6 Handling Authorization Calls and Decisions
Oracle Entitlements Server contains a set of different application programming interfaces (API) that allows the caller to request authorization for a particular subject and handle the returned decisions. This chapter contains the following sections.
6.1 Using the Authorization Request API
The Oracle Entitlements Server Authorization API are used by components for authorization checks during runtime. The following comprise the authorization API options in this release.
-
PEP API - The AzAPI defines a set of interfaces that enable a Java module to supply and consume all the necessary information for submitting an eXtensible Access Control Markup Language (XACML) resquest and receiving a XACML response. The PEP API is a package built on top of the AzAPI package to simplify the creation of Policy Enforcement Points (PEP). See Section 6.2, "Using the PEP API" for more information.
-
checkPermission()- This method uses JavaPermissionobjects to grant access to protected resources. See Section 6.4, "Making checkPermission() Calls" for more information.
6.2 Using the PEP API
The AzAPI is a Java API developed by the OpenAZ project and designed to communicate requests for authorization decisions and responses to same. The communications are based on the authorization decision request and response standards defined in the XACML specifications and require that an authorization engine create request and response messages using these definitions. The AzAPI interfaces enable a Policy Decision Point (PDP) to supply and consume all the XACML information required when submitting an authorization resquest and receiving an authorization response.
Note:
More information on the OpenAZ project can be found at http://openliberty.org/wiki/index.php/OpenAz_Main_Page.
The PEP API is a Java package built on top of the AzAPI. It contains utility classes for building a Policy Enforcement Point (PEP), and is designed to present a more simplified, scalable interface than the AzAPI, using native Java objects rather than XACML data objects. Figure 6-1 illustrates the relationship between the AzAPI, the PEP API and Oracle Entitlements Server.
Figure 6-1 Relationship Between Open AZ API and PEP API
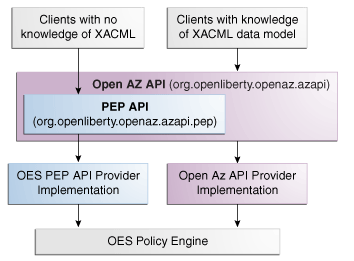
Description of "Figure 6-1 Relationship Between Open AZ API and PEP API"
Oracle Entitlements Server provides an implementation of the org.openliberty.openaz.azapi.pep package. The PEP API provider is packaged in oracle.security.jps.openaz.pep. For each PEP API request, the PEP API provider implementation is responsible for converting and mapping native Java objects to the underlying security platform. For each PepRequest, the PEP API provider invokes the Oracle Entitlements Server Authorization Engine and returns a PepResponse object. The provider also provides a default DecisionHandler implementation. The following sections have more information.
6.2.1 Using the PEP API
This section contains sample code that illustrates ways in which the PEP API can be used. Example 6-1 shows how to authenticate the user with the login service and use the authentiated subject in a PEP API authorization request. This code is specific to a Java Standard Edition (JSE) container.
Example 6-1 Using Authenticated Subject in PEP API Request
ServiceLocator locator = JpsServiceLocator.getServiceLocator();
LoginService loginService = locator.lookup(LoginService.class);
CallbackHandler cbh = new MyCallbackHandler("name", "password".toCharArray());
LoginContext ctx = loginService.getLoginContext(new Subject(), cbh);
ctx.login();
Subject s = ctx.getSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s, action, resourceString, env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet()) {
System.out.print("obligation: name = " + name + ", values = " +
obligations.get(name).getStringValues());
}
Example 6-2 illustrates how, after Java Enterprise Edition (JEE) authentication, you can get the WebLogic Server subject to use with the PEP API.
Example 6-2 Using WebLogic Server with PEP API Request
import weblogic.security.Security;
...
Subject s = Security.getCurrentSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s, action, resourceString, env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet()) {
System.out.print("obligation: name = " + name + ", values = "
+ obligations.get(name).getStringValues());
}
Example 6-3 illustrates how, after Java Enterprise Edition (JEE) authentication, you can get the Websphere Application Server subject to use with the PEP API.
Example 6-3 Using Websphere Application Server with PEP API Request
import com.ibm.websphere.security.auth.WSSubject;
...
Subject s = WSSubject.getCallerSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response = PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s, action, resourceString, env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet()) {
System.out.print("obligation: name = " + name + ", values = " + obligations.get(name).getStringValues());
}
Note:
It is recommended to call the newPepRequest() method with a Java Authentication and Authorization Service (JAAS) subject and not a string subject. A string subject will be converted to a JAAS subject.
6.2.2 Formatting PEP API Authorization Request Strings
Example 6-4 illustrates the newQueryPepRequest() method for creating an authorization request using subject and environment objects.
Example 6-4 newQueryPepRequest Method
public PepRequest newQueryPepRequest
(object subjectObj,
Object environmentObj
String scope
PepRequestQueryType queryType)
throws PepException
This method contains a string to define the scope of the request. Within the scope string is defined a resource string. The following sections contain information on how to format these strings.
6.2.2.1 Formatting the Scope String
The scope input string is a PDP policy-specific resource representation that encapsulates resource, actions and search scope information. It is represented as:
String scope = "resource = resourceString,actions = actionString1, actionString2, actionString3, searchscope = immediate/children";
The following is true regarding this representation.
-
resourceis required and the resource string should appear first within the scope string. See Section 6.2.2.2, "Formatting the Resource String." -
actionsis optional. If present, it contains a comma separated list of requested actions. -
searchscopeis optional and takes a value of children (the default value) or immediate.-
If the value is
children,resourceStringmay contain only the application identifier as documented in Section 6.2.2.2, "Formatting the Resource String." In this case, the PEP API provider will query the specified resource object and its children (if any). In the following example, Scope string defines a resource which contains a Resource string (with application identifier), no actions and no defined search scope; thus, the search scope is set tochildren, by default.String scope = "resource = PepQueryTest/resource_type_1/resource_1";
-
If the value is
immediate,resourceStringshould be fully qualified as documented in Section 6.2.2.2, "Formatting the Resource String." In this case, the PEP API provider will query the specified resource object. For example:String scope = "resource = PepQueryTest/resource_type_1/resource_1, actions = action1,action2, searchscope=immediate";
-
The following Scope string defines a hierarchical resource.
String scope= "resource = PepQueryTest/hierarchical_type//res1/res2/res3, searchscope= children";
6.2.2.2 Formatting the Resource String
The string should be in the format appId + / + resourceType + / + resourceName. The forward slash (/) is the delimiter. The appId and resourceType cannot be empty but the resourceName can be empty for a query request only.
When formatting the string, there is no need to escape the delimiter character if it is used in the resourceName. For example, if there is a hierarchical resource with the name /res1/res2/res3, the resource string passed to the PEP API will be appId/ResType//res1/res2/res3.
It is necessary to escape the delimiter character if it is used in the appId or resourceType though. In these cases, a string with more than two delimiters is considered invalid. The special characters \ and / must be escaped as in the following examples:
-
myapp/computer\/laptop/myboxsignifies a resource in the applicationmyappwith the resource typecomputer/laptopand the resource namemybox. -
myapp/computer\\laptop/myboxsignifies a resource in the applicationmyappwith the resource typecomputer\laptopand the resource namemybox. -
myapp/computer\laptop/myboxis invalid because the character after \ is neither/nor\.
Note:
For strings in Java, the character \ itself needs to be escaped. Thus the three strings previously documented, in Java, are:
-
myapp/computer\\/laptop/mybox -
myapp/computer\\\\laptop/mybox -
myapp/computer\\laptop/mybox
6.2.3 Processing Query Requests
The code in this section are examples of a query against a particular resource. Example 6-5 is a query request against a particular resource. Note that the search scope is defined as immediate.
Example 6-5 Requesting Authorization Against a Resource
... String scope = "resource = PepQueryTest/resource_type_1/resource_1, actions = action1, searchscope=immediate"; PepRequest req = PepRequestFactoryImpl.getPepRequestFactory(). newQueryPepRequest(subject, env, scope, PepRequestQueryType.RETURN_ONLY_ALLOWED_RESULTS); //this method is backed by AuthorizationService.queryActionsOnResource PepResponse resp = req.decide(); //List of RuntimeAction objects List actions = (List) resp.getAction(); RuntimeResource resource = (RuntimeResource) resp.getResource();
Example 6-6 is a query request against a particular resource and its children. Note that the search scope is defined as children.
Example 6-6 Requesting Authorization Against a Resource and Children
...
String scope = "resource=PepQueryTest/Hierarchical/\\/res1";
PepRequest req = PepRequestFactoryImpl.getPepRequestFactory
(subject, env, scope, PepRequestQueryType.VERBOSE);
//this method is backed by AuthorizationService.queryActionsOnChildResource
PepResponse resp = req.decide();
ArrayList arrayList;
List grantedActions;
List deniedActions;
int i = 0;
//there can be more than 1 result when searchscope="children"
while (resp.next()) {
RuntimeResource res = (RuntimeResource) resp.getResource();
//both granted actions and denied actions are returned for PepRequestQueryType.VERBOSE
//PepResponse.getAction() returns an ArrayList where ArrayList.get(0) returns list of granted actions;
//it returns an ArrayList where ArrayList.get(1) returns list of denied actions;
arrayList = (ArrayList) resp.getAction();
grantedActions = null;
deniedActions = null;
if (arrayList != null) {
grantedActions = (List) arrayList.get(0);
deniedActions = (List) arrayList.get(1);
}
String resourceName = res.getResourceName();
}
Example 6-7 is an example of code written for bulk authorization.
Example 6-7 Requesting Bulk Authorization
public void testBulkRequest() throws Exception {
Map<String, String> env = new HashMap<String, String>();
env.put("dynamic_attr", "dynamic_attr_value");
String resourceString =
MY_APPLICATION + "/" + MY_RESOURCE_TYPE + "/" + MY_RESOURCE;
String wrongAction = "wrong_action";
PepResponse resp = pepRequestFactory.newBulkPepRequest(
subject,
Arrays.asList(new Object[]{MY_ACTION, wrongAction}),
Arrays.asList(new Object[]{resourceString, resourceString}),
env).decide();
//
// first request
//
assertTrue(resp.next());
assertTrue("resp.allowed() is expected to be true!! ", resp.allowed());
assertSame(MY_ACTION, resp.getAction());
assertSame(RESOURCE_STRING, resp.getResource());
//
// second request
//
assertTrue(resp.next());
assertFalse("resp.allowed() is expected to be false!! ", resp.allowed());
assertSame(wrongAction, resp.getAction());
assertSame(RESOURCE_STRING, resp.getResource());
//
// call next() again..
//
assertFalse(resp.next());
}
6.2.4 Getting Obligations
An Obligation specifies optional information that is returned to the calling application with the access decision. Each obligation in the PEP API response has a map in type Map<String, String>. (There are no double quotes around the String value.) Example 6-8 is an authorization request that also requests any Obligations.
Example 6-8 Getting Obligation with PEP API Authorization Request
Subject s = ...; // a Jps subject (with app roles inside)
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s,action,resourceString,env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet())
{ System.out.print("obligation: name = " + name + ", values = " + obligations.get(name).getStringValues()); }
Example 6-9 is an example of an Obligation output. Again, there are no double quotes around the string value.
6.2.5 Configuring the PEP API
To use the PEP API, the identity store, the policy store, the Policy Distribution Service, and the user assertion login module must be defined in jps-config.xml. Example 6-10 is not a complete file but copied below for demonstration purposes.
Example 6-10 Sample jps-config.xml File
...
<serviceInstance name="idstore.ldap" provider="idstore.ldap.provider">
<property name="idstore.config.provider"
value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider"/>
<property name="CONNECTION_POOL_CLASS"
value="oracle.security.idm.providers.stdldap.JNDIPool"/>
</serviceInstance>
<serviceInstance name="pdp.service" provider="pdp.service.provider">
<property name="sm_configuration_name" value="permissionSm"/>
<property name="work_folder" value="/tmp"/>
<property name="authorization_cache_enabled" value="true"/>
<property name="role_cache_enabled" value="true"/>
<property name="session_eviction_capacity" value="500"/>
<property name="session_eviction_percentage" value="10"/>
<property name="session_expiration_sec" value="60"/>
<property name="oracle.security.jps.ldap.policystore.refresh.interval"
value="30000"/>
<property name="oracle.security.jps.policystore.refresh.purge.timeout"
value="600000"/> <\!-\- 10 minutes -->
<property name="loading_attribute_backward_compatible" value="false"/>
<\!-\- Properties for controlled mode PD -->
<property name="oracle.security.jps.runtime.policy.distribution.mode"
value="non-controlled"/>
<property name="oracle.security.jps.runtime.configuration.id"
value="${atzsrg.pdp.configuration_id}"/>
<property name="oracle.security.jps.runtime.instance.name"
value="${atzsrg.pdp.instance_name}"/>
<property name="oracle.security.jps.runtime.flushDistribution"
value="${atzsrg.pdp.always_flush}"/>
</serviceInstance>
<serviceInstance name="policystore.oid" provider="policy.oid">
<property name="max.search.filter.length" value="4096"/>
<property name="security.principal" value="cn=orcladmin"/>
<property name="security.credential" value="welcome1"/>
<property name="ldap.url" value="ldap://scl58116.us.oracle.com:3060"/>
<property name="oracle.security.jps.ldap.root.name" value="cn=jpsTestNode"/>
<property name="oracle.security.jps.farm.name" value="cn=duyang_wls.atzsrg"/>
<property name="oracle.security.jps.policystore.resourcetypeenforcementmode"
value="Lenient"/>
</serviceInstance>
<serviceInstance name="user.assertion.loginmodule" provider="jaas.login.provider">
<description>User Assertion Login Module</description>
<property name="loginModuleClassName"
value="oracle.security.jps.internal.jaas.module.assertion.
JpsUserAssertionLoginModule"/>
<property name="jaas.login.controlFlag" value="REQUIRED"/>
</serviceInstance>
...
<jpsContexts default="default">
<jpsContext name="default">
<serviceInstanceRef ref="idstore.ldap"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
<serviceInstanceRef ref="policystore.oid"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="audit"/>
<serviceInstanceRef ref="pip.service.ootb.ldap"/>
...
</jpsContext>
</jpsContexts>
6.3 Making XACML Calls
Oracle Entitlements Server allows external applications to ask authorization questions using the XACML 2.0 protocol. The Web Services Security Module contains a XACML gateway that allows it to receive XACML authorization requests and return XACML authorization responses. This capability is supported only when using the Multi-Protocol Security Module.
The Web Services Security Module XACML gateway acts as a remote PDP. It uses the standard XACML 2.0 context to convey authorization requests and responses between the PEP and the PDP. Here is the processing sequence for a XACML authorization request.
-
The PEP (application) establishes a session, authenticates a user and gets a valid token for the principal. Example 6-11 illustrates how to establish the section and send a XACML 2.0 authorization request.
Example 6-11 Sample Code to Establish Session For XACML Gateway
setupSession(); request = createRequest(); try { resp = xacmlSvc.authorize(request); } catch (AxisFault af) { if (isTokenExpired(af)) { resetupSession(); try { resp = xacmlSvc.authorize(request); } catch (RemoteException e) { throw new XACMLException("Error calling the XACML service.", e); } } else { throw new XACMLException(“Error calling the XACML service.”, af); } } catch (RemoteException e) { throw new XACMLException("Error calling the XACML service.", e); } private boolean isTokenExpired(AxisFault af) { String faultReason = af.getFaultReason(); if((faultReason != null) && (faultReason.indexOf ("IdentityAssertionException") != -1)) { return true; } return false; } private void setupSession() throws XACMLException { if (identity == null) { establishSession(); } } private void resetupSession() throws XACMLException { establishSession(); } private void establishSession() throws XACMLException { try { EstablishSessionType sess = new EstablishSessionType(); sess.setPrincipalsInfo(convertSubjectToPrincipalsInfo(subject)); sess.setRequestedCredentialType(OES_CREDENTIAL_TYPE); AuthenticationResultType result = atzSvc.establishSession(sess); identity = result.getIdentityAssertion(); } catch (Exception e) { throw new XACMLException("Unable to authenticate user.", e); } if (identity == null) { throw new XACMLException("Null identity received. Unable to establish session for " + subject); } System.out.println("Authentication Succeeded, Identity: "); MessageElement ele = identity.get_any()[0]; System.out.println(ele.getFirstChild()); } -
The PEP sends a XACML request containing the token to the PDP (Security Module). Example 6-12 is sample code that details how to create a XACML authorization request.
Example 6-12 Creating a XACML Request
private RequestType createRequest() throws XACMLException { // create resource String res = "Library/LibraryResourceType/Book"; AttributeType attr = createAttribute(res, RESOURCE_ID, XML_STRING_TYPE); ResourceType resource = new ResourceType(null, new AttributeType[]{attr}); // create action String actionStr = "borrow"; attr = createAttribute(actionStr, ACTION_ID, XML_STRING_TYPE); ActionType action = new ActionType(new AttributeType[]{attr}); // create environment String isRegistered = input.getString("Is the user registered in the library (yes|no): "); String numberOfBorrowedBooks = input.getString("How many books has the user borrowed already:: "); EnvironmentType env; List attrs = new ArrayList(); attrs.add(createAttribute(isRegistered, XACML_NAMESPACE + "RegisteredAttribute", XML_STRING_TYPE)); attrs.add(createAttribute(numberOfBorrowedBooks, XACML_NAMESPACE + "NumberOfBorrowedBooksAttribute", XML_STRING_TYPE)); // obligations attrs.add(createAttribute(LIST_VAL1, XACML_NAMESPACE + ATTRIBUTE_NAME, XML_STRING_TYPE)); attrs.add(createAttribute(LIST_VAL2, XACML_NAMESPACE + ATTRIBUTE_NAME, XML_STRING_TYPE)); env = new EnvironmentType((AttributeType[])attrs.toArray(new AttributeType[attrs.size()])); // subject attr = createAttribute(identity.get_any(), SUBJECT_ID, XACML_NAMESPACE + OES_CREDENTIAL_TYPE); SubjectType subject = new SubjectType(new AttributeType[]{attr}, null); // now construct the request with subject, resource, action and environment. return new RequestType(new SubjectType[]{subject}, new ResourceType[]{resource}, action, env); }Example 6-13 is a sample XACML 2.0 authorization request. The
SSM-SOAPWS.wsdlfile provides the operation interface definitions.Example 6-13 XACML 2.0 Authorization Request
<Request xmlns="urn:oasis:names:tc:xacml:2.0:context:schema:os"> <Subject xsi:type="ns1:SubjectType" xmlns:ns1="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <Attribute AttributeId="urn:oasis:names:tc:xacml:1.0:subject:subject-id" DataType="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#OESIdentityAssertion" xsi:type="ns1:AttributeType"> <AttributeValue xsi:type="ns1:AttributeValueType"> <OESIdentityAssertion xmlns="http://security.bea.com/ssmws/ssm-soap-types-1.0.xsd"> SU=John;TS=1288702235781;CT=1</OESIdentityAssertion> </AttributeValue> </Attribute> </Subject> <ns2:Resource xsi:type="ns2:ResourceType" xmlns:ns2="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns2:Attribute AttributeId="urn:oasis:names:tc:xacml:2.0:resource:resource-id" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns2:AttributeType"> <ns2:AttributeValue xsi:type="ns2:AttributeValueType"> Library/LibraryResourceType/Book</ns2:AttributeValue> </ns2:Attribute> </ns2:Resource> <ns3:Action xsi:type="ns3:ActionType" xmlns:ns3="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns3:Attribute AttributeId="urn:oasis:names:tc:xacml:1.0:action:action-id" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns3:AttributeType"> <ns3:AttributeValue xsi:type="ns3:AttributeValueType">borrow</ns3:AttributeValue> </ns3:Attribute> </ns3:Action> <ns4:Environment xsi:type="ns4:EnvironmentType" xmlns:ns4="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns4:Attribute AttributeId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#RegisteredAttribute" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns4:AttributeType"> <ns4:AttributeValue xsi:type="ns4:AttributeValueType">yes</ns4:AttributeValue> </ns4:Attribute> <ns4:Attribute AttributeId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl #NumberOfBorrowedBooksAttribute" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns4:AttributeType"> <ns4:AttributeValue xsi:type="ns4:AttributeValueType">2</ns4:AttributeValue> </ns4:Attribute> </ns4:Environment> </Request> -
The XACML gateway asserts the token and converts it to the applicable identity.
-
Oracle Entitlements Server reaches an authorization decision regarding the principal using any applicable policies and returns a XACML response to the PEP. Example 6-14 is a sample XACML 2.0 authorization response. The
SSM-SOAPWS.wsdlfile provides the operation interface definitions.Example 6-14 XACML 2.0 Authorization Response
<Response xmlns="urn:oasis:names:tc:xacml:2.0:context:schema:os"> <Result ResourceId="Library/LibraryResourceType/Book"> <Decision>Permit</Decision> <Status> <StatusCode Value="urn:oasis:names:tc:xacml:1.0:status:ok"/> </Status> <ns1:Obligations xmlns:ns1="urn:oasis:names:tc:xacml:2.0:policy:schema:os"> <ns1:Obligation ObligationId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#Roles" FulfillOn="Permit"> <ns1:AttributeAssignment DataType="http://www.w3.org/2001/XMLSchema#string" AttributeId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#role"> AuthenticatedUser</ns1:AttributeAssignment> </ns1:Obligation> <ns1:Obligation ObligationId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl# ResponseAttributes" FulfillOn="Permit"> <ns1:AttributeAssignment DataType="http://www.w3.org/2001/XMLSchema#dateTime" AttributeId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#decisionTime"> 2010-11-02T12:50:43.685Z</ns1:AttributeAssignment> </ns1:Obligation> </ns1:Obligations> </Result> </Response>
6.4 Making checkPermission() Calls
A Java Permission object represents access to a resource. A Permission object is constructed and assigned (access granted) based on the configured policy in effect. Java checkPermission() authorization is based on these permissions.
Oracle Entitlements Server supports the use of the checkPermission() method in the following standard classes:
-
java.lang.SecurityManager -
java.security.AccessControllerNote:
The static
AccessController.checkPermissionmethod uses the default access control context (the context inherited when the thread was created). To check permissions on some other context, call the instancecheckPermission()method on a particularAccessControlContextinstance.
Additionally, Oracle Entitlements Server supports the use of the checkPermission() method in the oracle.security.jps.util.JpsAuth class.
Tip:
Oracle recommends the use of the checkPermission() method in the oracle.security.jps.util.JpsAuth class as it provides improved debugging support, better performance, and audit support.
When invoking the checkPermission() method (in a JavaSE application), make sure:
-
The
java.security.policysystem property has been set to the location of the Oracle Platform Security Services/Oracle WebLogic Server policy file. -
Your application first calls the
setPolicy()method to explicitly set the policy provider. This is illustrated by the following sample code.java.security.Policy.setPolicy(new oracle.security.jps.internal.policystore.JavaPolicyProvider());
oracle.security.jps.util.JpsAuth.checkPermission() works exactly as the standard methods by accepting a Permission object. If the requested access is allowed, checkPermission() returns quietly; if denied, an AccessControlException is thrown. The following sample illustrates how you might use checkPermission().
java.security.Policy.setPolicy(new
oracle.security.jps.internal.policystore.JavaProvider()); // Java SE env only
PolicyContext.setContextID(TARGET_APP); // Java SE env only
// authorization runtime
Subject s = new Subject(); s.getPrincipals().add(new WLSUserImpl("wcai")); s.setReadOnly();
JpsSubject.invokeAs(s, new PrivilegedAction<Object>() {
public Object run() {
FilePermission perm2 = new FilePermission(“HARRY_PORTER”, "read");
psAuth.checkPermission(perm2);
return null;
}