Trusted Extensions Protections
Trusted Extensions software enhances the protection of the Oracle Solaris OS. Trusted Extensions restricts users and roles to an approved label range. This label range limits the information that users and roles can access.
Trusted Extensions displays the Trusted Path symbol, an unmistakable, tamper-proof emblem that appears at the left of the trusted stripe. In Trusted GNOME, the stripe is at the top of the screen. The Trusted Path symbol indicates to users when they are using security-related parts of the system. If this symbol does not appear when the user is running a trusted application, that version of the application should be checked immediately for authenticity. If the trusted stripe does not appear, the desktop is not trustworthy. For a sample desktop display, see Figure 6–1.
Figure 6-1 Trusted Extensions Multilevel Desktop
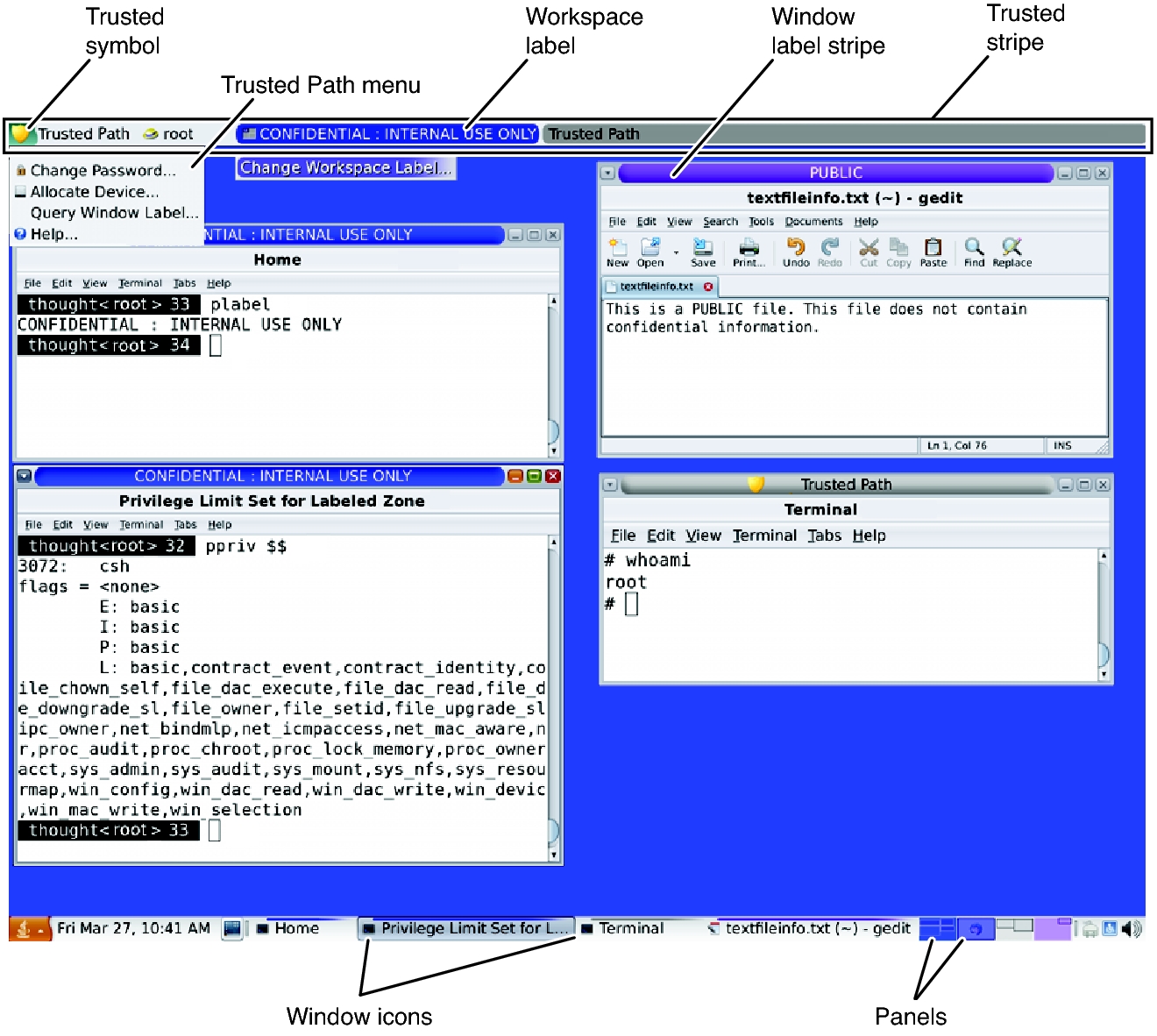
Most security-related software, that is, the Trusted Computing Base (TCB), runs in the global zone. Regular users cannot enter the global zone or view its resources. Users are subject to TCB software, such as when changing passwords. The Trusted Path symbol is displayed whenever the user interacts with the TCB.