11 Extending the Domain to Include Oracle Access Management
This chapter describes how to extend the domain to include Oracle Access Management Access Manager in the Oracle Identity Management enterprise deployment.
This chapter includes the following topics:
-
Section 11.1, "Overview of Extending the Domain to Include Oracle Access Management Access Manager"
-
Section 11.8, "Deploying Managed Server Configuration to Local Storage"
-
Section 11.9, "Starting Managed Servers WLS_OAM1 and WLS_OAM2"
-
Section 11.11, "Creating a Single Keystore for Integrating Access Manager with Other Components"
-
Section 11.12, "Backing Up the Access Manager Configuration"
11.1 Overview of Extending the Domain to Include Oracle Access Management Access Manager
Access Manager enables your users to seamlessly gain access to web applications and other IT resources across your enterprise. It provides a centralized and automated single sign-on (SSO) solution, which includes an extensible set of authentication methods and the ability to define workflows around them. It also contains an authorization engine, which grants or denies access to particular resources based on properties of the user requesting access as well as based on the environment from which the request is made. Comprehensive policy management, auditing, and integration with other components of your IT infrastructure enrich this core functionality.
Access Manager consists of several components, including OAM Server, Oracle Access Management Console, and WebGates. The OAM Server includes all the components necessary to restrict access to enterprise resources. The Oracle Access Management Console is the administrative console to Access Manager. WebGates are web server agents that act as the actual enforcement points for Access Manager. Follow the instructions in this chapter and Chapter 15, "Configuring Single Sign-on for Administration Consoles in an Enterprise Deployment" to install and configure the Access Manager components necessary for your enterprise deployment.
11.2 About Domain URLs
After you complete this chapter, the following URL will be available:
Table 11-1 OAM URLs After Web Tier Configuration
| Component | URLs | User | SSO User |
|---|---|---|---|
|
OAM Console |
|
|
|
|
Oracle Enterprise Manager Fusion Middleware Control |
|
|
|
|
Oracle Directory Services Manager |
|
|
|
|
Oracle Entitlements Server Policy Manager |
|
|
|
11.3 Using Different Directory Configurations
Access Manager normally uses a single LDAP store to hold Identity Information. You can, however, configure Oracle Access Management Access Manager to use multiple directory stores of different types, such as Oracle Virtual Directory and a third party directory.
When you use multiple directories, you can present the directories to Access Manager as a single consolidated directory, using Oracle Virtual Directory. Alternatively, you can configure Access Manager to access each directory individually.
For more information, see the following chapters in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite:
To learn more about the different types of directory configuration for Access Manager, consult the Access Manager documentation listed under "Related Documents" in the Preface. Customers considering these variations should adjust their directory and Access Manager deployment accordingly.
11.4 Prerequisites
Before you configure Access Manager, ensure that the following tasks have been performed on IDMHOST1 and IDMHOST2:
-
Prepare the Identity Store as described in Chapter 9, "Preparing Identity Stores."
-
Configure Oracle Web Tier on WEBHOST1 and WEBHOST2 as described in Chapter 10, "Installing and Configuring Oracle Web Tier for an Enterprise Deployment."
-
Configure the load balancer as described in Section 3.3, "About Virtual Server Names Used by the Topologies."
11.5 Extending Domain with Access Manager
Start the configuration wizard on IDMHOST1 by executing the command:
IAM_MW_HOME/oracle_common/common/bin/config.sh
Then proceed as follows:
-
On the Welcome screen, select Extend an Existing WebLogic Domain. Click Next.
-
On the Select a WebLogic Domain screen, using the navigator, select the domain home of the WebLogic Administration Server, for example:
ASERVER_HOMEClick Next
-
On the Select Extension Source screen, select Oracle Access Management [iam].
Click Next
-
On the Configure JDBC Component Schema screen, do the following:
Select OAM Infrastructure.
For the Oracle RAC configuration for component schemas, select Convert to GridLink.
Click Next.
-
The Gridlink RAC Component Schema screen appears. In this screen, enter values for the following fields, specifying the connect information for the Oracle RAC database that was seeded with RCU.
-
Driver: Select Oracle's driver (Thin) for GridLink Connections,Versions:10 and later.
-
Select Enable FAN.
-
Do one of the following:
-
If SSL is not configured for ONS notifications to be encrypted, deselect SSL.
-
Select SSL and provide the appropriate wallet and wallet password.
-
-
Service Listener: Enter the SCAN address and port for the RAC database being used. You can identify this address by querying the parameter
remote_listenerin the database:SQL>show parameter remote_listener; NAME TYPE VALUE ------------------------------------------------------------- remote_listener string DB-SCAN.MYCOMPANY.COM:1521
Notes:
-
For Oracle Database 11g Release 1 (11.1), use the virtual IP and port of each database instance listener, for example:
DBHOST1-VIP.mycompany.com(port1521) andDBHOST2-VIP.mycompany.com(port1521), where1521isDB_LSNR_PORT -
For Oracle Database 10g, use multi data sources to connect to an Oracle RAC database. For information about configuring multi data sources see Appendix A, "Using Multi Data Sources with Oracle RAC."
-
-
ONS Host: Enter the SCAN address for the Oracle RAC database and the ONS remote port as reported by the database:
srvctl config nodeapps -s ONS exists: Local port 6100, remote port 6200, EM port 2016
Note:
For Oracle Database 11g Release 1 (11.1), use the hostname and port of each database's ONS service, for example:
DBHOST1.mycompany.com (port 6200)
and
DBHOST2.mycompany.com (port 6200)
Enter the following RAC component schema information:
Schema Name Service Name Schema Owner Password Access Management
OAMEDG.mycompany.comEDG_OAMpassword
-
-
In the Test JDBC Data Sources screen, confirm that all connections were successful.
The connections are tested automatically. The Status column displays the results. If all connections are not successful, click Previous to return to the previous screen and correct your entries.
Click Next when all the connections are successful.
-
On the Test Component Schema screen, the Wizard attempts to validate the data sources. If the data source validation succeeds, click Next. If it fails, click Previous, correct the problem, and try again.
-
On the Select Optional Configuration screen, select Managed Servers, Clusters and Machines.
Click Next
-
When you first enter the Configure Managed Servers screen, a managed server called oam_server1 is created automatically. Rename oam_server1 to WLS_OAM1 and update its attributes as shown in the following table. Then, add a new managed server called WLS_OAM2 with the following attributes.
Name Listen Address Listen Port Port Variable SSL Listen Port SSL Enabled WLS_OAM1
IDMHOST1.mycompany.com
14100OAM_PORTN/A
No
WLS_OAM2
IDMHOST2.mycompany.com
14100OAM_PORTN/A
No
Notes:
-
Do not change the configuration of the managed servers that were configured as a part of previous deployments.
-
Do not delete the default managed servers that are created. Rename them as described.
Click Next.
-
-
On the Configure Clusters screen, create a cluster by clicking Add. Supply the following information:
Name Cluster Messaging Mode oam_clusterUnicastLeave all other fields at the default settings and click Next.
-
On the Assign Servers to Clusters screen, associate the Managed Servers with the cluster. Click the cluster name in the right pane. Click the Managed Server under Servers, then click the arrow to assign it to the cluster.
Assign servers to the cluster as follows:
Cluster Server oam_cluster
WLS_OAM1
WLS_OAM2
Note:
Do not change the configuration of any clusters which have already been configured as part of previous application deployments.
Click Next.
-
On the Configure Machines screen, create a machine for each host in the topology. Click the Unix Machine tab and then click Add to add the following machines:
Note:
"Name" can be any unique string. "Node Manager Listen Address" must be a resolvable host name.
Name Node Manager Listen Address Node Manager Listen Port Port Variable IDMHOST1.mycompany.comIDMHOST1.mycompany.com5556NMGR_PORTIDMHOST2.mycompany.comIDMHOST2.mycompany.com5556NMGR_PORTLeave all other fields to their default values.
Note:
The machine name does not need to be a valid host name or listen address; it is just a unique identifier of a Node Manager location
Click Next.
-
On the Assign Servers to Machines screen, assign servers to machines as follows:
IDMHOST1: WLS_OAM1
IDMHOST2: WLS_OAM2
Click Next to continue.
-
On the Configuration Summary screen, click Extend to extend the domain.
Note:
If you receive a warning that says:
CFGFWK: Server listen ports in your domain configuration conflict with ports in use by active processes on this host
Click OK.
This warning appears if Managed Servers have been defined as part of previous installs and can safely be ignored.
-
On the Installation Complete screen, click Done.
-
Restart WebLogic Administration Server as described in Section 17.1, "Starting and Stopping Oracle Identity Management Components."
11.6 Configuring Access Manager
This section contains the following topics:
11.6.1 Removing IDM Domain Agent
By default, the IDMDomainAgent provides single sign-on capability for administration consoles. In enterprise deployments, WebGate handles single sign-on, so you must remove the IDMDomainAgent. Remove the IDMDomainAgent as follows:
Log in to the WebLogic console at the URL listed in Section 17.2, "About Identity Management Console URLs."
Then:
-
Select Security Realms from the Domain Structure Menu
-
Click myrealm.
-
Click the Providers tab.
-
Click Lock and Edit from the Change Center.
-
In the list of authentication providers, select IAMSuiteAgent.
-
Click Delete.
-
Click Yes to confirm the deletion.
-
Click Activate Changes from the Change Center.
-
Restart WebLogic Adminisration Server and ALL running Managed Servers, as described in Section 17.1, "Starting and Stopping Oracle Identity Management Components."
11.6.2 Setting a Global Passphrase
By default, Access Manager is configured to use the Open security model. If you plan to change this mode using idmConfigTool, you must set a global passphrase. Although you need not set the global passphrase and the web gate access password to be the same, it is recommended that you do.You do this by performing the following steps.
-
Log in to the OAM console at the URL listed in Section 17.2, "About Identity Management Console URLs."
as the WebLogic administration user.
-
Click the System Configuration tab.
-
Click Access Manager Settings located in the Access Manager section.
-
Select Open from the Actions menu. The access manager settings are displayed.
-
If you plan to use Simple security mode for OAM servers, supply a global passphrase.
-
Click Apply.
11.6.3 Configuring Access Manager by Using the IDM Configuration Tool
Now that the initial installation is done, you must perform the following tasks:
-
Configure Access Manager to use an external LDAP Directory, (
IDSTORE.mycompany.com). -
Create Access Manager WebGate Agent.
You perform these tasks by using idmConfigTool.
Note:
Two parameter settings determine whether you are configuring Access Manager with Oracle Identity Manager integration or Access Manager alone.
-
To configure Access Manager with Oracle Identity Manager integration, set
OAM11G_OIM_INTEGRATION_REQtotrueand specify a value forOAM11G_OIM_OHS_URL. -
To configure Access Manager without Oracle Identity Manager, set
OAM11G_OIM_INTEGRATION_REQtofalse.
These parameters are used to add extra links, such as Forgotten Password, to the Access Manager credential collection page
If you configure Access Manager without Oracle Identity Manager, then decide to add Oracle Identity Manager at a later date, you must run this command again to configure Access Manager with Oracle Identity Manager integration.
Perform the following tasks on IDMHOST1:
-
Set
MW_HOMEtoIAM_MW_HOME.Set
ORACLE_HOMEtoIAM_ORACLE_HOME.Set
JAVA_HOMEtoJAVA_HOME. -
Create a properties file called
config_oam1.propswith the following contents:WLSHOST: ADMINVHN.mycompany.com WLSPORT: 7001 WLSADMIN: weblogic WLSPASSWD: Admin Password IDSTORE_DIRECTORYTYPE: OUD IDSTORE_HOST: IDSTORE.mycompany.com IDSTORE_PORT: 389 IDSTORE_BINDDN: cn=oudadmin IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid OAM11G_SERVER_LOGIN_ATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_SYSTEMIDBASE: cn=systemids,dc=mycompany,dc=com IDSTORE_OAMSOFTWAREUSER: oamLDAP IDSTORE_OAMADMINUSER: oamadmin PRIMARY_OAM_SERVERS: IDMHOST1.mycompany.com:5575,IDMHOST2.mycompany.com:5575 WEBGATE_TYPE: ohsWebgate11g ACCESS_GATE_ID: Webgate_IDM OAM11G_OIM_WEBGATE_PASSWD: password to be assigned to WebGate COOKIE_DOMAIN: .mycompany.com OAM11G_WG_DENY_ON_NOT_PROTECTED: true OAM11G_IDM_DOMAIN_OHS_HOST: SSO.mycompany.com OAM11G_IDM_DOMAIN_OHS_PORT: 443 OAM11G_IDM_DOMAIN_OHS_PROTOCOL: https OAM11G_SERVER_LBR_HOST: SSO.mycompany.com OAM11G_SERVER_LBR_PORT: 443 OAM11G_SERVER_LBR_PROTOCOL: https OAM11G_OAM_SERVER_TRANSFER_MODE: simple OAM_TRANSFER_MODE: simple OAM11G_IDM_DOMAIN_LOGOUT_URLS: /console/jsp/common/logout.jsp,/em/targetauth/emaslogout.jsp OAM11G_IDSTORE_ROLE_SECURITY_ADMIN: OAMAdministrators OAM11G_SSO_ONLY_FLAG: false COOKIE_EXPIRY_INTERVAL: 120 OAM11G_IMPERSONATION_FLAG: false OAM11G_OIM_INTEGRATION_REQ: false OAM11G_OIM_OHS_URL:https://SSO.mycompany.com:443 SPLIT_DOMAIN:trueWhere:
-
WLSHOST(ADMINVHN) is the host of your administration server. This is the virtual name. -
WLSPORTis the port of your administration server,WLS_ADMIN_PORTin Section B.3. -
WLSADMINis the WebLogic administrative user you use to log in to the WebLogic console. -
WLSPASSWDis the WebLogic administrator password. -
IDSTORE_DIRECTORYTYPEisOUD,OIDorOVD. -
IDSTORE_HOSTandIDSTORE_PORTare the host and port of the Identity Store directory when accessed through the load balancer. These areLDAP_LBR_HOSTandLDAP_LBR_PORTin the Section B.3 worksheet. -
IDSTORE_BINDDNis an administrative user in the Identity Store directory. -
IDSTORE_USERSEARCHBASEis the location in the directory where Users are stored. -
IDSTORE_GROUPSEARCHBASEis the location in the directory where Groups are stored. -
IDSTORE_SEARCHBASEis the location in the directory where Users and Groups are stored. -
IDSTORE_SYSTEMIDBASEis the location of a container in the directory where the user oamLDAP is stored. -
IDSTORE_OAMSOFTWAREUSERis the name of the user you created in Section 9.4, "Preparing the Identity Store" to be used to interact with LDAP. -
IDSTORE_OAMADMINUSERis the name of the user you created in Section 9.4, "Preparing the Identity Store" to access your OAM Console. -
PRIMARY_OAM_SERVERSis a comma separated list of your OAM Servers and the proxy ports they use, for example: IDMHOST1:OAM_PROXY_PORTNote:
To determine the proxy ports your OAM Servers use:
-
Log in to the OAM console at the URL listed in Section 17.2, "About Identity Management Console URLs."
-
Click the System Configuration tab.
-
Expand Server Instances under the Common Configuration section
-
Click an OAM Server, such as WLS_OAM1, and select Open from the Actions menu.
-
Proxy port is the one shown as Port.
-
-
ACCESS_GATE_IDis the name you want to assign to the WebGate. -
OAM11G_OIM_WEBGATE_PASSWDis the password to be assign to the WebGate. -
OAM11G_IDM_DOMAIN_OHS_HOSTis the name of the load balancer which is in front of the OHS's. -
OAM11G_IDM_DOMAIN_OHS_PORTis the port that the load balancer listens on (HTTP_SSL_PORT). -
OAM11G_IDM_DOMAIN_OHS_PROTOCOLis the protocol to use when directing requests at the load balancer. -
OAM11G_WG_DENY_ON_NOT_PROTECTED, when set tofalse, allows login pages to be displayed. It should be set totruewhen using webgate11g. -
OAM_TRANSFER_MODEis the security model that the Oracle Access Manager Servers function in. Valid values aresimpleandopen. If you use thesimplemode, you must define a global passphrase, as defined in Section 11.6.2, "Setting a Global Passphrase." -
OAM11G_OAM_SERVER_TRANSFER_MODEis the security model that the OAM Servers function in, as defined in Section 11.6.2, "Setting a Global Passphrase." -
OAM11G_IDM_DOMAIN_LOGOUT_URLSis set to the various logout URLs. -
OAM11G_SSO_ONLY_FLAGconfgures Access Manager as authentication only mode or normal mode, which supports authentication and authorization.If
OAM11G_SSO_ONLY_FLAGistrue, the OAM Server operates in authentication only mode, where all authorizations return true by default without any policy validations. In this mode, the server does not have the overhead of authorization handling. This is recommended for applications which do not depend on authorization policies and need only the authentication feature of the OAM Server.If the value is
false, the server runs in default mode, where each authentication is followed by one or more authorization requests to the OAM Server. WebGate allows the access to the requested resources or not, based on the responses from the OAM Server. -
OAM11G_IMPERSONATION_FLAGis set totrueif you are configuring OAM Impersonation. -
OAM11G_SERVER_LBR_HOSTis the name of the load balancer fronting your site. This and the following two parameters are used to construct your login URL. -
OAM11G_SERVER_LBR_PORTis the port that the load balancer is listening on (HTTP_SSL_PORT). -
OAM11G_SERVER_LBR_PROTOCOLis the URL prefix to use. -
OAM11G_OIM_INTEGRATION_REQshould be set totrueif you are building a topology which contains both OAM and OIM. Otherwise set tofalseat this point. This value is only set to true when performing Access Manager/Oracle Identity Manager integration and is set during the integration phase. -
OAM11G_OIM_OHS_URLshould be set to the URL of your load balancer. This parameter is only required if your topology contains OAM and OIM. -
COOKIE_DOMAINis the domain in which the WebGate functions. -
WEBGATE_TYPEis the type of WebGate agent you want to create. -
OAM11G_IDSTORE_NAMEis the Identity Store name. If you already have an Identity Store in place which you wish to reuse (rather than allowing the tool to create a new one for you), then set the value of this parameter to the name of the Identity Store you wish to reuse. -
OAM11G_SERVER_LOGIN_ATTRIBUTEwhen set touid, ensures that when users log in, their username is validated against theuidattribute in LDAP. -
SPLIT_DOMAINshould be set totrueIf you are creating a domain with just OAM or OAM located in a different domain from OIM (Split Domain). Otherwise, it is not necessary to specify this parameter.
-
-
Configure Access Manager using the command
idmConfigToolwhich is located at:IAM_ORACLE_HOME/idmtools/binNote:
When you run the
idmConfigTool, it creates or appends to the fileidmDomainConfig.param. This file is generated in the same directory that theidmConfigToolis run from. To ensure that each time the tool is run, the same file is appended to, always run theidmConfigToolfrom the directory:IAM_ORACLE_HOME/idmtools/binThe syntax of the command on Linux is:
idmConfigTool.sh -configOAM input_file=configfileFor example:
idmConfigTool.sh -configOAM input_file=config_oam1.props
When the command runs you are prompted to enter the password of the account you are connecting to the Identity Store with. You are also asked to specify the passwords you want to assign to these accounts:
-
IDSTORE_PWD_OAMSOFTWAREUSER
-
IDSTORE_PWD_OAMADMINUSER
-
-
Check the log file for any errors or warnings and correct them. A file named
automation.logis created in the directory where you run the tool. -
Restart WebLogic Administration Server as described in Section 17.1, "Starting and Stopping Oracle Identity Management Components."
Note:
After you run idmConfigTool, several files are created that you need for subsequent tasks. Keep these in a safe location.
Two 11g WebGate profiles are created: Webgate_IDM, which is used for intercomponent communication and Webgate_IDM_11g, which is used by 11g Webgates.
The following files exist in the directory ASERVER_HOME/output/Webgate_IDM_11g. You need these when you install the WebGate software.
-
cwallet.sso -
ObAccessClient.xml -
password.xml
Additionally, you need the files aaa_cert.pem and aaa_key.pem, which are located in the directory ASERVER_HOME/output/Webgate_IDM.
11.6.4 Validating the Configuration
To Validate that this has completed correctly.
-
Access the OAM console at:
http://ADMIN.mycompany.com/oamconsole -
Log in as the Access Manager administration user you created in Section 9.4, "Preparing the Identity Store," for example,
oamadmin. -
Click the System Configuration tab
-
Expand Access Manager - SSO Agents - OAM Agents.
-
Click the open folder icon, then click Search.
-
You should see the WebGate agents
Webgate_IDMandWebgate_IDM_11g, which you created in Section 11.6.3, "Configuring Access Manager by Using the IDM Configuration Tool."
11.6.5 Updating Newly-Created Agent
After generating the initial configuration, you must edit the configuration and add advanced configuration entries.
-
Select System Configuration Tab
-
Select Access Manager - SSO Agents - OAM Agent from the directory tree. Double-click or select the open folder icon.
-
On the displayed search page click Search to perform an empty search.
-
Click the Agent
Webgate_IDM. -
Select Open from the Actions menu.
-
Set Maximum Number of Connections to
10for all of the OAM Servers listed in the primary servers list. -
If the following Logout URLs are not listed, add them:
-
/oamsso/logout.html -
/console/jsp/common/logout.jsp -
/em/targetauth/emaslogout.jsp
-
-
Click Apply.
-
Repeat Steps 4 through 7 for the WebGate agent Webgate_IDM_11g.
-
Click Policy Configuration tab.
-
Click Host Identifiers.
-
Click Open.
-
Click Search.
-
Click IAMSuiteAgent.
-
Click
+in the Host Name Variations box. -
Enter the following information:
-
Host Name:
ADMIN.mycompany.com -
Port:
80(HTTP_PORT)
-
-
Click Apply.
11.6.6 Modifying Access Manager Resources
During deployment, a number of resources are created in Access Manager with protection levels set. In order for Oracle Identity Manager to function correctly, one of these resources needs to be modified and one created.
To do this perform the following steps:
-
Log in to the OAM console at the URL listed in (About Identity and Access Management Console URLs.")
-
Navigate to IAM Suite application domain.
-
Navigate to Resources tab
-
Click New Resource and enter the following information:
-
Type: http
-
Description:
provisioning-callback -
Host Identifier:
IAMSuiteAgent -
Resource URL:
/provisioning-callback/** -
Protection Level:
Excluded -
Authentication Policy:
n/a -
Authorization Policy:
n/a
-
-
Click Apply.
-
Locate the resource
/identity/**and click on it in the Search results window. -
Click Edit.
-
Change the Protection Level to Excluded.
-
Click Apply.
11.6.7 Updating Existing WebGate Agents
If you have changed the OAM security model using the idmConfigTool you must change the security model used by any existing Webgates to reflect this change.
To do this, perform the following steps:
-
Log in to the Oracle Access Management Console as the Access Manager administration user you created in Section 9.4, "Preparing the Identity Store," at the URL listed in Section 17.2, "About Identity Management Console URLs."
-
Click the System Configuration tab.
-
Expand Access Manager - SSO Agents.
-
Click OAM Agents and select Open from the Actions menu.
-
In the Search window, click Search.
-
Click each Agent that was not created by
idmconfigToolin Section 11.6.3, "Configuring Access Manager by Using the IDM Configuration Tool", for example: IAMSuiteAgent. -
Set the Security value to the new security model. Add any missing Access Manager servers to the displayed list.
Click Apply.
11.6.8 Perform Bug 13824816 Workaround
To work around Bug 13824816, add a condition to the Admin role using the WebLogic Administration Server Console.
Note:
Perform this step now only if you specified the parameter SPLIT_DOMAIN as true when you performed the steps in Section 11.6.3, "Configuring Access Manager by Using the IDM Configuration Tool.".
If you perfomed those steps with the parameter SPLIT_DOMAIN set to false, perform the steps in this section AFTER you have integrated Oracle Identity Management with Oracle Access Manager. Section 12.23.5, "Perform Bug 13824816 Workaround, if Necessary" will remind you when you reach that point.
To add conditions to the Admin role in the Security Realm:
-
Log in to the WebLogic Administration Server Console at the URL listed in Section 17.2, "About Identity Management Console URLs."
-
In the left pane of the console, click Security Realms.
-
On the Summary of Security Realms page, click myrealm under the Realms table.
-
On the Settings page for myrealm, click the Roles & Policies tab.
-
On the Realm Roles page, expand the Global Roles entry under the Roles table. This brings up the entry for Roles.
-
Click the Roles link to go to the Global Roles page.
-
On the Global Roles page, click the Admin role to go to the Edit Global Role page:
-
On the Edit Global Roles page, under Role Conditions, click Add Conditions.
-
On the Choose a Predicate page, select Group from the predicates list and click Next.
-
On the Edit Arguments Page, specify
OAMAdministratorsin the Group Argument field and click Add. -
Click Finish to return to the Edit Global Rule page.
The Role Conditions now show the
OAMAdministratorsGroup as an entry. -
Click Save to finish adding the Admin role to the
OAMAdministratorsGroup.
11.7 Configuring Access from Web Tier
If you are adding Access Manager to an existing domain, don't forget to include OAM in the Web Tier configuration as described in Section 10.3.3, "Creating Virtual Hosts to Support Identity Management."
11.8 Deploying Managed Server Configuration to Local Storage
Once the configuration is complete, you must propagate the Oracle Identity Manager configuration to the managed server directory on IDMHOST1 and IDMHOST2.
You do this by packing and unpacking the domain, you pack the domain first on IDMDomain on IDMHOST1 then unpack it on IDMHOST1 and IDMHOST2.
Follow these steps to propagate the domain to the managed server domain directory.
-
Invoke the
packutility fromORACLE_COMMON_HOME/common/bin/on IDMHOST1../pack.sh -domain=ASERVER_HOME -template=iam_domain.jar -template_name="IAM Domain" -managed=trueThis creates a file called
iam_domain.jar. Copy this file to IDMHOST2. -
On IDMHOST1 and IDMHOST2, invoke the utility
unpack, which is also located in the directory: ORACLE_COMMON_HOME/common/bin/./unpack.sh -domain=MSERVER_HOME -template=iam_domain.jar -overwrite_domain=true -app_dir=MSERVER_HOME/applications
11.9 Starting Managed Servers WLS_OAM1 and WLS_OAM2
Start the managed servers WLS_OAM1 and WLS_OAM2 as described in Section 17.1, "Starting and Stopping Oracle Identity Management Components."
11.10 Validating Access Manager
You can validate Access Manager by using the oamtest tool. To do this, perform the following steps:
-
Ensure that
JAVA_HOMEis set in your environment. -
Add
JAVA_HOME/binto yourPATH, for example:export PATH=$JAVA_HOME/bin:$PATH
-
Change directory to:
IAM_ORACLE_HOME/oam/server/tester -
Start the test tool in a terminal window using the command:
java -jar oamtest.jar
-
When the OAM test tool starts, enter the following information in the Server Connection section of the page:
-
Primary IP Address:
IDMHOST1.mycompany.com -
Port:
5575(OAM_PROXY_PORT) -
Agent ID:
Webgate_IDM_11g -
Agent Password:
webgate password
Note:
if you configured simple mode, you must select Simple and provide the global passphrase.
Click Connect.
In the status window you see:
[reponse] Connected to primary access server -
-
In the Protected Resource URI section enter:
-
Scheme:
http -
Host:
ADMIN.mycompany.com -
Port:
80(HTTP_PORT) -
Resource:
/oamconsole
Click Validate.
In the status window you see:
[request][validate] yes -
-
In the User Identity window, enter:
-
Username:
oamadmin -
Password:
oamadmin password
Click Authenticate.
In the status window, you see:
[request] [authenticate] yesClick Authorize.
In the status window you see.
[request] [authorize] yes -
The following is an example of a test:
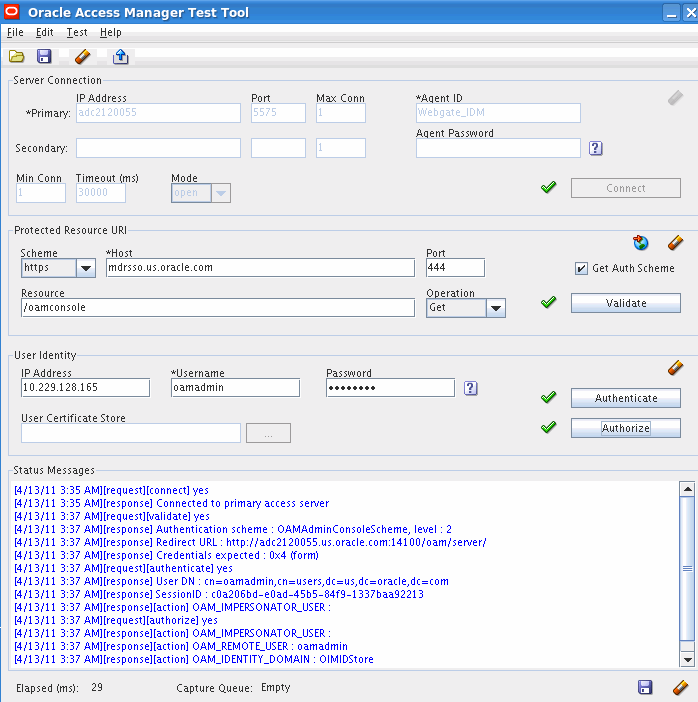
Repeat this test for each access server in the topology, remembering to change the connection details for each server.
11.11 Creating a Single Keystore for Integrating Access Manager with Other Components
When you configure Access Manager to work using the simple transport protocol, all traffic to Access Manager is encrypted. When you integrate Access Manager with other components, such as Oracle Identity Manager, you must enable the product being integrated to understand this encryption. (This is not necessary when the transport model is open.) You do this by using a keystore.
When you change Access Manager to use the simple protocol, keystores are created automatically in the directory ASERVER_HOME/output/webgate-ssl. This directory contains the following files:
-
oamclient-keystore.jks–contains the private key. -
oamclient-truststore.jks–contains the Access Manager simple mode CA certificate
These files are accessed using the Global Passphrase defined at the time of enabling Access Manager in simple mode.
Some products require configuring with both of the files above and some products, such as Oracle Identity Manager require a single consolidated keystore.
To create a keystore suitable for use by Oracle Identity Manager, perform the following steps.
-
Change directory to
ASERVER_HOME/output/webgate-ssl, for example:cd ASERVER_HOME/output/webgate-ssl -
Copy the file
oamclient-keystore.jkstossoKeystore.jks, for examplecp oamclient-keystore.jks ssoKeystore.jks
-
Import the trust store into the new keystore
ssoKeystore.jksusing the command:keytool -importcert -file IAM_ORACLE_HOME/oam/server/config/cacert.der -trustcacerts -keystore PathName_to_keystore -storetype JKSEnter the keystore password when prompted.
For example:
keytool -importcert -file IAM_ORACLE_HOME/oam/server/config/cacert.der -trustcacerts -keystore ssoKeystore.jks -storetype JKS
Note:
The files ssoKeystore.jks and oamclient-truststore.jks are required when you integrate Access Manager running in Simple mode with Oracle Identity Manager. When you integrate these components, you are asked to copy these files to the ASERVER_HOME/config/fmwconfig directory. If you subsequently extend the domain on machines where these files have been placed using pack/unpack, you must recopy ssoKeystore.jks and oamclient-truststore.jks after unpacking.
11.12 Backing Up the Access Manager Configuration
Back up the database, the WebLogic domain, and the LDAP directories, as described in Section 17.6.3, "Performing Backups During Installation and Configuration."