9 Auditing Administrative and Run-time Events
In Oracle Fusion Middleware, auditing refers to the process of collecting for review specific information related to administrative, authentication, and run-time events. Auditing can help you evaluate adherence to polices, user access controls, and risk management procedures. Auditing provides a measure of accountability and answers to the "who has done what and when" types of questions. Audit data can be used to create dashboards, compile historical data, and assess risks. Analyzing recorded audit data allows compliance officers to perform periodic reviews of compliance policies. (Analyzing and using audit data is outside the scope of this chapter.)
This chapter describes the administrative and run-time events that can be audited for Oracle Access Management services (Access Manager, Security Token Service, Identity Federation, and Mobile and Social) as well as information on configuring common auditing settings and validating your auditing configuration. It includes the following topics:
Note:
There is nothing specific or separate related to auditing OpenSSO Agents or Identity Context. Unless explicitly stated, information in this chapter is the same for all Oracle Access Management services.9.1 Understanding Oracle Fusion Middleware Auditing
Review the following sections in the Oracle Fusion Middleware Application Security Guide to gain an understanding of auditing and the Audit Framework in Oracle Fusion Middleware.
-
Oracle Fusion Middleware Audit Framework Reference for details about how the Audit database is laid out
9.2 Introduction to Oracle Access Management Auditing
Many businesses must now be able to audit identity information and user access on applications and devices. Compliance audits help an enterprise conform with regulatory requirements—Sarbanes-Oxley or the Health Insurance Portability and Accountability Act (HIPAA) are two examples.
Oracle Access Management uses the Oracle Fusion Middleware Common Audit Framework to support auditing for a large number of user authentication and authorization run-time events, and administrative events (changes to the system). The Oracle Fusion Middleware Common Audit Framework provides uniform logging and exception handling and diagnostics for all audit events.
Auditing is based on configuration parameters set using the Oracle Access Management Console which enables data capture for a user or set of users. While auditing can be enabled or disabled, it is normally enabled in production environments. Audit data can be written to either a single, centralized Oracle Database instance or to flat files known as bus-stop files.
Note:
The Oracle Fusion Middleware Common Audit Framework database audit store does not include Access Manager policy or session-data and is not configured through the Oracle Access Management Console.Auditing has minimal performance impact, and the information captured by auditing can be useful (even mission-critical). The audit log file helps the audit Administrator track errors and diagnose problems if the audit framework is not working properly.
This section contains the following topics.
9.2.1 About Oracle Access Management Auditing Configuration
An Administrator controls certain auditing parameters using the Oracle Access Management Console. This auditing configuration is recorded in the oam-config.xml file. Additional auditing configuration is required through the Common Audit Framework.
Note:
Oracle recommends that you use only the Oracle Access Management Console or WebLogic Scripting Tool (WLST) commands for changes; do not edit theoam-config.xml file directly.Event configuration (mapping events to levels) occurs in the component_events.xml file. An audit record contains a sequence of items that can be configured to meet particular requirements.
Within the Oracle Access Management Console, you can set the maximum log file and log directory size. Audit policies (known as Filter Presets declare the types of events to be captured by the audit framework for particular components.
Audit policies cannot be configured using Fusion Middleware Control, therefore audit filter settings in the EM Console will not be applied to the audit function within Oracle Access Management. Oracle Access Management does not use JPS infrastructure to configure the audit configuration. There are no WebLogic Scripting Tool (WLST) commands for auditing.
9.2.2 About Audit Record Storage
Audit data can be written to either a single, centralized Oracle Database instance or to flat files known as bus-stop files. By default, audit data is recorded to the file but administrators can change the configuration to log audit data to a database. Although the formats differ, audit data content is identical in both the flat file and the database.
-
Audit Bus-stop: Local files containing audit data records before they are pushed to the audit data store. In the event that no audit data store is configured, audit data remains in these bus-stop files. The bus-stop files are simple text files that can be queried easily to look up specific audit events. When an audit data store is in place, the bus-stop acts as an intermediary between the component and the audit data store. The local files are periodically uploaded to the audit data store based on a configurable time interval.
Bus-stop files for Java components are located in:
$DOMAIN_HOME/servers/$SERVER_NAME/logs/auditlogs/OAM/audit.log
Bus-stop files for system components are located in:
$ORACLE_INSTANCE/auditlogs/OAM/oam_server1/audit.log
-
Database Logging: Implements the Common Auditing Framework across a range of Oracle Fusion Middleware products. The benefit is audit-function commonality at the platform level.
-
Database Audit Store: In production environments, Oracle recommends using a database audit store to provide scalability and high-availability for the Common Audit Framework. A key advantage of the audit data store is that audit data from multiple components can be correlated and combined in reports; for example, authentication failures in all Middleware components and instances. Audit data is cumulative and grows over time so ideally this is a stand-alone RDBMS database for audit data only and not used by other applications.
Note:
The preferred mode in production environments is writing audit records to a stand-alone RDBMS database for audit data only.To switch to a database as the permanent store for your audit records, you must first use the Repository Creation Utility (RCU) to create a database schema for audit data. The RCU seeds that database store with the schema required to store audit records in a database. After the schema is created, configuring a database audit store involves:
-
Creating a data source that points to the audit schema you created
-
Configuring the audit store to point to the data source
Figure 9-1 provides a simplified view of the audit architecture with a supported database. As previously documented, the Oracle Fusion Middleware Audit Framework schema is provided by the RCU.
Figure 9-1 Audit to Database Architecture
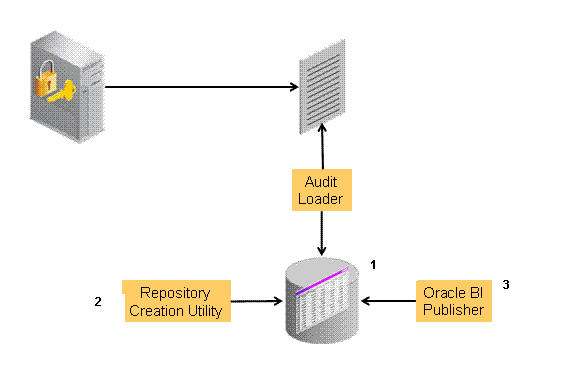
Description of "Figure 9-1 Audit to Database Architecture"
See Also:
-
"Configuring and Managing Auditing" in the Oracle Fusion Middleware Application Security Guide
An independent audit loader process reads the flat log file and inserts records in the log table of the Oracle database. The audit store allows Administrators to expose audit data with Oracle Business Intelligence Publisher using a variety of out-of-the-box reports.
-
9.2.3 About Audit Reports and Oracle Business Intelligence Publisher
Oracle Access Management integrates with Oracle Business Intelligence Publisher, which provides a pre-defined set of compliance reports through which the data in the database audit store is exposed. These reports allow you to drill down the audit data based on various criteria, such as user name, time range, application type, and execution context identifier (ECID). Out-of-the-box, there are several sample audit reports available with Oracle Access Management and accessible with Oracle Business Intelligence Publisher. You can also use Oracle Business Intelligence Publisher to create your own custom audit reports.
Oracle BI Enterprise Edition (Oracle BI EE) is a comprehensive set of enterprise business intelligence tools and infrastructure, including a scalable and efficient query and analysis server, an ad-hoc query and analysis tool, interactive dashboards, proactive intelligence and alerts, real-time predictive intelligence, and an enterprise reporting engine. The components of Oracle BI EE share a common service-oriented architecture, data access services, analytic and calculation infrastructure, metadata management services, semantic business model, security model and user preferences, and administration tools. Oracle BI EE provides scalability and performance with data-source specific optimized analysis generation, optimized data access, advanced calculation, intelligent caching services, and clustering.
See Also:
Using Audit Analysis and Reporting in the Oracle Fusion Middleware Security GuideFor an overview of how to prepare Oracle BI EE for use with auditing reports for Oracle Access Management, see "Preparing Oracle Business Intelligence Publisher EE".
Oracle BI EE reports contain enumerated fields, the data fields and labels of which are self-explanatory. Content of reports is described in Table 9-1 (taken from Knowledge Base Doc ID 1495333.1 on My Oracle Support.
Table 9-1 Oracle Business Intelligence Enterprise Edition Reports for OAM
| Report Type | Description |
|---|---|
|
Account Management |
User ID | Timestamp | Component/ Application Name | Event Details |
|
Authentication_Statistics |
Authentication_statistics Failure | Userid | Number of Events AuthenticationFromIPByUser IP Address | Distinct User Count | Total Attempts | Users AuthenticationPerIP IP Address | Distinct Users | Total Number of Attempts AuthenticationStatisticsPerServer Server Instance Name | Success Count | Failure Count |
|
Errors_and_Exceptions |
All_Errors_and_Exceptions User ID | Timestamp | Component/Application Name | Client IP Address | Message Event | Event Details Authentication_Failures User ID | Timestamp | Component/ Application Name | Client IP Address | Authentication Method | Message Event Details | Authorization_Failures Users_Activities Authentication_History User ID | Timestamp | Component/ Application Name | Client IP Address | Authentication Method | Message Event Details | Authorization_Failures Multiple_Logins_From_Same_IP IP Address | Usernames Used |
For more information, see the following topics:
9.2.4 About the Audit Log and Data
An audit log file helps the audit administrator track errors and diagnose problems when the audit framework is not working properly. An audit log file records several fields including (but not limited to) Date, Time, Initiator, EventType, EventStatus, MessageText, ECID, RID ContextFields, SessionId, TargetComponentType, ApplicationName, and EventCategory.
See Also:
The topic on audit logs in the chapter on configuring and managing auditing in the Oracle Fusion Middleware Security Guide9.3 Access Manager Events You Can Audit
This section provides the following topics:
9.3.1 Access Manager Administrative Events You Can Audit
Administrative events are those generated when the Oracle Access Management Console is used. The Access Manager-specific administrative events that can be audited and the details captured for them are listed in Table 9-2. These event definitions and configurations are implemented as part of the audit service in Oracle Platform Security Services.
Note:
The amount and type of information that is logged is controlled by choosing a filter preset from the Audit Configuration section. Auditable events for each filter preset are fixed in the read-onlycomponent_events.xml file. Editing or customizing this file is not supported.Table 9-2 Access Manager Administrative Audit Events
| Administrative Event | Event Data Include |
|---|---|
|
Oracle Access Management Console Login success/failure |
|
|
Authentication Policy Creation |
|
|
Authentication Policy Modification |
|
|
Authentication Policy Removal |
|
|
Resource Creation |
|
|
Resource Modification |
|
|
Resource Removal |
|
|
Authentication Scheme Creation |
|
|
Authentication Scheme Modification |
|
|
Authentication Scheme Removal (Delete) |
|
|
Response Creation |
|
|
Response Modification |
|
|
Response Removal (Delete) |
|
|
Partner Addition |
|
|
Partner Modification |
|
|
Partner Removal |
|
|
Conditions creation |
|
|
Conditions Modification |
|
|
Conditions Removal |
|
|
Server Domain creation |
|
|
Server Domain Modification |
|
|
Server Domain Removal |
|
|
Server configuration change |
|
9.3.2 Access Manager Run-time Events You Can Audit
Run-time events are those generated by some of the events the Access Manager component engines issue when interacting with one another. The run-time events that can be audited, when they are issued, and the details captured for them are listed in Table 9-3. These event definitions and configurations are implemented as part of the audit service in Oracle Platform Security Services.
Note:
The amount and type of information that is logged is controlled by choosing a filter preset in the Audit Configuration. Auditable events for each filter preset are fixed in the read-onlycomponent_events.xml file. Editing or customizing this file is not supported.Table 9-3 Access Manager Run-time Audit Events
| Run-time Event | Issued When | Event Details Include |
|---|---|---|
|
Authentication Attempt |
A user attempts to access a protected resource and the request arrives at the SSO server; this event might be followed by the events credential submit and authentication success or failure. |
|
|
Authentication Success |
A client submits credentials and credential validation is successful. |
|
|
Authentication Failure |
A client submits credentials and credential validation fails. |
|
|
Session Creation |
Authentication succeeds. |
|
|
Session Destroy |
Authentication succeeds. |
|
|
Login success |
A client finishes the login procedure and it is forwarded to the agent. |
|
|
Login failure |
A client fails to login; this event is issued only when all the retry authentication attempts allowed have failed or when the account is locked. |
|
|
Logout success |
A client finishes the logout procedure and is forwarded to the agent. |
|
|
Logout failure |
A client fails to logout. |
|
|
Credential Collection |
A client is redirected to the credential collection page. |
|
|
Credential Submit |
A client submits credentials. |
|
|
Authorization Success |
A client has been authorized to access a resource. |
|
|
Authorization Failure |
A client has not been authorized to access a resource. |
|
|
Server Start Up |
The server starts up. |
|
|
Server Shut Down |
The server shuts down. |
|
9.3.3 Auditing Authentication Events
Auditing events during authentication can help Administrators scrutinize security weaknesses in their systems. The events that an Administrator can configure for auditing during authentication are:
-
Authentication success
-
Authentication failure
-
Create, modify, delete, or view Authentication Policy data
Information related to the user being authenticated may include the following:
-
IP address
-
Browser type
-
User Login ID
-
Time of Access
Note:
Oracle recommends that you avoid auditing, logging, or tracing sensitive user attributes, such as user passwords.Information about users requesting authentication or brute force attacks can be stored in the file system or in a back-end database.
9.4 Mobile and Social Events You Can Audit
This section provides the following topics:
9.4.1 REST Run-Time Audit Events
You can audit the run-time events in the following table.
Table 9-4 REST Run-Time Audit Events
| Run-time Event | Issued When | Event Details Include |
|---|---|---|
|
Partner Security Validation Event |
Partner credentials are validated using the appropriate security mechanism. The event is logged for both success and failure scenarios. |
|
|
Create Token |
A token is created. |
|
|
Terminate Token |
A token is terminated. |
|
|
Get Token |
A token is obtained/read. |
|
9.4.2 Mobile and Social Audit Events
You can audit the runtime events in the following table.
Table 9-5 Mobile and Social Run-Time Audit Events
| Run-Time Event | Issued When | Event Details Include |
|---|---|---|
|
IDP Login |
A user attempts to log in using an identity provider |
|
|
IDP Rest Access |
The REST service for identity providers is accessed |
|
|
IDP User Profile |
The user profile related to a user authenticated by an identity provider is obtained |
|
|
Local Registration |
A user registers locally by providing registration info |
|
|
Security Validation |
The security mechanism on the Identity Provider REST Services for Relying Party (RP) is validated |
|
|
OpenID Authentication Request |
An OpenID authentication request is initiated |
|
|
OAuth Authentication Request |
An OAuth authentication request is initiated |
|
|
OAuth Access Token Request |
An OAuth access token request is initiated |
|
|
Local Login |
User logs in locally |
|
9.5 Identity Federation Events You Can Audit
The Identity Federation service also uses the Fusion Middleware Audit Framework for auditing. The following data is part of each audit record, regardless of the event or event type that is audited:
-
timestamp - Date and time the audit event occurred
-
initiator - the initiator of the audit event (for some events this attribute may be empty)
-
ECID - the execution context ID
The Fusion Middleware Audit Framework supports the following audit levels:
-
None
-
Low
-
Medium
-
Custom
Events can be audited in different categories and audit levels. Table 9-6 lists the event categories and where they are described in this chapter.
Table 9-6 Categories of Audit Events for Identity Federation
| Category | Described in ... |
|---|---|
|
Session Management |
|
|
Protocol Flow |
|
|
Server Configuration |
|
|
Security |
See Also:
Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation chapter on "Diagnostics and Auditing" for greater detailThe following section contain more information.
9.5.1 Session Management Events for Identity Federation
Session Management events for this Identity Federation release, include a subset of auditable events for the previous release. For attributes of each event, see "Session Management Events" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Table 9-7 Identity Federation Session Management Events
| Auditable Events | Auditing Not Supported in This Release for ... |
|---|---|
|
CreateUserSession – Creation of a session after a successful login |
CreateUserFederation – Creation of a user federation between two remote servers |
|
DeleteUserSession – Deletion of a session after logout |
UpdateUserFederation - Updating the user federation between two remote servers |
|
CreateActiveUserFederation – Creation of an active federation after successful login |
DeleteUserFederation – Deletion of a user federation between two remote servers |
|
CreateActiveUserFederation – Creation of an active federation after successful login |
|
|
DeleteActiveUserFederation - Deletion of an active federation after logout |
|
|
LocalAuthentication – Authentication of a user at OIF |
|
|
LocalLogout - Logout of a user at Identity Federation |
9.5.2 Protocol Flow Events for Identity Federation
Protocol flow events for this Identity Federation release, include a subset of auditable events for the previous Identity Federation release. For attributes of each event, see "Protocol Flow Events" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Table 9-8 Protocol Flow Events for Identity Federation
| Auditable Events | Auditing Not Supported in This Release for ... |
|---|---|
|
IncomingMessage Message being received by Identity Federation |
AssertionCreation Creation of an assertion by Identity Federation (Success only |
|
OutgoingMessage Message being sent by Identity Federation (Success only) |
|
|
AssertionConsumption Consumption of an assertion by Identity Federation (Success only) |
9.5.3 Server Configuration Events for Identity Federation
Auditable Server configuration events for this Identity Federation release, include a subset of auditable events for the previous Identity Federation release. For attributes of each event, see "Server Configuration Events" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Table 9-9 Server Configuration Identity Federation
| Auditable Events | Auditing Not Supported in This Release for ... |
|---|---|
|
CreateConfigProperty Adding a new configuration property (Success only) |
SetDataStoreType Changing the type of a data store (Success only) |
|
ChangeConfigProperty Changing the value of an existing configuration property (Success only) |
ChangeDataStore Setting of the federation data store (Success only) |
|
DeleteConfigProperty Deleting a configuration property (Success only) |
|
|
CreatePeerProvider Adding a new provider to the list of trusted providers (Success only) |
|
|
UpdatePeerProvider Updating the information on an existing provider in the list of trusted providers (Success only) PeerProviderID |
|
|
DeletePeerProvider Deleting a provider from the list of trusted providers (Success only) |
|
|
LoadMetadata Loading of metadata (Success only) |
|
|
ChangeFederation Changing of the trusted providers (Success only) |
|
|
ChangeServerProperty Changing of a server configuration property (Success only) |
9.5.4 Security Events for Identity Federation
Auditable security events for this Identity Federation release, include all auditable events for the previous Identity Federation release. For attributes of each event, see "Security Events" in Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Table 9-10 Security Events for Identity Federation
| Auditable Events | Auditing Not Supported in This Release for ... |
|---|---|
|
CreateSignature Creation of a digital signature by Identity Federation |
n/a |
|
VerifySignature Verification of a digital signature by Identity Federation |
|
|
EncryptData Encryption of data by Identity Federation |
|
|
DecryptData Decryption of data by Identity Federation |
9.6 Security Token Service Events You Can Audit
Security Token Service provides an independent audit configuration file, named component_events.xml, that defines specific event types and events to audit. The following sections provide more details.
9.6.1 About Audit Record Content Common to All Events
The following data is part of each audit record, regardless of the event or event type that is audited:
-
Date and time of event
-
IP address of the client initiating event
-
Client identity
-
Processing time for the event
9.6.2 Security Token Service Administrative Events You Can Audit
Security Token Service administrative events fall into several configuration management operations defined in component_events.xml. See details in Table 9-11.
Table 9-11 Security Token Service Configuration Management Operations
| Security Token Service Configuration Operations | Description |
|---|---|
|
Common Attributes |
|
|
Create Validation Template |
Audit event recorded for the creation of a Validation Template referenced by CreateValidationTemplate. Attributes:
|
|
Update Validation Template |
Audit event recorded for the update of a Validation Template referenced by UpdateValidationTemplate. Attributes:
|
|
Delete Validation Template |
Audit event recorded for the delete event of a Validation Template referenced by DeleteValidationTemplate. Attributes:
|
|
Create Issuance Template |
Audit event recorded for the creation of an Issuance Template referenced by CreateIssuanceTemplate. Attributes:
|
|
Update Issuance Template |
Audit event recorded for the update of an Issuance Template referenced by UpdateIssuanceTemplate. Attributes:
|
|
Delete Issuance Template |
Audit event recorded for the delete event of an Issuance Template referenced by DeleteIssuanceTemplate. Attributes:
|
|
Create Partner Profile |
Audit event recorded for the creation of Partner Profile referenced by CreatePartnerProfile. Attributes:
|
|
Update Partner Profile |
Audit event recorded for the update of a Partner Profile referenced by UpdatePartnerProfile. Attributes:
|
|
Delete Partner Profile |
Audit event recorded for the delete event of Partner Profile referenced by DeletePartnerProfile. Attributes:
|
|
Create Partner |
Audit event recorded for the creation of Partner Profile referenced by CreatePartner. Attributes:
|
|
Update Partner |
Audit event recorded for the update of a Partner Profile referenced by UpdatePartner. Attributes:
|
|
Delete Partner |
Audit event recorded for the delete event of Partner Profile referenced by DeletePartner. Attributes:
|
|
Generic Admin Creation |
Audit event recorded for the generic create administrative operation referenced by GenericAdminCreation. Attributes:
|
|
Generic Admin Update |
Audit event recorded for the update of a generic update administrative operation referenced by GenericAdminUpdate. Attributes:
|
|
Generic Admin Removal |
Audit event recorded for generic delete administrative operation referenced by GenericAdminDeletion. Attributes:
|
9.6.3 Security Token Service Run-time Events You Can Audit
Security Token Service-specific run-time events for token operations are defined in component_events.xml. See details in Table 9-12.
Table 9-12 Security Token Service-specific Run-time Events
| Token Operations | Description |
|---|---|
|
Common Attributes |
|
|
Incoming Message |
Incoming RSTR message received by Security Token Service referenced by OutgoingMessage. Attributes populated for this event, if available:
|
|
Outgoing Message |
Outgoing RSTR message received by Security Token Service referenced by IncomingMessage. Attributes populated for this event, if available:
|
|
Token Validation |
Audit event for token validation in Security Token Service referenced by TokenValidation. The status attribute indicates whether or not the validation operation was successful. Attributes populated for this event, if available:
|
|
Token Generation |
Audit event for token generation in Security Token Service referenced by TokenGeneration. Attributes populated for this event, if available:
|
|
LDAP User Authentication |
Audit event for local user authentication with the LDAP Directory referenced by LDAPUserAuthentication. Attributes populated for this event, if available:
|
|
Generic Runtime Operation |
Audit event for a generic operation performed by Security Token Service referenced by GenericRuntimeOperation Attributes populated for this event, if available:
|
9.7 Setting Up Auditing for Oracle Access Management
The following overview provides a list of the tasks that must be performed before you can perform auditing for Oracle Access Management.
Task overview: Configuring auditing
-
Set up the audit data store, as described in "Setting Up the Audit Database Store".
-
Set up publishing for audit reports, as described in "Preparing Oracle Business Intelligence Publisher EE".
-
Edit the Audit Configuration in the Oracle Access Management Console, as described in:
See Section 9.8, "Validating Auditing and Reports" for details testing and validating the audit configuration.
9.7.1 Setting Up the Audit Database Store
This topic provides an overview of the tasks required to create the audit database and extend the schema using the Repository Creation Utility (RCU). This task is required before you can audit events for Oracle Access Management if you choose a database store for audit data.
See Also:
-
Oracle Fusion Middleware Application Security Guide for details on managing the audit store
-
Oracle Fusion Middleware Repository Creation Utility User's Guide
Task overview: Creating the database audit store
-
Create an audit database, version 11.1.0.7 or later, as described in the Oracle Fusion Middleware Application Security Guide.
-
Run the RCU against the database, as described in "Create the Audit Schema using RCU" in the Oracle Fusion Middleware Repository Creation Utility User's Guide.
-
Set up audit data sources for the audit loader and configure it for the OAM Server as described in "Set Up Audit Data Sources" in the Oracle Fusion Middleware Application Security Guide:
-
Use the Java EE audit loader configuration for WebLogic Server.
-
Use the JNDI name of the data source jdbc/AuditDB that points to the database that was set up in step 2 above.
-
-
In the service instance specified in the domain file
($DOMAIN_HOME/config/fmwconfig/jps-config.xml), enable database auditing by changing the value of the propertyaudit.loader.repositoryTypetoDB. For example:<serviceInstance name="audit.db" provider="audit.provider"> <property name="audit.loader.repositoryType" value="DB"/> <property name="auditstore.type" value="db"/> <property name="audit.loader.jndi" value="jdbc/AuditDB"/> <property name="audit.maxDirSize" value="0"/> <property name="audit.filterPreset" value="None"/> <property name="audit.maxFileSize" value="104857600"/> <property name="audit.loader.interval" value="15"/> <propertySetRef ref="props.db.1"/> </serviceInstance>
-
Restart the WebLogic Server.
-
Ensure that the audit loader is configured for the OAM Server and that it points to the proper database, as described in "Configure a Database Audit Store for Java Components" in the Oracle Fusion Middleware Application Security Guide.
-
Maintain the bus-stop files, as described in "Tuning the Bus-stop Files" in the Oracle Fusion Middleware Application Security Guide.
9.7.2 Preparing Oracle Business Intelligence Publisher EE
You must prepare Oracle Business Intelligence Publisher Enterprise Edition (EE) for use with Oracle Access Management audit reports as outlined in the following procedure.
See Also:
-
Oracle Fusion Middleware Metadata Repository Builder's Guide for Oracle Business Intelligence Enterprise Edition
-
Oracle Fusion Middleware Developer's Guide for Oracle Business Intelligence Enterprise Edition
-
Oracle Fusion Middleware User's Guide for Oracle Business Intelligence Enterprise Edition
Task overview: Prepare Oracle BI Publisher
-
Install Oracle BI Publisher, as described in the Oracle Business Intelligence Enterprise Edition Installation and Upgrade Guide.
-
Perform tasks as described in "Set Up Oracle Reports in Oracle Business Intelligence Publisher" in the Oracle Fusion Middleware Application Security Guide:
-
Unzip the
oam_audit_reports_11_1_2_0_0.zipinto your Reports folder.This zip file is located in the $ORACLE_HOME/oam/server/reports/ directory.
-
Set up the JNDI connection for the audit data source or the JDBC connection the audit database.
The datasource name must be "Audit".
-
-
Set up audit report templates, as described in the section "Set Up Audit Report Templates" of the Oracle Fusion Middleware Application Security Guide.
-
Set up audit report filters, as described in the section "Set Up Audit Report Filters" of the Oracle Fusion Middleware Application Security Guide.
-
View reports from the following path: Reports/Oracle_Fusion_Middleware_Audit reports.
See Also:
"Validating Auditing and Reports"
9.7.3 Using the Oracle Access Management Console for Audit Configuration
Within Oracle Access Management, certain Audit Configuration settings are accessible as Common Settings under the System Configuration. These settings are not required when you audit to a database. Figure 9-2 shows the Audit Configuration section of the Common Settings page.
Figure 9-2 Common Settings: Auditing Configuration

Description of "Figure 9-2 Common Settings: Auditing Configuration"
The Auditing section provides settings for the Log Directory, Filter Settings, and Audit Configuration Users.
Note:
The actual log directory cannot be configured using the Oracle Access Management Console. It is the default directory for the Common Audit Framework audit loader. Changing the directory impacts the audit loader and is not supported.Table 9-13 describes the elements in the Audit Configuration page.
Table 9-13 Audit Configuration Elements
| Elements | Description |
|---|---|
|
Maximum Directory Size |
The maximum size, in MBs, of the directory that contains audit output files. For example, assuming that the maximum file size is 10, a value of 100 for this parameter implies that the directory allows a maximum of 10 files. Once the maximum directory size is reached, the audit logging stops. For example, a value of 100 specifies a maximum of 10 files if the file size is 10 MB. If the size exceeds this, the creation of audit logs stops. This is configured using the |
|
Maximum File Size |
The maximum size, in MBs, of an audit log file. Once the size of a file reaches the maxi mum size, a new log file is created. For example, specifying 10 directs file rotation when the file size reaches 10 MB. This is configured using the |
|
Filter Enabled |
Check this box to enable event filtering. |
|
Filter Preset |
Defines the amount and type of information that is logged when the filter is enabled. The default value is Low.
Events for each filter preset are fixed in the read-only component_events.xml file. Editing or customizing this file is not supported for Oracle Access Management. Only items that are configured for auditing at the specified filter preset can be audited. |
|
Users |
Specifies the list of users whose actions are included only when the filter is enabled. All actions of the special users are audited regardless of the filter preset. Administrators can add, remove or edit special users from this table. |
9.7.4 Adding, Viewing, or Editing Audit Settings
The Administrator controls the amount and type of information that is logged by choosing a filter preset from the Audit Configuration tab on the OAM Server Common Properties page.
Note:
Auditable events for each filter preset are fixed in the read-onlycomponent_events.xml file. Editing or customizing this file is not supported.The following procedure describes how to add, view, or edit OAM Server Common Audit Configuration settings. Individual audit policies cannot be configured using Fusion Middleware Control. Oracle Access Management does not use JPS infrastructure to configure the audit configuration. There are no WebLogic Scripting Tool (WLST) commands for auditing.
To view or edit auditing configuration in the Oracle Access Management Console
-
From the Oracle Access Management Console, click Common Settings.
-
In the Audit Configuration section, enter appropriate details for your environment (Table 9-13):
-
Maximum Log directory size
-
Maximum Log file size
-
Filter Enabled
-
Filter Preset (to define verbosity of audit data)
-
Users to include specific users from the audit by clicking the Add (+) button above the Users table and entering a value in the field.
-
-
Click Apply to submit the Audit Configuration (or close the page without applying changes).
-
Restart AdminServer and OAM Servers after changes are applied.
9.8 Validating Auditing and Reports
Use the following procedure to test your run-time event auditing configuration.
-
Configure auditing parameters as described in "Setting Up Auditing for Oracle Access Management".
-
Ensure the Agents and Servers are running.
-
Prepare BI EE Publisher as described in "Preparing Oracle Business Intelligence Publisher EE".
To validate your auditing configuration
-
Authentication Event: Audit Console login success/failure as described here or any administrative event described in Table 9-2, "Access Manager Administrative Audit Events".
-
Sign out of Oracle Access Management Console.
-
Sign in to Oracle Access Management Console with invalid user (not Administrator) credentials.
-
Sign in to Oracle Access Management Console using the proper Administrator credentials.
-
Review Log File: Open the audit.log file and search for the last Administrative event entries:
$DOMAIN_HOME/servers/$ADMINSERVER_NAME/logs/auditlogs/OAM/audit.log
-
Review Database Log:
-
Perform tasks in "Setting Up the Audit Database Store".
-
Generate an Authentication event as described in Step 1.
-
Connect to the database and connecting to the database and reviews audit events under IAU_BASE table.
-
-
-
Runtime Event: Audit Authorization success/failure as described here or any runtime event described in Table 9-3, "Access Manager Run-time Audit Events".
-
In a browser window, enter the URL of a protected resource for which you are not authorized.
-
Review Log File: Open the audit.log file and search for the last Administrative event entries:
$DOMAIN_HOME/servers/$ADMINSERVER_NAME/logs/auditlogs/OAM/audit.log
-
Review Database Log:
-
Perform tasks in "Setting Up the Audit Database Store".
-
Generate and Authentication event as described in Step 1.
-
Connect to the database and connecting to the database and reviews audit events under IAU_BASE table.
-
-
-
Audit Configuration Changes: See Also "Adding, Viewing, or Editing Audit Settings".
-
From the Oracle Access Management Console, System Configuration tab, Common Configuration, modify Maximum Directory Size (MB) and Maximum File Size (MB) parameters.
-
Repeat Steps here to confirm auditing is working.
-
-
View Reports:
-
Sign in to Oracle BI EE. For example:
http://host:port/xmlpserver
Here, host is the computer hosting Oracle BI Publisher; port is the listening port for BI Publisher; xmlpserver is the login page for BI Publisher.
-
In Oracle BI Publisher Enterprise, locate the desired reports. For example:
Click Shared Folders, the component that contains the report you would like to view and then select the desired report.
-
Perform any analysis as desired, or edit your auditing configuration as needed.
$MW_HOME/user_projects/domains/base_domain/servers/oam_server1/logs/ auditlogs/OAM/
-
-
Archive and manage audit logs according to your company policies.