1 Introduction to the Life Cycle Management (LCM) Tools
This chapter describes and illustrates the deployment reference topologies you can deploy using the Life Cycle Management (LCM) tools and the instructions in this guide. It also summarizes the high-level tasks required to install and deploy the Oracle Identity and Access Management software using the LCM tools.
This chapter contains the following sections:
-
Section 1.1, "About the Automated Deployment of Oracle Identity and Access Management"
-
Section 1.2, "Overview of Deploying Oracle Identity and Access Management With the LCM Tools"
-
Section 1.3, "Oracle Identity and Access Management Topologies Supported by the LCM Tools"
-
Section 1.4, "Understanding the Supported Oracle Identity Manager Topologies"
1.1 About the Automated Deployment of Oracle Identity and Access Management
The following sections describe the Oracle Identity and Access Management automated deployment, patching, and upgrade tools:
-
Section 1.1.1, "Purpose of the Automation Tools for 11g Release 2 (11.1.2.3)"
-
Section 1.1.2, "Packaging and Distribution of the Automation Tools"
-
Section 1.1.3, "Deployment Capabilities of the LCM Tools for Oracle Identity and Access Management"
-
Section 1.1.4, "Patching Capabilities of the LCM Tools for Oracle Identity and Access Management"
-
Section 1.1.5, "Upgrade Capabilities of the LCM Tools for Oracle Identity and Access Management"
1.1.1 Purpose of the Automation Tools for 11g Release 2 (11.1.2.3)
The LCM tools provide automated installation and configuration capabilities for Oracle Identity and Access Management on both single host environments and on highly available, production systems.
Use this guide to automate the deployment of Oracle Identity and Access Management on a single host, primarily for evaluation of the Oracle Identity and Access Management software.
For information about using the LCM tools to deploy Oracle Identity and Access Management in a highly available production environment, refer to the Enterprise Deployment Guide for Oracle Identity and Access Management.
You can use the LCM tools as an alternative to the manual installation and configuration steps provided in the Installation Guide for Oracle Identity and Access Management.
1.1.2 Packaging and Distribution of the Automation Tools
Oracle packages all the software required to automatically deploy, patch, and upgrade Oracle Identity and Access Management in a single software distribution known as the Oracle Identity and Access Management Deployment Repository.
When you download and unpack the archives for Deployment Repository distribution, you end up with a directory structure that contains a software repository. Within this repository are all the software installers required to install and configure Oracle Identity Manager, as well as the Oracle Identity and Access Management Life Cycle Management Tools.
For more informations, see Section 2.5, "About the Deployment Repository and LCM Tools Directory Structure".
1.1.3 Deployment Capabilities of the LCM Tools for Oracle Identity and Access Management
The LCM tools for Oracle Identity and Access Management provide the following deployment capabilities and restrictions:
-
The Oracle Identity and Access Management LCM tools automate all aspects of installing, configuring, deploying, and patching the software.
Note however, that this guide describes a limited number of specific Oracle Identity and Access Management topologies on a single host. For more information about the topologies supported by this guide, see Section 1.3, "Oracle Identity and Access Management Topologies Supported by the LCM Tools".
For additional topologies, see the Enterprise Deployment Guide for Oracle Identity and Access Management.
-
The Oracle Identity and Access Management software and the required components such as the Java Development Kit (JDK), Oracle WebLogic Server, Oracle HTTP Server, and Oracle SOA Suite are packaged into a single repository that can be downloaded from the Oracle Technology Network (OTN) or the Oracle Software Delivery Cloud.
This single repository makes it easy to be sure you have the correct prerequisite software before you begin the deployment process. This repository includes a set of software installers and is a completely different download from the conventional distributions available for the standard, manual installation process.
-
If the LCM tools are used to deploy Oracle HTTP Server with the Oracle Access Manager Webgate software, then the Webgate will be configured to automatically protect relevant Oracle Identity and Access Management management consoles.
-
The LCM Tools use the Environment Health Check Utility to verify that your system requirements before you deploy and to verify the environment after you deploy.
For more information, see Verifying Your Oracle Identity and Access Management Environment.
-
The environment you deploy using the LCM tools can later be upgraded component by component, so as to minimize downtime.
Further, in an integrated environment, where the automated tools are used to deploy multiple Oracle Identity and Access Management products, you can choose to upgrade one product without affecting other products.
For more information, see the Oracle Fusion Middleware Upgrade Guide for Oracle Identity and Access Management.
1.1.4 Patching Capabilities of the LCM Tools for Oracle Identity and Access Management
You can use the LCM tools to apply one or more Interim (one-off) or Bundle Patches to an IDM deployment that was installed using the LCM tools. It is important to note that automated patching is supported only for those components installed and configured using the LCM tools.
All patching occurs within a patch session. Each Oracle Identity and Access Management deployment topology is implemented as multiple tiers, including the Directory tier, Application tier, and Web tier. Each product belongs to a single tier, but common patches, if found, are applied to all three.
A session can be created to apply one or more patches, or to rollback selected patches. A session in progress can be aborted if required. If actions need to be rolled back, in the current tier or for tiers that have already been completed, a new rollback session can be created using patches for the affected products.
When patching an environment that was created with the LCM tools, the LCM patching feature:
-
Patches all nodes
-
Applies the patch to both shared and local storage
-
Stops and starts affected servers
-
Executes post-patch artifact changes
-
Provides comprehensive state-sharing and reporting
Note:
Automated patching does not support the following:-
Patching of the database and Oracle WebLogic Server
-
Patching of Oracle Access Manager Webgates used for Web servers
-
Patching of the LCM Tools
For more information about the patching capabilities of the LCM tools, see "Patching Oracle Identity and Access Management Using Lifecycle Tools" in the Oracle Fusion Middleware Patching Guide for Oracle Identity and Access Management
1.1.5 Upgrade Capabilities of the LCM Tools for Oracle Identity and Access Management
For environments that were created using the LCM tools, the upgrade to a newer Oracle Identity and Access Management release is also automated.
To upgrade such an environment, you download a set of upgrade scripts, which can be customized to recognize the details of your environment. The scripts automate all the steps involved with upgrading an Oracle Identity Manager environment that was created using the LCM tools.
As with automated patching, the automated tools do not upgrade the database, JDK, or Webgate software. It does, however, upgrade the Oracle HTTP Server instances that were deployed using the LCM tools.
For more information, see the "Upgrading Oracle Identity and Access Management LCM Provisioned Environments" in the Oracle Fusion Middleware Upgrade Guide for Oracle Identity and Access Management.
1.2 Overview of Deploying Oracle Identity and Access Management With the LCM Tools
Table 1-1 describes each of the steps and provides links to more information about each step.
Table 1-1 Roadmap for Creating the Reference Topologies with the LCM Tools
| Task | Description | More Information |
|---|---|---|
|
Determine the topology you want to deploy |
Review the topologies supported by the LCM Tools and determine which topology is best suited for the requirements of your organization. |
Section 1.3, "Oracle Identity and Access Management Topologies Supported by the LCM Tools" |
|
Review the certifications and system requirements. |
Before you install and configure Oracle Identity and Access Management, you should ensure that your existing products are certified for use with Oracle Identity and Access Management. In addition, you should review the system requirements, such as memory and disk space requirements and required Linux install packages. |
Section 2.1, "Verifying Certification, System Requirements, and Interoperability" |
|
Run the Health Check Utility to ensure your certification and system requirements have been met. |
This step ensures that you can run the Deployment Wizard and the basic and mandatory system requirements have been met. |
Section 2.2, "Running the Health Check Utility to Verify Basic System Requirements" |
|
Determine the LDAP Directory requirements for the topology you selected |
Some of the supported topologies require a supported LDAP directory service. If you plan to use an existing directory service, there are tasks you must perform to prepare the directory for use with Oracle Identity and Access Management. |
|
|
Download and unpack the LCM Tools and Repository from the Oracle Technology Network (OTN) or the Software Delivery Cloud |
When you unpack the archives, you end up with a standard directory structure that includes a software repository. The software repository contains all the installers required to install the Oracle Identity and Access Management software, as well as the installer for installing the LCM Tools. |
Section 2.4, "Obtaining the LCM Tools and Oracle Identity and Access Management Software Repository" |
|
Identify and prepare a database for use with Oracle Identity and Access Management |
A database is required to store the required schemas for the Oracle Identity and Access Management products and components. You can identify an existing database instance, or use the database installation software included in the repository to install a new database. |
Section 2.6, "About Preparing a Database for an Oracle Identity and Access Management Deployment" |
|
Install the LCM Tools |
From the software repository, locate and run the LCM Tools installer, which installs the provisioning tools that enable you to automatically deploy Oracle Identity and Access Management. |
Section 2.8, "Installing the Oracle Identity and Access Management Lifecycle Tools" |
|
Run the Deployment Wizard to create a new deployment response file. |
The Deployment Wizard (one of the LCM Tools), prompts you for important information about your hardware and software environment, such as the selected topology, database, and LDAP directory information. The wizard uses this information to create a response file that can later be used to automatically deploy Oracle Identity and Access Management. |
|
|
Run the Deployment Wizard or the command line to deploy the Oracle Identity Manager software. |
For this step, you use the response file (which now contains all the details about your hardware and software environment) to deploy the Oracle Identity and Access Management software automatically. |
Chapter 5, "Performing Oracle Identity and Access Management Deployment" |
1.3 Oracle Identity and Access Management Topologies Supported by the LCM Tools
This section describes the reference topologies you can create using the Oracle Identity and Access Management LCM Tools. This guide provides complete instructions for creating this topology with the Oracle Identity and Access Management LCM Tools.
For more information, refer to the following topics:
1.3.1 Diagram of the OIM-Only Topology
Figure 1-1 shows the topology you can create by selecting the Oracle Identity Manager (OIM) Only option on the Select IAM Products page in the Oracle Identity Manager Deployment Wizard.
Figure 1-1 Oracle Identity Manager (OIM) Only Topology Diagram
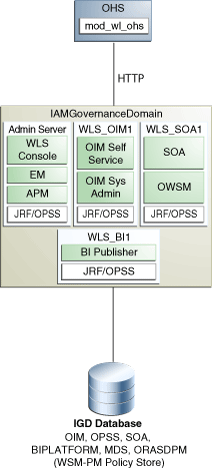
Description of ''Figure 1-1 Oracle Identity Manager (OIM) Only Topology Diagram''
1.3.2 Diagram of the Oracle Access Manager (OAM) Suite and Oracle Mobile Security Suite (OMSS) Only Topology
Figure 1-2 shows the topology you can create by selecting the Oracle Access Manager (OAM) Suite and Oracle Mobile Suite (OMSS) Only option on the Select IAM Products page in the Oracle Identity and Access Management Deployment Wizard.
Figure 1-2 Oracle Access Manager (OAM) Suite and Oracle Mobile Security Suite (OMSS) Only Topology Diagram
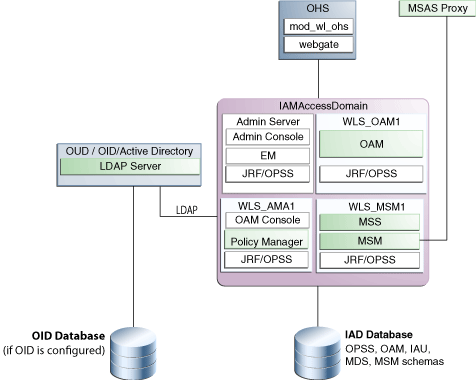
Description of ''Figure 1-2 Oracle Access Manager (OAM) Suite and Oracle Mobile Security Suite (OMSS) Only Topology Diagram''
1.3.3 Diagram of the OIM-OAM-OMSS Integrated with Directory Topology
Figure 1-3 shows the topology you can create by selecting the OIM-OAM-OMSS Integrated with Directory Only option on the Select IAM Products page in the Oracle Identity and Access Management Deployment Wizard.
Figure 1-3 OIM-OAM-OMSS Integrated with Directory Topology
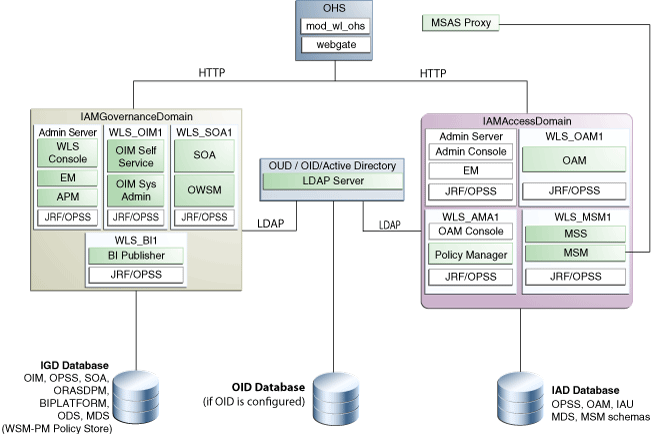
Description of ''Figure 1-3 OIM-OAM-OMSS Integrated with Directory Topology''
1.4 Understanding the Supported Oracle Identity Manager Topologies
Each of the topologies supported by the LCM Tools can be organized into three tiers, as a way to explain the purpose and structure of the topology elements:
-
Web Tier
-
Application Tier
-
Directory/Database Tier
Although it is not shown on the figures, there can also be a directory tier (which is often included in the database tier). If a dedicated directory tier is introduced, LDAP directories can be placed within that tier.
This section contains the following topics:
1.4.1 About the Web Tier
Most of the Identity and Access Management components can function without the web tier, but for most enterprise deployments, the web tier is desirable. For example, to support enterprise level single sign-on using products such as Oracle Single Sign-On and Access Manager, the web tier is required.
In the web tier, Oracle HTTP Server, WebGate (an Access Manager component), and the mod_wl_ohs plug-in module are installed. The mod_wl_ohs plug-in module enables requests to be proxied from Oracle HTTP Server to a WebLogic Server running in the application tier.
The web tier also is where the Mobile Security Access Server (MSAS) is installed when you select any topology that includes Oracle Access Manager. MSAS is a component in the Oracle Mobile Security Suite that provides a central access point for securing traffic from mobile devices to intranet resources. For more information, see "Mobile Security Access Server Architecture Overview" in Administering Oracle Mobile Security Access Server.
1.4.2 About the Application Tier
Depending on the topology you are deploying, the application tier can consist of the following Oracle Identity and Access Management components:
-
Oracle Access Management Access Manager (OAM) and its related components, deployed in the IAMAccess domain. Within this domain:
-
The Oracle WebLogic Server Administration Server hosts the Oracle WebLogic Server Administration Console, and Oracle Enterprise Manager Fusion Middleware Control.
-
A set of Managed Servers configured with Oracle JRF, which provides the frameworks and infrastructure for the Oracle Fusion Middleware software
-
The WLS_OAM1 Managed Server, which hosts the Oracle Access Manager J2EE application.
-
The WLS_AMA1 Managed Server, which hosts Access Management Administration software, including the Policy Manager and the Oracle Access Manager Console.
-
The WLS_MSM1 Managed Server, which hosts the Oracle Mobile Security Services sofware. Mobile devices can then be configured to use a proxy that connects to the Mobile Security Access Server, running on the WLS_MSM Managed Server.
-
-
The governance components, which are deployed to the IAMGovernence domain. Within this domain:
-
The Oracle WebLogic Server Administration Server for the domain hosts the Oracle WebLogic Server Administration Console, Oracle Enterprise Manager Fusion Middleware Control, and the Oracle Access Manager Console.
-
A set of Managed Servers configured with Oracle JRF, which provides the frameworks and infrastructure for the Oracle Fusion Middleware software
-
The WLS_OIM1 Managed Server, which hosts the Oracle Identity Manager self-service console and Oracle Identity Manager system administration software.
-
The WLS_SOA1 Managed Server, which hosts Oracle SOA Suite and Oracle Web Services Manager (OWSM).
-
The WLS_BI1 Managed Server, which hosts the Oracle Business Intelligence Publisher sofware, which is automatically configured for use with Oracle Identity Manager during deployment.
-
1.4.3 About the Directory/Database Tier
The database tier consists of:
-
One or more databases where the required product schemas are installed. The schemas installed depend up on which components are configured as part of the topology.
For an Oracle Access Manager deployment, the database is referred to as the IAD Database; for an Oracle Identity Manager deployment, it's referred to as the IGD Database.
-
An LDAP directory service (LDAP Server), which is preconfigured before deployment for use with Oracle Access Manager, or with LDAP sync when Oracle Identity Manager and Oracle Access Manager are deployed as part of an integrated topology.
This directory can be an Oracle Unified Directory, Oracle Internet Directory, or a Microsoft Active Directory Instance. If it is an Oracle Internet Directory instance, you can use a separate database for the Oracle Internet Directory data.