11 Managing Oracle Privileged Account Manager on IBM WebSphere
Most of the conceptual and procedural information contained in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager applies to both WebLogic and WebSphere environments.
This chapter provides information that is specific to using Oracle Privileged Account Manager on IBM WebSphere.
The topics include:
-
Differences in How Oracle Privileged Account Manager is Deployed in Oracle Fusion Middleware
-
Differences in Getting Started with Administering Oracle Privileged Account Manager
-
Differences in Oracle Privileged Account Manager Authorization
-
Differences in Configuring and Managing the Servers on IBM WebSphere
-
Differences When Adding Targets to Oracle Privileged Account Manager on IBM WebSphere
-
Differences in Managing Oracle Privileged Account Manager Auditing and Logging
-
Configuring Oracle Privileged Account Manager for High Availability in a Clustered Environment
-
Upgrading Oracle Privileged Account Manager on IBM WebSphere
-
Limitations and Known Issues When Using Oracle Privileged Account Manager on IBM WebSphere
11.1 Differences in How Oracle Privileged Account Manager is Deployed in Oracle Fusion Middleware
This section describes the differences in how Oracle Privileged Account Manager on IBM WebSphere is deployed within Oracle Fusion Middleware.
Figure 11-1 illustrates a WebSphere cell configuration:
Figure 11-1 Oracle Privileged Account Manager on IBM WebSphere Deployed Within Oracle Fusion Middleware
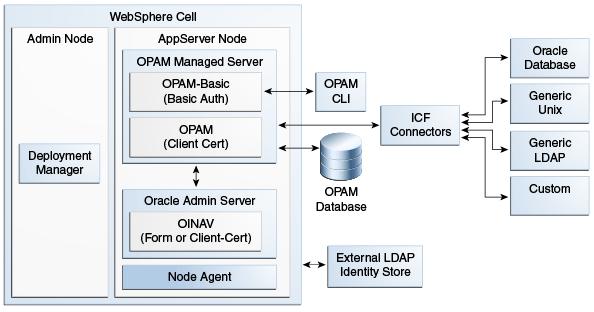
As you examine this figure, note that the cell configuration contains two profiles:
-
Deployment Manager profile: This profile contains an Admin Node in which a Deployment Manager server is running.
-
AppServer profile: This profile contains an AppServer Node in which the following servers are running:
-
OracleAdminServer: The Oracle Identity Navigator application, which hosts the Oracle Privileged Account Manager Console, is deployed on this server. The chosen authorization mode is either form or client-cert, as required.
Because IBM WebSphere does not have an embedded LDAP server, you must configure an external LDAP server to serve as an identity store for users, groups, and so forth.
-
Oracle Privileged Account Manager Managed Server: Two Oracle Privileged Account Manager applications are deployed on this server. One application uses a basic authorization-mode, which is required for the Oracle Privileged Account Manager command line tool. The other application uses a client-cert authorization mode, which the Oracle Privileged Account Manager Console uses to talk to the Oracle Privileged Account Manager server.
This server is similar to a WebLogic Managed Server where the data source is targeted for the Oracle Privileged Account Manager database store and where the ICF connectors are configured.
-
11.2 Differences in Getting Started with Administering Oracle Privileged Account Manager
This section contains information about starting to administer Oracle Privileged Account Manager in an IBM WebSphere environment.
The topics include
11.2.1 Default Ports
After installing 11g Release 2 on IBM WebSphere, Oracle recommends that you become familiar with the following default ports for Oracle Privileged Account Manager in this release:
| Port Type | Default Port | Description |
|---|---|---|
|
Oracle Privileged Account Manager |
18102 |
Default SSL-enabled port for the Oracle Privileged Account Manager application server ( In a shiphome (such as an out-of-the-box environment) there are two WebSphere servers relevant to Oracle Privileged Account Manager:
|
|
OracleAdminServer |
9002 |
Default non-SSL port for the OracleAdminServer application server (where Oracle Identity Navigator and the Oracle Privileged Account Manager Console are deployed). |
|
OracleAdminServer responds to SSL |
9003 |
Default SSL-enabled port for the OracleAdminServer application server (where Oracle Identity Navigator and the Oracle Privileged Account Manager Console are deployed). |
11.2.2 Starting Oracle Privileged Account Manager on IBM WebSphere
This section provides information about tasks you must perform before starting the Oracle Privileged Account Manager Console on IBM WebSphere.
The topics include
11.2.2.1 Before You Begin
Before starting Oracle Privileged Account Manager, perform the following steps:
Set IBM WebSphere-Specific Environment Variables
You must set the following IBM WebSphere-specific environment variables:
| Variable | Set Value To |
|---|---|
APPSERVER_TYPE |
was |
WAS_HOME |
Full path of the WebSphere application server home directory For example: /WASSH/WebSphere/AppServer |
WAS_DMGR_PROFILE_HOME |
Deployment Manager profile home directory
The Deployment Manager deploys applications to a cell of application servers, which it manages. A profile defines the runtime environment. The profile includes all of the configurable files that the server processes in the runtime environment. Set to an absolute path, for example: /WASSH/WebSphere/AppServer/profiles/Dmgr01 |
Seed the Identity Store for Oracle Privileged Account Manager
Seeding the identity store is a required task. For information about seeding the identity store with the necessary Oracle Privileged Account Manager users and groups, refer to "Preparing the Identity Store" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.
Note:
Before executing the instructions in "Preparing the Identity Store," you must set the IBM WebSphere-specific environment variables described in Set IBM WebSphere-Specific Environment Variables.11.2.2.2 Configuring Oracle Privileged Account Manager on IBM WebSphere
To configure Oracle Privileged Account Manager on IBM WebSphere, perform the following steps from the machine where the Deployment Manager is running:
-
From a command window, set the following:
On UNIX:
setenv WAS_HOME setenv ORACLE_HOME setenv DMGR_CELL_HOME
Note:
When settingDMGR_CELL_HOME, use a value that is similar to the following:$WAS_HOME/profiles/<DMGR Profile Name>/config/cells/<Cell Name>
-
Go to the
$ORACLE_HOME/opam/bindirectory and run the following
script:On UNIX:
opam-was_config.sh
Provide the following information when prompted:
-
Deployment Manager Hostname
-
Deployment Manager SOAP Connector Port
-
Deployment Manager Bootstrap Address Port
-
WebSphere Admin Username
-
WebSphere Admin Password
Note:
The port values are located in this file:$WAS_HOME/profiles/<Dmgr profile>/properties/portdef.props
-
-
After running the script, you must:
Stop the Deployment Manager by navigating to the following directory in the IBM WebSphere home and entering the following command:
On UNIX:
profiles/dmgr_profileName/bin/stopManager.sh
For example, on a UNIX operating system:
/disk01/IBM/WebSphere/AppServer/profiles/Dmgr01/bin/stopManager.sh
Note:
If you are running thestopManager.sh (or stopManager.bat) command from the WAS_HOME/bin directory, then you must specify the -profileName parameter. For example, on a UNIX operating system:
WAS_HOME/bin/stopManager.sh -profileName dmgr_profileName
After stopping the node and IBM WebSphere Deployment Manager, you can start the Deployment Manager, node, and servers as described in Section 2.12, "Task 12: Start the IBM WebSphere Servers."
Note:
When you perform the final step to start any additional servers, be sure to use opam_server1 as the Oracle Privileged Account Manager server name.After starting the servers:
-
If you enabled Transparent Data Encryption (TDE) mode as described in Section 2.7, "Task 7: Optional: Enabling TDE in Oracle Privileged Account Manager Data Store (For Oracle Privileged Account Manager Users Only)," then you have finished installing and configuring Oracle Privileged Account Manager on IBM WebSphere. No further steps are required. You can now verify the Oracle Privileged Account Manager functionality.
-
If you decided not to enable TDE mode, then you must complete steps to set up non-TDE mode. Continue to Section 11.2.2.3, "Setting Up Non-TDE Mode" for instructions.
11.2.2.3 Setting Up Non-TDE Mode
Note:
Oracle Privileged Account Manager can operate with Oracle Database TDE (Transparent Data Encryption) mode. Oracle strongly recommends to enable the TDE mode for enhanced security.If you want to disable TDE mode, you must set the flag tdemode to false.
Note:
The steps described in this section are required only if you chose to skip Section 2.7, "Task 7: Optional: Enabling TDE in Oracle Privileged Account Manager Data Store (For Oracle Privileged Account Manager Users Only)".Complete the following steps to disable TDE mode:
-
Set the environment variables
ORACLE_HOMEandJAVA_HOME. -
Run the following script:
On UNIX:
ORACLE_HOME/opam/bin/opam.sh -url OPAM_Server_Url -x modifyglobalconfig -propertyname tdemode -propertyvalue false -u OPAM_APPLICATION_CONFIGURATOR_USER -p Password
Where
OPAM_Server_URLis of the form:https://OPAM_Managed_Server_Hostname:OPAM_Managed_Server_SSL_port/opam-basic
Note:
You can enable or disable TDE mode at any point after installing and configuring Oracle Privileged Account Manager. For more information about changing the TDE mode at a later time, refer to the "Securing Data On Disk" topic in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.When the scripts are finished running, you will be finished installing and configuring Oracle Privileged Account Manager on IBM WebSphere. No further steps are required, and you can verify the Oracle Privileged Account Manager functionality.
11.3 Differences in Oracle Privileged Account Manager Authorization
This section contains information about understanding Oracle Privileged Account Manager authorization on IBM WebSphere.
11.3.1 Administration Role Types
Most of the information in the "Administration Role Types" section of the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager is applicable for both WebLogic and WebSphere environments. However, the following information is specific to understanding the bootstrap user in the WebSphere environment.
After installation, the default administrator is the wasadmin user (also known as the bootstrap user) who is a member of the Administrators group. You must use the wasadmin user to create and assign users to the Oracle Privileged Account Manager Admin Roles described in Table 2-1 in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager. Those users can then perform the administration tasks described in this table.
Note:
Although it is possible for the default administrator to assign all those roles to himself or herself, this is not typical.After installation, you can use the wasadmin user, as the bootstrap user, to map the users from the domain identity store to the Oracle Privileged Account Manager Common Admin Roles detailed in Table 2-1. Users mapped to the Security Administrator role can assign the Common Admin Roles to other users, and can later replace the wasadmin user in your environment. After you complete the initial user mapping, replace the default administrator user by mapping the Security Administrator role to at least one administrator user defined in your domain identity store.
11.4 Differences in Configuring and Managing the Servers on IBM WebSphere
The "Configuring and Managing the Servers" chapter of the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager advises that you review the Oracle publications listed in Table 4-1 Reference Publications before you start configuring the Oracle Privileged Account Manager server.
If you are adding and managing an Oracle Privileged Account Manager server on IBM WebSphere, review Section 9.1, "IBM WebSphere Identity Stores" for information about the following topics:
-
IBM WebSphere concepts and terminology
-
Creating a default authenticator in Oracle WebLogic Server
-
Configuring the OVD authenticator in Oracle WebLogic Server
11.5 Differences When Adding Targets to Oracle Privileged Account Manager on IBM WebSphere
The procedure for adding targets to Oracle Privileged Account Manager is described in "Adding Targets to Oracle Privileged Account Manager" of the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager. However, the process for configuring an Oracle database target is slightly different if you are using Oracle Privileged Account Manager on IBM WebSphere:
If you select an Oracle database target, then no driver jar is required. For other target systems, you must include one of the following third-party jars:
-
For MSSQL: Copy the
sqljdbc4.jar. -
For MySQL: Copy the
mysql-connector-java-5.1.20-bin.jar. -
For Sybase: Copy the
jconn4.jar.
You can modify the connector jars to include these third-party jars as follows:
-
Make a back-up copy of the DBUM connector bundle, which is available in
ORACLE_HOME/connectors/dbum/bundle/org.identityconnectors.dbum-1.0.1116.jar -
Create a
temporary/libfolder and put the third-party jars in that folder. -
Update the bundle with the third-party jar:
jar -uvf org.identityconnectors.dbum-1.0.1116.jar lib/JAR_NAME -
Remove the
temporary/libfolder. -
Restart all Oracle Privileged Account Manager processes for the change to take effect.
For more information, refer to "Installing the Connector on the Connector Server" in the Oracle Identity Manager Connector Guide for Database User Management.
11.6 Differences in Managing Oracle Privileged Account Manager Auditing and Logging
This section provides information that is specific to configuring Oracle Privileged Account Manager auditing and logging on IBM WebSphere.
The topics include:
11.6.1 Configuring Auditing for Oracle Privileged Account Manager
The procedures for configuring file-based auditing or database-based auditing on an IBM WebSphere server are essentially the same as described in "Configuring Auditing in Oracle Privileged Account Manager" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager; except for the following:
-
For both file-based auditing and database-based auditing, when instructed to launch the application server shell, you must launch WSAdmin rather than WLST.
-
WebSphere executes commands beginning with
Audit.When performing any of the steps that use a WLST audit command (getAuditPolicy,setAuditPolicy,getAuditRepository, orsetAuditRepository), you must ensureAudit.precedes the command name.For example,
Audit.getAuditPolicy()on WebSphere is equivalent togetAuditPolicy()on WebLogic.Note:
Refer to Section 8.2, "Setting Up Reporting and Auditing for OAAM on IBM WebSphere" for more information about executing these steps. The steps for Oracle Privileged Account Manager are analogous.
11.6.2 Configuring Basic Logging for Oracle Privileged Account Manager
The procedures for configuring Oracle Privileged Account Manager logging on an IBM WebSphere server is essentially the same as described in "Configuring Basic Logging" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager; but with the following caveats:
-
Instead of invoking WLST to run the commands, you must first enter the WSAdmin shell. For more information, visit the following website:
http://pic.dhe.ibm.com/infocenter/wasinfo/v6r1/index.jsp?topic=%2Fcom.ibm.websphere.nd.doc%2Finfo%2Fae%2Fae%2Frxml_commandline.htmlHowever, instead of invoking the default IBM version of WSAdmin, you must invoke the Oracle version of WSAdmin to obtain support for Oracle commands. You can invoke the Oracle version of WSAdmin from the following location:
IAM_HOME/common/bin -
To invoke the WLST commands, you must precede each command with
OracleODL. For example,-
To use the
getLogLevelcommand in WLST, you must rungetLogLevel(logger="oracle.idm.opam")
-
To use the command on WebSphere, you must run
OracleODL.getLogLevel(logger="oracle.idm.opam")
-
-
The log messages generated by Oracle Privileged Account Manager's logger (such as,
oracle.idm.opam) are stored in the following location:$WAS_HOME/profiles/[ProfileName]/[ServerName]/logs/[AppServerName]/ [AppServerName]-diagnostic.log
11.7 Differences in Performing Advanced Configuration Tasks for Oracle Privileged Account Manager on IBM WebSphere
This section describes the differences in performing the following advanced configuration tasks for Oracle Privileged Account Manager on IBM WebSphere:
11.7.1 Differences When Configuring Oracle Privileged Account Manager to Communicate with Target Systems Over SSL
To communicate securely over SSL with a target system, the IBM WebSphere instance running Oracle Privileged Account Manager must trust the SSL certificate used by the target system because Oracle Privileged Account Manager inherits its SSL configuration from the IBM WebSphere container in which it runs. To have the IBM WebSphere instance running Oracle Privileged Account Manager (and therefore Oracle Privileged Account Manager) trust the target system's SSL certificate, you must import the certificate into the truststore used by that IBM WebSphere instance.
Use the following steps to enable SSL communication between the target system and Oracle Privileged Account Manager:
-
Export the SSL certificate from the target system host computer.
Note:
The steps for exporting an SSL certificate are different for each target system type. Refer to the product documentation provided for your target system for detailed instructions. -
Copy the certificate to the machine where you have the IBM WebSphere instance running Oracle Privileged Account Manager.
If you have the Oracle Privileged Account Manager/Oracle Identity Navigator Console and the Oracle Privileged Account Manager server running on different machines, you must copy the SSL certificate to the Oracle Privileged Account Manager server machine.
-
To import the certificate into the IBM WebSphere Cell's truststore,
-
Log in to the IBM WebSphere Console.
-
Select Security > SSL certificate and key management > Key stores and certificates > CellDefaultTrustStore > Signer certificates > Add.
-
From the Add screen, enter your hostname into the Alias field.
-
Specify the Data Type, as follows:
If the exported certificate is in: Then select: BASE64-encoded format Base 64 encoded ASCII Data Binary format Binary DER data -
Locate the certificate file to be imported on the local file system where IBM WebSphere is running. Enter the full path and file name into the File Name field.
-
-
Import the file, and then verify that it imported correctly.
Note:
For more information about managing Oracle Fusion Middleware security on IBM WebSphere, refer to Chapter 11, "Managing Oracle Privileged Account Manager on IBM WebSphere."For more general topics and concepts, refer to the Oracle Fusion Middleware Application Security Guide.
11.7.2 Differences When Securing Data On Disk
After initial installation, the procedures for enabling or disabling Oracle Database Transparent Data Encryption (TDE) mode for Oracle Privileged Account Manager on IBM WebSphere are essentially the same as described in "Securing Data on Disk" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.
The only difference is that for both the "Enabling TDE Mode" and "Disabling TDE Mode" sections, the OPAM_Server_Url must be in the following form:
https://OPAM_Managed_Server_Hostname:OPAM_Managed_Server_SSL_port/
opam-basic
11.8 Differences When Integrating with Oracle Identity Manager
This section describes several differences to be aware of when you are integrating Oracle Privileged Account Manager with Oracle Identity Manager. The topics include:
11.8.1 Differences When Retrieving and Importing the CA Certificate
If you are configuring Oracle Privileged Account Manager for integration with Oracle Identity Manager, the procedures for retrieving and importing the CA Certificate are slightly different than described in "Adding the CA Certificate" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.
Difference When Retrieving the CA Certificate
In the first step, when you are directed to connect to the Oracle Privileged Account Manager server web service, you must connect to
https://opamhost:opamSSLport/opam-basic
Differences When Importing the CA Certificate
Use these steps to import the CA certificate to an IBM WebSphere truststore:
-
Log in to the IBM WebSphere Console.
-
Select Security > SSL certificate and key management > Key stores and certificates > CellDefaultTrustStore > Signer certificates > Add.
-
From the Add screen, enter the hostname of the Oracle Privileged Account Manager server into the Alias field.
-
Select the Base 64 encoded ASCII Data data type because the Oracle Privileged Account Manager server CA certificate (
.pem) file was exported in BASE64-encoded format. -
Locate the Oracle Privileged Account Manager server CA certificate (.pem) file on the local file system where IBM WebSphere is running. Enter the full path and file name into the File Name field.
-
Save the
.pemfile tomaster configuration.
11.8.2 Differences When Running the opamSetup Script
The basic procedure for running the Oracle Privileged Account Manager-Oracle Identity Management integration setup script (opamSetup) is described in "Running the opamSetup Script" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.
However, if you are running this script on an IBM WebSphere server, there is a minor difference in the description of the ctxFactory option. The usual context factory name (noted parenthetically in the table) is different for IBM WebSphere as shown here:
| Option | Description |
|---|---|
| -ctxFactory <Initial context factory> | Provide the name of the context factory (usually com.ibm.websphere.naming.WsnInitialContextFactory). |
11.9 Differences When Using the Oracle Privileged Account Manager Command Line Tool and REST Interfaces on IBM WebSphere
When using the Oracle Privileged Account Manager command line tool or REST interfaces on IBM WebSphere, you must be aware of the following differences:
-
The target URL for Oracle Privileged Account Manager is,
https://opamhost:opamSSLport/opam-basicThis difference only applies to the command line tool and REST interfaces. In the Oracle Privileged Account Manager Console when you add an Oracle Privileged Account Manager server, you use the same URL for both IBM WebSphere and WebLogic.
-
The default port for the OracleAdminServer (where the Oracle Privileged Account Manager Console runs) is 9002. The Oracle Privileged Account Manager Managed Server port (18102) is the same on both IBM WebSphere sand WebLogic.
11.10 Configuring Oracle Privileged Account Manager for High Availability in a Clustered Environment
This section describes how to install and configure Oracle Privileged Account Manager on IBM WebSphere in a clustered configuration with High Availability support.
Note:
This information is specific to Oracle Privileged Account Manager on IBM WebSphere.Topics in this section include:
11.10.1 Overview of a Clustered Configuration
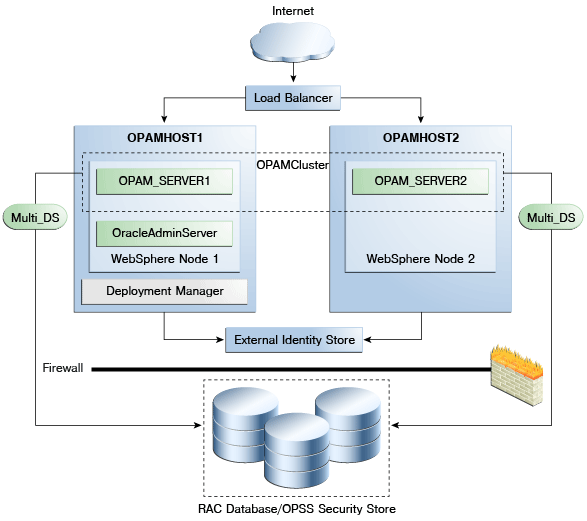
To set up Oracle Privileged Account Manager in a clustered configuration with high availability support, you must configure two machines as follows:
-
Deployment Manager machine:
-
IBM WebSphere Deployment Manager
-
IBM WebSphere Node 1
-
OracleAdminServer
-
opam_server1
-
-
IBM WebSphere Node 2 machine:
-
IBM WebSphere Node 2
-
opam_server2
-
Refer to the following figure.
11.10.2 Installing Oracle Privileged Account Manager for a Clustered Configuration
To install and configure Oracle Privileged Account Manager for maximum high availability, perform the following tasks:
-
Identify a Database and Install the Required Database Schema
-
Configure the Oracle Platform Security Services Security Store
11.10.2.1 Identify a Database and Install the Required Database Schema
You must install a database and load the Oracle Privileged Account Manager schema into that database.
For more information, refer to Section 2.3, "Task 3: Identify a Database and Install the Required Database Schemas."
11.10.2.2 Install IBM WebSphere
Install the IBM WebSphere Application Server software, including the latest Fix Pack, on both the Deployment Manager machine and on the IBM WebSphere Node 2 machine.
For instructions, refer to Section 2.4, "Task 4: Install the IBM WebSphere Software."
11.10.2.3 Install the Oracle Identity and Access Management Suite
You must install the Oracle Identity and Access Management Suite on both the Deployment Manager machine and on the IBM WebSphere Node 2 machine.
For instructions, refer to the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
When installing Oracle Fusion Middleware products on IBM WebSphere, the following special instructions apply:
-
When you run the Oracle Fusion Middleware installer, you must use the
-DSHOW_APPSERVER_TYPE_SCREEN=trueparameter to let the Oracle Universal Installer prompt for the IBM WebSphere home location.For example,
diskname/iamsuite/Disk1/runInstaller -jreLoc diskname/IBM/WebSphere/AppServer/java/jre -DSHOW_APPSERVER_TYPE_SCREEN=true
-
When you are prompted to specify a JRE/JDK location, you can specify the following directory in the IBM WebSphere home:
On UNIX: WAS_HOME/java
For example, if you are using the default location for a typical IBM WebSphere Application Server directory on a UNIX operating system:
diskname/IBM/WebSphere/AppServer/java -
When you are prompted to provide a Middleware home, note that you can enter a new Middleware home directory path.
When you install Oracle Fusion Middleware products on Oracle WebLogic Server, you create the Middleware home. This is because Oracle WebLogic Server is included in the Middleware home.
In contrast, when you install Oracle Fusion Middleware on IBM WebSphere, you create the Middleware home when you install the Oracle Fusion Middleware software. This is because the IBM WebSphere software is not installed inside the Middleware home. It is installed in a separate directory structure.
-
When you select IBM WebSphere as your application server and you are prompted for the Application Server location, enter the path to the IBM WebSphere Application Server directory that you created in Section 2.4, "Task 4: Install the IBM WebSphere Software."
For example,
diskname/IBM/WebSphere/AppServer/
11.10.2.4 Configure IBM WebSphere on the Deployment Manager Machine
On the Deployment Manager machine, use the Oracle Fusion Middleware Configuration Wizard to create the Oracle Privileged Account Manager cell. By default, the Configuration Wizard is located at
MW_HOME/Oracle_IDM1/common/bin/was_config.sh
Select Oracle Privileged Account Manager (Form auth-mode OINAV) or Oracle Privileged Account Manager (Client-cert auth-mode OINAV), depending on the auth-mode required for Oracle Identity Navigator.
Table 11-2 provides information about specific Configuration Wizard screens and the appropriate information to enter on those screens—it does not cover self-explanatory, standard screens.
Table 11-2 Information for Specific Configuration Wizard Screens
| Screen Name | Input Description |
|---|---|
|
Select Optional Configuration |
At a minimum, you must select the Application Servers, Clusters and End Points option—this is a required option. |
|
Configure Application Servers |
Perform the following steps:
|
|
Configure Clusters Screen |
Perform the following steps:
|
|
Configure Additional Cluster Members |
Click Next or, optionally, add servers to an existing system in the cluster. |
11.10.2.5 (Optional) Set Up TDE Mode
Oracle Privileged Account Manager can operate with Oracle Database TDE (Transparent Data Encryption) mode. You can choose to enable or disable TDE mode; however, Oracle strongly recommends that you enable the TDE mode for enhanced security.
This section includes the following topics:
11.10.2.5.1 Enabling TDE in the Database
To enable TDE (Transparent Data Encryption) in the database for Oracle Privileged Account Manager, refer to "Enabling Transparent Data Encryption" in the Oracle Database Advanced Security Administrator's Guide.
For more information about using TDE, refer to "Securing Stored Data Using Transparent Data Encryption" in the Oracle Database Advanced Security Administrator's Guide.
11.10.2.5.2 Enabling Encryption in the Oracle Privileged Account Manager Schema
To enable encryption in the Oracle Privileged Account Manager schema, run the opamxencrypt.sql script with the Oracle Privileged Account Manager schema user, using sqlplus or any other client.
IAM_HOME/opam/sql/opamxencrypt.sql
For example,
sqlplus DEV_OPAM/welcome1 @IAM_HOME/opam/sql/opamxencrypt.sql
11.10.2.6 Configure the Oracle Platform Security Services Security Store
Note:
You must execute this task from the machine where you are running the Deployment Manager.To configure the Oracle Platform Security Services (OPSS) Database Security Store, follow the instructions in Section 2.10, "Task 10: Configure the Database Security Store."
11.10.2.7 Start the Deployment Manager
To start the Deployment Manager, go to the WAS_HOME/bin location and execute the following command:
./startManager.sh -profileName <dmgr_prof_name>
11.10.2.8 Configure IBM WebSphere on the IBM WebSphere Node 2 Machine
On WebSphere Node 2 machine, launch the Oracle Fusion Middleware Configuration Wizard to federate the machine and configure its cell. By default, the Configuration Wizard is located at
MW_HOME/Oracle_IDM1/common/bin/was_config.sh
Table 11-3 provides information about specific Configuration Wizard screens and the appropriate information to enter on those screens—it does not cover self-explanatory, standard screens.
Table 11-3 Information for Specific Configuration Wizard Screens
| Screen Name | Input Description |
|---|---|
|
Select Configuration Option |
Select the Federate Machine and Configure Cell option. |
|
Specify Profile and Node Name Information |
Enter information about the profile and node names you want to create for the WebSphere Node 2 Machine. |
|
Specify Deployment Manager Information |
Enter information about the existing Deployment Manager system. |
|
Select Optional Configuration |
Be sure to select the Application Servers, Clusters and End Points option—this is a required option. |
|
Configure Additional Cluster Members |
Perform the following steps:
|
11.10.2.9 Configure the External LDAP Server
On IBM WebSphere, OPSS supports only LDAP-based registries. OPSS does not support IBM WebSphere's built-in file-based user registry.
To configure the Oracle Internet Directory store for OPSS:
-
Enter the following command:
cd <oracle_common>/common/bin -
Run the
wsadmincommand using the same credentials that you provided when you set up the IBM WebSphere cell../wsadmin.sh -conntype SOAP -port <port_number> -user <username> -password <passwd>
The port details are available in this file:
$WAS_HOME/profiles/Dmgr01/logs/AboutThisProfile.txt -
Enter the following command:
Opss.configureIdentityStore(propsFileLoc="<location of properties file>")
Use the following sample properties file for reference:
user.search.bases=cn=Users,dc=myhost,dc=mycompany,dc=com group.search.bases=cn=Groups,dc=myhost,dc=mycompany,dc=com subscriber.name=dc=myhost,dc=mycompany,dc=com ldap.host=ldaphost.mycompany.com ldap.port=3333 # admin.id must be the full DN of the user in the LDAP admin.id=cn=orcladmin,cn=Users,dc=myhost,dc=mycompany,dc=com admin.pass=welcome1 user.filter=(&(uid=%v)(objectclass=person)) group.filter=(&(cn=%v)(objectclass=groupofuniquenames)) user.id.map=*:uid group.id.map=*:cn group.member.id.map=groupofuniquenames:uniquemember ssl=false # primary.admin.id indicates a user who has admin permissions in the LDAP, must be the name of the user, for example, for user "cn=tom", the primary.admin.id is "tom" primary.admin.id=orcladmin # optional, default to "OID" idstore.type=OID # Optional properties for JPS LDAP identity store can also be configured in the file. username.attr=cn user.object.classes=person
-
Set the IBM WebSphere-specific environment variables as described in Set IBM WebSphere-Specific Environment Variables.
Note:
After completing the preceding steps, you must seed the identity store with the necessary Oracle Privileged Account Manager users and groups. Refer to "Preparing the Identity Store" in the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager for information.11.10.2.10 Configure Oracle Privileged Account Manager
You are now ready to configure Oracle Privileged Account Manager. You must perform this task from the Deployment Manager machine.
For instructions, refer to Section 11.2.2.2, "Configuring Oracle Privileged Account Manager on IBM WebSphere."
11.10.2.11 Restart the Servers
To restart the servers:
-
Stop the Deployment Manager on the Deployment Manager machine. Execute the following from
$WAS_HOME/bin:./stopManager.sh -profileName <dmgr_prof_name> -username <username> -password <password>
-
Stop the node on WebSphere Node 2 machine. Execute:
./stopNode.sh -profileName <server_prof_name> -username <username> -password <password>
-
Start the Deployment Manager, node, and servers on Deployment Manager machine. Execute:
./startManager.sh -profileName <dmgr_prof_name> ./syncNode.sh <dmgr_host_name> <SOAP connector port> -profileName <server_prof_name> -username <username> -password <password> ./startNode.sh -profileName <server_prof_name> ./startServer.sh OracleAdminServer -profileName <server_prof_name> ./startServer.sh <opam_server_name> -profileName <server_prof_name>
-
Start the node and Oracle Privileged Account Manager server on WebSphere Node 2 machine:
./syncNode.sh <dmgr_host_name> <SOAP connector port> -profileName <server_prof_name> -username <username> -password <password> ./startNode.sh -profileName <server_prof_name> ./startServer.sh <opam_server_name> -profileName <server_prof_name>
After starting the servers:
-
If you enabled Transparent Data Encryption (TDE) mode as described in Section 11.10.2.5, "(Optional) Set Up TDE Mode," then you have finished installing and configuring Oracle Privileged Account Manager on IBM WebSphere. No further steps are required. You can now verify the Oracle Privileged Account Manager functionality.
-
If you decided not to enable TDE mode, then you must complete steps to set up non-TDE mode on both of the nodes. Refer to Section 11.2.2.3, "Setting Up Non-TDE Mode" for instructions.
11.11 Upgrading Oracle Privileged Account Manager on IBM WebSphere
This section describes how to upgrade and configure Oracle Privileged Account Manager on IBM WebSphere.
The topics include:
Note:
When you are instructed to start or stop the servers during the upgrade process, use the steps described in Section 3.2.1, "Starting and Stopping Servers on IBM WebSphere."11.11.1 Upgrading from Release 11gR2 PS1 to Release 11gR2 PS2
To upgrade from Oracle Privileged Account Manager Release 11gR2 PS1 to Oracle Privileged Account Manager Release 11gR2 PS2, perform the following steps:
11.11.1.1 Stop the Servers
The following procedure shows the sequence you must use to stop the servers, the node, and the Deployment Manager in the cell:
-
Stop the Oracle Privileged Account Manager Managed Server by navigating to the following directory in the IBM WebSphere home and entering the following command:
On UNIX operating systems:
profiles/<server_profileName>/bin/stopServer.sh <OPAM managed server name>
For example:
/disk01/IBM/WebSphere/AppServer/profiles/Custom01/bin/stopServer.sh opam_server1
Note:
If you are running thestopServer.sh(orstopServer.bat) command from WAS_HOME/bindirectory, you must specify the-profileNameparameter.For example, on a UNIX operating system:
WAS_HOME/bin/stopServer.sh opam_server1 -profileName <server_profileName>
-
Stop OracleAdminServer by navigating to the following directory in the IBM WebSphere home and entering the following command:
On UNIX operating systems:
profiles/<server_profileName>/bin/stopServer.sh OracleAdminServerFor example:
/disk01/IBM/WebSphere/AppServer/profiles/Custom01/bin/stopServer.sh OracleAdminServer
Note:
If you are running thestopServer.sh(orstopServer.bat) command from WAS_HOME/bindirectory, you must specify the-profileNameparameter.For example, on a UNIX operating system:
WAS_HOME/bin/stopServer.sh OracleAdminServer -profileName <server_profileName>
-
Stop the node by navigating to the following directory in the IBM WebSphere home and entering the following command:
On UNIX operating systems:
profiles/<server_profileName>/bin/stopNode.shFor example:
/disk01/IBM/WebSphere/AppServer/profiles/Custom01/bin/stopNode.sh
Note:
If you are running thestopNode.sh(orstopNode.bat) command from WAS_HOME/bindirectory, you must specify the-profileNameparameter.For example, on a UNIX operating system:
WAS_HOME/bin/stopNode.sh -profileName <server_profileName>
-
Stop the Deployment Manager by navigating to the following directory in the IBM WebSphere home and entering the following command:
On UNIX operating systems:
profiles/dmgr_profileName/bin/stopManager.shFor example, on a UNIX operating system:
/disk01/IBM/WebSphere/AppServer/profiles/Dmgr01/bin/stopManager.sh
Note:
If you are running thestopManager.sh(orstopManager.bat) command from theWAS_HOME/bindirectory, then you must specify the -profileNameparameter.For example, on a UNIX operating system:
WAS_HOME/bin/stopManager.sh -profileName dmgr_profileName
11.11.1.2 Update the Oracle Privileged Account Manager Binaries
To update the Oracle Privileged Account Manager binaries to 11.1.2.2.0, you must use the Oracle Identity and Access Management 11.1.2.2.0 installer. To use this installer, perform the following tasks:
-
Start the Oracle Identity and Access Management 11g Release 2 (11.1.2.2.0) Installer
-
Install Oracle Identity and Access Management 11g Release 2 (11.1.2.2.0)
11.11.1.2.1 Obtain the Software
For information about obtaining Oracle Fusion Middleware 11g software, refer to the Oracle Fusion Middleware Download, Installation, and Configuration Readme Files on the Oracle Technology Network.
11.11.1.2.2 Start the Oracle Identity and Access Management 11g Release 2 (11.1.2.2.0) Installer
To start the Oracle Identity and Access Management Installer
Note:
-
If you are installing on an IBM AIX operating system, you must run the
rootpre.shscript from theDisk1directory before you start the Installer. -
Starting the Installer as the
rootuser is not supported.
On UNIX operating systems:
-
Navigate to the directory where you extracted the contents of the Installer.
-
Move to the following location:
cd Disk1
-
Run the following command:
./runInstaller -jreLoc <full path to the JRE directory> -DSHOW_APPSERVER_TYPE_SCREEN=TRUEFor example:
./runInstaller -jreLoc <MW_HOME>/jdk160_29/jre -DSHOW_APPSERVER_TYPE_SCREEN=TRUENote:
When you select IBM WebSphere as your application server and you are prompted for the Application Server Location, enter the path to the IBM WebSphere application server directory.For example:
diskname/IBM/WebSphere/AppServer/
On Windows operating systems:
-
Navigate to the directory where you extracted the contents of the Installer.
-
Move to the following location:
cd Disk1
-
Run the following command:
setup.exe -jreLoc <full path to the JRE directory> -DSHOW_APPSERVER_TYPE_SCREEN=TRUEFor example:
setup.exe -jreLoc <MW_HOME>/jdk160_29/jre -DSHOW_APPSERVER_TYPE_SCREEN=TRUE
Note:
-
If you do not specify the
-jreLocoption on the command line when using the Oracle JRockit JDK, then the following warning message is displayed:-XX:MaxPermSize=512m is not a valid VM option.
Ignoring this warning message does not affect the installation. You can continue with the installation.
On 64-bit platforms, if you install Oracle WebLogic Server using the generic jar file, then the
jrockit_1.6.0_29directory is not created in your Middleware Home. You must enter the absolute path to the JRE folder from where your JDK is located. -
When you select IBM WebSphere as your application server and you are prompted for the Application Server Location, enter the path to the IBM WebSphere application server directory.
For example:
diskname/IBM/WebSphere/AppServer/
11.11.1.2.3 Install Oracle Identity and Access Management 11g Release 2 (11.1.2.2.0)
Use the Oracle Identity and Access Management 11.1.2.2.0 Installer to upgrade existing Oracle Identity and Access Management binaries to 11.1.2.2.0 as follows:
-
Start the Installer, and when the Welcome screen appears, click Next.
-
The Install Software Updates screen appears. Select whether or not you want to search for updates, and then click Next.
-
The Prerequisite Checks screen appears. If all prerequisite checks pass inspection, click Next.
-
When the Specify Installation Location screen appears,
-
Point the Middleware Home to the existing Middleware Home installed on your system.
-
Specify the path of the existing Oracle Identity and Access Management Home in the Oracle Home Directory field. This directory is also referred to as <IAM_HOME>.
-
Click Next.
-
-
The Installation Summary screen appears, and it displays a summary of the choices that you made. Review this summary and decide whether you want to proceed with the installation.
-
To modify any of your configuration settings at this stage, select a topic in the left navigation page and modify your choices.
-
To continue installing Oracle Identity and Access Management, click Install.
-
-
The Installation Progress screen appears.
Monitor the progress of your installation. The location of the installation log file is listed for reference. After the installation progress reaches 100%, click OK.
If you encounter any issues, check the log file. For information about locating the log files, see "Locating Installation Log Files" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
Note:
If you cancel or abort while the installation is in progress, you must manually delete the <IAM_HOME> directory before you can reinstall the Oracle Identity and Access Management software.To invoke online help at any stage of the installation process, click Help on the installation wizard screens.
-
When the Installation Complete screen appears, click Finish.
This installation process copies the 11.1.2.2.0 Oracle Identity and Access Management software to your system.
For more information, refer to "Installing and Configuring Oracle Identity and Access Management (11.1.2.2.0)" in the Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management.
11.11.1.3 Upgrade the Database Schema
Run the Patch Set Assistant to upgrade the database schema. Refer to "Upgrading Schemas Using Patch Set Assistant" in the Oracle Fusion Middleware Upgrade Guide for Identity and Access Management for instructions.
11.11.1.4 Start the Servers
After stopping the node and IBM WebSphere Deployment Manager, you can start the Deployment Manager, node, and servers as described in Section 11.2.2, "Starting Oracle Privileged Account Manager on IBM WebSphere."
Note:
When you perform the final step to start any additional servers, be sure to use opam_server1 as the Oracle Privileged Account Manager server name.11.11.1.5 Update the Applications
After starting the servers, you must update the Oracle Identity Navigator and Oracle Privileged Account Manager applications to the upgraded instance. You can update these applications by using one of the following methods:
11.11.1.5.1 From the Command Line
To update the Oracle Identity Navigator and Oracle Privileged Account Manager applications from the command line:
-
Update the Oracle Identity Navigator application, as follows:
-
Navigate to the following location:
ORACLE_HOME/common/bin -
Run the following command:
-
On UNIX operating systems:
./wsadmin.sh -conntype SOAP -port <port_number> -f <IAM_HOME>/oinav/tools/updateOinavWas.py -o <IAM_HOME> -user <username> -password <passwd>
-
On Windows operating systems:
wsadmin.cmd -conntype SOAP -port <port_number> -f <IAM_HOME>\oinav\tools\updateOinavWas.py -o <IAM_HOME> -user <username> -password <passwd>
Note:
The port values are located in this file:$WAS_HOME/profiles/<Dmgr profile>/properties/portdef.props
-
-
-
Update the Oracle Privileged Account Manager applications, as follows:
-
Navigate to the following location:
ORACLE_HOME/common/bin -
Run the following command:
-
On UNIX operating systems:
./wsadmin.sh -conntype SOAP -port <port_number> -f <IAM_HOME>/opam/tools/updateOpamWas.py -o <IAM_HOME> -user <username> -password <passwd>
-
On Windows operating systems:
wsadmin.cmd -conntype SOAP -port <port_number> -f <IAM_HOME>\opam\tools\updateOpamWas.py -o <IAM_HOME> -user <username> -password <passwd>
Note:
The port values are located in the following file:$WAS_HOME/profiles/<Dmgr profile>/properties/portdef.props
-
-
11.11.1.5.2 From the IBM WebSphere Console
To update the applications from the IBM WebSphere Console:
-
Select Applications > Application Types > WebSphere enterprise applications.
-
Update the Oracle Identity Navigator application, as follows:
-
Select the oiNavApp application.
-
Click Update.
-
Enter (or browse to) the new
EARfile inOracle_Home.You can find the
oinavEARfiles in the following locations. Use one of these files, depending on the auth-mode install template that was selected in the original instance.<IAM_HOME>/oinav/modules/oinav.ear_11.1.1.3.0/websphere/oinav-was-form.earor
<IAM_HOME>/oinav/modules/oinav.ear_11.1.1.3.0/websphere/oinav-was-cc.ear -
No further changes are necessary. Click Next on the subsequent screens and then click Finish. A final screen displays so you can save your changes.
-
-
Update the Oracle Privileged Account Manager applications, as follows:
Note:
You must update two applications,opamandopam-basic.-
Select the opam application.
-
Click Update.
-
Enter (or browse to) the new
EARfile inOracle_Home.Use the
opamEARfile in the following location:<IAM_HOME>/opam/modules/opam.ear_11.1.2/websphere/opam-was-cc.ear -
Click Finish.
-
Go back and select the opam-basic application.
-
Click Update.
-
Enter (or browse to) the new
EARfile inOracle_Home.Use the opam-basic
EARfile in the following location:<IAM_HOME>/opam/modules/opam.ear_11.1.2/websphere/opam-was-basic.ear -
No further changes are necessary. Click Next on the subsequent screens and then click Finish. A final screen displays so you can save your changes.
-
11.11.2 Performing Optional Upgrade Steps in 11gR2 PS2 Release
For this release, the following new upgrade steps are optional:
-
Configure Oracle Privileged Session Manager for the Upgraded Instance
-
Configure Oracle Identity Navigator on the Oracle Privileged Account Manager Managed Server
Configure Oracle Privileged Session Manager for the Upgraded Instance
The Oracle Privileged Session Manager (Session Manager) application was introduced in 11g Release 2 PS2 to manage the privileged sessions to a target system. For more information about Session Manager, refer to the Oracle Fusion Middleware Administrator's Guide for Oracle Privileged Account Manager.
To configure Oracle Privileged Session Manager for the upgraded instance,
-
Stop the servers as described in Section 11.11.1.1, "Stop the Servers."
-
If more than one IBM WebSphere Deployment Manager profile is present, ensure that the profile where Oracle Privileged Account Manager is configured is the default profile.
Note:
Ignore this step if you only have one IBM WebSphere Deployment Manager profile present.$WAS_HOME/bin/manageprofiles.sh -getDefaultName $WAS_HOME/bin/manageprofiles.sh -setDefaultName <opam_dmgr_profile_name>
-
Go to the following location:
$ORACLE_HOME/common/bin -
Using WSAdmin, run the
configureSessionManagerWas.pyscript. For example,-
On UNIX operating systems:
./wsadmin.sh –f $ORACLE_HOME/opam/tools/configureSessionManagerWas.py -o <Path to Oracle Home Directory>
-
On Windows operating systems:
.\wsadmin.cmd –f $ORACLE_HOME\opam\tools\configureSessionManagerWas.py -o <Path to Oracle Home Directory>
-
-
Start the servers, as described in Section 11.11.1.4, "Start the Servers."
Configure Oracle Identity Navigator on the Oracle Privileged Account Manager Managed Server
To configure Oracle Identity Navigator on the Oracle Privileged Account Manager managed server,
-
Stop the servers.
-
Go to the following location:
$ORACLE_HOME/common/bin -
Run
was_config.sh(orwas_config.cmdon Windows) and select the "OINAV for Managed Server" install template. Ignore the conflicts detected. -
Start the servers, as described in Section 11.11.1.4, "Start the Servers."
When you start the servers, Oracle Identity Navigator will be running on the OracleAdminServer and the Oracle Privileged Account Manager managed server. If required, you can remove the OracleAdminServer from the application targets.
11.12 Limitations and Known Issues When Using Oracle Privileged Account Manager on IBM WebSphere
This section describes any limitations or known issues for this delivery of Oracle Privileged Account Manager on IBM WebSphere.
11.12.1 Limitations
There are no limitations for this release of Oracle Privileged Account Manager on IBM WebSphere:
11.12.2 Known Issues
This section describes any known issues for using Oracle Privileged Account Manager on IBM WebSphere.
Table 11-4 Known Issues for Oracle Privileged Account Manager on IBM WebSphere
| Bug # | Issue |
|---|---|
|
16074104 |
When Oracle Privileged Account Manager is running on IBM WebSphere, you cannot add CSF mappings corresponding to a Oracle WebLogic Server domain. Similarly, when Oracle Privileged Account Manager is running on Oracle WebLogic Server, you cannot add CSF mappings corresponding to a IBM WebSphere cell. |