11 Managing Keys and Certificates with the Keystore Service
This chapter explains how to use the Keystore Service to administer keys and certificates.
-
Section 11.2, "Keystore Management with the Keystore Service"
-
Section 11.3, "Certificate Management with the Keystore Service"
11.1 About the Keystore Service
The OPSS Keystore Service enables you to manage keys and certificates for SSL, message security, encryption, and related tasks. You use the Keystore Service to create and maintain keystores that contain keys, certificates, and other artifacts. The following topics introduce Keystore Service concepts:
11.1.1 Structure of the Keystore Service
Each keystore created with the Keystore Service is uniquely referenced by an application stripe and keystore.
-
Application Stripe
Keys and certificates created in the keystore reside in an application stripe or product, and each stripe in a domain is uniquely named.
-
Keystore
The keystore name is unique within an application stripe. Each product or application is allowed to create more than one keystore within its application stripe.
Thus (appstripe1, keystoreA) is unique and distinct from (appstripe1, keystoreB), which is distinct from (appstripe2, keystoreA).
In turn, each keystore may contain the following entries, referenced by an alias that is unique within the keystore :
-
Asymmetric Keys - These include the public key and the corresponding private key, and are typically used for SSL communication. The public key is wrapped in a certificate.
-
Symmetric Keys - These keys are generally used for encryption.
-
Trusted Certificates - These certificates are typically used to establish trust with an SSL peer.
11.1.2 Types of Keystores
The Keystore Service lets you create two types of keystores:
-
Keystores protected by Permission
These types of keystores are protected by authorization policies and any access to them by runtime code is protected by code source permissions. The key data in the backend is encrypted using an encryption key that is generated uniquely for each domain.
-
Keystores protected by Password
These types of keystores are protected by keystore and/or key passwords. Any access to them by runtime code requires access to the keystore and key password (if different from the keystore password). The key data in the back-end is encrypted using the keystore/key password through password based encryption (PBE).
It is recommended that you use permission-protected keystores for applications. If you require high security and are willing to manage passwords, however, consider using keystores that are password-protected.
Note:
The Keystore Service does not manage passwords for keystore or keys. The product or application is responsible for managing them in an appropriate repository. For example, you may choose to store the passwords for your applications in a credential store.
11.1.3 Domain Trust Store
Although each application may configure multiple keystores for its SSL usage, a domain-level trust store comes pre-configured for all products and applications to use for trust management.
This domain trust store contains the trusted certificates of most well-known third-party Certificate Authorities (CAs) as well as the trusted certificate of the demo CA that is configured with the Keystore Service. Each application can simply point to this domain trust store for its SSL needs, eliminating the need to create a dedicated trust store for this task.
For one-way SSL, applications can simply use the domain trust store and do not need to create any keystore or trust store.
For two-way SSL, applications should create only the keystore containing their identity certificate and use the domain trust store for trust.
Note:
The domain trust store is a shared store for all products and applications in a domain. The decision to add or remove trust should not be taken lightly since it may affect all other products in the domain.
Consider creating a custom trust store only if a product's trust management requirements are not met by the domain trust store.
11.1.4 Keystores for Domains with Multiple Servers
For a domain with multiple servers, the only recommended store types are LDAP or DB. Do not configure a file-based store in such an environment.
11.2 Keystore Management with the Keystore Service
This section describes the typical life cycle of keystores and certificates, and how to use the keystore service to create and maintain keystores and certificates. It includes these topics:
11.2.1 About the Keystore Life Cycle
Typical life cycle events for a KSS keystore are as follows:
-
The keystore is created in the context of an application stripe. Keystores can be created directly or by importing a keystore file from the file system.
-
The list of available keystores is viewed and specific keystores selected for update.
-
Keystores are updated or deleted. For a password-protected keystore, update operations require that the keystore password be entered.
-
The keystore password can be changed.
-
The keystore can be deleted.
-
Keystores can be exported and imported. KSS supports migration for JKS and JCEKS certificate formats.
11.2.2 Common Keystore Operations
This section explains the following keystore operations that you can perform through Fusion Middleware Control or at the command line:
11.2.2.1 Creating a Keystore with Fusion Middleware Control
Take these steps to create a keystore:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Select the stripe in which the keystore is to be created. If necessary, create a stripe as follows:
-
Click Create Stripe. The Create Stripe dialog appears.
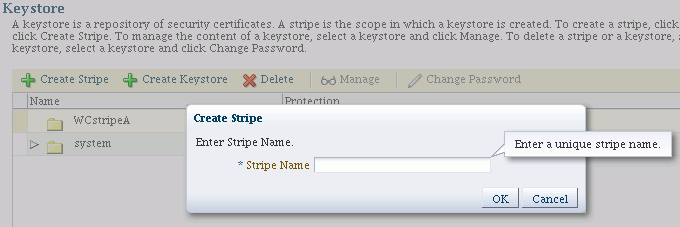
-
Provide a unique stripe name. Any combination of characters is possible, but it is recommended that you do not use the forward slash (/) in the name.
-
Click Submit. The new stripe appears in the list of stripes and you can select it for keystore creation.
-
-
Click Create Keystore.
-
The Create Keystore dialog appears.
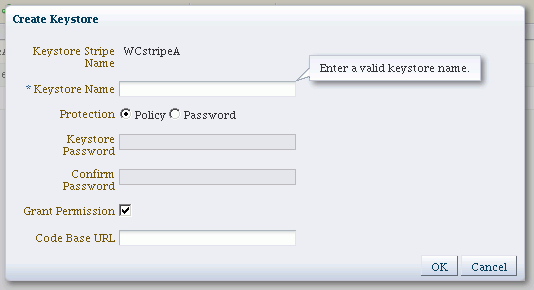
-
Complete the dialog form as follows:
-
Keystore Name: Enter a unique keystore name. Do not use any special (non-ascii) characters or characters from a different encoding or locale.
-
Protection Type: Select the protection mechanism for the keystore; choose between Policy and Password.
-
For a password-protected keystore, enter a valid password.
-
Grant Permission: Check this box to grant permissions using code URL.
-
-
Click OK. The new keystore appears under the appropriate stripe.
11.2.2.2 Creating a Keystore at the Command Line
You can create a keystore using the createKeyStore script at the command line. For example, assuming the stripe name is teststripe1, use this command to create a permission-based keystore:
svc.createKeyStore(appStripe='teststripe1', name='keystore1', password='password',permission=true)
where password is the password for this keystore. Section 11.4 explains how to obtain the OPSS service command object.
Any combination of characters is possible when specifying a new stripe, but it is recommended that you do not use the forward slash (/) in the name.
Enter a unique keystore name. Do not use any special (non-ascii) characters or characters from a different encoding or locale.
See Also:
11.2.2.3 Deleting a Keystore with Fusion Middleware Control
When you delete a keystore, be aware that all certificates in the keystore are also deleted. If any functions rely on these certificates, they will be rendered unusable as a result.
Take these steps to delete a keystore:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Delete.
-
The Delete Keystore dialog appears.
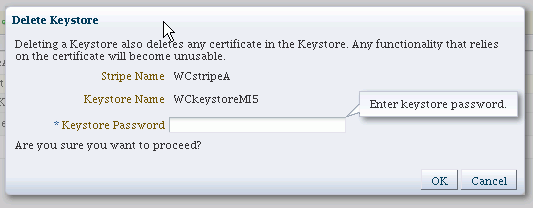
-
If this is a password-protected keystore, enter the keystore password.
-
Click OK.
11.2.2.4 Deleting a Keystore at the Command Line
You can delete a keystore using the deleteKeyStore script at the command line. For example, assuming the stripe is named appstripe1, use this command to delete a keystore:
svc.deleteKeyStore(appStripe='appstripe1', name='keystore1', password='password')
where password is the password for this keystore. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.2.2.5 Changing Keystore Password with Fusion Middleware Control
To change the password for a password-protected keystore:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Change Password.
-
The Change Keystore Password dialog appears.

-
Enter the old and new passwords.
-
Click OK.
11.2.2.6 Changing Keystore Password at the Command Line
You can change a keystore's password using the changeKeyStorePassword script at the command line. For example, assuming the instance name is system, use this command to change the keystore password:
svc.changeKeyStorePassword(appStripe='system', name='keystore2', currentpassword='currentpassword', newpassword='newpassword')
where currentpassword is the current password for this keystore, and newpassword is the new password. Section 11.4 explains how to obtain the OPSS service command object.
11.2.2.7 Exporting a Keystore at the Command Line
You can export a keystore using the exportKeyStore script at the command line. For example, assuming stripe name mystripe, alias named myorakey to be exported, alias password keypassword1, the following command exports the keystore to a file:
svc.exportKeyStore(appStripe='mystripe', name='keystore2', password='password',aliases='myorakey', keypasswords='keypassword1', type='JKS',filepath='/tmp/file.jks')
where password is the password for this keystore. Section 11.4 explains how to obtain the OPSS service command object.
To export multiple keys using this command, specify a comma-separated list of aliases and keypasswords.
When exporting a keystore containing a symmetric key, use the JCEKS type. For example:
svc.exportKeyStore(appStripe='mystripe', name='keystore2', password='password',aliases='myorakey', keypasswords='keypassword1', type='JCEKS',filepath='/tmp/file.jks')
See Also:
11.2.2.8 Importing a Keystore at the Command Line
You can import a keystore using the importKeyStore script at the command line. For example, assuming stripe name mystripe, alias named myorakey to be imported, alias password keypassword1, the following command imports a keystore from an operating system file:
svc.importKeyStore(appStripe='mystripe', name='keystore2', password='password',aliases='myorakey', keypasswords='keypassword1', type='JKS', permission=true, filepath='/tmp/file.jks')
where password is the keystore password. Section 11.4 explains how to obtain the OPSS service command object.
To import multiple keys using this command, specify a comma-separated list of aliases and keypasswords.
See Also:
11.3 Certificate Management with the Keystore Service
This section explains how to manage certificates with the Keystore Service. It contains these topics:
11.3.1 About the Certificate Life-cycle
Typical life cycle events for a certificate residing in a Keystore Service keystore are as follows:
-
A self-signed certificate is automatically created for the keypair.
-
A certificate signing request (CSR) is generated for the certificate, and can be saved to a file.
-
The CSR is sent to a certificate authority, who verifies the sender, signs and returns the signed certificate.
-
Certificates are imported into the keystore. A certificate can either be pasted into a text box or imported from the file system. You can import both user certificates and trusted certificates (also known as CA certificates) in this way.
-
Certificates or trusted certificates are exported from the keystore out to a file.
-
Certificates or trusted certificates are deleted from the keystore.
11.3.2 Common Certificate Operations
This section explains the common certificate operations:
-
Generating CSR for a Certificate with Fusion Middleware Control
-
Importing a Certificate or Trusted Certificate with Fusion Middleware Control
-
Exporting a Certificate or Trusted Certificate with Fusion Middleware Control
-
Exporting a Certificate or Trusted Certificate at the Command Line
-
Changing Certificate Password with Fusion Middleware Control
11.3.2.1 Generating a Keypair with Fusion Middleware Control
To generate a certificate with an associated keypair:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
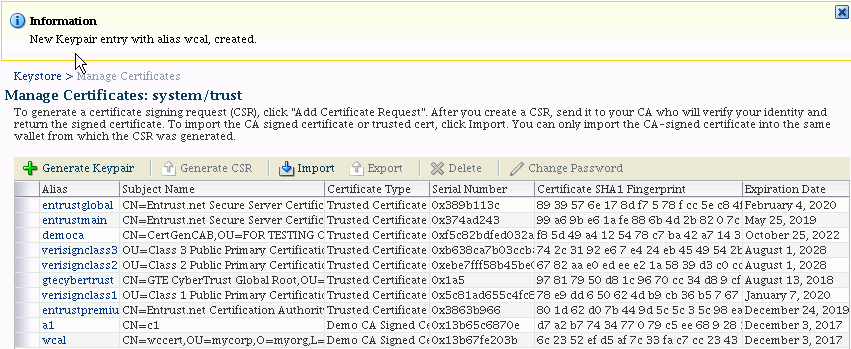
The Manage Certificates page appears:
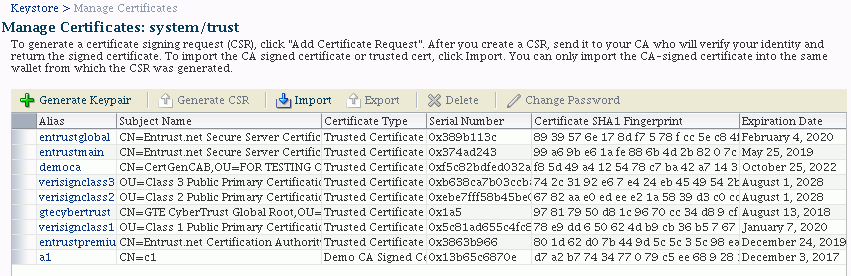
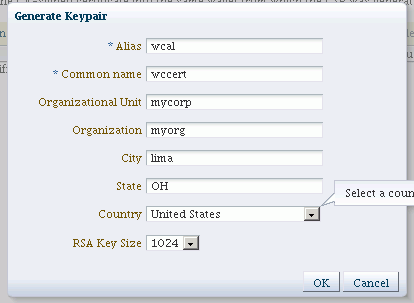
Click Generate Keypair.
-
The Generate Keypair dialog appears:
-
Provide the following information:
-
Alias (required)
-
Common Name (required)
-
Organizational Unit
-
Organization
-
City
-
State
-
Country: Choose from the drop-down box.
-
RSA Key Size: Choose from the drop-down box. Default is 1024 bytes.
-
-
Click OK.
The new certificate appears in the list of certificates.
-
You can view the certificate details by clicking on the certificate alias:
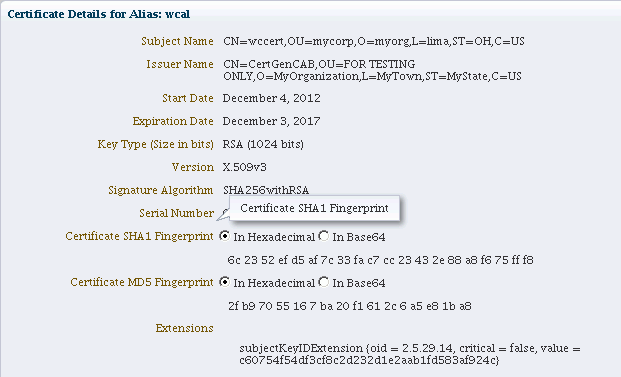
The generated keypair is wrapped in a CA signed certificate (using a Demo CA). To use this certificate for SSL or where trust needs to be established, applications must either use the domain trust store as their trust store (since it contains the Demo CA certificate) or import the certificate to a custom application-specific trust store..
11.3.2.2 Generating a Keypair at the Command Line
You can generate a keypair for a keystore using the generateKeyPair script at the command line. For example, assuming an application stripe named appstripe2, the following command creates a keypair with alias myalias:
svc.generateKeyPair(appStripe='appstripe2', name='keystore2', password='password', dn='cn=www.example.com', keysize='1024', alias='myalias', keypassword='keypassword')
where password is the keystore password and keypassword is the password of the alias. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
The generated keypair is wrapped in a CA signed certificate (using a Demo CA). To use this certificate for SSL or where trust needs to be established, applications must either use the domain trust store as their trust store (since it contains the Demo CA certificate) or import the certificate to a custom application-specific trust store.
11.3.2.3 Generating CSR for a Certificate with Fusion Middleware Control
To generate a CSR for a certificate or trusted certificate:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
The Manage Certificates page appears. Select the row corresponding to the certificate and click Generate CSR.
-
The Generate CSR dialog appears:

You can:
-
Copy and paste the entire CSR into a text file, and click Close.
or
-
Click Export CSR to automatically save the CSR to a file.
-
You can send the resulting certificate request to a certificate authority (CA) which will return a signed certificate.
11.3.2.4 Generating CSR for a Keypair at the Command Line
You can generate a CSR for a keypair using the exportKeyStoreCertificateRequest script at the command line. For example, assuming an application stripe stripe1, the following command generates a CSR from the keypair testalias:
svc.exportKeyStoreCertificateRequest(appStripe='stripe1', name='keystore1', password='password', alias='testalias', keypassword='keypassword', filepath='/tmp/csr-file')
where password is the keystore password and keypassword is the password of the alias. The CSR is exported to an operating system file. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.3.2.5 Importing a Certificate or Trusted Certificate with Fusion Middleware Control
To import a certificate into a password-protected keystore:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
The Manage Certificates page appears. Click Import.
-
The Import Certificate dialog appears:
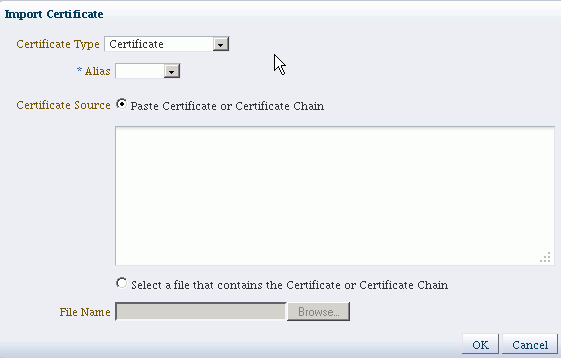
Complete this form as follows:
-
Select the certificate type, either Certificate or Trusted Certificate, from the drop-down.
-
Select the alias from the drop-down.
-
Specify the certificate source. If using the Paste option, copy and paste the certificate directly into the text box. If using the Select a file option, click Browse to select the file from the operating system.
-
Click OK. The imported certificate or trusted certificate appears in the list of certificates.
-
-
Click OK.
The certificate appears in the list of certificates.
11.3.2.6 Importing a Certificate at the Command Line
You can import a certificate using the importKeyStoreCertificate script at the command line. For example, assuming an application stripe appstripe1, the following command imports a certificate with alias mykey from an operating system file:
svc.importKeyStoreCertificate(appStripe='appstripe1', name='keystore2', password='password', alias='mykey', keypassword='keypassword', type='Certificate', filepath='/tmp/cert.txt')
where password is the keystore password and keypassword is the password of the alias. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.3.2.7 Exporting a Certificate or Trusted Certificate with Fusion Middleware Control
Take these steps to export a certificate or trusted certificate:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
The Manage Certificates page appears. Select the row corresponding to the certificate and click Export .
-
The certificate export dialog appears:
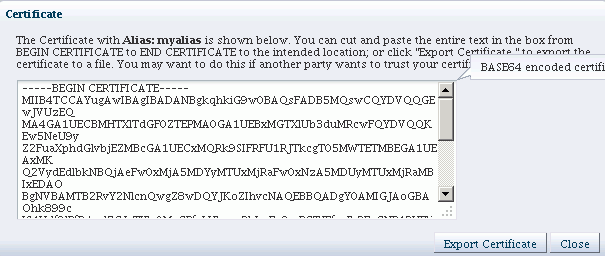
You can:
-
Copy and paste the entire certificate into a text file, and click Close.
or
-
Click Export Certificate to automatically save the certificate to a file.
-
11.3.2.8 Exporting a Certificate or Trusted Certificate at the Command Line
You can export a certificate using the exportKeyStoreCertificate script at the command line. For example, assuming an application stripe appstripe1, the following command exports a certificate with alias mykey to an operating system file:
svc.exportKeyStoreCertificate(appStripe='appstripe1', name='keystore2', password='password', alias='mykey', keypassword='keypassword', type='Certificate', filepath='/tmp/cert.txt')
where password is the keystore password and keypassword is the password of the alias. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.3.2.9 Deleting a Certificate with Fusion Middleware Control
Take these steps to delete a certificate:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
The Manage Certificates page appears. Select the row corresponding to the certificate and click Delete.
-
The Delete Certificate dialog appears:
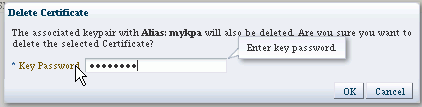
You are asked to confirm deletion. Click OK.
11.3.2.10 Deleting a Certificate at the Command Line
You can delete a certificate from a keystore using the deleteKeyStoreEntry script at the command line. For example, assuming an application stripe appstripe, the following command deletes a certificate with alias orakey:
ssvc.deleteKeyStoreEntry(appStripe='appstripe', name='keystore2', password='password', alias='orakey', keypassword='keypassword')
where password is the keystore password and keypassword is the password of the alias. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.3.2.11 Changing Certificate Password with Fusion Middleware Control
Take these steps to change certificate password:
-
Log in to Fusion Middleware Control.
-
From the navigation pane, locate the domain of interest.
-
Navigate to Security, then Keystore. The Keystore page appears.
-
Expand the stripe in which the keystore resides. Select the row corresponding to the keystore.
-
Click Manage.
-
If the keystore is password-protected, you are prompted for a password. Enter the keystore password and click OK.
-
The Manage Certificates page appears. Select the row corresponding to the certificate and click Change Password.
-
The Change Key Password dialog appears:
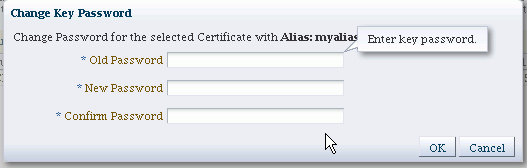
-
Enter the old and new passwords and click OK.
11.3.2.12 Changing Certificate Password at the Command Line
You can change a certificate password using the changeKeyPassword script at the command line. For example, assuming an application stripe system1, the following command deletes a certificate with alias testkey:
svc.changeKeyPassword(appStripe='system1', name='keystore', password='password', alias='testkey', currentkeypassword='currentkeypassword', newkeypassword='newkeypassword')
where password is the keystore password and keypassword is the password of the certificate alias. Section 11.4 explains how to obtain the OPSS service command object.
See Also:
11.4 About Keystore Service Commands
The Keystore Service uses a dedicated set of command-line commands for keystore operations such as creating and managing keystores, exporting certificates, and generating keypairs. While their usage is similar, these commands are distinct from other OPSS commands.
The starting point for using the Keystore Service command set is getOpssService, which gets an OPSS service command object that enables you to:
-
execute commands for the service
-
obtain command help
The general syntax is:
variable = getOpssService(name='service_name')
where
-
the
variablestores the command object -
the service name refers to the service whose command object is to be obtained. The only valid value is '
KeyStoreService'.
For example:
svc = getOpssService(name='KeyStoreService')
11.5 Getting Help for Keystore Service Commands
To obtain help for any Keystore Service command, start by obtaining a service command object as explained in Section 11.4. Use this object in conjunction with the help command and the command in question.
To obtain a list of all Keystore Service commands, enter:
svc.help()
To obtain help for a specific command, enter:
svc.help('command-name')
For example, the following returns help for the exportKeyStore command:
svc.help('exportKeyStore')
11.6 Keystore Service Command Reference
This section provides a reference to the keystore service commands, which are listed in Table 11-1.
Note:
The abbreviation KSS is used to refer to the Keystore Service in command descriptions. Thus KSS keystore refers to a keystore created and managed with the Keystore Service.
Table 11-1 Keystore Service Commands
| Command | Description |
|---|---|
|
Changes the password for a key. |
|
|
Changes the password of a keystore. |
|
|
Creates a new keystore. |
|
|
Deletes the named keystore. |
|
|
Deletes a keystore entry. |
|
|
Exports a keystore to file. |
|
|
Exports a certificate, trusted certificate, or certificate chain. |
|
|
Generates and exports a certificate request. |
|
|
Generates a key pair in a keystore. |
|
|
Generates a symmetric key in a keystore. |
|
|
Retrieves information about a certificate or trusted certificate. |
|
|
Retrieves secret key properties. |
|
|
Imports a keystore from a file. |
|
|
Imports a certificate, trusted certificate or certificate chain. |
|
|
Lists expiring certificates and optionally renews them. |
|
|
Lists the aliases in a keystore. |
|
|
Lists the keystores in a stripe. |
11.6.1 changeKeyPassword
Changes the password for a key identified by an alias.
svc.changeKeyPassword(appStripe='stripe', name='keystore', password='password', alias='alias', currentkeypassword='currentkeypassword', newkeypassword='newkeypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= name of the keystore.
-
password= the keystore password.
-
alias= alias of the key entry whose password is changed.
-
currentkeypassword= the current key password.
-
newkeypassword= the new key password.
svc.changeKeyPassword(appStripe='system', name='keystore', password='password', alias='orakey', currentkeypassword='currentkeypassword', newkeypassword='newkeypassword')
11.6.2 changeKeyStorePassword
Changes the password of a KSS keystore.
svc.changeKeyStorePassword(appStripe='stripe', name='keystore', currentpassword='currentpassword', newpassword='newpassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore whose password is changed.
-
currentpassword= current keystore password.
-
newpassword= new keystore password.
svc.changeKeyStorePassword(appStripe='system', name='keystore2', currentpassword='currentpassword', newpassword='newpassword')
11.6.3 createKeyStore
Creates a new KSS keystore.
svc.createKeyStore(appStripe='stripe', name='keystore', password='password',permission=true|false)
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe in which the keystore is created.
-
name= the name of the keystore.
-
password= Password of the keystore.
-
permission= true if keystore is protected by permission only, false if protected by password.
svc.createKeyStore(appStripe='system', name='keystore1', password='password',permission=true)
11.6.4 deleteKeyStore
Deletes the named KSS keystore.
svc.deleteKeyStore(appStripe='stripe', name='keystore', password='password')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe in which keystore resides.
-
name= the name of the keystore to be deleted.
-
password= password of the keystore to be deleted.
svc.deleteKeyStore(appStripe='system', name='keystore1', password='password')
11.6.5 deleteKeyStoreEntry
Deletes a KSS keystore entry.
svc.deleteKeyStoreEntry(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= alias of the entry to be deleted.
-
keypassword= the key password of the entry to be deleted.
svc.deleteKeyStoreEntry(appStripe='system', name='keystore2', password='password', alias='orakey', keypassword='keypassword')
11.6.6 exportKeyStore
Exports a KSS keystore to a file.
svc.exportKeyStore(appStripe='stripe', name='keystore', password='password', aliases='comma-separated-aliases', keypasswords='comma-separated-keypasswords', type='keystore-type', filepath='absolute_file_path')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the password of the KSS keystore as well as the file to which the keystore is exported. Note that if the file does not exist, its password is set to the specified password. If it exists, its password is changed to the specified password.
-
aliases= comma separated list of aliases to be exported.
-
keypasswords= comma-separated list of the key passwords corresponding to aliases. The password is required if exporting from a password-protected keystore. The password is ignored for a permission-protected keystore.
-
type= exported keystore type. Valid values are 'JKS' or 'JCEKS'.
-
filepath= absolute path of the file where keystore is exported.
svc.exportKeyStore(appStripe='system', name='keystore2', password='password',aliases='orakey,seckey', keypasswords='keypassword1,keypassword2', type='JKS',filepath='/tmp/file.jks')
11.6.7 exportKeyStoreCertificate
Exports a certificate, trusted certificate, or certificate chain from a KSS keystore.
svc.exportKeyStoreCertificate(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword', type='entrytype',filepath='absolute_file_path')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= alias of the entry to be exported.
-
keypassword= the key password.
-
type= type of keystore entry to be exported. Valid values are 'Certificate', 'TrustedCertificate' or 'CertificateChain'.
-
filepath= absolute path of the file where certificate, trusted certificate or certificate chain is exported.
svc.exportKeyStoreCertificate(appStripe='system', name='keystore2', password='password', alias='orakey', keypassword='keypassword', type='Certificate', filepath='/tmp/cert.txt')
11.6.8 exportKeyStoreCertificateRequest
Generates and exports a certificate request.
svc.exportKeyStoreCertificateRequest(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword', filepath='absolute_file_path')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= alias of the key pair from which certificate request is generated.
-
keypassword= the key pair password.
-
filepath= absolute path of the file where certificate request should be exported.
svc.exportKeyStoreCertificateRequest(appStripe='system', name='keystore2', password='password', alias='orakey', keypassword='keypassword', filepath='/tmp/certreq.txt')
11.6.9 generateKeyPair
Generates a key pair in a KSS keystore and wraps it in a demo CA-signed certificate.
svc.generateKeyPair(appStripe='stripe', name='keystore', password='password', dn='distinguishedname', keysize='keysize', alias='alias', keypassword='keypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore where key pair is generated.
-
password= the keystore password.
-
dn= the distinguished name of the certificate wrapping the key pair.
-
keysize= the key size.
-
alias= the alias of the key pair entry.
-
keypassword= the key password.
svc.generateKeyPair(appStripe='system', name='keystore2', password='password', dn='cn=www.myhost.com', keysize='1024', alias='orakey', keypassword='keypassword')
11.6.10 generateSecretKey
Generates a symmetric key in a KSS keystore.
svc.generateSecretKey(appStripe='stripe', name='keystore', password='password', algorithm='algorithm', keysize='keysize', alias='alias', keypassword='keypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore where symmetric key is generated.
-
password= the keystore password.
-
algorithm= the symmetric key algorithm.
-
keysize= the key size.
-
alias= the alias of the key entry.
-
keypassword= the key password.
svc.generateSecretKey(appStripe='system', name='keystore2', password='password', algorithm='AES', keysize='128', alias='seckey', keypassword='keypassword')
11.6.11 getKeyStoreCertificates
Retrieves information about a certificate or trusted certificate.
svc.getKeyStoreCertificates(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
keypassword= the key password.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= the alias of the certificate, trusted certificate, or certificate chain to be displayed.
svc.getKeyStoreCertificates(appStripe='system', name='keystore3', password='password', alias='orakey', keypassword='keypassword')
11.6.12 getKeyStoreSecretKeyProperties
Retrieves secret key properties like the algorithm.
svc.getKeyStoreSecretKeyProperties(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= the alias of the secret key whose properties are displayed.
-
keypassword= the secret key password.
svc.getKeyStoreSecretKeyProperties(appStripe='system', name='keystore3', password='password', alias='seckey', keypassword='keypassword')
11.6.13 importKeyStore
Imports a KSS keystore from file.
svc.importKeyStore(appStripe='stripe', name='keystore', password='password', aliases='comma-separated-aliases', keypasswords='comma-separated-keypasswords', type='keystore-type', permission=true|false, filepath='absolute_file_path')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
aliases= comma separated aliases of the entries to be imported from file.
-
keypasswords= comma separated passwords of the keys in file.
-
type= Imported keystore type. Valid values are 'JKS' or 'JCEKS'.
-
filepath= absolute path of the keystore file to be imported.
svc.importKeyStore(appStripe='system', name='keystore2', password='password',aliases='orakey, seckey', keypasswords='keypassword1, keypassword2', type='JKS', permission=true, filepath='/tmp/file.jks')
11.6.14 importKeyStoreCertificate
Imports a certificate, trusted certificate, or certificate chain to a KSS keystore.
svc.importKeyStoreCertificate(appStripe='stripe', name='keystore', password='password', alias='alias', keypassword='keypassword', type='entrytype', filepath='absolute_file_path')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
alias= alias of the entry to be imported.
-
keypassword= the key password of the newly imported entry.
-
type= type of keystore entry to be imported. Valid values are 'Certificate', 'TrustedCertificate' or 'CertificateChain'.
-
filepath= absolute path of the file from where certificate, trusted certificate or certificate chain is imported.
svc.importKeyStoreCertificate(appStripe='system', name='keystore2', password='password', alias='orakey', keypassword='keypassword', type='Certificate', filepath='/tmp/cert.txt')
11.6.15 listExpiringCertificates
Lists expiring certificates and optionally renews them.
svc.listExpiringCertificates(days='days', autorenew=true|false)
where:
-
svc=the service command object obtained through a call to getOpssService().
-
days=only list certificates within these many days from expiration.
-
autorenew=
truefor automatically renewing expiring certificates;falsefor only listing them.
svc.listExpiringCertificates(days='365', autorenew=true)
11.6.16 listKeyStoreAliases
Lists the aliases in a KSS keystore for a given type of entry.
svc.listKeyStoreAliases(appStripe='stripe', name='keystore', password='password', type='entrytype')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe containing the keystore.
-
name= the name of the keystore.
-
password= the keystore password.
-
type= the type of entry for which aliases are listed. Valid values are 'Certificate', 'TrustedCertificate', 'SecretKey' or '*' (wildcard).
svc.listKeyStoreAliases(appStripe='system', name='keystore2', password='password', type='Certificate') svc.listKeyStoreAliases(appStripe='system', name='keystore2', password='password', type='TrustedCertificate') svc.listKeyStoreAliases(appStripe='system', name='keystore2', password='password', type='SecretKey') svc.listKeyStoreAliases(appStripe='system', name='keystore2', password='password', type='*')
11.6.17 listKeyStores
Lists all the KSS keystores in a stripe.
svc.listKeyStores(appStripe='stripe')
where:
-
svc=the service command object obtained through a call to getOpssService().
-
appStripe= the name of the stripe whose keystores are listed.
svc.listKeyStores(appStripe='system') svc.listKeyStores(appStripe='*')