4 Integrating Oracle Identity Federation
This chapter describes how to integrate Oracle Access Manager with Oracle Identity Federation to create an authenticated session.
This chapter contains these sections:
-
Configuring Oracle Identity Federation for Oracle Access Manager
-
Configuring Oracle Access Manager for Oracle Identity Federation
4.1 Background and Integration Overview
This section provides background about the integration procedure. Topics include:
4.1.1 About Integration with Oracle Identity Federation
About Oracle Identity Federation
Oracle Identity Federation is a standalone, self-contained federation server that enables single sign-on and authentication in a multiple-domain identity network.
The SP integration Engine included with Oracle Identity Federation consists of a servlet that processes requests from the server to create a user authenticated session at the Identity and Access Management (IAM) server. The engine includes several internal plug-ins that allow it to interact with different IAM servers, including Oracle Access Manager.
Two integration modes are described in this chapter:
-
SP Mode
This mode enables Oracle Identity Federation to authenticate the user and propagate the authentication state to Oracle Access Manager, which maintains the session information.
-
Authentication Mode
This mode enables Oracle Access Manager to authenticate the user.
Note:
When integrating in Authentication Mode, SP Mode will be required for logout purposes.
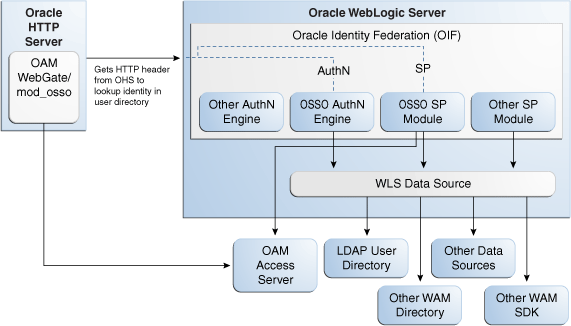
Figure 4-1 describes the processing flow in each mode.
In the SP mode, Oracle Identity Federation uses the federation protocols to identify a user, and requests the authentication module to create an authenticated session at Oracle Access Manager. To integrate in SP mode, see "SP Mode Integration Procedure".
In the authentication mode, Oracle Access Manager looks up the user identity in the LDAP store and obtains a session cookie so that the user can access the requested resource, which is protected by either mod_osso or Oracle Access Manager 11g WebGate. To integrate in authentication mode, see "Authentication Mode Integration Procedure".
4.1.2 Overview of Integration Tasks
The tasks required to integrate Oracle Access Manager with Oracle Identity Federation are similar for both modes, with some variation.
Configuring the SP mode requires the following tasks:
-
Ensure that the necessary components, including Oracle WebLogic Server and Identity Management (IdM) components, are installed and operational.
For details, see Section 4.1.3 and Section 4.1.4.
-
Register Oracle HTTP Server as a partner with Oracle Access Manager to protect a resource.
For details, see Section 4.2.
-
Configure the Oracle Identity Federation server to function as a service provider (SP) with Oracle Access Manager.
For details, see Section 4.3.
-
Configure the Oracle Access Manager server to delegate the authentication to Oracle Identity Federation.
For details, see Section 4.4.
-
Protect the resource with the OIFScheme.
For details, see Section 4.5.
-
Test the integration.
For details, see Section 4.6.
Authentication Mode Integration Procedure
Configuring the authentication mode requires the following tasks:
-
Ensure that the necessary components, including Oracle WebLogic Server and Identity Management (IdM) components, are installed and operational.
For details, see Section 4.1.3 and Section 4.1.4.
-
Register Oracle HTTP Server as a partner with the Oracle Access Manager server to protect a resource.
For details, see Section 4.2.
-
Configure the Oracle Identity Federation server to function as an identity provider (IdP) with Oracle Access Manager.
For details, see Section 4.3.
-
Test the integration.
For details, see Section 4.6.
4.1.3 Prerequisites
You must install the following components prior to undertaking the integration tasks:
-
Oracle WebLogic Server
-
Oracle HTTP Server 11g
-
Oracle Access Manager 11g
-
Oracle Identity Federation 11g
-
mod_osso (required in authentication mode)
Note:
Refer to the Certification Matrix for platform and version details.
4.1.4 Additional Setup
Ensure that the administration and managed servers are up and running.
For testing purposes, identify or create a resource to be protected; for example, create an index.html file to serve as a test resource.
Access the Fusion Middleware Control console for the Oracle Identity Federation server using a URL of the form:
http://oif_host:oif_em_port/em
Verify that all the servers are running.
4.2 Register Oracle HTTP Server with Oracle Access Manager
This section shows how you can register Oracle HTTP Server and either 11g WebGate or mod_osso with Oracle Access Manager, depending on the protection mechanism you have chosen.
This section contains these topics:
-
Register Oracle HTTP Server and mod_osso with Oracle Access Manager
-
Register Oracle HTTP Server and WebGate with Oracle Access Manager
4.2.1 Register Oracle HTTP Server and mod_osso with Oracle Access Manager
Follow these steps to register Oracle HTTP Server and mod_osso with Oracle Access Manager:
Note:
MW_HOME represents the Oracle Fusion Middleware Home directory.
-
Locate the
OSSORequest.xmlfile in the directory:MW_HOME/Oracle_IDM1/oam/server/rreg/input
Make the necessary changes to the file by setting the host, port, and agent name to appropriate values. The server address is the Oracle Access Manager admin server address and AgentBaseURL must have the Oracle HTTP Server host and port.
-
Locate the
oamreg.shscript, which resides in:MW_HOME/Oracle_IDM1/oam/server/rreg/bin
Execute the script using this command string (user is
weblogic, and you must supply the password):./oamreg.sh inband input/OSSORequest.xml
-
Configure mod_osso with static directives. For instructions see "Configuring mod_osso with Static Directives" in the Oracle Fusion Middleware Application Security Guide.
-
The script executed in Step 3 generates an
osso.conffile in the directory:MW_HOME/Oracle_IDM1/oam/server/rreg/output/AgentNameCopy the file to the following location:
Oracle_WT1/instances/instance1/config/OHS/ohs1/moduleconf/osso/
-
Locate the
mod_osso.conffile in the directory:Oracle_WT1/instances/instance1/config/OHS/ohs1/moduleconf
Add these directives to the file:
OssoSecureCookies offOssoConfigFile path_to_osso.conf_file -
Uncomment the
Locationtag and fill in the protected resource path.In authentication mode:
<Location /fed/user/authnoam11g> require valid-user AuthType Osso </Location>
-
Restart Oracle HTTP Server.
Oracle_WT1/instances/instance1/bin/opmnctl restartproc process-type=OHS
4.2.2 Register Oracle HTTP Server and WebGate with Oracle Access Manager
Integrating Oracle Access Manager 11g WebGate with Oracle Identity Federation requires:
-
Integrating Oracle Identity Federation with Oracle Access Manager 11g in SP mode (as described in Section 4.3), using the OAM11g SP engine
-
Enabling logout in the OAM11g SP engine: the logout integration with Oracle Access Manager 11g will be performed using the OAM11g SP engine, instead of the OAM11g authentication engine
Follow these steps to register Oracle HTTP Server andOracle Access Manager 11g WebGate with Oracle Access Manager for authentication:
Note:
In this procedure, MW_HOME represents the Oracle Fusion Middleware Home directory.
-
Locate the OAM11GRequest.xml file or the OAM11GRequest_short.xml file, which resides in the directory:
MW_HOME/Oracle_IDM1/oam/server/rreg/input
Make the necessary changes to the file.
-
Locate the oamreg.sh script, which resides in the directory:
MW_HOME/Oracle_IDM1/oam/server/rreg/bin
Execute the script using the command string:
Note:
The user is
weblogic, and you must supply the password../oamreg.sh inband input/OAM11GRequest.xml
or
./oamreg.sh inband input/OAM11GRequest_short.xml
-
Using the Oracle Access Manager console, create a resource representing the Oracle Identity Federation URL to be protected by Oracle Access Manager for authentication. This URL contains the hostname and port of the Oracle Identity Federation server, and the path to the resource, which is mode-dependent.
For example, in authentication mode:
https://oif-host:oif-port/fed/user/authnoam11g -
Protect this resource with an authentication policy and an authorization policy.
-
Restart Oracle HTTP Server:
Oracle_WT1/instances/instance1/bin/opmnctl restartproc process-type=OHS
4.3 Configuring Oracle Identity Federation for Oracle Access Manager
This section describes how to configure Oracle Identity Federation to be integrated with Oracle Access Manager:
-
In SP mode, where Oracle Access Manager will delegate authentication to Oracle Identity Federation for Federation SSO.
-
In Authentication mode, where Oracle Identity Federation will delegate authentication to Oracle Access Manager.
Note:
When integrating in Authentication Mode, SP Mode will be required for logout purposes.
This section contains these topics:
-
Configuring the Oracle Identity Federation Authentication Engine
-
Configuring the Oracle Identity Federation SP Integration Module
4.3.1 Verifying User Data
Oracle Identity Federation and Oracle Access Manager must use the same LDAP directory. The LDAP directory must be defined in Oracle Access Manager as the default Identity Store and in Oracle Identity Federation as the User Data Store. The following steps verify the data store configuration.
-
Locate the Oracle Identity Federation instance in Fusion Middleware Control.
-
Navigate to Administration, then Data Stores.
-
Ensure that the User Data Store points to the same directory as the default Access Manager Identity Store
4.3.2 Configuring the Oracle Identity Federation Authentication Engine
The following procedure configures the Oracle Identity Federation Authentication Engine to retrieve information provided by the WebGate 11g agent.
-
Locate the instance of Oracle Identity Federation in Fusion Middleware Control.
-
Navigate to Administration and then Authentication Engines.
-
Enable the Oracle Access Manager 11g authentication engine.
-
Select the Agent Type.
-
If mod_osso is used, select Mod OSSO as the Agent Type.
-
If WebGate 11g is used, select WebGate 11g as the Agent Type.
-
-
Select the User Unique ID Header.
-
If mod_osso is used, select Proxy Remote User as the User Unique ID Header.
-
If WebGate 11g is used, enter OAM_REMOTE_USER as the User Unique ID Header.
-
-
In the Default Authentication Engine drop-down list, select Oracle Access Manager 11g.
-
Logout configuration: leave logout disabled as it will be configured in the Oracle Access Manager 11g SP Engine
-
Click Apply.
4.3.3 Configuring the Oracle Identity Federation SP Integration Module
This section lists the steps that need to be performed to configure Oracle Identity Federation in SP mode for Access Manager, so that Oracle Identity Federation can send assertion tokens and direct session management to Access Manager.
-
Locate the instance of Oracle Identity Federation in Fusion Middleware Control.
-
Navigate to Administration and then Service Provider Integration Modules.
-
Select the Oracle Access Manager 11g tab.
-
Configure as follows then click Apply.
-
Check the Enable SP Module box.
-
Select Oracle Access Manager 11g from the Default SP Integration Module drop-down menu.
-
Check the Logout Enabled box.
-
Configure the Login URL as
http://oam_host:oam_port/oam/server/dap/cred_submit
where oam_host and oam_port are the host and port number of the Oracle Access Manager server respectively.
-
Configure the Logout URL as
http://oam_host:oam_port/oam/server/logout
where oam_host and oam_port are the host and port number of the Oracle Access Manager server respectively.
-
Set the value of the Username Attribute to
uidto match the Oracle Access Manager username attribute.
-
-
Click Regenerate.
This action generates a keystore file that contains the keys used to encrypt and decrypt tokens that are exchanged between the Oracle Access Manager and Oracle Identity Federation servers. Be sure to save the keystore file using the Save As dialog.
-
Copy the keystore file to a location within the installation directory of Access Manager.
Make a note of the location to refer to later.
4.4 Configuring Oracle Access Manager for Oracle Identity Federation
This section describes how to configure Oracle Access Manager to integrate with Oracle Identity Federation.
-
In SP mode, where Oracle Access Manager will delegate authentication to Oracle Identity Federation for Federation SSO.
-
In Authentication mode, where Oracle Identity Federation will delegate authentication to Oracle Access Manager.
This section contains these topics:
4.4.1 Configuring the OIFScheme
The following procedure configures Oracle Access Manager to redirect the user to Oracle Identity Federation for authentication when the OIFScheme is used to protect a resource using Federation SSO.
-
Log in to the Oracle Access Manager Administration Console.
-
Select the Policy Configuration tab.
-
Select and open the OIFScheme.
-
In the Challenge URL field, modify the value of OIFHost and port to reflect your deployment.
-
Confirm that the value of the Context Type drop-down is set to
external. -
Click Apply to save the changes.
4.4.2 Registering Oracle Identity Federation as a Trusted Access Manager Partner
Use the WebLogic Scripting Tool and the following procedure to update the OIFDAP partner block in the oam-config.xml configuration file.
Note:
Be sure you have copied the keystore file to a location within the installation directory of Access Manager. See Configuring the Oracle Identity Federation SP Integration Module.
-
Enter the shell environment by executing the WLST script.
$DOMAIN_HOME/common/bin/wlst.sh
-
Connect to the Oracle Access Manager administration server using the following syntax.
connect('weblogic','password','host:port') -
Execute the following command to update the partner block in the configuration file.
registerOIFDAPPartner(keystoreLocation=location_of_keystore_file, logoutURL=logoutURL)
where logoutURL defines the Oracle Identity Federation logout URL to invoke when the Oracle Access Manager server logs the user out. For example:
registerOIFDAPPartner(keystoreLocation="/home/pjones/keystore", logoutURL="http://abcdef0123.in.mycorp.com:1200/fed/ user/spslooam11g?doneURL= http://abc1234567.in.mycorp.com:6001/oam/pages/logout.jsp")
4.4.3 Updating the MatchLDAPAttribute
MatchLDAPAttribute is used to locate the user in Oracle Access Manager in a Federation SSO SP flow. Use the following procedure to set the value to uid by modifying the oam-config.xml file.
-
Open the
oam-config.xmlfile located in$DOMAIN_HOME/config/fmwconfig/. -
Locate the
MatchLDAPAttributestring (located under the DAPModules and 7DASE52D elements) and set the value touid.The modified section should look as follows:
<Setting Name="DAPModules" Type="htf:map"> <Setting Name="7DASE52D" Type="htf:map"> <Setting Name="name" Type="xsd:string">DAP</Setting> <Setting Name="MatchLDAPAttribute" Type="xsd:string">uid</Setting> <Setting Name="MAPPERCLASS" Type="xsd:string">oracle.security.am.engine.authn. internal.executor.DAPAttributeMapper</Setting> </Setting> </Setting>
-
Save the file and exit.
4.5 Protecting a Resource with OIFScheme
After the integration of Oracle Access Manager and Oracle Identity Federation in SP mode, a resource can now be protected using OIFScheme. OIFScheme triggers a Federation SSO operation when an unauthenticated user requests access to a resource protected by said scheme. To protect using the OIFScheme, in the applicable Application Domain (under the Policy Configuration tab), define an Authentication Policy using the OIFScheme and protect a resource using that Authentication Policy.
4.6 Testing The Configuration
The final task is to test the configured integration. The steps are different depending on whether you have used SP Mode or Authentication Mode. More information is in the following sections.
4.6.1 Testing With SP Mode
Follow this procedure to test for correct configuration when in SP mode.
-
Establish Federated Trust between Oracle Identity Federation and a remote Identity Provider.
-
Set that Identity Provider as the Default SSO Identity Provider.
-
Access the protected resource.
When set up correctly, you should be redirected to the Identity Provider for authentication.
-
Enter valid credentials on the login page.
The user should exist in both the Identity Provider security domain and the Oracle Identity Federation and Oracle Access Manager security domains.
-
Check that you are redirected to the protected page.
Additionally, verify that the following cookies have been created:
-
OAM_ID
-
ORA_OSFS_SESSION
-
OHS Cookie
-
4.6.2 Testing With Authentication Mode
Follow this procedure to test for correct configuration when in Authentication Mode.
-
Establish Federated Trust between Oracle Identity Federation and a remote Service Provider.
-
Initiate Federation SSO from the Service Provider.
-
Verify that you are redirected to the Oracle Access Manager login page at the Identity Provider.
-
Enter valid credentials and process the page.
-
Verify that you are redirected to the Service Provider domain.