49.3 Defining Service Providers
A Service Provider is defined for each back-end service that is available to client applications.
This configures how the Mobile and Social server will interface with the defined back-end Service Provider. Depending on the services that you are providing, you may only need to configure one or two of the available Service Provider options. For example, if you are only providing authentication services, you do not need to define the User Profile Service Provider or Authorization Service Provider.
You need to familiarize yourself with the following topics to define Service Providers:
49.3.1 Defining, Modifying or Deleting an Authentication Service Provider
An Authentication Service Provider allows Mobile and Social to authenticate users, client applications, and access permissions using a back-end Authentication Service by way of a token exchange.
Upon successful authentication and verification, a token may be returned to the client application. The following authentication types are supported.
-
When installed with Access Manager, Mobile and Social supports JSON Web Tokens (JWT) and Access Manager (OAM) tokens.
-
When installed without Access Manager, only the JSON Web Token (JWT) type is supported.
Note:
See Deployment Constraints for Mobile and Social for information about deploying Mobile and Social with a Webgate.
The following topics include information regarding Authentication Service Providers:
49.3.1.1 Pre-Configured Authentication Service Providers
Mobile and Social provides pre-configured Authentication Service Providers for the Authentication Services listed.
See Table 49-1 for details.
For each token type (Access Manager and JWT), Mobile and Social provides separate "out-of-the-box" mobile and non-mobile (or desktop) Service Provider configurations. Separate configurations are provided so that you can optimize each to best meet the needs of each access mode. Mobile devices must use a mobile Service Provider, however, non-mobile devices can use either a mobile service provider or a non-mobile service provider if correct input is provided.
Mobile Service Providers use Client Registration Handles to register mobile devices, whereas non-mobile Service Providers use Client Tokens to authenticate non-mobile devices. The Client Token capability in Mobile and Social can be disabled, but the Client Registration Handle capability cannot.
Table 49-1 Pre-configured Authentication Service Providers
| Authentication Service | Mobile and Social Service Provider Name | Description |
|---|---|---|
|
Access Manager |
OAMAuthentication |
Provides pre-configured support for users using desktop devices to authenticate using Access Manager. This Service Provider can issue a Client Token, but it cannot register mobile devices. The following Java class implements this Service Provider: oracle.security.idaas.rest.provider.token.OAMSDKTokenServiceProvider |
|
Mobile Access Manager |
MobileOAMAuthentication |
Provides pre-configured support for users using mobile devices to authenticate using Access Manager. This Service Provider supports registering new devices using a Client Registration Handle when the User authenticates. The following Java class implements this Service Provider: oracle.security.idaas.rest.provider.token.MobileOAMTokenServiceProvider |
|
JSON Web Token |
JWTAuthentication |
Provides pre-configured support for users using non-mobile applications to authenticate using the JSON Web Token format. JSON Web Token is a compact token format that is suitable for space-constrained environments such as HTTP Authorization headers. This Service Provider can issue a Client Token, but it cannot register new devices using a Client Registration Handle. The following Java class implements this Service Provider: oracle.security.idaas.rest.provider.token.JWTTokenServiceProvider |
|
Mobile JSON Web Token |
MobileJWTAuthentication |
Provides pre-configured support for users using mobile devices to authenticate using the Mobile JSON Web Token format. This Service Provider supports registering new devices using a Client Registration Handle. The following Java class implements this Service Provider: oracle.security.idaas.rest.provider.token.MobileJWTTokenServiceProvider |
|
JWT-OAM Token Provider |
JWTOAMAuthentication |
Allows lightweight, long-duration JWT tokens to be exchanged for OAM tokens. OAM tokens provide SSO and OAM resource access to clients. This provider allows users using non-mobile applications to get a new OAM token without having to provide credentials if they have a valid, long-duration JWT token. |
|
Mobile JWT-OAM Token Provider |
MobileJWTOAMAuthentication |
Allows lightweight, long-duration JWT tokens to be exchanged for OAM tokens. OAM tokens provide SSO and OAM resource access to clients. This provider allows users using mobile applications to get a new OAM token without having to provide credentials if they have a valid, long-duration JWT token. |
|
Social Identity Web Token |
InternetIdentityAuthentication |
Provides pre-configured support for apps using Mobile and Social Services to accept an authentication result from Social Identity (for example, Google, Facebook, Twitter, and so on). This Service Provider supports registering new devices using a Client Registration Handle. After the User authenticates with the Identity Provider, this Service Provider issues a User Token to the requesting client application. The User Token allows the User to obtain a Client Registration Handle for the device. This service uses the same Java class as the JSON Web Token service, but it is configured with two additional name-value attribute pairs. The following Java class implements this Service Provider: oracle.security.idaas.rest.provider.token.JWTTokenServiceProvider |
49.3.1.2 JWT-OAM Token Authentication Service Provider
Depending on your deployment, you may want to have a long-duration JWT token instead of one or more long-duration OAM tokens. A JWT token is lightweight and makes an ideal token to hold for a long duration.
Using the JWT-OAM token exchange feature, your application authenticates the user with a user name and password, then obtains a JWT token, an OAM user token, and an OAM master token. You can configure the JWT token to have a very long duration compared to the duration of OAM tokens. Once the OAM tokens expire, clients use the still-valid long-duration JWT token to get OAM tokens again.
The presence of OAM tokens can provide mobile and non-mobile clients with access to resources protected by Access Manager. Exchanging a JWT token for OAM tokens benefits the user, who does not need to provide credentials to get new OAM tokens to replace the expired tokens.
As an added security measure, Mobile and Social can require users to enter an additional credential, such as a PIN, when using a JWT user token to get an OAM token.
See Using User Credentials to Exchange a JWT Token for an OAM Token.
49.3.1.3 Creating an Authentication Service Provider
You can create an authentication service provider and modify its default attributes and values.
To create an Authentication Service Provider:
49.3.1.4 Editing or Deleting an Authentication Service Provider
You can edit or delete an Authentication Service Provider.
Select the Service Provider in the panel and click Edit or Delete on the panel's tool bar.
49.3.1.5 Using User Credentials to Exchange a JWT Token for an OAM Token
As an added security measure, Mobile and Social can require users to enter an additional credential, such as a PIN, when using a JWT user token to get an OAM token.
To enable the user PIN requirement, specify the JWT_UT+CRED parameter as described in Table 49-5 when configuring the TokenExchangeInput attribute.
To use this feature, the user PIN or other credential must be present in the user entry in the directory server. Mobile and Social does not put restrictions on credential values; it simply validates the credential value submitted by the user with the value present in the user entry. For security reasons, user credentials should be saved as hashed attributes.
See Configuring OAM to use the JWT-OAM and PIN Token Service Provider for the steps required to get this configuration to work.
49.3.1.6 Configuring OAM to use the JWT-OAM and PIN Token Service Provider
You can configure OAM to use the JWT-OAM and the PIN Token Service Provider.
To configure:
-
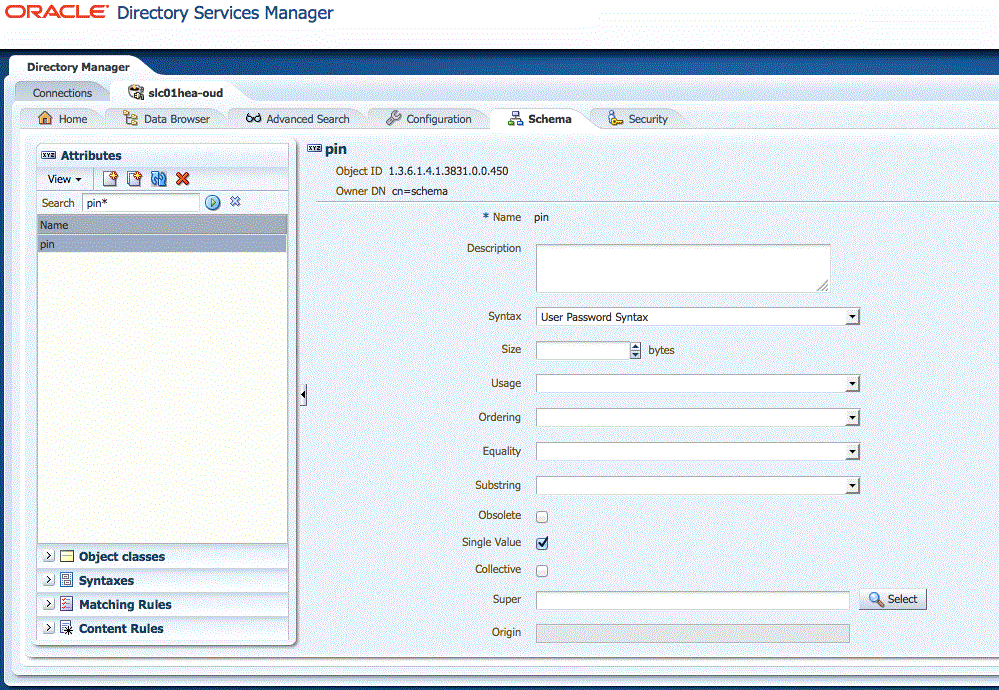
Open your directory server and extend the LDAP Schema for the PIN Attribute. After the LDAP schema change, you can add new users and modify existing users to have a PIN value.
-
Create the PIN attribute.
Figure 49-1 provides an example on how to use Oracle Directory Services Manager (ODSM) and Oracle Unified Directory (OUD).
Figure 49-1 Using ODSM to create the PIN attribute in OUD
-
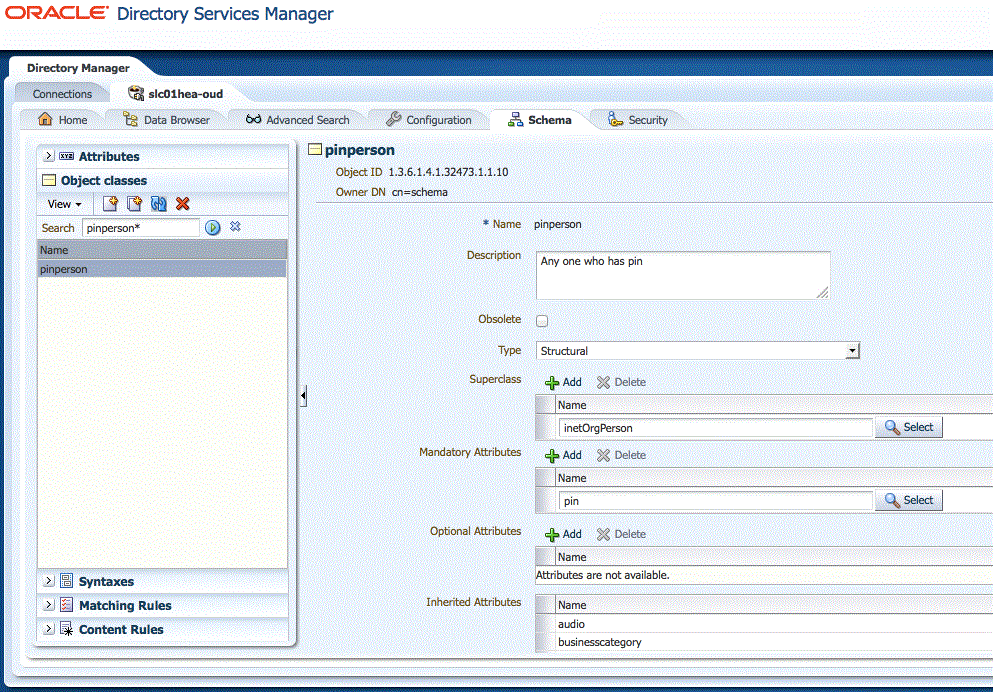
Create a PINPERSON object class.
Figure 49-2 provides an example using Oracle Directory Services Manager (ODSM).
Figure 49-2 Using ODSM to create the pinperson object class
-
-
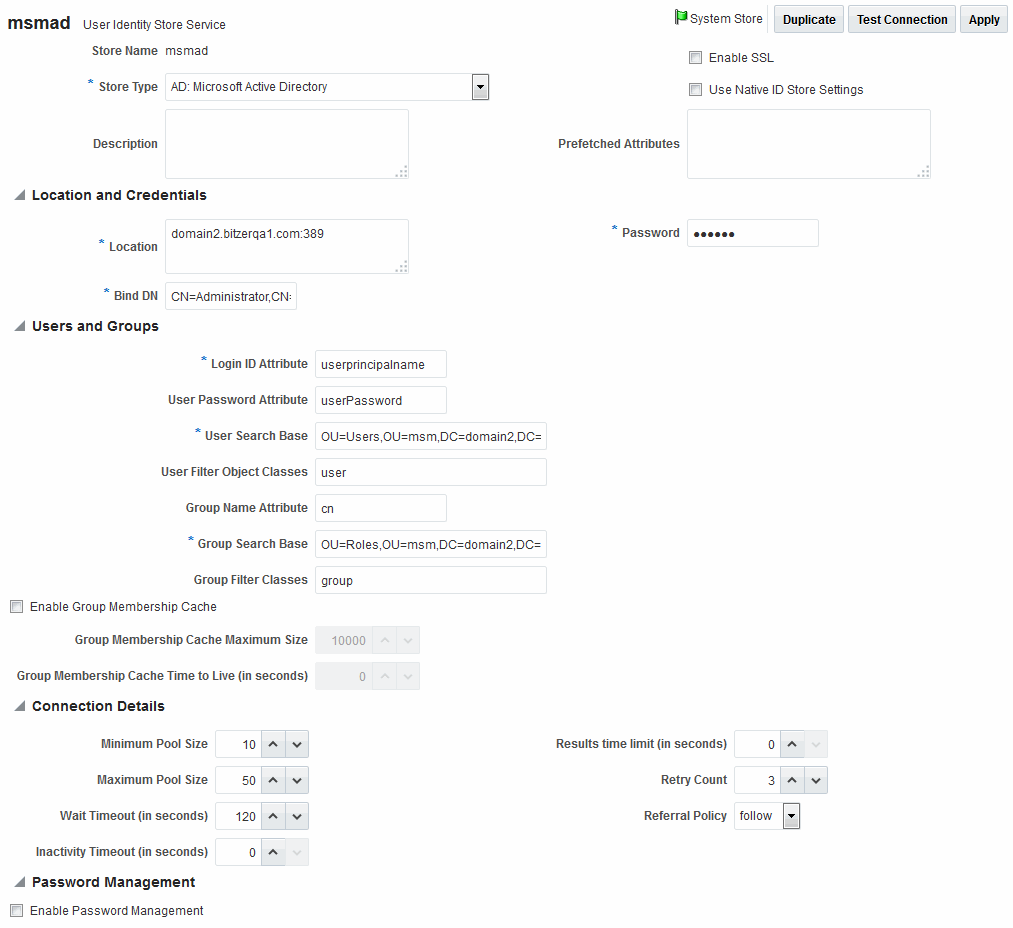
Using the OAM Console, create a new IdentityStore for the external LDAP server that you extended to use the PIN attribute.
-
Log in to the OAM Console and click Configuration at the top of the window.
-
Click User Identity Stores.
-
Click the Create button to create a new IdentityStore in OAM ID Stores.
See Figure 49-3 for details.
Figure 49-3 Using the OAM Console to create an IdentityStore
-
-
Add a new OAM authentication module for the new Identity Store.
-
In the OAM console, click Application Security at the top of the window.
-
Select Create Custom Authentication Module from the Create (+) drop-down menu in the Plug-ins section.
-
On the General tab, type a Name--for example,
PINBasedUserPlugin. -
On the Steps tab, type the following values:
Step Name:
UIPlug-in Name:
UserIdentificationPlugInPlug-in Parameters:
- KEY_LDAP_FILTER:
(&(uid={KEY_USERNAME})(pin={cred}))- KEY_IDENTITY_STORE_REF:
OUDIdentityStore(This data store has to be added first to do this step.)- KEY_SEARCH_BASE_URL:
ou=users,dc=ngam,dc=oracle,dc=com -
On the Steps Orchestration tab, choose UI from the Initial Step menu.
-
-
Add a new authentication scheme.
-
In the OAM console, click Application Security at the top of the window.
-
Select Create Authentication Scheme from the Create (+) drop-down menu in the Access Manager section.
-
Complete the form:
Name:
PINBasedUserAuthNSchemeAuthentication Level:
3Challenge Method:
FORMAuthentication Module: Choose the authentication module you created in the previous step--for example,
PINBasedUserPlugin.
-
-
Change the authentication policy to use the new authentication scheme.
-
In the OAM console, click Application Security at the top of the window.
-
Click Application Domains in the Access Manager section.
-
FInd the IAM Suite domain and open the OICTokenExchangePolicy policy.
-
From the Authentication Scheme drop-down menu, choose PINBasedUserAuthNScheme.
-
-
Configure the (Mobile) JWTOAMAuthenticationProvider.
-
In the OAM console, click Mobile Security at the top of the window.
-
Click Mobile and Social Services.
-
Open the MobileJWTOAMAuthentication service provider for editing.
-
From the Identity Directory Service Name drop-down menu, choose the directory service that points to the IdentityStore you created in step 2.
-
If a desktop (or non-mobile) service is required, repeat steps a and b to configure the JWTOAMAuthentication provider.
-
-
Create an application profile.
-
In the OAM console, click Mobile Security at the top of the window.
-
Click Mobile and Social Services.
-
In the Application Profiles section, click the Create button and create a new application profile (for example,
mobileapp1).
-
-
Update the MobileServiceDomain.
-
In the OAM console, click Mobile Security at the top of the window.
-
Click Mobile and Social Services.
-
In the Service Domains section, find the MobileServiceDomain domain and open it for editing.
-
In the Application Profiles section (subtab), add the application profile you created in the previous step (
mobileapp1). -
Click the Service Profiles subtab to open it and change the Authentication Service to
MobileJWTOAMAuthentication.
-
49.3.2 Defining, Modifying or Deleting an Authorization Service Provider
An Authorization Service Provider allows a back-end Identity service to make authorization decisions on behalf of a connected application.
The following topics provide information about Authorization Service Providers:
49.3.2.1 Creating an Authorization Service Provider
You can create an authorization service provider and modify its attributes and values.
To create:
49.3.2.2 Editing or Deleting an Authorization Service Provider
You can edit or delete an Authorization Service Provider.
Select the Service Provider in the panel and click Edit or Delete on the panel's tool bar.
49.3.2.3 Pre-Configured Authorization Service Provider
Mobile and Social provides a pre-configured Authorization Service Provider for Access Manager named the OAMAuthorization Authorization Service Provider.
The oracle.security.idaas.rest.provider.authorization.OAMSDKAuthZServiceProvider Java class implements the pre-configured Authorization Service Provider.
49.3.3 Defining, Modifying or Deleting a User Profile Service Provider
A User Profile Service Provider allows an application to query and update a directory server.
Many LDAP compliant directory servers are supported including:
-
Microsoft Active Directory
-
Novell eDirectory
-
Oracle Directory Server Enterprise Edition
-
Oracle Internet Directory
-
Oracle Unified Directory
-
Oracle Virtual Directory (using the Oracle Internet Directory template)
-
OpenLDAP
-
IBM Tivoli Directory Server (using the OpenLDAP template)
-
WebLogic Server Embedded LDAP
Mobile and Social includes a pre-configured User Profile Service Provider that your organization can use, or you can create your own. Before you can create a User Profile Service Provider you must first create an Identity Directory Service profile. The (IDS) is a flexible service used by Access Manager as the means for accessing multiple identity data stores. For more information about the Identity Directory Service, see Managing the Identity Directory Service User Identity Stores.
The following sections contain more information about User Profile Service Providers.
49.3.3.1 Creating a User Profile Service Provider
You can create a User Profile Service Provider and modify its attributes and values.
To create:
49.3.3.2 Editing or Deleting a User Profile Service Provider
You can edit or delete a User Profile Service Provider.
Select the Service Provider in the panel and click Edit or Delete on the panel's tool bar.
49.3.3.3 User Profile Service Provider Configuration Properties
When you edit a User Profile Service Provider that you or another Administrator has already created, the additional User Profile Service Provider Configuration properties for the Identity Directory Service connection appears.
The additional User Profile Service Provider Configuration properties are as follows:
Name - The name of this User Profile Service Provider.
Description - (Optional) Type a short description that will help you or another Administrator identify this service in the future.
Attributes
Add or delete User Profile Service Provider Attributes and their values.
See Table 49-8 for details.
Note:
LDAP attribute names are generally not case sensitive but when communicating with the Oracle Identity Governance Framework (IGF), LDAP attribute names are case sensitive.
Table 49-9 User Profile Service Provider Default Attribute Names and Values
| Name | Default Value | Notes |
|---|---|---|
|
|
false |
Supported values include |
|
|
|
If accessControl is enabled, specify the distinguished name (DN) of the adminGroup to see if the User is in it. |
|
|
|
Supported values include |
|
|
true |
Supported values include This attribute is not included in a new installation of Mobile and Social. An Administrator can add this property. |
Identity Directory Service
Name - The Identity Directory Service profile that connects the User Profile Service Provider to one or more directory servers. For more information about the Identity Directory Service.
See Managing the Identity Directory Service User Identity Stores.
-
If either of the default Identity Directory Services are selected (either
userroleoridxuserrole) you cannot view or edit the configuration values. -
If an Identity Directory Service connection that you or another Administrator created is selected, you can view and edit the configuration values as needed.
Relationship Configuration
Type the URI segment used to access the corresponding column in the Identity Directory Service. Use Add to add a new relationship or Remove to remove a configured relationship.
-
Access URI - Type a URI segment that will be used to access a corresponding data column in the Identity Directory service. For example, if
memberOfis the Access URI, then:http://host:port/.../idX/memberOf
would be the URI to access related entities of an entity with ID
idX. -
Identity Directory Service Relation - Choose the Directory Service relationship that is to be accessed by the Access URI segment. You can configure relationships on the Relationships tab in the Identity Directory Service configuration section provided that the Identity Directory Service is not the pre-configured UserProfile Identity Provider. (You cannot configure Identity Directory Service relationships for the UserProfile Service Provider.)
-
Entity URI Attribute - Type the JSON attribute name to be used in the URI response sent from the Mobile and Social server. For example, if person-uri is the specified entity URI attribute, the URI response would be as follows:
{ {"person-uri":uriY1, ...}, {"person-uri":uriY2, ...}, ... }where
uriY1anduriY2are the direct URIs to access each of the related entities. -
Scope for Requesting Recursion - Use Scope attribute values with the scope query parameter to retrieve a nested level of attributes in a relationship search. To access related entities recursively, type the value to be used. The Mobile and Social default configuration uses two scope attribute values:
toTopandall. If the Scope for Requesting Recursion value is the attribute valueall, then the following REST URI example is used to make the request:http://host:port/.../idX/reports?scope=all
In this example, the URI returns the entities related to the entity with ID
idX, as well as all further related entities.