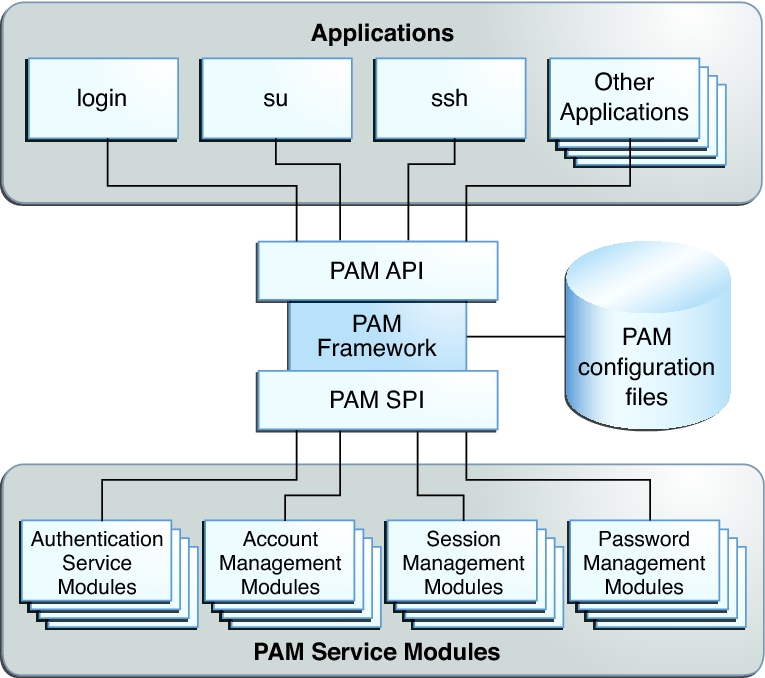
Introduction to the PAM Framework
-
Applications that use PAM
-
PAM framework
-
PAM service modules
-
PAM configuration, including choice of modules and user assignment
The PAM framework consists of four parts:
The framework provides a uniform way for authentication-related activities to take place. This approach enables application developers to use PAM services without having to know the semantics of the authentication policy. With PAM, administrators can tailor the authentication process to the needs of a particular system without having to change any applications. Rather, administrators adjust the PAM configuration.
The following figure illustrates the PAM architecture.
Figure 1-1 PAM Architecture
-
Applications communicate with the PAM framework through the PAM application programming interface (API).
For information about using the API, see the pam(3PAM) man page and Chapter 3, Writing PAM Applications and Services, in Developer’s Guide to Oracle Solaris 11 Security .
-
PAM service modules communicate with the PAM framework through the PAM service provider interface (SPI). For more information, see the pam_sm(3PAM) man page.
For a brief description of selected service modules, see PAM Service Modules and the pam.conf(4) and pam_user_policy(5) man pages.
The architecture works as follows:
Administrators can configure one or more series of modules to manage site requirements. This series of modules is called a PAM stack. The stack is evaluated in order. If an application requires more than one PAM stack, the application developer must create more than one service name. For example, the sshd daemon provides and requires several service names for PAM. For the list of PAM service names for the sshd daemon, search for the word PAM in the sshd(1M) man page. For details of the PAM stack, see PAM Stacking. PAM Stacking Example steps through a PAM authentication stack.