8 Working with Privileged Accounts
This chapter provides some background information about privileged accounts and describes how to work with those accounts using the Oracle Privileged Account Manager Console.
This chapter includes the following sections:
-
Section 8.2, "Adding Privileged Accounts into Oracle Privileged Account Manager"
-
Section 8.9, "Removing Privileged Accounts from Oracle Privileged Account Manager"
Note:
You can also manage Oracle Privileged Account Manager accounts from the command line or by using Oracle Privileged Account Manager's RESTful interface.
-
For information about using the Oracle Privileged Account Manager Command Line Tool (CLI), refer to Section A.5, "Working with Accounts" in Appendix A, "Working with the Command Line Tool."
-
For information about using the Oracle Privileged Account Manager RESTful interface, refer to Section B.6, "Account Resource" in Appendix B, "Working with Oracle Privileged Account Manager's RESTful Interface."
8.1 What is a Privileged Account?
An account on a target is considered privileged in a deployment when that account
-
Is associated with elevated privileges
-
Is used by multiple end-users on a task-by-task basis
-
Requires its usage to be controlled and audited
You cannot create accounts in, or delete accounts from, your environment by using Oracle Privileged Account Manager. Oracle Privileged Account Manager only manages existing accounts that were provisioned using other mechanisms.
When you "add" an account in Oracle Privileged Account Manager, you are creating a reference to that account. In effect, you are registering the account and asking Oracle Privileged Account Manager to manage it. When you "remove" the account from Oracle Privileged Account Manager, you are only removing the reference to that account.
Note:
Administrators determine which accounts are privileged within a particular deployment, and they must configure Oracle Privileged Account Manager to manage those accounts.
You must be an Oracle Privileged Account Manager administrator with the Security Administrator Admin Role to add and manage accounts.
Oracle Privileged Account Manager enables you to manage both system and application accounts.
This section contains the following topics:
8.1.1 Managing System Accounts
Oracle Privileged Account Manager's primary purpose is to manage privileged system accounts on a supported target system. Oracle Privileged Account Manager does not mandate what constitutes a privileged system account — it can manage any account on a target system. Administrators are responsible for identifying which accounts are privileged. A privileged account is typically a system account that allows a user to perform administration tasks.
Privileged accounts are suitable for management through Oracle Privileged Account Manager if they are used and shared by multiple individuals in the organization and administrators are required to track the use of these accounts.
Administrators perform the following steps to register an account as a privileged account to be managed by Oracle Privileged Account Manager:
-
Add the target to Oracle Privileged Account Manager (if this has not already been done). Refer to Section 6.2, "Adding Targets to Oracle Privileged Account Manager" for instructions.
-
Add the identified privileged account to the target and assign a Password Policy. Refer to Section 8.2, "Adding Privileged Accounts into Oracle Privileged Account Manager" and Section 9.2.5, "Assigning Password Policies" for instructions.
-
Grant access to end users directly or by using LDAP roles/groups and assign a Usage Policy. Refer to Section 10.2, "Granting Accounts to Users" and Section 9.2.5, "Assigning Password Policies" for instructions.
8.1.2 Managing Application Accounts
Applications use application accounts to connect to target systems at run time. Traditionally, administrators set up these accounts once during installation and then they are forgotten. Consequently, application accounts can potentially cause hidden vulnerabilities in your deployment. For example, passwords might become less secure over time because they were created using outdated policies or commonly used deployment passwords might be compromised.
Oracle Privileged Account Manager enables you to better manage application accounts. In particular, for applications that store their application accounts in the Credential Store. These applications consume the account credentials at run time from the Credential Store through the Credential Store Framework.
For example, because an application account is essentially a special version of a system account, you can register an application account in Oracle Privileged Account Manager as described in Section 8.1.1, "Managing System Accounts." You can then add the corresponding CSF mappings for every application that depends on that account, which is how CSF uniquely identifies a credential stored within CSF, and how an application finds its credential in CSF. For more information about CSF mapping, refer to "Guidelines for the Map Name" in the Oracle Fusion Middleware Application Security Guide.
If you register an account's CSF mappings with Oracle Privileged Account Manager, then every time the account's password changes, Oracle Privileged Account Manager can update the CSF entries that correspond to the registered mappings to reflect the new password and the applications continue to work without service interruption.
Note:
Oracle Privileged Account Manager updates, or synchronizes, CSF only when a password change occurs. Refer to Section 17.3, "Integrating with the Credential Store Framework" for information about integrating Oracle Privileged Account Manager with CSF.
You can also use the plug-in framework to synchronize passwords to non-CSF application wallets. You can write a plug-in on the passwordcycle and resetaccountpassword operations for the Server resource to capture all password update operations, and then add custom logic to synchronize the resource to your application wallet. Refer to Section 11.2.7, "Supported Operations and Timings" for more information.
Additionally, you can apply a Password Policy to these applications that periodically cycles the account password. Cycling the password ensures that the application accounts are always compliant with the latest corporate policies and they remain secure. Oracle Privileged Account Manager performs this task with no service interruption.
Finally, its useful to note that Oracle Privileged Account Manager can support an account as both a system account (shared and used by multiple end-users) and as an application account (only used by an application at run time) at the same time. In this configuration, a human end-user who's been granted access can "check out" the application account to perform manual administrative operations as that application without disrupting application functionality.
8.1.3 Understanding Sharing Accounts
Oracle Privileged Account Manager enables you to specify whether an account is shared or not shared.
-
Shared accounts enable multiple users to check out the account at the same time.
-
Unshared accounts (Default) enable only one user to check out an account at a time.
Because unshared accounts are more secure, Oracle recommends that you designate an account as shared only if there are compelling business reasons to do so. If sharing is necessary, be sure to read Section 2.4.2, "Securing Shared Accounts."
8.2 Adding Privileged Accounts into Oracle Privileged Account Manager
Note:
Accounts are always added to a target, so you must add a target object before you can add an account. Refer to Section 6.2, "Adding Targets to Oracle Privileged Account Manager" for more information.
Never use the same account as the service account and as a privileged account to be managed by Oracle Privileged Account Manager. Refer to Chapter 7, "Working with Service Accounts" for information about service accounts.
You can add a new privileged account from either of the following pages:
To add an account by using the Accounts page,
-
Select Accounts from the Administration accordion.
-
Click the Add icon located above the Search results table.
To add an account by using the Targets page,
-
Select Targets in the Administration accordion.
-
Use the Search Targets portlet to populate the Search Results table with a list of all available targets.
-
Locate the target where you want to add the account and open it by clicking the Target Name link.
-
When the Target: TargetName page displays, select the Privileged Accounts tab.
-
Click Add in the table toolbar.
In both cases, when you click Add, the Account: Untitled page displays with the following subtabs:
Note:
Only the General tab is active at this point.
-
General: Use to specify information needed to add the account.
-
Grants: Use to associate users and groups (grantees) with the account.
-
Credential Store Framework: Use to add or remove Credential Store Framework (CSF) mappings for the account.
-
Checkout History: Use to search for, and view information about, any users who check out this account. (Refer to "From the Checkout History Tab" for more information.)
Use these subtabs and the instructions provided in the following sections to finish adding the account:
8.2.1 Adding the Account
To add an account you must complete the Step 1: Set Target and Step 2: Add Account sections on the General tab as follows:
-
Provide a Target Name and Target Type.
-
If a Target Name and a Target Type are already displayed, proceed to Step 1 in the Set the Account section.
-
If the either parameter is <undefined>, click the search icon.
-
-
When the Set Target dialog displays, enter a value in the Target Name field and click the Search button to locate the target where you want to add the account.
For example, if you know the target name begins with "r," you can type an
rinto the Target Name field and click the Search button. -
When the search results display in the Search Results table, select (check) the Row box next to a target name and then click Set.
The selected Target Name and its Target Type are displayed on the General tab.
-
When the Set Account dialog displays, enter one or more letters in the Account Name field and click the Search button to locate the account you want to add.
Note:
Wildcard searches (for example, using percent (
%) or underscore (_) symbols) are not supported in the Set Account dialog because you perform search account operations against real targets.For example, if you know the account name begins with "s," you can type an
sinto the Account Name field and click the Search button.Note:
When you add privileged accounts to a lockbox target, a Password field is also displayed in the Console.
Oracle Privileged Account Manager does not manage accounts on lockbox targets; therefore it cannot reset the passwords on those accounts. You must provide the password to be used when users check out those privileged accounts.
For more information about lockbox targets, refer to Section 6.1, "What Are Targets?"
-
When the search results display in the Search Results table, select (check) the Row box next to an account name and then click Set.
Note:
You must not add the target's service account as a privileged account to be managed by Oracle Privileged Account Manager.
The selected account is displayed as the Account Name on the General tab.
-
Enable the Shared Account box to allow multiple users to check out this account at the same time.
Note:
Refer to Section 8.1.3, "Understanding Sharing Accounts" and Section 8.5, "Checking Out Privileged Accounts" for more information.
-
Specify a Password Policy.
Note:
Oracle Privileged Account Manager automatically assigns the Default Password Policy to new accounts. However, Oracle Privileged Account Manager administrators with the Security Administrator or the User Manager Admin Role can create new policies.
You can leave the default policy set or choose a different policy from the Password Policy drop-down menu.
For more information about policies, refer to Chapter 9, "Working with Policies."
-
Click Test to confirm that the account can be managed by Oracle Privileged Account Manager with these settings.
If the account configuration settings are valid, a "
Test Succeeded" message displays. -
Click Save.
Note:
The Grants, Credential Store Framework, and Checkout History tabs do not become active until you save the new account information.
A new Current Checkouts section is displayed at the bottom of the General tab page. The table in this section enables you to view the following:
-
Which users currently have the account checked out
-
Type of checkout (password or session)
-
Checkout expiration date
-
Recordings (or transcripts) related to the account checkout
In addition, if you are an administrator with the User Manager Admin Role, you can use the Force check-in option to check in accounts. Refer to Forcing a Check-In.
-
You can now add grantees and CSF mappings to the account. Continue to Section 8.2.2, "Adding Grantees" and Section 8.2.3, "Adding CSF Mappings" for more information.
8.2.2 Adding Grantees
This section provides instructions for adding grantees to a privileged account.
Note:
-
You must be an Oracle Privileged Account Manager administrator with the User Manager Admin Role to add, edit, or delete grantees.
-
Adding a new account does not automatically grant you access to that account. You must complete the process for adding yourself as a grantee.
-
Before adding grantees to an account, be sure to read Section 2.4.4, "Avoiding Assignments through Multiple Paths."
To associate users and groups with a new account, select the Grants tab and then complete the following steps:
-
To associate users, click Add from the Users table toolbar.
-
In the Add Users dialog, enter one or more letters of a name into the User Name field and click the arrow icon to search for that user.
-
When the search results display, select (check) each user you want to associate with this account.
-
When you are finished adding users, click Add and then click Close.
Oracle Privileged Account Manager adds those user names to the Users table on the Grants tab and automatically assigns the Default Usage Policy.
To assign a different policy, select it from the Usage Policy menu.
-
-
To associate groups, click Add from the Groups table toolbar.
-
In the Add Group dialog, enter a name into the Group Name field and click the arrow icon to search for that group.
-
When the search results display, select (check) each group you want to associate with this account.
-
When you are finished adding groups, click Add and then click Close.
Oracle Privileged Account Manager adds those group names to the Groups table on the Grants tab and automatically assigns the Default Usage Policy.
To assign a different policy, select it from the Usage Policy menu.
-
Note:
Removing a user or group grant from an account does not automatically cancel all existing checkouts.
When grantees check out an account, they are guaranteed access to that account until one of the following events occur:
-
The grantee checks in the account
-
Oracle Privileged Account Manager automatically checks in the account because the checkout duration has exceeded the expiration period specified by the account's Usage Policy
-
An administrator forces an account check-in
However, after the account is checked in, the grantee cannot check out that account again unless an administrator re-adds them as a grantee.
8.2.3 Adding CSF Mappings
Oracle Privileged Account Manager enables you to securely store and synchronize account credentials with the Oracle Credential Store Framework (CSF). This capability is useful for managing the lifecycle of application passwords stored in CSF.
When you configure CSF synchronization for an account, Oracle Privileged Account Manager changes the account password based on the assigned Usage Policy.
Note:
Oracle Privileged Account Manager updates, or synchronizes, CSF only when a password change occurs.
For more information about CSF and how Oracle Privileged Account Manager manages CSF credentials, refer to Section 17.3, "Integrating with the Credential Store Framework."
To add CSF mappings to an account, complete the following steps:
-
Select the Account Name link in the Search Results table.
-
When the Account: AccountName page displays, select the Credential Store Framework tab.
-
Click Add.
A new row displays in the table with empty fields in each column.
-
Enter the following information into the empty fields:
-
Administration Server URL. Enter the server URL in this format, protocol://listen-address:listen-port
For example, if you are using the https protocol and the SSL port is 7002, you would enter
https://localhost:7002 -
Username and Password. Enter the login credentials of the Oracle WebLogic Server administrator.
-
Mapping. Enter the Map name you created in CSF.
-
Key. Enter the unique Key you created in CSF.
-
-
Click Add again to create another mapping. You can create as many CSF mappings as needed.
-
When you are finished adding information, click Test to validate the mapping.
A dialog displays with either a success message or an error message.
8.3 Searching for Privileged Accounts
You can search for accounts by using one or more of the following parameters:
-
Account Name
-
Target Type (All, ldap, unix, database, or lockbox)
-
Target Name
-
Domain
-
Description
To search for an account,
-
Select Accounts in the Administration accordion.
-
When the Accounts tab displays, use the Search portlet parameters to configure your search.
-
For example, to search for a list of all accounts on a particular target, enter one or more letters of the target name into the Target Name field.
-
To search for all available accounts, do not specify any search parameters.
-
-
Click Search.
Review your search results in the Search Results table.
Note:
You can use the View menu, located above the Search Results table, to manage how the search results are displayed in the table. Refer to the table in Section 4.3.6, "Working with a Search Results Table" for more information.
-
To perform another search, click Reset.
8.4 Opening Privileged Accounts
Opening an account enables you to view or edit the configuration parameters for that account.
You can open privileged accounts from any Search Results table containing an Account Name link. For example,
-
Select Accounts in the Administration accordion and click Search.
-
When the results display in the Search Results table, locate the account you want to open and perform one of the following actions:
-
Click the Account Name (an active link) in the Search Results table.
-
Select the account Row and then click Open.
-
The Account: AccountName page opens. From this page, depending on your Admin Role, you can view and configure account settings related to the associated target, grants, Credential Store Framework, and checkouts.
8.5 Checking Out Privileged Accounts
Oracle Privileged Account Manager enables grantees to check out an account in two ways:
-
Password Checkouts: Enables grantees to access and check out granted account by using encrypted passwords.
-
Session Checkouts (on UNIX systems only): Enables grantees to access and check out granted accounts without ever knowing the actual account credentials.
Note:
You can also use the Oracle Privileged Account Manager command line tool or the RESTful interface to check out accounts.
-
To use the command line tool, refer to Section A.5.4, "
checkoutCommand." -
To use the RESTful interface, refer to Section B.6.10, "Check Out an Account."
8.5.1 Checking Out Passwords
Any administrator or end user can check out a privileged account password if they have been granted access to that account. (Refer to Chapter 10, "Working with Grantees" for more information.)
Note:
You must be an administrator with the Security Administration Admin Role to modify or remove an account.
Privileged accounts are not shared by default, which means when one user checks out the account, it becomes unavailable to other users and prevents conflicting actions. However, administrators can configure shared accounts, which enables multiple users to check out the account at the same time. (Refer to Section 8.1.3, "Understanding Sharing Accounts" for more information.)
The steps for checking out a password are as follows:
-
Select My Accounts in the Home accordion.
-
On the My Accounts page, locate the account you want to check out in the Search Results table and select that row (Figure 8-1).
-
Click Password Check Out.
-
The Check-Out Account dialog displays with the Account Name, Target Name, and a blank Justifications field. Enter a comment in this field if you choose to, and then click Checkout.
If the checkout is successful, a Check-Out Account - Success dialog displays. This dialog contains an encrypted Password. You can view this Password in clear text by clicking the Show Password box.
If the checkout fails, the Check-Out Account dialog displays with a message stating you cannot check out the account, which may indicate someone else has already checked out that account.
Note:
To see if an account is already checked out, click the account name. When the Account: AccountName page opens, you can review the Current Checkouts table to see who checked out the account, what type of checkout it was (password or session), when the account was checked out, the checkout expiration date, and view a recording (if available).
-
Click Close to close the dialog and return to the Search Results table.
-
To verify that you checked out the account successfully:
-
Select My Checkouts from the Home accordion. When the My Checkouts page displays, locate the account name in the table.
-
If you have the Security Administrator Admin Role or the User Manager Admin Role, you can select Accounts from the Administration accordion and click Search. When the Search Results display, select the account name in the table to open the Account: AccountName page. The account should be listed in the Current Checkouts table.
-
8.5.2 Checking Out Privileged Account Sessions
Privileged sessions provide an extra level of security for privileged accounts on UNIX targets. Through privileged sessions, a grantee can access the granted account without ever knowing the actual account credentials.
Note:
Session checkout is not available for other target types.
Any administrator or end user can check out a privileged account session if they have been granted access to that account and if the Usage Policy associated with the account allows session checkouts. (Refer to Chapter 10, "Working with Grantees" and Section 9.3.3, "Modifying the Default Usage Policy" for more information.)
To check out a session,
-
Select My Accounts in the Home accordion and then click Search.
The My Accounts page is refreshed and all of your accounts are displayed in the Search Results table.
Note:
If you already know to how to establish the session using an SSH client, and you know the Oracle Privileged Account Manager server host, port, UNIX target, and UNIX account name, proceed to step 3.
-
Select the account row, and then click Session Check Out to view the connection information you need to establish the session using an SSH client.
For example:
Account Name: opamuser1 Target Name: sample-unix SSH Port: 1222 Instruction: ssh -p <port> <opamuser>:<targetname>: <accountname>@<sessionmgrhost> Use opam password on password prompt.
Where:
-
port is the port where Oracle Privileged Session Manager is running.
-
opamuser is the Oracle Privileged Account Manager end user.
-
targetname is the name of the target to which you are connecting.
-
accountname is the account you will be using on that target.
-
sessionmgrhost is the host on which you are running Session Manager.
Note:
The preceding example uses default Oracle Privileged Account Manager connection settings and instructions. Oracle Privileged Account Manager administrators can configure this information to whatever is appropriate for their own environments.
Refer to Section 5.3, "Managing the Oracle Privileged Session Manager Server" for information about configuring these settings.
-
-
Use your favorite SSH client to connect to a target or an account through the Oracle Privileged Session Manager server.
For example, using the SSH client on a standard Linux machine, you would perform the following steps:
-
Open a command window.
-
At the prompt, enter the connection information as noted in the Session Checkout dialog.
For example:
prompt> ssh –p 1222 opamuser1:target_system:user1@sessionmgrhost
A message displays stating that you are authenticated with partial success.
-
-
Enter the appropriate Oracle Privileged Account Manager password when you see the prompt to complete the connection to the Oracle Privileged Session Manager server.
-
To confirm the connection, type
idat the prompt, and the account'suid,gid, andgroupinformation will be returned. -
Return to the My Accounts page in the Console
-
To verify that you checked out the session successfully:
-
Select My Checkouts from the Home accordion. When the My Checkouts page displays, locate the account name in the table and review the Checkout Type column.
-
If you have the Security Administrator Admin Role or the User Manager Admin Role, you can select Accounts from the Administration accordion and click Search. When the Search Results display, select the account name in the table to open the Account: AccountName page. The session should be listed in the Current Checkouts table.
-
Note:
You do not have to perform any special steps to check in a checked out session. If you use the procedure described in Section 8.6, "Checking In Privileged Accounts," then the account is checked back in regardless of the checkout type (password or session).
8.6 Checking In Privileged Accounts
Any administrator or end user can check in their checked-out accounts by using the steps described in Regular Check-In.
Administrators with the User Manager Admin Role can force an account check-in (check in privileged accounts that have been checked out by other users) when necessary. Use the steps described in Forcing a Check-In.
Note:
In either case, you use the same steps to check in an account password or an account session.
To check in a checked out privileged account:
-
Select My Checkouts on the Home accordion.
The My Checkouts page displays with all of your checked-out accounts (passwords and sessions) listed in the Search Results table.
-
Select the account row or rows you want to check in.
-
When the Check-in icon located above the table becomes active, click the icon.
-
When the Check-in Accounts dialog displays, click the Check In button.
If the check-in is successful, Oracle Privileged Account Manager removes the account name(s) from the My Checkouts table and the account becomes available for check out again.
-
Select Accounts in the Administration accordion, and then search for the account as described in Section 8.3, "Searching for Privileged Accounts."
-
Select (check) the account you want to check in.
-
When the Force Check In option located above the table becomes active, click the icon.
The Confirm Forced Check In dialog displays, asking you to confirm that you want to check in the account. Be aware that forcing the check in will log out all users that currently have the account checked out.
-
To proceed, click the Check In button.
If the check-in is successful, the account becomes Available for check out again.
Note:
You can also use the Oracle Privileged Account Manager command line tool or the RESTful interface to check-in accounts.
-
To use the command line tool, refer to Section A.5.3, "
checkinCommand." -
To use the RESTful interface, refer to Section B.6.15, "Check In an Account."
8.7 Viewing a Session Recording
If necessary, administrators can view a recording, in transcript format, of the actions taken by the user during an account checkout (password or session).
Note:
The Session Monitoring Update Interval in seconds setting on the Session Manager Configuration Page controls how often on-going session transcripts are updated. Refer to step 2 in Section 5.3.3, "Managing the Oracle Privileged Session Manager Properties" for more information.
The following table describes the different transcript types, where you can access these recordings, and which Admin Roles are required to view the transcripts:
| Recording Type | Viewing Location | Admin Role |
|---|---|---|
|
On-going session transcripts |
The account's Current Checkouts table |
Security Admin or User Manager |
|
Expired session transcripts |
The account's Checkout History tab |
Security Admin or User Manager |
|
Expired session transcripts |
Checkout History Report page |
Security Auditor |
The next three sections provide instructions for accessing these recordings.
From a Current Checkouts Table
-
Open the account as described in Section 8.4, "Opening Privileged Accounts."
-
When the Account: AccountName page displays, locate the correct user in the Current Checkouts table, and click the Recording icon (
 ) in that row.
) in that row.A new tab opens in your browser and the recording displays in a transcript format. For example,
-
Open the account as described in Section 8.4, "Opening Privileged Accounts."
-
When the Account: AccountName page displays, select the Checkout History tab.
A new tab opens in your browser and the recording displays in a transcript format.
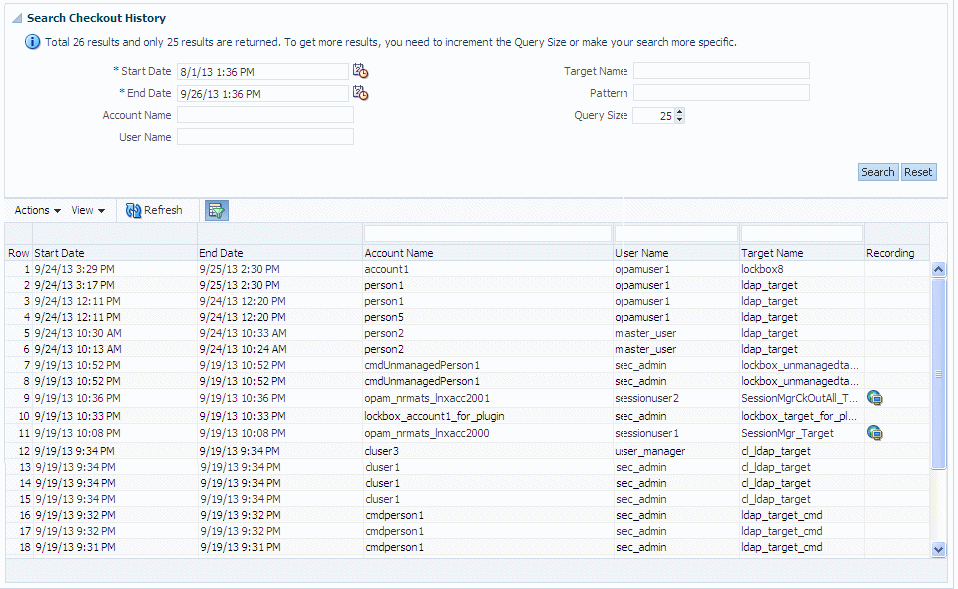
-
Specify the period in which to search by providing the Start Date and End Date (required fields). Include any other, optional search criteria in the Search Checkout History section, and then click Search.
-
When the search results display in the table, locate the user whose transcript you want to review, and click the Recording icon (
 ) in that row.
) in that row.
From the Checkout History Page
-
Select the Checkout History Report link from the Reports accordion to open the Checkout History page.
-
Use the Search Checkout History portlet to configure search parameters:
-
You must specify a Start Date and an End Date range in which to search for checkouts. Type the date and time into the blank fields or use the Calendar icons.
-
Enter information into one or more of the Account Name, User Name, Target Name, or Pattern fields.
Note:
Use the Pattern field to search for a string in the recording of a checkout event.
-
Enter a value into the Query field to limit the number of returned results.
-
-
Click Search and the results will display in the table.
-
Locate the correct account and user row in the table, and click the Recording icon in that row.
-
You are prompted to select a program, such as Wordpad, in which to open the transcript. Select a program and click Open.
The recording opens in the selected program, and displays in a transcript format (refer to Figure 8-2).
8.8 Managing Privileged Account Passwords
Oracle Privileged Account Manager provides the following options for managing privileged account passwords:
Note:
You can also perform these password management tasks by using the Oracle Privileged Account Manager command line tool or REST API.
-
For command line instructions, refer to
Section A.5, "Working with Accounts." -
For REST API instructions, refer to
Section B.6, "Account Resource."
Oracle Privileged Account Manager audits password management actions to keep track of password access.
Note:
The procedures for showing and resetting a target's service account password are different from the procedures described in this section. Refer to Section 7.3, "Managing Service Account Passwords" for information.
8.8.1 Showing an Account Password
If necessary, you can view a password in clear text for an account that you have checked out by using the Show Password option. For example, if you forget a password, you can use this feature to view the password again.
Any user can review passwords for accounts they have checked out. However, you cannot access passwords after the account is checked back in or view passwords for accounts that are checked out by other users. Attempts to do so will cause an error.
Note:
Administrators with the Security Administration Admin Role, who can access all system and target service accounts, can use this feature to view current the password for both checked out and checked in privileged accounts.
You can access the Show Password option from the My Checkouts page as follows:
-
Select My Checkouts in the Home accordion to open the My Checkouts page.
-
Select the account's row number.
-
When the Show Password icon becomes active, click the icon.
The Current Password dialog displays with the Account Name and the Password in clear text.
-
When you are finished click Close.
Administrators with the Security Administration or User Manager Admin Role can access the Show Password option as follows:
-
Ensure that you have the privileged account checked out.
Note:
For most users, if they try to view the password for an account that has already been checked back in, an error will result.
However, if you are an administrator with the Security Administrator or User Manager Admin Role, you can use this command to reset a password for both checked out and checked-in accounts.
-
Select Accounts in the Administration accordion.
-
When the Accounts page displays, use the Search portlet to locate the account.
-
Select the account row number and when the Show Password icon becomes active, click the icon.
The Current Password dialog displays with the Account Name and the Password in clear text.
-
When you are finished click Close.
8.8.2 Viewing an Account's Password History
Use the Password History option to view the password history for an account.
Note:
You must be an administrator with the Security Administration Admin Role to view the password history for a privileged account.
To view a privileged account's password history,
-
Select Accounts in the Administration accordion to open the Search Accounts page, and then click Search.
-
Select the row number of the account.
-
When the Password History icon becomes active, click the icon.
The Show Password History dialog displays with the Account Name, and the Password in clear text, and the Modification Time (Date and time of the password reset).
-
When you are finished click Close.
8.8.3 Resetting an Account Password
If necessary, you can manually reset the existing password for an account that you have checked out by using the Reset Password option.
If Security Administrators do not want to use randomized password generation, they can manually set a password of their choosing. For example, administrators might prefer to set a simple, easy-to-type password for one time use, such as during a system upgrade.
To reset an account password, use the following steps
-
Ensure that you have the privileged account checked out.
Note:
For most users, if they try resetting the password for an account that has already been checked back in, an error will result.
However, if you are an administrator with the Security Administrator Admin Role, you can use this command to reset a password for both checked out and checked-in accounts.
-
Select Accounts in the Administration accordion.
-
When the Accounts tab displays, use the Search portlet to locate the account.
-
Select the account row number and then click Reset Password.
The Reset Password dialog displays and provides the following information about the account password:
-
Account Name
-
Target Name
This dialog also contains a New Password field.
-
-
Type a password into the space provided and click Save.
You can use a password string of your choosing. The string does not have comply with the Oracle Privileged Account Manager Password Policy because the Password Policy is used for randomized password generation.
A message displays with the name of the selected account and the new password.
8.9 Removing Privileged Accounts from Oracle Privileged Account Manager
You can remove a privileged account from Oracle Privileged Account Manager by using the Search Accounts page or the Targets page.
WARNING:
When you remove a privileged account, you remove all information about the account that is stored in Oracle Privileged Account Manager.
Before removing a privileged account, it is critical that you first capture all relevant information from that account. For example, save the current password associated with that privileged account.
To remove an account from the Search Accounts page,
-
Locate the account to remove.
-
Select Accounts in the Administration accordion.
-
Click Search in the Search Accounts portlet to populate the Search Results table with a list of all available accounts.
To narrow the results or to locate a particular account, enter search criteria in one or more the Search Accounts fields, and then click Search.
-
-
In the Search Results table, select the account to be removed, and then click Remove.
-
When you are finished, click the Apply button located at the top of the page.
To remove an account from a target,
-
Locate the target from which you want to remove the account.
-
Select Targets in the Administration accordion.
-
Click Search in the Search Targets portlet to populate the Search Results table with a list of all available targets.
To narrow the results or to locate a particular target, enter search criteria in one or more the Search Targets fields, and then click Search.
-
-
Click the target name in the Search Results table to open the target.
-
Select the Privileged Accounts tab.
-
In the Search Results table, select the account to be removed and then click Remove.
-
When you are finished, click the Apply button located at the top of the page.