19 Deploying the Oracle Password Filter for Microsoft Active Directory
This chapter explains how to install and configure the Oracle Password Filter for Microsoft Active Directory.
Note:
To use the Oracle Password Filter for Microsoft Active Directory, your Oracle back-end directory must be Oracle Internet Directory. The Oracle Unified Directory back-end directory and the Oracle Directory Server Enterprise Edition back-end directory do not support integration with the Oracle Password Filter for Microsoft Active Directory.
This chapter contains the following sections:
-
Overview of the Oracle Password Filter for Microsoft Active Directory
-
Configuring and Testing Oracle Internet Directory with SSL Server-Side Authentication
-
Importing a Trusted Certificate into a Microsoft Active Directory Domain Controller
-
Testing SSL Communication Between Oracle Internet Directory and Microsoft Active Directory
-
Installing and Reconfiguring the Oracle Password Filter for Microsoft Active Directory
-
Removing the Oracle Password Filter for Microsoft Active Directory
For help troubleshooting an issue with the Oracle Password Filter for Microsoft Active Directory, see the following topic in Appendix E, "Troubleshooting the Oracle Directory Integration Platform."
Note:
The installation file for the Oracle Password Filter for Microsoft Active Directory is located on the Oracle Application Server CD-ROM (Disk 1) for Windows.
A 32-bit version and a 64-bit version of the password filter application are provided. The 32-bit version should only be installed on a 32-bit OS, and the 64-bit version should only be installed on a 64-bit OS. See "Installing the Oracle Password Filter for Microsoft Active Directory" for installation instructions.
19.1 Overview of the Oracle Password Filter for Microsoft Active Directory
This section describes the purpose of the Oracle Password Filter for Microsoft Active Directory and how it works. It contains these topics:
-
What is the Oracle Password Filter for Microsoft Active Directory?
-
How Does the Oracle Password Filter for Microsoft Active Directory Work?
-
How Do I Deploy the Oracle Password Filter for Microsoft Active Directory?
19.1.1 What is the Oracle Password Filter for Microsoft Active Directory?
Oracle Directory Integration Platform enables synchronization between the Oracle back-end directory (the back-end directory must be Oracle Internet Directory to use Oracle Password Filter for Microsoft Active Directory) and Microsoft Active Directory. The Oracle Directory Integration Platform can retrieve all Microsoft Active Directory attributes with the exception of user passwords. Oracle Application Server Single Sign-On uses an external authentication plug-in to verify user credentials in Microsoft Active Directory and automatically store the updated password in the Oracle back-end directory. Applications such as Oracle Database Enterprise User Security that do not use Oracle Application Server Single Sign-On can use the Oracle Password Filter for Microsoft Active Directory to retrieve passwords from Microsoft Active Directory and store the password in the Oracle back-end directory.
Note:
Your Oracle back-end directory must be Oracle Internet Directory to support Enterprise User Security. The Oracle Unified Directory back-end directory and the Oracle Directory Server Enterprise Edition back-end directory do not support integration with other Fusion Middleware components, including Enterprise User Security.
When users change their passwords from their desktops, the updated password is automatically synchronized with the Oracle back-end directory. More specifically, the Oracle Password Filter for Microsoft Active Directory monitors Microsoft Active Directory for password changes, which it then stores in the Oracle back-end directory. This allows users to be authenticated with their Microsoft Active Directory credentials and authorized to access resources by using information stored in the Oracle back-end directory. Storing Microsoft Active Directory user credentials in the Oracle back-end directory also provides a high availability solution in the event that the Microsoft Active Directory server is down. The Oracle Password Filter is installed on each Microsoft Active Directory server and automatically forwards password changes to the Oracle back-end directory.
Note:
Enterprise User Security can only verify user credentials that are stored in the Oracle Internet Directory back-end directory. For this reason, to verify user credentials in Microsoft Active Directory with Enterprise User Security, you must use the Oracle Password Filter to retrieve passwords from Microsoft Active Directory into the Oracle Internet Directory back-end directory.
The Oracle Password Filter for Microsoft Active Directory does not require the Oracle Directory Integration Platform to synchronize passwords from Microsoft Active Directory to the Oracle back-end directory. The only requirement is that users synchronized from Microsoft Active Directory to the Oracle back-end directory must include the ObjectGUID attribute value to identify the user in both directories. The Oracle Password Filter for Microsoft Active Directory does not enforce password policies, or differences in password policies, between Microsoft Active Directory and the Oracle back-end directory. Instead, the system administrator must ensure that the password policies are consistent in both directories.
Password change requests occur when an account is created, an administrator resets a user's password, or when a user changes his or her own password. In order for the Oracle Password Filter for Microsoft Active Directory to capture Microsoft Active Directory passwords, one of these events must occur. Passwords that were set prior to installing the Oracle Password Filter for Microsoft Active Directory cannot be captured unless a system administrator forces a global password change request to all users.
Note:
The Oracle Password Filter for Microsoft Active Directory only captures password changes for 32-bit or higher Windows systems that have been integrated with Microsoft Active Directory.
19.1.2 How Does the Oracle Password Filter for Microsoft Active Directory Work?
This section describes how the Oracle Password Filter for Microsoft Active Directory works. It contains these topics:
19.1.2.1 How Clear Text Password Changes are Captured
When a password change request is made, the Local Security Authority (LSA) of the Windows operating system calls the Oracle Password Filter for Microsoft Active Directory package that is registered on the system. When the LSA calls the Oracle Password Filter for Microsoft Active Directory package, it passes to it the user name and changed password. The Oracle Password Filter for Microsoft Active Directory then performs the synchronization.
19.1.2.2 Password Changes are Stored when the Oracle Back-end Directory is Unavailable
When the Oracle back-end directory is unavailable, the password change events are archived securely and the encrypted passwords are stored in the Microsoft Active Directory. The Oracle Password Filter for Microsoft Active Directory attempts to synchronize these entries until it reaches the specified maximum number of retries.
19.1.2.3 Password Synchronization is Delayed Until Microsoft Active Directory Users are Synchronized with Oracle Identity Management
The Oracle Password Filter for Microsoft Active Directory is notified immediately when a new user is created in Microsoft Active Directory. However, Oracle Directory Integration Platform will not synchronize entries until the next scheduled synchronization interval. For this reason, passwords for new user entries are stored in encrypted format in Microsoft Active Directory until the next synchronization. The Oracle Password Filter for Microsoft Active Directory then attempts to synchronize these entries until it reaches the specified maximum number of retries.
19.1.2.4 Password Bootstrapping
Because the original clear text form of a password is not retrievable by the Oracle Password Filter for Microsoft Active Directory, you cannot perform initial bootstrapping to synchronize passwords from Microsoft Active Directory to the Oracle back-end directory. However, you can instruct users to change their passwords or force a password change for all users in Microsoft Active Directory by changing the password expiration policy.
19.1.3 How Do I Deploy the Oracle Password Filter for Microsoft Active Directory?
The general procedures for installing and configuring the Oracle Password Filter for Microsoft Active Directory are as follows;
-
Enable synchronization between the Oracle back-end directory (Oracle Internet Directory) and Microsoft Active Directory by following the instructions described in Chapter 18, " Integrating with Microsoft Active Directory".
-
Configure and test the Oracle back-end directory in SSL server authentication mode by following the instructions in "Configuring and Testing Oracle Internet Directory with SSL Server-Side Authentication".
-
Import the Oracle back-end directory trusted server certificate into the Microsoft Active Directory domain controller by following the instructions in "Importing a Trusted Certificate into a Microsoft Active Directory Domain Controller".
-
Verify that the Oracle back-end directory and Microsoft Active Directory can communicate with SSL server authentication by following the instructions in "Testing SSL Communication Between Oracle Internet Directory and Microsoft Active Directory".
-
Install the Oracle Password Filter for Microsoft Active Directory by following the instructions in "Installing the Oracle Password Filter for Microsoft Active Directory".
-
Configure the Oracle Password Filter for Microsoft Active Directory by following the instructions in "Reconfiguring the Oracle Password Filter for Microsoft Active Directory".
19.2 Configuring and Testing Oracle Internet Directory with SSL Server-Side Authentication
The Oracle Password Filter communicates password changes from Microsoft Active Directory to Oracle Internet Directory using the Secure Socket Layer (SSL) protocol, which provides data encryption and message integrity for a TCP/IP connection. More specifically, to synchronize password changes between Oracle Internet Directory and Microsoft Active Directory, you must use SSL server authentication mode, which allows a client to confirm a server's identity.
When combined with digital certificates, SSL also provides both server authentication and client authentication. Server authentication with SSL requires that you install a digital certificate on the server side of the communications link. When an SSL transaction is initiated by a client, the server sends its digital certificate to the client. The client examines the certificate to validate that the server has properly identified itself, including verifying that the certificate was issued by a trusted Certificate Authority (CA).
The subject attribute of the Oracle Internet Directory server certificate must match the Oracle Internet Directory server hostname. For example, if the Oracle Internet Directory server hostname is oid.oracle.com, then the subject attribute of the Oracle Internet Directory server certificate must also be oid.oracle.com. If the subject attribute of the Oracle Internet Directory server certificate does not match the Oracle Internet Directory server hostname, the Microsoft Active Directory password filter API will not accept the Oracle Internet Directory server certificate as being valid, despite the ldapbind -U 2 command's success. Oracle Internet Directory configured for Server authentication is also referred to as SSL type 2.
In the case of Oracle Internet Directory and Microsoft Active Directory integration, Oracle Internet Directory is the server and Microsoft Active Directory is the client. The Oracle Password Filter for Microsoft Active Directory uses SSL to protect the password during transmission between the Microsoft Active Directory domain controller and the Oracle Internet Directory server.
Note:
The certificate you use with the Oracle Password Filter for Microsoft Active Directory can be generated by any X.509-compliant certificate authority capable of accepting PKCS#10 standard certificate requests and producing certificates compliant with the X.509, Version 3, ISO standard and with RFC 2459.
To configure and test Oracle Internet Directory with SSL server-side authentication, refer to Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
19.3 Importing a Trusted Certificate into a Microsoft Active Directory Domain Controller
Server-authenticated SSL communication between a Microsoft Active Directory domain controller and Oracle Internet Directory will fail if the domain controller does not recognize the Oracle Internet Directory SSL certificate as valid. In order for a domain controller to accept an Oracle Internet Directory SSL certificate, you must use the Microsoft Management Console to import the certificate authority's trusted certificate into the domain controller.
To use the Microsoft Management Console to import the certificate authority's trusted certificate into the domain controller:
-
Select Run from the Windows Start menu. The Run dialog box displays. In the Run dialog box, type mmc, and then click OK. The Microsoft Management Console window displays.
-
Select Add/Remove Snap-in from the File menu. The Add/Remove Snap-in dialog box displays.
-
In the Add/Remove Snap-in dialog box, click Add. The Add Standalone Snap-in dialog box displays.
-
In the Add Standalone Snap-in dialog box, select Certificates, and then click Add. The Certificates snap-in dialog box displays, prompting you to select an option for which the snap-in will manage certificates.
-
In the Certificates snap-in dialog box, select Computer Account, and then click Next. The Select Computer dialog box displays.
-
In the Select Computer dialog box, select Local Computer, and then click Finish.
-
Click Close in the Add Standalone Snap-in dialog box, and then click OK in the Add/Remove Snap-in dialog box. The new console displays Certificates (Local Computer) in the console tree.
-
In the console tree, expand Certificates (Local Computer), and then click Trusted Root Certification Authority.
-
Point to All Tasks on the Action menu, and then select Import. The Welcome page of the Certificate Import Wizard displays. Click Next to display the File to Import page.
-
On the File to Import page, enter the path and file name of the certificate authority's trusted root certificate, or click Browse to search for a file, and then click Next. The Certificate Store page displays.
-
On the Certificate Store page, select Place all certificates in the following store. If Trusted Root Certification Authorities is not already selected as the certificate store, click Browse and select it. Click Next. The Completing the Certificate Import page displays.
-
On the Completing the Certificate Import page, click Finish. A dialog box displays indicating that the import was successful. Click OK.
-
Click Save from the File menu. The Save As dialog box displays. Enter a name for the new console, and then click Save.
-
Close Microsoft Management Console.
Note:
For help on importing a trusted certificate with Microsoft Management Console, refer to your Windows product documentation or visit Microsoft Help and Support at http://support.microsoft.com.
19.4 Testing SSL Communication Between Oracle Internet Directory and Microsoft Active Directory
The Oracle Password Filter for Microsoft Active Directory installs a command named ldapbindssl on the domain controller that you can use to test SSL communication between Oracle Internet Directory and Microsoft Active Directory.
Note:
The ldapbindssl binary is included in the Oracle Password Filter for Microsoft Active Directory installation. You cannot execute the ldapbindssl command without first installing the Oracle Password Filter for Microsoft Active Directory.
The syntax for the ldapbindssl is as follows:
ldapbindssl -h oid_hostname -p ssl_port -D binddn -w password
To test SSL connectivity from Microsoft Active Directory to Oracle Internet Directory:
-
Open a command prompt window on the domain controller and navigate to the folder where you installed the Oracle Password Filter for Microsoft Active Directory.
-
Enter the
ldapbindsslcommand to test SSL communication with Oracle Internet Directory. For example, the following command attempts to bind to an Oracle Internet Directory host named oraas.mycompany.com on SSL port 3133:ldapbindssl -h oraas.mycompany.com -p 3133 -D binddn -w password
If the
ldapbindsslcommand is successful, the following response is returned:bind successful
If the
ldapbindsslcommand is not successful, the following response is returned:Cannot connect to the LDAP server
If you cannot connect from Microsoft Active Directory to Oracle Internet Directory in SSL mode, verify that you successfully imported a trusted certificate into your Microsoft Active Directory domain controller, as described in "Importing a Trusted Certificate into a Microsoft Active Directory Domain Controller".
-
Close the command prompt window.
19.5 Installing and Reconfiguring the Oracle Password Filter for Microsoft Active Directory
This section describes how to install and reconfigure the Oracle Password Filter for Microsoft Active Directory. It contains these topics:
-
Installing the Oracle Password Filter for Microsoft Active Directory
-
Reconfiguring the Oracle Password Filter for Microsoft Active Directory
Before you install or reconfigure the Oracle Password Filter for Microsoft Active Directory, be sure to collect the necessary configuration parameters for Microsoft Active Directory and for Oracle Internet Directory. Table 19-1 lists the configuration parameters you will need for Microsoft Active Directory and Table 19-2 lists the configuration parameters you will need for Oracle Internet Directory.
Table 19-1 Oracle Password Filter Configuration Parameters for Microsoft Active Directory
| Parameter | Description |
|---|---|
|
Domain |
The Microsoft Active Directory domain for this domain controller. This value is typically the DNS domain name, in the form mycompany.com. |
|
Base DN |
The container in the Microsoft Active Directory DIT where the Oracle Password Filter searches for entries with changed passwords. If password propagation fails, the DNS of the failed password will be stored in an entry named |
|
Port |
The Microsoft Active Directory LDAP port (usually 3060). |
|
Host |
The IP address (NOT the host name) of the Microsoft Active Directory domain controller. |
|
Microsoft Active Directory User |
A user name with read privileges on the entire Microsoft Active Directory DIT and privileges to create an organizational unit and subtree entries under the Microsoft Active Directory base DN. Note that you must enter a user name and not the DN of an administrative user. This value is usually in the form administrator@machine_name. |
|
Microsoft Active Directory User Password |
The specified Microsoft Active Directory user's password. |
|
Log File Path |
A directory where log files will be written, such as E:\ADPasswordFilter\Log. |
Table 19-2 Oracle Password Filter Configuration Parameters for Oracle Internet Directory
| Parameter | Description |
|---|---|
|
Base DN |
The container in the Oracle Internet Directory DIT where the Oracle Password Filter searches for entries synchronized from Microsoft Active Directory. For example: |
|
Host |
Specifies the host name where the Oracle Internet Directory LDAP processes are running. For Oracle Internet Directory installations running in a high availability configuration, use the virtual host name of the load balancer. |
|
SSL Port |
The Oracle Internet Directory port that is configured for SSL server authentication. |
|
Non-SSL Port |
The Oracle Internet Directory for unencrypted communication. |
|
Oracle Internet Directory User |
The distinguished name of an Oracle Internet Directory user with permissions to update user passwords in the base DN. For example: |
|
Oracle Internet Directory User Password |
The specified Oracle Internet Directory user's password. |
19.5.1 Installing the Oracle Password Filter for Microsoft Active Directory
This section describes how to install the Oracle Password Filter for Microsoft Active Directory on a domain controller.
Note:
The Microsoft Active Directory and Oracle Internet Directory configuration parameters listed in the following procedure are described in Table 19-1 and Table 19-2.
To install the Oracle Password Filter for Microsoft Active Directory on a domain controller:
-
Do the following:
For 32-bit systems
-
Locate the
setup.exefile in theutils\adpwdfilterdirectory in the distribution package. -
Run the
setup.execommand to extract the installation files to a directory on your domain controller. -
Navigate to the directory where you extracted the installation files and double-click
setup.exe.The Welcome page of the Oracle Password Filter for Microsoft Active Directory installation program displays, informing you that the program will install the Oracle Password Filter for Microsoft Active Directory.
For 64-bit systems
-
Updating the PATH environment variable on your Windows system is a prerequisite for installing the 64-bit version of the Oracle Password Filter for Microsoft Active Directory.
Append the following to the PATH environment variable on your Windows system:
C:\windows\SysWOW64For instructions about how to edit Windows environment variables, refer to the following page:
-
Locate the
setup.exefile in theutils\adpwdfilter\64bitdirectory in the distribution package. -
Run the
setup.execommand to extract the installation files to a directory on your domain controller. -
Navigate to the directory where you extracted the installation files and double-click
setup.exe.The Welcome page of the Oracle Password Filter for Microsoft Active Directory installation program displays, informing you that the program will install the Oracle Password Filter for Microsoft Active Directory.
-
-
On the Welcome page, click Next. The Installation Requirements page displays, notifying you that SSL must be enabled between Oracle Internet Directory and Microsoft Active Directory and that installing the Oracle Password Filter for Microsoft Active Directory must restart your computer at the end of the installation process.
-
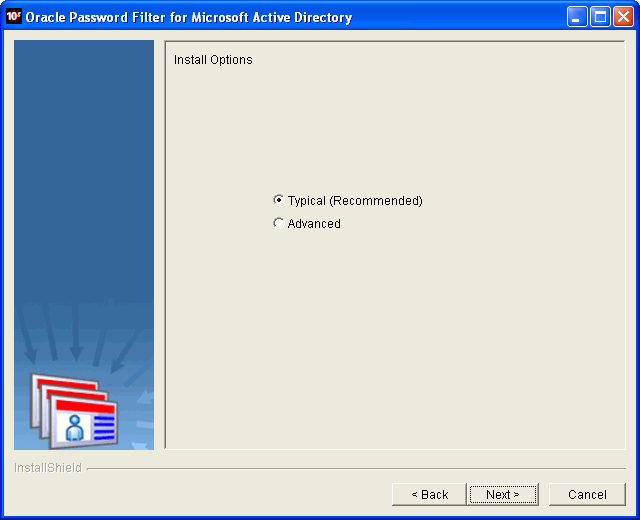
On the Installation Requirements page, click Next. The Installation Options page displays.
Description of the illustration oimig018.gif
-
On the Installation Options page, select Typical (Recommended) or Advanced. Selecting to perform an advanced installation allows you to specify attributes for Oracle Internet Directory and Microsoft Active Directory later in the installation process (Step 13). Click Next. The Installation Location page displays, prompting you for the folder where you want to install Oracle Password Filter for Microsoft Active Directory.
-
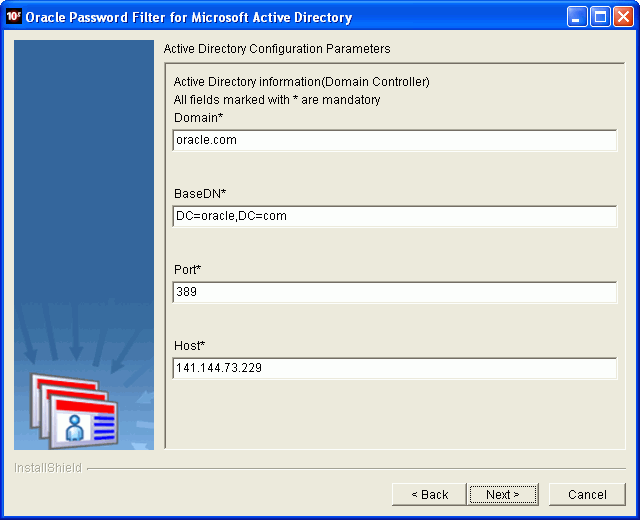
On the Installation Location page, accept the default installation directory or enter a different directory. You can also select Browse to locate a different directory. Click Next after selecting an installation directory. The Microsoft Active Directory Configuration Parameters page displays.
Description of the illustration oimig020.gif
-
On the Microsoft Active Directory Configuration Parameters page, enter values for the following parameters:
-
Domain
-
Base DN
-
Port
-
Host
-
-
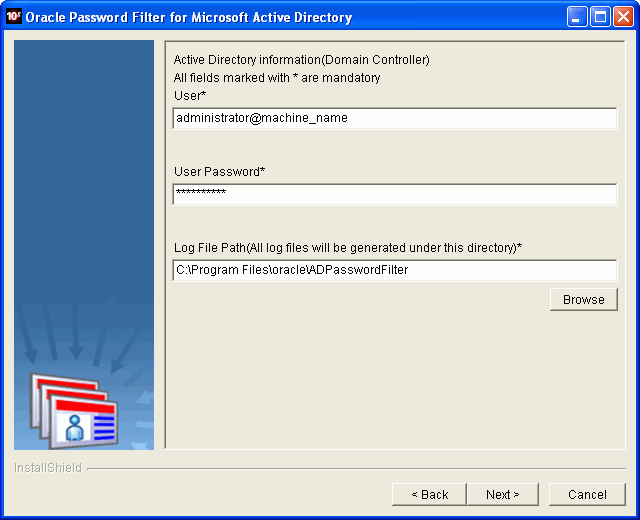
Click Next. The Microsoft Active Directory Domain Controller Information page displays.
Description of the illustration oimig021.gif
-
On the Microsoft Active Directory Domain Controller Information page, enter values for the following parameters:
-
User
-
User Password
-
Log File Path
-
-
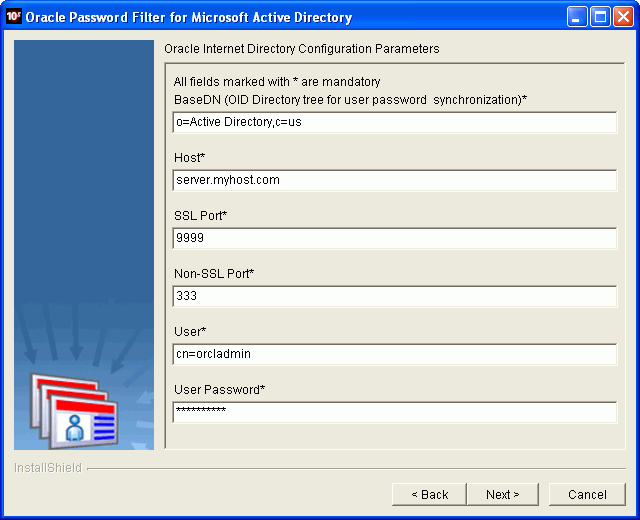
Click Next to continue. The Oracle Internet Directory Configuration Parameters page displays.
Description of the illustration oimig022.gif
-
On the Oracle Internet Directory Configuration Parameters page, enter values for the following parameters:
-
Base DN
-
Host
-
SSL Port
-
Non-SSL Port
-
User
-
User Password
Important:
If you have configured both import and export synchronization between Oracle Internet Directory and Microsoft Active Directory, be sure to enter for the User and User Password parameters the same bind DN and password that are specified in the synchronization profile that imports values from Microsoft Active Directory into Oracle Internet Directory. This is necessary to prevent password updates from looping between Oracle Internet Directory and Microsoft Active Directory.
-
-
Click Next to continue. The Oracle Password Filter Configuration Parameters page displays.
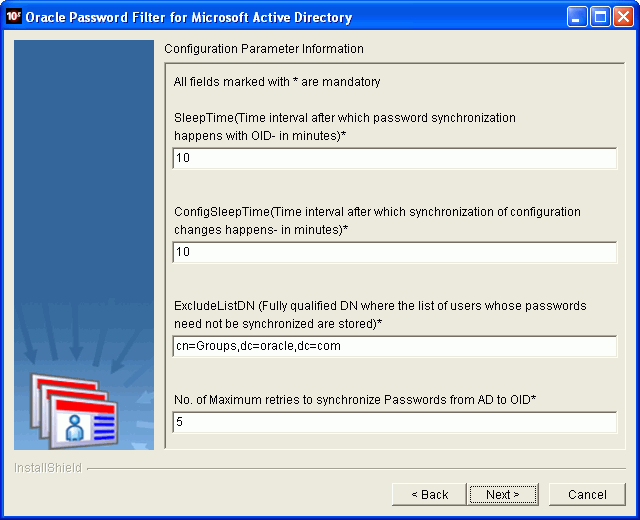
Description of the illustration oimig023.gif
-
On the Oracle Password Filter Configuration Parameters page, enter values for the following parameters:
-
SleepTime: The number of minutes between attempts to synchronize passwords changes between Oracle Internet Directory and Microsoft Active Directory.
-
ConfigSleepTime: The number of minutes between attempts to synchronize configuration changes between Oracle Internet Directory and Microsoft Active Directory.
-
ExcludeListDN: A fully qualified DN containing a list of users whose passwords should not be synchronized.
-
Maximum Retries: Specifies the maximum number of attempts to synchronize a password.
-
-
Click Next to continue. If you chose Advanced on the Installation Options page, the Specify Attributes page displays.
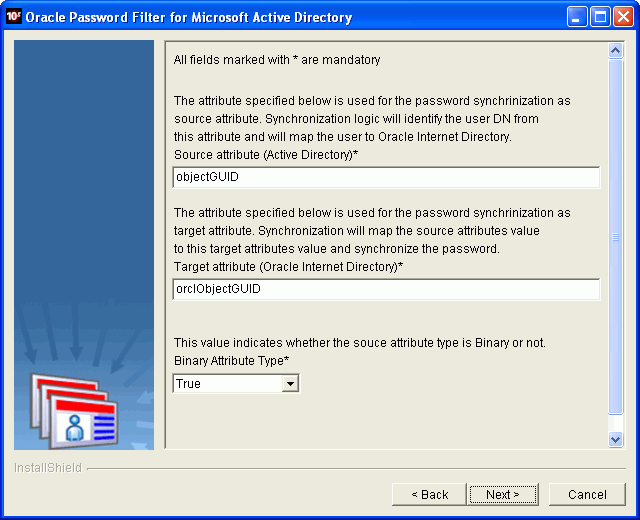
Description of the illustration oimig024.gif
Perform the following steps for advanced installations:
-
On the Specify Attributes page displays, enter values in the Source Attribute (Microsoft Active Directory) and Target Attribute (Oracle Internet Directory) boxes for any attributes that you want to synchronize between the two directories. Also, select a value of
trueorfalsefrom the Binary Attribute Type box to specify whether the source attribute type is binary. -
Click Next to continue. The Summary page displays and lists the path where the Oracle Password Filter for Microsoft Active Directory will be installed.
-
-
On the Summary page, click Next to install the Oracle Password Filter.
-
When prompted whether or not to upload schema extensions to Oracle Internet Directory, always select No. You do not want to upload schema extensions to Oracle Internet Directory because it comes preloaded with the schema extension attributes required for the Microsoft Active Directory Password filter.
The Reboot Domain Controller page displays.
-
On the Reboot Domain Controller page, click Next to restart the computer.
-
Do the following:
For 32-bit systems
-
After the computer restarts, log in as an administrator. The remaining configuration tasks for the Oracle Password Filter execute automatically after you log in.
For 64-bit systems
-
After the computer restarts, log in as an administrator.
-
Locate the following two DLL files in
C:\WINDOWS\syswow64and copy them toC:\WINDOWS\system32:oraidmpwf10.dllorclmessages.dllNote:
Be sure to copy (not move) these DLL files. A copy of the DLL files needs to be in both the <system root>
/system32and <system root>/syswow64folders. -
Restart the Active Directory server.
-
The Oracle Password Filter for Microsoft Active Directory is now installed.
19.5.2 Reconfiguring the Oracle Password Filter for Microsoft Active Directory
In most cases, you should not need to reconfigure the Oracle Password Filter following the installation process. However, you can reconfigure the Oracle Password Filter for Microsoft Active Directory by running the Oracle Password Filter for Microsoft Active Directory installation program.
Note:
The Microsoft Active Directory and Oracle Internet Directory configuration parameters listed in the following procedure are described in Table 19-1 and Table 19-2.
To reconfigure the Oracle Password Filter for Microsoft Active Directory:
-
Navigate to the directory where you extracted the installation files and double-click setup.exe. The Welcome page of the Oracle Password Filter for Microsoft Active Directory configuration program displays, informing you that the installation program will reconfigure the Oracle Password Filter for Microsoft Active Directory.
-
On the Welcome page, click Next. The Microsoft Active Directory Configuration Parameters page displays.

Description of the illustration oimig020.gif
-
On the Microsoft Active Directory Configuration Parameters page, modify the following parameters:
-
Domain
-
Base DN
-
Port
-
Host
-
-
Click Next. The Oracle Internet Directory Configuration Parameters page displays.
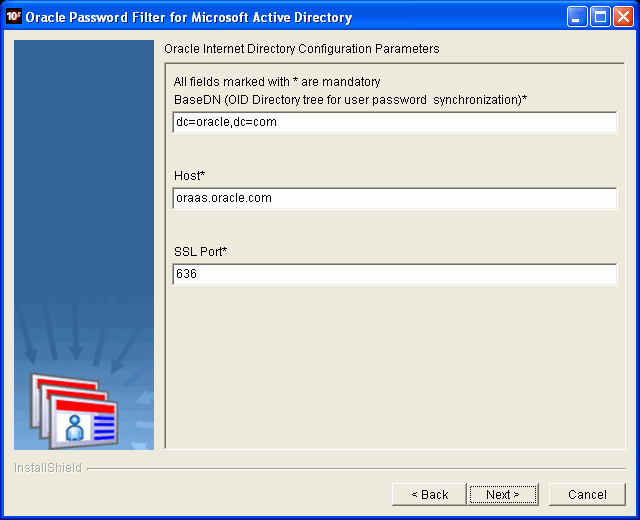
Description of the illustration oimig026.gif
-
On the Oracle Internet Directory Configuration Parameters page, modify the following parameters:
-
Base DN
-
Host
-
SSL Port
Note:
At the point of reconfiguring, two configuration set entries exist in Oracle Internet Directory and two instances of the Oracle Internet Directory server are running, each instance with one configuration set entry. Enter the SSL port of the second configuration set entry in the SSL Port field.
-
-
Click Next to continue. The Oracle Password Filter Configuration Parameters page displays.

Description of the illustration oimig023.gif
-
On the Oracle Password Filter Configuration Parameters page, modify the following parameters
-
SleepTime: The number of minutes between attempts to synchronize passwords changes between Oracle Internet Directory and Microsoft Active Directory.
-
ConfigSleepTime: The number of minutes between attempts to synchronize configuration changes between Oracle Internet Directory and Microsoft Active Directory.
-
ExcludeListDN: A fully qualified DN containing a list of users whose passwords should not be synchronized.
-
Maximum Retries: Specifies the maximum number of attempts to synchronize a password.
-
-
Click Next to continue. The Oracle Password Filter Users page displays.
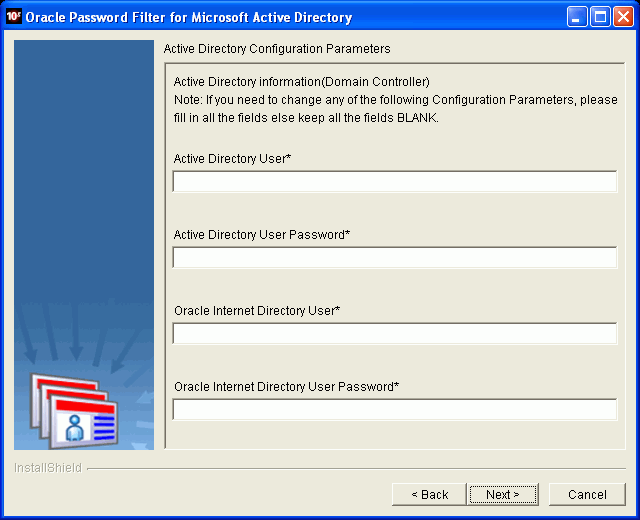
Description of the illustration oimig027.gif
-
On the Oracle Password Filter Users page, modify the following parameters:
-
Microsoft Active Directory User
-
Microsoft Active Directory User Password
-
Oracle Internet Directory User
-
Oracle Internet Directory User Password
Important:
If you have configured both import and export synchronization between Oracle Internet Directory and Microsoft Active Directory, be sure to enter for the User and User Password parameters the same bind DN and password that are specified in the synchronization profile that imports values from Microsoft Active Directory into Oracle Internet Directory. This is necessary to prevent password updates from looping between Oracle Internet Directory and Microsoft Active Directory.
-
-
Click Next to continue. The Reconfiguration Completed Successfully page displays.
-
On the Reconfiguration Completed Successfully page, click Finish to reconfigure the Oracle Password Filter.
19.6 Removing the Oracle Password Filter for Microsoft Active Directory
This section describes how to remove (uninstall) the Oracle Password Filter for Microsoft Active Directory.
To remove the Oracle Password Filter for Microsoft Active Directory:
-
Open in a text editor the prepAD.ldif file, which is located in the directory where you installed the Oracle Password Filter for Microsoft Active Directory. Delete the entries and container listed in the prepAD.ldif file from your Microsoft Active Directory installation.
-
Click the Windows Start menu and select Run.
The Run dialog box opens.
-
Enter regedt32 in the Run dialog box and click OK.
The Registry Editor opens.
-
Navigate to the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\orclidmpwf\OIDConfig
-
Note the container assigned to the
OidSinkNodeentry. The default value assigned to this entry iscn=Products,cn=OracleContext. -
Select Control Panel from the Windows Start menu. The Control Panel window displays. In the Control Panel window, select Add or Remove Programs. The Add or Remove Programs window displays.
-
In the Add or Remove Programs window, select Oracle Password Filter for Microsoft Active Directory from the list of currently installed programs, and then click Change/Remove. The Welcome page of the Oracle Password Filter for Microsoft Active Directory installation program displays, informing you that the program will remove the Oracle Password Filter for Microsoft Active Directory.
-
On the Welcome page, click Next. The Summary page displays and lists the path from where the Oracle Password Filter for Microsoft Active Directory will be removed.
-
On the Summary page, click Next. The Restart Required page appears notifying you that removing the Oracle Password Filter for Microsoft Active Directory requires a restart at the end of the deinstallation process.
-
On the Restart Required page, click Next. A final page appears informing you that you must restart your computer. Click Next to restart your computer.
-
On the system where Oracle Internet Directory is installed, use Oracle Directory Services Manager or ldapdelete to delete the following entry and its subentries in the
cn=PWSync,OidSinkNodecontainer:CN=Active_Directory_Host, cn=PWSync,OidSinkNode
-
Create a new text file named deleteOIDSchema.ldif that contains the following entries:
dn: cn=subschemasubentry changetype: modify delete: objectclasses objectclasses: ( 2.16.840.1.113894.8.2.1002 NAME 'adconfig' SUP top STRUCTURAL MUST ( cn ) MAY ( ADBaseDN $ deleteomain $ ADHost $ ADPort $ Log $ ResourceFilePath ) ) dn: cn=subschemasubentry changetype: modify delete: objectclasses objectclasses: ( 2.16.840.1.113894.8.2.1001 NAME 'oidconfig' SUP top STRUCTURAL MUST ( cn ) MAY ( OIDBaseDN $ OIDHost $ OIDPort $ passwdattr $ MSDEDSN $ OIDObjectClass $ OIDLog $ ExcludeListDN $ MAX_RETRIES $ OIDSSLType $ OIDWalletLoc $ OidSinkNode $ SleepTime $ stop $ ConfigSleepTime $ OIDConfigSynchKey ) ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1001 NAME 'OIDBaseDN' DESC 'OID Base Search DN' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1002 NAME 'OIDHost' DESC 'OID Host' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1003 NAME 'OIDPort' DESC 'OID Port' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1004 NAME 'passwdattr' DESC 'Pass Attribute' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1005 NAME 'MSDEDSN' DESC 'DB DSN' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1006 NAME 'OIDObjectClass' DESC 'AD Object Class' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1007 NAME 'OIDLog' DESC 'OID Log' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1008 NAME 'ExcludeListDN' DESC 'Exclude List' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1009 NAME 'MAX_RETRIES' DESC 'Max Retries' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1010 NAME 'OIDSSLType' DESC 'OID SSL Type' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1011 NAME 'OIDWalletLoc' DESC 'OID Wallet Loc' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1012 NAME 'OidSinkNode' DESC 'Config Sync Node' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1013 NAME 'SleepTime' DESC 'Sleep Time for store thread' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1014 NAME 'stop' DESC 'Stop flag for store thread' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1015 NAME 'ConfigSleepTime' DESC 'Sleep Time for config thread' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 22.16.840.1.113894.8.1.1016 NAME 'OIDConfigSynchKey' DESC 'Config Sync key' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1017 NAME 'ADBaseDN' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1018 NAME 'ADPort' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1019 NAME 'ADHost' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1020 NAME 'ADDomain' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1021 NAME 'Log' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' ) dn: cn=subschemasubentry changetype: modify delete: attributetypes attributetypes: ( 2.16.840.1.113894.8.1.1022 NAME 'ResourceFilePath' SYNTAX '1.3.6.1.4.1.1466.115.121.1.15' )
-
Use an
ldapmodifycommand to load the deleteOIDSchema.ldif file:$ORACLE_HOME/bin/ldapmodify -h OID host -p OID port \ -D binddn -q -f deleteOIDSchema.ldif
Note:
You will be prompted for the password.