32 Delegating Privileges for Oracle Identity Management
This chapter explains how to store all the data for users, groups, and services in one repository, and delegate the administration of that data to various administrators. It also explains the default security configuration in Oracle Internet Directory.
This chapter contains these topics:
-
Section 32.1, "Introduction to Delegating Privileges for Oracle Identity Management"
-
Section 32.2, "Delegating Privileges for User and Group Management"
-
Section 32.3, "Delegating Privileges for Deployment of Oracle Components"
-
Section 32.4, "Delegating Privileges for Component Run Time"
Note:
All references to Oracle Delegated Administration Services in this chapter refer to Oracle Delegated Administration Services 10g (10.1.4.3.0) or later.
32.1 Introduction to Delegating Privileges for Oracle Identity Management
Oracle Identity Management enables you to store all the data for users, groups, and services in one repository, and to delegate a particular administrator for each set of data. By providing both a centralized repository and customized delegated access, Oracle Identity Management is both secure and scalable.
This section contains these topics:
-
Section 32.1.2, "Delegation in an Oracle Fusion Middleware Environment"
-
Section 32.1.4, "Privileges for Administering the Oracle Technology Stack"
32.1.1 How Delegation Works
Using the delegation model, a global administrator can delegate to realm administrators the privileges to create and manage the identity management realms for hosted companies. Realm administrators can, in turn, delegate to end users and groups the privileges to change their application passwords, personal data, and preferences. Each type of user can thus be given the appropriate level of privileges.
To delegate the necessary privileges, you assign the user to the appropriate administrative group. For example, suppose that you store data for both enterprise users and the e-mail service in the directory, and must specify a unique administrator for each set of data. To specify a user as the administrator of enterprise users, you assign that user to, say, the Enterprise User Administrators Group. To specify a user as the administrator of the e-mail services, you assign that user to, say, the E-mail Service Administrators Group.
32.1.2 Delegation in an Oracle Fusion Middleware Environment
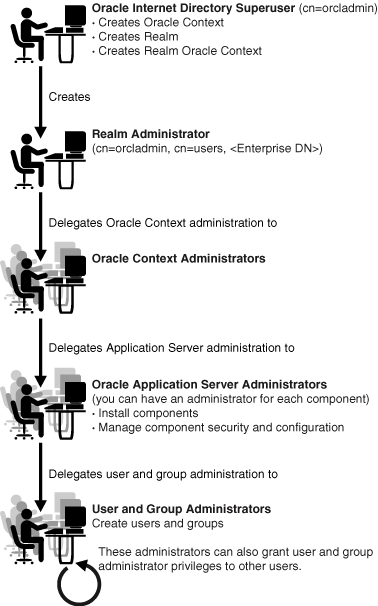
Figure 32-1 shows the flow of delegation in an Oracle Fusion Middleware environment.
As Figure 32-1 shows, in an Oracle Fusion Middleware environment the directory superuser (cn=orcadmin) creates:
-
The Oracle Context
-
The realm
-
The realm-specific Oracle Context
-
The entry for the realm administrator (
cn=orcladmin, cn=users,Enterprise DN)
The realm administrator, in turn, delegates administration of the Oracle Context to specific users by assigning those users to the Oracle Context Administrators Group. Oracle Context Administrators then delegate administration of the Oracle Application Server to one or more users by assigning them to the Oracle Fusion Middleware Administrators Group. The Oracle Fusion Middleware Administrators install and administer Oracle Fusion Middleware components and delegate administration of user and group data to the User and Group Administrators group. The User and Group Administrators create users and groups. They can also grant user and group administrator privileges to other users.
32.1.3 About the Default Configuration
When you first install Oracle Internet Directory, the default configuration establishes access control policies at various points in the directory information tree (DIT). Default access controls are placed on the User and Group containers as described later in this chapter. Likewise, default privileges for specific directory entities are discussed later in this chapter. In addition, certain default privileges are granted to Everyone and to each user as described in Table 32-2.
Table 32-1 Default Privileges Granted to Everyone and to Each User
| Subject | Default Privileges |
|---|---|
|
Everyone |
The following privileges at the Root DSE:
|
|
Each user |
Complete access to his or her own attributes—including the |
You can customize this default configuration to meet the security requirements of your enterprise.
32.1.4 Privileges for Administering the Oracle Technology Stack
Administering the Oracle technology stack requires the privileges described in Table 32-2.
Table 32-2 Privileges for Administering the Oracle Technology Stack
| Type of Privilege | Description | More Information |
|---|---|---|
|
User and group management privileges |
These are delegated to either Oracle components that use the identity management infrastructure or to end users themselves |
Section 32.2, "Delegating Privileges for User and Group Management" |
|
Deployment-time privileges |
These are required to deploy any Oracle component. They may include privileges to create appropriate entries inside the directory, or to store metadata in a common repository. Such privileges must be given, for example, to an administrator of Oracle Portal. |
Section 32.3, "Delegating Privileges for Deployment of Oracle Components" |
|
Run-time privileges |
These are required to facilitate the run-time interactions of Oracle components within the identity management infrastructure. These include privileges to view user attributes, add new users, and modify the group membership. Such privileges must be given to the administration tool specific to each Oracle component, enabling it to access or create entries inside Oracle Internet Directory. |
Section 32.4, "Delegating Privileges for Component Run Time" |
Caution:
Be careful when modifying the default ACLs in any Oracle Context. Doing so can disable the security of Oracle components in your environment. See component-specific documentation for details on whether you can safely modify the default ACLs in an Oracle Context.
See Also:
Section 37.1, "Introduction to Migrating Data from Other Data Repositories" if you have an existing directory structure that you now want to migrate to an Oracle Application Server environment
32.2 Delegating Privileges for User and Group Management
Administrative privileges are delegated to either Oracle components that use the identity management infrastructure or to end users themselves. A privilege can be delegated to either an identity—for example, a user or application—or to a role or group.
This section contains these topics:
-
Section 32.2.1, "How Privileges Are Granted for Managing User and Group Data"
-
Section 32.2.3, "Default Privileges for Managing Group Data"
32.2.1 How Privileges Are Granted for Managing User and Group Data
To delegate administrative privileges, the Oracle Internet Directory superuser does the following:
-
Creates an identity management realm
-
Identifies a special user in that realm who is called the realm administrator
-
Delegates all privileges to that realm administrator
This realm administrator, in turn, delegates certain privileges that Oracle components require to the Oracle defined roles—for example, Oracle Fusion Middleware administrators. The Oracle components receive these roles when they are deployed.
In addition to delegating privileges to roles specific to Oracle components, the realm administrator can also define roles specific to the deployment—for example, a role for help desk administrators—and grant privileges to those roles. These delegated administrators can, in turn, grant these roles to end users. In fact, because a majority of user management tasks involve self-service—like changing a phone number or specifying application-specific preferences—these privileges can be delegated to end users by both the realm administrator and Oracle component administrators.
In the case of a group, one or more owners—typically end users—can be identified. If they are granted the necessary administrative privileges, then these owners can manage the group by using Oracle Internet Directory Self-Service Console, Oracle Directory Services Manager, or command-line tools.
32.2.2 Default Privileges for Managing User Data
Managing users involves privileges to:
-
Create and delete user entries
-
Modify user attributes
-
Delegate user administration to other users
The access control policy point (ACP) for creating users is at the Users container in the identity management realm.
This section describes each of these privileges in more detail.
32.2.2.1 Creating Users for a Realm
To create users for a realm, an administrator must be a member of the Subscriber DAS Create User Group. Table 32-3 describes the characteristics of this group.
Table 32-3 Characteristics of the Subscriber DAS Create User Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Users container in the default realm allows the Subscriber DAS Create User Group in the realm Oracle Context to create users under the Users container. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the User Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.2.2 Modifying Attributes of a User
To modify user attributes, an administrator must be a member of the Subscriber DAS Edit User Group. Table 32-4 describes the characteristics of this group.
Table 32-4 Characteristics of the Subscriber DAS Edit User Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Users container in the default identity management realm allows the Subscriber DAS Edit User Group in the realm Oracle Context to modify various attributes of users. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the User Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.2.3 Deleting a User
To delete a user in a realm, an administrator must be a member of the DAS Delete User Group. Table 32-5 describes the characteristics of this group.
Table 32-5 Characteristics of the DAS Delete User Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Users container in the default identity management realm allows the DAS Delete User Group in the realm Oracle Context to delete a user from the realm. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the User Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.2.4 Delegating User Administration
A delegated administrator can perform specified operations within the directory and requires permission to add any user to the User Creation, User Edit, or User Delete Groups described previously.
To grant user administration privileges to a delegate administrator, the granting administrator must be a member of the User Privilege Assignment Group. Table 32-6 describes the characteristics of this group.
Table 32-6 Characteristics of the User Privilege Assignment Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL policy for each of the groups previously mentioned allows members of the User Privilege Assignment Group to add users to or remove them from those groups. |
|
Administrators |
The Oracle Internet Directory superuser Oracle Context Administrators Group Owners of this group. The DNs of these owners are listed as values of the |
|
DN |
|
32.2.3 Default Privileges for Managing Group Data
Managing users and groups involves privileges to:
-
Create and delete group entries
-
Modify group attributes
-
Delegate group administration to other users
The ACP for creating groups is at the Groups container in the identity management realm.
32.2.3.1 Creating Groups
To create groups in Oracle Internet Directory, an administrator must be a member of the Group Creation Group. Table 32-7 describes the characteristics of this group.
Table 32-7 Characteristics of the Group Creation Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Groups container in the realm allows the Group Creation Group to add new groups in the realm. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the Oracle Fusion Middleware Administrators Group Members of the Group Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.3.2 Modifying the Attributes of Groups
To modify the attributes of groups under the Groups container in a realm, an administrator must be a member of the Group Edit Group. Table 32-8 describes the characteristics of this group.
Table 32-8 Characteristics of the Group Edit Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Groups container in the realm allows the Group Edit Group to modify various attributes of groups in the realm. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the Oracle Fusion Middleware Administrators Group Members of Group Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.3.3 Deleting Groups
To delete groups, an administrator must have membership in the Group Delete Group. Table 32-9 describes the characteristics of this group.
Table 32-9 Characteristics of the Group Delete Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Groups container in the realm allows the Group Delete Group to delete groups in the realm. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the Group Privilege Assignment Group Members of the DAS Administrators Group Owners of this group |
|
DN |
|
32.2.3.4 Delegating Group Administration
To delegate group administration to other users—that is, to add or remove users from the Group Creation, Group Edit, or Group Delete Groups described previously—an administrator must be a member of the Group Privilege Assignment Group. Table 32-10 describes the characteristics of this group.
Table 32-10 Characteristics of the Group Privilege Assignment Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL policy for the Group Creation, Group Edit, or Group Delete Groups allows members of Group Privilege Assignment Group to add users to or remove them from those groups. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Owners of the group. The DNs of these owners are listed as values of the |
|
DN |
|
32.3 Delegating Privileges for Deployment of Oracle Components
This section discusses the groups responsible for deploying Oracle components. It describes the tasks these administrators perform and the privileges they can grant. It includes these topics:
-
Section 32.3.3, "User Management Application Administrators"
-
Section 32.3.4, "Trusted Application Administrators"
Note:
Oracle Internet Directory superusers have all the privileges of Oracle Fusion Middleware Administrators and Trusted Application administrators, and must be members of the Oracle Fusion Middleware Administrators Group. They can:
-
Assign the Oracle Fusion Middleware Administrator role to a user
-
Assign the Trusted Application role to a user
-
Assign the User Management Application Administrator role to a user
-
32.3.1 How Deployment Privileges Are Granted
To enable administrators to deploy Oracle components, the superuser:
-
Grants certain deployment privileges to various groups—for example, the Oracle Fusion Middleware Administrators Group
-
Adds the administrators to those privileged groups
The delegated administrators, in turn, can delegate privileges to other administrators.
32.3.2 Oracle Application Server Administrators
Table 32-11 describes the characteristics of the Oracle Application Server Administrators Group.
Table 32-11 Characteristics of the Oracle Application Server Administrators Group
| Characteristic | Description |
|---|---|
|
Tasks |
Perform repository database installation that creates a repository database registration entry in the directory Perform mid-tier installation. To associate a mid-tier with a repository, the user must have the appropriate privileges with a specific repository database. Install and configure Oracle Fusion Middleware components that create application entities in Oracle Internet Directory Grant to component entities the run-time privileges listed later in this section Configure provisioning profiles for components so that the components can receive update notifications |
|
Privileges this group can delegate to components |
Read Common User Attributes—except passwords, certificates, and similar security credentials Read common group attributes Create, edit, and delete groups Authenticate a user Read application verifiers |
|
Administrators |
Oracle Internet Directory superuser Oracle Context Administrator Owners of this group |
|
DN |
|
32.3.3 User Management Application Administrators
User Management Application Administrators must be members of the Oracle Fusion Middleware Administrators Group.
Table 32-12 describes the characteristics of the User Management Application Administrators Group.
Table 32-12 Characteristics of the User Management Application Administrators Group
| Characteristic | Description |
|---|---|
|
Tasks |
User Management Application administrators install specific applications that have interfaces to perform user management operations—for example, Oracle Portal and Oracle Application Server Wireless. |
|
Privileges this group can delegate to components |
Create, edit, and delete user attributes |
|
Administrators |
Oracle Internet Directory superuser Oracle Context Administrator Owners of this group |
|
DN |
|
32.3.4 Trusted Application Administrators
Trusted Application administrators must be members of the Oracle Fusion Middleware Administrators Group.
Table 32-13 describes the characteristics of the Trusted Application Administrators Group.
Table 32-13 Characteristics of the Trusted Application Administrators Group
| Characteristic | Description |
|---|---|
|
Tasks |
Install specific identity management components—for example, Oracle Single Sign-On, Oracle Delegated Administration Services, and Oracle Application Server Certificate Authority |
|
Privileges this group can delegate to components |
Read, compare, or reset the user password Proxy as the end-user Read, compare, or modify the user's certificate and SMIME certificate |
|
Administrators |
Oracle Internet Directory superuser Oracle Context Administrator Owners of this group |
|
DN |
|
32.4 Delegating Privileges for Component Run Time
Many Oracle components administer user entries in Oracle Internet Directory and need the corresponding privileges. For example:
-
When the Oracle Single Sign-On server authenticates a user, that server:
-
Connects to Oracle Internet Directory using its own identity
-
Verifies that the password entered by the user matches that user's password stored in the directory
To do this, the Oracle Single Sign-On server needs permission to compare user passwords. To set up the Oracle Single Sign-On cookie, it needs permission to read user attributes.
-
-
To grant access to a user, Oracle Portal must retrieve that user's attributes. To do this, it logs in to Oracle Internet Directory as a proxy user, impersonating the user seeking access. It therefore needs the privileges of a proxy user.
In general, Oracle components can require these privileges:
-
Read and modify user passwords
-
Compare user passwords
-
Proxy on behalf of users accessing applications
-
Administer the Oracle Context where all Oracle components store their metadata
Most Oracle components ship with a preconfigured set of privileges. You can change these default privileges to satisfy specific business requirements—for example, by removing privileges to create and delete user entries.
See Also:
Oracle Application Server Security Guide in the 10g (10.1.4.0.1) library for further information about the component delegation model.
This section describes the security privileges required by Oracle components. It contains these topics:
-
Section 32.4.1, "Default Privileges for Reading and Modifying User Passwords"
-
Section 32.4.2, "Default Privileges for Comparing User Passwords"
-
Section 32.4.3, "Default Privileges for Comparing Password Verifiers"
-
Section 32.4.4, "Default Privileges for Proxying on Behalf of End Users"
-
Section 32.4.5, "Default Privileges for Managing the Oracle Context"
-
Section 32.4.6, "Default Privileges for Reading Common User Attributes"
-
Section 32.4.7, "Default Privileges for Reading Common Group Attributes"
-
Section 32.4.8, "Default Privileges for Reading the Service Registry"
-
Section 32.4.9, "Default Privileges for Administering the Service Registry"
32.4.1 Default Privileges for Reading and Modifying User Passwords
Reading and modifying user passwords requires administrative privileges on the security-related attributes in the directory—for example, the userPassword attribute. It requires membership in the User Security Administrators Group described in Table 32-14.
Table 32-14 Characteristics of the User Security Administrators Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The default ACL policy at the Root (DSE Entry) allows members of the User Security Administrators Group to read, write, compare, and search on |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the Trusted Application Administrators Group |
|
DN |
|
32.4.2 Default Privileges for Comparing User Passwords
Comparing user passwords requires permission to compare a user's userPassword attribute. This operation is performed by components such as Oracle Unified Messaging that authenticate end users by using their passwords stored in Oracle Internet Directory.
Comparing user passwords requires membership in the Authentication Services Group described in Table 32-15.
Table 32-15 Characteristics of the Authentication Services Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL policy at the Users container in the default identity management realm allows the Authentication Services Group to perform compare operation on the |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Members of the Application Server Administrators Group Owners of this group |
|
DN |
|
32.4.3 Default Privileges for Comparing Password Verifiers
To compare password verifiers, a user must have permission to compare the userpassword attribute. Comparing password verifiers requires membership in the Verifier Services Group described in Table 32-16.
Table 32-16 Characteristics of the Verifier Services Group
| Characteristic | Description |
|---|---|
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators group Members of the Application Server Administrators group Owners of this group |
|
DN |
|
32.4.4 Default Privileges for Proxying on Behalf of End Users
A proxy user has the privilege to impersonate an end user, performing on that user's behalf those operations for which that user has privileges. In an Oracle Fusion Middleware environment, the Oracle Delegated Administration Services proxies on behalf of the end user, and, through the Oracle Internet Directory Self-Service Console, performs operations on that user's behalf. In such a case, the access controls on the directory server eventually govern the operations that the user can perform.
Proxying on behalf of end users requires membership in the User Proxy Privilege Group described in Table 32-17.
Table 32-17 Characteristics of the User Proxy Privilege Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL at the Users container in the default identity management realm allows User Proxy Privilege Group to proxy on behalf of the end user. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group Owners of the groups. The DNs of these owners are listed as values of the Members of the Trusted Application Administrators Group |
|
DN |
|
32.4.5 Default Privileges for Managing the Oracle Context
To manage a specific Oracle Context, a user must have complete access to it. Managing an Oracle Context requires membership in the Oracle Context Administrators Group described in Table 32-18. An Oracle Context Administrators Group exists for each Oracle Context and has administrative permission in the specific Oracle Context.
Table 32-18 Characteristics of the Oracle Context Administrators Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The ACL policy at the root node of the Oracle Context allows members of Oracle Context Administrators Group to perform all administrative operations within the Oracle Context. Such a policy is set up when a new Oracle Context is created in the directory. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Oracle Context Administrators Group |
|
DN |
|
32.4.6 Default Privileges for Reading Common User Attributes
Common user attributes are: mail, orclguid, displayname, preferredlanguage, orcltime, gender, dateofbirth, telephonenumber, wirelessaccountnumber. To read these attributes requires membership in the Common User Attributes Group described in Table 32-19.
Table 32-19 Characteristics of the Common User Attributes Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The default ACL is on the User container in the realm and grants permission to read common user attributes. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Application Server Administrators Group Owners of this group |
|
DN |
|
32.4.7 Default Privileges for Reading Common Group Attributes
Common group attributes are: cn, uniquemember, displayname, and description. To read these attributes requires membership in the Common Group Attributes Group described in Table 32-20.
Table 32-20 Characteristics of the Common Group Attributes Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The default ACL is on the Group container in the realm and grants permission to read these attributes: |
|
Administrators |
The Oracle Internet Directory superuser Members of the Application Server Administrators Group Owners of this group |
|
DN |
|
32.4.8 Default Privileges for Reading the Service Registry
To view the contents of the Service Registry requires membership in the Service Registry Viewers Group described in Table 32-21.
Table 32-21 Characteristics of the Service Registry Viewers Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The default ACL is on the Services container in the root Oracle Context. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Application Server Administrators Group Owners of this group |
|
DN |
|
32.4.9 Default Privileges for Administering the Service Registry
To administer the Service Registry requires membership in the Service Registry Administrators Group described in Table 32-22.
Table 32-22 Characteristics of the Common Group Attributes Group
| Characteristic | Description |
|---|---|
|
Default ACP |
The default ACL is on the Services container in the root Oracle Context. |
|
Administrators |
The Oracle Internet Directory superuser Members of the Application Server Administrators Group Owners of this group |
|
DN |
|