the proper database schemas for the Oracle WSM policy store, then extend an Oracle Service Bus domain to include Oracle Web Services Manager.
Note:
After you add Oracle WSM to an Oracle Service Bus domain, you cannot disable Oracle WSM in the domain.
-
Use the Oracle Repository Creation Utility (RCU) to create the Oracle WSM database schemas in a supported database. Select the following schemas to create:
-
SOA and BPM Infrastructure
-
Metadata Services and AS Common Schemas are automatically selected when you select SOA Infrastructure
Make a note of the settings used to create the schemas, in particular the schema owner for Metadata Services.
For more information on running RCU, see the Oracle Fusion Middleware Repository Creation Utility User's Guide.
-
-
Extend your Oracle Service Bus domain with Oracle WSM and Oracle Enterprise Manager. Select the following domain templates when running the Oracle Fusion Middleware Configuration Wizard:
-
Oracle Service Bus OWSM Extension
-
Oracle WSM Policy Manager (automatically selected when you select the OWSM Extension)
-
Oracle Enterprise Manager (optional, needed for creating and managing Oracle WSM policies)
As part of the domain extension, the Oracle Configuration Wizard creates an OWSM MDS Schema in the JDBC configuration window. Select the schema and set the database information based on the RCU settings used to create the Oracle WSM schemas in the previous step, in particular the schema owner for Metadata Services (MDS).
For more information, see "Creating a Domain" in the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle SOA Suite.
-
-
As a best practice, configure the keystore on JPS, with both the Oracle WebLogic Server and the JPS keystore referencing the same kind of keystore. For example, if you use a JKS file keystore, JPS and Oracle WebLogic Server should point to the same file. If you use an FKS keystore, JPS and Oracle WebLogic Server should point to the same FKS configuration.
For information on creating the keystore, see "Configuring Keystores for Message Protection" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
After successful extension of the domain and creation of the keystore for Oracle WSM, you can create Oracle WSM policies using the Oracle Enterprise Manager Fusion Middleware Control and attach policies to services in Oracle Service Bus. Oracle WSM automatically provides commonly used policies.
With the domain running, you can access Oracle Enterprise Manager with the following URL:
http://host:port/em
For more information on managing Oracle WSM policies, see "Managing Web Service Policies" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
50.2.2 Attaching Oracle Web Services Manager Policies to Oracle Service Bus Services
This section provides guidelines for attaching Oracle WSM policies to Oracle Service Bus services. After you extend your Oracle Service Bus domain to include Oracle WSM and create policies using Oracle Enterprise Manager, you can attach those policies to the following types of proxy and business services in Oracle Service Bus on the Policies page:
-
WSDL (SOAP)
-
WSDL (XML)
-
Any SOAP
-
Any XML
-
Messaging
Note:
For non-SOAP WSDL, Any XML, and Messaging types, Service Bus supports a subset of the Oracle WSM policies supported for SOAP services. Policies for non-SOAP services are only supported when using the HTTP transport.
You can attach Oracle WSM policies only at the service level, and you cannot embed them in service WSDLs. For a given service, you must use either Oracle WSM policies or WLS 9 policies, but not both. You can, however, use one type of policy in a proxy service and another type in a corresponding business service.
In Eclipse, when adding Oracle WSM policies to services, you must be connected to a running domain that has Oracle WSM enabled. If you are not connected to a running server in the development environment, you can only view and remove previously added Oracle WSM policies, and Oracle Service Bus shows a warning that the Oracle WSM policies will be validated only on publish.
Note:
When working with multiple servers in Eclipse, Eclipse chooses the first valid Oracle Service Bus server in the list of servers for retrieval of Oracle WSM policies.
Oracle Service Bus provides an "Add Compatible" feature on business service configurations that lets you replace WSDL embedded WS-Security policies not natively supported by Oracle Service Bus with compatible Oracle WSM policies.
When attaching policies in the development environment, keep in mind that services in the development environment can be out of sync with services in the Oracle Service Bus Administration Console, so take care when updating services from Eclipse to the Console.
If you copy a service to create a same type of service (for example, copy a business service to create a new business service), be sure to review your Oracle WSM policies in the new service and make any necessary adjustments.
50.2.2.1 Policy Overrides
After adding Oracle WSM policies to a service, you can provide policy overrides on the Security page.
For the policies used, the user interface displays the override keys (properties) and their default values. The key names come from the policy binding. If an override is allowed, a text box appears next to a key's default value where you can provide an override value.
Oracle Service Bus does not provide well-known keys for override, such as sign key alias or CSF key, which points to user credentials in a CSF store. (Oracle Service Bus provides user credentials in the service account.)
Override keys you provide are passed to the Oracle Web Service Manager agent during invocation.
50.2.3 Configuring SAML
See Chapter 53, "Using SAML with Oracle Service Bus." For information on configuring SAML with Oracle WSM, see "Configuring SAML" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
50.2.4 Advertising WSDLs to Support WS Standards
When WSDLs contain embedded Oracle Web Service Manager policies, you can advertise the policies to be compatible with the following policy standards, supported by Oracle Service Bus and Oracle SOA Suite:
-
WS-Policy 1.2 (default) and 1.5
-
WS-Security Policy 1.1 (default), 1.2, and 1.3
Using special query parameters in URLs to access WSDLs embedded with Oracle WSM policies, Oracle Service Bus generates WSDLs that comply with the required standards. For more information on accessing WSDLs with a URL, see "Viewing Resources in a Web Browser" in the Oracle Fusion Middleware Administrator's Guide for Oracle Service Bus.
Note:
This feature is not available in the Oracle Service Bus "Export WSDL" or "Generate WSDL" functionality.
The special query parameters are &wsp (WS-Policy) and &wssp (WS-Security Policy), and you can use them in conjunction with the WSDL, PROXY, and BIZ URL patterns for retrieving WSDLs. For example:
-
http://localhost:7001/proxy/myProxy?WSDL&wsp=1.5&wssp=1.2Returns the WSDL for myProxy, a WSDL-based proxy service, so that the Oracle WSM policy reference conforms to WS-Policy 1.5 and WS-Security Policy 1.2.
Note:
In the previous URL,
/proxy/myProxyis the endpoint URI for the proxy service. -
http://localhost:7001/sbresource?PROXY/myProject/myProxy&wsp=1.5&wssp=1.2Returns the WSDL for myProxy, a WSDL-based proxy service, so that the Oracle WSM policy reference conforms to WS-Policy 1.5 and WS-Security Policy 1.2.
-
http://localhost:7001/sbresource?BIZ/myProject/myBiz&wsp=1.5&wssp=1.3Returns the WSDL for myBiz, a WSDL-based business service, so that the Oracle WSM policy reference conforms to WS-Policy 1.5 and WS-Security Policy 1.3.
-
http://localhost:7001/sbresource?WSDL/proxy/myProxyReturns the WSDL for myProxy, a WSDL-based proxy service, so that the Oracle WSM policy reference conforms to WS-Policy 1.2 and WS-Security Policy 1.1. Because no query parameters are used, Oracle Service Bus uses the defaults.
-
http://localhost:7001/proxy/myProxy?WSDL&wssp=1.3Because WS-Security Policy 1.3 is compatible only with WS-Policy 1.5, this returns the WSDL for myProxy so that the Oracle WSM policy reference conforms to WS-Security Policy 1.3 and WS-Policy 1.5.
-
Invalid Values/CombinationsWS-Security Policy 1.2 and 1.3 are compatible only with WS-Policy 1.5. For invalid value examples, see Table 50-1.
Tip:
In a Web browser, try different query parameter versions see how the returned WSDL changes.
For a quick reference of query parameter combinations, see the following section, Section 50.2.4.1, "WSDL Query Parameter Reference for WS Policies."
50.2.4.1 WSDL Query Parameter Reference for WS Policies
This section provides a quick reference showing valid and invalid combinations of the &wsp and &wssp query parameters described in the previous section, Section 50.2.4, "Advertising WSDLs to Support WS Standards."
The examples use ?WSDL to retrieve the WSDL. You can also use the ?PROXY and ?BIZ methods of WSDL retrieval, as described in "Viewing Resources in a Web Browser" in the Oracle Fusion Middleware Administrator's Guide for Oracle Service Bus.
As shown in Table 50-1, when one or more parameters is omitted, Oracle Service Bus provides the valid default. For the invalid value exceptions, WS-Security Policy 1.2 and 1.3 are compatible with only WS-Policy 1.5, and vice versa.
Table 50-1 Valid and Invalid Combinations of the &wsp and &wssp Query Parameters
| Query Parameter Combinations | WS-Policy Version | WS-Security Policy Version |
|---|---|---|
|
...?WSDL |
1.2 |
1.1 |
|
...?WSDL&wsp=1.2 |
1.2 |
1.1 |
|
...?WSDL&wsp=1.5 |
1.5 |
1.3 |
|
...?WSDL&wssp=1.1 |
1.2 |
1.1 |
|
...?WSDL&wssp=1.2 |
1.5 |
1.2 |
|
...?WSDL&wssp=1.3 |
1.5 |
1.3 |
|
...?WSDL&wsp=1.2&wssp=1.1 |
1.2 |
1.1 |
|
...?WSDL&wsp=1.5&wssp=1.2 |
1.5 |
1.2 |
|
...?WSDL&wsp=1.5&wssp=1.3 |
1.5 |
1.3 |
|
...?WSDL&wsp=1.2&wssp=1.2 |
Invalid value exception |
Invalid value exception |
|
...?WSDL&wsp=1.2&wssp=1.3 |
Invalid value exception |
Invalid value exception |
|
...?WSDL&wsp=1.5&wssp=1.1 |
Invalid value exception |
Invalid value exception |
|
...?WSDL&wsp=3.0&wssp=1.2 |
Invalid value exception |
Invalid value exception |
|
...?WSDL&wsp=1.2&wssp=2.0 |
Invalid value exception |
Invalid value exception |
50.2.5 Deployment Considerations
When you export Oracle Service Bus configurations that contain services with Oracle WSM policy references, the references are maintained. You must ensure that the referenced policies also exist in the target environment. If the target environment is the IDE, warnings are displayed saying that policies will be validated on publish.
50.2.6 Auditing
To audit policy events in Oracle Enterprise Manager, you must set up an audit data repository and set up event collection. For more information, see the following topics in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services:
-
"Viewing Audit Reports" – Pre-defined audit reports for Oracle WSM in Oracle Business Intelligence Publisher include statistics for Oracle Service Bus.
You can audit the following policy-level events:
-
Policy creation, deletion, or modification
-
Assertion template creation, deletion, or modification
50.2.7 Monitoring Statistics
Oracle Enterprise Manager policy monitoring statistics and usage/impact analysis for Oracle Service Bus are not available. Therefore, you are not able to see the impact of policy modifications on the services to which those policies are attached. However, Oracle Service Bus collects WS-Security error statistics for Oracle WSM policy enforcement errors as it does for WLS 9 policies, and those statistics are available in the Oracle Service Bus service monitoring dashboard.
50.2.8 Supported Seed Policies and Unsupported Assertions
This section lists the Oracle Web Services Manger seed policies and assertions that Oracle Service Bus supports and does not support.
User-defined assertions are supported.
Notes:
The assertion or policy "enabled/disabled" option in the Oracle Enterprise Manager Fusion Middleware Control user interface does not determine whether or not an assertion or policy is supported in Oracle Service Bus. Supported policies and assertions are listed in this section.
50.2.8.1 Supported Seed Policies
Table 50-2 lists the supported Oracle WSM seed policies for business and proxy services that are configured with the SOAP or WSDL (SOAP) service type. Table 50-3 lists the supported Oracle WSM seed policies for business and proxy services that are configured with the WSDL (non-SOAP), XML, or Messaging service type using the HTTP Transport. User-defined policies are also supported.
Notes:
In the development environment, if you use unsupported seed policies:
-
An effective WSDL generated in the development environment will skip unsupported policies.
-
Validation is performed on service publish.
For more information on the following policies, see "Predefined Policies" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
Table 50-2 Supported Oracle WSM Seed Policies for SOAP and WSDL (SOAP) Service Types
| Type | Client Policy | Service Policy |
|---|---|---|
|
Authentication only |
oracle/wss_username_token_client_policy |
oracle/wss_username_token_service_policy |
|
Authentication only |
oracle/wss10_saml_token_client_policy |
oracle/wss10_saml_token_service_policy |
|
Authentication only |
oracle/wss10_saml20_token_client_policy |
oracle/wss10_saml20_token_service_policy |
|
Authentication only |
oracle/wss11_kerberos_token_client_policy |
oracle/wss11_kerberos_token_service_policy |
|
Message Protection only |
oracle/wss10_message_protection_client_policy |
oracle/wss10_message_protection_service_policy |
|
Message Protection only |
oracle/wss11_message_protection_client_policy |
oracle/wss11_message_protection_service_policy |
|
Authentication and Message Protection |
N/A |
oracle/wss_saml_or_username_token_over_ssl_service_policy |
|
Authentication and Message Protection |
oracle/wss10_saml_hok_with_message_protection_client_policy |
oracle/wss10_saml_hok_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss10_saml_token_with_message_integrity_client_policy |
oracle/wss10_saml_token_with_message_integrity_service_policy |
|
Authentication and Message Protection |
oracle/wss10_saml_token_with_message_protection_client_policy |
oracle/wss10_saml_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss10_saml20_token_with_message_protection_client_policy |
oracle/wss10_saml20_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy |
oracle/wss10_saml_token_with_message_protection_ski_basic256_service_policy |
|
Authentication and Message Protection |
oracle/wss10_username_id_propagation_with_msg_protection_client_policy |
oracle/wss10_username_id_propagation_with_msg_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss10_username_token_with_message_protection_client_policy |
oracle/wss10_username_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy |
oracle/wss10_username_token_with_message_protection_ski_basic256_service_policy |
|
Authentication and Message Protection |
oracle/wss10_x509_token_with_message_protection_client_policy |
oracle/wss10_x509_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_kerberos_token_with_message_protection_client_policy |
oracle/wss11_kerberos_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
N/A |
oracle/wss11_saml_or_username_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_saml_token_with_message_protection_client_policy |
oracle/wss11_saml_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_saml20_token_with_message_protection_client_policy |
oracle/wss11_saml20_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_saml_token_with_identity_switch_message_protection_client_policy |
oracle/wss11_saml_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_username_token_with_message_protection_client_policy |
oracle/wss11_username_token_with_message_protection_service_policy |
|
Authentication and Message Protection |
oracle/wss11_x509_token_with_message_protection_client_policy |
oracle/wss11_x509_token_with_message_protection_service_policy |
|
Authentication only |
oracle/wss_http_token_client_policy Basic authentication only. Supported Service Bus Transports: HTTP For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_http_token_service_policy Basic authentication only. Supported Service Bus Transports: HTTP For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
oracle/wss_http_token_over_ssl_client_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_http_token_over_ssl_service_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
oracle/wss_saml_token_bearer_over_ssl_client_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_saml_token_bearer_over_ssl_service_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
oracle/wss_saml_token_over_ssl_client_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_saml_token_over_ssl_service_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
oracle/wss_username_token_over_ssl_client_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_username_token_over_ssl_service_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
N/A |
oracle/wss_saml_or_username_token_over_ssl_service_policy Supported Service Bus Transports: HTTP(S) For more information on this policy, see Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authorization only |
N/A |
oracle/whitelist_authorization_policy |
|
Authorization only |
N/A |
oracle/binding_authorization_denyall_policy |
|
Authorization only |
N/A |
oracle/binding_authorization_permitall_policy |
Table 50-3 Supported Oracle WSM Seed Policies for WSDL (non-SOAP), XML, and Messaging Service Types with HTTP Transport
| Type | Client Policy | Service Policy |
|---|---|---|
|
Authentication only |
oracle/wss_http_token_client_policy Basic authentication only. For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_http_token_service_policy Basic authentication only. For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authentication and Message Protection |
oracle/wss_http_token_over_ssl_client_policy For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
oracle/wss_http_token_over_ssl_service_policy For more information on this policy, see Section 50.2.9.1, "wss_http_token_*_policy Guidelines" and Section 50.2.9.2, "Oracle WSM Authentication Policy Guidelines." |
|
Authorization only |
N/A |
oracle/whitelist_authorization_policy |
|
Authorization only |
N/A |
oracle/binding_authorization_denyall_policy |
|
Authorization only |
N/A |
oracle/binding_authorization_permitall_policy |
50.2.8.2 Unsupported Assertions
Table 50-4 lists unsupported Oracle WSM assertions for both SOAP and non-SOAP services. The table also indicates which policies contain the assertions and describes the affected capabilities and alternatives to achieve the capabilities. Any assertions not listed are supported, including user-defined assertions.
Table 50-4 Unsupported Assertions for SOAP and non-SOAP Services
| Unsupported Assertion | Oracle WSM Policies Containing the Assertion | Capability Affected and Alternative |
|---|---|---|
|
binding-permission-authorization |
oracle/binding_permission_authorization_policy |
Permission-based access control to service. Alternative: Use XACML authorization policies. |
|
OptimizedMimeSerialization (MTOM) |
oracle/wsmtom_policy |
MTOM Alternative: Use MTOM configuration directly on proxy/business service. |
|
RMAssertion |
oracle/wsrm10_policy oracle/wsrm11_policy |
WS-RM 1.0/1.1 Alternative: Use the WS transport directly in Oracle Service Bus for WS-RM 1.0. |
|
sca-component-authorization |
oracle/component_authorization_denyall_policy oracle/component_authorization_permitall_policy |
Role-based access control to deny/permit all to access the component. Alternative: Not applicable |
|
sca-component-permission-authorization |
oracle/component_permission_authorization_policy |
Permission based Access Control to component Alternative: Not applicable |
|
UsingAddressing |
oracle/wsaddr_policy |
To require WS-Addressing Alternative: Configure WS-Addressing on business services that use the SOA-DIRECT transport; or add WS-Addressing to messages in an Oracle Service Bus pipeline. |
|
wss-sts-issued-token-over-ssl |
oracle/wss_sts_issued_saml_bearer_token_over_ssl_client_policy oracle/wss_sts_issued_saml_bearer_token_over_ssl_service_policy |
WS-Security 1.0 + SAML Bearer 1.1 (STS-Issued, such as WS-Trust) + SSL Alternative: Not applicable |
|
wss11-sts-issued-token-with-certificates |
oracle/wss11_sts_issued_saml_hok_with_message_protection_client_policy oracle/wss11_sts_issued_saml_hok_with_message_protection_service_policy oracle/wss11_sts_issued_saml_with_message_protection_client_policy |
WS-Security 1.1 + SAML Holder of Key (HoK) (STS-Issued, such as WS-Trust) + Message Protection Alternative: Not applicable |
|
sts-trust-config |
oracle/sts_trust_config_policy |
WS-Trust Alternative: Not applicable |
50.2.9 Guidelines for Using Oracle WSM with Oracle Service Bus
This section provides guidelines for using certain Oracle WSM policies, and also describes behavior changes when using Oracle WSM policies with SOAP with Attachments, MTOM, and XOP.
50.2.9.1 wss_http_token_*_policy Guidelines
This section provides guidance on using the wss_http_token policies with Oracle Service Bus.
Note:
When using the HTTP transport with an Oracle WSM policy, set the Authentication property for the transport to None. Setting it to any other value conflicts with the Oracle WSM policy.
When you enable specific options on the policies in Oracle WSM, certain guidelines apply. The options are:
-
Authentication Mode – Oracle WSM and Oracle Service Bus support only "Basic" authentication mode in the policy. Any other mode causes an exception.
-
Transport Security – This option indicates that the invocation has to be done on the SSL channel. At runtime:
-
Proxy Services: If you enable this option on the policy, you must enable the HTTPS Required option on the proxy service containing the policy.
-
Business Services: No validation occurs on the business service configuration when you enable this option on the policy, so be sure that the business service endpoint addresses use HTTPS. A runtime error is thrown if an endpoint does not use HTTPS.
-
-
Mutual Authentication Required – This option indicates two-way SSL.
-
Proxy Services: This option is not supported for use on proxy services. Clear this option when using the wss_*_over_ssl_* _policy policies provided by Oracle WSM.
-
Business Services: Because Oracle WSM ignores this option on outbound messages, this option has no effect when used with business services.
-
-
Include Timestamp – This option enforces the inclusion of timestamp in the SOAP header.
-
Proxy Services: When you enable this option with proxy services, Oracle WSM ensures the timestamp is available and valid in the SOAP header.
-
Business Services: When you enable this option with business services, Oracle WSM adds a timestamp to the SOAP header if a timestamp does not already exist.
Note:
When applying wss_http_token policies to proxy and business services that use non-SOAP service types with the HTTP transport, the Include Timestamp option in the Oracle WSM policy must be disabled.
-
50.2.9.2 Oracle WSM Authentication Policy Guidelines
When you use token transport policies on an Oracle Service Bus service, such as wss_http_token_over_ssl_client_policy or wss_username_token_over_ssl_client_policy, the Authentication property on the service's transport configuration page to None. You can use either an Oracle WSM token policy or handle authentication through the transport, but not both.
50.2.9.3 Oracle WSM Policies and SOAP with Attachments (SwA)
You can attach any of the supported Oracle WSM policies (listed in Table 50-2) to proxy and business services that include support for SOAP with Attachments (SwA). In addition to securing the message body, you can configure message protection policies to include SwA attachments for message signing, message encryption, or both. When you include SwA attachments, you can also include MIME headers. Policies are configured in Oracle Enterprise Manager. For more information, see "Configuring Policies" and "Protecting Messages" in Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
50.2.9.4 Oracle WSM Policies and MTOM-Formatted Messages
You can attach Oracle WSM policies to proxy and business services that include support for MTOM-formatted SOAP messages and that use the HTTP, Local, or SB Transport. Message processing for all supported policies (listed in Table 50-2) is the same for SOAP messages in MTOM format as for any other SOAP message, with the exception of message protection policies.
50.2.9.4.1 Usage Guidelines
When applying Oracle WSM policies to services that support messages in MTOM format, follow these guidelines:
-
For proxy services, the incoming message must first be encrypted using an equivalent client policy.
-
Set the Authentication property for the transport to None when configuring the service. Setting it to any other value conflicts with the Oracle WSM policy.
50.2.9.4.2 Proxy Services
When a proxy service with XOP/MTOM enabled uses any supported Oracle WSM inbound request enforcement policies, the xop:Include elements or ctx:binary-content references that correspond to the actual message are inlined. The pipeline does not encounter any ctx:binary-content references in the payload, but instead sees the Base64-encoded data for the binary content that corresponds to the xop:Include elements. Note that the message contents do not change.
In the following cases, the xop:Include elements are not inlined:
-
HTTP security (transport policies) with SSL disabled and the authentication set to Basic.
-
HTTP security (transport policies) with SSL enabled, no required timestamp validation, and authentication set to Basic.
With the above policy types, Role Based Access Control policies can be used with no change in behavior. Any other enabled assertions in the attached policies (even logging assertions) would cause the binary content to be inlined.
The format of the inbound response depends on whether XOP/MTOM support is enabled. If it is enabled, the inbound response is always MTOM-encoded. If XOP/MTOM support is not enabled, the response payload is a SOAP message.
50.2.9.4.3 Business Services
When a business service with XOP/MTOM enabled does not use Oracle WSM encryption policies, any ctx:binary-content references in the outbound request are replaced by xop:Include elements. When any Oracle WSM policy is applied aside from message protection policies, the behavior and message structure are unchanged.
However, when an encryption policy is applied, the xop:Include elements are inlined before being encrypted. The outbound request message includes the xop:Include elements and corresponding MIME attachments for the binary content associated with the encrypted data (not for the original binary content). On the service side, the pipeline sees the Base64-encoded data for the binary-content in the client pipeline. As with proxy services, the message contents do not change.
For the business service's outbound response, the behavior is the same as for a proxy service, described above. Additionally, the xop:Include elements are not inlined for HTTP security (transport policies) with SSL enabled, timestamp validation, and authentication set to Basic.
50.3 Use Cases: Oracle Service Bus and WLS 9 Policies with Oracle Web Services Manager
This section provides use cases that highlight the interaction between Oracle Service Bus services using WLS 9 policies and Oracle WSM features in providing security throughout the service pipeline.
When using Oracle WSM with WLS 9 policies in Oracle Service Bus services, no configuration is required, and you do not have to extend an Oracle Service Bus domain with Oracle WSM. You implement Oracle WSM features at the desired client and service locations, and the interaction and enforcement occurs automatically.
Note:
In future releases of Oracle Service Bus, Oracle WSM policies will replace and enhance the functionality of WLS 9 security policies. While this version of Oracle Service Bus continues to support WLS 9 policies, you should consider using Oracle WSM policies for new service creation to prepare for the eventual deprecation of WLS 9 policy support.
For more information about Oracle WSM, see the following:
-
Oracle Fusion Middleware Security and Administrator's Guide for Web Services
Oracle WSM 10.1.3 documentation at
https://download.oracle.com/docs/cd/E10291_01/index.htm -
"Overview of Interoperability with Oracle Service Bus 10g Security Environments" in the Oracle Fusion Middleware Interoperability Guide for Oracle Web Services Manager
This document describes the following security use cases with Oracle WSM:
Note:
There is no equivalent of Gateway in Oracle Web Services Manager 11.1.1.
50.3.1 Message Protection
This section describes the following use cases:
50.3.1.1 Message Protection with Client Agent
You can implement this use case with the following versions of Oracle WSM:
-
11.1.1.x
-
10.1.3.x
Figure 50-1 illustrates using the Oracle Web Services Manager Client Agent for message protection.
Figure 50-1 Message Protection With an Oracle Web Services Manager Client Agent
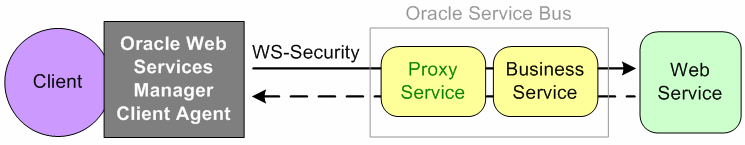
Description of "Figure 50-1 Message Protection With an Oracle Web Services Manager Client Agent"
The proxy service has an inbound message protection policy. The Oracle Web Services Manager Client Agent sends a signed and encrypted request to the proxy service. The proxy service receives the secured request and, acting as an active intermediary, decrypts and verifies signature and routes the request to the business service. The business service invokes the Web service, gets the response back, and sends it to the proxy service. The proxy service signs and encrypts the response and sends it to the Oracle Web Services Manager Client Agent. The Client Agent receives the secure response, decrypts and verifies the signature, and passes the response to the client.
50.3.1.2 Message Protection with Server Agent
You can implement this use case with the following versions of Oracle WSM:
-
11.1.1.x
-
10.1.3.x
Figure 50-2 illustrates using the Oracle Web Services Manager Server Agent for message protection.
Figure 50-2 Message Protection With an Oracle Web Services Manager Server Agent
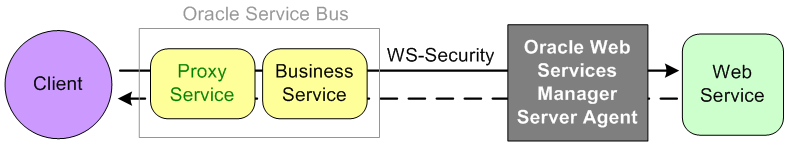
Description of "Figure 50-2 Message Protection With an Oracle Web Services Manager Server Agent"
The client sends a plain request through the proxy and business services in Oracle Service Bus. The business service signs and encrypt the request and sends the message to the Oracle Web Services Manager Server Agent. The Server Agent decrypts and verifies the request. The plain message response is passed back to the client.
50.3.1.3 Message Protection with Client and Server Agents
You can implement this use case with the following versions of Oracle WSM:
-
11.1.1.x
-
10.1.3.x
Figure 50-3 illustrates using the Oracle Web Services Manager Client and Server Agents for message protection.
Figure 50-3 Message Protection With an Oracle Web Services Manager Client and Server Agents
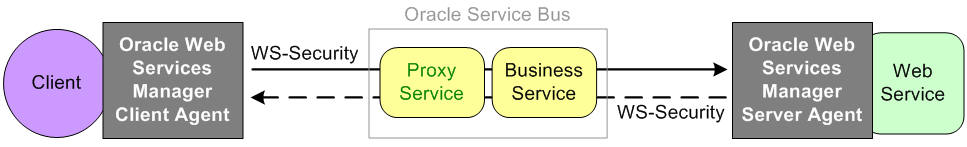
Description of "Figure 50-3 Message Protection With an Oracle Web Services Manager Client and Server Agents"
The Oracle Web Services Manager Client Agent signs and encrypts a client request and sends the request through to the proxy service. The proxy service decrypts and verifies the signature and passes the request to the business service, which signs and encrypts the request. The Web service has a Server Agent injected in it. The Server Agent has an inbound message protection policy that decrypts and verifies the signature, then signs and encrypts the response. The response is sent back to the business service, which verifies the message and passes the response to the proxy service. The proxy service generates a signed and encrypted response and sends it to the Client Agent. The Client Agent decrypts and verifies the response, then returns the plain response to the client.
50.3.1.4 Message Protection with Gateway
You can implement this use case with the following versions of Oracle WSM:
-
10.1.3.x
Figure 50-4 illustrates using the Oracle Web Services Manager Gateway for message protection.
Figure 50-4 Message Protection With an Oracle Web Services Manager Gateway
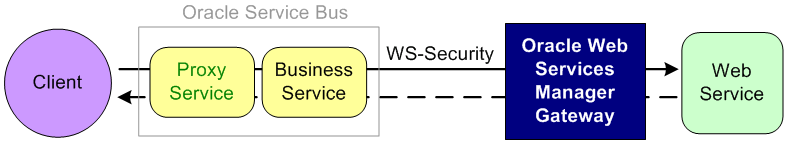
Description of "Figure 50-4 Message Protection With an Oracle Web Services Manager Gateway"
The client sends a plain request through the proxy and business services in Oracle Service Bus. The business service signs and encrypts the request and sends the message to the Oracle Web Services Manager Gateway. The Gateway decrypts and verifies the request. The plain message response is passed back to the client.
50.3.2 Authentication
You can implement this use case with the following versions of Oracle WSM:
-
11.1.1.x
-
10.1.3.x
Figure 50-5 illustrates using the Oracle Web Services Manager Client Agent for authentication.
Figure 50-5 Authentication with an Oracle Web Services Manager Client Agent
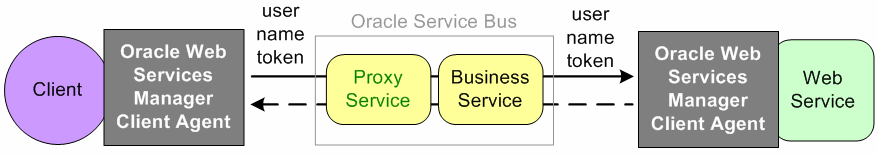
Description of "Figure 50-5 Authentication with an Oracle Web Services Manager Client Agent"
The proxy service has a user name token policy. The client, through Oracle Web Services Manager Client Agent, sends a request to the proxy service with user credentials at the message level in a user name token. The proxy service maps the user credential from the user name token using credential mapping and sends it through the business service to the Web service for authentication. The Web service is protected using an Oracle Web Services Manager service agent with an inbound user name token policy. The Oracle Web Services Manager Service Client Agent extracts and authenticates the user credentials. The response is then sent back through the business service and the proxy service to the client.
50.3.3 Perimeter Security
You can implement this use case with the following versions of Oracle WSM:
-
10.1.3.x
Figure 50-6 illustrates using Oracle Web Services Manager Gateway for enforcing perimeter security.
Figure 50-6 Perimeter Security with Oracle Web Services Manager Gateway
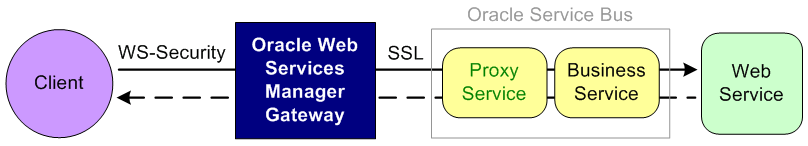
Description of "Figure 50-6 Perimeter Security with Oracle Web Services Manager Gateway"
Oracle Web Services Manager Gateway virtualizes the service exposed by the Oracle Service Bus proxy service. The inbound request to the Oracle Web Services Manager Gateway has a message protection policy. The client sends a secure request to the Oracle Web Services Manager Gateway virtualized service, which is signed and encrypted.
The Oracle Web Services Manager Gateway acts as a security enforcement point and decrypts and verifies the signature. Oracle Web Services Manager Gateway then routes the plain request to the proxy service over SSL. The proxy service forwards the request to the business service, which invokes the Web service and gets the plain response back. The response moves back through the proxy service and Oracle Web Services Manager Gateway to the client.
50.3.4 Identity Propagation
You can implement this use case with the following versions of Oracle WSM:
-
10.1.3.x
Figure 50-7 illustrates using the Oracle Web Services Manager Gateway for identity propagation using SAML (Security Assertion Markup Language) token version 1.1.
Figure 50-7 Identity Propagation with Oracle Web Services Manager Gateway
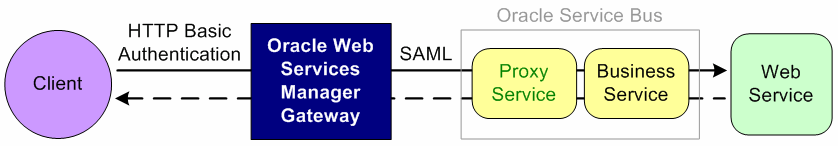
Description of "Figure 50-7 Identity Propagation with Oracle Web Services Manager Gateway"
The client sends a basic HTTP authentication request to the Oracle Web Services Manager Gateway. Oracle Web Services Manager Gateway authenticates the user using the user name and password from the HTTP header. Oracle Web Services Manager Gateway generates a SAML sender voucher assertion with the authenticated user identity (token mediation), inserts the SAML token, and sends the assertion to the proxy service. The proxy service receives the SAML assertion with the user identity and, acting as an active intermediary, verifies the user identity. The proxy service then passes the request to the business service. The response travels back through the business service, proxy service, and Oracle Web Services Manager Gateway to the client.